Navigation
- Verify Domain Controller Certificates
- LDAP Load Balancing
- Create LDAP Authentication Server
- Authentication Feedback and Global Licenses
- Multiple Active Directory Domains
Verify LDAPS
Use the tool ldp.exe to verify that the Domain Controllers have valid certificates installed and the service account is able to bind to the LDAP tree.
- ldp.exe is included with the Remote Server Administration Tools (AD DS Snap-Ins and Command-Line Tools)
- Run ldp.exe
- Open the Connection menu and click Connect.
- Check the box next to SSL. Change the port to 636. Then enter the FQDN of a Domain Controller and click OK.
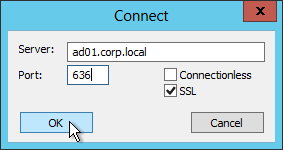
- If it connected successfully, you can then attempt a bind. If the connection was unsuccessful then there’s probably an issue with the certificate installed on the Domain Controller.
- Open the Connection menu and click Bind.
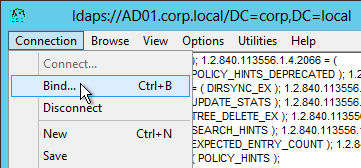
- Change the Bind type to Simple bind. Then enter the service account credentials. You can use DOMAIN\Username or you can use Username@Domain.com. Click OK.
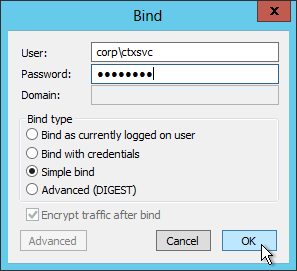
- Look on the right pane to verify a successful bind. If not, fix the credentials and try again.
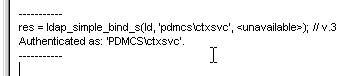
- Once you have successfully binded, you can view the directory tree by opening the View menu and click Tree.
- Click the drop-down to view the directory partitions.
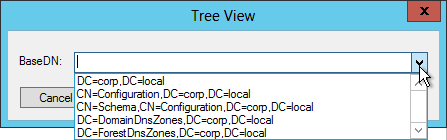
- Repeat these steps to verify each Domain Controller and any load balanced LDAPS.
LDAP Load Balancing
Before you create an LDAP authentication policy, setup LDAPS load balancing:
You can create multiple load-balancing Virtual Servers to load balance multiple domains. These load-balancing Virtual Servers can share the same VIP if their port numbers are different. Or you can use a different VIP for each domain.
LDAP Server
To create the LDAP Authentication Server, do the following:
- On the left, expand Authentication and click Dashboard.
- On the right, click Add.
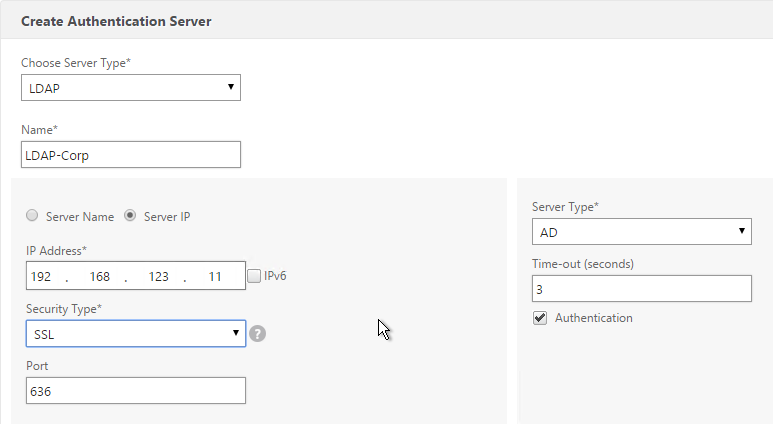
- In the Choose Server Type drop-down, select LDAP.
- Enter LDAP-Corp as the name. If you have multiple domains, you’ll need a separate LDAP Server per domain so make sure you include the domain name.
- Change the selection to Server IP. Enter the VIP of the load balancing vServer for LDAP.
- Change the Security Type to SSL.
- Enter 636 as the Port. Scroll down.
- In the Connection Settings section, in the Base DN field, enter your Active Directory DNS domain name in LDAP format.
- Enter the credentials of the LDAP bind account in userPrincipalName format. Domain\Username also works.
- Check the box next to BindDN Password and enter the password. Scroll down.
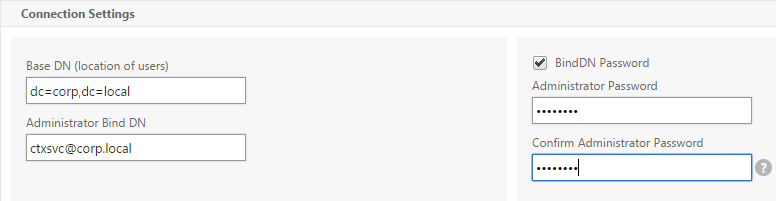
- In the Other Settings section, use the drop-down next to Server Logon Name Attribute, Group Attribute, and Sub Attribute Name to select the default fields for Active Directory.
- On the right, check the box next to Allow Password Change.
- Note: there is a checkbox for Validate LDAP Server Certificate. If you want to do this, see Citrix Discussions for instructions for loading the root certificate to /nsconfig/truststore.
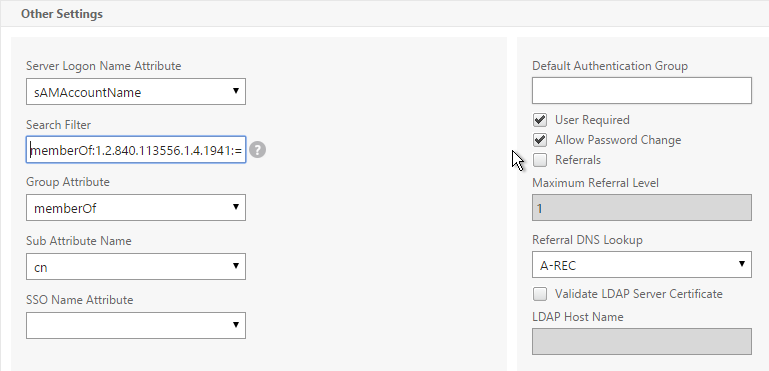
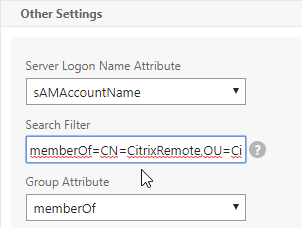
- If you want to restrict access to only members of a specific group, in the Search Filter field, enter memberOf=<GroupDN>. See the example below:
memberOf=CN=CitrixRemote,OU=Citrix,DC=corp,DC=localYou can add :1.2.840.113556.1.4.1941: to the query so it searches through nested groups. Without this users will need to be direct members of the filtered group.memberOf:1.2.840.113556.1.4.1941:=CN=CitrixRemote,OU=Citrix,DC=corp,DC=local
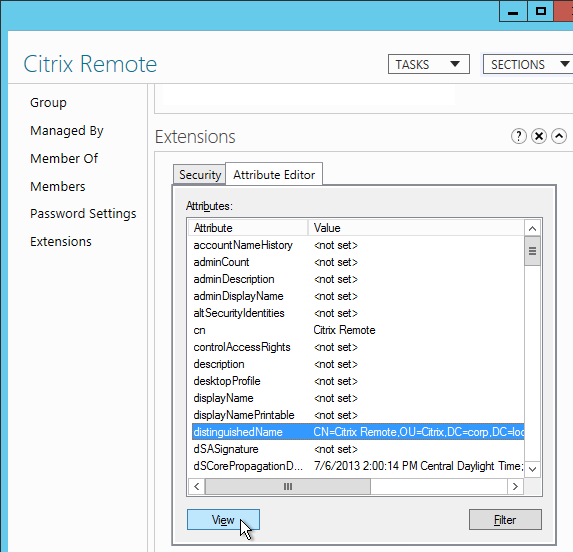
Citrix CTX132802 How to Use the ldapsearch Utility on the NetScaler Gateway Enterprise Edition Appliance to Validate a Search Filter- An easy way to get the full distinguished name of the group is through Active Directory Administrative Center. Double-click the group object and switch to the Extensions page. On the right, switch to the Attribute Editor tab.
- Or in Active Directory Users & Computers, enable Advanced view, browse to the object (don’t use Find), double-click the object, and switch to the Attribute Editor tab.
- Scroll down to distinguishedName, double-click it and then copy it to the clipboard.
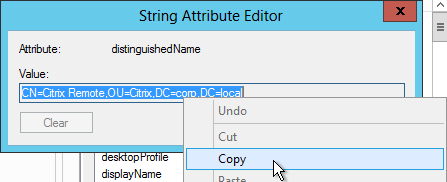
- Back on the NetScaler, in the Search Filter field, type in memberOf= and then paste the Distinguished Name right after the equals sign. Don’t worry about spaces.
- Scroll down and click More.
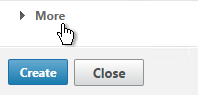
- For Nested Group Extraction, if desired, change the selection to Enabled.
- Set the Group Name Identifier to samAccountName.
- Set the Group Search Attribute to memberOf. Select << New >> first.
- Set the Group Search Sub-Attribute to CN. Select << New >> first
- For the Group Search Filter field, see CTX123795 Example of LDAP Nested Group Search Filter Syntax.
- Scroll down and click Create.
add authentication ldapAction Corp-Gateway -serverIP 10.2.2.210 -serverPort 636 -ldapBase "dc=corp,dc=local" -ldapBindDn "corp\\ctxsvc" -ldapBindDnPassword Passw0rd -ldapLoginName samaccountname -searchFilter "memberOf=CN=Citrix Remote,CN=Users,DC=corp,DC=local" -groupAttrName memberOf -subAttributeName CN -secType SSL -passwdChange ENABLED
- The status of the LDAP Server should be Up.
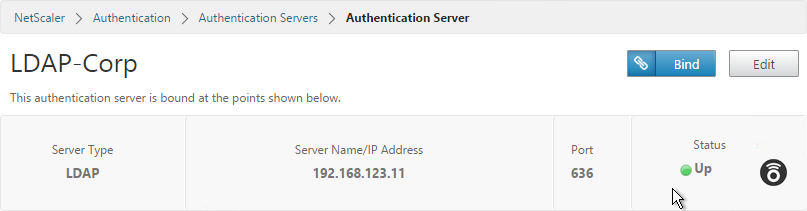
- The Authentication Dashboard doesn’t allow you to create the LDAP Policy at this time. Instead the LDAP Policy will be created later when you bind the LDAP Server to the NetScaler Gateway vServer.
Authentication Feedback and Licenses
- On the left, under NetScaler Gateway, click Global Settings.
- On the right, in the right column, click Change authentication AAA settings.
- If you are using Gateway features that require Gateway Universal licenses, then change the Maximum Number of Users to the number of Gateway Universal licenses you have installed on this appliance. This field has a default value of 5, and administrators frequently forget to change it, thus only allowing 5 users to connect.
- If desired, check the box for Enable Enhanced Authentication Feedback. This feature provides a message to users if authentication fails. The message users receive include password errors, account disabled or locked, or the user is not found, to name a few. Click OK.
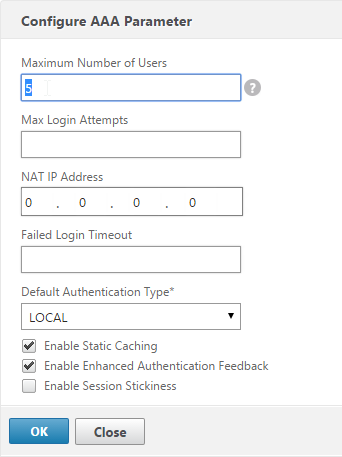
set aaa parameter -enableEnhancedAuthFeedback YES -maxAAAUsers 200
Next Step
- For two-factor, configure RADIUS Authentication
- Otherwise, Configure NetScaler Gateway Session Policies
Multiple Domains
To support multiple Active Directory domains on a NetScaler Gateway, you create multiple LDAP authentication policies, one for each Active Directory domain, and bind all of the LDAP policies to the NetScaler Gateway Virtual Server. When the user logs into NetScaler Gateway, only the username and password are entered. The NetScaler will then loop through each of the LDAP policies in priority order until it finds one that contains the entered username/password.
What if the same username is present in multiple domains? As NetScaler loops through the LDAP policies, as soon as it finds one with the specified username, it will try to authenticate with that particular LDAP policy. If the password doesn’t match the user account for the attempted domain then a failed logon attempt will be logged in that domain and NetScaler will try the next domain.
Unfortunately, the only way to enter a realm name during user authentication is to require users to login using userPrincipalNames. To use userPrincipalName, set the LDAP Policy/Server with the Server Logon Name Attribute set to userPrincipalName.
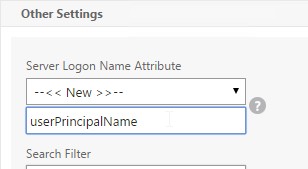
You can even do a combination of policies: some with samAccountName and some with userPrincipalName. The samAccountName policies would be searched in priority order and the userPrincipalName policies can be used to override the search order. Bind the userPrincipalName policies higher (lower priority number) than the samAccountName policies.
Note: NetScaler 11.0 build 64 supports adding a domain name drop-down list to the logon page. Then use Cookie expressions in the auth policies and session policies. However, this probably doesn’t work for Receivers. See CTX203873 How to Add Drop-Down Menu with Domain Names on Logon Page for NetScaler Gateway 11.0 64.x and later releases for details. 💡
After authentication is complete, a Session Policy will be applied that has the StoreFront URL. The NetScaler Gateway will attempt to log into StoreFront using SSO so the user doesn’t have to login again. When logging into NetScaler Gateway, only two fields are required: username and password. However, when logging in to StoreFront, a third field is required: domain name. So how does NetScaler specify the domain name while logging in to StoreFront?
There are two methods of specifying the domain:
- Configure multiple session policies with unique Single Sign-on Domains. Inside the Session Policy is a field called Single Sign-on Domain for specifying the domain name. If there is only one Active Directory domain then you can use the same Session Policy for all users. However, if there are multiple domains then you would need multiple Session Policies, one for each Active Directory domain. But as the NetScaler loops through the LDAP policies during authentication, once a successful LDAP policy is found, you need a method of linking an LDAP policy with a Session Policy that has the corresponding SSO Domain. This is typically done using AAA groups. This method is not detailed here but the general steps are: In the LDAP policy, specify a Default Authentication Group. Create a AAA group that matches it. Then bind the corresponding Session Policy to that AAA group.
- Alternatively, configure the LDAP policy/server to extract the user’s UPN and then authenticate to StoreFront using UPN. This is the easiest method but some domains don’t have userPrincipalNames configured correctly.
This userPrincipalName method is detailed below:
- In each of your NetScaler LDAP policies/servers, in the Other Settings section, in the SSO Name Attribute field, enter userPrincipalName (select –<< New >>– first). Make sure there are no spaces after this name. NetScaler will use this attribute to authenticate the user against StoreFront.
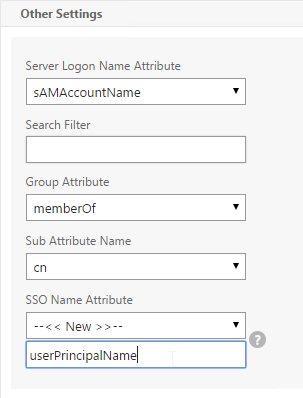
- In StoreFront Console, right-click the Store, and click Manage Authentication Methods.
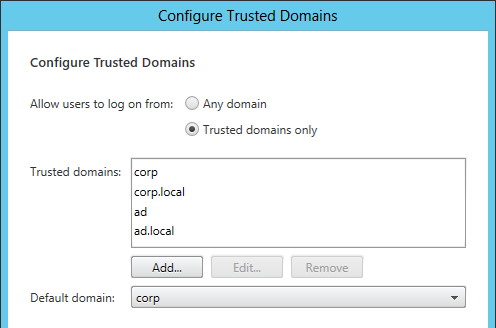
- On the right, click the gear icon, and then click Configure Trusted Domains.
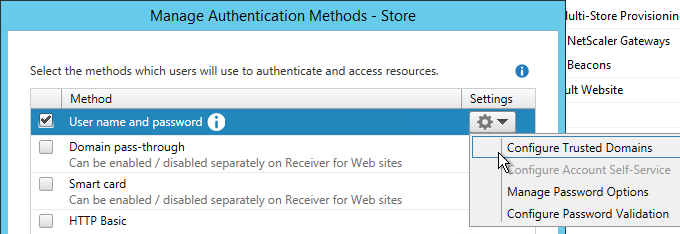
- In the Trusted domains box, select Any domain.
- Or add your domains in DNS format. The advantage of entering domain names is that you can select a default domain if internal users forget to enter a domain name during login. The DNS format is required for UPN logins (e.g. SSO from NetScaler Gateway).
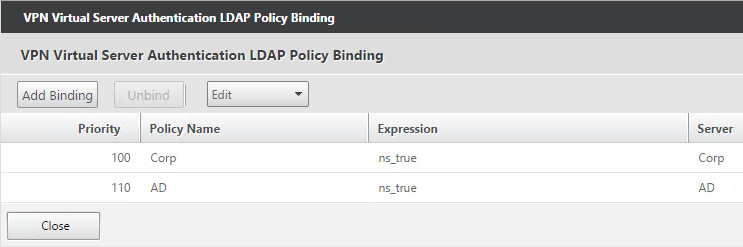
- On the NetScaler Gateway Virtual Server, bind LDAP authentication polices in priority order. It will search them in order until it finds a match.
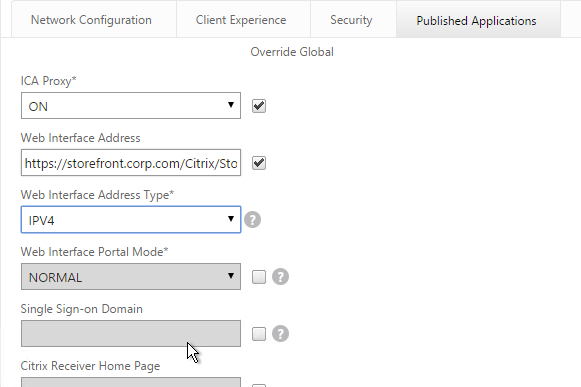
- In your session policies, make sure Single Sign-on Domain is not configured. Since NetScaler is using the userPrincipalName, there’s no need to specify a domain. If Single Sign-on Domain is configured, then Single Sign-on authentication will fail.
Carl,
Just followed the Citrix Federated Authentication Service instructions.
Now when we login we get “The Username or password is incorrect” when launching the citrix desktop.
Before setup of FAS, the netscaler was configured for idp/SAML and we could successfuly login albeit authenticating to Microsoft as username@domain.com then to launch the citrix desktop simply as “SAMaccountname”
I think the storefront server is not accepting the UPN as we cannot login directly to Storefont as the UPN.
Can you help? What are we missing?
Thanks
What do you see in StoreFront Server > Event Viewer > Applications and Services > Citrix Delivery Services?
Hi Carl,
somehow I’m missing the option to “Allow Password Change” in the LDAP server settings. Authentication is working fine, but I would like to give users the option to change their passwords.
Any obvious things that springs to mind?
Thanks!
Is the protocol set to SSL or TLS?
Spot on Carl, we’re using “Plaintext” and thus this choice were not available. Changed to SSL now an everything is working.
Thank you!
Hi Carl,
Hope You are safe and Good during this pandemic. This is a bit emergency help. I will explain in detail below.
We have two domains (ca.ds.com and internal.thecs.com). We are using Netscaler for the gateway. We want both the domain users (users are with different username and password) to access the same production citrix url and use the published resources.
1.The domain trust has been established
2.Two LDAP policy has been created in Netscaler Gateway
3.We have added both the domains in the store front trusted domains.
Now what happens is When the user from ca.ds.com access the Citrix gateway with username and password it is getting authenticated and the published resources are available and users are able to access it.
But when the users from internal.thecs.com tries to access the Citrix gateway, after they enter the credentials(username and password) the page comes to this error “Server Error : 404 – File or Directory not Found.
The Resource you are looking for might have been removed, had its name changed , or is temporarily unavailable.”
Please help me this is bit critical we are stuck in with the production downtime.
Thank You,
Azifkhan.N
What URL do you see in the address bar? Is it valid for the StoreFront server? Do you have a Session Policy with the invalid Web Interface address?
Hi Carl,
Thanks for your quick reply so kind of you. i see the same url of my store. yes it is valid. When users try to connect from ca.ds.com domain they are able to access everything.but when users from internal.thecs.com they get this error. we have one session policy with valid web interface address. Do i need to have one more policy and with invalid web interface address?
Thanks,
Azifkhan.N
I assume the URL is /Citrix/StoreWeb or something like that?
Are you able to log into StoreFront from an internal machine (not through Gateway) using the new domain’s credentials?
Hi Carl,
Sorry for the late response . Was on a medical emergency . Please do help me as soon as possible . As i have mentioned earlier i was wrong , when i connect internal.thecs.com it is routing to my old store url. Only when users login with ca.ds.com credentials the url is pointing to new store. But the login url is same for all the users.
1.We have the old STA still in the gateway configuration (does it do any issues)
Please help me how to proceed further.
Thank,
Azifkhan.N
Great article Carl.
I configured AAA with LDAP authentication with multiple domains (Domain1 & Domain2). For some reason the Netscaler seems to be checking only if the user exists on either domains but not the passwords. If I enter correct username and wrong password it let’s the user through to the website. Any idea where I have configured it incorrectly?
In each LDAP server, make sure the Authentication checkbox on the top right is enabled. It’s checked by default.
Hi Carl,
Please advise I have configured Single Netscaler access gateway, the gateway is accessible for LAN and internet users.
I want to achieve AD Group1 LAN users should be able to access gateway URL and published XenApp resources, but few users i.e. 5 users out of 10 from same AD Group1 should not be able to authenticate gateway URL or XenApp resources should not be available for them over Internet.
Ho to achieve this with Netscaler 12.1 MPX
If you put the “Allowed” users in a new AD group, then you can configure the NetScaler LDAP Policy with a Search Filter that only allows members of that group to authenticate. I think this article has instructions for the Search Filter.
SmartAccess is more complicated.
Is there a way to provide a better error message than ‘Invalid credentials’ for those who are not in the AD group that’s allowed to auth through the gateway? Something like, ‘you do not have access to this portal. call the helpdesk.’
NetScaler has an Enhanced Authentication Feedback option but I’m not sure what it would say for this scenario. If it’s somewhat unique, then there are language files that can be modified with whatever message you want.
On the screenshot it shows blank on the field “Server Logon Name Attribute” after you added distinguished name. Is it supposed to changed to blank from samaccountName or left blank accidentally? Also, I seen a bug with netscaler that it adds long phantom password after reboot or making changes, which usually fixes after typing correct password for LDAP authentication. I get that issue every time I reboot during maintenance on 11.1 version
I probably added that screenshot later than the others. I’ll try to spin up a NetScaler 11.0 appliance and fix it. In the meantime, my 11.1 and 12.0 articles should have the correct screenshot.
Carl,
I see the option to change password using a web browser; accessing internally and externally. I do not see the option in the citrix receiver. Is this not an option using the citrix receiver 4.4.2000.16? Also when the password expires the user will be prompted to update the password correct?
Hey Carl,
I have followed all the steps and it already recognize the credentials but I get this error (”
The session has expired. Try logging in again”) at login. Might you help me? Thank’s.
That usually means persistence is not configured corrected on the StoreFront load balancer.
Check StoreFront Server, Event Viewer > Applications and Services > Citrix Delivery Services.
Thank’s for reply.
I have put the “loopback” to “false” and solved the above problem.
I only have one storefront server so I guess I do not need a load balancer, right?
I am trying to configure the multidomain with LDAP and it works but the users with the same user name give this failure:
Cannot complete your request.
Did you configure the NetScaler to send the domain name to StoreFront? See https://www.carlstalhood.com/netscaler-gateway-11-1-ldap-authentication/#domains
Yes, I followed the UPN method. I will try with the AAA Groups Method.
Hey Carl, great article as always.
you mention Citrix CTX203873 adding a drop down for domains, I followed the article and it works great for users working with a browser but once I added the rewrite policy I could no longer connect to the gateway vip. Have you tested this procedure and if so did you see the same results? Can the dropdown be in place and users still use the native receiver? thanks for the info!!
Hi Carl, we have two domains domain1 and domain2. I have followed the below steps for Multi domain authentication. Everything works fine for most of the users in both the domains . But for 2 users they get error “401 – Unauthorized: Access is denied due to invalid credentials”. When I created a duplicate user in same AD OU of the user account which have problem, the duplicate user is able to logon and see the published apps. Any suggestions on this problem from your side.
Multiple domain Authentication method :
1)Separate Auth policy for each domain with Server logon Attribiute as saMAccountname and SSO Name Attribute field as userPrincipalName
2)One session policy with no value in Single Sign on Domain
For two users, I could find following.
1. An AD user object in first domain and a Contact object in second domain.
Regards,
Nebeel
Is StoreFront configured to restrict the allowed domains? Is the UPN suffix configured correctly for those two users?
If the 401 is coming from NetScaler, what do you see in cat /tmp/aaad.debug.
Also check StoreFront > Event Viewer > Applications and Services > Citrix Delivery Services.
Hi Carl,
Thanks for the reply, we use Web interface 5.4 and there are no event that is related to this problem found in web interface servers.Next action I have is to check aaad.debug when user try for authentication. Any other checks you would advice me along with aaad.debug.
Web Interface events are logged to Event Viewer > Windows Logs > Application Log.
401 from WI usually means an issue with Callback.
The problem is only for two users. Other 400 + users can logon and access published resources without error. I have checked the call back fqdn by accessing in Internet explorer and do not find any cert error.
Then you might have to call Support so they can determine where the failure is occurring.
Do the users belong to a large number of groups?
Do the users belong to a large number of groups?
Ans: Nope. with a duplicate user with same number of group membership can login without error
Hi, great article, so even if the domains are trusted, Netscaler needs an individual binding to both of them to authenticate the user? Can’t the Netscaler send the authentication from the secondary (trusted) domain to the primary domain and the primary domain will do the authentication via the trust and send back success/no success in return?
You can point to a Global Catalog and rely on LDAP referrals. https://support.citrix.com/article/CTX200506
We are using the NetScaler Gateway for both ICA and SSLVPN for remote access. Does the SSLVPN client currently support users to reset or change their LDAP password? Similar to what CheckPoint SDL (Secure Domain Login) can do?
I don’t think I’ve tried it yet.
Ok. Thanks Carl. Do you know if it’s on the roadmap? Or how we may be able to test it? Appreciate the response.
Gateway 11.1 Client prompts users for credentials and supports password expiration. Or are you asking about integration with Windows logon?
Ok. So these are Windows 10 devices that will be connecting through the NS sslvpn. Do you know what the level of integration is with using microsoft’s credential provider and the netscaler? We want to test to see if there is a self-service option on the Netscaler to change expired AD passwords. The issue we are having is since the AD password is being cached when the user logs into their machine, however when they attempt to authenticate against the Netscaler it will fail if there AD password has expired.
Thanks again Carl
Carl,
I’m having difficulty allowing users to logon with UPN or Email address only from the mobile receiver. Web access works fine. I set the logon name attribute to “userPrincipalName”, and SSO Attribute to “userPrincipalName”, and it still doesn’t work. I’ve tried “mail” as well. I disabled “Single Sign On Domain” in the Published applications tab of the receiver session profile, to no avail. The only way I can get receiver to work is if I do a manual setup and choose Access Gateway or use a web page logon.
Do you have the steps to allow a mobile receiver to logon with email address or UPN?
Thank you.
Are you referring to discovery instead of authentication? Discovery points to FQDN. If Email address for discovery, then there are additional requirements.
No not discovery, for authentication. If I add the account by URL, it detects it’s a NetScaler gateway, but when I put in the user’s email address, it requires a domain. So I type in user@domain.com, and put domain.com in the domain field. It then converts the account into a Web Site and makes you log in a 3rd time, and then subsequent logons are in the Web Page.
Android? Android seems to insist on web-based auth.
Same problem on iOS or Windows?
We are receiving Valid credentials are not provided after password change. The server is reachable and port 389 is open and the server is a valid LDAP server.
Any help would be greatly appreciated.
Is it encrypted? TLS or SSL?
Sorry for the late reply and we are using TLS. We discovered what the issue was. The account had two special characters : and ). One or both them was causing the issue. We updated the password to not use the special characters.
Thanks
Sunshine
Carl,
I am looking to setup a contractor portal page. Currently we have 2 netscalers in HA and 2 SF in HA. I would like for our contractors to have a different storefront page. I do not see in your documentation. Am I missing another post you have created elsewhere?
Thanks in advance.
What do you mean by “different storefront page”?
Is this NetScaler Gateway? You want each tenant to have a different logon page? Simply create multiple Gateway vServers, each with different VIP/DNS.
For StoreFront, You can create different Stores on the same URL, each store has different authentication. However, Receiver might show all stores if you don’t hide them. And if you hide them, then you need to provide custom instructions to the users to add a hidden store. Or you can build a different StoreFront group.
This is a NetScaler gateway. Basically I want our contractors to have a different website they visit to gain access to our Citrix Environment. They will authenticate the same way with a AD user using LDAP just their SF page will be different.
Logon page comes from NetScaler. Create a separate Gateway vServer on a different VIP (and DNS name). Bind a different Portal Theme if you want.
You can create a separate StoreFront Store and point Gateway to that Store. Or create a separate StoreFront Server Group and point Gateway to the new group.
Hello Carl, please, I hope you could help me with a problem which is driving me crazy.
I followed your procedure to extract an AD group in order to apply some policies to a specific group. I see the NetScaler is retrieving the group name but it seems that the rewrite policy does not receive such name. I want the rewrite policy to redirect an unallowed user to an error page. How could I troubleshoot this?
The NS is retrieving the group name as follows:
Sun Sep 11 02:33:29 2016
/usr/home/build/rs_110_65_23_RTM/usr.src/netscaler/aaad/ldap_drv.c[370]: receive_ldap_user_search_event Binding user… 1 entries
Sun Sep 11 02:33:29 2016
/usr/home/build/rs_110_65_23_RTM/usr.src/netscaler/aaad/ldap_drv.c[395]: receive_ldap_user_search_event User DN= <>
Sun Sep 11 02:33:29 2016
/usr/home/build/rs_110_65_23_RTM/usr.src/netscaler/aaad/ldap_drv.c[487]: receive_ldap_user_search_event built group string for gsmith of:AllowedGroup
The Rewrite expression is witten as:
HTTP.REQ.USER.IS_MEMBER_OF(“AllowedGroup”)
I have not succeeded with this deployment. Please, any comment is welcome. Thanks.
Carl, Either I am completely stupid or simply my Netscaler version doesn’t have it but I do not have the check box item Allow Password Change in the Other Setting area of LDAP Server Authentication.
My Netscaler VPX is build 11.0.63.16nc Oct. 2015.
VPX License is Standard model iD 10.
If Security Type = PLAINTEXT, then the option disappears. You need TLS or SSL.
Thanks for the reply, didn’t think about that, however I have Netscaler MPX 8200 with Standard license. Load Balancing is (green) checked in the license page.
Thanks for your explanation. Authentication now works. From NS11.0: Build 64.34.nc I have problems about AAAGroups and nested AD Group. It seems that nested AD gruop does not bind with Intranet Applications that I configured in the past (with NS10.5 no problem). Do you know anything about it?
Did you configure the LDAP policy to extract nested groups? If you run cat /tmp/aaad.debug do you see the nested groups being returned?
Sorry for the later! I made several tests to answer 😉
I configure the LDAP policy to extract nested groups and if I run cat /tmp/aaad.debug I see nested group!
But launching VPN from remote I receive the following message “1013:Failed to parse configuration. Check the connection log for more information”.
In the connection log I see the following message “Split tunneling is enabled and an intranet application is not configured”.
In Netscaler I just configured intranet applications but:
– if intranet application is bound to primary group, I receive “1013” error
– if intranet application is bound to nested group VPN works
But necessary i have to use primary group to configure intranet applications.
Could you help me?
Thanks a lot and sorry for my bad english 😉
By “Primary Group”, do you mean the user’s Primary Group in AD, which defaults to Domain Users? NetScaler LDAP does not extract user Primary Groups. You can go to AD and change the user’s Primary Group and then NetScaler can see the old group. I think this is an LDAP limitation.
Sorry, I did not explain it well. I will try again to explain.
First case
UserA belong to GlobalGroupA; GlobalGroupA belong to LocalGroupVPN . Intranet applications is bound with LocalGroupVPN. UserA launches Gateway Plugin to use VPN from remote but he receives “1013” error.
Second case
UserA belong to LocalGroupVPN . Intranet applications is bound with LocalGroupVPN. UserA launches Gateway Plugin to use VPN from remote and it works.
I need to use “First case” but I receive the error.
Could you offer any advice in this situation?
Thanks!
I just tried it on 11.0 build 64 and it works.
I created a Domain Global group named CorpVPN and added my test account to it.
I created a Domain Local group named VPN and added CorpVPN to it.
On NetScaler, I configured Nested Group Extraction and enabled Split Tunnel.
I added AAA Groups for both VPN and CorpVPN.
I created an Intranet Application and bound it to VPN group only. Nothing is bound to CorpVPN. And it works.
I can see 1013 error if user is in neither group.
Are your groups in different domains?
No, groups are in the same domain. Very strange. Is there a way to view logs about Intranet Applications? Thanks a lot!
Our password has a # as well and it’s working right but the dashboard is failing. Other vServer without special characters are passing LOL.
Hello Carl, today I found out, that the UPN Method in our Multi Domain setup isn’t working completely. If users logon over the NetScaler Gateway Website, everything works fine. If they try to add our Store to their native Receiver, it could not be added. Configuring unique Sessions Policies for each domain with AAA Groups works perfect for us. Thanks for sharing your your knowledge!
What are the risks of changing your domain controller from a non-SSL to a SSL certificate that is required to set up LDAPS?
Windows 2003 required a reboot. Windows 2008 R2 should work immediately after installing the cert. I’m not aware of any risks.
Thanks Carl. I wasn’t sure if there was any implications of going from LDAP to LDAPS on our primary domain controller. Appreciate your help!
I am getting a message in the authentication dashboard on both of my ldap lb’d vservers that they are down Invalid Admin Bind Credentials. They worked in 10.5 before my upgrade and all monitors and vservers check out. Getting a message when logging in in aaad.debug that main timer 1 is firing and nothing else. No invalid credentials in the debug messages. No clue.
If you edit the LDAP server and re-enter the bind password, does it work?
No – still having bind issues
Have you tried ldp.exe and Simple Bind using the same bind credentials you entered in NetScaler?
Carl –
I know this is from a while ago but wanted to update – the gist of it is – if you are using a custom theme and cookies to login from a dropdown box – don’t forget to change the expression in the session policy…
I have the same problem. Looks like the bug in the authentication dashboard in version 11, the lb’s are actually working.
We had the >> down. invalid admin bind credentials < Dashboard check was running. And the Status was Down. After some hours of troubleshooting, we change the Bind User credentials. And Tada, everything was working fine. The old password (we used for years with build 10.5) contained some special characters (“#” and “-“), seems to me that the netscaler is unable to use these special characters and every time the Dashboard check is running, a wrong password is used for the ldap bind user which results in lock out of the user.
Hope this helps!
Thank you for pointing this out , our password also contains “#” character.
Load Balancing is not licensed with the Gateway version from what I understand. How is what you have detailed above achieved ?
There are four editions of NetScaler licenses: NetScaler Gateway (Only) Edition, Standard Edition, Enterprise Edition, and Platinum Edition. Each Edition includes everything in the lower editions. Standard Edition is the minimum for load balancing. If you purchased the NetScaler Gateway VPX then you are only licensed for NetScaler Gateway. You’d have to upgrade to VPX 10 Standard Edition or VPX 200 Standard Edition to get load balancing.