Navigation
- Monitor to verify that StoreFront is UP
- Server Objects
- Service Group
- Virtual Server
- SSL Redirect
- StoreFront Base URL
- Subscriptions/Favorites Replication Load Balancing
Monitor
Note: This is a Perl monitor, which uses the NSIP as the source IP. You can use RNAT to override this as described in CTX217712 How to Force scriptable monitor to use SNIP in Netscaler in 10.5.
- On the left, expand Traffic Management, expand Load Balancing, and click Monitors.
- On the right, click Add.
- Name it StoreFront or similar.
- Change the Type drop-down to STORERONT.
- If you will use SSL to communicate with the StoreFront servers, then scroll down, and check the box next to Secure.
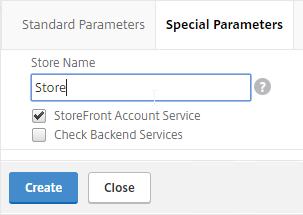
- Scroll up, and switch to the Special Parameters tab.
- In the Store Name field, enter the name of your store (e.g. MyStore) without spaces.
- Click Create.
add lb monitor StoreFront STOREFRONT -scriptName nssf.pl -dispatcherIP 127.0.0.1 -dispatcherPort 3013 -secure YES -storename Store
Servers
- On the left, expand Traffic Management, expand Load Balancing, and click Servers.
- On the right, click Add.
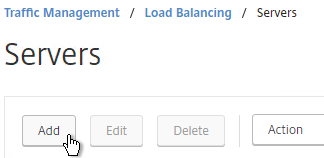
- Enter a descriptive server name, usually it matches the actual server name.
- Enter the IP address of the server.
- Enter comments to describe the server. Click Create.
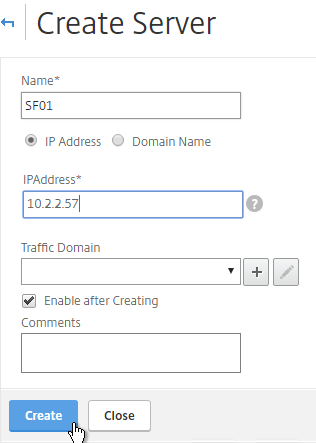
- Continue adding StoreFront servers.
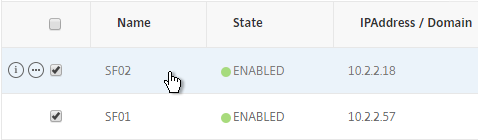
add server SF01 10.2.2.57 add server SF02 10.2.2.58
Service Group
- On the left, expand Traffic Management, expand Load Balancing, and click Service Groups.
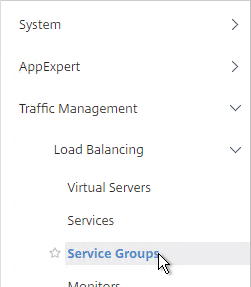
- On the right, click Add.
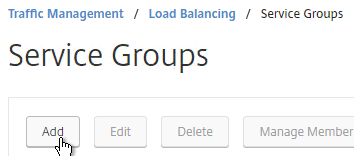
- Give the Service Group a descriptive name (e.g. svcgrp-StoreFront-SSL).
- Change the Protocol to HTTP or SSL. If the protocol is SSL, ensure that the StoreFront Monitor has Secure checked.
- Scroll down and click OK.
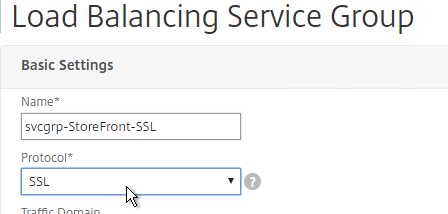
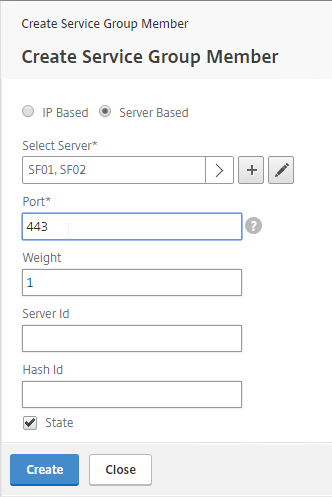
- Click where it says No Service Group Member.

- If you did not create server objects then enter the IP address of a StoreFront Server. If you previously created a server object then change the selection to Server Based and select the server objects.
- Enter 80 or 443 as the port. Then click Create.
- Click OK.

- On the right, under Advanced Settings , click Monitors.
- Click where it says says No Service Group to Monitor Binding.
- Click the arrow next to Click to select.
- Select your StoreFront monitor and click Select.
- Then click Bind.
- To verify that the monitor is working, on the left, in the Service Group Members section, click the Service Group Members line.
- Click the ellipsis next to a member and click Monitor Details.
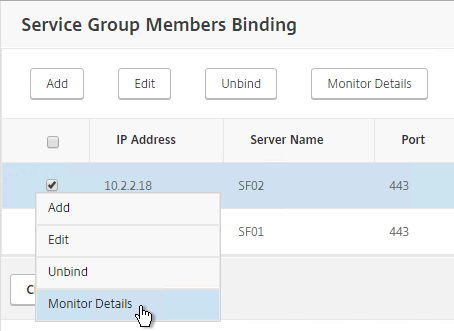
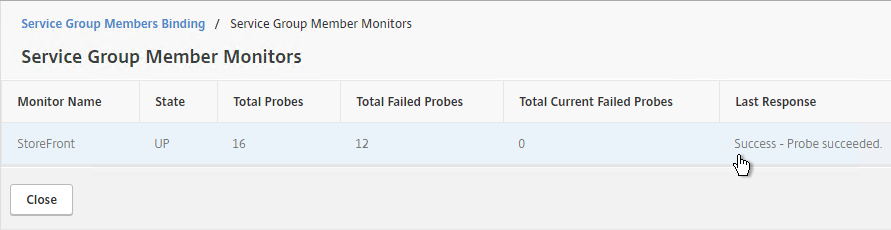
- The Last Response should be Success – Probe succeeded. Click Close twice.
- On the right, under Advanced Settings, click Settings.
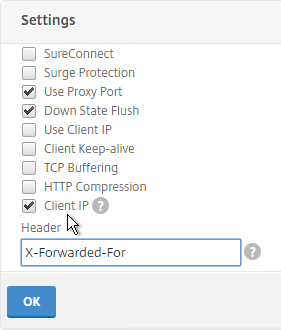
- On the left, in the Settings section, check the box for Client IP and enter X-Forwarded-For as the Header. Then click OK.
- Then click Done.
add serviceGroup svcgrp-StoreFront-SSL SSL -maxClient 0 -maxReq 0 -cip ENABLED X-Forwarded-For bind serviceGroup svcgrp-StoreFront-SSL SF01 443 bind serviceGroup svcgrp-StoreFront-SSL SF02 443 bind serviceGroup svcgrp-StoreFront-SSL -monitorName StoreFront
- If the Service Group is http and you don’t have certificates installed on your StoreFront servers (aka SSL Offload) then you’ll need to enable loopback in StoreFront.
- In StoreFront 3.5 and newer, you enable it in the GUI console.
- In StoreFront 3.0, run the following commands on the StoreFront 3.0 servers as detailed at Citrix Blog Post What’s New in StoreFront 3.0.
& "C:\Program Files\Citrix\Receiver StoreFront\Scripts\ImportModules.ps1" Set-DSLoopback -SiteId 1 -VirtualPath /Citrix/StoreWeb -Loopback OnUsingHttp
Load Balancing Virtual Server
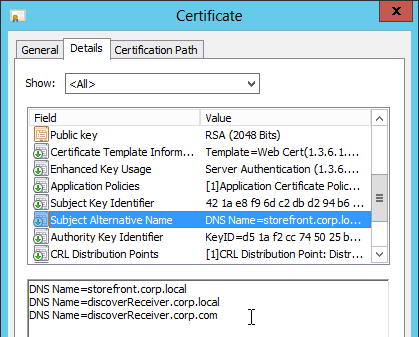
- Create or install a certificate that will be used by the SSL Offload Virtual Server. This certificate must match the DNS name for the load balanced StoreFront servers. For email discovery in Citrix Receiver, the certificate must either be a wildcard (*.corp.local) or have a subject alternative name for discoverReceiver.domain.com (domain.com = email address suffix)
- On the left, under Traffic Management > Load Balancing, click Virtual Servers.
- On the right click Add.
- Name it lbvip-StoreFront-SSL or similar.
- Change the Protocol to SSL.
- Specify a new internal VIP.
- Enter 443 as the Port.
- Click OK.
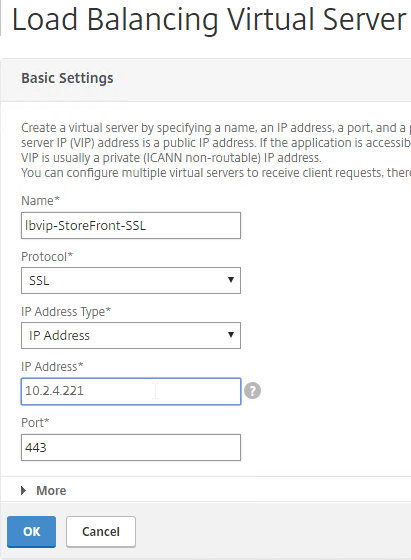
add lb vserver lbvip-StoreFront-SSL SSL 10.2.2.221 443 -persistenceType SOURCEIP -timeout 60
- On the left, in the Services and Service Groups section, click where it says No Load Balancing Virtual Server ServiceGroup Binding.
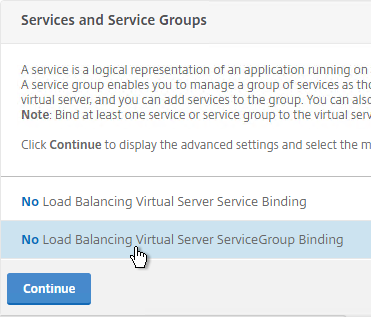
- Click the arrow next to Click to select.
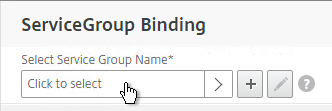
- Select your StoreFront Service Group and click Select.
- Click Bind.
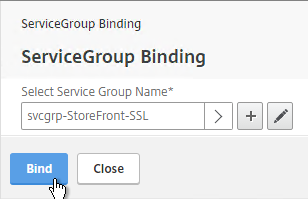
bind lb vserver lbvip-StoreFront-SSL svcgrp-StoreFront-SSL
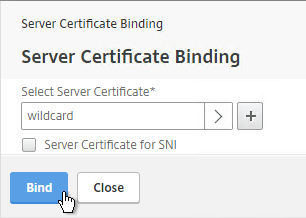
- Click Continue.
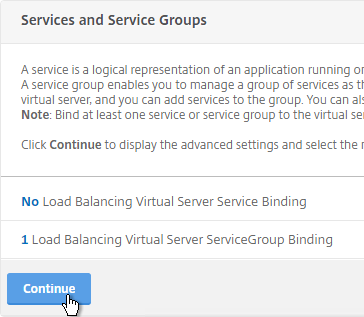
- Click where it says No Server Certificate.
- Click the arrow next to Click to select.
- Select the certificate for this StoreFront Load Balancing Virtual Server and click Select.
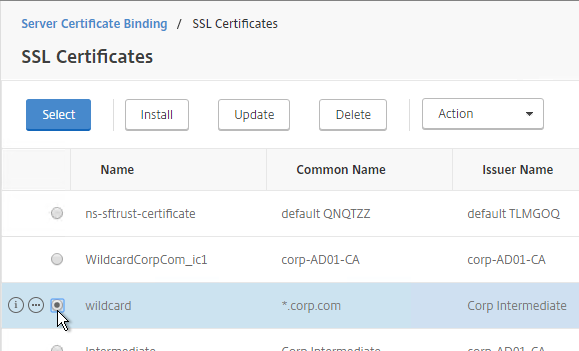
- Click Bind.
bind ssl vserver lbvip-StoreFront-SSL -certkeyName WildCorpCom
- Click Continue.
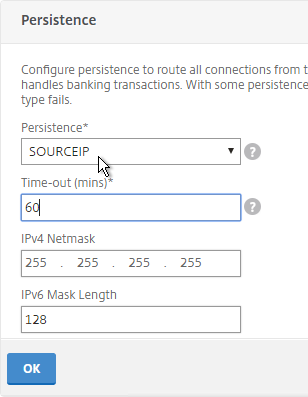
- On the right, in the Advanced Settings column, click Persistence.
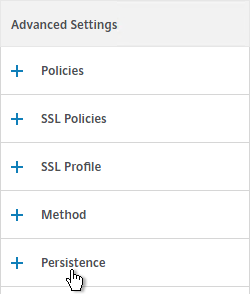
- On the left, in the Persistence section, select SOURCEIP. Do NOT use COOKIEINSERT persistence or Android devices will not function correctly.
- Set the timeout to match the timeout of Receiver for Web.
- The IPv4 Netmask should default to 32 bits.
- Click OK.
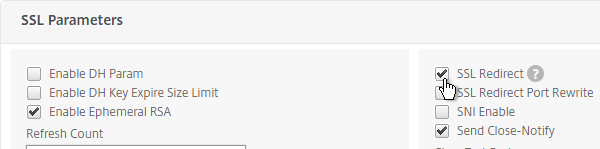
- If the NetScaler communicates with the StoreFront servers using HTTP (aka SSL Offload – 443 on client-side, 80 on server-side), and if you have enabled the Default SSL Profile, then you’ll either need to edit the Default SSL Profile to include the SSL Redirect option, or create a new custom SSL Profile with the SSL Redirect option enabled, and then bind the custom SSL Profile to this vServer.
- If the default SSL Profile is not enabled, then you’ll need to edit the SSL Parameters section on the vServer, and at the top right, check the box next to SSL Redirect. Otherwise the Receiver for Web page will never display.
-
set ssl vserver lbvip-StoreFront-SSL -sslRedirect ENABLED -ssl3 DISABLED
- If you haven’t enabled the Default SSL Profile, then perform other normal SSL configuration including: disable SSLv3, bind a Modern Cipher Group, and enable Strict Transport Security.
bind ssl vserver lbvip-StoreFront-SSL -certkeyName MyCert set ssl vserver lbvip-StoreFront-SSL -ssl3 DISABLED -tls11 ENABLED -tls12 ENABLED unbind ssl vserver lbvip-StoreFront-SSL -cipherName ALL bind ssl vserver lbvip-StoreFront-SSL -cipherName Modern bind ssl vserver lbvip-StoreFront-SSL -eccCurveName ALL bind lb vserver lbvip-StoreFront-SSL -policyName insert_STS_header -priority 100 -gotoPriorityExpression END -type RESPONSE
When connecting to StoreFront through load balancing, if you want to put the server name on the StoreFront webpage so you can identify the server, see Nicolas Ignoto Display server name with Citrix StoreFront 3.

SSL Redirect – SSL Load Balancing vServer Method
Users must enter https:// when navigating to the StoreFront website. To make it easier for the users, enable SSL Redirection.
This procedure details the SSL Load Balancing vServer method of performing an SSL redirect. An alternative is to use the Responder method.
- On the left, under Traffic Management > Load Balancing, click Virtual Servers.
- On the right, find the SSL Virtual Server you’ve already created, click the ellipsis next to it and click Edit.
- In the Basic Settings section, click the pencil icon.
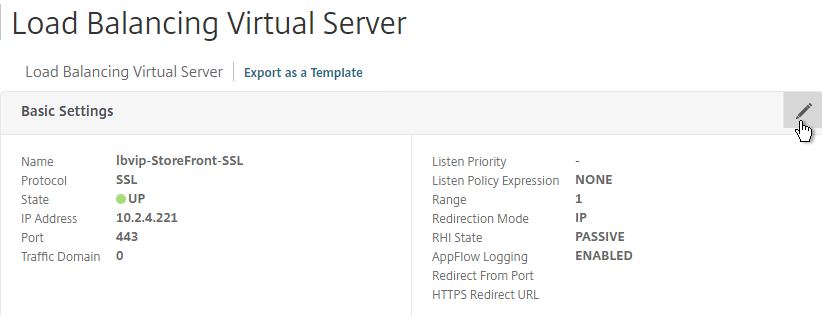
- Click the More link.
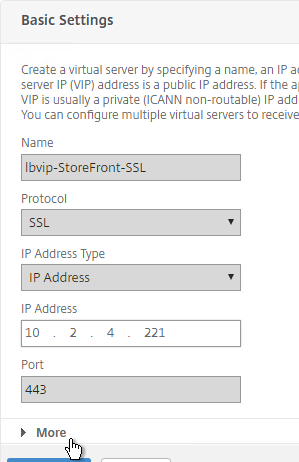
- In the Redirect from Port field, enter 80.
- In the HTTPS Redirect URL field, enter your StoreFront Load Balancing URL (e.g. https://storefront.corp.com).
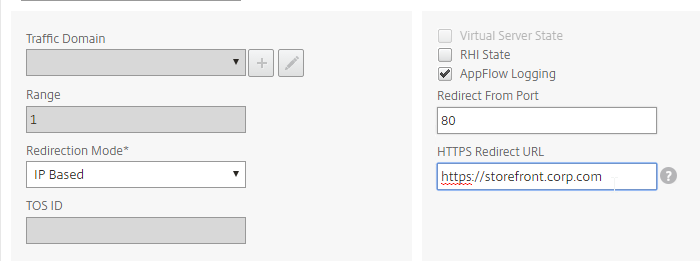
- Scroll down and click Continue twice.
set lb vserver lbvip-StoreFront-SSL -redirectFromPort 80 -httpsRedirectUrl https://storefront.corp.com
- This method does not add any new vServers to the list so it’s not easy to see if this is configured.
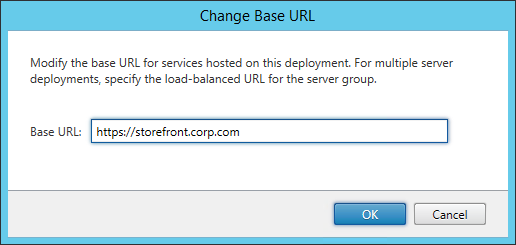
StoreFront Base URL
- Create a DNS Host record that resolves to the new VIP.
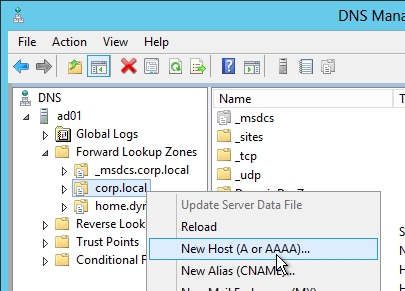
- The DNS name for StoreFront load balancing must be different than the DNS name for NetScaler Gateway. Unless you are following the Single FQDN procedure.
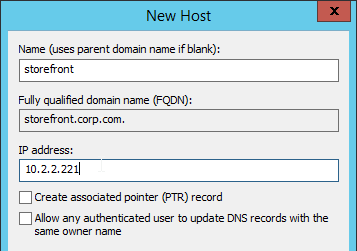
- In the Citrix StoreFront console, right-click Server Group and click Change Base URL.
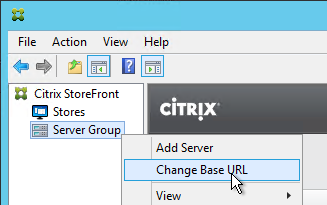
- Enter the new Base URL in https://storefront.corp.com format. This must match the certificate that is installed on the load balancer. Click OK.
Subscription Replication Load Balancing
If you have multiple StoreFront clusters (separate datacenters), you might want to replicate subscriptions between them. StoreFront subscription replication uses TCP port 808. To provide High Availability for this service, load balance TCP port 808 on the StoreFront servers. See Configure subscription synchronization at Citrix Docs for more information.
- On the left, expand Traffic Management, expand Load Balancing, and click Service Groups.
- On the right, click Add.
- Give the Service Group a descriptive name (e.g. svcgrp-StoreFront-SubRepl).
- Change the Protocol to TCP.
- Scroll down and click OK.
- Click where it says No Service Group Member.
- Change the selection to Server Based and select the StoreFront servers.
- Enter 808 as the port. Then click Create.
- Click OK.
- On the right, under Advanced Settings, click Monitors.
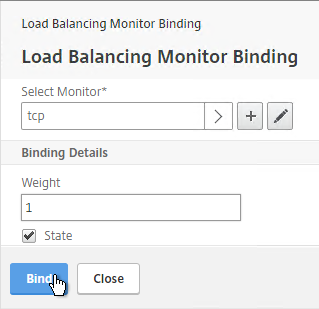
- On the left, in the Monitors section, click where it says No Service Group to Monitor Binding.
- Click the arrow next to Click to select.
- Select the tcp monitor and click Select.
- Then click Bind and click Done.
add serviceGroup svcgrp-StoreFront-FavRepl TCP bind serviceGroup svcgrp-StoreFront-FavRepl SF01 808 bind serviceGroup svcgrp-StoreFront-FavRepl SF02 808
- On the left, under Traffic Management > Load Balancing, click Virtual Servers.
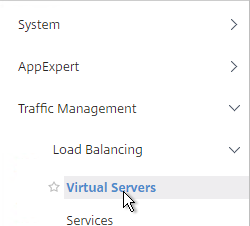
- On the right, click the ellipsis next to the existing StoreFront Load Balancing vServer, and click Add.
- Name it lbvip-StoreFront-SubRepl or similar.
- Change the Protocol to TCP.
- Specify the same VIP that you used for SSL Load Balancing of StoreFront.
- Enter 808 as the Port.
- Click OK.
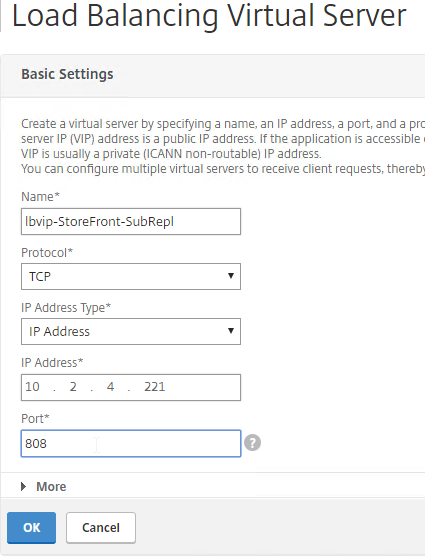
- Click where it says No Load Balancing Virtual Server ServiceGroup Binding.
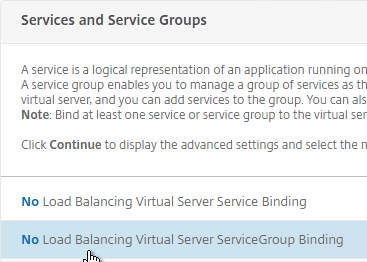
- Click the arrow next to Click to select.
- Select your StoreFront Subscription Replication Service Group and click Select.
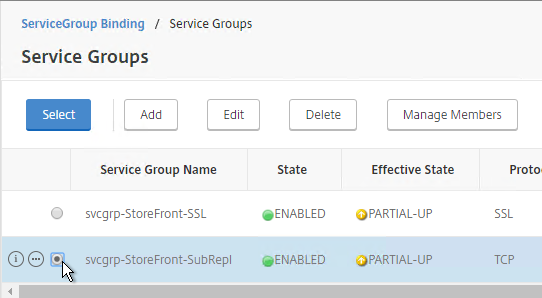
- Click Bind.
- Click Continue.
- Then click Done.
add lb vserver lbvip-StoreFront-FavRepl TCP 10.2.2.201 808 -persistenceType NONE bind lb vserver lbvip-StoreFront-FavRepl svcgrp-SF-FavRepl
Hi Carl, im change the StoreFront IIS certificate for our internal network, but now from external network (where we have public certificate) Workspace stop work 🙁
weird is https access via HTML5 work perfect..
need i put the IIS StoreFront certificate also on NetScaler?
It depends on what users connect to. If users connect to the Load Balancing VIP, then that’s where the cert needs to go.
What kind of key? Double-click the cert, go to the Details tab and look at the public key. Is it RSA 2048?
yes it is RSA 2048..
in NetScaler / Traffic Management / Load Balancing / Virtual Servers
have only two server with name httpredirect to port 80
Hi Carl,
I have an old xenapp 6.5 farm with web interface load balanced by the netscaler.
Is it possible to mantain the load balancing mode and add an ica proxy mode as a test to integrate with netscaler mas?
and if it is possible how can i do that?
Regards
You can add a Gateway Virtual Server on a different IP Address and different DNS name.
Thanks,
i’ll give it a try next week.
Hi,
I want to do this scenario:
Loadbalancing 2 SF Servers with 3 Stores on them.
I want to configure policies/actions that the user does not see to URL where he gets on the SF Server.
E.G. a.company.com -> sf_server/citrix/XenAppAWeb, b.company.com -> sf_server/citrix/XenAppBWeb ….
What rules do I have to use? Rewrite plus URL Transformation?
How to configure these rules?
Thanks for any hint!
Do we need to add a tcp profile for internal storefront lb like the default xa/xd profile?
StoreFront traffic tends to be minimal so it probably wouldn’t have any appreciable effect. But you’re welcome to adjust TCP parameters to reduce retransmissions, improve responsiveness, etc.
Hey Carl,
how do you prevent the NS to use her NSIP for Perl-Based Monitors like Storefront?
We have a separate Management-Network witch is accessed via Management-Port.
If we disconnect the Interface, for whatever reason, the Monitors go’s down, and the Service ist not available.
We had to ensure, that the NS uses his Datainterface with the SNIP.
Thanks
See How to Force Scriptable Monitors to Use SNIP https://support.citrix.com/article/CTX217712
Hi Carl,
I was wondering; in the latest Storefront releases, you can host multiple storefront instances in different webroots so that you can assign different storefront base URL’s to each… for lacking a better word… “customer”, making the sites more independant from each other. Using SNI on each webroot, we can now host multiple SSL secured storefront sites with different SSL certificates on one 1 ip per storefront node. Works like a charm.
Enter NetScaler and it’s storefront monitor… That one unfortunately does not understand this, as it does not send along the custom header info as you are now able to do in NetScaler 11.1 with an http-ecv monitor. Does that actually mean that for the services to gain “up status” we need to replace the storefront monitors with http-ecv monitors? or is there a way to get the storefron perl-script to also send the polling with custom headers?
Quick Question
NetScaler Gateway (NSG) and LB VIP to StoreFront to servers. We have 3 environments one running 10.5 Code with a NetScaler GateWay that get LB to Web Interface VIP. This works great.
Started a new VPX Instance
Runnning 11.1 Code
Using NSG
Store Front VIP (New)
In this new environment we see where the Client IP talks to NSG and then we see where Client IP talks to Storefront VIP. We see this when we do traces on the netscaler. When we run a wire shark capture from the client PC at the same time as a netscaler trace we only see traffic to NSG not the Store Front VIP.
Citrix has told me this is an issue and, then they set it up in there lab and see the same behavior said they saw the same thing. not sure wht to believe.
We only see problems with slowness when we reach abt 2000 users
We never turned on source routing the citrx engineer checked and had us reboot.
Are you doing VPN instead of ICA Proxy?
How do u exactly tell
On the Session Poilcy looks like we have ICA Proxy on checked in both environments
What build of 11.1? A GCM cipher fix was added to build 53.
So we are running 11.1.52.13 If this is a issue do you mind explaning theGCM Cipher Fix causes problems with the Client IP talking to NSG VIP and Then Store Front LB VIP. My undrstanding is that the Client talks to NSG VIP and that is it???
Any Citix docs that I can reference would be great also.
Thank you !!!
The bug is GCM performance. http://discussions.citrix.com/topic/383981-user-sessions-random-disconnecting-using-receiver-146012010/page-2#entry1960348
Sorry to keep asking the same question
When we do packet traces on netscaler we
Client talked Netscaler Gateway should we see client talk to Store Front VIP. Or shld the SNIP talk to Store Front VIP???
There are loopback connections inside the appliance so it’s possible you’re seeing those.
StoreFront VIP is on the same appliance as the NetScaler Gateway? Or separate appliance?
The Store Front Vip and the NSG Vip is on the same appliance.
Are you saying that external users are connecting directly to the StoreFront VIP instead of connecting to the Gateway? If Receiver is able to connect to the Internal Beacon, it will connect to the StoreFront Base URL instead of the Gateway URL.
Are you saying that external users are connecting directly to the StoreFront VIP instead of connecting to the Gateway? If Receiver is able to connect to the Internal Beacon, it will connect to the StoreFront Base URL instead of the Gateway URL.
FYI
I am new to Citrix not sure what you mean about the internal beacon and receiver communication
We only have internal Users
Clients PCs use Recevier or web browser. They first connect to NetScaler Gateway based on DNS https://citrix URL = NSG
Then Client goes to Store Front VIP I assume
We were thinking we woudln’t see traffic on Netscaler where the Client would start talking to both the NSG and Store Front VIP. When the client starts to talks to the Store Front VIP the conversations show a lot of errors. The conversations always seems to start with the NSG (Which it should) and then to the Citrix Store VIP.
In StoreFront Console, right-click Stores and click Manage Beacons. Set the internal beacon to a fake address. You might have to remove the Store from the client and add it again so it picks up the new beacon configuration.
Hi Carl, having issue with not able to ping SF lb vip even though NetScaler says its up. Any ideas? The snip is same network as vip.
IP conflict?
Can you ping it from another machine on the same network?
I found issue. The subnet mask of snip was incorrect and also interface bind required vlan tagging. Thanks for your help.
Hi Charl,
I did the load balance configuration for 2 Storefront servers through the Netscaler and it load balance fine with the Default Storefront store URL set in IIS but I created a second store and as soon as I add this url it get a 404 – File or directory not found.It seems anything other than the default store fails through the Load balanced Storefront.
Any ideas would be appreciated.?
Issue Resolved the changes did not propagate through correctly to both NetScalers when secondary store was created.
I am following these steps to configure LB for StoreFront. Since I am totally new to NetScaler, I need to cross check if my actions are correct.
As to configuring the SSL-Certificate for “Virtual Server”, same Certificate as the StoreFront was use. Meaning exported from StoreFront and imported into NetScaler. The Certificate entails all required DNS name for the load balanced StoreFront servers.
Is this procedure appropriate?
Thanks
Works for me. As long as the cert is valid and trusted by the Receiver clients.
In your steps “Service Group” was created while configuring the LB, however in the crashed introduction of Netscaler in “citrix XenDesktop” course, “service” was created instead in the LAB.
What determines when to use one above the other?
Hi Carl, Do you believe that we will have issues and if we leave the sourceip timeout to the default value 2 min. if so what kind of issues could be ?
Regards
Chris
Other than persistence not working after 2 minutes, even though the web session is 20+ minutes?
If leave persistence timeout 2 minutes and web session is 20+ minutes i can reproduce the following scenario that seems to be abnormal and i would like your opinion for the bellow case.
Access Gateway + NS Loadbalance -> group of 2 storefront
1) A User logged on through Access Gateway and the LB redirects the connection to Storefront1. New session created on Storefront1 and the client receives a csrftoken=1xxxxxx
2)After 3mins the user tries to open an application the LB redirects the connection to Storefront2. The user gets the message “your session has expired …please press ok” and user press click to OK button. So a new session is created to Storefront2 and the client receives a new csrftoken=2XXXXX.
3)After 3 mins the user tries to open an other application the LB redirects back to Storefront1 and gets the error “Cannot complete your request” in HTTP level the response from storefront1 is “403 Frorbiden. Access Denied. ” and I realized that the client has sent the csrftoken=2XXXXX which is not the same with session on Storefront1. (See csrftoken on step 1. )
Thanks
I’ve the same problem described! Did you resolve?
Thanks,
Roberto
Hi Roberto,
Receiver for Web (RfWeb) is session-based and requires sticky load balancing to ensure that requests during the http session are all directed to the same server. It is better to use cookie-insert LB persistence unless you have to support native Receiver for Android. If you have to use source ip LB persistence, you have to make sure that timeout is long enough for a typical RfWeb session. The timeout value has to be not less than the http session timeout value.
Thanks.
Hi Carl,
I noticed you have persistence set to SOURCEIP. If most users are accessing Storefront through Gateway, wouldn’t the persistence just see the SNIP for the gateway Netscalers as the source ip and send all traffic through a single Storefront server?
There are issues with Cookie Insert in Android devices. You’re welcome to try Cookie and make sure your Android devices still work.
I am using 443 in front and 80 to connect to storefont. I have enable SSL-rediect in storefront vsever. After logon to netscaler vserver, a error CTX134123 occurs while launch the xendesktop. Any suggestion on that?
Are you intentionally trying to use HTML5 Receiver? If not, in Chrome, click your name on the top right and click Change Receiver. Then click the big blue button to detect Receiver on your machine.
Yes, I am trying to use HTML5 receiver. Is it no way to make it works if intenetionally using HTML5?
Hi Carl,
I’ve setup StoreFront Load Balancing and when loading the site continually loads. It does not ever seem to give an error just spins. Each storefront server is accessible fine through the server FQDN however not when accessing through the LB VIP
the LB VIP is in a DMZ segment however all traffic is open and not seeing any traffic blocked on the firewall when hitting the site from our internal lan
any thoughts?
XD7.11 new install with new Netscaler VPX 11.1
Thanks,
Pete
Are you doing 443 on the front end and 80 on the back end? If so, edit the SSL vServer, go to SSL Parameters, and check the box next to SSL Redirect.
Hi Carl, 443 on front and back with the same cert on nscaler and SF server. Hitting https://SF-FQDN/Citrix/StoreWeb works fine on both SF servers. Service group on 443 with Storefront monitor is up. it must be something to do with the cert on the nscaler … i’ll post what I find
great site … very imformative
pete
Fix ended up being disabling TLSv12 then it worked. It is re-enabled now and it is still working … http://discussions.citrix.com/topic/368520-netscaler-11-and-storefront-30-load-balancing-broken/#entry1890881
Hi Carl,
I have Netscaler vpx 10.5 build 57.7 and I have done the load balancing for SF 2.5 using the storefront monitor. I upgraded my storefront from 2.5 to 3.8 and immediately my service group went down, When checked found that the monitor is not working, I changed the monitor to ping and service group came up. I tried to recreate the monitor and service group for 3.8, but still no luck. Could you please help.
Thank you!!
Regards,
Nivesh Pankaj
Edit the monitor. On the Special Parameters tab, make sure the boxes are unchecked.
Any way to get pass-through authentication for Storefront via the netscaler load balancer?
I have setup Storefront servers 3.6 with an HTTP store and netscaler 11.1 (no gateway) just basic HTTP load balancer. Is there a way to get the Domain pass through authentication working ?
The domain Pass-through works fine when connected to the Storefront servers individually, however when connected via the LB, it fails to perform Pass through.
Regards,
Kedar
FQDN? Is the FQDN added to the IE’s Local Intranet zone?
We used the instructions from this great post to loadbalance across two StoreFront servers.
We also included the ACL and RNAT statements to overcome the Perl monitor script limitation of using the NSIP instead of a SNIP. Everything works as expected, but I was curious if it would fail when removing the ACL and RNAT statements. And it kept working which should not be the case if the NSIP is used as source IP by the perl Monitor script.
In our setup, the Netscaler VPX (NS11.1: Build 48.10.nc) has three logical interfaces:
0/1: Management, VLAN1, contains the NSIP and a management SNIP
1/1: Frontend: VLAN X, contains the client facing VIPs and a SNIP
1/2: Backend: VLAN Y, the StoreFront servers are also in this subnet (no L3 in between). A SNIP is configured
When performing a tcpdump it looks like NAT is still in place. I want to understand this; is it changed in 11.1 that the SNIP is used? If so, the remark on top of the page can be adjusted 🙂
A snip from the tcpdump:
10:20:09.671482 IP NSIP.50488 > STOREFRONT1.80: Flags [S], seq 1083469940, win 65535, options [mss 1460,nop,wscale 3,sackOK,TS val 692992689 ecr 0], length 0
10:20:09.671489 IP SNIP.5835 > STOREFRONT1.80: Flags [S], seq 1083469940, win 65535, options [mss 1460,nop,wscale 3,sackOK,TS val 692992689 ecr 0], length 0
10:20:09.671981 IP STOREFRONT1.80 > SNIP.5835: Flags [S.], seq 3478389325, ack 1083469941, win 8192, options [mss 1460,nop,wscale 8,sackOK,TS val 100439748 ecr 692992689], length 0
10:20:09.671982 IP STOREFRONT1.80 > NSIP.50488: Flags [S.], seq 3478389325, ack 1083469941, win 8192, options [mss 1460,nop,wscale 8,sackOK,TS val 100439748 ecr 692992689], length 0
When performing a netstat from the Shell, it shows connections in TIME_WAIT state between the NSIP and the STOREFRONT1 server. From the shell, the IP addresses of the other interfaces are not present so I think I cannot trust what I see there.
I am working with Netscaler for a few months now and I really want to try to understand its behavior, thanks!
If NSIP does not have a route to the destination, I believe it will try to use a SNIP. However, you’ll want to do a real network trace on the NetScaler to verify that the SNIP was used as the source IP because I’ve seen asymmetric routing when depending on this behavior.
I’ll try to perform a real network trace since asymmetric routing is exactly what might be going on here (but requires different department to help me out ;).
The StoreFront servers are connected directly in the Backend Subnet so no routing is required. However, there is a route via the Backend network gateway for a larger network range; the backend subnet is a small part of that range (route for a /16, and the backend subnet is a /27 within this range)
Regards,
Marco
Hi Carl looking for some direction in troubleshooting storefront lb. Shouldn’t the VIP stop responding if both sf servers are down? If so that isn’t the case for me. Do you know what I could look at to see why Iam still getting responses from the VIP? I even disabled the vserver in netscaler
IP conflict?
Do you maybe have a port 80 vServer that’s still responding?
Hi Carl, I have 2 sites with DMZ NS GWs both in gslb. Each site also have SF servers with same base URL. When I shut down one sites SF server group but keep it’s NS GW running, when i try to access SF internally it fails, and external the NSGW fails. I don’t see failover to the other SF server group at other site. SF isn’t participating in gslb, but I would think because it’s common URL or DNS is the same across it would be able to reach. Am I thinking this wrong?