Navigation
- RADIUS Overview
- Two-factor Policies Summary
- Create Two-factor Policies
- Bind Two-factor Policies to Gateway
RADIUS Overview
For two-factor authentication using Azure Multi-factor Authentication, see Jason Samuel How to deploy Microsoft Azure MFA & AD Connect with Citrix NetScaler Gateway
Citrix CTX125364 How to Configure Dual Authentication on NetScaler Gateway Enterprise Edition for Use with iPhone and iPad.
Some two-factor products (e.g. SMS Passcode) require you to hide the 2nd password field. Receiver 4.4 and newer supports hiding the 2nd field if you configure a Meta tag in index.html. See CTX205907 Dual-Password Field Shows in First Authentication When Connecting to NetScaler Gateway from Windows Receiver for instructions. 💡
Two-factor authentication to NetScaler Gateway requires the RADIUS protocol to be enabled on the two-factor authentication product.
On your RADIUS servers you’ll need to add the NetScaler appliances as RADIUS Clients. When NetScaler uses a local (same appliance) load balanced Virtual Server for RADIUS authentication, the traffic is sourced from the NetScaler SNIP (Subnet IP). When NetScaler uses a direct connection to a RADIUS Server without going through a load balancing Virtual Server, or uses a remote (different appliance) Load Balancing Virtual Server, the traffic is sourced from the NetScaler NSIP (NetScaler IP). Use the correct IP(s) when adding the appliances as RADIUS Clients. And adjust firewall rules accordingly.
For High Availability pairs, if you locally load balance RADIUS, then you only need to add the SNIP as a RADIUS Client since the SNIP floats between the two appliances. However, if you are not locally load balancing RADIUS then you’ll need to add the NSIP of both appliances as RADIUS Clients. Use the same RADIUS Secret for both appliances.
Two-factor Policies Summary
When configuring the NetScaler Gateway Virtual Server, you can specify both a Primary authentication policy and a Secondary authentication policy. Users are required to successfully authenticate against both before being authorized for NetScaler Gateway.
For browser-based StoreFront, you need two authentication policies:
- Primary = LDAPS authentication policy pointing to Active Directory Domain Controllers.
- Secondary = RADIUS authentication policy pointing to RSA servers with RADIUS enabled.
For Receiver Self-service (native Receiver on mobile, Windows, and Mac), the authentication policies are swapped:
- Primary = RADIUS authentication policy pointing to RSA servers with RADIUS enabled.
- Secondary = LDAPS authentication policy pointing to Active Directory Domain Controllers.
If you need to support two-factor authentication from both web browsers and Receiver Self-Service, then you’ll need at least four authentication policies as shown below.
Primary:
- Priority 90 = RADIUS policy. Expression = REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver
- Priority 100 = LDAP policy. Expression = REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver
Secondary:
- Priority 90 = LDAP policy. Expression = REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver
- Priority 100 = RADIUS policy. Expression = REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver
Create Two-factor Policies
Do the following to create the Two-factor policies:
- Create an LDAP server.
- For RADIUS, on the left, expand Authentication, and click Dashboard.
- On the right, click Add.
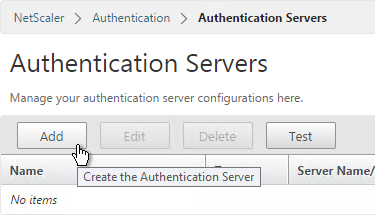
- Change Choose Server Type to RADIUS.
- Give the server a name.
- Specify the IP address of the RADIUS load balancing Virtual Server.
- Enter the secret key specified when you added the NetScalers as RADIUS clients on the RADIUS server. Click Create.
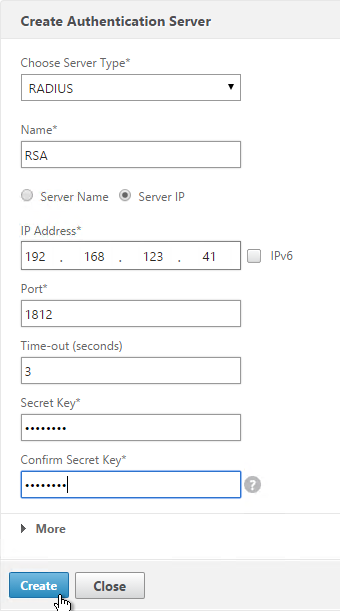
add authentication radiusAction RSA -serverIP 10.2.2.210 -serverPort 1812 -radKey Passw0rd
- Since you can’t create authentication policies from the authentication dashboard, go to NetScaler Gateway > Policies > Authentication > RADIUS.
- On the right, in the Policies tab, click Add.
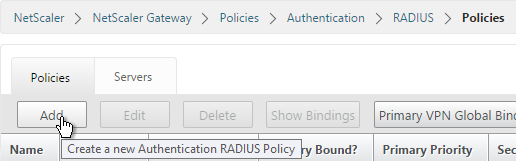
- Name it RSA-SelfService or similar.
- Select the RADIUS server created earlier.
- Enter an expression. You will need two policies with different expressions. The expression for Receiver Self-Service is HTTP.HEADER User-Agent CONTAINS CitrixReceiver.
- Click Create.
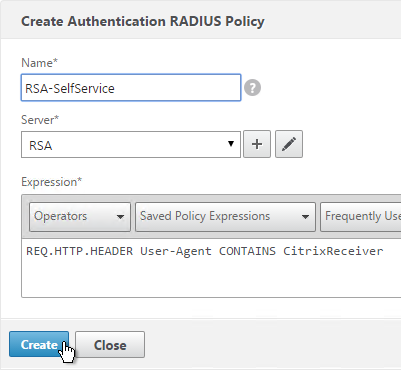
add authentication radiusPolicy RSA-Web "REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver" RSA add authentication radiusPolicy RSA-SelfService "REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver" RSA add authentication ldapPolicy Corp-Gateway-Web "REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver" Corp-Gateway add authentication ldapPolicy Corp-Gateway-SelfService "REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver" Corp-Gateway
- Create another policy to match the ones shown below. Both RADIUS policies are configured with the same RADIUS server. The only difference between them is the expression (CONTAINS vs NOTCONTAINS):
Name Expression Server RSA-SelfService REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver RSA RSA-Web REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver RSA 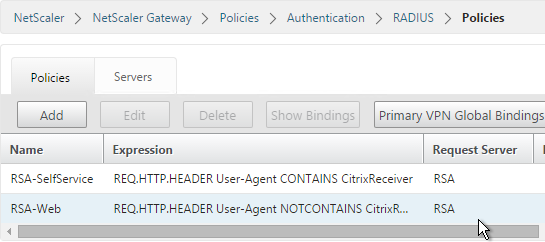
- Go to the NetScaler Gateway\Policies\Authentication\LDAP node.
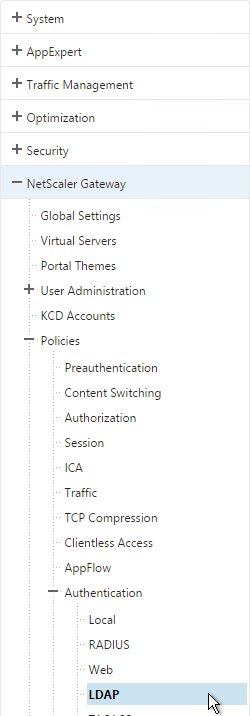
- On the Policies tab, create two policies with the expressions shown below. Both LDAP policies are configured with the same LDAP server. The only difference between them is the expression (CONTAINS vs NOTCONTAINS).
Name Expression Server LDAP-Corp-SelfService REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver LDAP-Corp LDAP-Corp-Web REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver LDAP-Corp 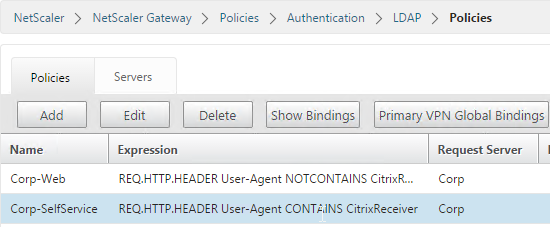
Bind Two-factor Policies to Gateway
- When you create the NetScaler Gateway Virtual Server, bind the policies as shown in the following table. Priority doesn’t matter because they are mutually exclusive.
Policy Name Type Bind Point LDAP-Corp-Web LDAP Primary RSA-SelfService RADIUS Primary LDAP-Corp-SelfService LDAP Secondary RSA-Web RADIUS Secondary 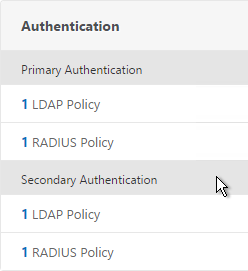
bind vpn vserver gateway.corp.com -policy Corp-Gateway-Web -priority 100 bind vpn vserver gateway.corp.com -policy RSA-SelfService -priority 110 bind vpn vserver gateway.corp.com -policy RSA-Web -priority 100 -secondary bind vpn vserver gateway.corp.com -policy Corp-Gateway-SelfService -priority 110 -secondary
- The session policy/profile for Receiver Self-Service needs to be adjusted to indicate which authentication field contains the Active Directory password. In the Session Profile, on the Client Experience tab is Credential Index. This needs to be changed to SECONDARY. Leave the session policy for Web Browsers set to Primary.
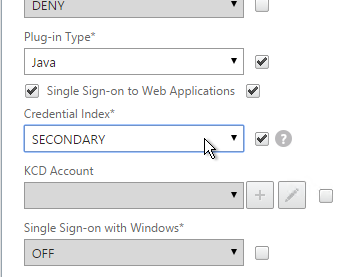
set vpn sessionAction "Receiver Self-Service" -ssoCredential SECONDARY
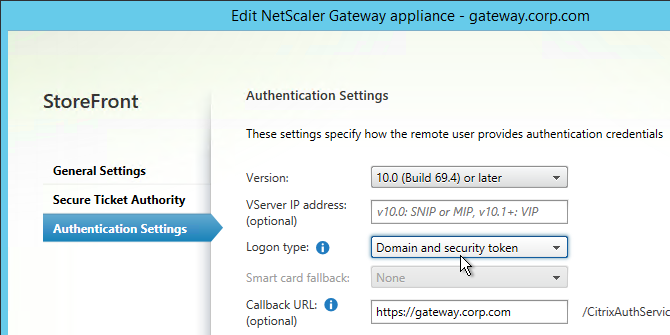
- On the StoreFront server, when creating the NetScaler Gateway object, change the Logon type to Domain and security token.
Hi Carl,
We has now configure Netscaler GW with MS MFA, which works really well.
Except with the Citrix Receiver, at the moment i face an issue, that i setup the account on the receiver, im able to login the first time with the mobile approvement, but if i want to logon a 2. time the receiver shows me a Token field which i dont have due the MFA Auth. (Mobile approvement)
User
Password
Token
did you or some one have any idea/help?
Is Domain + Token configured on the StoreFront Console > Manage NetScaler Gateways > Edit > Authentication? That’s what controls whether two fields show up or not.
Hello Carl, I’m trying implement two-factor using Imprivata. I just want to set up external two factor for the web client for now and not mobile devices. I created a secondary authentication method for Imprivata (RADIUS) and set the storefront to domain + token, but I keep getting two password fields. I tried entering the token into the secondary field, but that failed. Imprivata is also supposed to inject some instructions into the gateway, but I don’t see how that happens without some sort of redirect or customization. Any help would be greatly appreciated. Imprivata doesn’t seem to know how to deploy it and the documentation they provided is incomplete at best. Thanks!
Most two-factor vendors have instructions for NetScaler Gateway.
If all you want is to hide the second password field, Duo has instructions at https://duo.com/docs/citrix_netscaler-alt#modify-the-sign-in-page
Hello Steve. Were you ever able to get this working. I’ve had major headaches with this setup. According to Imprivata you don’t need to do the Primary/Secondary authentication, just the primary. I’ve gotten that piece to work. The problem I’m having is that any generic user can log into that virtual server as well. Imprivata doesn’t seem to be doing any group extraction. Its just passing on a success for the generic user and the Netscaler is allowing the user to log in. As you’ve said, Imprivata is no help. All I get from them is the default “It just always works. It must be something with your setup.” This company is driving me crazy!!! Any help you could provide would be great. Thanks. -Ken
HI Carl,
I have implemented Azure MFA server and all is working as expected, except for when any Apple MAC users connect via Citrix Receiver. It still asks for 2FA token. I would expect it just to ask for Username/pwd and then MFA would send SMS. However it never gets to the next screen. Any suggestions?
I usually do LDAP to MFA instead of RADIUS.
Otherwise, you’ll probably have to figure out how to hide the second password field.
Hi Carl do you know how i can configure two factor Azure MFA for Citrix Receiver to work. I have it working in web browser but when entering URL address in receiver it says it cannot be added
Can you add the account if two-factor is not enabled? Can’t add account usually means something wrong with the internal beacon.
I can add it fine with no two-factor.
The Gateway object in StoreFront console is configured with Domain + Token?
Did you swap the credentials in NetScaler Gateway?
Hey Carl,
I have this same issue that jig stated above, after MFA config , account is not getting added in receiver.
in above reply, are you saying that we have to add some configuration about our newly added primary authentication On Storefront..
We have added both the authentications as primary with a difference in priority one is 99 other is 100.
Please elaborate what exactly is required to be done, i hv gone through the above instructions though!
Thanks
Piyush
https://www.carlstalhood.com/netscaler-gateway-11-radius-authentication/#2fapoliciessummary shows a summary of the policies across the Primary and Secondary factors.
Hi, Carl.
I have a question, You can use 2 different radius solutions in the same service, for example, I can use RSA and MFA in the same AG service
Both at the same time for the same user? Or different methods for different users? If the latter, then you’ll probably need nFactor authentication. https://www.carlstalhood.com/nfactor-authentication-for-netscaler-gateway-11-1/
Hello,
Great article. I am trying to setup a loadbalance virtual service for the web tiers for selfservice.
I have 2 webtiers in my dmz and a AM in the lan. Firewall has a wan ip pointing to a vip in the dmz that is looking at the 2 webtiers. When a user accesses the wan ip or dns name externally I get page cannot be displayed. Its’ like the virtual server does not pass through the traffic.
Please can you assist with a an Idiots guide of setting up selfservice loadbalance on my vpx.
Is selfservice something Citrix specific? Or just a generic website?
It’s usually caused by incorrect routing configuration, especially if you have multiple interfaces. See https://www.carlstalhood.com/netscaler-11-system-configuration/#twoarm
Hello Carl, I have a question. Is it possible to have 2FA only based on group? For example, have users in AppAdmin group be prompted for 2FA while default users just get ID/PWD? Thank you.
Of course it would need the username before it knows what group you’re in. NFactor can do this.
Hello Carl,
I would like to setup a Two Factor Authentication (Citrix User Local password + One time Password) for Citrix NetScalar Virtual Server console with the help of Radius authentication. I just wanna test local password with OTP for now but not AD password in primary authentication. Can you please list me how to define the policies in Citrix NetScalar for implementing this setup ? Appreciate your help. Cheers !
Hi Carl,
I have a question, i think it’s simple for you…
I want to use two factor authentication…it works, but only if i use username, ad password and token.
The token is combined like this: ad password+onetimepassword.
So, what i want is only to use username and token (ad password+onetimepassword). If a set it up on the netscaler to use only the radius server as primary then i could logon from the Netscaler, which bring me to the storefront, but this one has a problem with the credentials….could you give me tip, what i must set it up, that it works?
thank you and regards
StoreFront, Controller, and VDA will need your password at some point.
I’m not sure if Federated Authentication Service would work for this.
Hi Carl,
thank you for your help regarding the pwcount cookie!
The authentication works now fine with SMS-Passcode.
However, I need to set the flags Secure and HttpOnly to this cookie. I did that within the rewrite action that sets pwcount=+1 and that pwcount cookie works fine.
Unfortunately there is a second pwcount cookie and this one is set with the value 2 and only the Secure flag.
If I understand it right it shouldn’t be needed to be read at the client side but I’m not absolutely sure about that.
But if I’m right, is there a way to force that cookie to also set the HttpOnly flag?
There is definitely javascript that reads the cookie. Check out login.js.
Therefore that script (login.js) is executed then along some other java scripts on the client side, right?
I wasn’t sure about that. Thank you for pointing that out.
And at least one other java script (js/tmindex_view.js) seems to read the second pwcount cookie and that is why it cannot have the HttpOnly flag set, because with that flag script access to the cookie is prevented.
I’m just pointing that out because it might be possible that someone else stumbles over this.
I’m just saying PCI-DSS Compliance…:)
It would be nice if you could confirm this explanation.
But anyway, thank you for helping me out a second time!
@ALL:
Something different about two factor authentication with SMS-Passcode:
As I understand it http://support.citrix.com/article/CTX205907 corrects the workaround 1 of http://support.citrix.com/article/CTX203775 a bit. Have a look on the putty screenshot on CTX205907 compared to point 3 of workaround 1.
However, it is not told there that the modified index.html gets overwritten with the the original index.html on every reboot of the Netscaler, therefore making workaround 1 pretty useless.
I suggest to have a closer look at workaround 2 or maybe workaround 3 on CTX203775.
I have finally implemented workaround 2 which seems to be the most elegant solution, making also adding the rewrite action and policy for the first pwcount cookie (pwcount=+1) obsolete.
Workaround 3 is the better solution compared to workaround 1, because the rewrite policy edits the index.html on the fly when a client requests it. That makes it unnecessary to edit the original index.html and is therefore a solution that survives a reboot of the Netscaler.
@Carl:
Maybe you want to point that out a bit better on the RADIUS Overview section of your blog post.
An addition to the two factor authentication with SMS-Passcode:
I did just another security scan after implementing workaround 2 of CTX203775 including unbinding the pwcount cookie rewrite policy and had a very nice effect:
The second pwcount cookie is set now to value 0 and also flagged both as Secure and HttpOnly. Maybe that is done by my rewrite action and policy that I have configured as explained in http://support.citrix.com/article/CTX138055.
But the point is that the Netscaler seems not to need to read that cookie with that configuration and therefore allows that it is flagged as HttpOnly, too.
This makes the workaround 2 the best solution when it comes to fulfill PCI-DSS-Compliance or high security needs.
Hi Carl,
I have a stupid issue with Netscaler 11.1 Build 48.10.
I did some tests with two factor authentication and removed the secondary authentication settings afterwards from my virtual server. But the logon page still shows the Password 2 Field.
I removed and recreated the virtual server (without secondary authentication settings) but the logon page still shows the Password 2 field.
At last I created a new virtual server with another name and ip address also without secondary authentication but the Password 2 field pops up on that logon page, too.
Do you have any idea how I can remove it?
Also that Password 2 field shouldn’t pop up by default on a new virtual server. Any ideas why this happens and how to get rid of it?
A cookie controls it. Same issue on different browsers/machines? Are you doing a rewrite to always create the pwcount cookie?
Yes, it happens on other machines, too. And no, I’m not doing a rewrite to always create the pwcount cookie.
Do I need to do that with single authentication, too?
How is it done?
Use Fiddler or your browser development tools to see if you’re getting the cookie.
I think it has to do with rewriting the pwcount cookie. I have found a solution on another site that explains how to do the rewrite when a two factor authentication is implemented.
See: https://discussions.citrix.com/topic/369016-netscaler-11-two-factor-authentication/
However I’m not sure how the rewrite policy expression should be defined in the case of a single authentication. At the moment I have created two rewrite policies, one with the expression “HTTP.REQ.HEADER(“Cookie”).CONTAINS(“pwcount”).NOT” and the other one with the expression “HTTP.REQ.HEADER(“Cookie”).CONTAINS(“pwcount”)” but I’m not so sure if it would make sense to bind both to the virtual server, especially on the long term. I did it for the moment and now the logon page doesn’t show the Password 2 field anymore. But how is it done correctly?
Hello Carl, this solution works for me, thanks for your contribution!
I would just like to ask is it possible to use Radius and LDAP authentication on a single gateway virtual server and have some user login via LDAP and some using their RSAsecureID tokens?
Also is Radius authentication supported for Web Interface on NetScaler as I have tried it and it authenticate successfully on the NetScaler and the RSA server but the Web Interface page does not launch or open?
You can do this in AAA nFactor. Hopefully they add nFactor to Gateway too.
Web Interface requires some sort of AD authentication. If Gateway doesn’t supply it then Web Interface should prompt you.
Great article, Carl! Thanks for making this available. I was about to pull my hair out until I found this with the info on reversed priorities for Receiver.
Hi Carl,
We have our Netscalers/Storefront and XA7.6 servers in a private visualized environment and need a MFA solution. Will Azure MFA work in this scenario with our current setup or do we need to have some sort of AD presence in Azure? Hope that makes sense.
Thanks in advance.
Azure MFA will work fine. There’s an installable component that will connect to your local AD. See http://www.jasonsamuel.com/2015/09/18/how-to-deploy-microsoft-azure-mfa-ad-connect-with-citrix-netscaler-gateway/ for details
now my receiver works but web receiver sais: cannot complete your request
what is that?
Check Event Viewer on your StoreFront Server. Event Viewer > Applications and Services > Citrix Delivery Services.
Soon as I posted my issue, I realized the error on my part, just needed to select the + next to Authentication to add a Radius policy. Sorry about that and thank you for all these great articles!
Hello Carl, this is create but ran into an issue (this could be on me though, I’m still green at Netscalers). When I go to bind to the Virtual Server, I’m not able to select any of the Radius Policies that were created in the beginning. Only LDAP policies are listed. Did I possibly miss a step?