RDP Proxy
NetScaler supports RDP Proxy through NetScaler Gateway. No VPN required. In 11.1 and newer, RDP can connect to Gateway on 443. In older NetScaler, RDP connects on 3389.
There are several ways of launching RDP sessions through NetScaler Gateway RDP Proxy:
- Bookmarks on the Clientless Access portal page.
- Bookmarks can be defined by the administrator.
- Or users can add their own RDP bookmarks.
- After logging in, change the URL in the browser to /rdpproxy/MyRDPServer. MyRDPServer can be IP or DNS.
- In the RfWebUI Portal Theme, the Add Bookmark link lets users enter an RDP address, and click Go.
The easy configuration is for one Gateway to do both authentication and RDP Proxy. Alternatively, you can have one Gateway vServer that authenticates the user and a different Gateway vServer to proxy the RDP connection. The Gateways use Secure Ticket Authority (STA) for mutual authentication. See Stateless RDP Proxy at docs.citrix.com for more information.
Links:
- RDP Proxy at Citrix Docs
- Kenny Baldwin blog post RDP-Proxy on NetScaler!
- Citrix Blog Post RDP Gateway on a NetScaler SSLVPN Virtual Server
- Citrix CTX200853 How to Configure RDP Profile on NetScaler Gateway
- RDP Proxy section in Unified Gateway FAQ at docs.citrix.com
- Anton van Pelt NetScaler Gateway = RD Gateway
Here are some requirements for RDP Proxy:
- NetScaler Enterprise Edition or Platinum Edition.
- NetScaler Gateway Universal Licenses for each user.
- NetScaler 11.1 build 49 and later come with built-in Gateway Universal licenses: NetScaler Standard Edition = 500 licenses, NetScaler Enterprise Edition = 1000 licenses, and NetScaler Platinum Edition = unlimited licenses.
- TCP 443 opened to the NetScaler Gateway Virtual Server. If older NetScaler, open TCP 3389 to the Gateway.
- TCP 3389 opened from the NetScaler SNIP to the RDP Servers.
Do the following to configure RDP Proxy:
- Go to System > Settings, and click Configure Advanced Features.
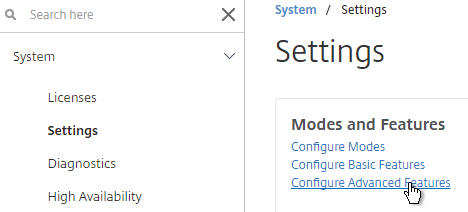
- Check the box for RDP Proxy, and click OK.
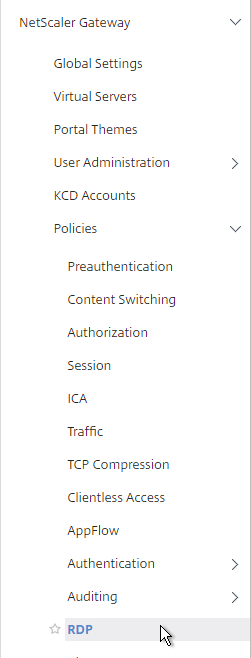
- Expand NetScaler Gateway, expand Policies, and click RDP.
- On the right, switch to the Client Profiles tab, and click Add.
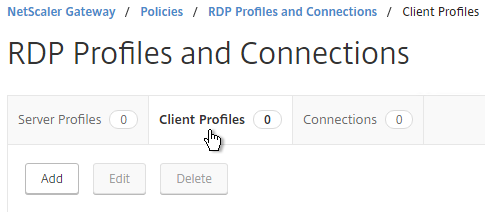
- Give the Client Profile a name, and configure it as desired. Scroll down.
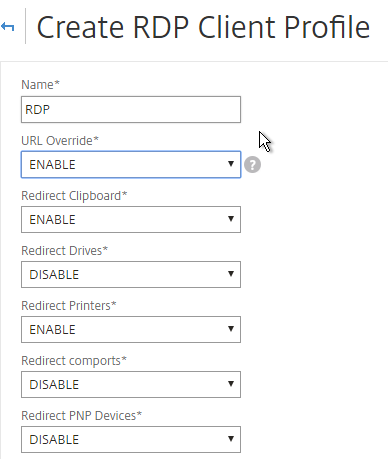
- It is no longer necessary to configure a Pre shared key or RDP Host. Just click Create.
- It is no longer necessary to create a RDP Server Profile.
- If you want to put RDP bookmarks on the Clientless Access portal page, on the left, expand NetScaler Gateway, expand Resources, and click Bookmarks.
- Alternatively, Simon Gottschlag Publish RDP Proxy Link via StoreFront shows how NetScaler Rewrite can insert an RDP Proxy link into a StoreFront web page.
- On the right, click Add.
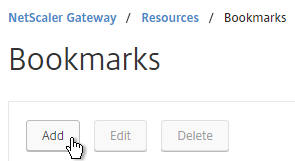
- Give the Bookmark a name.
- For the URL, enter rdp://MyRDPServer using IP or DNS.
- Check the box next to Use NetScaler Gateway As a Reverse Proxy, and click Create.
- Create more bookmarks as desired.
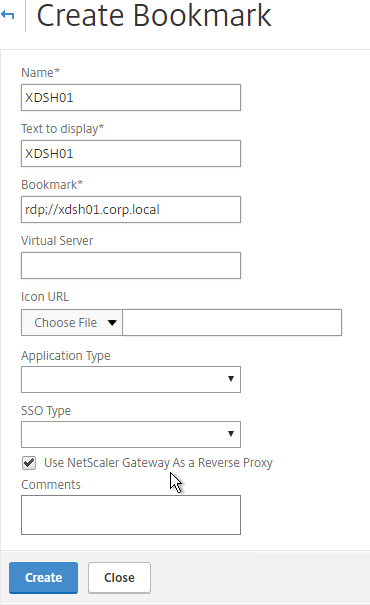
- Create or edit a Session Profile/Policy.
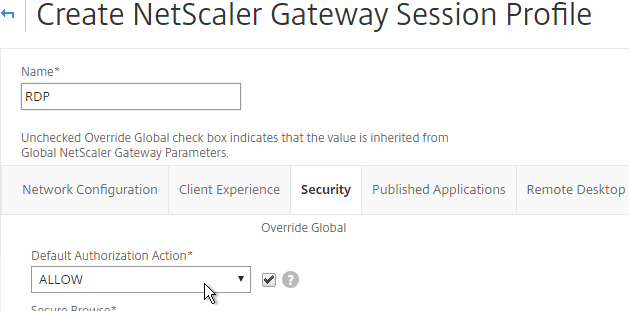
- On the Security tab, set Default Authorization Action to ALLOW. Or you can use Authorization policies to control access.
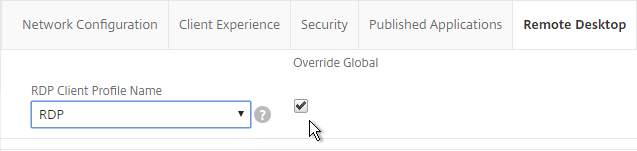
- On the Remote Desktop tab, Override Global and select the RDP Client Profile you created earlier.
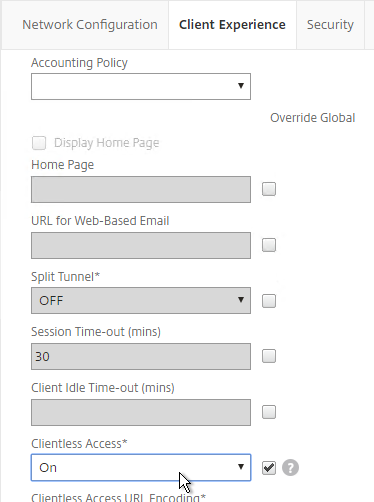
- If you want to use Bookmarks, on the Client Experience tab, set Clientless Access to On.
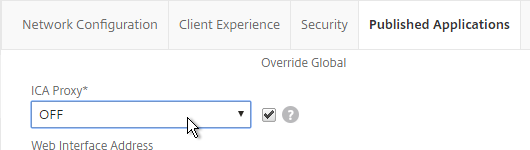
- On the Published Applications tab, make sure ICA Proxy is OFF.
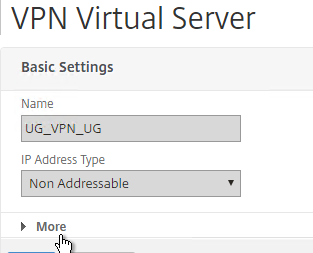
- Edit or Create your Gateway Virtual Server.
- In the Basic Settings section, click More.
- It is no longer necessary to bind a RDP Server Profile. Instead, RDP is proxied through 443 on the Gateway.
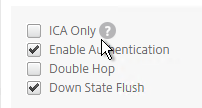
- Scroll down. Make sure ICA Only is not checked. This means you’ll need NetScaler Gateway Universal licenses for each user that connects through this Gateway.
- Bind a certificate.
- Bind authentication policies.
- Bind the session policy/profile that has the RDP Client Profile configured.
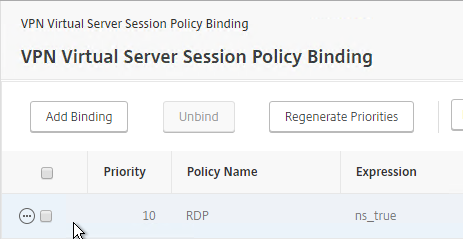
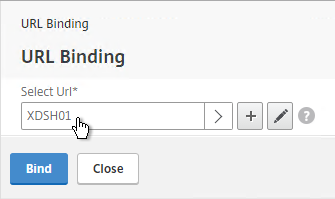
- You can bind Bookmarks to either the NetScaler Gateway Virtual Server, or to a AAA group. To bind to the NetScaler Gateway Virtual Server, on the right, in the Advanced Settings section, click Published Applications.
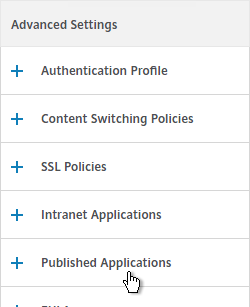
- On the left, in the Published Applications section, click where it says No Url.
- While editing your Gateway vServer, you can also enable the new RfWebUI Portal Theme. This requires StoreFront to be 3.6 or newer.
- Bind your Bookmarks.
- Since this NetScaler Gateway Virtual Server has ICA Only unchecked, make sure your NetScaler Gateway Universal licenses are configured correctly. On the left, expand NetScaler Gateway and click Global Settings.
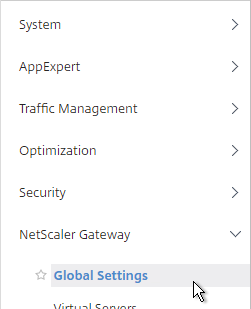
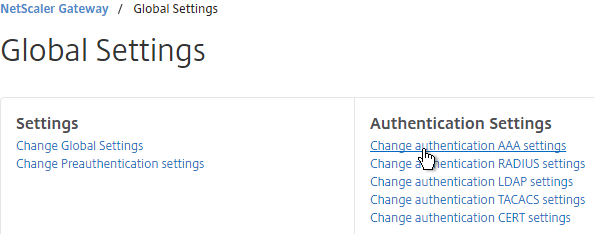
- On the right, click Change authentication AAA settings.
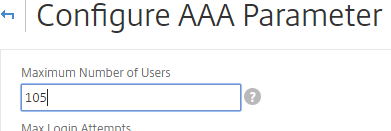
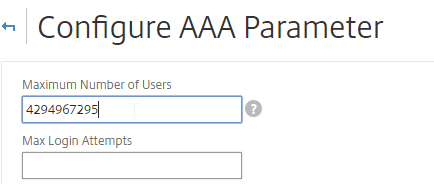
- Change the Maximum Number of Users to your licensed limit. In NetScaler 11.1 build 49 and newer, this value should already match the number of licensed users. In older builds, you must manually configure this setting, and if not configured, then it defaults to only 5 concurrent connections.
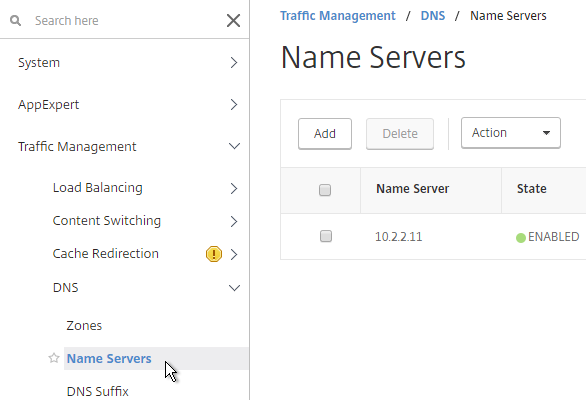
- If you want to connect to RDP servers using DNS, make sure DNS servers are configured on the appliance (Traffic Management > DNS > Name Servers).
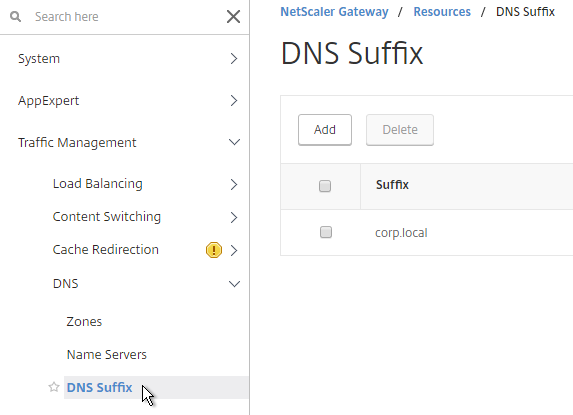
- If you want to use the short names instead of FQDNs, add a DNS Suffix (Traffic Management > DNS > DNS Suffix).
- Connect to your Gateway and login.
- If you configured Bookmarks, if RfWebUI theme, on the Apps tab, click Web and SaaS Apps.
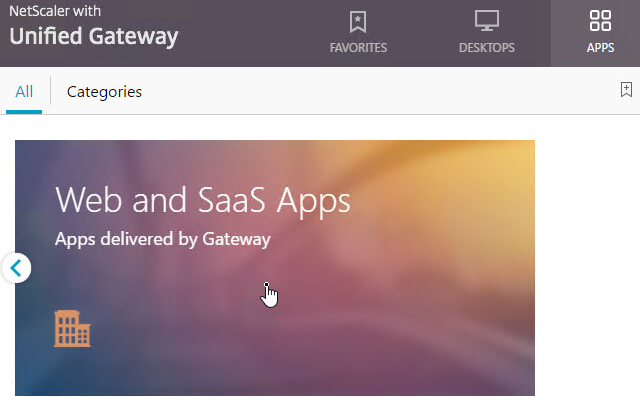
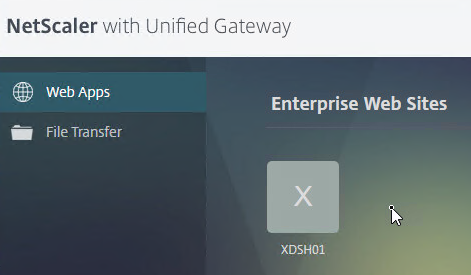
- If X1 theme, the bookmarks are on the Web Apps page.
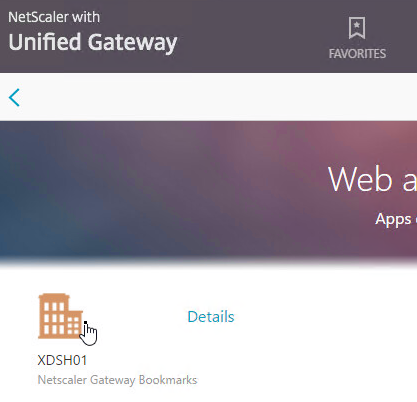
- Then click the Bookmark. If RfWebUI theme, you can also click Details to mark the Bookmark as a Favorite.
- Or you can change the address bar to /rdpproxy/MyRDPServer. You can enter an IP address (e.g. rdpproxy/192.168.1.50) or a DNS name (/rdpproxy/myserver).
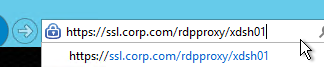
- If you edit the downloaded .rdp file, notice that it’s connecting on port 443.
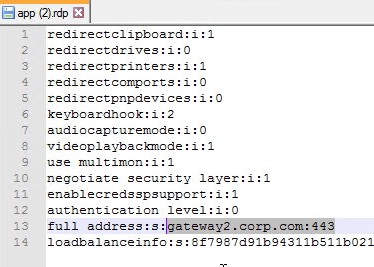
- Then open the downloaded .rdp file.

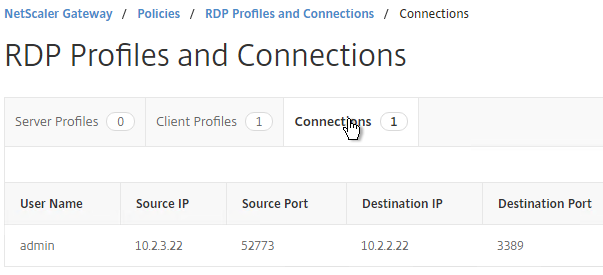
- You can view the currently connected users by going to NetScaler Gateway > Policies > RDP, and on the right is the Connections tab.
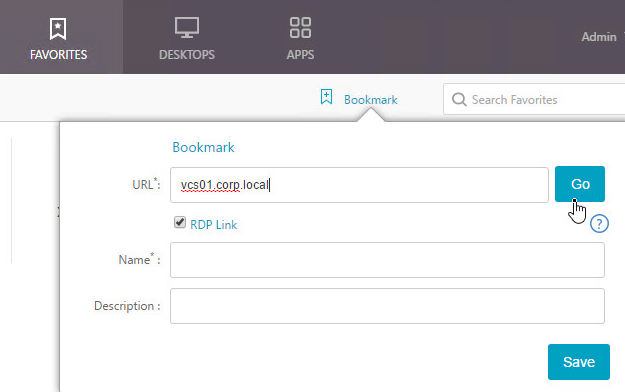
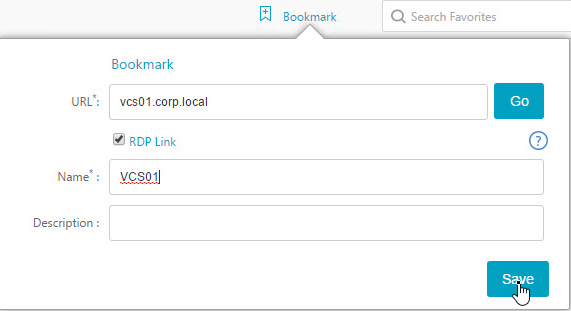
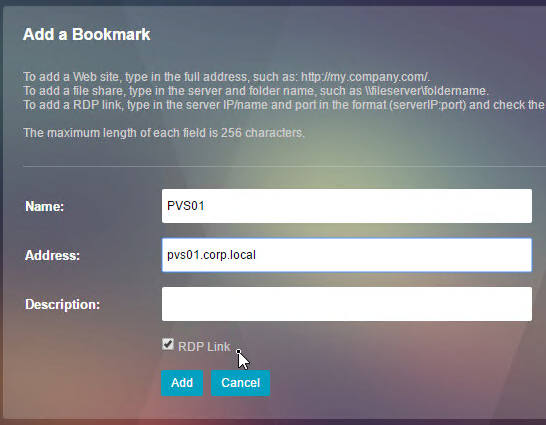
- If using the RfWebUI theme, another way to launch RDP sessions is to click the Add Bookmark link, enter a destination DNS/IP, check the box next to RDP Link, and click Go.

- You can also Save the bookmark.
- Then access the saved bookmark from Apps > Personal Bookmarks.
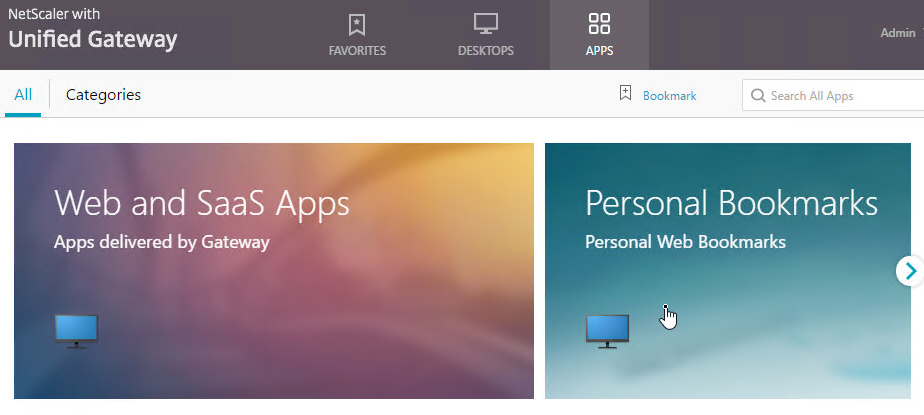
- Personal bookmarks are stored in
/var/vpn/bookmarkon the appliance. You might want to back these up and replicate them to other Gateway appliances participating in GSLB. See NetScaler 11.1 Personal Bookmarks at Citrix Discussions.
- The X1 theme has an Add button on the Web Apps page.
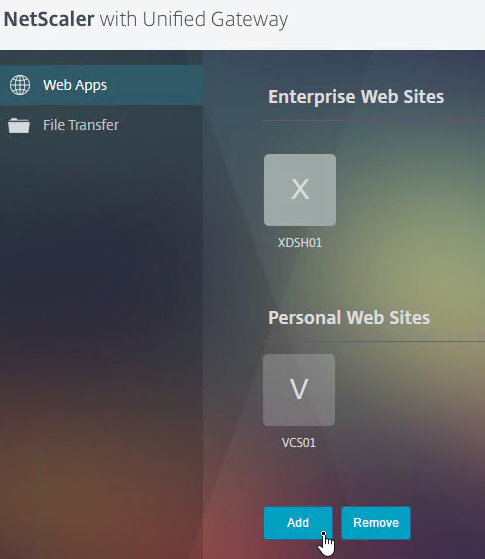
- But there is no Go button. Instead, you save the Bookmark and launch it from the list.
Has anyone tried to access the secondary node by creating a bookmar?
Hi Carl,
is there a way to disable custom bookmarks creation by users?
I dont want users to be able to create own bookmarks.
Gruesse
Daniel
Here’s a thread – https://discussions.citrix.com/topic/381468-portal-theme-rfwebui-disable-top-right-bookmark-button/
Carl,
Does this completely secure the RDP traffic, can this replace the RDP Gateway server which would typically be in the DMZ?
RDP Proxy requires you to use a web page to login to Gateway and then enter the address of a destination RDP server. Does that meet your needs?
It does as long as the traffic is secure. What i am trying to do is use the netscaler as the “remote gateway” for user connecting from the outside then from there they can connect back to the RDS Web Access server to get their apps and or desktops.
I need to be sure that the RDP proxy will secure and inspect the traffic from the outside.
thanks.
I don’t think RDP Proxy can get icons dynamically from RDWeb. Also, I don’t think you can configure RDWeb to proxy RDP through Citrix Gateway.
Citrix Gateway’s RDP Proxy feature is designed for users that use a browser to login to Citrix Gateway. After login, the user types in a machine name and the RDP connection is proxied through Citrix Gateway.
Thanks.
So this would not be a solution to replace having a Remote GW server in the DMZ?
Or once they authenticate through the netscaler they are then presented with a URL to sign in to the RDP Web access (hopefully SSO can work here).
I just need a secure way to get into the network.
FYI, using a traffic policy to disable SSO for RDP proxy will disable the RDP profile enforcement. With SSO disabled users are able to override the RDP file flipping 0’s to 1’s for any feature.
Hi Carl,
First of all, Great site! using it in and out 🙂
I have one question about RDP proxy: Does it work via native Citrix receiver client?
I was on phone with CITRIX rep and he said that Native receiver requires to set ICA ON, thus RDP proxy will not work on receiver. Indeed, once I set ICA to ON it worked, but ICA-OFF does not. Is there any way around?
I use 11.1 and Unified gateway solution
With ICA OFF and RFWebUI with client choice disabled I have both Storefront icons and RDP proxy on one page. All works perfect via receiverforWeb. But cannot mke it work ( RDP) on native client
Your opinion is much appreciated
Are you asking for Gateway RDP Bookmarks to show up in native Receiver?
When you say “ICA”, do you mean “ICA Proxy”? Or do you mean “ICA Only”?
Yes Carl, I am trying to have RDP bookmarks to show up in native receiver
I mean “ICA Proxy” . OFF – native receiver does not work at all but required for RDP proxy, ON – Native receiver works, but no bookmarks
Good day, Carl.
Your publications are excellent
I would be very grateful for advice in dealing with the problem.
Can’t run RDP
NetScaler mpx 8200-2 PCs, Release 11.1 Build 50.10 nc
Settings performed by your recommendations
DNS, NTP, LDAP,ping work
NSIP=172.16.15.154/29
VIP=85.143.143.182
SNIP=10.1.0.2
Terminal Server 192.168.15.131
On a Terminal Server, authentication runs
the remote user session does not rise,
session hanging-
Connect to:
85.143.143.182:3389
Configuring remote session
I do not see errors in the logs
nstcpdump.sh port 3389 на Netscaler
15:12:04.119602 IP 176.59.17.47.58083 > 85.143.143.182.3389: Flags [S], seq 3125859020, win 8192, options [mss 1260,nop,wscale 8,nop,nop,sackOK], length 0
15:12:04.119607 IP 85.143.143.182.3389 > 176.59.17.47.58083: Flags [S.], seq 1020259861, ack 3125859021, win 8190, options [mss 1220,nop,wscale 4,nop,nop,sackOK], length 0
15:12:04.151587 IP 176.59.17.47.58083 > 85.143.143.182.3389: Flags [.], ack 1, win 257, length 0
15:12:04.171789 IP 176.59.17.47.58083 > 85.143.143.182.3389: Flags [P.], ack 1, win 257, length 91
15:12:04.171813 IP 85.143.143.182.3389 > 176.59.17.47.58083: Flags [.], ack 92, win 2225, length 0
15:12:04.171814 IP 10.1.1.2.14018 > 192.168.15.131.3389: Flags [S], seq 3944707652, win 8190, options [mss 1460,nop,wscale 4,nop,nop,sackOK], length 0
15:12:05.178729 IP 10.1.1.2.14018 > 192.168.15.131.3389: Flags [S], seq 3944707652, win 8190, options [mss 1460,nop,wscale 4,nop,nop,sackOK], length 0
15:12:07.173613 IP 192.168.15.131.3389 > 10.1.1.2.14018: Flags [S.], seq 2790690802, ack 3944707653, win 64000, options [mss 1460,nop,wscale
……
The problem is solved. Adding Traffic Policy = REQ. HTTP.URL CONTAINS rdpproxy
I too have an issue related to credssp being enabled. I have logged a case with Citrix support. They tell me that this setting is not specified by Netscaler, and their theory is that it’s comming from the destination RDS host.
Allthough I have my doubts.
I’ll try and remember to update here, if I ever find a solution.
Hi, I’m working closely with Citrix on this and all other points mentioned. I think the credssp is set by the NetScaler and is forced. I’ve created a traffic policy with the RDPproxy path as an expression, so only applies to RDP proxy connections; this traffic policy turns SSO off and works ok; however, like you, should have answers soon on how to set the credssp parameter to off. I’m also looking on how to auto generate user RDP icons, in a NetScaler friendly format, based on a CMDB callout; a CMDB which holds information about users desktop assignment(s).
Hi Geoff,
Have you or Citrix managed to come up with a solution to disable credssp in the RDP file generated by the NetScaler?
Hi, no, but tbh applying the traffic policy to disable SSO works just fine.
Geoff
Hi Carl,
We have set up the RDP Proxy identical to your post however we can’t get it working. We are using Windows Server 2012 R2.
The solution works fine when the server is a fresh install and has RDP enabled.
The solution fails when we install the RDS (Remote Desktop Services) role on the server. We keep getting the follows errors:
1. https://technet.microsoft.com/en-us/library/ee891061(v=ws.10).aspx
2. https://technet.microsoft.com/en-us/library/ee890979(v=ws.10).aspx
It points to a communication error between the RDS server and the NetScaler. Any thoughts would be much appreciated.
Regards,
Ben
Hi Ben,
do you want to use this as a single Terminalserver or in combination with a RDS Connection Broker?
Regards
Julian
Hi Julian,
It’s a single terminal server. The errors mentioned earlier are seen on the RDS server every time we connect.
Thanks,
Ben
Hello,
we seem to face exact the same issue you described.Have you got it working? If yes, could you please share the solution?
Best regards
Hermann
Hi Carl,
Is there a way to block users from entering /rdpproxy/RDPServer URL ? I want to be sure that a user get access to the bookmarks but nothing more.
Regards,
Stéphane
Thanks for the article Carl. Any idea how I can restrict RDP Bookmarks to different AD Groups and with different options like:
– AD Group 1 gets Bookmark “Support VM” with redirect Printers enabled
– AD Group 2 gets Bookmark “Support VM” and “Trainee VM” with redirect Printers disabled
– and so on…
Thanks and Regards
Julian
You can add Gateway AAA Groups that match the AD Group names, and assign bookmarks and Session Policies to the AAA Groups.
Thanks for the quick response. In my AAA Groups, there is no “Bookmarks” section under the advanced settings, like discribed here https://www.carlstalhood.com/netscaler-gateway-11-1-ssl-vpn/#bookmarks
NetScaler 11.1, 51.26
Is there a feature that must be activated or something else?!
Ok, found it… When you edit the AAA User or AAA Group under the section Security -> AAA, Users, then there are no Bookmark option. Edit the AAA User under NetScaler Gateway -> User Administration -> AAA User / AAA Groups, there’s the option visible. Funny.
Carl, thanks for this article. This is very promising from a MFA PCI perspective. It’s been a while since I engineered NetScaler (I architect now). Can you do something similar to this but using an SSH client such as PuTTy?
I don’t think so, but that’s an interesting question.
Hi Carl, custom RDP line works through the custom option in RDP client profiel but what if an existing entry, non custom, needs to be deleted from the file? I ask because my custom entry gets put at the top of the RDP file and a same default entry overrides it further down.
kind regards,
Geoff
I’m holding thumbs for a solution as well. I have the same issue when I try to override the default “enablecredsspsupport” setting in the RDP file generated.
Regards,
Pieter
Ok, so still need STA added for netscaler RDP proxy when SF/XA/XD is not used?
“In the case of a single gateway deployment, the STA server is not required.” https://docs.citrix.com/en-us/netscaler-gateway/11-1/rdp-proxy.html
Thanks Carl, all working fine. Just need to inject a custom line into the RDP file which downloaded, can this be done do you know? Geoff
In the RDP Client Profile, there’s a Custom Parameters field.
Hi Carl, on one of your screenshots you have a STA server set, which server should be used for STA exactly? Thanks, Geoff
Usually it’s your XenApp/XenDesktop Controllers.
Can the RDPserver be a Windows OS desktop i.e. one user, one desktop for every user conne
cting through this NetScaler RDP proxy?
I’m not aware of any restrictions. You just need to provide the address of the destination.
Thanks Carl, have you had experience of pre-populating automatically the users desktop name where it is already known what the users desktop is, instead of user having to provide this?
Hi Carl,
Thanks for this document.
Is it possible to launch only a RemoteApp through the RDP proxy ?
Best Regars,
Werner
Is it possible to disable Credssp support in the RDP file generated by the NetScaler RDP proxy?
Each downloaded RDP file contains the “enablecredsspsupport:i:1” setting which prevents users from changing expired passwords in a scenario where:
– SSO is disabled with a traffic policy
– Network Level Authentication and CredSSP is used on the remote RDP host
– The user’s password has expired
What seems to happen is that the user is authenticated, but the password change message cannot be passed to the user.
A workaround for a regular RDP file is to disable credssp by adding “enablecredsspsupport:i:0” to the RDP file. Adding this as a custom parameter in the RDP client profile does add the setting to the generated RDP file at the top of the file – HOWEVER, this is then overwritten by the original setting again which enabled it again.
Not sure if this behaviour can be changed, but any ideas would be greatly appreciated.
Did you find a workaround in the meantime?
Experiencing the same issue. I tried to rewrite the contents of the RDP file by first B64DECODE the body, get all content except for the enablecredsspsupport entry, then B64ENCODE the body again, but I can’t get any Rewrite policy to trigger on the Req/Res of the /rdpproxy/.. requests…
Unfortunately I have not been able to figure out a workaround for this… Still hopeful someone can come with something clever .
Hi Carl,
An ideas on this one…
Using NS 11.1, I’ve setup the RDP Proxy as per your guide (including the SSO traffic policy tip from Carsten). If I connect to the Gateway VServer IP directly, then everything works well – I can connect to the vserver login page and login successfully, choose the RDP Bookmark which downloads the RDP file and I can open that and it connects me to the RDP server as expected.
However, if I attempt to connect via the internet facing firewall (NATs to the Netscaler Gateway VIP), everything works until launching the RDP file… I receive “An internal error has occurred”.
Reviewing firewall logs indicates that 443 is passing through as expected, and I can access the vserver login page and login successfully. There doesn’t seem to be anything that is blocking the traffic.
Reviewing the nstcpdump doesn’t show any traffic for 3389 (I’m not using any custom ports).
We have a 2 arm setup – VServer is in a DMZ and the Netscaler SNIP is on the LAN.
Any thoughts would be appreciated.
Regards,
Robert
The firewall is not doing any sort of traffic inspection?
Hi Robert,
I had the same issue, because my RDP Server uses a different username.
A traffic policy has helped me: https://support.citrix.com/article/CTX207025
Best Regards,
Carsten
Hi Guys,
I had already tried turning off the traffic inspection etc on the firewall policy with no luck. I re-tested though just to be sure… Turns out the inbound policy on the ‘Next Gen’ firewall was configured to allow SSL and HTTP application type traffic through, not the actual inbound ports (i.e 80 and 443). Because RDP traffic over SSL isn’t your typical SSL web browsing traffic, it rejects the connection. Changing the inbound policy to allow specifically port 80 (for redirect to https) and 443, as opposed to the application type has resolved the issue.
Thanks for the tips!
Robert
Isn’t that a form of packet inspection?
Yes, I’d only gone as far as turning off inspection for gateway AV, URL filtering, content filtering, etc. Didn’t click until this morning that the application type was causing the issue.
Hi carl,
Thanks for your document. My RDP Proxy is working BUT I have this issue of intermittent disconnection of RDP session, basically user session hangs then black screen and RDP automatically tries to restablish connection but failed, However If user re-launch the RDP icon it connects back to the disconnected session.
Any ideas? It’s only happening on connection using RDP Proxy, all vServer using ICA proxy are fine.
thanks
Lauro
Maybe one of the timeouts in the Session Policy/Profile?
Hi Lauro, i am experiencing the same. Did u manage to pinpoint this issue? I see this behaviour on NetScaler build 11.0 65.31nc.
Thanks
Marc
Hi Carl,
Within the document, you have indicated a couple of times for “/rdpproxy/MyRDPServer” which we can either use DNS or IP for “MyRDPServer”. Is this a virtual server IP hosted by Netscaler? Or the Netscaler Gateway Virtual server IP?
I am assuming that it is not an actual RDP server acting as a terminal as that role should be replaced by Netscaler.
Do let me know if my understanding is wrong 🙂
Thanks for your guide as always.
MyRDPServer is the machine you’re trying to RDP to. NetScaler is just a proxy for the RDP connection.
so it is the internal resources 🙂 so for each RDP resources, I will need to create a separate client profile accordingly?
You usually only need one client resource.
You can then create bookmarks for each internal RDP Server (machine you want to use RDP to connect to). Or you can manually change the browser address bar to access another RDP server.
Hey Carl, first I want to thank you for your excellent blog posts!
I have read all instructions, when I click on the RDP bookmark, it opens an new tab with the /rdpproxy/RDPServer URL, but I see a message in the browser: “Error: Not a privileged User.” The .rdp file is not downloaded.
I’m sure all settings are exact as you blog describes. I’m running build-11.1-50.10 and have a Platinum license.
Do you have any clue?
Already solved, forgot to add the session policy to the VPN vserver.
Hi Carl,
Thanks for your awesome documentation (as usual!).
My setup doesn’t working properly, I’ve got “An internal error has occurred.” when a launch the RDP file after connecting RDP Proxy.
I made a Wireshark trace and I can see the NetScaler trying to connect to my server on the backend on port 3389 but a got a connection reset. I tried different target (win10, ws2012, domain/nondomain). The firewall is disable (On + “Allow All” in the profile) on the target. I’m able to connect to this target directly. I tried also to disable NLA on RDP without success.
This is a brand new NetScaler in my lab at build 11.1.49.11.
Any idea what I can check?
same issue
Thanks you for the post. I’ve configured everything, but I get the message “could not connect to the remote computer” I think the netscaler snip cannot connect to the rdp server. Is there a way to test this?
From the NetScaler CLI, run
shell, then runnstcpdump.sh port 3389to see the RDP traffic. If you see R flag, then a firewall is blocking.Thank you for your help. Another question, I’ve established SSO between Office 365 and the netscaler gateway virtual server. With SAML authenticationt to the unified gateway the rdp session won’t start (already afraid for it), with ldap authentication it works fine. Is there a way to get it working with saml authentication to the unified gateway?
I’m guessing it needs the user’s password to perform SSON.
For SAML to XenApp, Citrix has a way of requesting smart card certificates for login. I assume they don’t have similar functionality for RDP.
Hi Carl,
I had the same problem, I saw also the R Flag, but the reason was, that the user was not authorized to do RDP on that server.
The problem was the SSO from the Netscaler, the RDP destination uses different accounts.
The traffic policy from CTX208324 has helped me.
Best regards,
Carsten