This page contains generic instructions for all SSL Virtual Servers including: Load Balancing, NetScaler Gateway, and Content Switching.
Navigation
- Cipher Group
- Default SSL Profile
- SSL vServer Configuration – Bind Cert, Ciphers, ECC, and STS
- SSL Tests
- SSL Redirect – Down vServer Method
- SSL Redirect – Responder Method
💡 = Recently Updated
Cipher Group
References:
- Citrix Blogs – Scoring an A+ at SSLlabs.com with Citrix NetScaler – 2016 update 💡
- CJHarms Perfect Forward Secrecy and NetScaler MPX Revisited
- Anton van Pelt Make your NetScaler SSL VIPs more secure (Updated)
- Citrix CTX201710 Cipher/Protocol Support Matrix of NetScaler Appliances:
- VPX 11.0 build 64 and older support fewer ciphers than MPX. This was corrected in 11.0 build 65.
- Ryan Butler has a PowerShell script at Github that can automate NetScaler SSL configuration to get an A+. 💡
- The easiest way to create a cipher group is from the CLI. See Citrix Blogs Scoring an A+ at SSLlabs.com with Citrix NetScaler – 2016 update for cipher group CLI commands.
- Go to Traffic Management > SSL > Cipher Groups.
- On the right, click Add.
- Name it Modern or similar.
- In the middle, click Add.
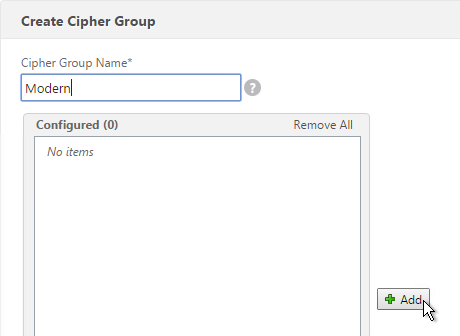
- Use the search box to find a particular cipher.
- Check the box next to one of the results and click the arrow to move it to the right. See Citrix Blogs Scoring an A+ at SSLlabs.com with Citrix NetScaler – 2016 update for recommended ciphers. The recommended ciphers vary based on the hardware platform and support for older clients.
- Click Create when done.
Default SSL Profile
In NetScaler 11.0 build 64 and newer, SSL Profiles are much more functional. You can use SSL Profiles to disable SSLv3, bind ciphers, and bind ECC curves.
Note: the default SSL Profile affects all SSL Virtual Servers unless you create additional SSL Profiles and bind the additional SSL Profiles to individual SSL Virtual Servers.
Citrix CTX201710 Cipher/Protocol Support Matrix of NetScaler Appliances – VPX 11.0 build 64 and older supports fewer ciphers than MPX. This was corrected in 11.0 build 65.
NetScaler 11.0 build 65 adds TLS 1.2 for back-end connections from VPX appliances. However, it does not appear to be possible to enable TLS 1.2 on SSL Profiles on VPX. If you don’t enable the default SSL profiles then you can enable TLS 1.2 on each Service Group or Service. If you are using VPX, don’t enable Default SSL profile as detailed in this section. 💡
NetScaler 11.0 build 64 and older does not do a proper handshake with TLS 1.2 IIS servers. To work around this problem, disable TLS 1.2 on the load balancing services as detailed at CTX205578 Back-End Connection on TLS 1.1/1.2 from NetScaler to IIS Servers Break. Or upgrade to 11.0 build 65.
Also see CTX205576 NetScaler to Back-End SSL Handshake Failure on Disabling SSL 3.0 on Back-End (Physical) Servers. These articles describe both SSL services and SSL_BRIDGE services.
- Go to Traffic Management > SSL.
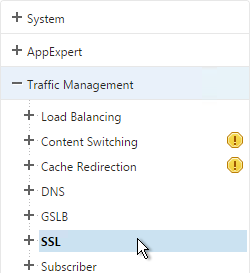
- On the right, in the right column, click Change advanced SSL settings.
- Near the bottom, check the box next to Enable Default Profile. Note: this will change SSL settings on all SSL Virtual Servers to match the default SSL profile. You might want to do this during a maintenance window. Click OK when done.
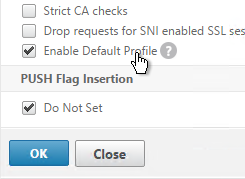
- If you go back into Advanced SSL Settings, notice that the Default Profile is enabled and there’s no way to disable it.
- To change the default SSL profile, on the left, go to System > Profiles.
- On the right, switch to the SSL Profile tab.
- Highlight the frontend or backend default profile and click Edit. Note: this is the same place where you can create more SSL profiles.
- Notice that SSLv3 is disabled by default.
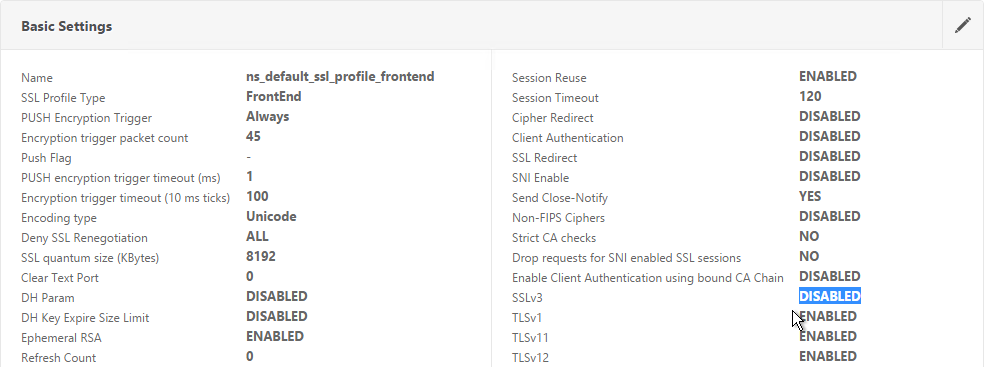
- If you do any SSL Offload (SSL on the client side, HTTP on the server side) then you’ll need to edit the Basic Settings section and enable SSL Redirect. Or you can create a new SSL Profile with this option enabled. It’s near the bottom of the section. With this option enabled, any 301/302 redirects from the server with HTTP locations are rewritten to HTTPS locations. You might need this option for StoreFront load balancing if doing SSL Offload.
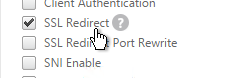
- It’s currently not possible to bind user-defined cipher groups using the GUI but you can easily do this using the CLI. First unbind the DEFAULT cipher group and then bind the Modern cipher group.
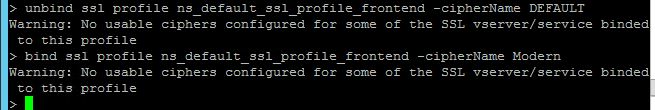
unbind ssl profile ns_default_ssl_profile_frontend -cipherName DEFAULT bind ssl profile ns_default_ssl_profile_frontend -cipherName Modern
- If you edit one of your SSL Virtual Servers, there’s an SSL Profile section indicating that the default profile is being used. You can change the binding to a different SSL Profile.
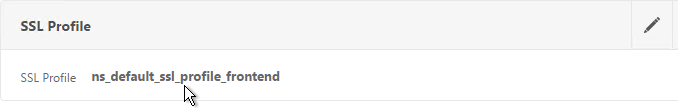
Bind Certificate, Bind Cipher Group, Disable SSLv3, Enable STS
NetScaler 11.0 build 64 and older do not do a proper handshake with TLS 1.2 IIS servers. To work around this problem, disable TLS 1.2 on the load balancing services as detailed at CTX205578 Back-End Connection on TLS 1.1/1.2 from NetScaler to IIS Servers Break. Also see CTX205576 NetScaler to Back-End SSL Handshake Failure on Disabling SSL 3.0 on Back-End (Physical) Servers. These articles describe both SSL services and SSL_BRIDGE services.
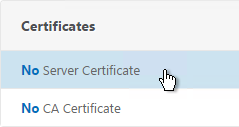
- When creating the SSL Virtual Server, on the left, in the Certificates section, click where it says No Server Certificate.
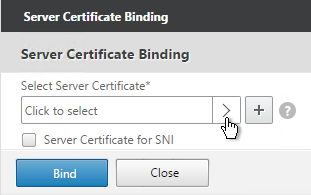
- Click where it says Click to select.
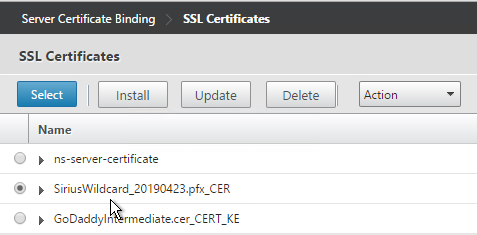
- Select a certificate and click Select.
- Click Bind.
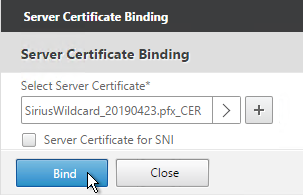
bind ssl vserver MyvServer -certkeyName MyCert
- If the SSL Parameters section isn’t added, on the right, in the Advanced Settings column, click SSL Parameters.
- On the left, in the SSL Parameters section, click the pencil icon.
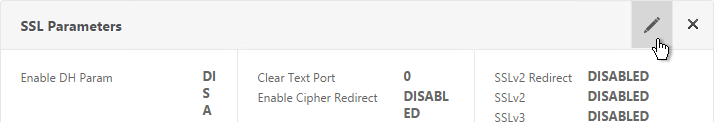
- Uncheck the box next to SSLv3. This removes a security vulnerability. Make sure TLSv11 and TLSv12 are enabled. Click OK.
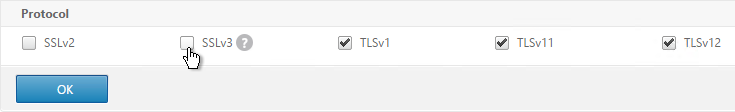
set ssl vserver MyvServer -ssl3 DISABLED -tls11 ENABLED -tls12 ENABLED
- On the right, in the Advanced Settings column, click SSL Ciphers.
- On the left, in the SSL Ciphers section, select the previously created Modern Cipher Group and click OK.
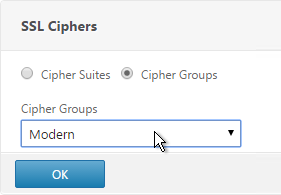
unbind ssl vserver MyvServer -cipherName ALL bind ssl vserver MyvServer -cipherName Modern
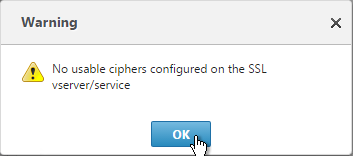
- If you see a warning about No usable ciphers, click OK and ignore it.
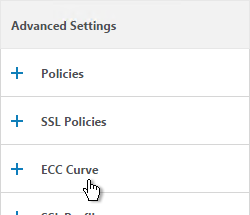
- SSL Virtual Servers created on newer versions of NetScaler will automatically have ECC Curves bound to them. However, if this appliance was upgraded from an older version then the ECC Curves might not be bound. On the right, in the Advanced Settings section, click ECC Curve.
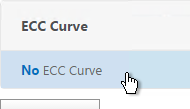
- On the left, in the ECC Curve section, click where it says No ECC Curve.
- Click to select.
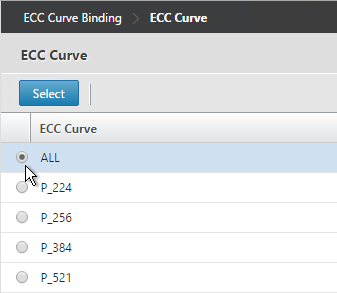
- Choose ALL and click Select.
bind ssl vserver MyvServer -eccCurveName ALL
- Click Bind.
- Consider enabling Strict Transport Security by creating a rewrite policy and binding it to this SSL Virtual Server. See Anton van Pelt Make your NetScaler SSL VIPs more secure (Updated). Also see CTX205221 How Do I Do HSTS on NetScaler?
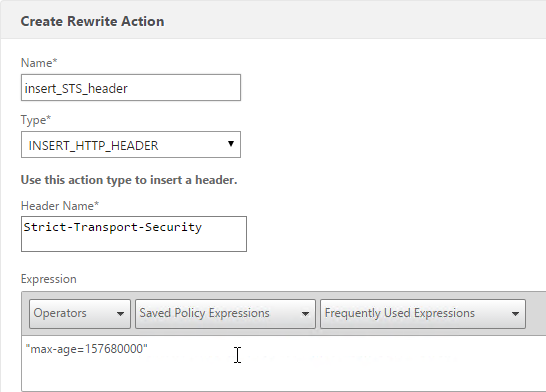
enable ns feature rewrite add rewrite action insert_STS_header insert_http_header Strict-Transport-Security "\"max-age=157680000\"" add rewrite policy insert_STS_header true insert_STS_header bind lb vserver MyvServer -policyName insert_STS_header -priority 100 -gotoPriorityExpression END -type RESPONSE
SSL Tests
After you’ve created an SSL Virtual Server, run the following tests:
- Go to https://www.digicert.com/help/ to verify the certificate chain.
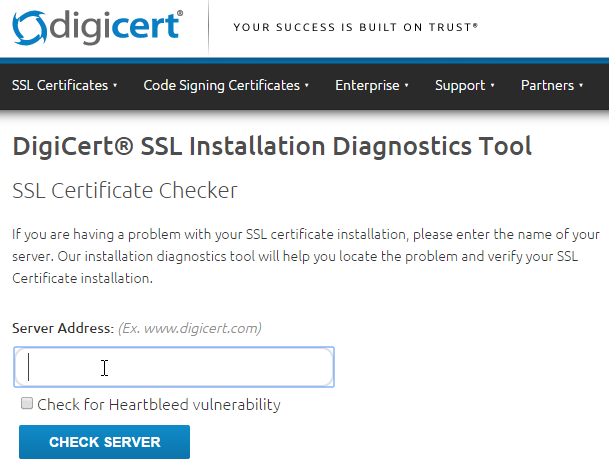
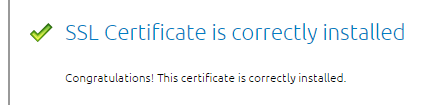
- Go to https://www.ssllabs.com/ssltest/ and check the security settings of the website.
SSL Redirect – Down vServer Method
If you created an SSL Virtual Server that only listens on SSL 443, then users must enter https:// when navigating to the website. To make it easier for the users, create another load balancing Virtual Server on the same VIP but listens on HTTP 80 and then redirects the user’s browser to reconnect on SSL 443.
The Down Virtual Server Method is easy but the Redirect Virtual Server must be down in order for the redirect to take effect. Another option is to use Responder policies to perform the redirect.
- On the left, under Traffic Management > Load Balancing, click Virtual Servers.
- On the right, find the SSL Virtual Server you’ve already created, right-click it and click Add. Doing it this way copies some of the data from the already created Virtual Server.
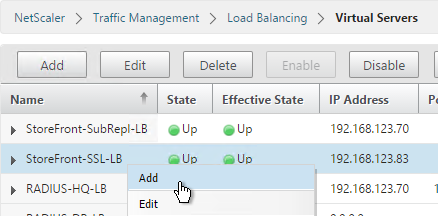
- Change the name to indicate that this new Virtual Server is an SSL Redirect.
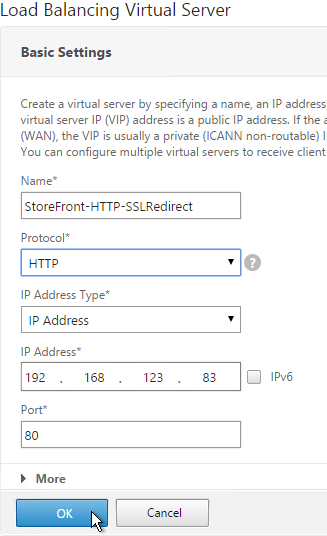
- Change the Protocol to HTTP on Port 80.
- The IP Address should already be filled in. It must match the original SSL Virtual Server. Click OK.
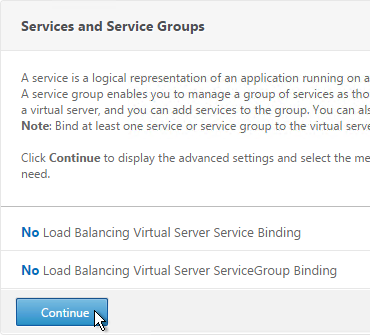
- Don’t select any services. This vServer must intentionally be marked down so the redirect will take effect. Click Continue.
- On the right, in the Advanced Settings column, click Protection.
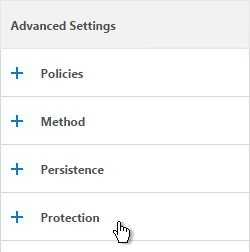
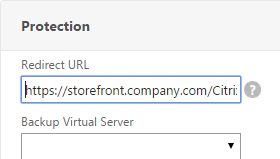
- In the Redirect URL field, enter the full URL including https://. For example: https://storefront.company.com/Citrix/StoreWeb. Click OK.
- Click Done.
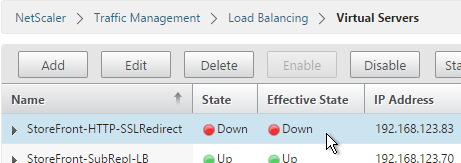
- When you view the SSL redirect Virtual Server in the list, it will have a state of DOWN. That’s OK. The Port 80 Virtual Server must be DOWN for the redirect to work.
SSL Redirect – Responder Method
The Down Virtual Server Method is easy but the Redirect Virtual Server must be down in order for the redirect to take effect. Another option is to use Responder policies to perform the redirect. This method requires the Redirect Virtual Server to be UP.
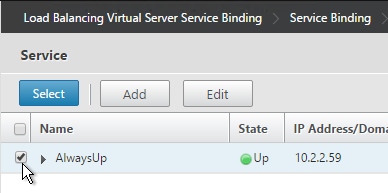
- Create a dummy Load Balancing service. This dummy service can be bound to multiple Redirect Virtual Servers.
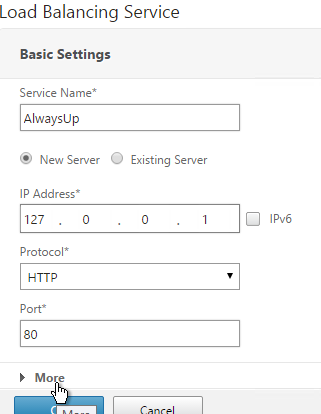
- Name it AlwaysUp or similar.
- Use a loopback IP address (e.g. 127.0.0.1). After the service is created it changes to a NetScaler-owned IP.
- Click the More link.
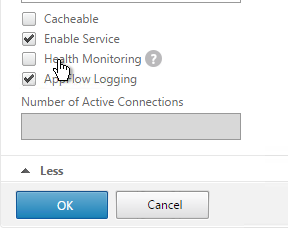
- This dummy service must always be UP so uncheck the box next to Health Monitoring. Click OK and then click Done.
add server 127.0.0.1 127.0.0.1 add service AlwaysUp 127.0.0.1 HTTP 80 -healthMonitor NO
- On the left, expand AppExpert and click Responder.
- If Responder is not enabled, right-click Responder and click Enable Feature.
enable ns feature RESPONDER
- Under Responder, click Actions.
- On the right, click Add.
- Give the action a name.
- Change the Type to Redirect.
- Enter an expression. The following expression can be used by multiple Redirect Virtual Servers. Or you can create a Responder Action with a more specific Target. Click Create.
"https://" + HTTP.REQ.HOSTNAME.HTTP_URL_SAFE + HTTP.REQ.URL.PATH_AND_QUERY.HTTP_URL_SAFE
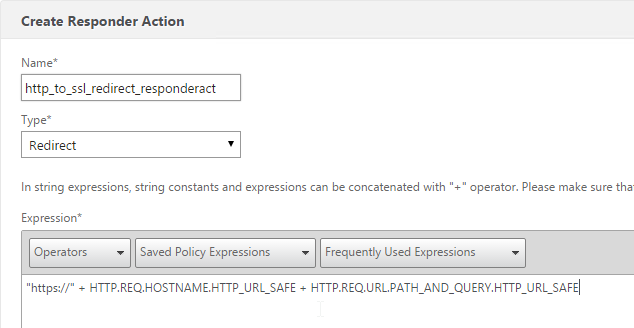
add responder action http_to_ssl_redirect_responderact redirect "\"https://\" + HTTP.REQ.HOSTNAME.HTTP_URL_SAFE + HTTP.REQ.URL.PATH_AND_QUERY.HTTP_URL_SAFE" -responseStatusCode 302
- On the left, under Responder, click Policies.
- On the right, click Add.
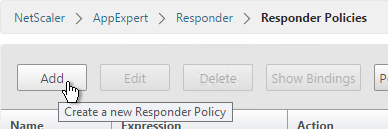
- Give the policy a name.
- Select the previously created Responder action.
- For the expression, enter the following. Then click Create.
HTTP.REQ.IS_VALID
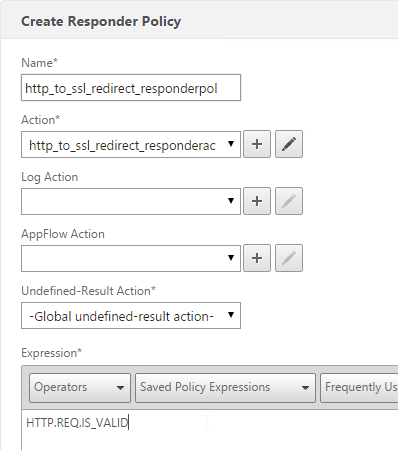
add responder policy http_to_ssl_redirect_responderpol HTTP.REQ.IS_VALID http_to_ssl_redirect_responderact
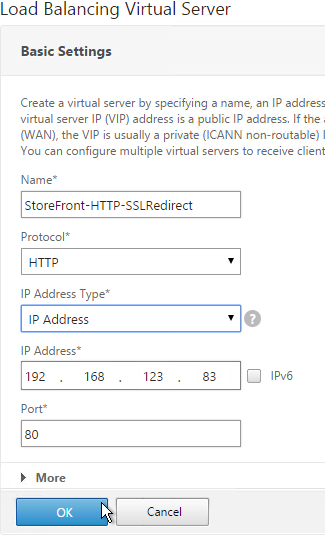
- Create a Load Balancing Virtual Server with Protocol HTTP and Port 80. The VIP should match an existing SSL Virtual Server or NetScaler Gateway Virtual Server.
- Bind the Dummy (AlwaysUp) service, and click OK.
- On the right, in the Advanced Settings column, click Policies.
- Click the plus icon in the top right of the Policies box.

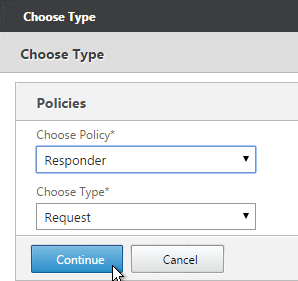
- Select Responder and click Continue.
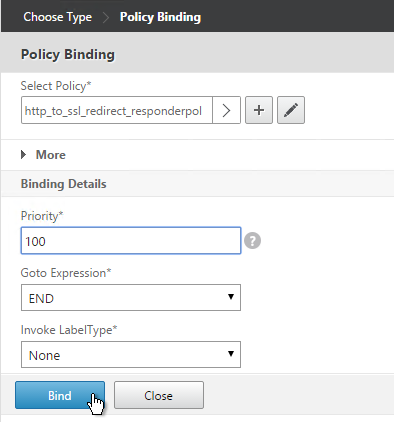
- Select the Redirect Responder policy and click Bind. Then click Done.
add lb vserver MyvServer-HTTP-SSLRedirect HTTP 10.2.2.201 80 bind lb vserver storefront.corp.com-HTTP-SSLRedirect AlwaysUp bind lb vserver storefront.corp.com-HTTP-SSLRedirect -policyName http_to_ssl_redirect_responderpol -priority 100 -gotoPriorityExpression END -type REQUEST
- The primary advantage of this method is that the Redirect Virtual Server is UP.
Beginning in Netscaler ADC 13.0 84.11, setting an HSTS value to max-age=157680000 causes the user to timeout after clicking the Login button in some environments.
Setting max-age to 0 (Default) fixes the issue
Doesn’t max-age=0 mean disable it? I think max-age=157680000 is 5 years. The recommendation from SSL Labs is 1 year. https://blog.qualys.com/vulnerabilities-threat-research/2016/03/28/the-importance-of-a-proper-http-strict-transport-security-implementation-on-your-web-server
Thank you for the link Carl,
Per it’s recommendation i just set it to 31536000 and my gateway works properly. I’m not sure why 157680000 caused it to freeze up.
Hi Carl,
Quick question.
Have already content switching enabled and virtual server assigned (before my time). As will have two domains for Exchange I would need to enable SNI on virtual server. But every time I’m enabling error pops up ‘Option not applicable for this type of service’.
Any advice?
What version and build of NetScaler?
13.058.32
Thanks
What protocol is configured on the Content Switch?
Is SNI enabled in SSL Parameters on the Content Switch?
Simple SSL and just one service on it at the moment.
Actually I cannot enable SNI in sll properties.
When doing that I’m getting this error.
I wonder if it’s a bug in your build. Try upgrading ADC 13.0 to the latest build.
Don’t think so. Tried to create brand new virtual server and was able to tick SNI box in SSL properties then.
If you go to System > Diagnostics > Running Configuration, you can search for the name of the Content Switch and compare its config with the new Content Switch to determine the difference.
Can’t see any big difference.
With new virt server you are enabling SSL properties as literally as first thing. So, there are no issues with enabling SNI.
Would i get same result if there would be just one cert but with SAN urls pointing to 2 domains?
SAN names would eliminate the need for SNI.
Thanks. That is option as well. Thanks.
For this one is SSL. Only service at the moment.
And in parameters I cannot tick box for SNI and hit ok cause after that I’m getting error.
Hi Carl,
I have a strange one, im running NS 13.0 41.28.nc, I think there may be a bug as I can get A+ on SSL Labs, then try again 5 mins later and receive an F because of protocol support saying im vulnerable to zombie poodle and openssl 0-length.
I dont even have the ciphers vulnerable to those exploits enabled on my NS.. have you seen this type of behavior before?
I often get more failures than pass but marks but I’ve followed best practice from start to finish and cant figure out why I pass sometimes and fail on a retest.
SSL Labs will sometimes report your server is vulnerable if you are using a wildcard certificate and it finds a different server in the same domain that is also vulnerable. It should indicate the other server’s IP address.
I just checked SSL Labs and got the same error with any CBC ciphers configured.
Ahh, interesting… I am using a wild card cert which is used for a few different services, although the SSL Report: (xxx.xxx.xxx.xxx) reveals the IP address for external Citrix.
I am however using the two below CBC Ciphers
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384
Do you have a personal opinion this Cipher suite?
I’ve been able to reproduce a pass mark with a “WEAK” warning marked against those ciphers.
Another frustration is that I will sometimes get both poodle/zombie and 0-length and other times only poodle/zombie
Apologies if this is a double up, my first post timed out.
Hello Carl,
If you want to do a SSL Redirect you can bind the Respond Policy simply to a Content Switch with the IP and desired port e.g. 80. Here you dont need a Dummy Service or so some other.
Regards
Dirk
Hi Carls,
We have created the custom Cipher group having Ciphers added as per client request. We applied that Cipher group to Netscaler gateway Internal Virtual server. Also we applied the Cipher group to traffic management > load balancing > Store Front virtual servers. After saving the changes, Citrix stopped working. Although we are able to login in to netscaler gateway., But when clicking on applications, its giving error – Applications not available.
Please suggest on this. Either we need to update ciphers on gateway only not on storefront virtual servers. I am very confused about it. Please help.
What version of StoreFront?
StoreFront is using HTTPS to communicate with the Delivery Controllers?
Or do you have Unified Gateway (Clientless Access Portal) and it can’t communicate with StoreFront?
hello mr carl, I need your help, please, we have a problem in our platform, is that we have some servers with Liferay portal listening for port 80 the ssl is done ofloading in the netscaler with a virtual ip of LB in port 443 appears content mixed, I’ve tried with x-forwarder-, rewrite policies but I have not managed to eliminate the content mixed error, please could you help me.
SSL Offload can be a pain sometimes.
The best solution is to configure the web app to support SSL Offload. I found this for Liferay. See the bottom part. https://community.liferay.com/blogs/-/blogs/nginx-ssl-load-balancing-with-liferay
Thank you carl, regards
Hola, A mi me paso lo mismo , eso se soluciona creando politicas de rewrite, para pasar todo el contenido que haya en http a https.
Hi Carl,
in the process of designing exchange 2016 load balancing. what’s your feeling about adding a secondary LAN interface to a netscaler in the dmz? i’m assuming it’s against best security practices? if we want to load balance internal client connectivity, what’s the best way to do that, internal load balancers? resolve mail traffic to VIP on dmz netscaler? thanks for your time
Ideally, separate load balancers for internal VIPs.
Great article…
Thank you Carl,
Hi,
Ran a check of external URL and “SHA-1 cipher suites were detected”
Any idea what “Ciphers/how to remove” from the Netscaler or should this be done on the backend web Servers?
Did you follow this? https://www.citrix.com/blogs/2016/06/09/scoring-an-a-at-ssllabs-com-with-citrix-netscaler-2016-update/
Hi Carl
Have a GSLB setup with 2 Netscalers NS 11.1 Build 53.11
I have a custom Cipher group, with Ciphers added to this group, now i want to remove a cipher from this group, what will happen to active sessions using this cipher? can this be accomplished without user being disconnected?
Hi Carl,
How are you today ?
We are trying to Loadbalance skype application, we have SSL based VIP and certificate binded to it, But unable to access the Skype URL through VIP, where as able to access through Server. can you let me know where do i need to check or proceed with troubleshooting.
Are you using this guide? https://www.citrix.com/content/dam/citrix/en_us/documents/products-solutions/deploying-skype-for-business-server-2015-with-netscaler.pdf
Carl,
First of all, great site!
I have a question for you, we are using SSL Bridges, but need to somehow redirect the HTTPS URL to another one, I know we can easily redirect with normal SSLs, but not with SSL Bridges.
Is there any way we can create a rewrite/redirect rule for https://company_a.com to https://company_b.com?
Thanks!
You can implement the redirect on the back-end web server. But since NetScaler isn’t decrypting the traffic, there isn’t much it can do.
Thanks for the quick reply, we’ll look into that.
If you’re redirecting https to the same VIP, the certificate would have to match both FQDNs.
Is there a way out to perform the mentioned redirection without getting “This page is not secure” error even if the certificate domain does not match the URL that is going to be redirected.
Port 443 SSL requires the certificates on the vServer to match whatever the user typed in the user’s address bar. You can enable SNI to bind multiple certificates to a single Virtual Server.
Hi Carl,
I am facing issue of SSL handshake between Netscaler to server. Using Netscaler VPX provisioned on SDX 11500 version NS11.0 67.12.nc. The back end servers are HP Non-stop SSL server (Linux) for which doing load balancing. SSL End-to-end encryption configured with HTTPS customized monitor for health check. But I am receiving error for probes Failure – Time out during SSL handshake stage. The issue is intermittent, sometimes its giving pattern found in response and instantly after 3 probes ssl handshake error. Could you please let me know why I am facing this issue.
Thanks in advance.
If you do a network trace on the NetScaler, what do you see?
Firewall between NetScaler and server? Traffic inspection device (e.g. Next Gen Firewall, IPS)?
Do you have multiple SNIPs configured on the same subnet?
Did you figure out cause of your issue ? I’m having same problem.
Hi Carl, How do I configure a vServer to load balance for back end 2 NTP servers in Active Standby mode?
Hi Carl,
any news on the SSL default profile ? I want to bind my own SSL ciphers to my ssl profile to secure my vserver. DTo dont do it on every vserver i want to create one ssl profile with ciphers and ecc included.
but netscaler told me, i must activate the default ssl profile to do it.
Is ssl backend communication with TLS 1.2 working now with vpx 11.0 build 68 ? Or why dont activate the default ssl profile ?
It should work now.
However, once you enable the Default SSL Profile, would you ever change it? If it’s bound to a bunch of vServers, you’d probably have to test each vServer prior to changing the Default SSL Profile. Or you can create a new SSL Profile and bind it to each vServer.
Hi Carl,
I have problems getting a Java FTP client to work.
We have the Serv-U FTP server which provides SFTP as well as a web gui.
I have configured a LB server for the TCP22 connection and all works fine from ex. FileZilla FTP client.
Our users can also connect to a HTTPS gui and up/download files. This GUI is configured as a CS that accepts the HTTPS connection and forwards it to a LB vserver that is load balancing between the 2 servers. the connection “on the back” is also HTTPS.
Here comes the problem:
From the HTTPS gui the user can launch a Java “FTP” client that connects using the credentials from the HTTPS connection. This Java application launches without problems but when transferring files the files will copy approx 20-40 sec and the the connection is dropped. I have tried to capture the traffic but since it is HTTPS it doesn’t reveal much.
Connecting directly to the Serv-U servers all works fine.
Have you seen this type of behaviour?
Thanks
Jeppe
Hi Carl,
Is there any way to disable Default_ns_profile?
If you look in ns.conf, there is a command to enable it. You can remove that command and reboot. Then you’ll probably have to reconfigure your SSL vServer SSL settings.
Hello Carl,
I figured I would ask you this question, I have been struggling with some time.
We are using PaloAlto to perform SSL decryption for Sharefile to block malware and certain file types; however, PA does not support Diffie Helmen ciphers so I need to create a custom cipher suite. This has been completed but here is the issue.
I currently have sharefile on a CSW and really don’t want to burn another public IP for the ciphers, but what I noticed is that the client only respects the ciphers on the CSW not the LB VIP. Is there any way to redirect the cipher negotiation to the LB vip??
I applied all of the settings on a NetScaler 11.0 66.11nc VPX. I now get my A+ at SSLLABS, but can’t login anymore. Only get a blank page. On my Server 2012 R2 Storefront 3.6 installation I have a bunch of “Schannel” Errors, that the ciphers are not supported. What do I have to change in the IIS to work with the A+ NetScaler?
You made changes on the backend connection?
At least not intentional. I’m testing the github script right now (https://github.com/ryancbutler/Citrix/blob/master/Netscaler/set-nsssl.ps1) instead of doing it by myself. But I remember having the same error in the past, while I first tried to achieve the A+.
But if you mean “ns_default_ssl_profile_backend” then no, I don’t think there has been a change.
I really just want the A+ and the Stroefront setup working.
Maybe I have this error: http://www.jasonsamuel.com/2015/10/15/citrix-netscaler-10-5-to-11-0-firmware-upgrade-issues-to-watch-out-for/
I solved the error accroding to “http://www.jasonsamuel.com/2015/10/15/citrix-netscaler-10-5-to-11-0-firmware-upgrade-issues-to-watch-out-for/”
Had to disable TLS1.2 on the IIS. Seems to be a pretty bad joke from Microsoft..
Hi Carl, you recommend to not use Default SSL Profile with NetScaler 11.0 VPX 65.
Do you know if this has been solved with “build-11.0-66.11_nc” so we can now follow your guide the same for MPX and VPX?
I have not done it at any customer so I don’t know if it works or not. I believe it’s fixed in 11.0 build 65. It seems to work in 11.1. However, even in 11.1, enabling default SSL Profile disables new features. So I’m more inclined to skip the Default SSL Profile and instead manually bind a Custom SSL Profile to each SSL vServer.
Thank you very much. I will also stick to the manual way, and will ignore the SSL Profile feature.
If the GitHub Script works as well as it seems, then it won’T be more work anyway.
THanks for all this work. It is a big help to the Netscaler community.
I have an issue with an SSL offload implementation.
THe backend server runs oracle application server. The appserver respond to http:7778 for initiation and redirects to Oracle SSO Server listening on http:7777.
I setup the ssl offload using a CS on https:4443 and works for the oracle appserver only, i.e. it works for http:7778.
I have 2 CS policies one for each lb service http:7778 and http:7777, but the ssl offload does not work with authentication portion.
Here is the config I have so far.
add server csmstest_server 192.168.190.198 -comment oracle-app-csms-appdev
add service csmstest_http_78_svc csmstest_server HTTP 7778 -gslb NONE -maxClient 0 -maxReq 0 -cip DISABLED -usip NO -useproxyport YES -sp ON -cltTimeout 180 -svrTimeout 360 -CKA NO -TCPB NO -CMP NO
add service csmstest_http_77_svc csmstest_server HTTP 7777 -gslb NONE -maxClient 0 -maxReq 0 -cip DISABLED -usip NO -useproxyport YES -sp ON -cltTimeout 180 -svrTimeout 360 -CKA NO -TCPB NO -CMP NO
add ssl certKey csmstest -cert csmstest.cer -key csmstest
link ssl certKey csmstest mreca02
add lb vserver csmstest_http_78_lb_vserv HTTP 10.1.12.196 80 -persistenceType NONE -Listenpolicy None -cltTimeout 180
add lb vserver csmstest_http_77_lb_vserv HTTP 10.1.12.195 80 -persistenceType NONE -Listenpolicy None -cltTimeout 180
add cs vserver csw_vserv_SSL_csmstest SSL 10.10.35.197 443 -cltTimeout 180 -Listenpolicy None
add cs vserver csw_vserv_HTTP_csmstest HTTP 10.10.35.197 80 -cltTimeout 180 -Listenpolicy None
add cs policy csw_pol_csmstest-78 -rule “HTTP.REQ.URL.CONTAINS(\”/csms\”)”
add cs policy csw_pol_csmstest-77 -rule “HTTP.REQ.URL.CONTAINS(\”/mysso/\”)”
bind lb vserver csmstest_http_78_lb_vserv csmstest_http_78_svc
bind lb vserver csmstest_http_77_lb_vserv csmstest_http_77_svc
bind cs vserver csw_vserv_SSL_csmstest -policyName csw_pol_csmstest-78 -targetLBVserver csmstest_http_78_lb_vserv -priority 110
bind cs vserver csw_vserv_SSL_csmstest -policyName csw_pol_csmstest-77 -targetLBVserver csmstest_http_77_lb_vserv -priority 120
bind cs vserver csw_vserv_HTTP_csmstest -policyName http-to-https_responder_pol -priority 100 -gotoPriorityExpression END -type REQUEST
bind ssl vserver csw_vserv_SSL_csmstest -certkeyName csmstest
Using curl here is the sequence of events:
curl -I -v -s http://sy00011.bc.broward.cty:7778/csms/Index.do 1 > /dev/null
* About to connect() to sy00011.bc.broward.cty port 7778
* Trying 192.168.190.198… connected
* Connected to sy00011.bc.broward.cty (192.168.190.198) port 7778
> HEAD /csms/Index.do HTTP/1.1
> User-Agent: curl/7.15.5 (x86_64-redhat-linux-gnu) libcurl/7.15.5 OpenSSL/0.9.8b zlib/1.2.3 libidn/0.6.5
> Host: sy00011.bc.broward.cty:7778
> Accept: */*
>
< HTTP/1.1 302 Redirect to Oracle SSO Server
< Location: http://sy00011.bc.broward.cty:7777/pls/orasso/orasso.wwsso_app_admin.ls_login?Site2pstoreToken=v1.4~159632FC~ACB59D2A915DB34889C1DA173C7543564A62BDF208D5A5668644D98510E12414DE6CF10EE6C0901E78A32A16210785C079E5DAE778BC27B6F9FACFC9626002B1743B241BBBD02175D173F77FB635A1737DC2239837EAD684C79BD5CB167306982B48CF09916071436A7CF96FD9D2377F2918142F042286011463B9223410EC4FD72B056649CF5EE20605427132B82B7018CB18E01055B09C9647CD846A6151102CAD625650AC8974BAEEDBFC58561D574FEDD6B45FA31A9316C5B2A3CCD4A5FA0348C04A79D9E9C2530EBE40940C92B9
< Cache-Control: private
< Content-Type: text/html
< Set-Cookie: JSESSIONID=c0a8bec630dc86caf5c34e334edfa5beb1b5f4505112.e3mOc3yQa3eLe34Sa3ySb38Ob3f0mRbHqObGrlbOnl92; path=/csms
< Server: Oracle-Application-Server-10g/10.1.2.0.2 Oracle-HTTP-Server OracleAS-Web-Cache-10g/10.1.2.0.2 (N;ecid=84994757831,0)
< Date: Tue, 28 Jun 2016 14:10:13 GMT
< Osso-Paranoid: true
* Connection #0 to host sy00011.bc.broward.cty left intact
* About to connect() to 1 port 80
* Trying 0.0.0.1… Failed to connect to 0.0.0.1: Invalid argument
* Success
* couldn't connect to host
* Closing connection #1
* Closing connection #0
If the Access Gateway Virtual Server is configured to use (for the sake of brevity) ciphers 1, 2, 3, and 4 (in that order) AND the AG VServer is talking to the STAs over https then does the OS of the STAs, Windows 2k8R2 for example, need to also support those same ciphers suites?
If that is a correct statement, then does the order come into play? In other words, if the client browser hits the AG VIP and an ECDHE GCM cipher is supported and it uses it. The client browser and the NetScaler support that cipher, authentication can happen, but the STAs (2k8R2) do not, users will get a TLS handshake will fail when they attempt to launch an app?
The ciphers on the Gateway vServer only apply to the client-side of the connection.
When NetScaler connects to STA it’s using a server-side connection, which allows all ciphers. You can verify this by running a network trace on NetScaler and look for SSL Handshake.
Hi Carl – how would I go about attaching the HSTS rewrite policy to a content switching VIP?
I would probably bind it to each of the target LB vServers.
Hi Carl,
how can I bind the HTSTS policy to an AAA vServer? I didn’t found there any rewrite option….
Best Regards,
Carsten
If you’re content switching AAA, then maybe you can bind it to the content switch.
Hi, very good job that you are doing here! :).
Have you ever tested the ssllabs.com check with the latest NetScaler release (11.0-65.35)?
For me an error occured and I think because of the release version and not because of my settings.
Would be great if you could proof it.
Regards
I just got an A on 65.31. What are you seeing?
After a couple of seconds it says “Assessment failed: Unable to connect to the Server”.
Usually it works without a problem.
Moreover in the description it says (next to some other possible reasons for the failure):
“NetScaler issues – some NetScaler versions appear to reject SSL handshakes that do not include certain suites or handshakes that use a few suites. If the test is failing and there is a NetScaler load balancer in place, that’s most likely the reason”
I am using a “near to default” SSL-Profile, just with DHE configured for PFS.
TLS 1.2 is also activated in the profile.
I have also added the TLS1.2 ciphers although using the VPX but they finally seem to work with this release.
Removing the TLS1.2 ciphers from the SSL-Profile did not change anything.
Unfortunately I have activated the default ssl-profile setting on the VPX before I noticed that this setting seems to be “irreversible”.
Any idea why it is not possible to revert this setting?
Everything is working fine but I would like to know why the test is failing.
It might also be a firewall issue – I did not do a ssllabs check before I upgraded to the latest release so I don’t know if it has worked before.
Hi Carl, I tried to apply http to http rediction to a web service, users inside and outside the local network have to reach the site through internet, the firewall has ports 80 and 443 open and are pointed to the NS VIP on port 443 and 80 respectively, if i test the site using the fqdn the user reach the public ip but it seems like it does not hit the vip addres, if i use the private ip on the lan redirection seems to work, but it kind of looks like redirection doesnt work when i use fqdn/path, do you have any suggestions? thanks in advance
Is your NetScaler connected to multiple subnets? If so then your networking/routing might not be setup correct. Enabling Mac Based Forwarding might help.
What is your Responder policy expression?
You’ll probably need to do some network troubleshooting. Does the DNS name resolve correctly? Use tools like WireShark or Fiddler to troublehshoot.
Hi Carl, Thank you for your response. I am connected to multiple subnets (gonna double check if I do have MBF activated), this is my responder policy “https://\” + HTTP.REQ.HOSTNAME.HTTP_URL_SAFE + HTTP.REQ.URL.PATH_AND_QUERY.HTTP_URL_SAFE”, I will also try with fiddler to see if I have any luck. Thanks!
Actually, that’s the Responder action.
I think I see an extra backslash in there.
The NetScaler GUI lets you Evaluate your expressions to make sure they work correctly.
Carl, I’ve created a site called apps-test that is working beautifully. Custom portal theme, two form authentication, load balanced storefront, everything is working great. The problem is that the test is over and now management wants the site rebranded to just “apps.xxx.org” for deployment. When I change the cert and change the URL on the storefronts, it still somehow tries to go to apps-test instead, the browser complains about the cert, and even the custom portal theme is wrecked.
So my question is, what is the correct way to change the URL and cert on a virtual server without breaking everything? Please and thanks in advance.
You can search through the NetScaler config for the wrong URL. I’m guessing you have a hard coded site redirect somewhere – either on NetScaler or on StoreFront.
Hi Carl
Netscaler can configure two Radius Server?(Is an AD by default and Radius Server)
Are you asking how to configure two different RADIUS policies for NetScaler Gateway? If so, follow my two-factor instructions but replace LDAP with your first RADIUS policy.
Or are you instead asking how to load balance RADIUS?
Hi Carl
Not sure if I’m right here, but let me ask a question.
I tried to configure STA on netscaler over a LB vserver (one for each STA!) and set Netprofiles on the Services because we have multiple SNIPs. Everything works with STA on port 80 but not on port 443.
Do you have an idea, how to configure STA vserver for https?
I’m now searching for so Long with no success. Maybe you have a solution?
Thanks
Are you saying that you created the SSL LB for each STA and configured Gateway with https:// STA URLs and it doesn’t work?
Yes, thats correct. the same way with http it works! Tried to configure LB with TCP 443 or SSL_TCP 443 or SSL_Bridge with no success.
Any idea?
The protocol should be SSL. I’ll try to do it myself and see if it works. Do you also have SSL cert on the STA server?
I just created an SSL LB vServer with one HTTP service. I added it to Gateway using https://VIP and it immediately read the STA ID. Works for me.
What if you add a https Service?
For me it works as well with a http Service. But if I Change it to a SSL Service it doesn’t work anymore.
We do have a SSL certificate on the STA Server.
What type of certificate do you add on the SSL LB vServer?
Did you configure https://VIP with the IP address of the LB vServer or with a DNS Name?
I did VIP (IP Address). That eliminates DNS issues. NetScaler doesn’t verify certs so it works.
I’ll try an SSL service later. But usually SSL -> HTTP is the more difficult case.
Maybe you have a physical NetScaler with one of the builds that enables TLS 1.2 on the services. In that case you can try disabling TLS 1.1/1.2 on the SSL service.
Thats it!!!!
Disabling TLS 1.1/1.2 did it…
Your great, thanks
There seems to be a lot of issues with TLS 1.2 and Windows servers.
Have you tried NetScaler v11 62.10 yet? I’m having a terrible time finding a set of ciphers for a test VPX instance that doesn’t give me “No usable ciphers configured on the SSL vserver” error.
That’s a normal warning.