Navigation
- Change Log
- Citrix Gateway Feature Licensing
- RfWebUI Portal Theme
- DNS SRV Records for Email-based discovery
- Customize Logon Page
- UDP Audio Through Citrix Gateway
- Citrix VPN from Mobile Devices
- StoreFront – Rewrite X-Citrix-Via
- Device Certificates
💡 = Recently Updated
Change Log
- 2023 Dec 19 – added link to NetScaler article Visually change RFWebUI with CSS
- 2023 Oct 20 – added link to NetScaler article Unleashing RfWebUI Potential: JavaScript-Powered Citrix Gateway Login Page Customization
- 2019 Oct 4 – RfWebUI – added link to CTX258331 Customizing the on-premises Citrix Gateway authentication page to look identical to Citrix Cloud logon page
- 2018 Dec 7 – added nFactor EPA to Device Certificates section
- 2018 Dec 5 – renamed NetScaler Gateway to Citrix Gateway
- 2018 Nov 6 – Other Customizations – added link to Manuel Kolloff Adding additional languages to NetScaler RfWebUI Theme
- 2018 Mar 21 – in RfWebUI section, added link to CTP Simon Gottschlag RfWebUI Idle Timeout
- 2018 Mar 21 – in RfWebUI section, added link to CTP Simon Gottschlag Remove “Password 2” from RfWebUI
Citrix Gateway Feature Licensing
Here is a listing of some Citrix Gateway features and the licenses they require:
| Feature | ADC Editions | Universal Licenses? |
|---|---|---|
| StoreFront Load Balancing | Standard/Enterprise/Platinum | |
| Global Server Load Balancing (GSLB) | Enterprise/Platinum | |
| ICA Proxy and StoreFront Proxy | All | |
| Two-factor Auth (RADIUS) | All | |
| StoreFrontAuth (nFactor) | Enterprise/Platinum | |
| nFactor Authentication | Enterprise/Platinum | |
| Native OTP Authentication (nFactor) | Enterprise/Platinum | |
| Self-Service Password Reset (SSPR) | Enterprise/Platinum | |
| HDX Insight (AppFlow) | Enterprise/Platinum | |
| SmartAccess | All | Yes |
| SmartControl | Platinum | Yes |
| RDP Proxy | Enterprise/Platinum | Yes |
| SSL VPN | All | Yes |
| PCoIP Proxy | Enterprise/Platinum | Yes |
| Unified Gateway | Enterprise/Platinum | Yes |
| Citrix SCOM MP for NetScaler | Platinum |
All Editions = Citrix Gateway VPX, NetScaler Standard Edition, NetScaler Advanced Edition (formerly known as Enterprise Edition), and NetScaler Premium Edition (formerly known as Platinum Edition).
- Citrix Gateway VPX is the inexpensive VPX appliance that only does Citrix Gateway. It doesn’t even do Load Balancing. This edition is no longer sold by Citrix.
- NetScaler Advanced Edition is the minimum edition for many Gateway features, and thus is recommended for all Gateway purchases.
Gateway Universal Licenses – many Citrix Gateway features require Citrix Gateway Universal licenses for each concurrent connection to the Citrix Gateway Virtual Server. See the above table for which features require these licenses.
When you create a Citrix Gateway Virtual Server, in the Basic Settings section, the ICA Only setting determines if you need Citrix Gateway Universal licenses or not. If the Virtual Server is set to ICA Only is true, then features requiring Universal Licenses are disabled. But if ICA Only is set to false, then you need a Citrix Gateway Universal license for every user that connects to this Citrix Gateway Virtual Server.
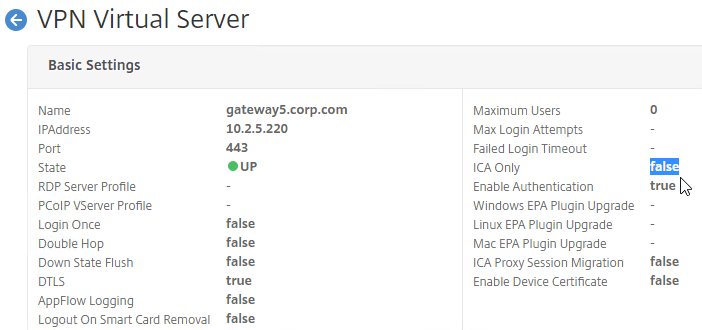
Most editions of NetScaler include Gateway Universal licenses:
- Citrix Gateway VPX does not come with any Gateway Universal Licenses. This edition is no longer sold by Citrix.
- NetScaler Standard Edition comes with 500 Gateway Universal Licenses. This edition is no longer sold by Citrix.
- NetScaler Advanced Edition comes with 1,000 Gateway Universal Licenses
- NetScaler Premium Edition comes with unlimited Gateway Universal Licenses
If your NetScaler Edition does not include a sufficient number of Universal Licenses for your user load, then you can acquire these licenses through other means:
- Citrix Virtual Apps and Desktops (CVAD) Premium Edition includes Gateway Universal licenses for each licensed user
- “a la carte” Citrix Gateway Universal Licenses – these are very inexpensive
You can install more Gateway Universal licenses on the NetScaler appliance. The Gateway Universal licenses are allocated to the case sensitive hostname of each appliance. If you have an HA pair, and if each node has a different hostname, then allocate the Gateway Universal licenses to the first hostname, and then reallocate the same licenses to the other hostname.
To see the hostname, click your username on the top right.
To change the hostname:
- Click the gear icon on the top right. Note: this icon won’t work unless you are logged in as nsroot.
- Then click the third section.
Go to https://citrix.com/account and allocate your purchased Gateway Universal licenses to the hostname of the appliance.
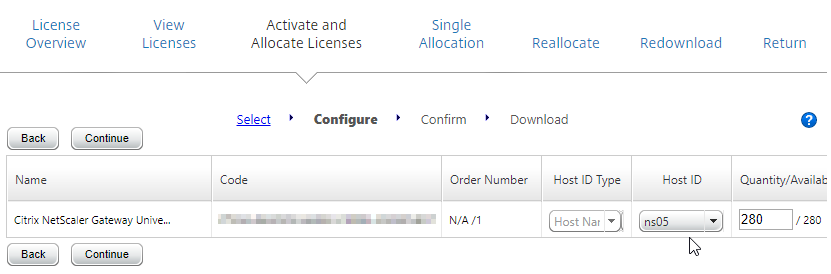
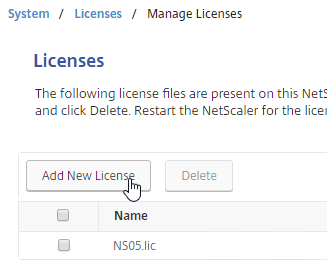
To upload the allocated Gateway Universal licenses to the appliance, go to System > Licenses > Manage Licenses. A reboot is required.
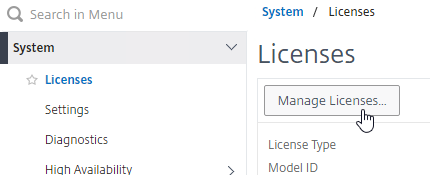
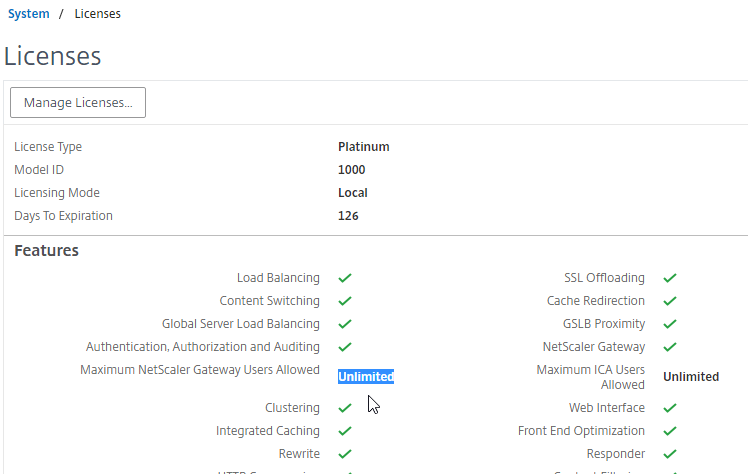
To see the number of installed Gateway Universal licenses:
- On the left, expand System, and click Licenses.
- On the right, in the Maximum Citrix Gateway Users Allowed field is the number of licensed users for Citrix Gateway Virtual Servers that are not set to ICA Only.
RfWebUI Portal Theme
Citrix Blog Post Branding your Deployment Part 2: Matching NetScaler to StoreFront explains Citrix Gateway Portal Themes, how to edit the Portal Theme CSS, and warns about GUI changes overwriting CSS file changes.
NetScaler article Unleashing RfWebUI Potential: JavaScript-Powered Citrix Gateway Login Page Customization explains how to use JavaScript to customize the RfWebUI theme.
NetScaler article Visually change RFWebUI with CSS shows how to relocate the form header to the top of the username input field and make it bold and adjust the positioning of the “User name:” and “Password:” labels nearer to the input fields.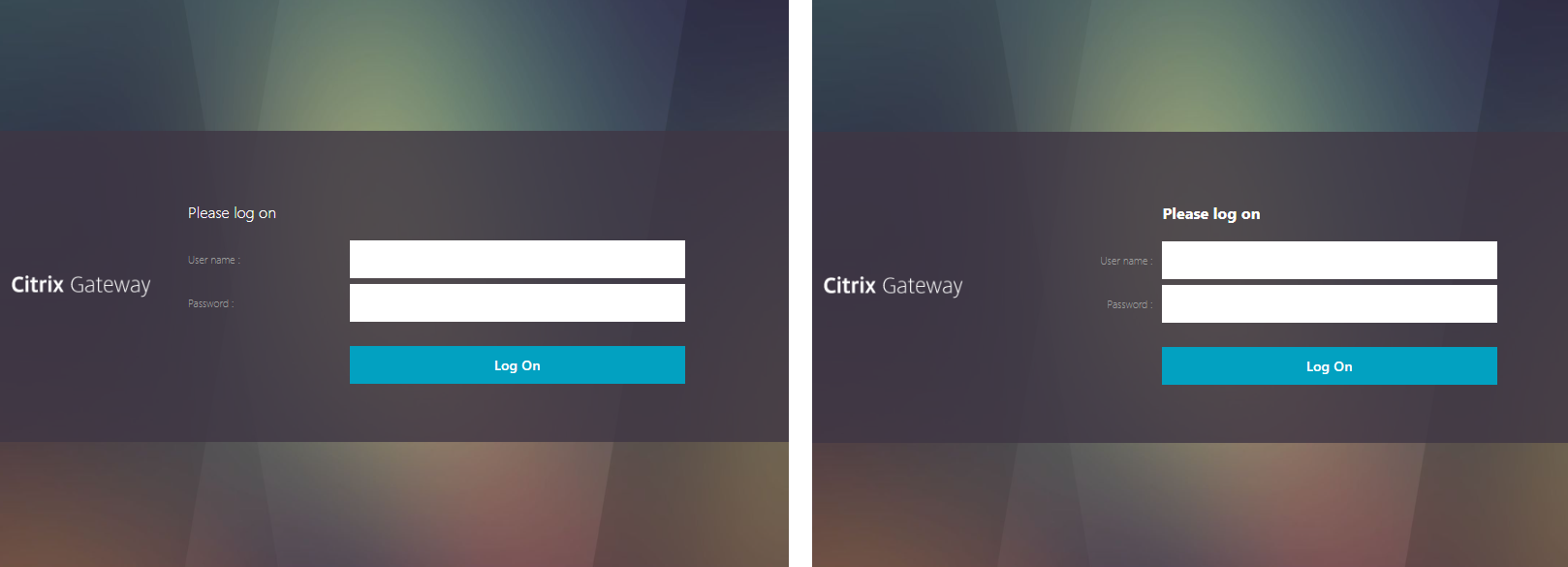
If you want the logon page for Citrix Gateway to look like Citrix Cloud, then see CTX258331 Customizing the on-premises Citrix Gateway authentication page to look identical to Citrix Cloud logon page.
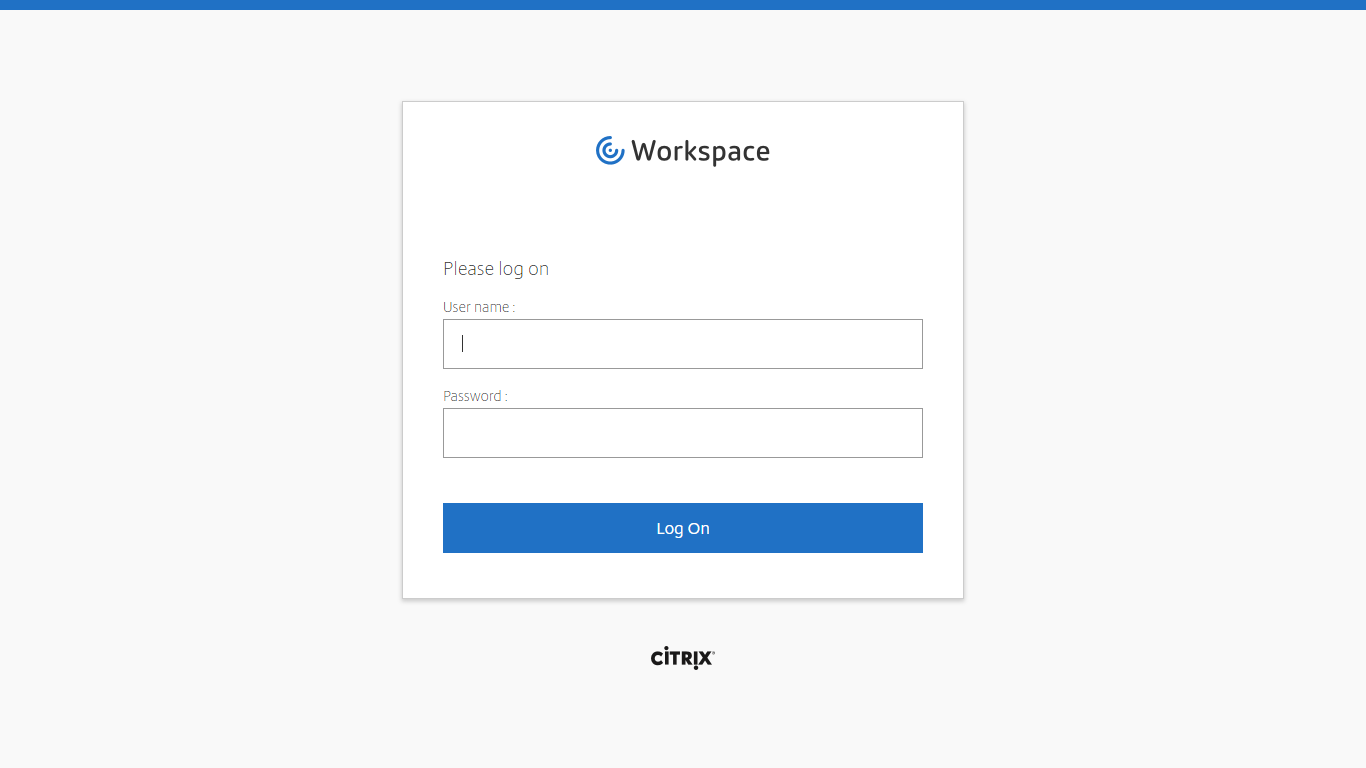
If you want the logon page for Citrix Gateway to look more like StoreFront 3.0 and newer, enable the built-in RfWebUI or X1 theme. RfWebUI is optimized for Unified Gateway (Clientless VPN) since it provides the exact same appearance and user experience as StoreFront 3.x. The Unified Gateway RfWebUI theme can display RDP Links, Web Links (bookmarks), PCoIP published icons, along with the familiar StoreFront apps and desktops. Note: RfWebUI requires StoreFront 3.6 or newer.
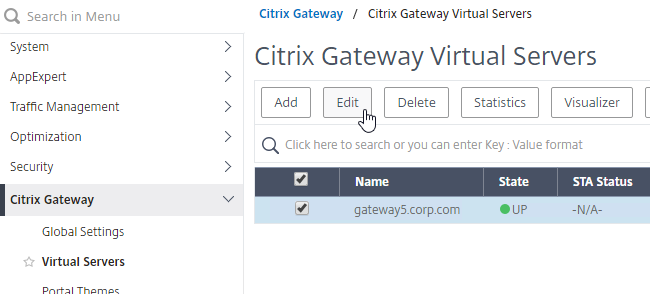
- Go to Citrix Gateway > Virtual Servers and edit an existing Virtual Server.
- If you see the Portal Theme section on the left:
- Then click the pencil icon.

- Then click the pencil icon.
- If you don’t see Portal Theme on the left:
- On the right, in the Advanced Settings section, click Portal Themes.
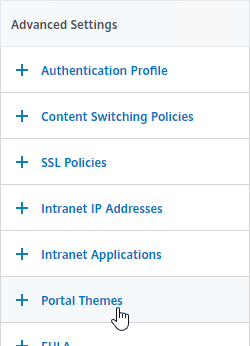
- On the right, in the Advanced Settings section, click Portal Themes.
- On the left, change the Portal Theme drop-down to RfWebUI. Click OK.
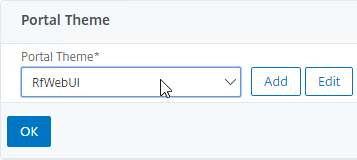
- Click Done to close the Gateway Virtual Server.
bind vpn vserver gateway.corp.com -portaltheme RfWebUI
- When you access the Citrix Gateway login page you’ll see the theme.
RfWebUI Customizations
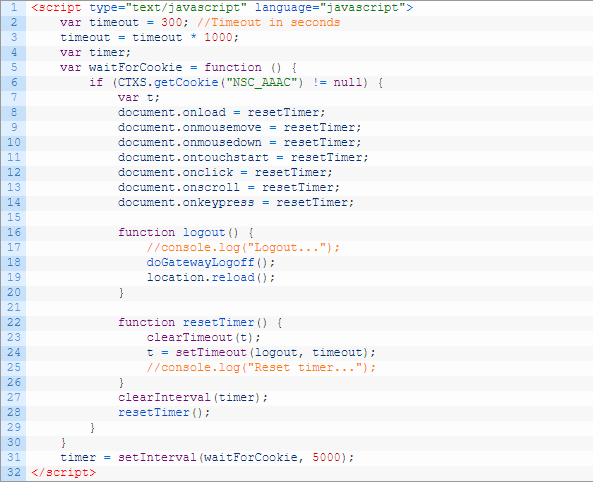
- If you want an idle timer for RfWebUI, see CTP Simon Gottschlag RfWebUI Idle Timeout.
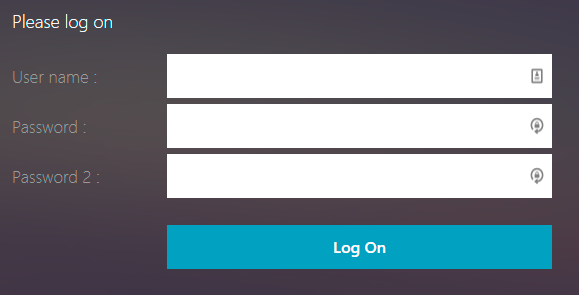
- If you have challenge-based RADIUS authentication, and if you need to remove the second password field from RfWebUI, see CTP Simon Gottschlag Remove “Password 2” from RfWebUI.
Custom Portal Theme
You can create your own theme by starting from one of the built-in themes:
- Go to Citrix Gateway > Portal Themes.
- On the right, click Add.
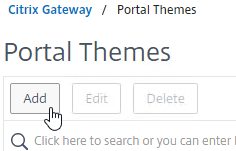
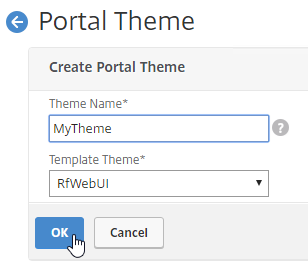
- Give the theme a name, select RfWebUI as the Template Theme, and click OK.
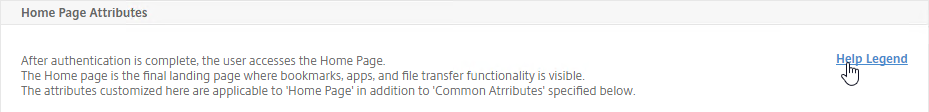
- In the Look and Feel section, there are two sub-sections: one for Home Page Attributes, and one for Common Attributes.
- The Home Page Attributes section is for Unified Gateway (aka VPN Clientless Access). Notice that the Websites Sections can be disabled.
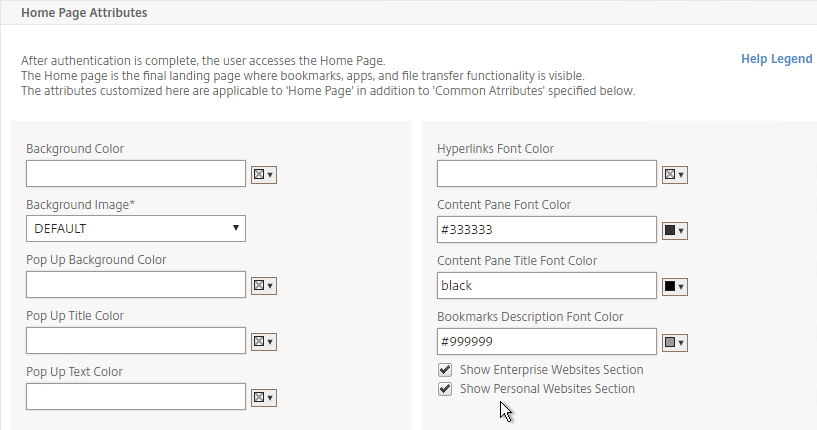
- The Help Legend link at the top of the section shows you what the other fields modify.
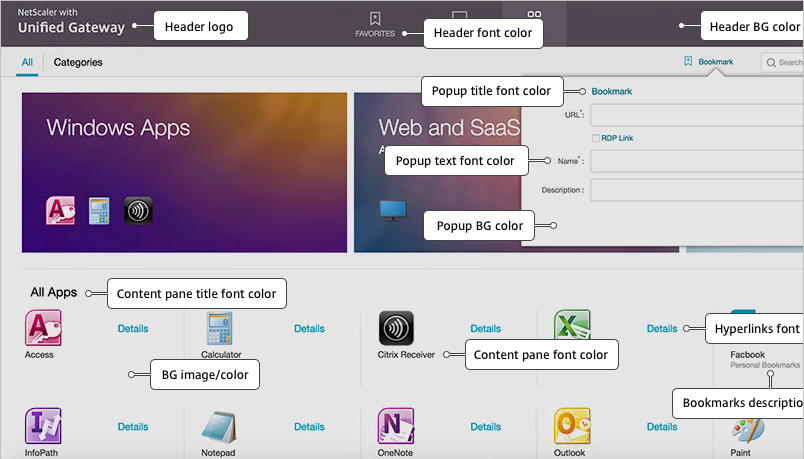
- If you want to modify some attributes of the logon page, use the Common Attributes sub-section. The labels are changed later.
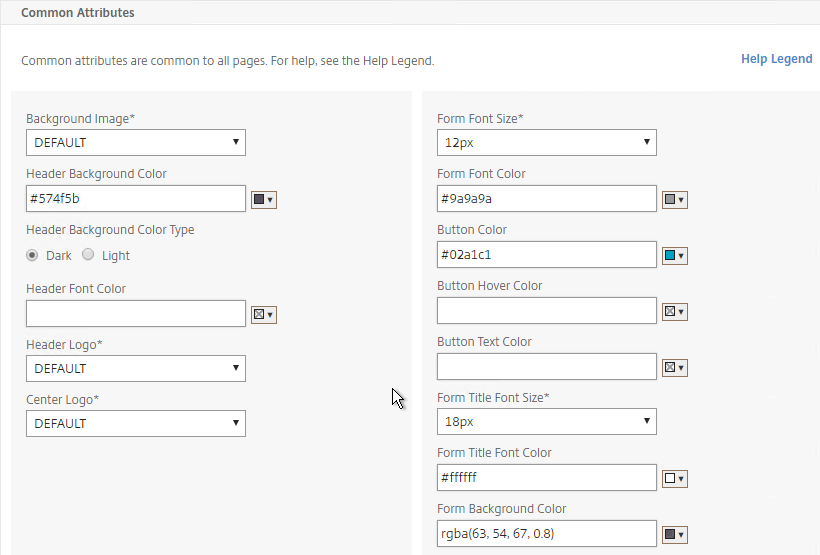
- The Help Legend link at the top of the Common Attributes section shows you what the fields modify.
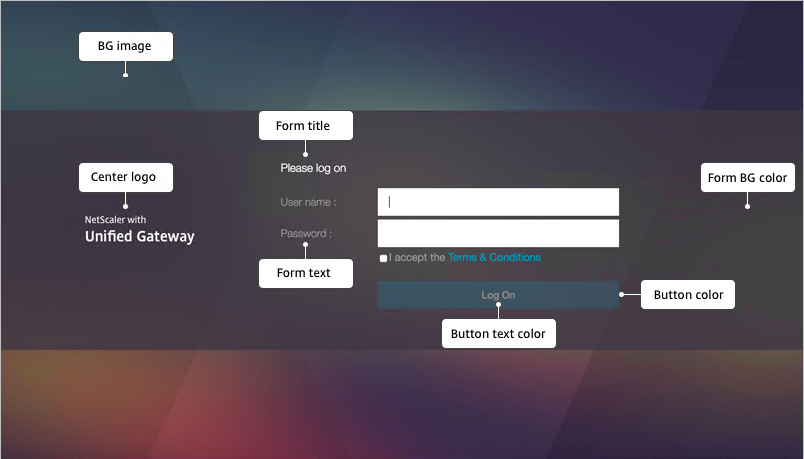
- Make changes as desired, and click OK at the bottom of the page.
- After you click OK, the Language section appears.
- In the Language section, select a language, and click OK.
- On the right, in the Advanced Settings section, click Login Page.
- Make changes as desired (e.g. Password Field Titles), and click OK.
- At the top of the screen, click the link to Click to Bind and View Configured Theme.

- Select a Gateway Virtual Server, and click Bind and Preview. Notice that you can also bind Portal Themes to AAA vServers.
- The logon page is displayed.
- You could go to /var/netscaler/logon/themes/MyTheme/css and make more changes to custom.css, but this file gets overwritten any time you make a change in the Portal Themes section of the NetScaler GUI.
- Citrix CTX209526 NetScaler; How to Copy a Portal Theme from the Device running version 11.0 to another Device running 11.0.
Public DNS SRV Records
When a user launches Receiver, instead of typing in the Gateway FQDN, the user can enter an email address. Receiver uses the email suffix to lookup the Gateway FQDN. It does this by looking for an SRV record named _citrixreceiver._tcp in the email suffix’s domain (e.g. _citrixreceiver._tcp.corp.com). If you have multiple email suffixes, then you need to add the SRV record to each email suffix DNS zone.
Note: to eliminate certificate and/or trust prompts, the Gateway certificate must match discoverReceiver.email.suffix (e.g discoverReceiver.corp.com). If you have multiple email suffixes, then you need the certificate to match every email suffix.
To enable email-based discovery, add a SRV record to each public email suffix DNS zone. Here are sample instructions for a Windows DNS server:
- In Server Manager, click Tools > DNS.
- In the left pane of DNS Manager, right-click your DNS domain, and click Other New Records.
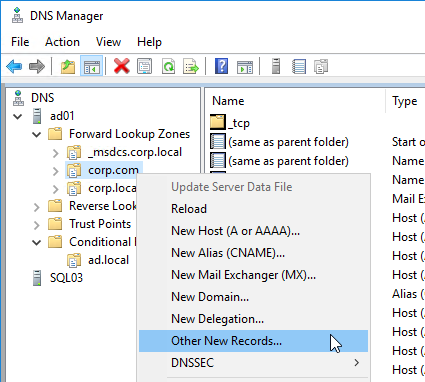
- In the Resource Record Type dialog box, select Service Location (SRV), and then click Create Record.
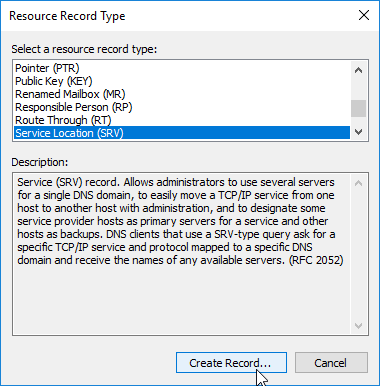
- In the New Resource Record dialog box, do the following:
- In the Service box, enter the host value
_citrixreceiver. - In the Protocol box, enter the value
_tcp. - In the Port number box, enter 443.
- In the Host offering this service box, specify the fully qualified domain name (FQDN) for your Citrix Gateway Virtual Server in the form servername.domain (e.g. gateway.company.com).
- In the Service box, enter the host value
- Click OK to close the New Resource Record dialog box.
- Click Done to close the Resource Record Type dialog box.
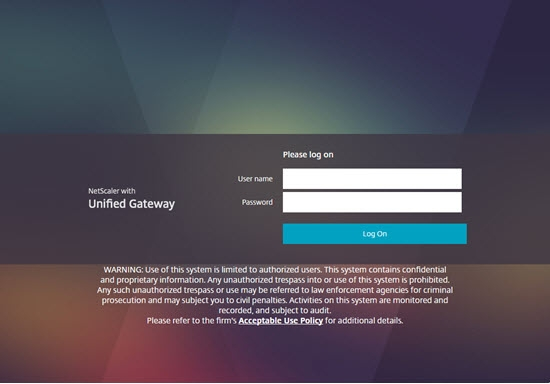
Customize Logon Page
Logon Page Labels
When two factor authentication is configured on Citrix Gateway, the user is prompted for User name, Password, and Password 2.
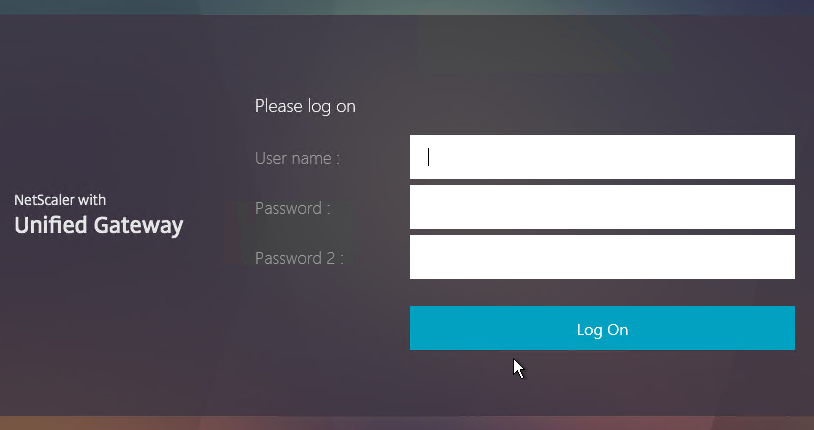
The Password field labels can be changed to something more descriptive, such as Active Directory or RSA:
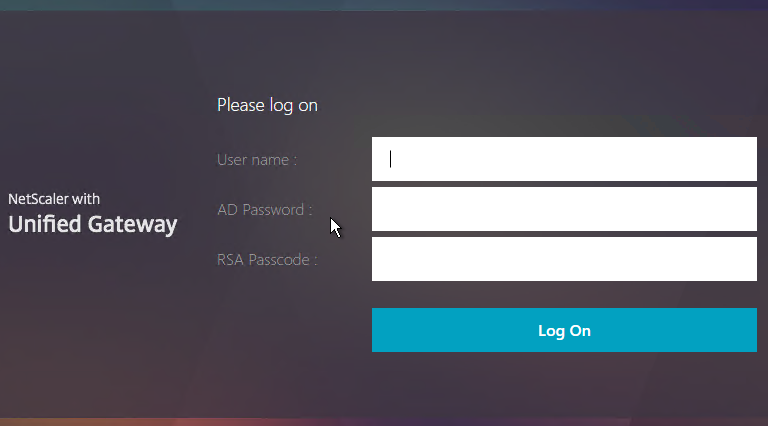
To change the labels, edit a Portal Theme:
- Go to Citrix Gateway > Portal Themes, and edit an existing theme. You can’t edit the built-in themes, so you’ll have to create one if you haven’t already.
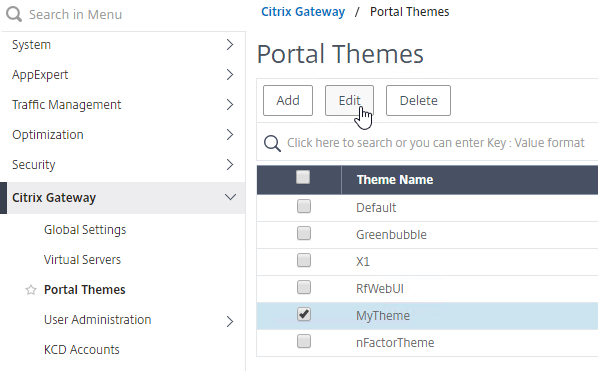
- If you see the Login Page section on the left:
- Click the pencil icon in the Login Page section.
- Click the pencil icon in the Login Page section.
- If you don’t see the Login Page section on the left:
- On the right, in the Advanced Settings column, click Login Page to add it to the left.
- On the right, in the Advanced Settings column, click Login Page to add it to the left.
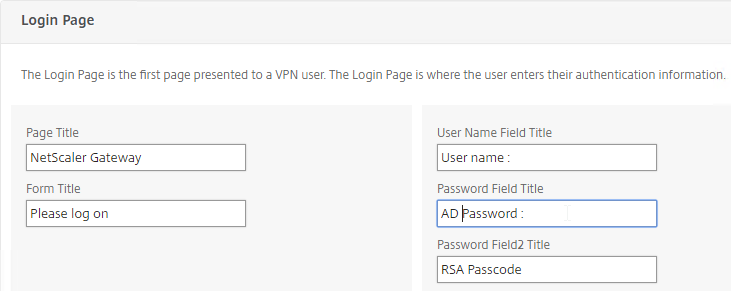
- On the left, in the Login Page section, change the two Password fields to your desired text.
- Click OK to close the Login Page section.
- If you are using the RfWebUI theme, the default text size for the form field labels is 17px. However, the Portal Themes editor defaults to 12px. You can change it back to 16px or 18px by doing the following:
- In the Look and Feel section, click the pencil icon.
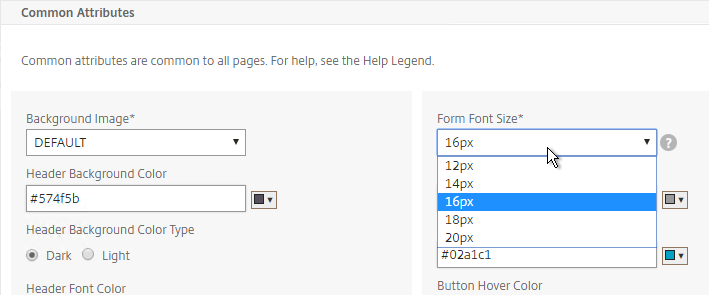
- Scroll down to the Common Attributes section.

- Change the Form Font Size drop-down to 16px or 18px.
- Click OK to close the Look and Feel section.
- In the Look and Feel section, click the pencil icon.
- In the Portal Theme section at the top of the page, you can Click to Bind and View Configured Theme to Preview your changes.
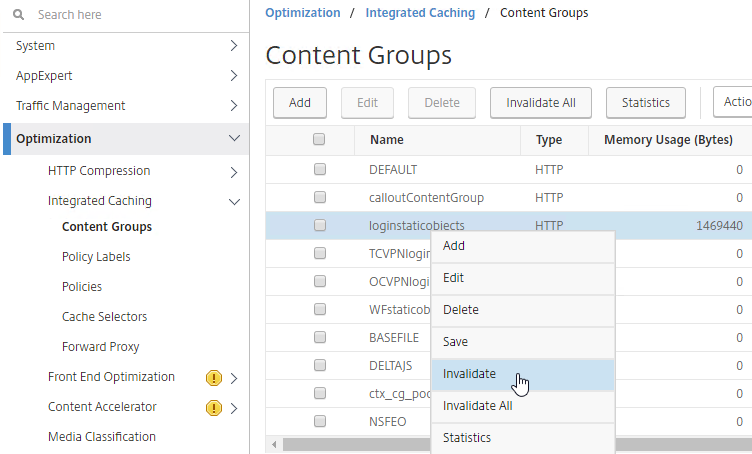
- You might have to invalidate the loginstaticobjects Integrated Caching Content Group (Optimization > Integrated Caching > Content Groups) before the changes appear. This seems to be true even if Integrated Caching is disabled.
Logon Security Message (Disclaimer, EULA)
You can force users to agree to a EULA before they are allowed to login.
Clicking the Terms & Conditions link allows the user to view the EULA text that you have entered.
Do the following to configure the EULA:
- Go to Citrix Gateway > Resources > EULA.
- On the right, click Add.
- Give the EULA a name, and enter some text. You can even enter HTML code. See the example posted by Chris Doran at Citrix Discussions.
- Scroll down, and click Create.
- Edit a Gateway Virtual Server.
- On the right, in the Advanced Settings column, click EULA.
- On the left, in the EULA section, click where it says No EULA.

- Click where it says Click to select.
- Click the radio button next to the previously created EULA, and click Select.
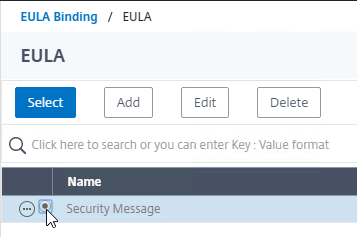
- Click Bind.
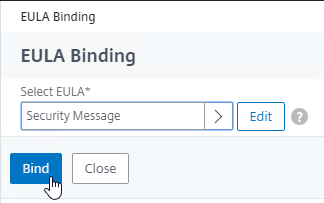
- Mike Roselli at Automatic EULA Acceptance by Cookie Rewrite Guide at Citrix Discussions details Rewrite policies that change the behavior so that users only have to accept the EULA once. It records acceptance in a cookie.
- Sam Jacobs Adding an EULA for AAA Login at CUGC explains how to enable the EULA on the AAA logon page.
Theme File Customization
The original themes (Default, Green Bubble, and X1) use files from /netscaler/ns_gui/vpn/js and /var/netscaler/logon/themes. A commonly edited file is /netscaler/ns_gui/vpn/js/gateway_login_form_view.js since this file is responsible for rendering the logon form.
The new RfWebUI theme is different than the original themes, because it pulls files from /var/netscaler/logon/LogonPoint/receiver. This means the customizations for NetScaler 11.0 won’t work with the new RfWebUI theme. When reviewing customization guides for NetScaler 11, be aware that most of them won’t work for the RfWebUI theme.
Logon Page Links
Citrix CTX202444 How to Customize NetScaler Gateway 11 logon Page with Links shows how to add links to the Citrix Gateway 11 logon page. This only works in the Default, Green Bubble, and X1 themes (no RfWebUI theme).
Other Customizations
CTP Sam Jacobs at Adding Text, Links and Other Elements to the NetScaler Logon Page – Part 2 at CUGC explains how to add text to the RfWebUI theme logon page. The process for RfWebUI is quite different than the older themes:
- Text is stored in
/var/netscaler/logon/themes/<theme>/strings.<language code>.json - Custom CSS is stored in
/var/netscaler/logon/themes/<theme>/css/theme.css - Sample Logon Page:
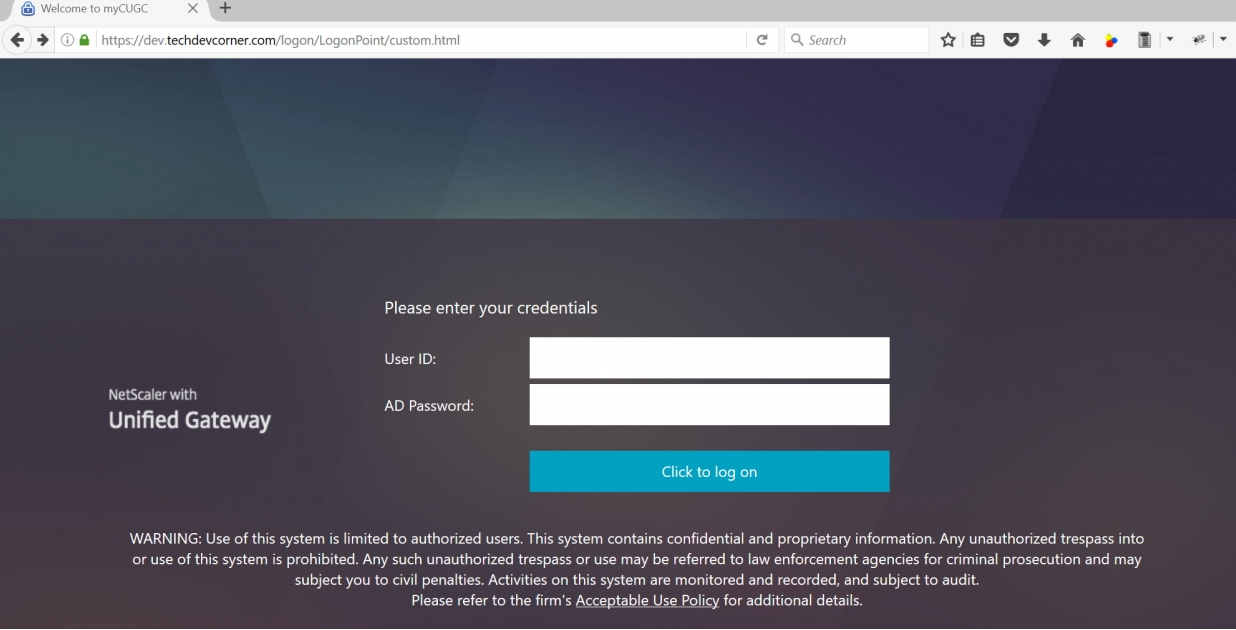
CTP Sam Jacobs at Adding Text, Links and Other Elements to the NetScaler Logon Page – Part 1 at CUGC explains how to modify custom.css and en.xml to add text below the logon box on the Logon Page. No Rewrite policies or source code modifications needed.
Mike Roselli at Netscaler 11 Theme Customization – How to Add Links and Verbiage at Citrix Discussions has sample rewrite policies to customize the Citrix Gateway logon page with additional HTML.
Craig Tolley Customising the NetScaler 11 User Interface – Adding Extra Content: add new sections to login page. These sections pull content from local HTML files.
Daniel Ruiz Set up a maintenance page on NetScaler Gateway: configure a Responder policy (see the blog post for sample HTML code). During maintenance, manually bind the Responder policy to the Gateway. Manually remove the policy after maintenance is complete.
Manuel Kolloff Adding additional languages to NetScaler RfWebUI Theme
UDP Audio Through Gateway
From John Crawford at Citrix Discussions and Marius Sandbu Enabling Citrix Receiver audio over NetScaler Gateway with DTLS
Note: Enabling DTLS on the Gateway also enables the Gateway to support EDT (Adaptive Transport) and Framehawk.
Requirements for UDP Audio:
- Citrix Receiver 4.2 or newer
- UDP 443 allowed to Citrix Gateway Virtual Server
- UDP 16500-16509 allowed from Citrix SNIP to the VDAs
To enable UDP Audio through Gateway, make changes on both the Citrix Gateway Virtual Server, and in Receiver:
- Edit a Citrix Gateway Virtual Server.
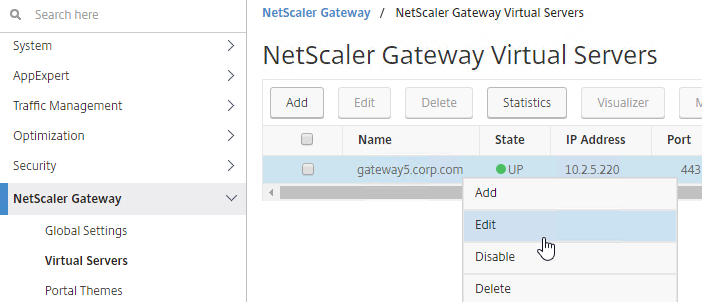
- In the Basic Settings section, click the pencil icon.
- Click More.
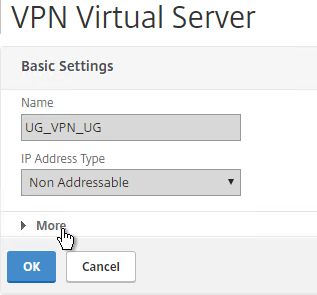
- Enable the DTLS option, and click OK.
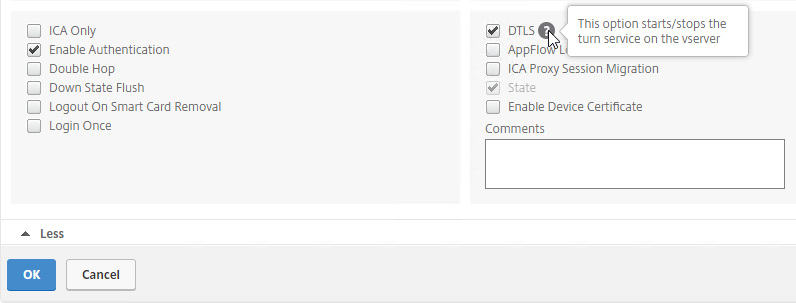
- After enabling DTLS, it probably won’t work until you unbind the Gateway certificate, and rebind it.
- On the left, click where it says 1 Server Certificate.
- Click Add Binding.
- Click where it says Click to select.
- Click the radio button next to the same certificate that’s already bound. Click Select.
- Click Bind.
- Click Close.
- Click Continue to close the Certificate section.
- On the left, click where it says 1 Server Certificate.
Client-side configuration
There are two methods of enabling RTP on the client side:
- Edit default.ica on the StoreFront server
- Use GPO to modify the client-side config
To edit the default.ica file on the StoreFront server (h/t Vipin Borkar): Edit the file C:\inetpub\wwwroot\Citrix\Store\App_Data\default.ica and add the following lines to the Application section:
EnableRtpAudio=true EnableUDPThroughGateway=true AudioBandwidthLimit=1
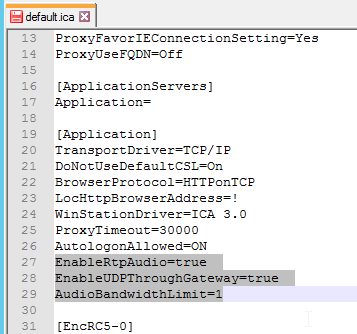
To use GPO to modify the client-side config:
- Copy the receiver.admx (and .adml) policy template into PolicyDefinitions if you haven’t already.
- Edit a GPO that applies to Receiver machines. You can also edit the local GPO on a Receiver machine.
- Go to Computer Configuration | Policies | Administrative Templates | Citrix Components | Citrix Workspace app | User Experience.
- On the right, edit the setting Client audio settings.
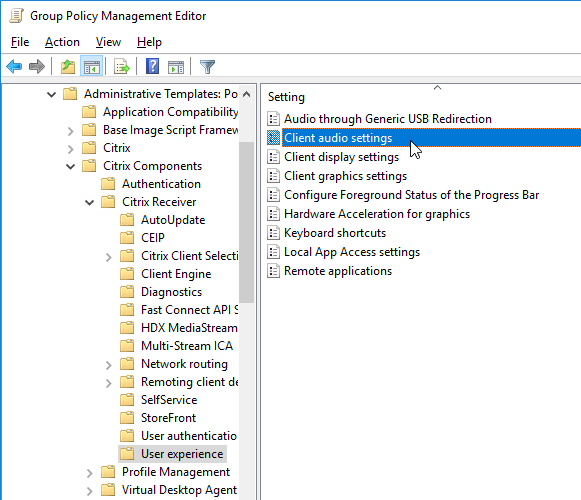
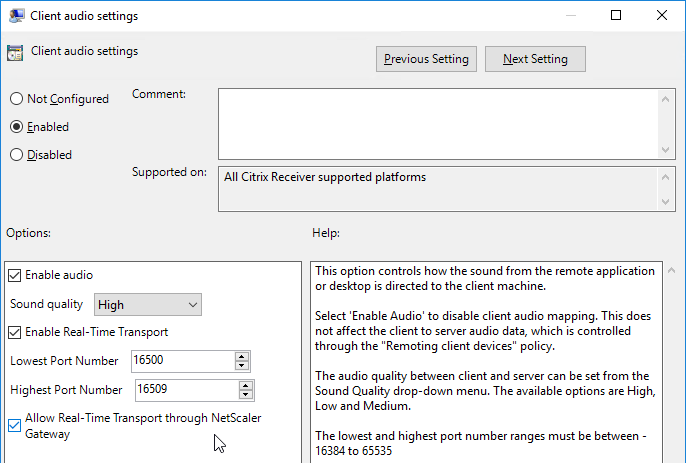
- Do the following in the Client audio settings dialog box.
- Enable the setting.
- Set audio quality as desired. Higher quality = higher bandwidth.
- Check to Enable Real-Time Transport.
- Check to Allow Real-Time Transport through Gateway.
- Click OK to close the Client audio settings dialog box.
- Look in the client-side registry at HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Citrix\ICA Client\Engine\Lockdown Profiles\All Regions\Lockdown\Virtual Channels\Audio to make sure the registry keys applied.
- When you launch the first session after enabling Real-Time Transport, you might be prompted to enable it through the client-side firewall.
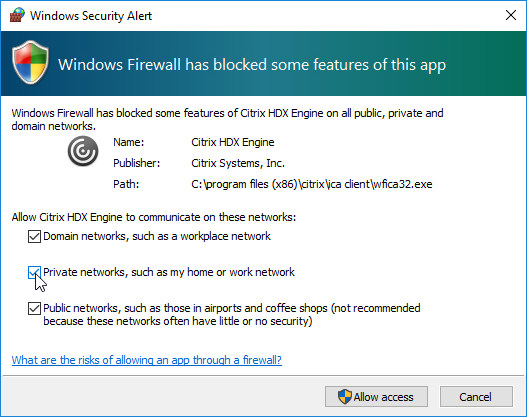
To view the current UDP Audio sessions:
- In the NetScaler GUI, click the Citrix Gateway node.
- On the right, click DTLS ICA Connections.
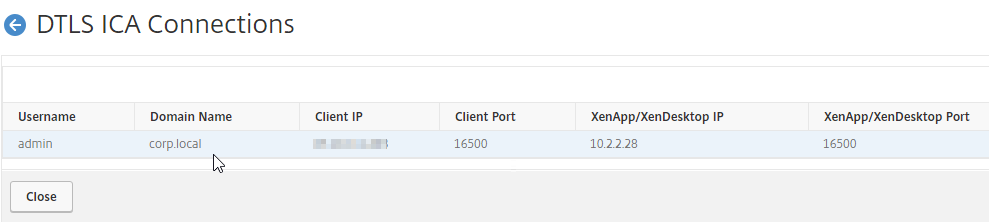
- This will show you all users that have UDP Audio connections through Citrix Gateway. Note: this is different than EDT. To see EDT (UDP) HDX connections, click ICA Connections instead.
Citrix VPN from Mobile Devices
Links:
- Citrix CTX201129 Configuration for Controlled Access to Different VPN Plugin Through NetScaler Gateway for XenMobile Deployments
- Citrix CTX227658 Per app VPN for android – Cannot connect to internal resources
Citrix VPN Clients on Mobile Devices (Android, iOS) contain one of the following in their User-Agent strings. You can use this text in a Session Policy expression.
- CitrixReceiver/NSGiOSplugin
- CitrixReceiver/CitrixVPN
To block the Citrix VPN client connections from mobile devices, do one of the following:
- Create an AppExpert > Responder > Policy with Action = DROP and Expression =
HTTP.REQ.HEADER("User-Agent").CONTAINS("CitrixReceiver/NSGiOSplugin")|| HTTP.REQ.HEADER("User-Agent").CONTAINS("CitrixReceiver/CitrixVPN"). Either bind the Responder Policy Globally, or bind it to the Gateway vServers.
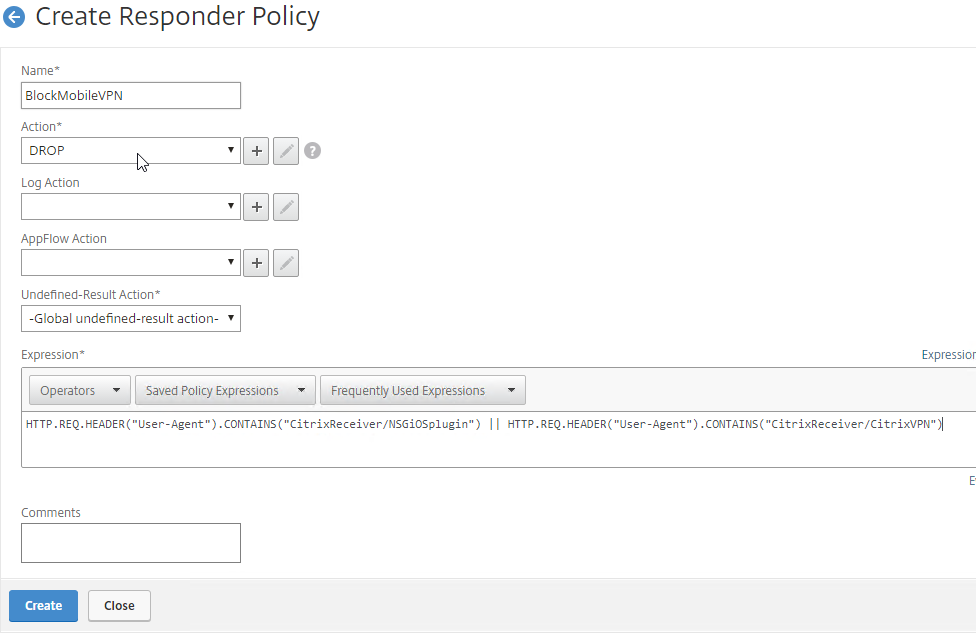
- In your Gateway Session Policies, on the Client Experience tab, set the Plug-in Type to Java. If any of them are set to Windows/MAC OS X, then VPN for Mobile is allowed.
StoreFront – Rewrite X-Citrix-Via
When Citrix Gateway communicates with StoreFront, it adds a header called X-Citrix-Via that contains the FQDN entered in the user’s address bar. StoreFront uses this header to find a matching Gateway object so StoreFront knows how to handle the authentication. In Citrix Gateway 11.0 and newer, you can create a rewrite policy to change this header. This is useful when changing URLs or using DNS aliases for Gateways. See CTX202442 FAQ: Modify HTTP Header X-Citrix-Via on NetScaler for more details.
Here’s a sample rewrite policy for this header:
enable ns feature REWRITE add rewrite action rwact_storefront replace "HTTP.REQ.HEADER(\"X-Citrix-Via\")" "\"mystorefront.mydomain.com\"" add rewrite policy rwpol_storefront "HTTP.REQ.HEADER(\"X-Citrix-Via\").NE(\"mystorefront.mydomain.com\")" rwact_storefront bind vpn vserver mygateway-vs -policy rwpol_storefront -priority 100 -type REQUEST
Device Certificates
Citrix Gateway can require Device Certificates (machine based) before a user can login. The Endpoint Analysis Plug-in reads the machine certificate, and compares it to a CA certificate that is bound to the Citrix Gateway Virtual Server.
- Device Certificates are different from User Certificates.
- Administrator permissions are required to access the machine certificate’s private key. Citrix Gateway Plug-in (VPN client) can workaround this requirement.
- OCSP is required. You can use Microsoft Online Responder.
To enable Device Certificates on Citrix Gateway
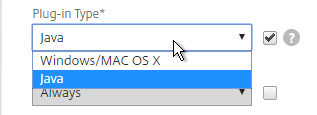
- Create a OCSP Responder on NetScaler and bind it to the CA Certificate. See CTX200290 How to Configure Device Certificate on NetScaler Gateway for details. At Traffic Management > SSL > Certificates > OCSP Responder.
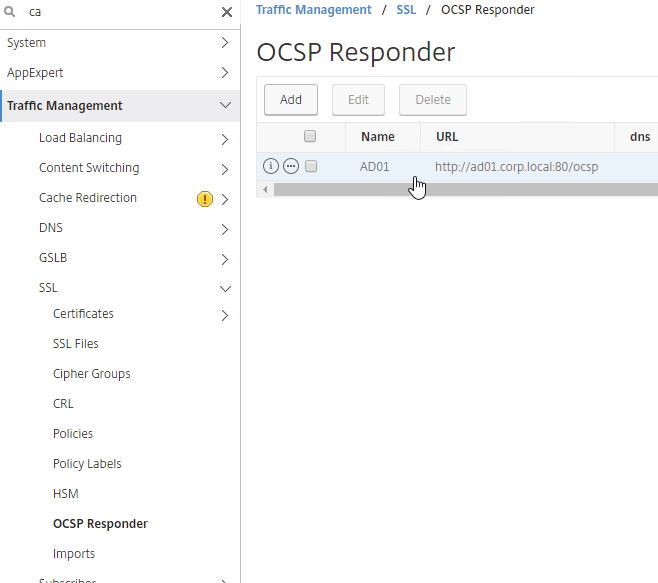
- The URL for Microsoft Online Responder is http://ocsp_server_FQDN:80/ocsp.
- Misja Geuskens at Netscaler Device certificate checks fails with W2K12R2 Online responder says don’t check the Nonce box.
- Import CA certificates for Root and Intermediate. At Traffic Management > SSL > Certificates > CA Certificates.
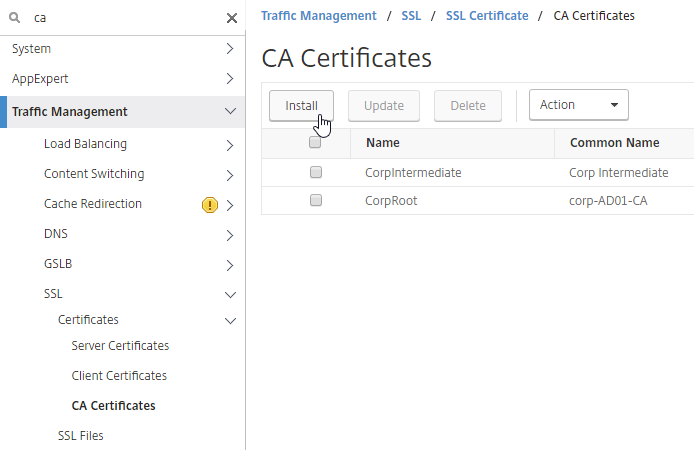
- Right-click each CA certificate, and click OCSP Bindings.
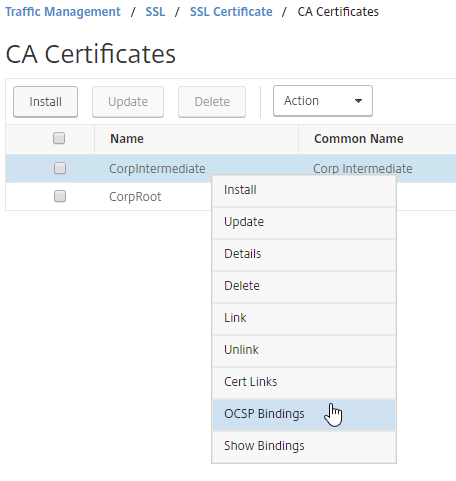
- Select the OCSP Responder you created earlier.
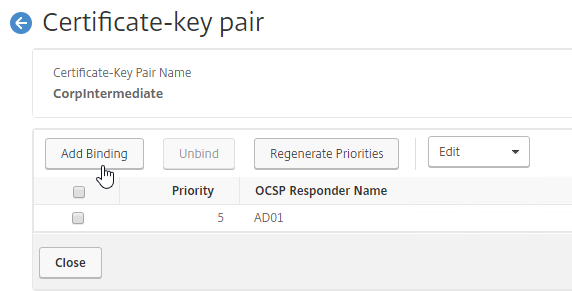
- Select the OCSP Responder you created earlier.
- Bind the CA certificates to the Gateway Virtual Server in the CA certificates section.
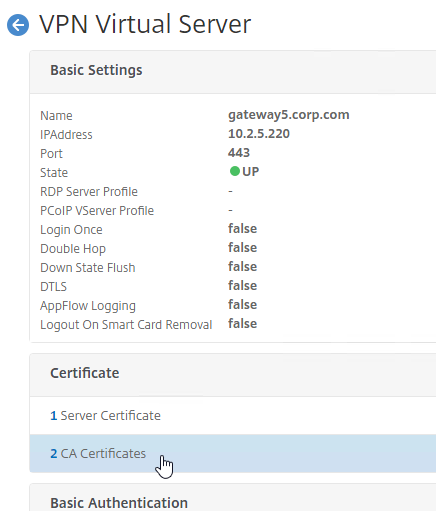
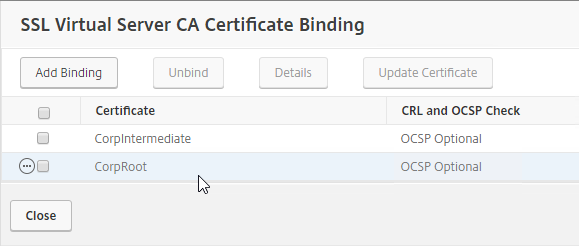
- Enable Device Certificates in the Citrix Gateway Virtual Server > Basic Settings > More section. Move the same CA certificates to the right.
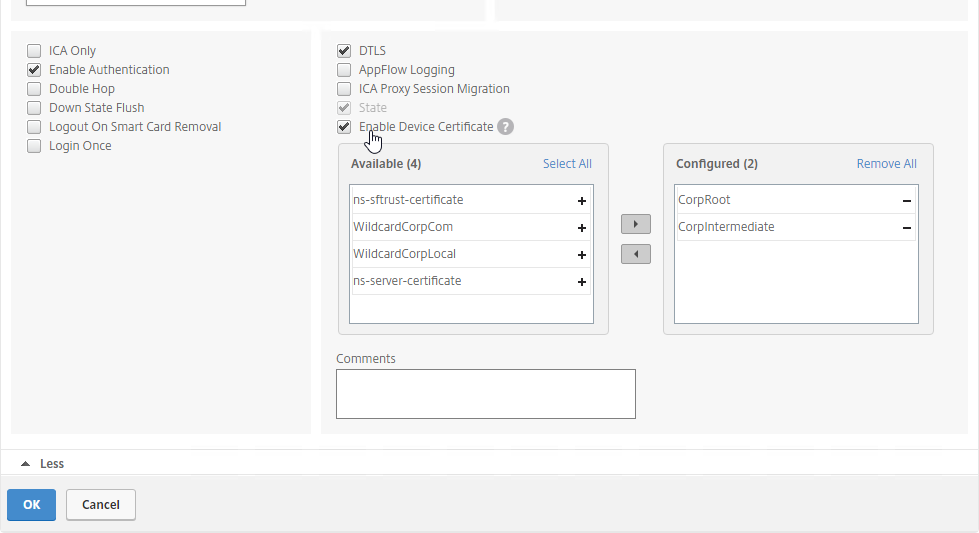
Device Certificates in nFactor (AAA)
nFactor Endpoint Analysis also supports Device Certificates. OCSP (described earlier) is also required for this feature.
- It’s probably easier to search the menu for EPA than to actually navigate to Security > AAA – Application Traffic > Policies > Authentication > Advanced Policies > Actions > EPA.
- On the right, click Add.
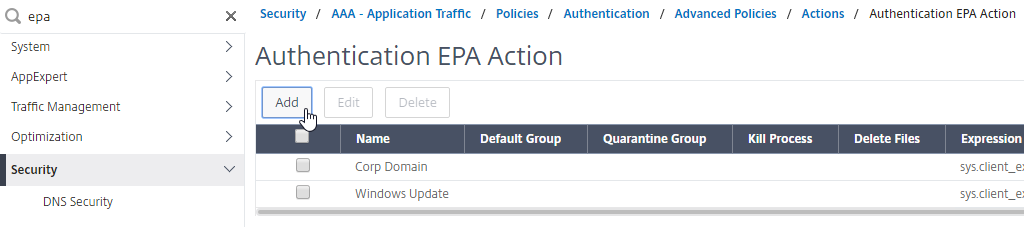
- On the bottom right, click EPA Editor.
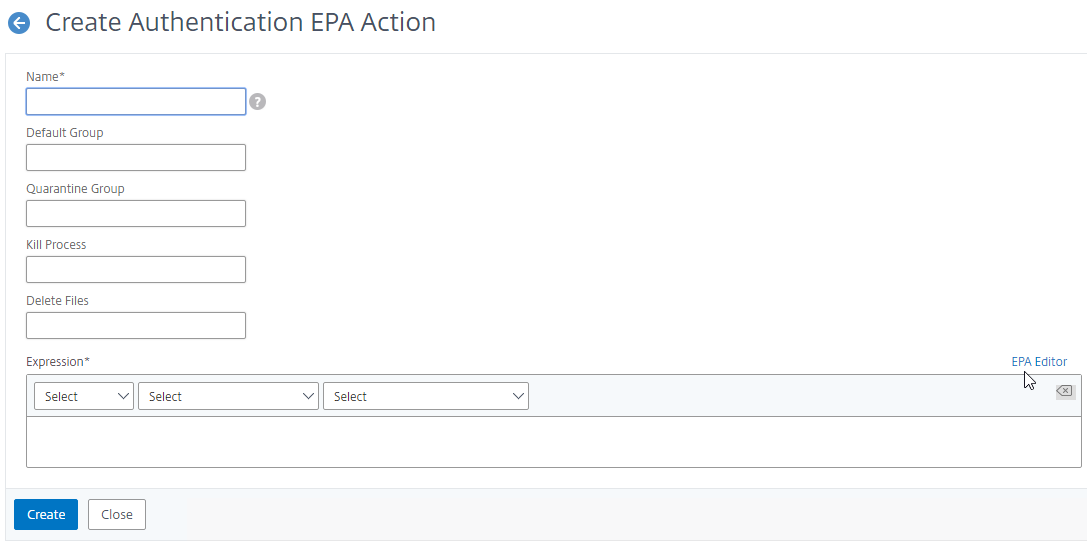
- Change the first drop-down to Common.
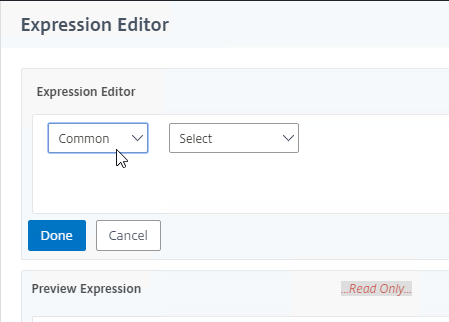
- Change the second drop-down to Device Certificate and then click Done
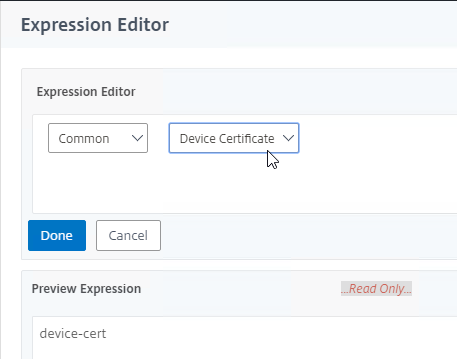
- Give the EPA Action a name and then click Create.
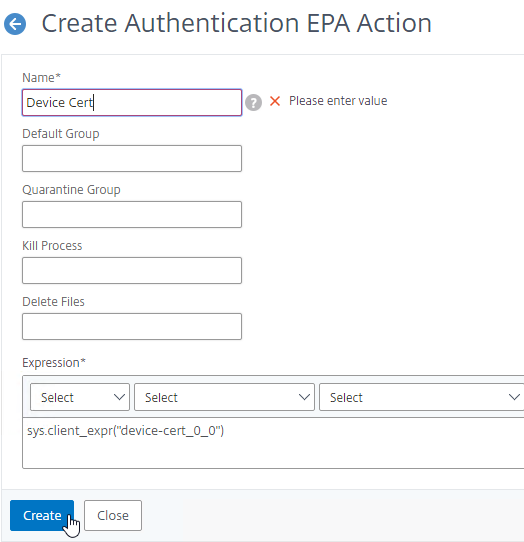
- You can now use this EPA Action in your nFactor configuration.
- On the Gateway Virtual Server, bind CA certificates as described in the previous section.
- On the AAA Virtual Server, click the pencil in the Basic Settings section.
- Click More.
- Near the bottom, click Add next to the CA for Device Certificate section to bind CA certificates. Then click OK.
User Experience
Users will be prompted to install the Endpoint Analysis plugin.
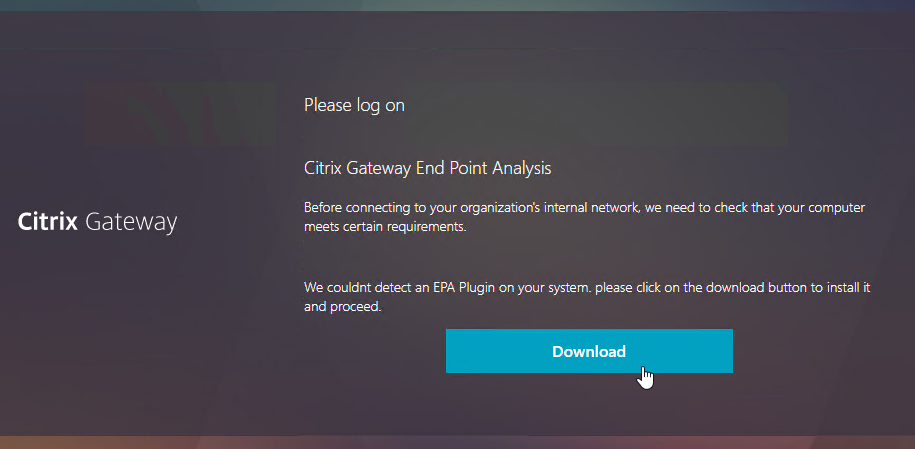
Click Yes to run the scan. Note: if the user is not an administrator of the local machine, then you must also install the Citrix Gateway Plug-in (VPN client) to handle the security restrictions.
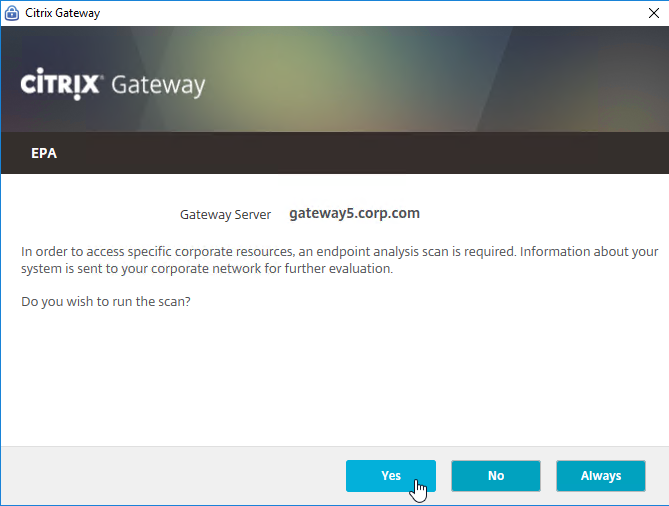
If there are multiple certificates on the client machine, the user will be prompted to select one.
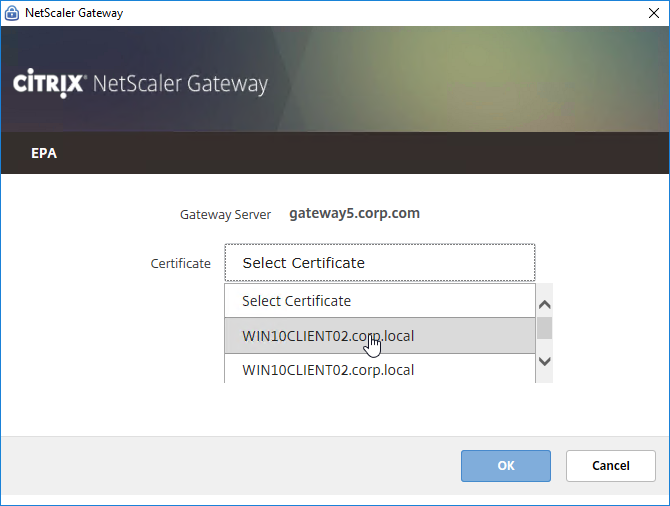
The chosen machine certificate is stored in %localappdata%\Citrix\AGEE\config.js. The user won’t be prompted for certificate selection again unless you delete this file.
This same folder contains nsepa.txt, which lets you troubleshoot device certificate checking. The most common issue is lack of permissions, which is handled by installing the Citrix Gateway VPN Plug-in. The Gateway VPN Plug-in version must match the firmware version.
Hello Carl,
very interesting article, thank you.
I am trying to configure my Secure Access client and my Netscaler portal so that the login field of the Secure Access client is automatically filled with the username of the local authenticated user.
I have modified the config.js file likethis :
“auto open homepage`”:null,`”connectingTo`”:`”rGatewayURL`”,`”connections`”:[{`”name`”:`”$strConnectionName`”,`”url`”:`”$strGatewayURL`”}],`”debug logging`”:null,`”language`”:null,`”lastUserName`”:`”%username%”}”
It does not work, the login field desperately stays blank.
Modifying the xml file on the Netscaler does not work neither.
Do you see a way to automatically fill the login field of the Secure Access client with the %username% variable of the Windows session please ?
Hello Carl,
The link to the Netscaler article whose title starts with “Unleashing” is broken. In your post here, it is under the RFWebUI header near the beginning. Here is the current link as of my posting this comment:
https://community.netscaler.com/articles/security/unleashing-rfwebui-potential-javascript-powered-citrix-gateway-login-page-customization/
Thanks for pointing that out. I updated the links.
Hi Carl. You write “Citrix Virtual Apps and Desktops (CVAD) Premium Edition includes Gateway Universal licenses for each licensed user”. That’s exactly how I understood it too. However, the Citrix Universal Premium license is allocated to the license server. How do I get this as a Gateway Universal license in Netscaler in addition to the 1000 of the Netscaler Advanced Edition?
https://mycitrix.com/account should have a separate license for Gateway Universal.
Thank you Carl. I can see Citrix Access Gateway Universal license in Citrix license portal but these are from the old, invalid Virtual Apps Premium licenses. I think I’ll have to reach out to our partner.
Hello, Carl!
Could you help with some advice, please. I can’t cope with the task for a long time. How can I add certificate template validation on Citrix Gateway? It is necessary that only certificates written to a USB token are accepted, and those issued for other purposes are rejected.
Thx for an answer!
I would like to enable a dynamic footer on the landing page, Any suggestions?
Currently, whenever I zoom in or out it moves/misplaces the content of the footer.
Hi Carl,
Is it possible just to only display the Enterprise Web icons after a user logs in?
Thanks,
Rob
Hi Carl –
Seems the both the Sam Jacobs links are no longer available. Are they available elsewhere?
I found his blog and updated the links. Thanks for pointing this out.
Hi Carl,
First of all thanks for sharing this Blog. it helped lot, however, in my setup EPA scan is not working for Ubuntu machines.
pls suggest on this.
I have not tried Ubuntu EPA but here are some links:
https://www.citrix.com/downloads/citrix-gateway/plug-ins/Citrix-Gateway-VPN-EPA-Clients-Ubuntu.html
https://support.citrix.com/article/CTX214394/netscaler-gateway-endpoint-analysis-supported-operating-system-and-browsers
https://docs.citrix.com/en-us/citrix-gateway/current-release/vpn-user-config/endpoint-policies.html#endpoint-analysis-scans-supported-for-ubuntu
Hello Carl, I am unable to find it, after logon i get the unified gateway, I know there is a pretty easy way to change it to go to the citrix farm after logging on the ADC? (I found this once in one of your comments but now I am unable to find it.)
In a Session Policy, on the Published Apps tab, enable ICA Proxy.
Ah yeah! just needed that little nudge in the right direction.. thank you! BTW- as always great site and amazing tips with the email OTP\MFA with rdp and this information! big thank you!
What about an automatic maintenance page of the nodes that are down. I haven’t found a good guide/explanation to do that properly. There is a reference to the guide from Daniel Ruiz, but that is a manual maintenance page. I am searching for an automatic solution. If all nodes are down, Netscaler should show a static maintenance page.
This may help: https://mickhilhorst.com/citrix/maintenance-page-using-responder-policy/
The link for “RfWebUI Customizations
If you want an idle timer for RfWebUI, see CTP Simon Gottschlag RfWebUI Idle Timeout.” is not working anymore. Any idea where to find this information now, or where to put that java script code posted?
Try https://xenit.se/tech-blog/rfwebui-idle-timeout/
What do you mean by this – UDP 443 allowed to Citrix Gateway Virtual Server
What is the source address?
All Internet. It’s for EDT (Adaptive Transport).
So the source being Any to dest – netscaler?
So does HDX Adaptive Transport need it? I’ve blocked it and UDP audio works internally. I’m doing these pieces separately. Session is TCP but Audio is UDP, so shouldn’t need to enable HDX Transport should I?
UDP Audio is separate from Adaptive Transport but it uses the same port number (UDP 443) and protocol (DTLS).
Found something strange. I enabled udp works fine, but only works if i go to the gateway via the website. I also get a microphone and webcam popup.
If I go gateway via the native workspace and have it configured, i don’t see UDP. I have added
EnableRtpAudio=true
EnableUDPThroughGateway=true
RtpAudioLowestPort=16500
RtpAudioHighestPort=16509
Hello Sir,
I’ve upgraded my MPX 5550 device to NS13.0 67.39. After the upgrade, my EPA scan is working properly as it was working in earlier version NS10.50 70.12. But After Citrix Gateway login, I’m not reaching to Storefront site from where I was launching my published desktop. Process is stuck at logon/logonpoint/index.html page saying page cannot be displayed. Urgent help required.
Thank you very much in advance.
I am looking to create different EPA failure pages that will let you determine which EPA you failed instead of the single EPA failure page under portal themes. I am using Nfactor for my EPA policies. Any way to do this?
Carl, I am trying to integrate DUO MFA and want to have 2 VIPS running in parallel (https://duo.com/docs/citrix-netscaler-alt). It has a step to modify the login form (gateway_login_form_view.js) but this affects both vips. Is there a way to apply the DUO customization for 1 vip on the login form and the other still remain with prior setup (say rsa). Thanks and great work!
Can you bind the rewrite policies to the Gateway vServer instead of binding them globally?
Hi, this is a question that also applies to our environment. How can I let one page point to another gateway_login_form_view.js in another directory? Or how can I customize a Portal to point to another (customized) ns_gui directory?
I seem to recall being able to do this using rewrites based on an expression. Here’s the closest I’ve found so far. https://netscalerrocks.com/netscaler/citrix-gw-one-gw-multiple-customers-with-different-logos/
Dear Carl,
Thanks for your speedy answer! It’s an honor. In the mean time I my search was still going on and I found that I used bad code in the custom gateway_login_form_view.js. After fixing this, the rewrite worked like a charm.
This helped: https://discussions.citrix.com/topic/372803-rewrite-variable-enter_passwd2-in-gateway_login_form_viewjs/
Hello – We have edited the RfWebUI theme to change to our branding. However, depending on the connecting device Windows/MAC/iPAd/Android tablet that is used our logo is either scaled perfect, gets stretched or squashes up depending on the device’s resolution.
Is there a way for the gateway to identify screen resolution size and adjust to all user’s get the same experience?
Thanks
Hi Carl,
Quick question, do you know if the password fields on the Netscaler Plugin can be customised. When you enable 2 Factor it simple says Secondary Password.
Thanks,
Did you configure a Portal Theme to change the Logon fields labels?
Hi Carl,
Customer is looking for domain field in the Gateway Login page. I have tried applying the rewrite policy mentioned in a citrix article but no luck. Have you configured it any where?.
I have done it multiple times without issue. Note: there are 12.1 builds that don’t process Gateway Responder/Rewrite correctly.
The article is https://support.citrix.com/article/CTX203873
Note: nFactor (AAA) has a different procedure for adding the domain list.
Hi Carl,
Its a very urgent situation, we have upgraded our NS MPX5550 to 12.1 and we had a custom theme for admin GUI login for NS. Now the custom file is not getting supported. The default admin_Ui folder is getting supported. Please provide ur inputs if u have seen this problem .
Note: When we replace our custom admin_ui folder taken as backup we are getting the logon page and we are able to enter reds. but after clicking login we are getting error as “This page is not working”
Please reply its urgent
Thanks in advance
Azifkhan.N
Did you recreate the theme after upgrading? The admin files from the older version won’t work in the newer version.
Hi Carl,
Thank you so much for your immediate reply. We didn’t recreate admin_ui , we got default admin_ui from citrix and running the environment currently. one last question will there be any problem or changes in the production on using default admin_ui. As we have custom theme for user page and that var\vpn is working fine.
Thanks,
Azifkhan.N
Is modification of Gateway or AAA logon page your only goal? If so, then you don’t need to modify admin_ui. The new method is to create a Portal Theme, modify the Portal Theme under /var/netscaler/logon/themes and then bind the theme to your Gateway or AAA vServer. For the old method, identify the specific files you are changing and put them in /var/vpn/vpn. https://support.citrix.com/article/CTX123780
Thank you so much, will let you know once the other node upgrade is completed. Thank you so much for your guidance doing a great job.
Hi Carl,
We have a situation, not able to import the custom theme file. Please provide steps to import the custom theme file,
Note: We have custom theme file already in place, as netscaler vendor is not supporting custom theme , they are not ready to help us.
Thanks,
Azifkhan
HI Carl
as always great site and amazing tips. Thank you for the great work your a Machine!
I hope you can help us out with this one :
I have a Netscaler 12.1 Question around customization and its getting my head in …
I have tried to add an external URL to a Citrix NetScaler Gateway landing page for users to access the https://passwordreset.microsoftonline.com to reset their passwords if needed . This turns out to be a bit of a hassle and dont seem to work.
I have been following the steps from the following articles with no luck
https://support.citrix.com/article/CTX202444
Addedd the following lines to the gateway_login_form_view.js file :
1) Add the following lines inside the function “rdx.gateway_login_form_view.prototype.make_view”. This line can be added below the code where the variable “enter_passwd2” is defined:
var link_container= $(“”).addClass(“eula_check”);
var ext_link= $(‘‘).attr({“class”:”plain form_text”,”style”:”padding-left: 5px;”}).html(“Azure Password Reset”);
link_container.append(ext_link);
2) Paste the following line below – form.append(eula_section,field_login);
form.append(link_container);
Note: If you do not use the EULA function, then paste this line below – form.append(field_login).
in the exact location as per the Citrix Article , with no luck
Any advice would be appreciated
Thanks
What theme do you have configured? The instructions for RfWebUI are different than the other themes.
Hello Carl,
I have the same setting like yours for device authentication but I get the message “This Client machine does not match the required security”.
Any help is greatly appreciated.
Thank you.
Hi Carl,
I updated the Netscaler to version 12.1.50.31.
The reason for this was because I have to check device certificats on Windows and Macs etc. with EPA.
A conspicuousness is that the public URL of the Netscaler Access Gateway usually after half an hour was no longer achievable. After a reboot of the Netscaler VPX it worked again.
But the greater problem is that the EPA check failed everytime. The Netscaler setup is identical to yours in the in the instructions above.
Do you have some ideas where the problem may be?
The EPA Log is here:
=========================
nsepa.exe
Date: 2019-01-30
Time: 10:32:31
Version: 12.1.50.31
=========================
10:32:31.280 | DEBUG | Browser handle is 00010966
10:32:31.280 | DEBUG | isPostEPA is set to 0 in UI
10:32:33.624 | DEBUG | EPA dialog is ready. Window ID=2098846
10:32:33.624 | DEBUG | No setting for language exists. We will use system language
10:32:33.624 | DEBUG | syspath=C:\Users\user1\AppData\Local
10:32:33.639 | DEBUG | ns_isOsWin10 : OS is Windows 10 or higher
10:32:33.639 | ERROR | getCurrentConIndex | 1397 | current connection value is incorrect https://citrix.example.com:8443
10:32:33.639 | DEBUG | It is pre-Auth EPA and user hasn’t marked this as trusted connection. We will show trust dialog
10:32:35.108 | DEBUG | User trusts the vserver
10:32:35.124 | DEBUG | created a new thread for EPA
——————————————————————————————
Phase: Pre Authentication EPA
——————————————————————————————
10:32:35.124 | EVENT | Initiating EPA SCAN
10:32:35.124 | DEBUG | vip=255.255.255.254
10:32:35.124 | DEBUG | ns_enablessl=1 basevport=0xfb20
10:32:35.124 | DEBUG | Input params: cookie length 32 location https://citrix.example.com:8443/epa/epa.html/ debug DEBUG vip citrix.example.com version 12.1.50.31
10:32:35.124 | EVENT | Making GET request to https://citrix.example.com:8443epatype
10:32:35.139 | VERBOSE | []
10:32:35.577 | DEBUG | downloaded total 22 bytes
10:32:35.577 | DEBUG | ns_HTTPrequest return value is: 22
10:32:35.577 | EVENT | Device Cert check Absent and EPA is Present
10:32:35.577 | EVENT | Making GET request to https://citrix.example.com:8443epaq
10:32:35.577 | VERBOSE | []
10:32:35.608 | DEBUG | downloaded total 331 bytes
10:32:35.608 | DEBUG | ns_HTTPrequest return value is: 331
10:32:35.608 | DEBUG | Received headers size 34816
10:32:35.608 | DEBUG | Received headers size 100
10:32:35.608 | DEBUG | csec_opts header is present
10:32:35.608 | DEBUG | Received headers size 7
10:32:35.608 | DEBUG | Server side CSEC encryption enabled
10:32:35.608 | DEBUG | Received headers size 261
10:32:35.608 | DEBUG | Received headers size 261
10:32:35.608 | DEBUG | Received headers size 261
10:32:35.624 | DEBUG | A cryptographic context key container has been acquired.
10:32:35.624 | DEBUG | An empty hash object has been created.
10:32:35.624 | DEBUG | Contents have been written to the BLOB.
10:32:35.624 | DEBUG | Key generated successfully
10:32:35.624 | DEBUG | CSEC debugging is not allowed
10:32:35.624 | DEBUG | num_mallocPolicyBuffer=1 print internal structure:
10:32:35.655 | ERROR | getCurrentConIndex | 1397 | current connection value is incorrect https://citrix.example.com:8443
10:32:35.655 | DEBUG | No pref. for certificate exits for this connection
10:32:35.655 | DEBUG | Didn’t find certificate based on pref. or pref. wasn’t set
10:32:35.655 | ERROR | getCertFromStore | 207 | Exited loop with error code -2146885628 which is Success
10:32:35.655 | EVENT | Using the only certificate present in the store
10:32:35.655 | DEBUG | CertCloseStore returned 0
10:32:35.749 | ERROR | signHelper | 975 | Getting signed BLOB size failed with error : -2146893802
10:32:35.749 | VERBOSE | Signing failed, try with service
10:32:35.749 | DEBUG | We will call newer signature function.
10:32:35.749 | EVENT | AG plugin and EPA plugin version matched. Trying with service
10:32:35.796 | DEBUG | service_getSignature success
10:32:35.796 | VERBOSE | Signing with service Succeeded
10:32:35.796 | EVENT | ns_EvalPolicy returns 3001
10:32:35.796 | DEBUG | ns_free_dependspol:num_mallocPolicyBuffer=0
10:32:35.796 | DEBUG | Memory has been allocated for the buffer.
10:32:35.796 | DEBUG | Memory has been allocated for the buffer.
10:32:35.796 | EVENT | Making POST request to https://citrix.example.com:8443epas
10:32:35.796 | VERBOSE | []
10:32:35.858 | DEBUG | downloaded total 271 bytes
10:32:35.858 | DEBUG | ns_HTTPrequest return value is: 271
10:32:35.858 | DEBUG | Received headers size 80
10:32:35.858 | ERROR | ns_parse_epareport | 1434 | Login failed due to EPA Scan
10:32:35.858 | DEBUG | No EPA scan failure. We won’t add header for error messages
10:32:35.858 | DEBUG | ns_start_epa returning Fall-ID : 98fc1
10:32:35.858 | DEBUG | num_mallocPolicyBuffer=0
10:32:35.858 | DEBUG | releasing buffers
10:32:35.858 | DEBUG | ns_StopSSL called
10:32:35.858 | DEBUG | ns_UnloadSecurityLibrary done
10:32:35.858 | EVENT | EPA has successfully completed
10:32:35.858 | DEBUG | EPA complete. stop showing progressbar
10:32:35.874 | ERROR | ns_free_crypto | 303 | CryptDestroyHash failed with error: 57
10:32:35.874 | EVENT | EPA check finished : EPA scans checks done successfully
10:32:35.952 | DEBUG | ShowEPADialog returned 1
Many Greetings
Matthias
Hello Matthias,
We seem to be having similar issues. Our errors are the same above. Noticed :
ns_parse_epareport | 1434 | Login failed due to EPA Scan
14:11:33.803 | DEBUG | No EPA scan failure. We won’t add header for error messages
14:11:33.803 | DEBUG | ns_start_epa returning Case ID : eed6b
14:11:33.803 | DEBUG | num_mallocPolicyBuffer=0
14:11:33.803 | ERROR | ns_free_crypto | 303 | CryptDestroyHash failed with error: 57
14:11:33.803 | EVENT | EPA check finished : EPA scans checks done successfully
14:11:33.803 | EVENT | Citrix Endpoint Analysis failed: Case ID : eed6b.failed with error: 57
We are on EPA version 12.1.52.15
EPA is failing when trying to initiate the VPN connection. We only have to checks to validate part of domain and has our AV installed. After 5 minutes at idle we can finally pass the EPA check but the first 5 minutes or so we continue to get ACCESS DENIED running the EPA. Thoughts?
Did you guys ever resolve this? Getting this error for a device cert EPA scan.
Hello Carl,
Thanks as always for your material.
I am creating a custom portal theme on NS VPX 12.1.49.23, and I have two questions based on RFWebUI:
1. I just want a white background. I notice there is an option for default and edit in the background selection box. Is there any way to just have a white background, without uploading an image. It seems expensive to load an image when the browser could render this. Am I missing some other config?
2. I tried uploading an image (of a white background) and it just spins endlessly, it’s a jpg. Have you seen this before? Can I just WinSCP my image to the NS and then use some command lines to assign the background image file to the theme I’m building?
Thanks in advance for any help you can offer.
The theme files are under /var/netscaler/logon/themes/MyTheme. I’m guessing you can edit the .css file under there to hide the background.
Yes if course! I really should have thought of that, sorry.
Thanks again.
Said.
Hi Carl ,
Any idea why i see at my firewall logs , the opposite communication from UDP 16500-16509 from Citrix SNIP to the VDAs ? The Snip is behind firewall and i see logs that from VDAs to SNIP at 16500-16509 . Its like the VDAs are trying to reply ..with UDP !?!
Best Regards
Prodromos
Is UDP Audio enabled?
Hi Carl ,
Yes its enabled . But i would expect only from Netscaler –> VDA UDP 16500-16509 .
I see the same from VDA 3*** port to SNIP UDP 16500-16509, did you ever find out the reason behind this?
Hi Carl,
I am planning to upgrade Citrix Netscaler (MPX8200) from 11.0 build 66 to 12.0 build 58. I have Enterprise license.
When I tried to download from Citrix it gave me too many options like :
NetScaler ADC
Netscaler App Firewall
Netscaler Gateway
Netscaler MAS
NetScaler SD-WAN
I am confused how can i verify which one is applicable for my Netscaler.
Any help would be highly appreciated.
ADC and Gateway are identical. Pick one of those.
Thanks for your quick reply.
Is there any way I could verify either from GUI or Putty to netscaler through some command
SD-WAN and MAS are completely different products.
NetScaler MPX = ADC.
NetScaler Gateway is just a special license for ADC.
Great I did upgrade from Netscaler 11.0 build 70.16 to 12.0 build 58.15 without any issue.
Thanks for your help in understanding firmware download options.
The reason I upgraded was duplicate radius authentication bug in 11.0 but unfortunately i could see same behavior in 12.0. If you can help me in this help would be much appreciated.
I have Radius policy configured on Netscaler and have pointed to Microsoft NPS server. When users open website (let say user has configured MFA to get phone calls) sometime website keep spinning and users get calls 3 times in the interval of 120 sec which i have set time out on Netscaler.
Every time users receive the call and press # but nothing happens and website keep spinning.
Any suggestion ?
Citrix support captured the logs and ask me to upgrade they did see duplicate request going out from Netscaler but even after upgrade its not working.
Are the RADIUS responses not making it back to NetScaler? Are you load balancing RADIUS? If not, is it perhaps sending the RADIUS request using a SNIP interface but the source IP is NSIP and the RADIUS server doesn’t know how to route the packet back to the NSIP? If you load balance RADIUS then it uses SNIP instead of NSIP.
Are the RADIUS responses not making it back to NetScaler? Are you load balancing RADIUS? If not, is it perhaps sending the RADIUS request using a SNIP interface but the source IP is NSIP and the RADIUS server doesn’t know how to route the packet back to the NSIP? If you load balance RADIUS then it uses SNIP instead of NSIP.
Is it possible to change the Netscaler Admin GUI color ?
The intention is to easily distinguish difference between LAB, Production, DR site Netscaler.
When i login to lab adim console must stay green, on the other hand when i login to production admin GUI color must be red.
Thank you.
Curious if anyone has been able to customize the “Enterprise Websites” or “Personal Website” sections (Web and SAAS Apps and Personal Bookmarks). I want them to appear but they take up a lot of real estate on the screen and I’m not a fan of the background colours, etc.
In Unified gateway, there’s an “E-Mail Home” icon that shows up, even when we don’t fill in that field. Can we remove that icon entirely?
Currently when we login to Unified Gateway, it defaults to icons verses Categories – is there a way to force default to the category view?
Yes, on the netscaler under /var/netscaler/logon/themes/ edit the scripts.js file
//This will maintain landing on category tab
CTXS.Extensions.onViewChange = function (viewName) {
if (viewName == ‘store’) {
window.setTimeout(function () {
CTXS.ExtensionAPI.navigateToFolder(‘\\’);
}, 0);
}
};
See https://support.citrix.com/article/CTX217238
Hi Carl,
Thanks for the great articles you’re enriching the Citrix User Communuity with.
I am fresh to Citrix and these articles help to speed up the learning side of things a lot..
I could use some help with the VPN side of things if you’d be so nice to provide your insight to the issue.
Currently we are hitting a problem with VPN & NLA (happens on Win7 and Win10).
Seems Citrix VPN Client is having problems with the Multi Firewall Profiles feature (e.g. WLAN Nic -> Public profile and Citrix-/VPN-NIC -> Domain profile).
At the same time we have set Block for Inbound & Outbound traffic for the Private-/Public-Profile, unless it is white-listed through a firewall rule. The Firewall is turned of completly for the Domain Profile.
In this constellation, after we establish the VPN connection, there no access possible to Intranet (NW-Shares, internal Collab-Sites) and to the Internet (www.bing.com, http://www.google.ch, etc..) possible. Not even a ping…
Seems the Windows Filtering Plattfrom (which accordig to MS acts even before the Firewall) seems to block outgoing packets, because it consideres them to be trying crossing Profiles (from Public -> Domain or Domain -> Public) and blocks them. This is according to MS due to the Strong-Host-Model scheme they have to the Multi-Profile feature.
The reason seems to be that Citrix (also Cisco??) is using 172.0.0.1 or 192.0.0.1 as Default-Gateway, DNS and DHCP Servers when internaly the 172.23.x.x., 172.26.x.x are used as subnets for the internal-network setup..
According to Citrix this usage of 172.0.0.1 is intrinsic (e.g. embedded into the source code) and cannot be modified.
Seems odd that we couldn^t change/modify this 172.0.0.1 IP to something that is “closer” to the final VPN-Client IP, e.g. we would like to use 172.23.x.1 (first IP of the VPN subnet) as the default gateway IP and thus hopefull avoding the whole Profile_Crossing trap we seem to be running into..
Any chance you’d have encountered something similar or would have an idea how we could change this 172.0.0.1 IP to something we define as a more “apropiate” IP-Adress.
Just to point it out: Our Citrix TMR stated that latley more customers did run into this and they “simply” dectivated the Firewall on the Cient-PC’s to solve the issue. This seems a bit strange to open up the client’s security to have VPN working properly…
-snip-
13:43:41.6653816 [Microsoft-Windows-Windows Firewall With Advanced Security/Firewall ] Network profile changed on an interface.
Adapter GUID: {5617a1c7-4d37-4670-bca9-1f66bfe0035f}
Adapter Name: ethernet_7
Old Profile: Public
New Profile: Domain
Next you will see the drop happening:
13:43:41.7837785 [Microsoft-Windows-WFP/Analytic] WFP: Packet Dropped – Filter Run-Time ID: 0x775CF, Layer Run-Time ID: 0x2C ?1601?-?01?-?01T00:00:00.000000000Z, 16, 172.23.244.130:3148, 16, 172.0.0.1:9748, 0, \device\harddiskvolume2\program files\citrix\secure access client\nsload.exe, S-1-5-21-1266304161-2867343829-1920029268-41660, 0xB, 1, 3, Inbound, false
A closer look reveals the reason for it:
timeStamp>2018-02-23T12:43:41.787Z
FWPM_NET_EVENT_FLAG_IP_PROTOCOL_SET
FWPM_NET_EVENT_FLAG_LOCAL_ADDR_SET
FWPM_NET_EVENT_FLAG_REMOTE_ADDR_SET
FWPM_NET_EVENT_FLAG_LOCAL_PORT_SET
FWPM_NET_EVENT_FLAG_REMOTE_PORT_SET
FWPM_NET_EVENT_FLAG_APP_ID_SET
FWPM_NET_EVENT_FLAG_USER_ID_SET
FWPM_NET_EVENT_FLAG_IP_VERSION_SET
FWPM_NET_EVENT_FLAG_REAUTH_REASON_SET
FWP_IP_VERSION_V4
17
172.23.244.130
172.0.0.1
3148
9748
0
5c006400650076006900630065005c0068006100720064006400690073006b0076006f006c0075006d00650032005c00700072006f006700720061006d002000660069006c00650073005c006300690074007200690078005c007300650063007500720065002000610063006300650073007300200063006c00690065006e0074005c006e0073006c006f00610064002e006500780065000000
\.d.e.v.i.c.e.\.h.a.r.d.d.i.s.k.v.o.l.u.m.e.2.\.p.r.o.g.r.a.m. .f.i.l.e.s.\.c.i.t.r.i.x.\.s.e.c.u.r.e. .a.c.c.e.s.s. .c.l.i.e.n.t.\.n.s.l.o.a.d…e.x.e…
S-1-5-21-1266304161-2867343829-1920029268-41660
FWPM_NET_EVENT_TYPE_CLASSIFY_DROP
488911
44
8 FWP_CONDITION_REAUTHORIZE_REASON_PROFILE_CROSSING
1 NlincPublic
3 NlincDomainAuthenticated
The filter ID 488911 points to the build-in filter previously initialized:
2018-02-23T12:43:41.664Z
FWPM_CHANGE_ADD
{c024ce67-6957-45f8-bbe0-d690420dcd58}
488911
{c024ce67-6957-45f8-bbe0-d690420dcd58}
Query User
Prompt the User for a decision corresponding this Inbound Traffic
{decc16ca-3f33-4346-be1e-8fb4ae0f3d62}
a00e000000000000
……..
FWPM_LAYER_ALE_AUTH_RECV_ACCEPT_V4
{b3cdd441-af90-41ba-a745-7c6008ff2301}
FWP_UINT8
8
FWPM_CONDITION_ORIGINAL_PROFILE_ID
FWP_MATCH_EQUAL
FWP_UINT32
1
FWP_ACTION_BLOCK
0
488911
FWP_UINT64
9223372036854776256
-snip-
Hope I was somewhat able to convey the problem we are having.
Any insight, tipps & tricks are appreciated to help solving this issue..
Thanks and best regards,
ErolU
Hi Carl,
Good Article, would you also share a customizations to prompt specific Citrix Receiver version from Netscaler authentication page.
Are you trying to block older Receiver? Or are you trying to tell the user what version of Receiver is installed?
StoreFront has an option to offer Receiver upgrades.
I’m trying to force users to prompt Receiver 4.3.100 who are using Windows 10 operating system on Netscaler Authentication page.
Under Public DNS SRV Records:
We could not add _discoverReceiver.domain.com in SAN portion of SSL. It took without ” _ ” though.
That appears to be a typo on my part. Should be fixed now. Thanks for pointing it out.
Great article, thank you. Would you happen to know where the background image for the Storefront logout is? It looks like /netscaler/ns_gui/vpn/media/X1-bg-img.jpg, but I customized that one and for some reason I keep getting the old image after logging out of Storefront. I already tried clearing my browser cache.
Isn’t it /Citrix/StoreWeb/receiver/images/common/ReceiverFullScreenBackground_46E559C0E6B5A27B.jpg on the StoreFront server?
Bingo! Thank you so much, sir. I’m a huge fan of all your work.
We found a few issues with RfWebUI (running NetScaler 12.0.53.13). One being that the WfWebUI portal theme loaded inconsistently across many devices (desktop and phone). We had to remove the cache policies that are automatically added when you create the NSGW virtual server (_cacheTCVPNStaticObjects, etc). Looks like the theme flips out when it tries to perform 302 or 304 requests for the web resources. I found a known issue Citrix article that kind of alluded to that, but didn’t mention caching. This was with Enterprise licensing too, which means I couldn’t change the policies (as I’m not licensed), but I could unlink them. Also, we’ve found the RfWebUI theme loads really poorly over high latency (e.g, 300 ms+) connections. Way worse than the default themes. Even X1 is a bit better, but no mobile support. I also assume this is related to all the AJAX requests the theme makes. Haven’t got a solution for that yet. The theme definitely looks better, but also has pretty serious flaws.
Hi Carl,
great articel as usual – especially when it comes to Portal theme customization!
Cheers, Jochen.
Have you been able to get the idle timeout to work when using the rfwebui?