Navigation
- Change Log
- VDA Virtual Machine Hardware
- Windows Configuration
- Install – Virtual Delivery Agent 2203 LTSR CU6
- Workspace app:
- Remote Desktop Licensing Configuration
- Reduce C: Drive Permissions
- Configure Pagefile for Citrix Provisioning
- Direct Access Users Group – allow non-administrators to RDP to the VDA
- Registry Settings – ShellBridge, EDT MTU, black screen, faster login, published Explorer, HTML5 Upload Folder, 4K Monitors, COM Ports
- Restore Legacy Client Drive Mapping
- Print Driver for Mac and Linux Clients
- HTML5 Workspace app – SSL for VDA
- Anonymous Accounts
- Antivirus
- Optimize Performance
- Apps
- Seal and Shut Down
- Uninstall VDA
💡 = Recently Updated
Change Log
- 2025 Jan 9 – Updated VDA Install for VDA 2203 LTSR CU6
- 2023 Oct 31 – updated the Workspace app versions
- 2022 Oct 12 – added link to VMware Tech Zone Windows 11 Support on vSphere.
- 2022 Sep 12 – added ShellBridge to fix published apps
Hardware
Hypervisor Host Hardware
- G0-EUC Moore’s law of Windows 10 1903 – Newer versions of Windows 10 have lower density than older versions
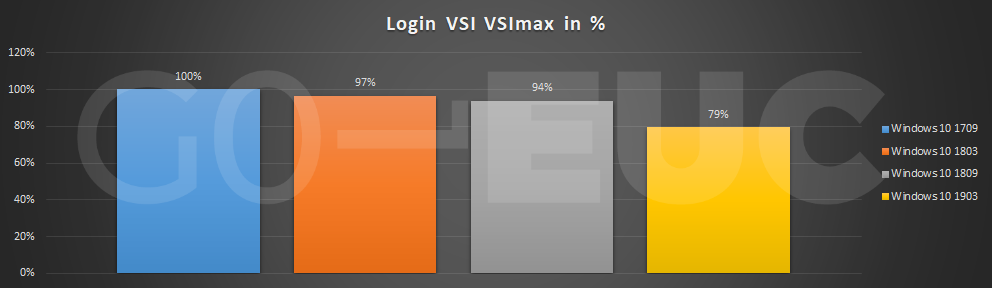
- Citrix Blog Post Citrix Scalability — The Rule of 5 and 10: Simply take the number of physical cores in a hypervisor host, multiply it by 5 or 10, and the result will be your Single Server Scalability. Use 5 if you’re looking for the number of Virtual Desktop VMs you can host on a box, and use 10 if you’re looking for the number of Virtual Apps user sessions you can host on a box.
Virtual Machine Hardware
- Operating system version support: VDA version 2203 LTSR supports Windows 11, Windows 10 64-bit (1607 and newer), Windows Server 2022, Windows Server 2019, and Windows Server 2016.
- Windows Server 2022 supports Microsoft 365 Apps (aka Office 365) 2302 and newer.
- Windows Server 2012 R2 is no longer supported. For Windows Server 2012 R2, install VDA 1912 LTSR with the latest Cumulative Update. VDA 1912 LTSR will work with newer Delivery Controllers (e.g., Delivery Controller 2203 LTSR).
- For older operating systems (e.g., Windows 7 or Windows Server 2008 R2), install VDA 7.15 LTSR with the latest Cumulative Update. VDA 7.15 LTSR will work with newer Delivery Controllers (e.g., Delivery Controller 2203 LTSR).
- Cloud VDAs – Cloud VDAs are supported if you are licensed for Citrix Cloud with Hybrid Usage rights. See CTX270373 Citrix Virtual Apps and Desktops: Public cloud support with Current Releases and Long Term Service Releases.
- Windows 11 and vSphere – Citrix supports Windows 11 on vSphere 7 or newer. Windows 11 requires TPM. vSphere requires VM encryption before it will let you add a TPM to the virtual machine. VM encryption requires a Key Provider. vSphere 7 has a Native Key Provider that does not need any additional servers or licenses. See VMware Tech Zone Windows 11 Support on vSphere.
- In vSphere Client, in Inventory, click the vCenter object. On the right, on the Configure tab, scroll down to Key Providers and add a Native Key Provider.
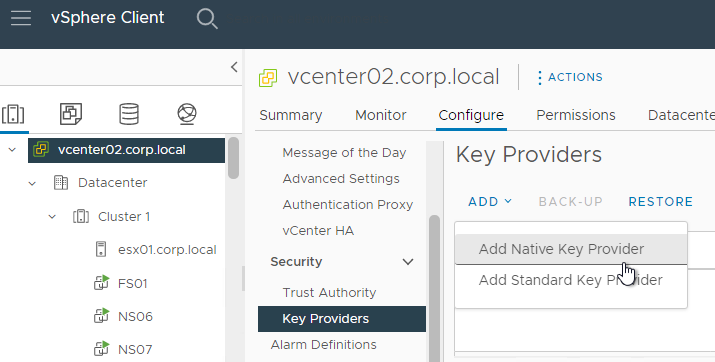
- After it’s added, select it and then click Back-up to activate it.
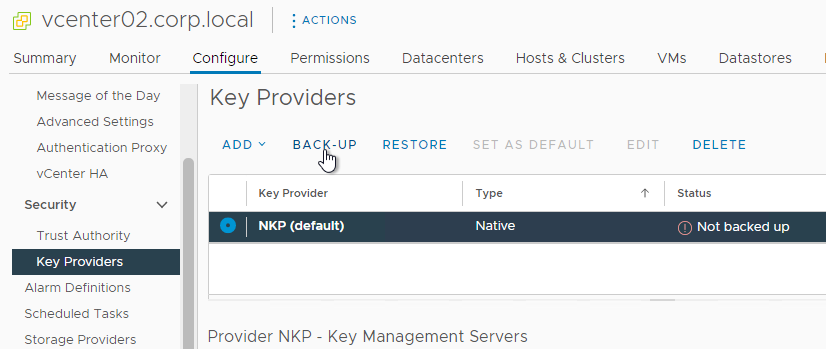
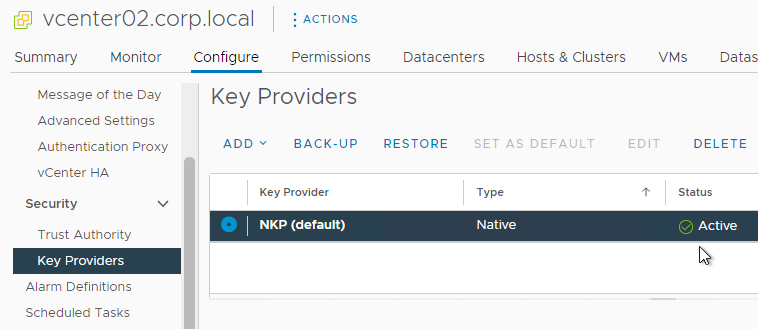
- In vSphere Client, in Inventory, click the vCenter object. On the right, on the Configure tab, scroll down to Key Providers and add a Native Key Provider.
- Microsoft TechNet Blog – Say No to Windows 10 Long Term Servicing Channel (LTSC)
- No Edge
- From January 2020, Microsoft Office 365 will not be supported on LTSC.
- Non-security operating system fixes and enhancements may not get back-ported to LTSC.
- CTX224843 Windows 10 compatibility with Citrix Virtual Desktops (XenDesktop). This article also has links to several other articles listing known issues with Windows 10 releases.
- Hypervisor Support – CTX131239 Supported Hypervisors for Virtual Desktops (XenDesktop) and Provisioning Services
- Firewall – the UDP-based EDT protocol is enabled by default. Make sure the UDP ports are open for ICA/HDX:
- UDP 1494
- UDP 2598
- UDP 443 – from Internet to Citrix Gateway.
- UDP 443 can also be used by internal ICA connections if VDA SSL is configured.
- For EDT through Citrix Gateway, make sure your Citrix ADC firmware is up to date, preferably 12.1 or newer. Then enable DTLS on the Gateway Virtual Server.
- VDA virtual machine sizing:
- For Windows 11 or Windows 10 virtual desktops, give the virtual machine: 2+ vCPU and 4+ GB of RAM – higher RAM for browsers
- For Windows Server 2022, 2019, or 2016 RDSH, give the virtual machine 8 vCPU, and 24-48 GB of RAM
- See Daniel Feller Sizing Windows 2016, Windows 2012 And Windows 10 Virtual Machines
- If using RAM caching (MCSIO or PvS), add more RAM for the cache.
- Remove the floppy drive.
- Remove any serial or LPT ports.
- If Windows 11 on vSphere:
- When creating the Windows 11 virtual machine, enable Encrypt this virtual machine.
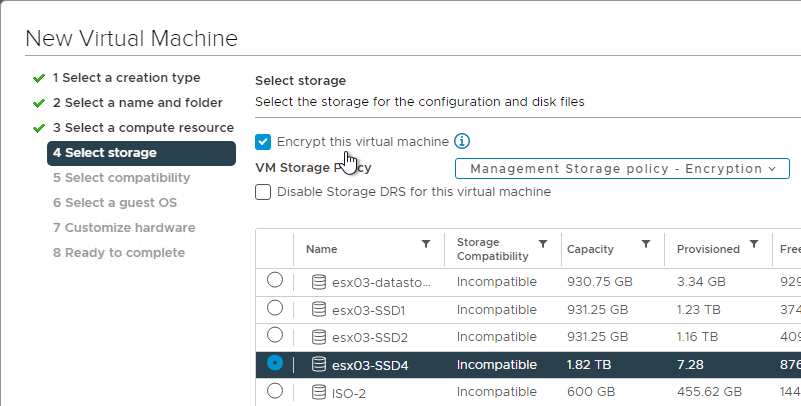
- In the Select a guest OS screen, if you don’t see Windows 11, then select Windows 10.
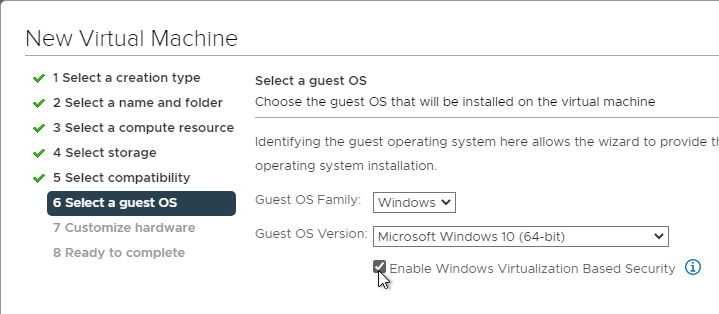
- On the Customize hardware page, make sure VM configuration files are encrypted. Hard disk encryption is not required and you can deselect it. Only the VM configuration files must be encrypted.
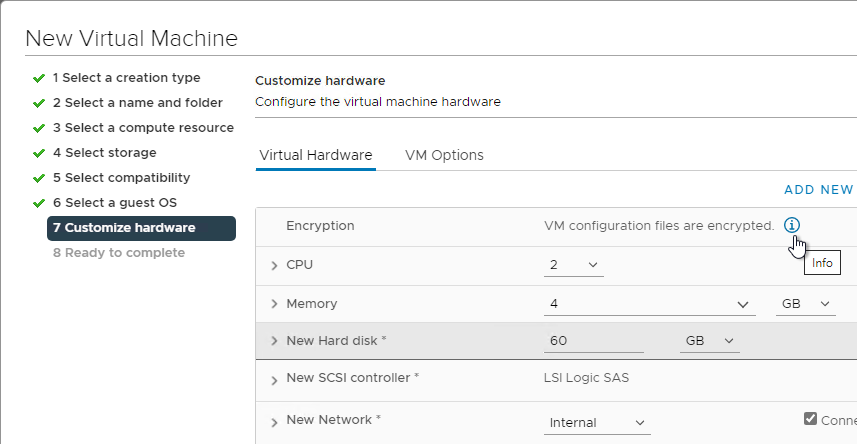
- Then you can use the Add New Device drop-down to add a Trusted Platform Module.
- When creating the Windows 11 virtual machine, enable Encrypt this virtual machine.
- If vSphere:
- To reduce disk space, reserve memory. Memory reservations reduce the size or eliminate the virtual machine .vswp file.
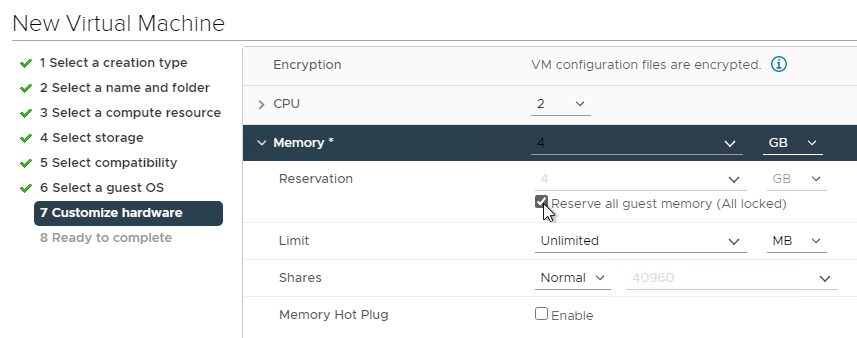
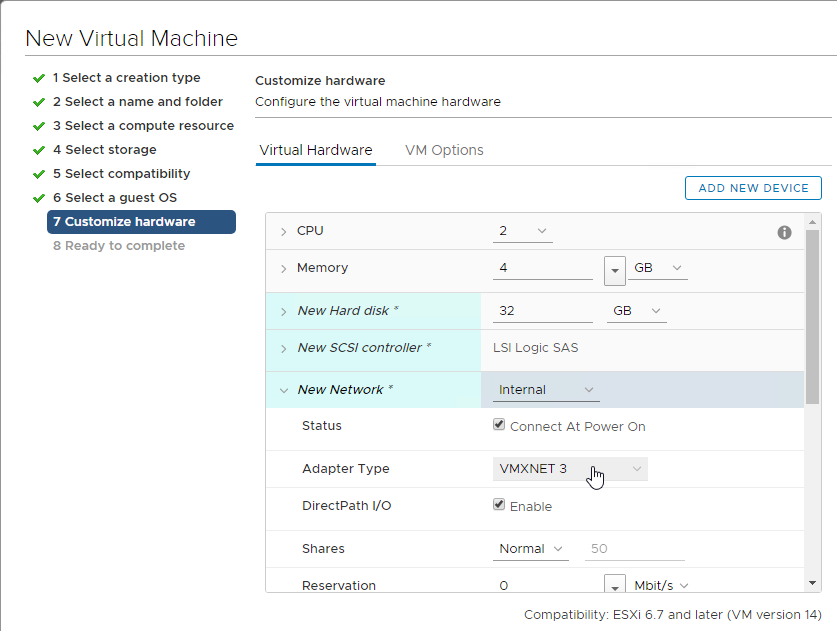
- The NIC should be VMXNET3.
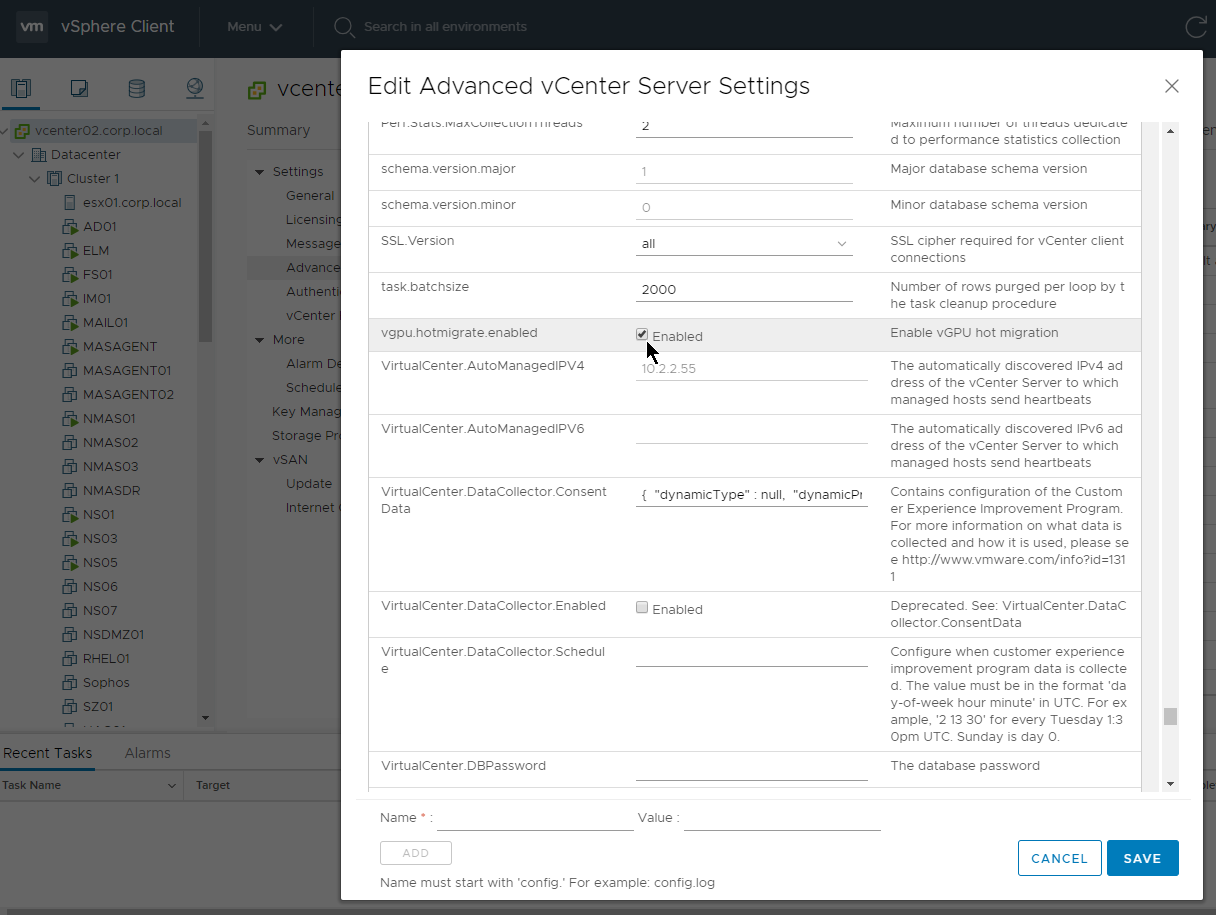
- For vGPU, set vgpu.hotmigrate.enabled Advanced vCenter Server Setting to true. (source = William Lam How to enable vGPU vMotion in vSphere 6.7 Update 1)
- To reduce disk space, reserve memory. Memory reservations reduce the size or eliminate the virtual machine .vswp file.
- App Layering and UEFI – Citrix App Layering 2003 and newer can import UEFI images by running a script instead of using a connector.
- If this VDA will boot from Citrix Provisioning:
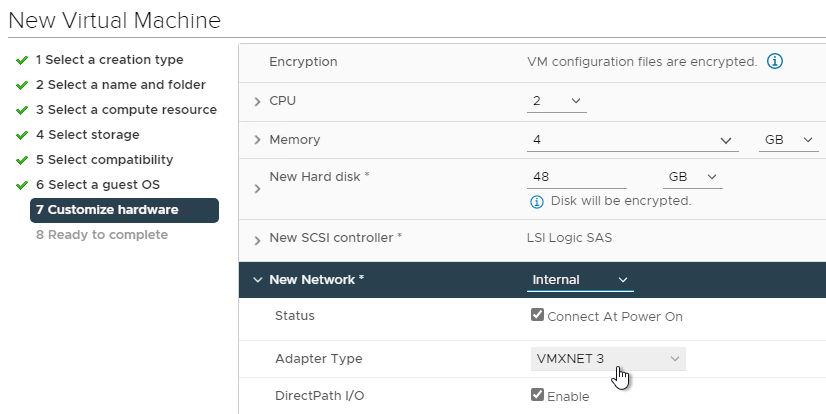
- For vSphere, the NIC Adapter Type must be VMXNET3.
- For vSphere, configure the CD/DVD Drive to boot from IDE instead of SATA. SATA won’t work with PVS.
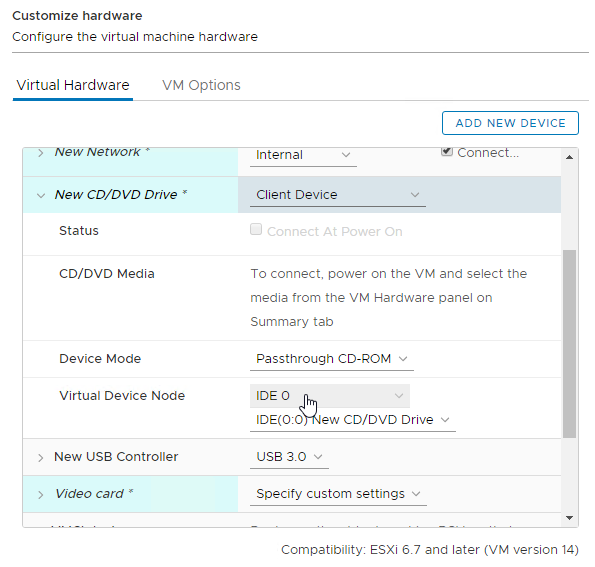
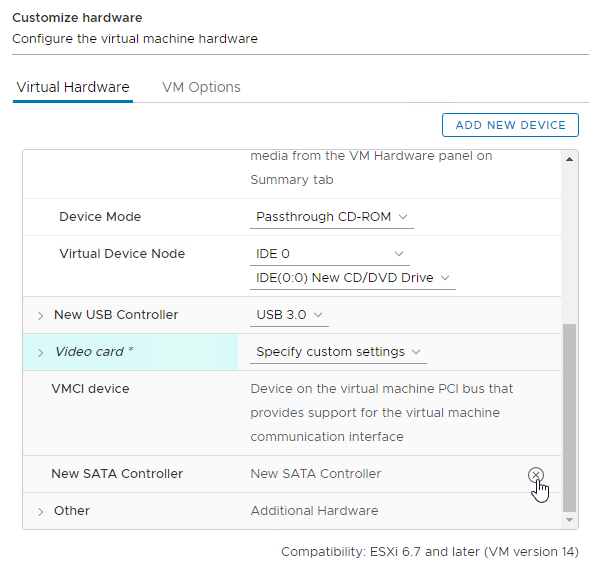
- Make sure you remove the SATA Controller after you change the CD/DVD Drive to be IDE.
- For vSphere, the NIC Adapter Type must be VMXNET3.
- Install the latest version of hypervisor drivers (e.g. VMware Tools).
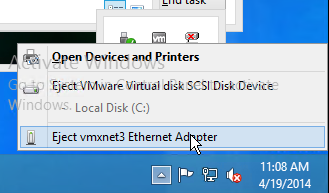
If vSphere, disable NIC Hotplug
- Users could use the systray icon to Eject the Ethernet Controller. Obviously this is bad.
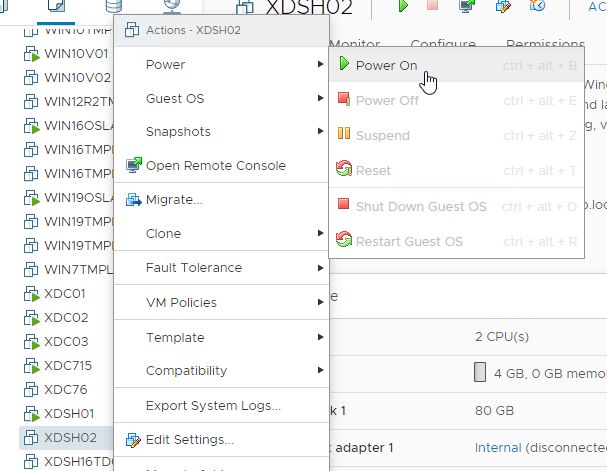
- To disable this functionality, power off the virtual machine.
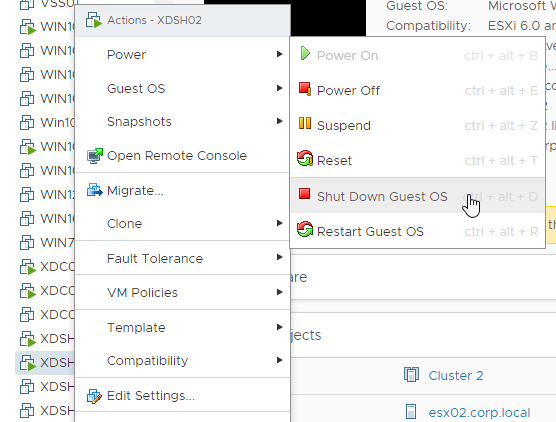
- Once powered off, right-click the virtual machine, and click Edit Settings.
- Switch to the tab named VM Options.
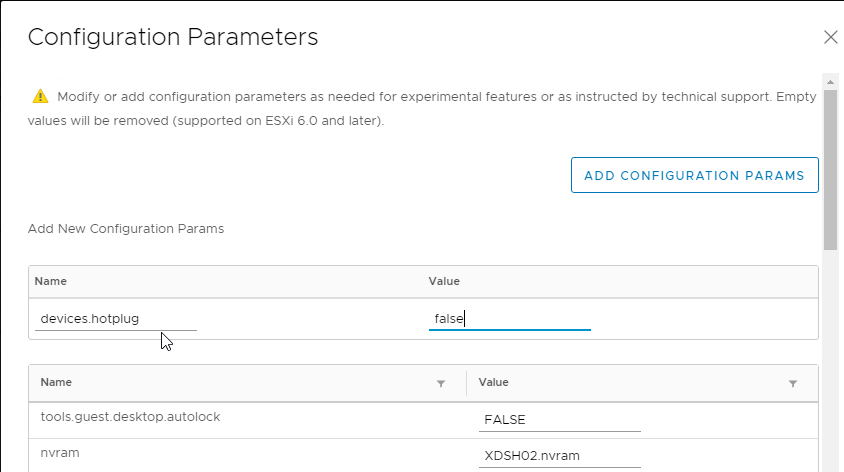
- Expand Advanced and then click Edit Configuration.
- Click the button labelled Add Configuration Params.
- For the Name, enter devices.hotplug.
- For the Value, enter false. Then click OK.
- The VM can then be powered on.
Windows Preparation
- Computer Group Policy – Make sure the Master VM is in the same OU as the Linked Clones so that the Master VM will get the computer-level GPO settings in its registry. Run gpupdate on the master after moving the VM to the correct OU. When Clones are created from the Master, the computer-level GPO settings will already be applied, thus eliminating timing issues.
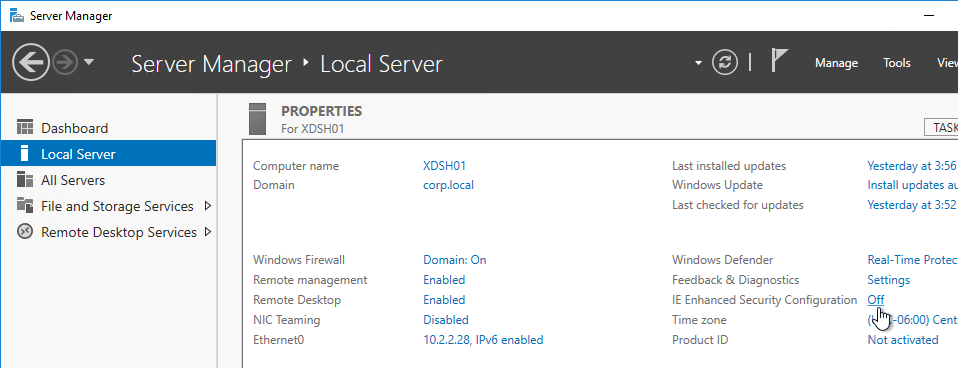
- If Server OS, disable IE Enhanced Security Configuration in Server Manager > Local Server.
- Run Windows Update. Do not skip this step. Many VDA installation problems are fixed by simply updating Windows.
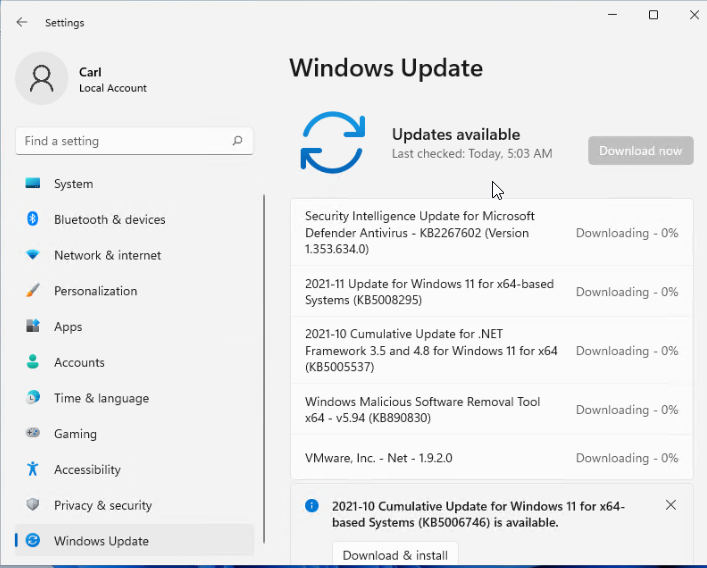
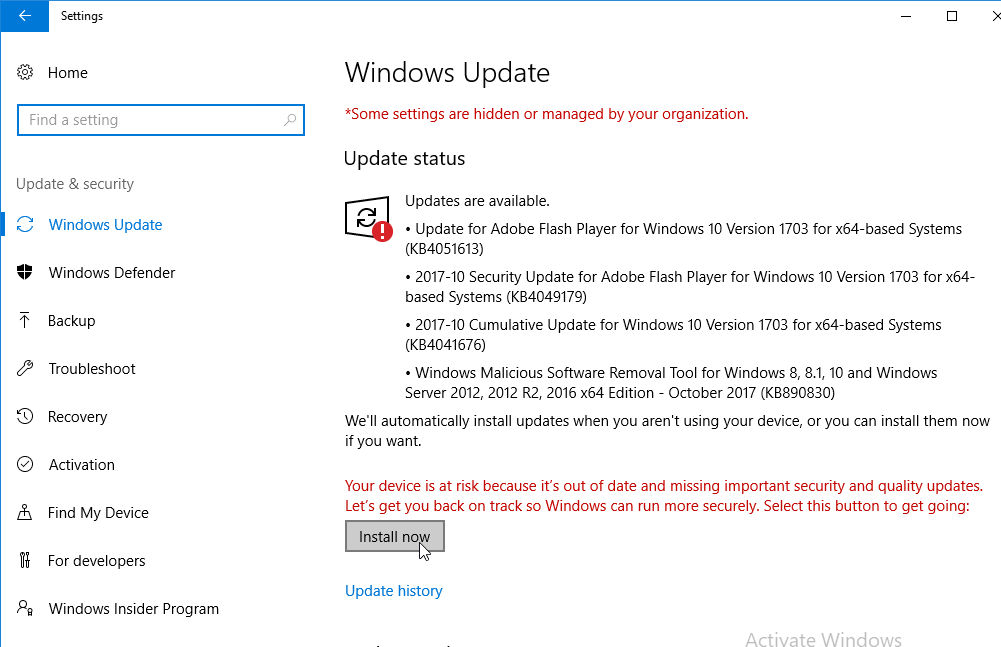
- Defer Feature Updates – For Windows 10, since Citrix VDA does not immediately support new Windows 10 versions, configure Windows Update to defer feature updates. In Windows 11, or in newer versions of Windows 10, defer updates can only be configured using group policy.
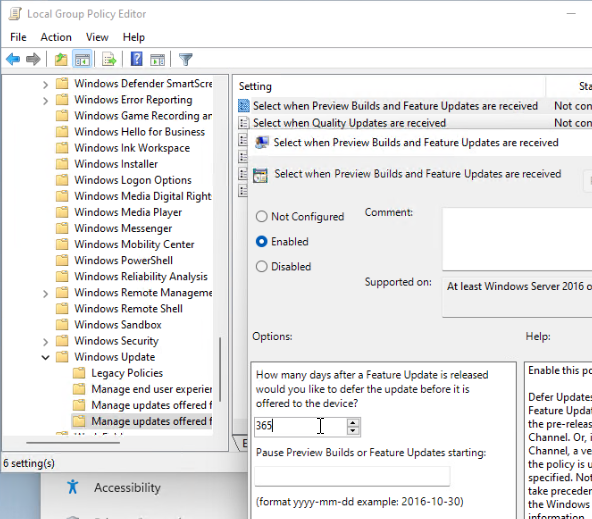
- Defer Feature Updates – For Windows 10, since Citrix VDA does not immediately support new Windows 10 versions, configure Windows Update to defer feature updates. In Windows 11, or in newer versions of Windows 10, defer updates can only be configured using group policy.
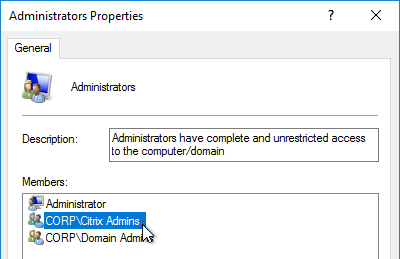
- Add your Citrix Administrators group to the local Administrators group on the VDA. Computer Management.
- The Remote Desktop Services “Prompt for Password” policy prevents Single Sign-on to the Virtual Delivery Agent. Check registry key
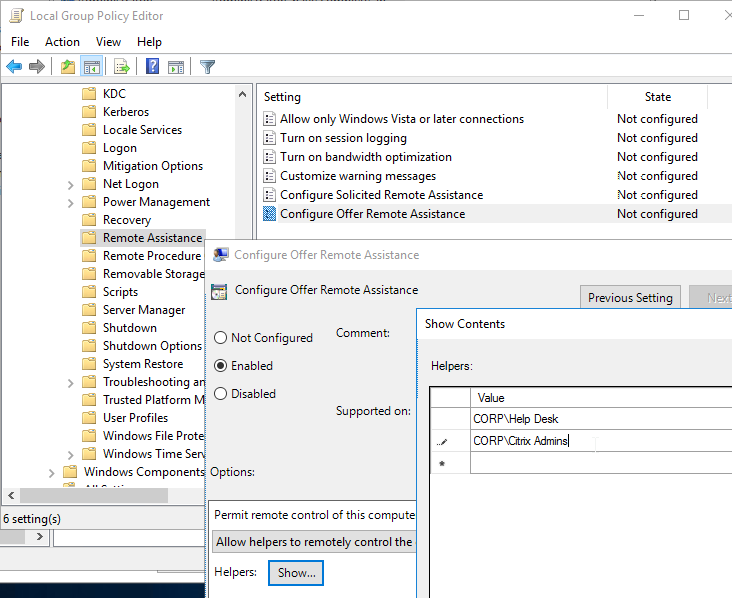
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Terminal Services. If fPromptForPassword = 1 then you need to fix group policy. The following GPO setting will prevent Single Sign-on from working.Computer Configuration | Policies | Administrative Templates | Windows Components | Remote Desktop Services | Remote Desktop Session Host | Security | Always prompt for password upon connectionOr set the registry valueHKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Portica\AutoLogon (DWORD) = 0x1. This registry value only applies to Single-session OS (aka Desktop OS), not Multi-session OS (aka Server OS). (source = comments) - For Remote Assistance in Citrix Director, configure the GPO setting Computer Configuration | Policies | Administrative Templates | System | Remote Assistance | Offer Remote Assistance. See Jason Samuel – How to setup Citrix Director Shadowing with Remote Assistance using Group Policy for more details.
Install/Upgrade Virtual Delivery Agent (VDA) 2203 LTSR CU6
Mixed versions – You can upgrade the VDAs before you upgrade the Delivery Controllers resulting in VDAs being newer than the Delivery Controllers. You can upgrade the Delivery Controllers before you upgrade the VDAs. In other words, you can mix and match VDA versions and Delivery Controller versions.
For a list of HDX improvements in VDA 2203 LTSR, see Citrix Blog Post Get to know the top HDX enhancements in the 2203 LTSR.
CLI Install:
Command Line Install Options are detailed at Install using the command line at Citrix Docs.
Scripted Upgrade:
To automate the upgrade of VDA software on persistent machines, see Dennis Parker at How to automate unattended VDA upgrade at Citrix Discussions for a sample script.
GUI Install:
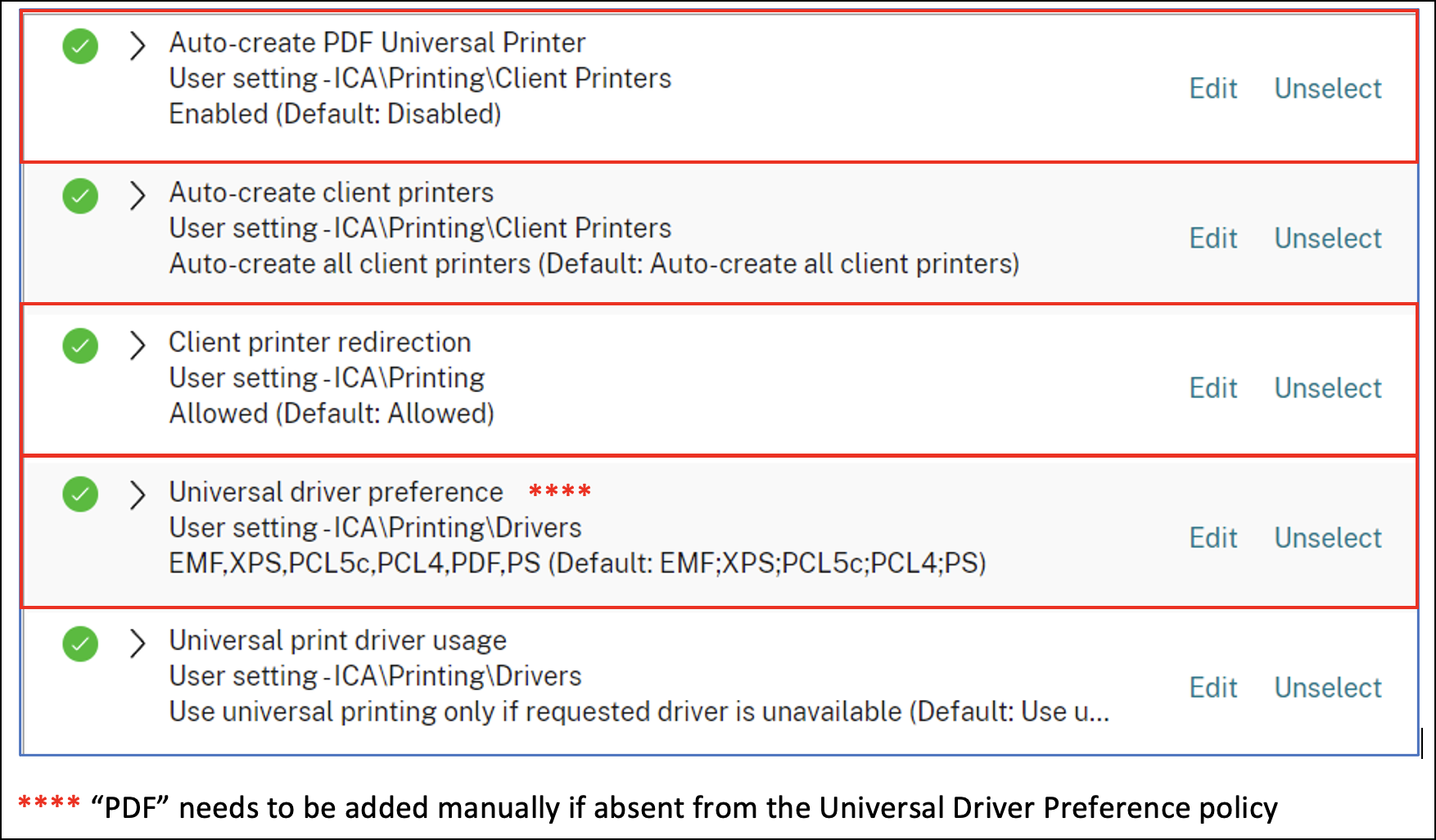
- Virtual Channel Allow List – the Citrix Policy setting named Virtual Channel Allow List is enabled by default in VDA 2203. Whitelist your non-Citrix (e.g., Zoom) virtual channels before upgrading your VDAs, or else your non-Citrix virtual channels will stop working.
- NVIDIA – ensure your NVIDIA Virtual GPU software supports the version of VDA that you are upgrading to.
- CU6 – Download the CVAD 2203 CU6 ISO.
- Mount the ISO and run AutoSelect.exe.
- Click either of the Start buttons. Both buttons do the same thing.
- On the top right, click Virtual Delivery Agent.
- In the Environment page, select Create a master MCS Image or Create a master image using Citrix Provisioning, and click Next.
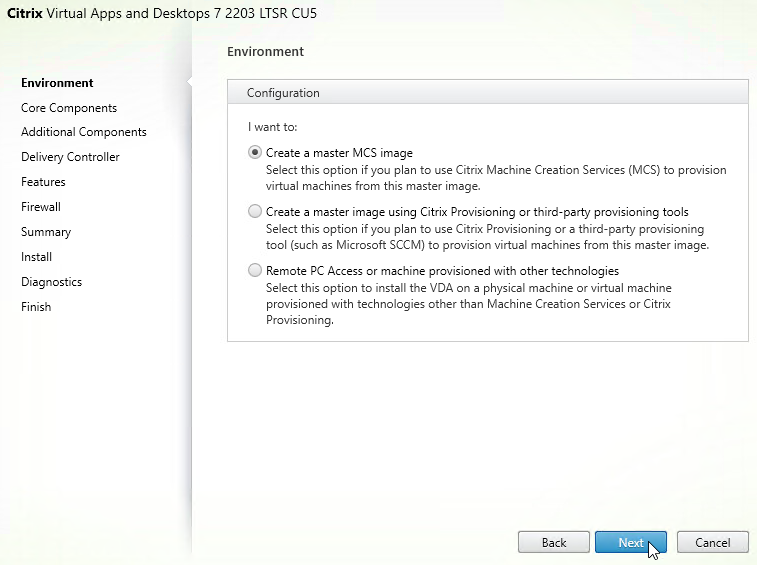
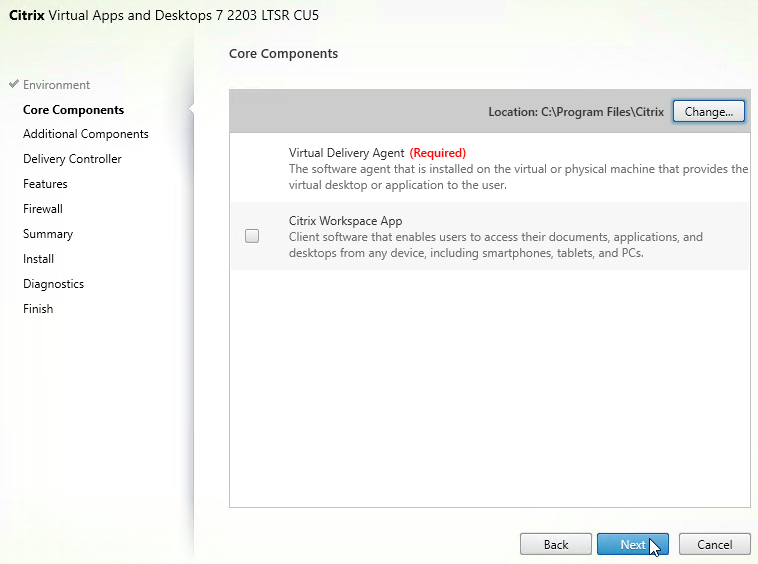
- In the Core Components page, if you don’t need Citrix Workspace App installed on your VDA, then leave it unchecked. Workspace app is usually only needed for double-hop ICA connections (connect to first VDA, and then from there, connect to second VDA). Click Next.
- In the Additional Components page:
- VDA has an option to install the Workspace Environment Management agent, but this option has been deprecated.
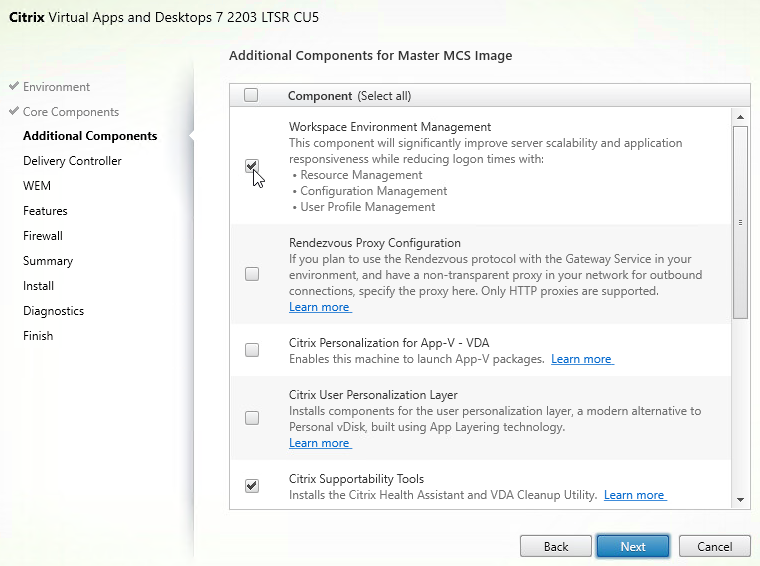
- Single-session OS (not Multi-session OS) has an option for Citrix User Personalization Layer (UPL). This component comes from Citrix App Layering but does not need any of the App Layering infrastructure.
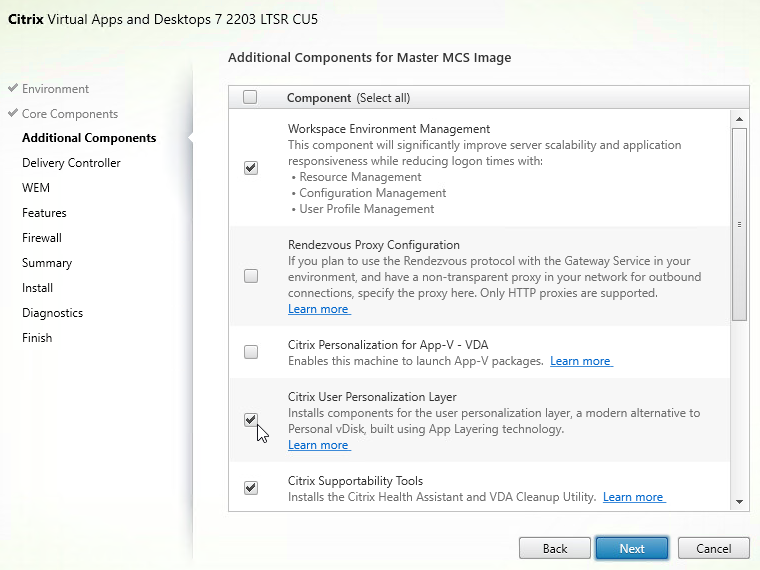
- Do not enable User Personalization Layer if you are also using Citrix App Layering.
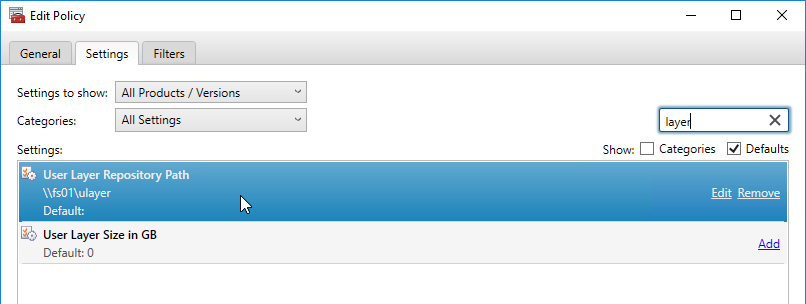
- Warning: A Citrix Policy setting activates Citrix User Personalization Layer by setting the UNC path to where the User Personalization Layers should be stored. The Citrix Policy setting should only be deployed to non-persistent machines. If you deploy the Citrix Policy Setting to your Master Image, then your Master Image will be hosed, and you must rebuild it from scratch.
- There’s an option for Machine Creation Services (MCS) storage optimization. This is also known as MCS I/O. This feature is only needed if you have slow storage.
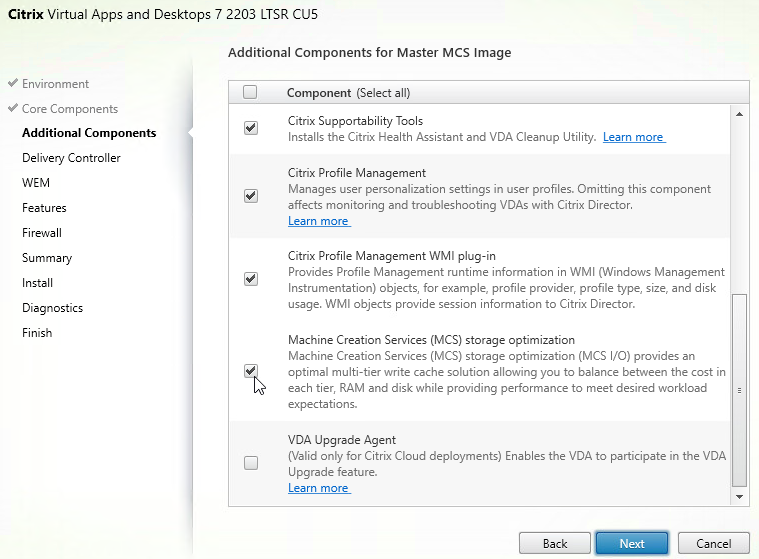
- VDA has an option to install the Workspace Environment Management agent, but this option has been deprecated.
- Click Next.
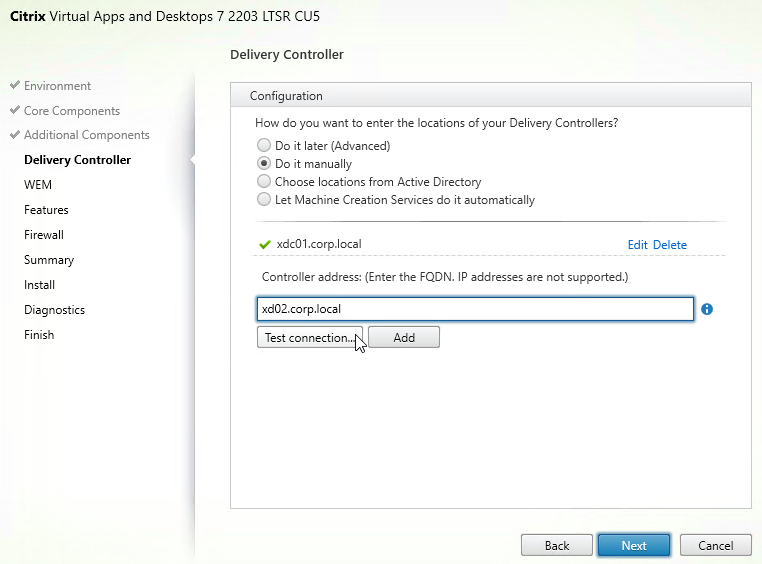
- In the Delivery Controller page, select Do it manually. Enter the FQDN of each Delivery Controller (at least two). Click Test connection. And then make sure you click Add. Click Next when done.
- If you see the WEM page, change it to WEM On-Premises, enter the address of the WEM Server, click Test connection, and then click Add. Click Next.
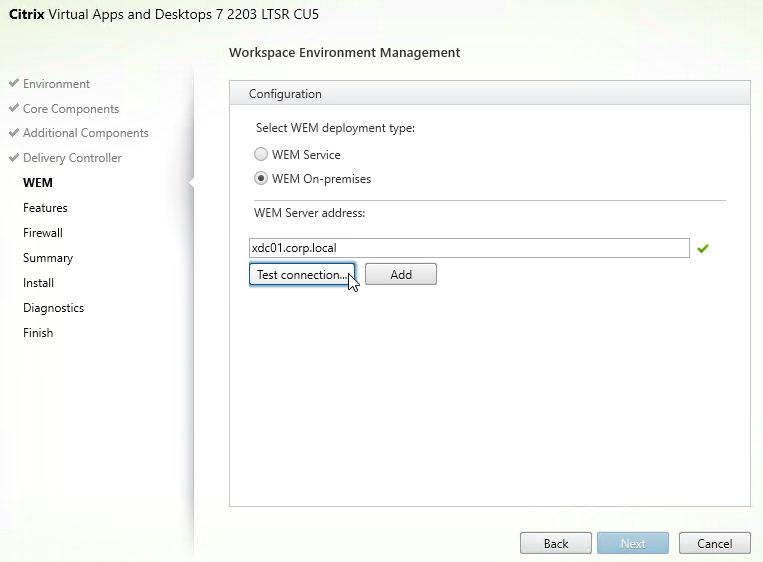
- In the Features page, if you want to use the features, then check the boxes. Remote Assistance is for Director. Use Screen Sharing allows users to share their sessions with other users. Then click Next.
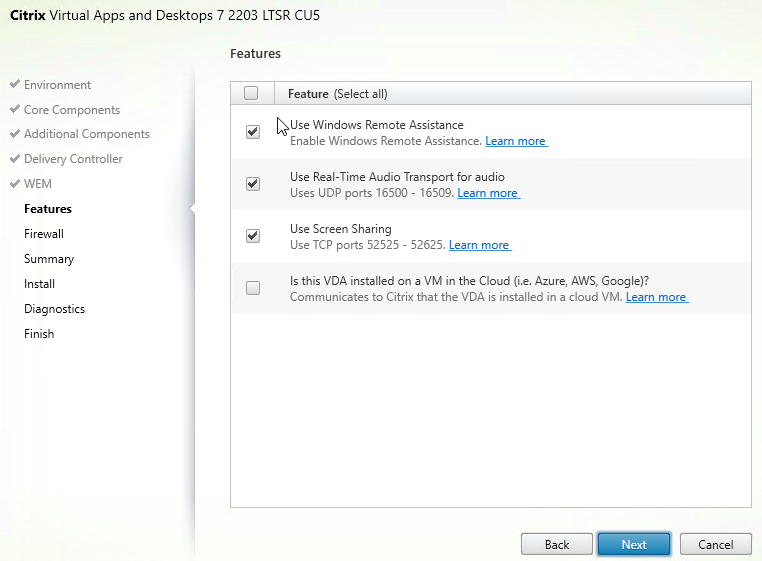
- In the Firewall page, there are ports 52525 – 52625 for Screen Sharing. Click Next.
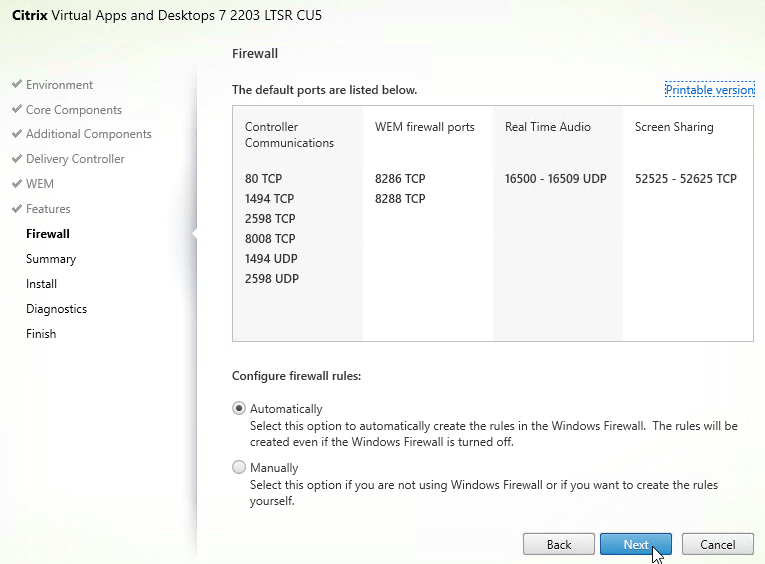
- In the Summary page, there’s an optional Enable restore on failure checkbox. click Install.
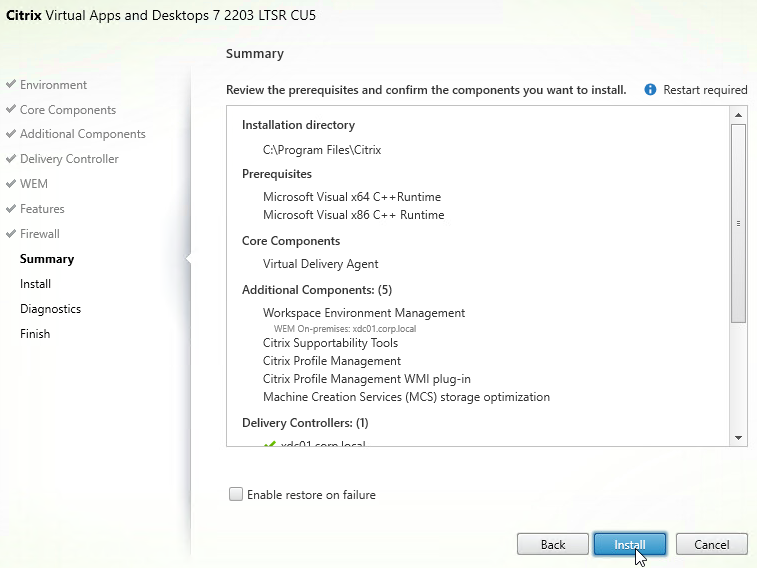
- Click Close if you are prompted to restart.
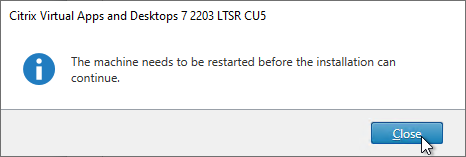
- After the machine reboots, login and installation should continue.
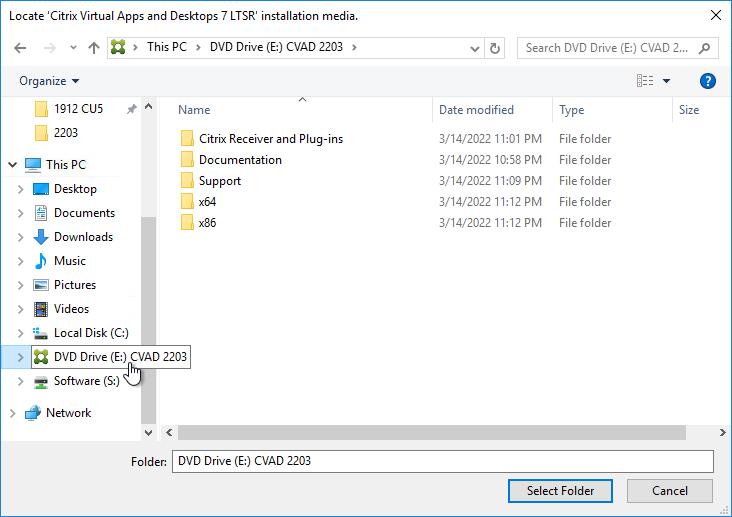
- After the reboot, and after logging in again, you might see a Locate ‘Citrix Virtual Apps and Desktops 7 LTSR’ installation media window. Don’t click anything yet.
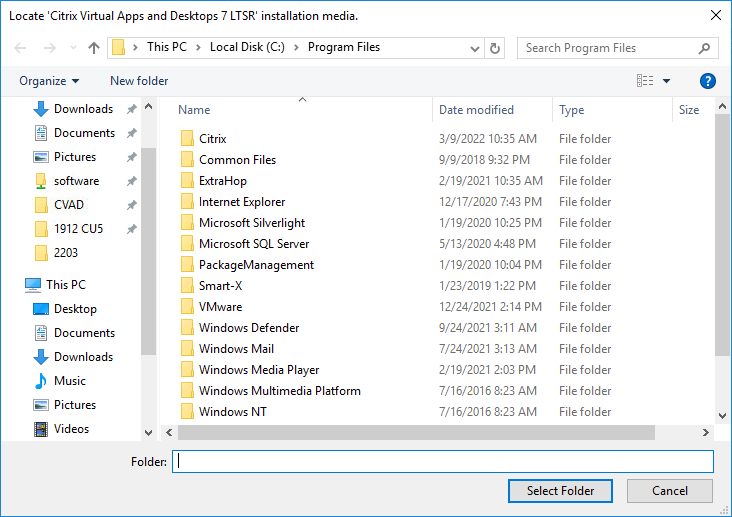
- Go to the Citrix_Virtual_Apps_and_Desktops_7_2203_5000.iso file and mount it.
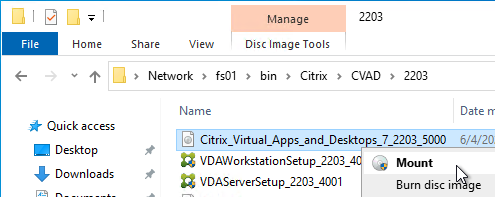
- Go back to the Locate ‘Citrix Virtual Apps and Desktops 7 LTSR’ installation media window.
- On the left, expand This PC, and click the DVD Drive.
- Click Select Folder.
- Installation will resume. Repeat these instructions after each reboot.
- After the reboot, and after logging in again, you might see a Locate ‘Citrix Virtual Apps and Desktops 7 LTSR’ installation media window. Don’t click anything yet.
- Note: NT SERVICE\CitrixTelemetryService needs permission to login as a service.
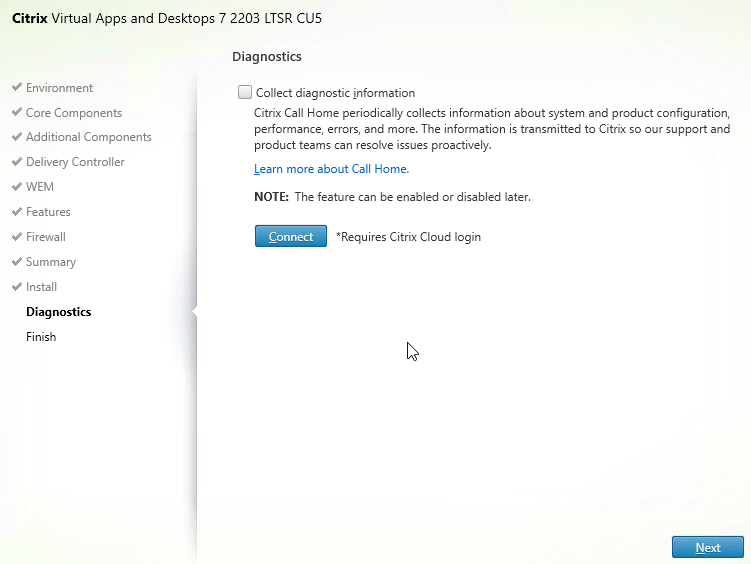
- In the Diagnostics page, you can optionally check the box next to Collect diagnostic information, click Connect, enter your Citrix account credentials, and then click Next.
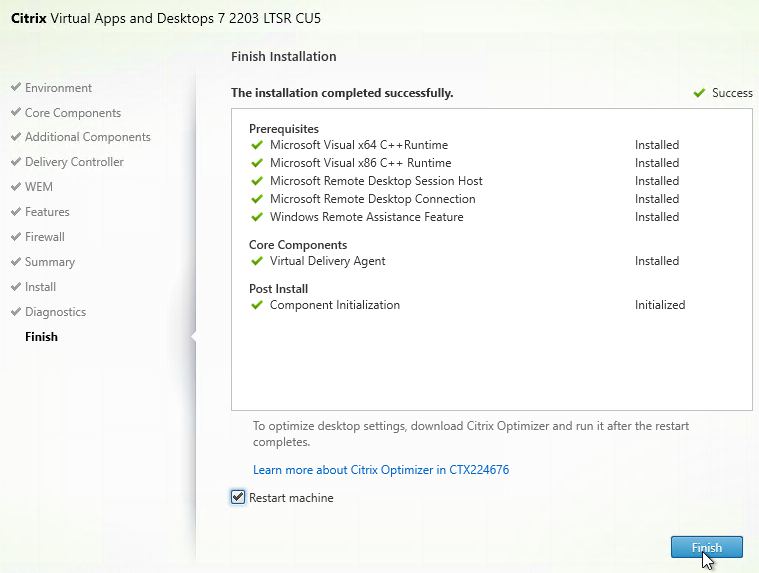
- In the Finish page, click Finish to restart the machine again.
- From CTX225819 When Launching an Application Published from Windows Server 2016, a Black Screen Appears for Several Seconds Before Application is Visible
- HKLM\SOFTWARE\Citrix\Citrix Virtual Desktop Agent\DisableLogonUISuppression (DWORD) should be set to 0.
If you need to roam the user’s Outlook .OST file (Outlook Cached Mode), Outlook Search Index, OneDrive cache, OneNote data, SharePoint data, Skype data, and/or Teams data, then download, install, and configure Microsoft FSLogix. FSLogix has more Office roaming features than Citrix Profile Management. A common architecture is to enable FSLogix Office Container for the Office cache files and use Citrix Profile Management for all other roaming profile files and registry keys.
Microsoft FSLogix is free for all Microsoft RDS CALs, Microsoft Virtual Desktop Access per-user CALs, and all Microsoft Enterprise E3/E5 per-user licenses. Notice that per-device licenses are excluded. See Licensing Requirements at Microsoft Docs.
Do the following to install Microsoft FSLogix on the VDA machine:
- Go to https://docs.microsoft.com/en-us/fslogix/install-ht and click the download link.
- Extract the downloaded .zip file.
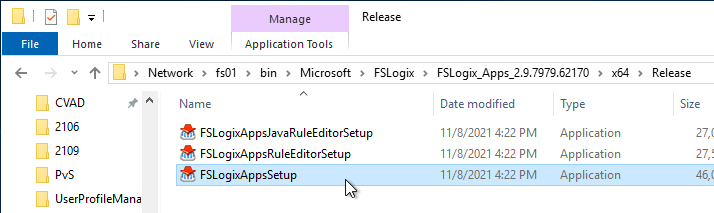
- In the FSLogix \x64\Release folder, run FSLogixAppsSetup.exe.
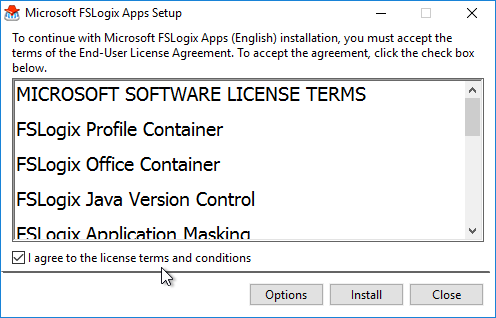
- Check the box next to I agree to the license terms and conditions and click Install.
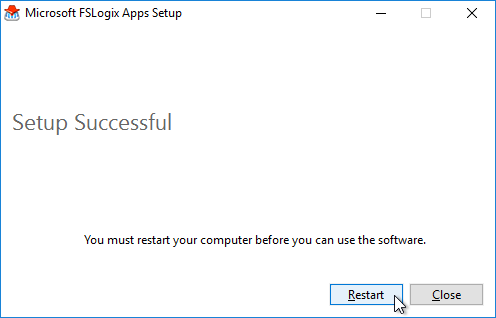
- In the Setup Successful page, click Restart.
- The installed version is shown in Apps & features.
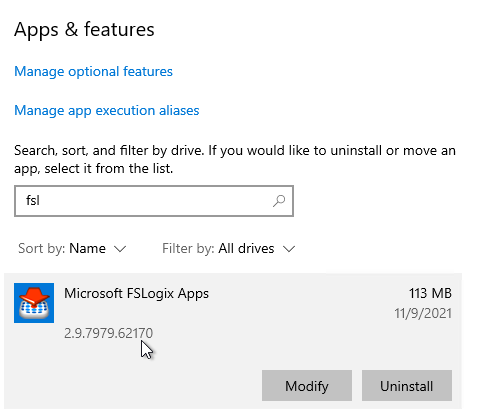
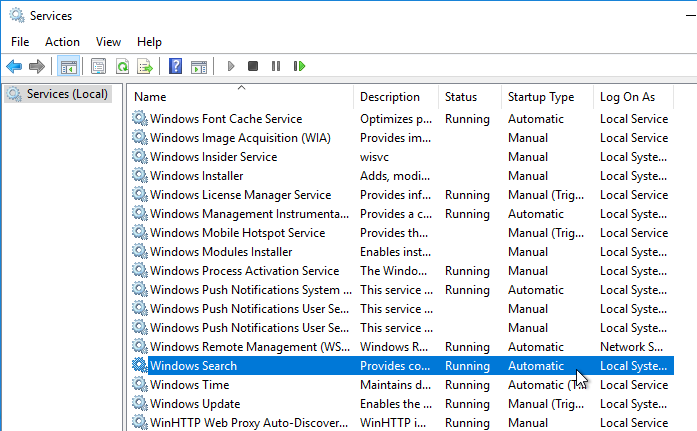
- Make sure the Windows Search service is set to Automatic and Running.
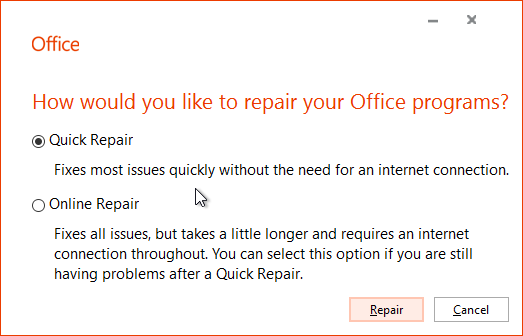
- If Office is already installed, then repair the Office installation after installing and starting the Windows Search Service.
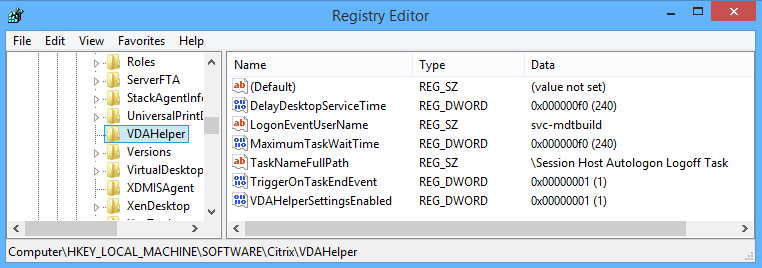
FSLogix is configured through Group Policy or by editing registry values on each FSLogix Agent machine.
Citrix Desktop Service
To prevent Citrix Desktop Service (BrokerAgent) from starting and registering with the Delivery Controllers before the boot process is complete, see Jeremy Saunders Controlling the Starting of the Citrix Desktop Service (BrokerAgent).
Customer Experience Improvement Program (CEIP)
Customer Experience Improvement Program (CEIP) is enabled by default. To disable it, create the registry value HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Telemetry\CEIP\Enabled (DWORD), and set it to 0 (zero). Also see CEIP at Citrix Insight Services at Citrix Docs.
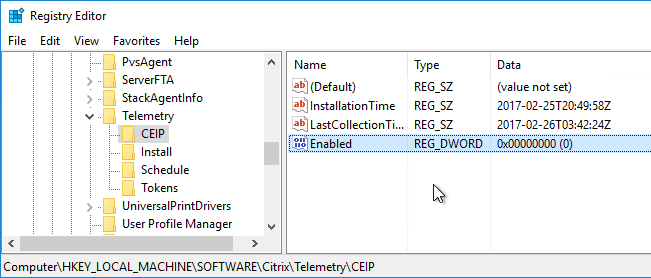
See https://www.carlstalhood.com/delivery-controller-2203-ltsr-and-licensing/#ceip for additional places where CEIP is enabled.
Connection Quality Indicator
The Connection Quality Indicator tells the user the quality of the connection. Position of the indicator is configurable by the user. Thresholds are configurable through group policy.
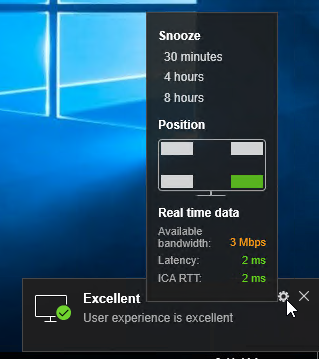
Download it from CTX220774 Connection Quality Indicator and install it. The article is very detailed.
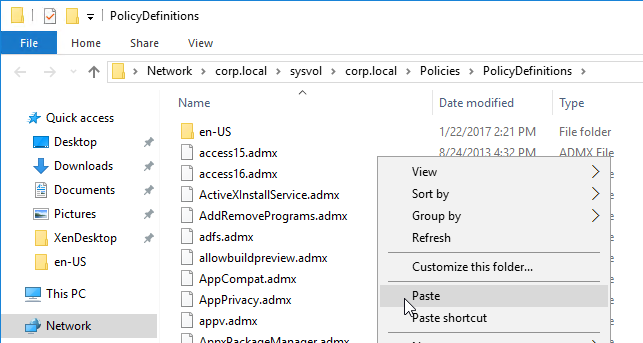
Group Policy templates are located at C:\Program Files (x86)\Citrix\Connection Quality Indicator\Configuration. Copy the files and folder to <Sysvol>\Policies\PolicyDefinitions, or C:\Windows\PolicyDefinitions.
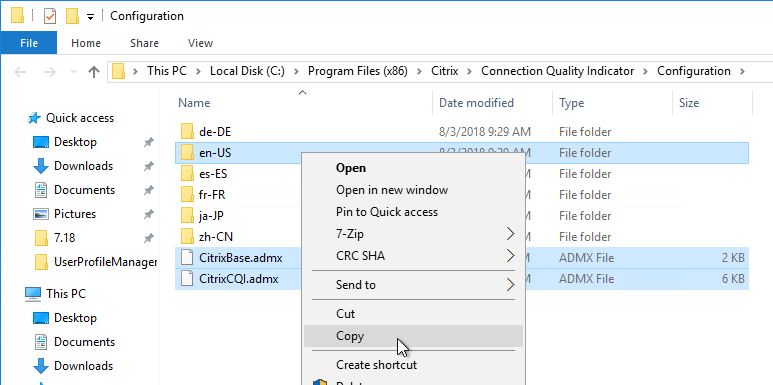
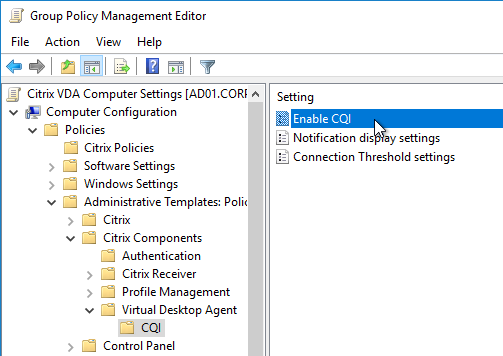
Find the Group Policy settings under Computer Config | Policies | Administrative Templates | Citrix Components | Virtual Desktop Agent | CQI
The user half of a GPO lets you disable CQI for some users and enable it for others.
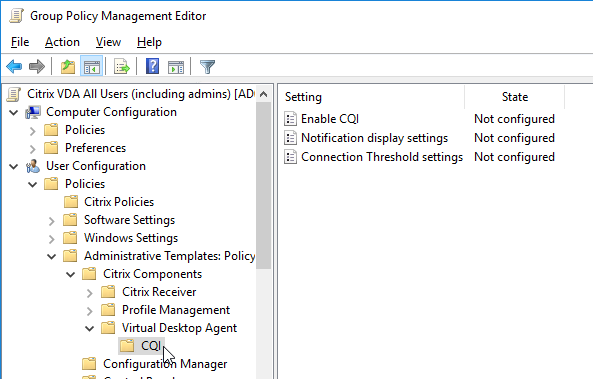
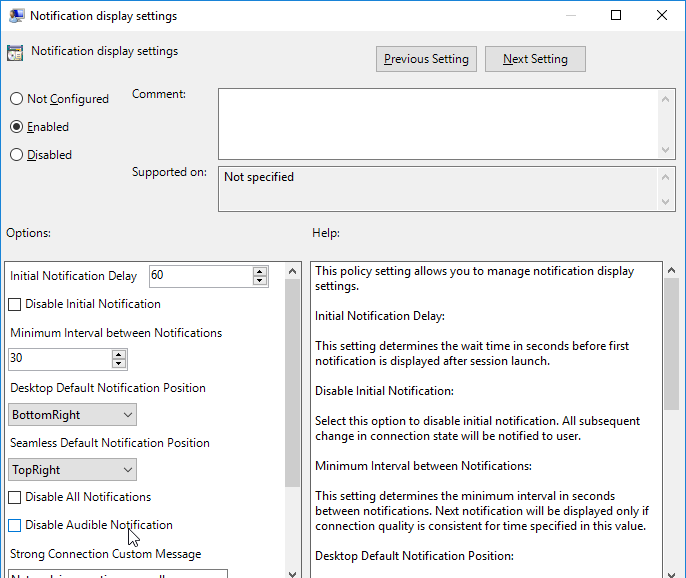
Notification display settings lets you customize the user notifications, or disable them.
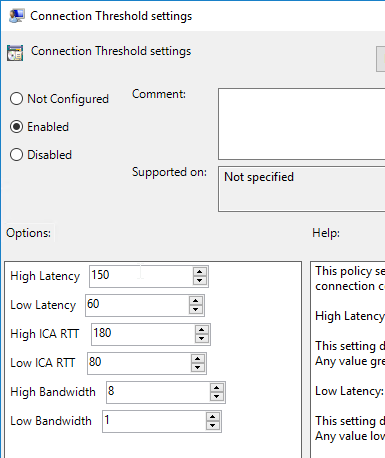
Connection Threshold Settings lets you set the notification thresholds.
Adaptive Transport
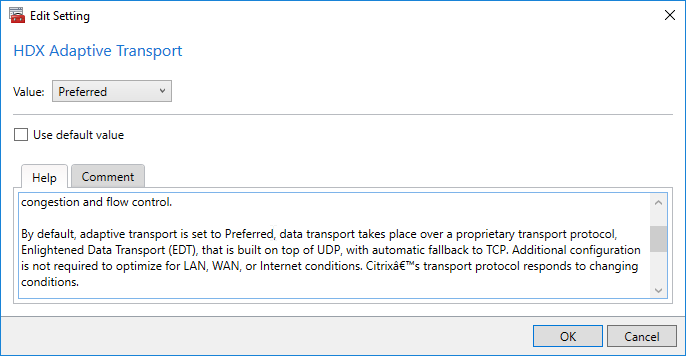
Adaptive Transport is a HDX/ICA protocol feature that tries to use UDP ports (EDT protocol) if they are open, and falls back to TCP ICA if UDP connection is not successful. On higher latency connections, EDT (UDP) tends to perform better than traditional TCP ICA.
The Citrix Policy setting HDX Adaptive Transport defaults to Preferred, which means Adaptive Transport is enabled by default.
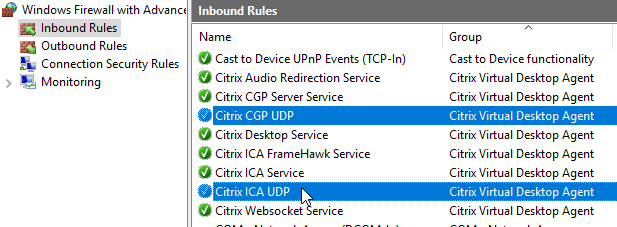
The Citrix EDT protocol use UDP Ports 1494/2598 for HDX connections to the VDA. The UDP ports should already be open in the VDA’s Windows Firewall. In other words, HDX/ICA uses both TCP and UDP ports.
For EDT (and Adaptive Transport) through Citrix Gateway, make sure your Citrix ADC firmware is up to date, preferably 12.1 or newer. Then make sure DTLS is enabled on the Gateway Virtual Server. DTLS is the UDP version of SSL/TLS. Also, open UDP 2598 and UDP 1494 from the ADC SNIP to the VDAs.
Verify that the VDA registered with a Controller
- If you restart the Virtual Delivery Agent machine, or restart the Citrix Desktop Service…
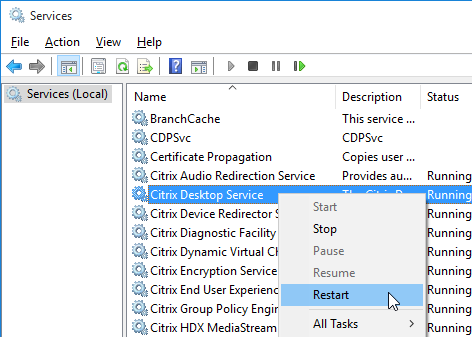
- In Windows Logs > Application log, you should see an event 1012 from Citrix Desktop Service saying that it successfully registered with a controller.
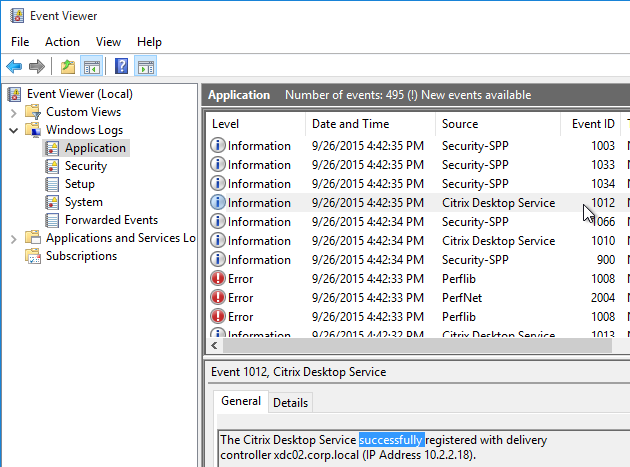
- If you don’t see successful registration, then you’ll need to fix the ListOfDDCs registry key.
- See VDA registration with Controllers at Citrix Docs.
- See The Most Common VDA Registration Issues & Troubleshooting Steps at Citrix Blogs.
- You can also run Citrix’s Health Assistant on the VDA.
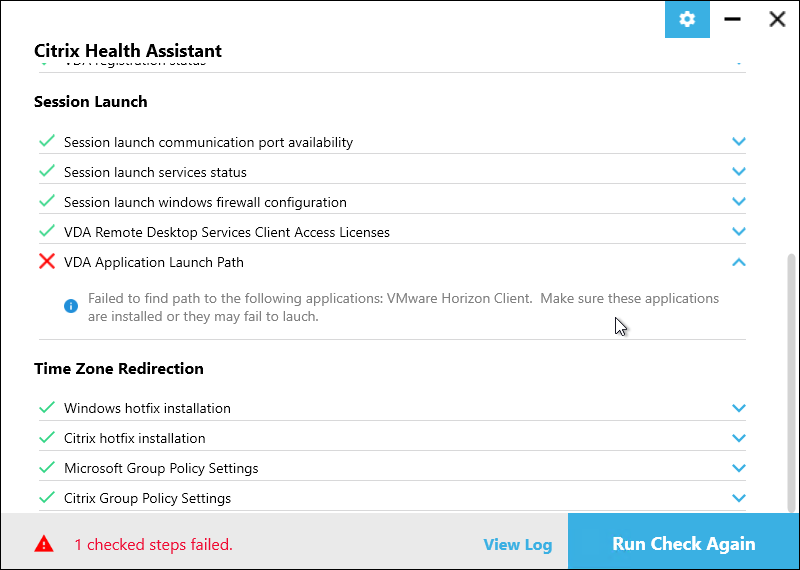
Citrix Workspace app
If you want to run Workspace app on the VDA machine, then install or upgrade.
Download and install Workspace app:
- Download Citrix Workspace app 2409.1 (Current Release).
- Or download Citrix Workspace app 2402 CU2 (aka 24.02.2000) LTSR.
- Or download Citrix Workspace app 2402 CU2 (aka 24.02.2000) LTSR.
- On the VDA, as administrator, run the downloaded CitrixWorkspaceApp.exe.
- In the Welcome to Citrix Workspace page, click Start.
- In the License Agreement page, check the box next to I accept the license agreement, and click Next.

- In the Enable Single Sign-on page, check the box next to Enable single sign-on, and click Install.

- In the Installation successful page, click Finish.

- Click Yes when asked to restart now.

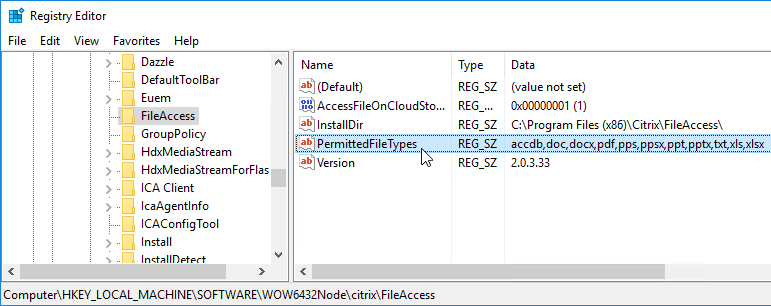
Citrix File Access 2.0.4 for Workspace app for Chrome
- If you support Workspace app for Chrome (Chromebook) and want published applications to open files on Google Drive, install Citrix File Access on the VDAs. Get it from the Citrix File Access for Chrome.
- Go to the extracted Citrix_File_Access_2.0.4, and run FileAccess.msi.
- In the Please read the File Access License Agreement page, check the box next to I accept the terms, and click Install.
- In the Completed the File Access Setup Wizard page, click Finish.
- File Access is listed in Apps & Features or Programs and Features as version 2.0.4.34.
- File Access has a default list of supported file extensions. The list can be expanded by editing the registry on the VDA. See CTX219983 Receiver for Chrome Error: Invalid command line arguments: Unable to open the file as it has an unsupported extension.
- To open a file from Google Drive, right-click and and open the file using Citrix Workspace app.
Remote Desktop Licensing Configuration
On Windows Server 2016 and newer RDSH, the only way to configure Remote Desktop Licensing is using group policy (local or domain). This procedure is not needed on virtual desktops.
- For local group policy, run gpedit.msc. Alternatively, you can configure this in a domain GPO.
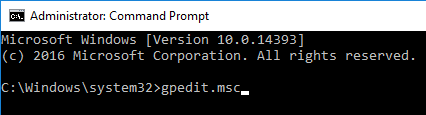
- Go to Computer Configuration > Administrative Templates > Windows Components > Remote Desktop Services > Remote Desktop Session Host > Licensing.
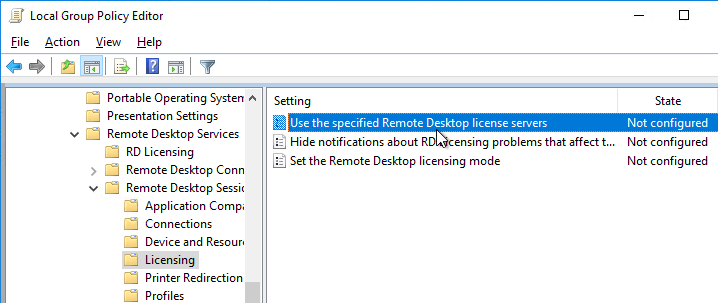
- Double-click Use the specified Remote Desktop license servers. Change it to Enabled, and enter the names of the RDS Licensing Servers (typically installed on Delivery Controllers). Click OK.
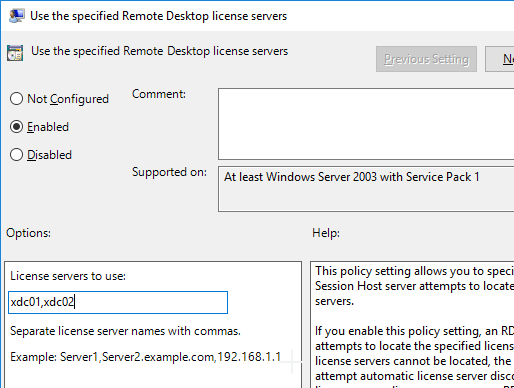
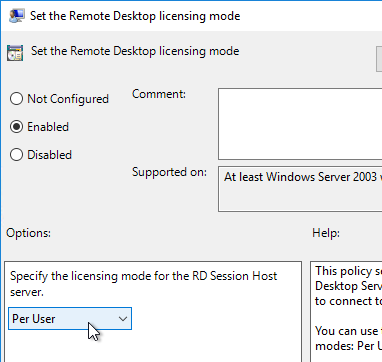
- Double-click Set the Remote Desktop licensing mode. Change it to Enabled and select Per User. Click OK.
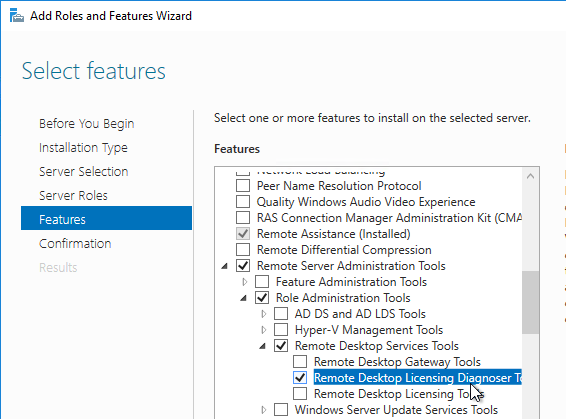
- Optionally, you can install the Remote Desktop Licensing Diagnoser Tool. In the Server Manager > Add Roles and Features Wizard, on the Features page, expand Remote Server Administration Tools, expand Role Administration Tools, expand Remote Desktop Services Tools, and select Remote Desktop Licensing Diagnoser Tool. Then Finish the wizard.
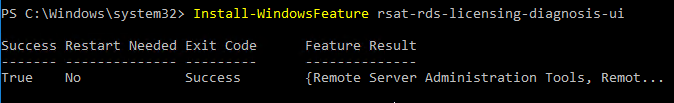
- If it won’t install from Server Manager, you can install it from PowerShell by running
Install-WindowsFeature rsat-rds-licensing-diagnosis-ui.
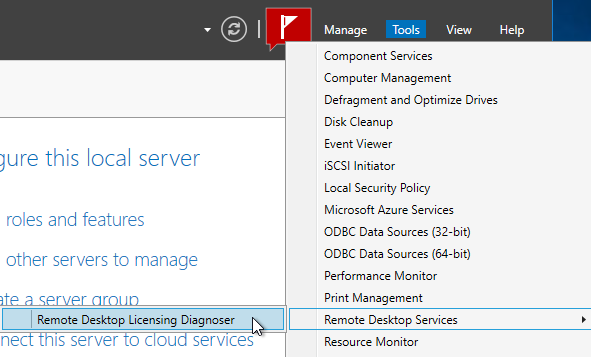
- In Server Manager, open the Tools menu, expand Remote Desktop Services (or Terminal Services), and click Remote Desktop Licensing Diagnoser.
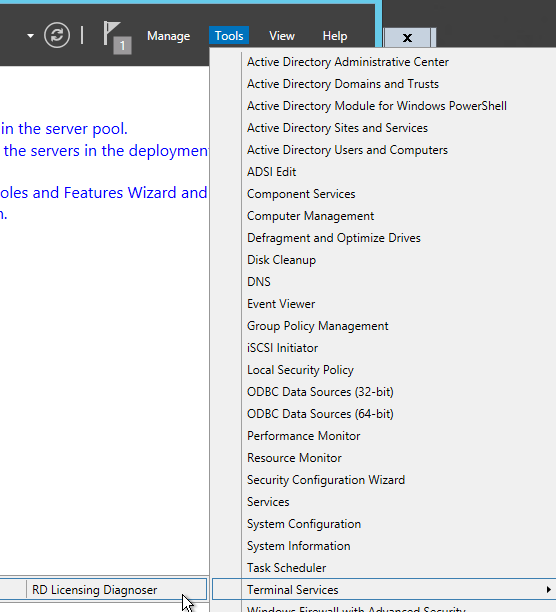
- The Diagnoser should find the license server and indicate the licensing mode. If you’re configured for Per User licenses, then it’s OK if there are no licenses installed on the Remote Desktop License Server.
Several people in Citrix Discussions reported the following issue: If you see a message about RD Licensing Grace Period has expired even though RD Licensing is properly configured, see Eric Verdumen No remote Desktop Licence Server availible on RD Session Host server 2012. The solution was to delete the REG_BINARY in HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\RCM\GracePeriod only leaving the default. You must take ownership and give admin users full control to be able to delete this value.
C: Drive Permissions
This section is more important for shared VDAs like RDSH (Windows Server 2016, Windows Server 2019, and Windows Server 2022).
The default permissions for C: drive allow users to store files on the C: drive in places other than their profile.
- Open the Properties dialog box for C:.
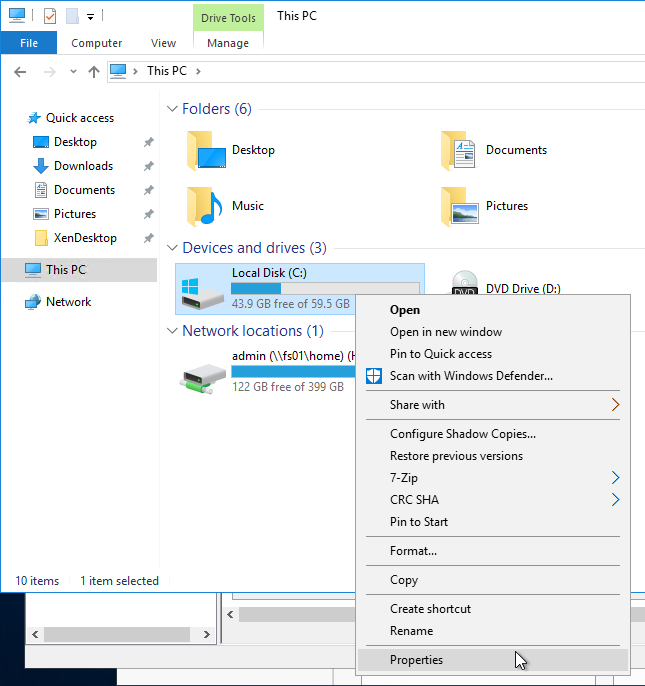
- On the Security tab, click Advanced.
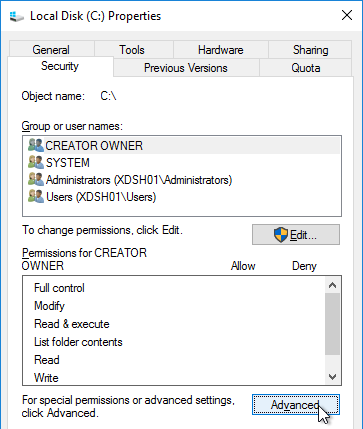
- If UAC is enabled, click Change permissions.
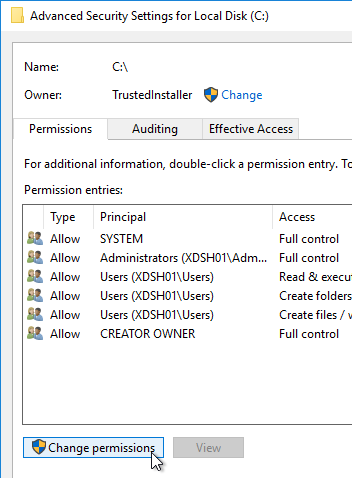
- Highlight the line containing Users and Create Folders, and click Remove.
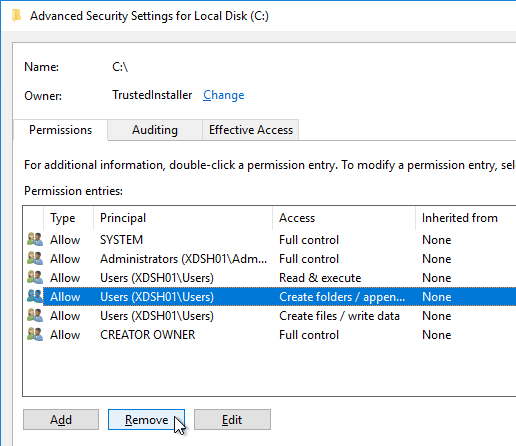
- Highlight the line containing Users and Create files (or Special), and click Remove. Click OK.
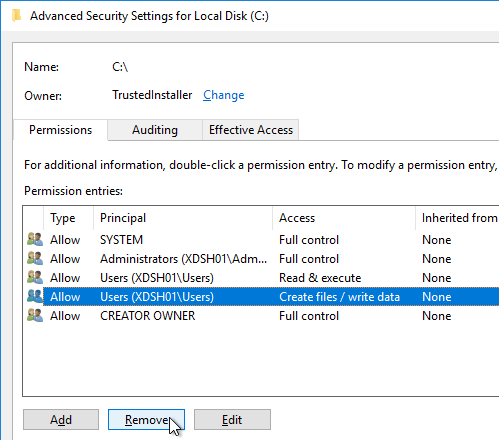
- Click Yes to confirm the permissions change.
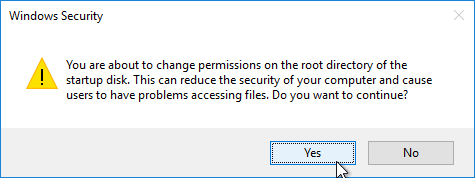
- If you see any of these Error Applying Security windows, click Continue. This window should appear multiple times.
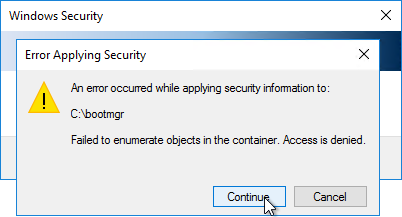
- Click OK to close the C: drive properties.
Pagefile
If this image will be converted to a Citrix Provisioning vDisk, then you must ensure the pagefile is smaller than the cache disk. For example, if you allocate 20 GB of RAM to your Remote Desktop Session Host, and if the cache disk is only 15 GB, then Windows will have a default pagefile size of 20 GB and Citrix Provisioning will be unable to move it to the cache disk. This causes Citrix Provisioning to cache to server instead of caching to your local cache disk (or RAM).
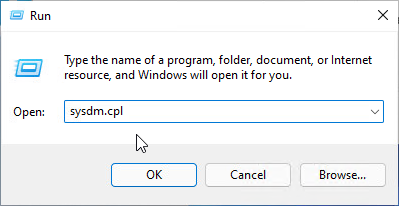
- Open System.
- The quickest method of opening advanced system parameters is to run sysdm.cpl.
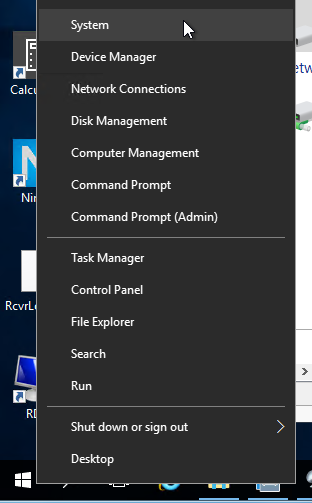
- In Windows Server 2016 and newer, you can right-click the Start button, and click System.
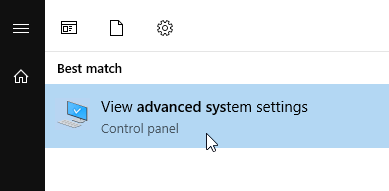
- In Windows 10 1703 or newer (or Windows Server 2019 or newer), search the Start Menu for advanced system settings.
- Another option is to open File Explorer, right-click This PC, and click Properties. This works in Windows 10 1703 and newer.
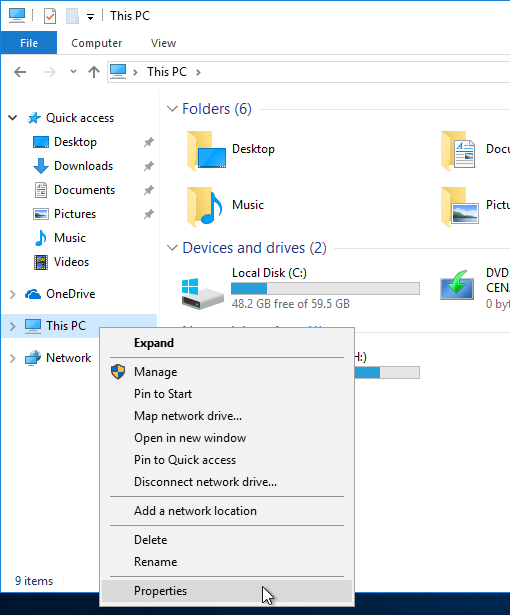
- The quickest method of opening advanced system parameters is to run sysdm.cpl.
- Click Advanced system settings.
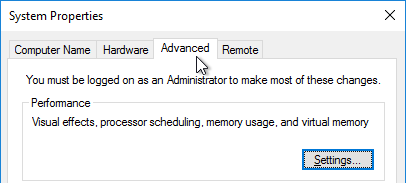
- On the Advanced tab, click the top Settings button.
- On the Advanced tab, click Change.
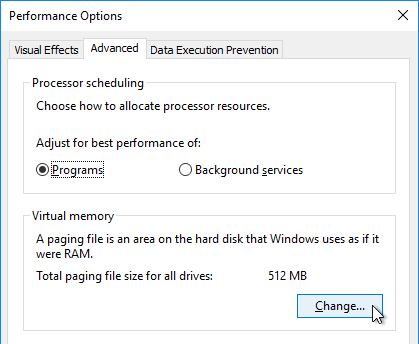
- Uncheck the box next to Automatically manage paging file size for all drives. Then either turn off the pagefile, or set the pagefile to be smaller than the cache disk. Don’t leave it set to System managed size. Click OK several times.
Direct Access Users
When Citrix Virtual Delivery Agent (VDA) is installed on a machine, non-administrators can no longer RDP to the machine. A new local group called Direct Access Users is created on each Virtual Delivery Agent. Add your non-administrator RDP users to this local group so they can RDP directly to the machine.
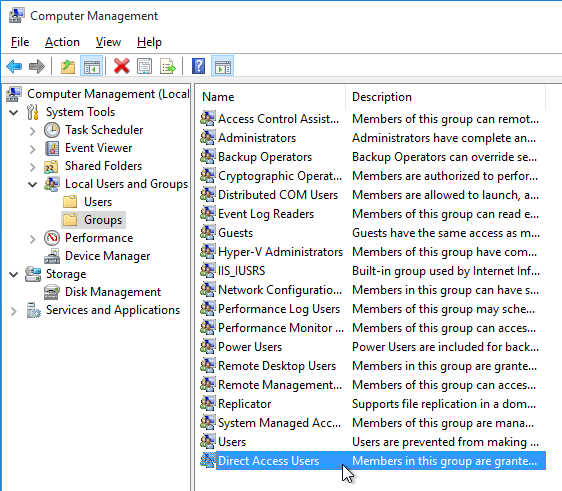
The HKLM\Software\Citrix\PortICA\DirectAccessUsers registry key determines which Local group the VDA references to determine if a user should be allowed Unbrokered RDP access. Members of the Local Administrators group will always be granted access. If the Registry Key does not exist, or gets deleted, VDA will always allow the Unbrokered RDP Connection. The Registry key and local group are created as part of the VDA installation process.
Registry
ShellBridge
ShellBridge is a new Windows feature that fixes the following published app issues:
VDA 2203 CU1 and newer support the ShellBridge feature. Windows must be Windows Server 2019 or newer (or Windows 10/11) running Windows patches from June 2022 or later. To enable it:
- Key =
HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Citrix Virtual Desktop Agent- Value (DWORD) =
ShellBridge= 1
- Value (DWORD) =
EDT MTU Discovery
EDT MTU Discovery prevents EDT packet fragmentation that might result in performance degradation or failure to establish a session. This feature requires the following:
- Citrix Workspace app 1911 for Windows or newer
- Citrix ADC 13.0.52.24 or newer
- Citrix ADC 12.1.56.22 or newer
In VDA 2203 MtuDiscovery is enabled by default. You can also set the following registry value on the VDA.
- Key =
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\Wds\icawd- Value (DWORD) =
MtuDiscovery= 1
- Value (DWORD) =
Black Screen when launch Published Apps on Windows Server 2016
From CTX225819 When Launching an Application Published from Windows Server 2016, a Black Screen Appears for Several Seconds Before Application is Visible: Citrix and Microsoft have worked together together to deliver code fixes for both Windows Server 2016 and Citrix Virtual Apps. Microsoft is targeting their KB4034661 patch for the third week of August 2017. This fix requires a registry edit to enable.
- Key =
HKLM\SOFTWARE\Citrix\Citrix Virtual Desktop Agent- Value (DWORD) =
DisableLogonUISuppression= 0
- Value (DWORD) =
Faster Login
From CTP James Rankin The ultimate guide to Windows logon time optimizations, part #6: DelayedDesktopSwitchTimeout tells the logon process to wait for a shorter time before switching from session 0 to the actual session in use.
- Key =
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System- Value (DWORD) =
DelayedDesktopSwitchTimeout= 1
- Value (DWORD) =
Published Explorer
From Citrix CTX128009 Explorer.exe Fails to Launch: When publishing the seamless explorer.exe application, the session initially begins to connect as expected. After the loading, the dialog box disappears, and the Explorer application fails to appear. On the VDA, use the following registry change to set the length of time a client session waits before disconnecting the session:
- Key =
HKLM\SYSTEM\CurrentControlSet\Control\Citrix\wfshell\TWI- Value (DWORD) =
LogoffCheckerStartupDelayInSeconds= 10 (Hexadecimal)
- Value (DWORD) =
Logon Disclaimer Window Size
If your logon disclaimer window has scroll bars, set the following registry values:
- Key =
HKEY_LOCAL_MACHINE\Software\Wow6432node\Citrix\CtxHook\AppInit_DLLS\Multiple Monitor Hook- Value (DWORD) =
LogonUIWidth= 300 - Value (DWORD) =
LogonUIHeight= 200
- Value (DWORD) =
Login Timeout
From Citrix CTX203760 VDI Session Launches Then Disappears: VDA, by default, only allows 180 seconds to complete a logon operation. The timeout can be increased by setting the following:
- Key =
HKLM\SOFTWARE\Citrix\PortICA- Value (DWORD) =
AutoLogonTimeout= decimal 240 or higher (up to 3599).
- Value (DWORD) =
From Citrix CTX138404 Application Connection Starts but Disappears after Timeout: after loading the published application, the dialog box disappears, and the application fails to appear.
- Key =
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Citrix\wfshell\TWI- Value (DWORD) =
ApplicationLaunchWaitTimeoutMS= decimal 60000
- Value (DWORD) =
Workspace app for HTML5/Chrome Upload Folder
The Workspace app for HTML5 (or Chrome) lets upload files.
By default, the user is prompted to select a upload location. If you use the Upload feature multiple times, the last selected folder is not remembered.
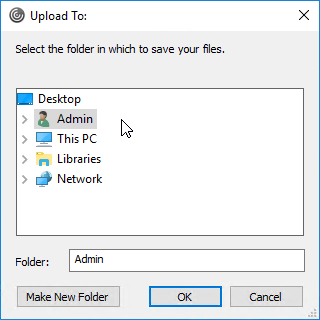
Citrix CTX217351 How to Customize File Upload and Download Using Receiver for HTML5 and Receiver for Chrome. You can specify a default uploads location by editing HKLM\Software\Citrix\FileTransfer\UploadFolderLocation on the VDA. Environment variables are supported. When this value is configured, users are no longer prompted to select an upload location. The change takes effect at next logon.
Note: HTML5/Chrome Workspace app also adds a Save to My Device location to facilitate downloads.
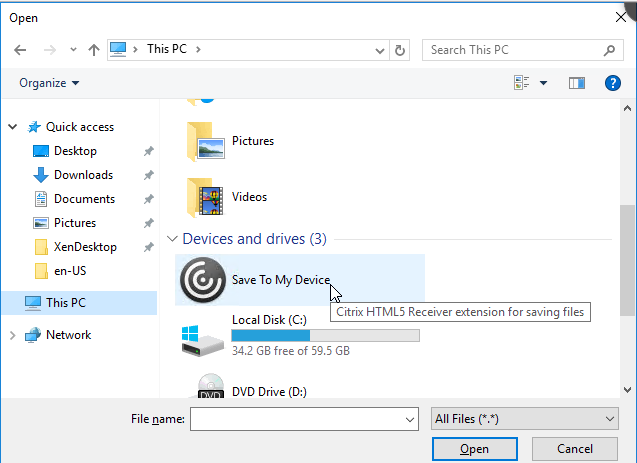
4K Monitors
From Citrix Knowledgebase article CTX218217 Unable to span across multiple monitors after upgrade to 7.11 VDA, Black/Blank screen appears on the monitors while connecting to ICA session:
- Calculate the video memory that is required for monitors using the following formula:
SumOfAllMons (Width * Height) * 4 / 0.3, where width and height are resolution of the monitor. Note: There is no hard and fast rule that will work for all cases.Example: Consider the resolution of monitor 1 is 1920*1200 and monitor 2 is 1366*768. Then SumOfAllMons will be (1920*1200 + 1366*768)
- CTX115637 Citrix Session Graphics Memory Reference describes how multi-monitor resolution is determined.
- Open the registry (regedit) and navigate to: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\vbdenum
- Increase the value of “MaxVideoMemoryBytes” REG_DWORD value to the above calculated memory.
- Reboot the VDA.
Citrix Policies also control graphics performance.
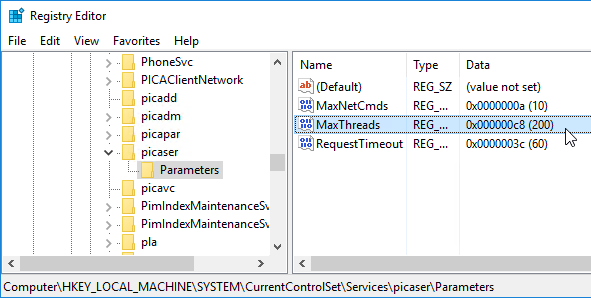
COM Port Threads
CTX212090 COM Port Intermittently Inaccessible During ICA Sessions: increase the default value of “MaxThreads” under the registry key HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\picaser\Parameters from 20 to a value greater than the number of COM port connections you want to support. For example, if a VDA server supports 100 sessions and each session opens two COM ports, the value of “MaxThreads” should be greater than 200.
NVIDIA vGPU GRID License
Allow NVIDIA vGPU GRID License to apply after the session is started. (Source = Jan Hendrik Meier NVIDIA GRID license not applied before the user connects – License Restriction will not be removed until the user reconnects)
- Key =
HKLM\SOFTWARE\NVIDIA Corporation\Global\GridLicensing- Value (DWORD) =
IgnoreSP= 1
- Value (DWORD) =
Legacy Client Drive Mapping
Citrix CTX127968 How to Enable Legacy Client Drive Mapping Format on XenApp: Citrix Client Drive Mapping no longer uses drive letters and instead they appear as local disks. This is similar to RDP drive mapping.
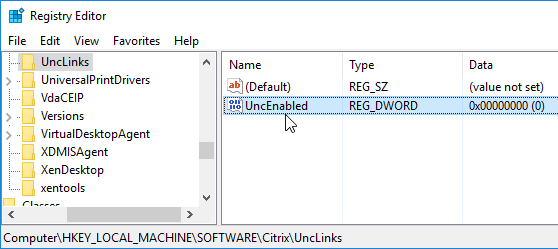
The old drive letter method can be enabled by setting the registry value:
- Key =
HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\UncLinks(create the key)- Value (DWORD) =
UNCEnabled= 0
- Value (DWORD) =
When you reconnect, the client drives will be mapped as drive letters (starts with V: and goes backwards).
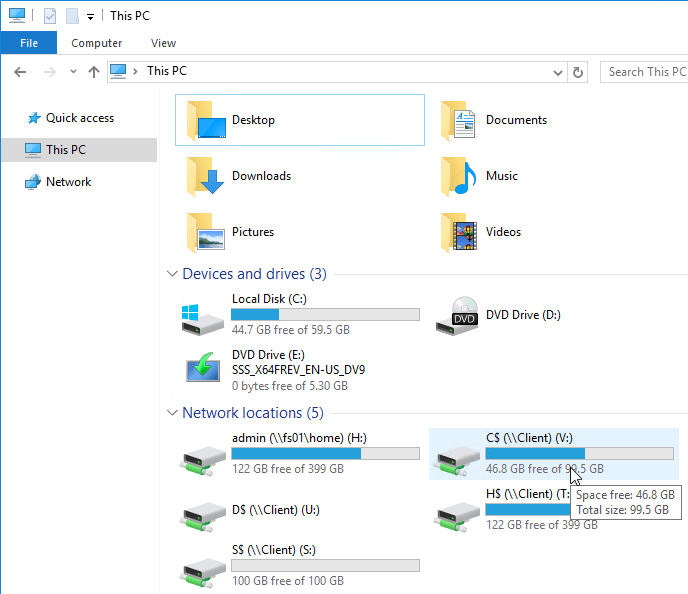
Print Driver for Mac/Linux Clients
Workspace app for Mac version 2203 and newer along with VDA 2112 and newer supports PDF printing instead of Postscript printing. With PDF, it’s no longer necessary to install the HP Color LaserJet 2800 Series PS driver on the VDA. Citrix Policy setting Universal driver preference must be adjusted to enable PDF printing as higher priority than PS (postscript) printing. See Citrix Docs for more details.
For Linux clients or older Mac clients, from CTX140208 Citrix Workspace App for Mac and Linux fail to Redirect Local printer to Citrix Sessions. By default, non-Windows clients cannot map printers due to a missing print driver on the VDA machine.
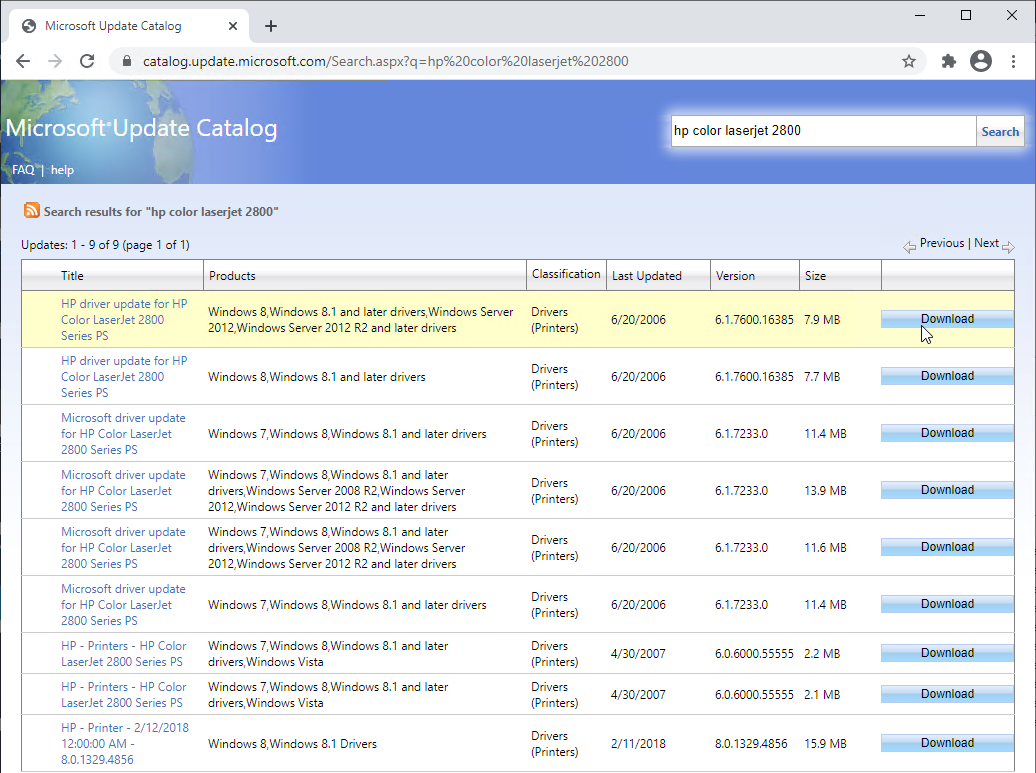
- Download the HP Color LaserJet 2800 Series PS driver directly from Microsoft Catalog as detailed at CTX283355 Client Printing from Linux/MAC is not working on Windows Server 2016 and 2019. The Catalog is at https://www.catalog.update.microsoft.com/. Then search for hp color laserjet 2800. Pick the 6.1.7600.16385 driver version.
- Extract the .cab file using 7-zip or similar.
- In Windows 10 1803+, open Printers & scanners. On the right (or scroll down) is a link to Print Server Properties.

- In older versions of Windows, you can get to Print server properties from Devices and Printers.
- In Windows prior to Windows 10 1703, click Start, and run Devices and Printers.
- In Windows 10 1703, open Printers & scanners, then scroll down, and click Devices and printers.
- In Windows prior to Windows 10 1703, click Start, and run Devices and Printers.
- In the Printers section, highlight a local printer (e.g. Microsoft XPS Document Writer). Then in the toolbar, click Print server properties.
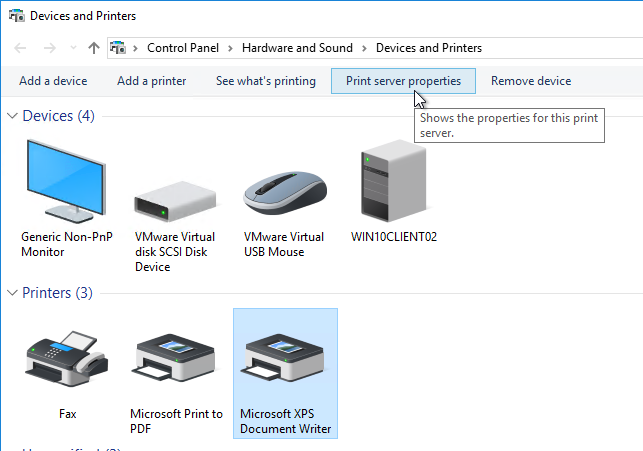
- Switch to the Drivers tab and click Change Driver Settings.
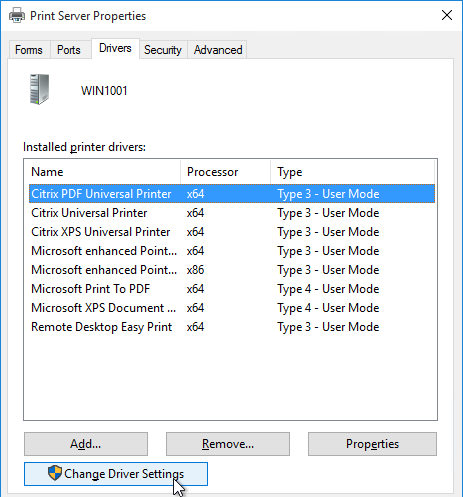
- Then click Add.
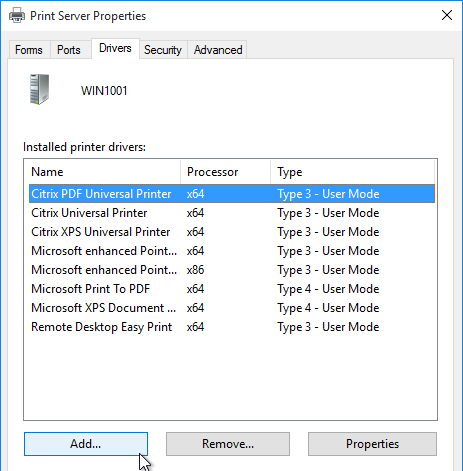
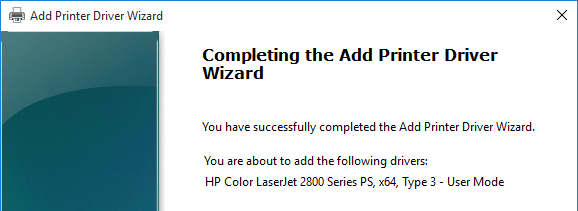
- In the Welcome to the Add Printer Driver Wizard page, click Next.
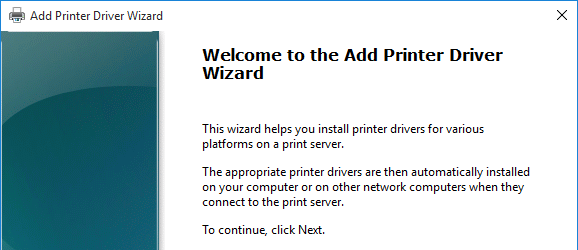
- In the Processor Selection page, click Next.
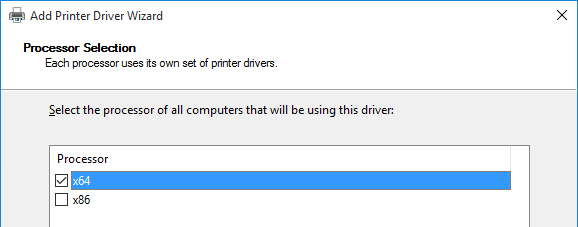
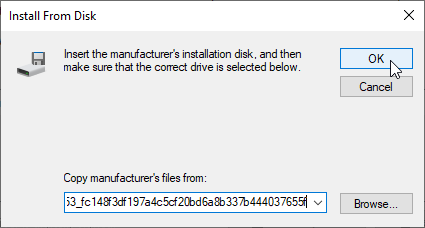
- In the Printer Driver Selection page, click Have Disk and browse to the .inf that you extracted from the .cab file.
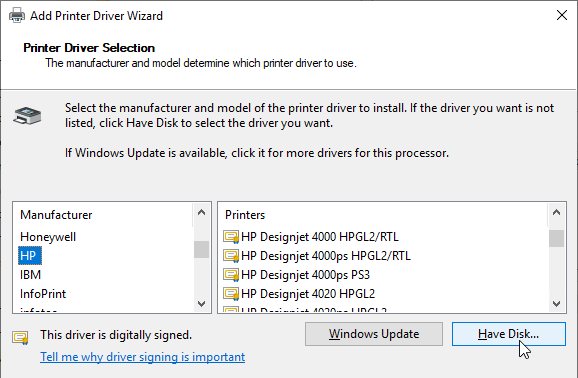
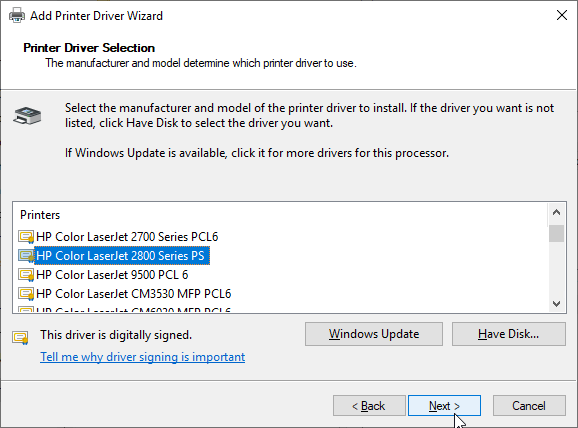
- Select HP Color LaserJet 2800 Series PS and click Next.
- In the Completing the Add Printer Driver Wizard page, click Finish.
SSL for VDA
If you intend to use HTML5 Workspace app internally, install certificates on the VDAs so the WebSockets (and ICA) connection will be encrypted. Internal HTML5 Workspace app will not accept clear text WebSockets. External users don’t have this problem since they are SSL-proxied through Citrix Gateway.
Notes:
- Each Virtual Delivery Agent needs a machine certificate that matches the machine name. This is feasible for a small number of persistent VDAs. For non-persistent VDAs, you’ll need some automatic means for creating machine certificates every time they reboot.
- As detailed in the following procedure, use PowerShell on the Delivery Controller to enable SSL for the Delivery Group. This forces SSL for every VDA in the Delivery Group, which means every VDA in the Delivery Group must have SSL certificates installed.
The following instructions for manually enabling SSL on VDA can be found at Configure TLS on a VDA using the PowerShell script at Citrix Docs.
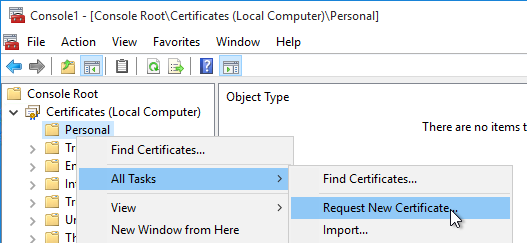
- On the VDA machine, run certlm.msc.
- Right-click Personal, expand All Tasks, and click Request New Certificate to request a certificate from your internal Certificate Authority. You can use either the Computer template or the Web Server template.
- You can also use group policy to enable Certificate Auto-Enrollment for the VDA computers.
- You can also use group policy to enable Certificate Auto-Enrollment for the VDA computers.
- Browse to the Citrix Virtual Apps and Desktops ISO. In the Support\Tools\SslSupport folder, shift+right-click the Enable-VdaSSL.ps1 script, and click Copy as path.
- Run PowerShell as administrator (elevated).
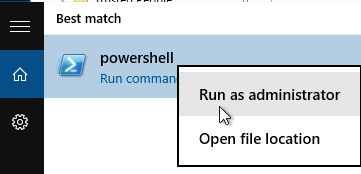
- Run the command Set-ExecutionPolicy unrestricted. Enter Y to approve.
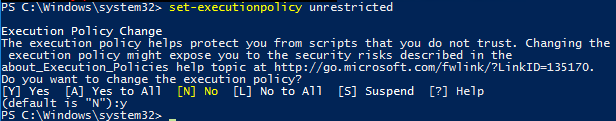
- In the PowerShell prompt, type in an ampersand (&), and a space.
- Right-click the PowerShell prompt to paste in the path copied earlier.
- At the end of the path, type in
-Enable - If there’s only one certificate on this machine, press Enter.
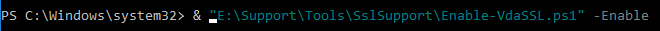
- If there are multiple certificates, then you’ll need to specify the thumbprint of the certificate you want to use. Open the Certificates snap-in, open the properties of the machine certificate you want to use, and copy the Thumbprint from the Details tab.
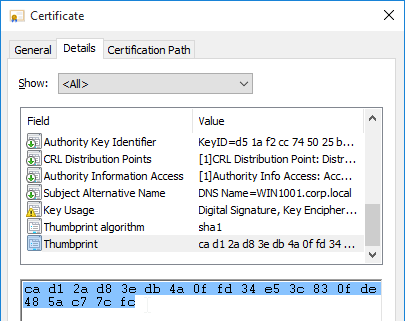 In the PowerShell prompt, at the end of the command, enter
In the PowerShell prompt, at the end of the command, enter‑CertificateThumbPrint, add a space, and type quotes (").Right-click the PowerShell prompt to paste the thumbprint.Type quotes (") at the end of the thumbprint. Then remove all spaces from the thumbprint. The thumbprint needs to be wrapped in quotes.
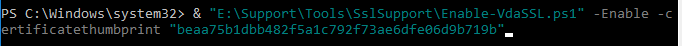
- There are additional switches to specify minimum SSL Version and Cipher Suites. Also see Citrix CTX226049 Disabling Triple DES on the VDA breaks the VDA SSL connection.

- Press <Enter> to run the Enable-VdaSSL.ps1 script.
- Press <Y> twice to configure the ACLs and Firewall.
- You might have to reboot before the settings take effect.
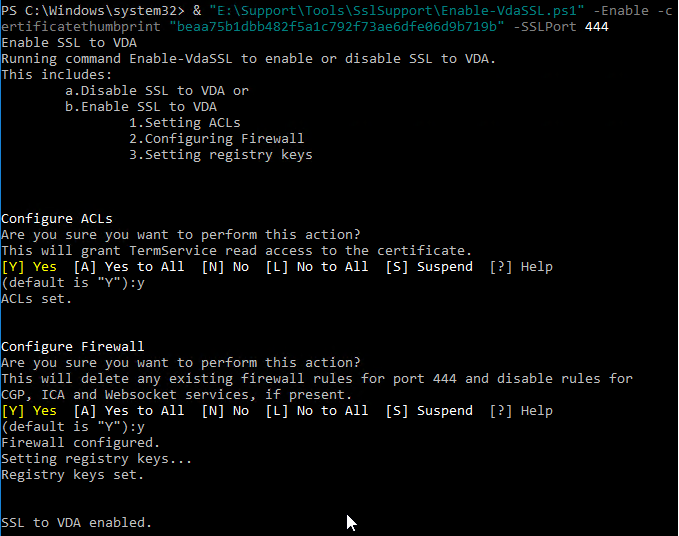
- Login to a Delivery Controller and run PowerShell as Administrator (elevated).
- Run the command
asnp Citrix.*
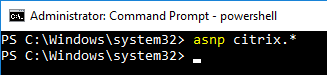
- Enter the command:
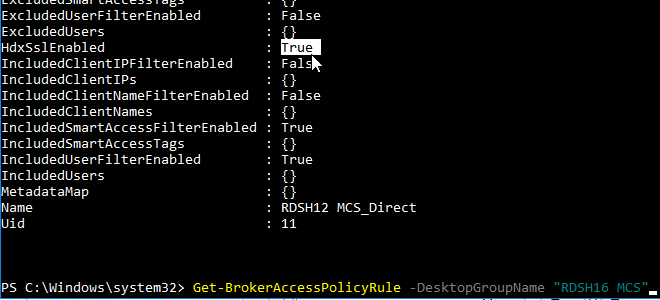
Get-BrokerAccessPolicyRule -DesktopGroupName '<delivery-group-name>' | Set-BrokerAccessPolicyRule ‑HdxSslEnabled $true
where <delivery-group-name> is the name of the Delivery Group containing the VDAs.
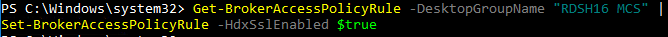
- You can run
Get-BrokerAccessPolicyRule -DesktopGroupName '<delivery-group-name>'to verify that HDX SSL is enabled.
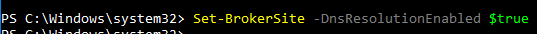
- Also run the following command to enable DNS resolution.
Set-BrokerSite –DnsResolutionEnabled $true
- Since the UDP-based EDT protocol is enabled by default, open port UDP 443 to the VDAs.
You should now be able to connect to the VDA using the HTML5 Workspace app from internal machines.
The Citrix blog post How To Secure ICA Connections in XenApp and XenDesktop 7.6 using SSL has a method for automatically provisioning certificates for pooled virtual desktops by enabling certificate auto-enrollment and setting up a task that runs after the certificate has been enrolled.
- From Russ Hargrove at A note on VDA certificates in 7.14 at Citrix Discussions: Citrix installs a new “Citrix XenApp/XenDesktop HDX Service” certificate in the Personal store which breaks the automation of the Enable-VdaSSL.ps1 script. To fix the problem, modify the task scheduler powershell script to:
Enable-VdaSSL.ps1 -Enable -CertificateThumbPrint (Get-ChildItem -path cert:\LocalMachine\My | Where-Object -FilterScript {$_.Subject -eq ""} | Select-Object -ExpandProperty Thumbprint) -Confirm:$False
For certificate auto-enrollment on non-persistent Remote Desktop Session Hosts (aka Multi-session OS, aka Server OS VDAs), see Non-Persistent Server SSL to VDA by Alfredo Magallon Arbizu at CUGC.
# First of all, make registry coherent with the listener status Set-ItemProperty -Path "HKLM:\System\CurrentControlSet\Control\Terminal Server\Wds\icawd" -Name "SSLEnabled" -Value 1 -Type DWORD # Then, shut down the listener, as it is not configured C:\Scripts\EnableSSL\Enable-VDASsl.ps1 -Disable -Confirm:$false # Finally, configure and start listener C:\Scripts\EnableSSL\Enable-VDASsl.ps1 -Enable -CertificateThumbPrint $Cert.Thumbprint -Confirm:$false
You can launch the above script from a scheduled task that triggers when certificate auto-enroll is complete.
SCHTASKS.EXE /CREATE /RU "SYSTEM" /SC "ONEVENT" /EC "Microsoft-Windows-CertificateServicesClient-Lifecycle-System/Operational" /MO "*[System[Provider[@Name='Microsoft-Windows-CertificateServicesClient-Lifecycle-System'] and (EventID=1006)]]" /TN "yourtaskname" /TR "powershell.exe -ExecutionPolicy ByPass -File yourscript.ps1"
Anonymous Accounts
If you intend to publish apps anonymously, then follow this section.
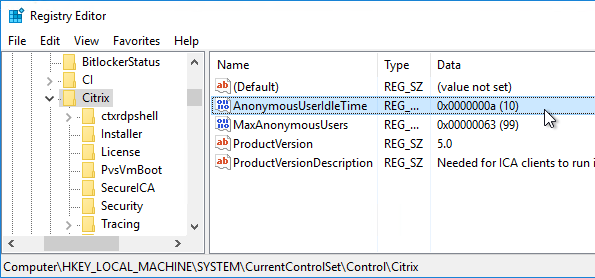
- Anonymous accounts are created locally on the VDAs. When VDA creates Anon accounts, it gives them an idle time as specified at HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Citrix\AnonymousUserIdleTime. The default is 10 minutes. Adjust as desired.
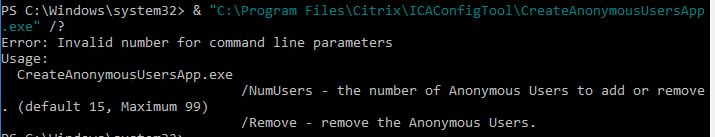
- Pre-create the Anon accounts on the VDA by running
"C:\Program Files\Citrix\ICAConfigTool\CreateAnonymousUsersApp.exe". If you don’t run this tool, then anonymous users can’t login.
- You can see the local Anon accounts by opening Computer Management, expanding System Tools, expanding Local Users and Groups and clicking Users.
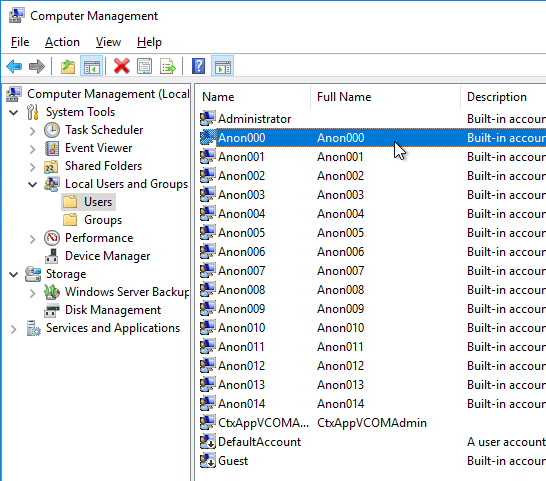
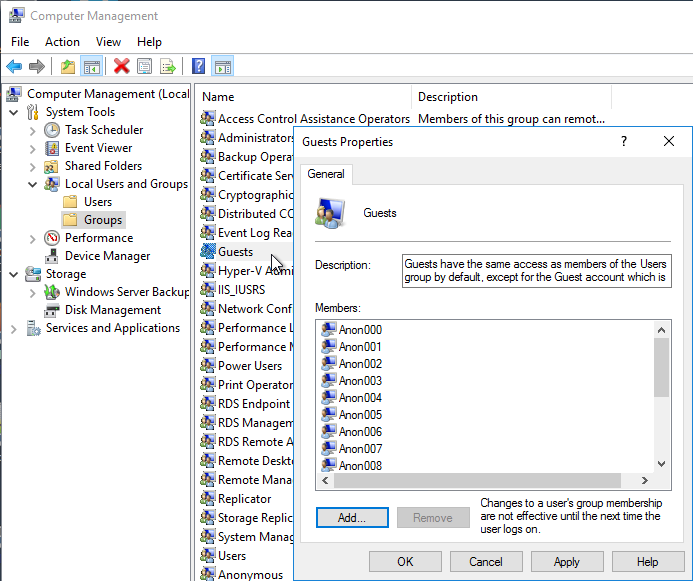
- If you want profiles for anonymous users to delete at logoff, then you’ll need to add the local Anon users to the local Guests group.
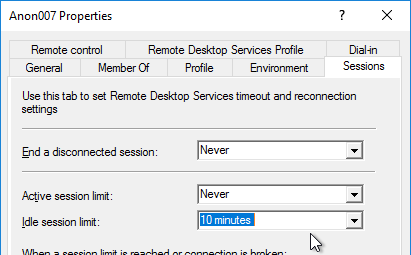
- If you open one of the accounts, on the Sessions tab, notice that idle timeout defaults to 10 minutes. Feel free to change it.
Group Policy for Anonymous Users
Since Anonymous users are local accounts on each Virtual Delivery Agent, domain-based GPOs will not apply. To work around this limitation, you’ll need to edit the local group policy on each Virtual Delivery Agent.
- On the Virtual Delivery Agent, run mmc.exe.
- Open the File menu, and click Add/Remove Snap-in.
- Highlight Group Policy Object Editor, and click Add to move it to the right.
- In the Welcome to the Group Policy Wizard page, click Browse.
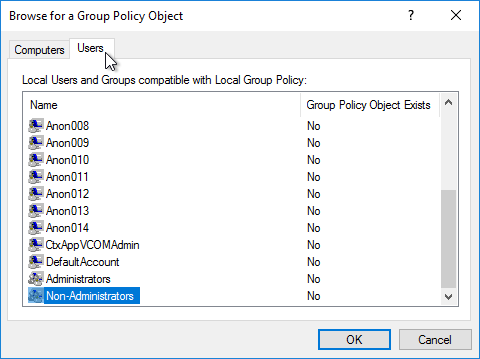
- On the Users tab, select Non-Administrators.
- Click Finish.
- Now you can configure group policy to lock down sessions for anonymous users. Since this is a local group policy, you’ll need to repeat the group policy configuration on every Virtual Delivery Agent image. Also, Group Policy Preferences is not available in local group policy.
Antivirus
Install antivirus using your normal procedure. Instructions vary for each Antivirus product.
Microsoft’s virus scanning recommendations (e.g. exclude group policy files) – http://support.microsoft.com/kb/822158.
Citrix’s Recommended Antivirus Exclusions
Citrix Tech Zone Endpoint Security and Antivirus Best Practices: provides guidelines for configuring antivirus software in Citrix Virtual Apps and Desktops environments.
Citrix Blog Post Citrix Recommended Antivirus Exclusions: the goal here is to provide you with a consolidated list of recommended antivirus exclusions for your Citrix virtualization environment focused on the key processes, folders, and files that we have seen cause issues in the field:
- Set real-time scanning to scan local drives only and not network drives
- Disable scan on boot
- Remove any unnecessary antivirus related entries from the Run key
- Exclude the pagefile(s) from being scanned
- Exclude Windows event logs from being scanned
- Exclude IIS log files from being scanned
See the Blog Post for exclusions for each Citrix component/product including: StoreFront, VDA, Controller, and Citrix Provisioning. The Blog Post also has links to additional KB articles on antivirus.
Symantec
Symantec links:
- Symantec TECH91070 Citrix and terminal server best practices for Endpoint Protection.
- Symantec TECH197344 Virtualization best practices for Endpoint Protection 12.1.x and SEP 14.x
- Symantec TECH180229 Endpoint Protection – Non-persistent Virtualization Best Practices
- Symantec TECH123419 How to prepare Symantec Endpoint Protection clients on virtual disks for use with Citrix Provisioning Server has a script that automates changing the MAC address registered with Symantec.
Trend Micro
Citrix CTX312452 Grey Screen when launching the applications or desktops – Ctxuvi event ID 1005 and 1003: Trend Micro have released a fix for their Deep Security Agent 20.0.0-2593 (20 LTS Update 2021-07-01).
Trend Micro Slow login on Citrix environment after installing OfficeScan (OSCE): The following registries can be used to troubleshoot the issue. These registries will allow a delay on the startup procedure of OSCE until the system has launched successfully. This avoids deadlock situations during login.
Citrix CTX136680 – Slow Server Performance After Trend Micro Installation. Citrix session hosts experience slow response and performance more noticeable while users try to log in to the servers. At some point the performance of the servers is affected, resulting in issues with users logging on and requiring the server to be restarted. This issue is more noticeable on mid to large session host infrastructures.
Trend Micro has provided a registry fix for this type of issue. Create the following registry on all the affected servers. Add new DWORD Value as:
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\TmFilterParameters] “DisableCtProcCheck”=dword:00000001
Trend Micro Links:
- Trend Micro Docs – Trend Micro Virtual Desktop Support
- Trend Micro Docs – VDI Pre-Scan Template Generation Tool
- Trend Micro 1056314 – Configuring the OfficeScan (OSCE) Virtual Desktop Infrastructure (VDI) client/agent
- Trend Micro 1055260 – Best practice for setting up Virtual Desktop Infrastructure (VDI) in OfficeScan
- Trend Micro 1056376 – Frequently Asked Questions (FAQs) about Virtual Desktop Infrastructure/Support In OfficeScan
Sophos
CTX238012 Logon process to VDAs is extremely slow when Citrix UPM is enabled. Set the following registry:
- HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Sophos\SavService\Application
- DisableAsyncScans (DWORD) = 1
Sophos Endpoint Security and Control: Best Practice for running Sophos on virtual systems: we’ve amassed the following practical information about how you can optimize our software to work with this technology.
Sophos Endpoint Security and Control: Installation and configuration considerations for Sophos Anti-Virus on a Remote Desktop Services server: It maybe desirable to disable the Sophos AutoUpdate shield icon
Sophos Endpoint Security and Control: How to include current version of Sophos in a disk image for cloned virtual machines: This procedure will make sure that the produced target/cloned computers:
- Get their distinct identity with Enterprise Console, under which they can be subsequently managed.
- Have the desired version of Sophos Anti-Virus already installed and configured on the created image.
Palo Alto Traps
- Install Traps Agent for Windows:
- Virtual desktop infrastructure (VDI) installation—Intended for non-persistent endpoints that replicate (also referred to as spawn) from a golden image which has Traps installed.
- Temporary session—Intended for either physical or virtual endpoints (such as a Remote Desktop Server) that repeatedly revert to a snapshot (or image) on which Traps is not installed.
Windows Defender Antivirus
Configure Microsoft Defender Antivirus on a remote desktop or virtual desktop infrastructure environment – Microsoft Docs
Configuring Microsoft Defender Antivirus for non-persistent VDI machines – Microsoft Blog
Disable Network protection and configure Citrix’s antivirus exclusions (source = Citrix CTX319676 Users sessions are getting disconnected – Connection Interrupted)
Onboarding and servicing non-persistent VDI machines with Microsoft Defender ATP
Cylance
CTX232722 Unable to launch application with Cylance Memory Protection Enabled. Cylance must be run in compatibility mode in order to the VDA and Cylance to run on the same machine. See the article for detailed instructions.
Optimize Performance
Citrix Optimizer
Download Citrix Optimizer and run it.
- Citrix Blog Post Citrix Optimizer 2.6 – What’s new.
- Select a template. Then click Optimize.
- To roll back Citrix Optimizer, see Citrix Blog Post Citrix Optimizer: How to Roll Back Changes.
Microsoft links:
- Microsoft Virtual-Desktop-Optimization-Tool.
- Microsoft Docs Optimizing Windows 10, version 2004 for a Virtual Desktop Infrastructure (VDI) role
- Microsoft Docs Recommended settings for VDI desktops contains a list of settings with their Default Value and Recommended value for VDI use
Optimization Notes:
- If this machine is provisioned using Citrix Provisioning, do not disable the Shadow Copy services.
- Citrix CTX213540 Citrix UPS Printers are not visible via Control Panel, Devices And Printers – don’t disable the Device Setup Manager Service
- Citrix CTX131995 User Cannot Launch Application in Seamless Mode in a Provisioning Services Server when XenApp Optimization Best Practices are Applied. Do not enable NtfsDisable8dot3NameCreation.
Applications
Choose application installers that install to C:\Program Files instead of to %appdata%. Search for VDI or Enterprise versions of the following applications. These VDI versions do not auto-update, so you’ll have to update them manually.
- Google Chrome – Chrome Enterprise
- Microsoft Edge – Edge for Business
- Microsoft Teams – Teams for VDI
- Microsoft OneDrive – Install the sync app per machine
- Zoom – Zoom VDI
- WebEx – WebEx VDI
- Cisco Jabber – Jabber VDI
- Etc.
Seal and Shut Down
If this VDA will be a master image in a Machine Creation Services or Citrix Provisioning catalog, after the master is fully prepared (including applications), do the following:
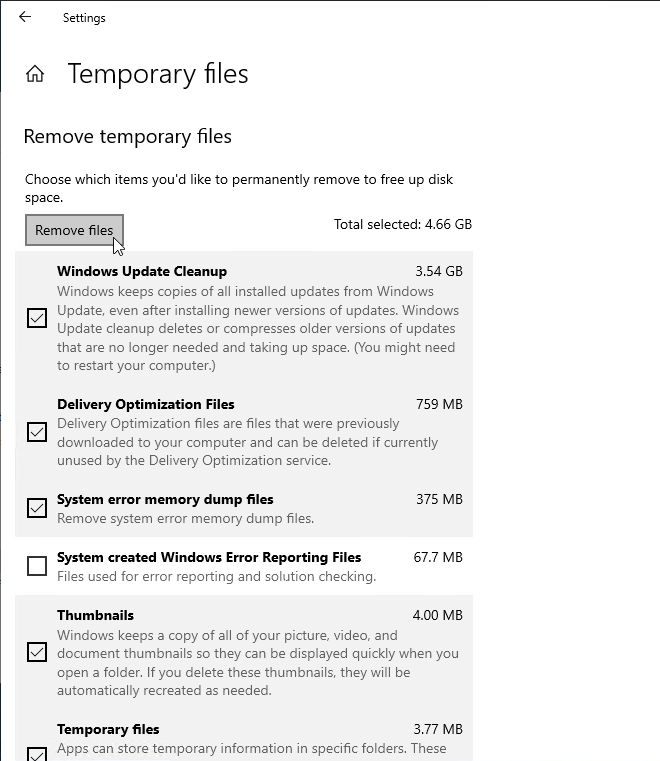
- Go to the properties of the C: drive, and run Disk Cleanup.
- If Disk Cleanup is missing, you can run cleanmgr.exe instead.
- Windows 10 1703 and newer has a new method for cleaning up temporary files.
- Right-click the Start button, and click System.
- Click Storage on the left, and click This PC (C:) on the right.
- Click Temporary Files.
- Check boxes, and click Remove files.
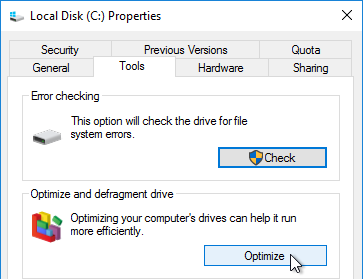
- On the Tools tab of the local C: drive Properties, click Optimize to defrag the drive.
 `
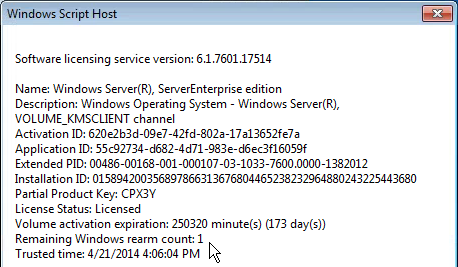
` - Run slmgr.vbs /dlv and make sure it is licensed with KMS and has at least one rearm remaining. It is not necessary to manually rearm licensing since MCS will do it automatically.
- Run Delprof2 to clean up local profiles. Get it from http://helgeklein.com/download/.
- Machine Creation Services and Citrix Provisioning require DHCP.

- Session hosts (RDSH) commonly have DHCP reservations.
- Base Image Script Framework (BIS-F) automates many sealing tasks. The script is configurable using Group Policy.
- Shut down the master image. You can now use Studio (Machine Creation Services) or Citrix Provisioning to create a catalog of linked clones.
Uninstall VDA
Uninstall the VDA from Apps & Features or Programs and Features. Then see CTX209255 VDA Cleanup Utility.
To run the VDA Cleanup Tool silently:
- Execute VDACleanupUtility.exe /silent /noreboot to suppress reboot.
- Once the VDACleanupUtility has finished executing, set up Auto logon for the current user.
- Reboot.
- After reboot, the tool will launch automatically to continue Cleanup.
Another option is to delete CitrixVdaCleanup value under HKLM\Software\Microsoft\Windows\CurrentVersion\RunOnce. Then after reboot, run VDACleanupUtility.exe /silent /reboot to indicate that it’s running after the reboot.
I’m deploying persistent machines with MCS in 2203 LTSR CU6 to VMware 7U3. The gold image is Win11 23H2 and has three drives (C: 200GB, D: 200GB and E:60GB) which are three distinct drives in VMware. When I create the machine catalog and the delivery group, the deployed VMs end up with two drives (C: 200GB and D: 16MB). Any ideas why this is happening and how I can get the deployed VMs to have the same drives as the gold image?
I think MCS supports multiple partitions on a single drive but not multiple drives. An alternative option is to use vCenter cloning instead of MCS to create persistent machines.
Thank you for the information. Of those two options, any idea which one would be more performant for the enduser?
Hi Carl,
Hoping for some clarity. We need to upgrade our VDAs from 2203 CU3 to CU5. We tried this a few months ago and after upgrading the entire environment to CU5, we immediately started experiencing long logon times. After working with Citrix support and unable to find a resolution, we rolled the image and VDAs back to CU3. This seemingly resolved the issue. We are now faced with the issue of once again needing to upgrade the VDAs to CU5. As you can imagine we are a bit hesitant as we do not want to cause another degradation in service. Our current server infrastructure in Server 2016 (including VDAs). The question: Can we upgrade our image and VDAs to Server 2022 and leave the Citrix Core components at 2016? Not sure if this will make a difference when we upgrade from CU3 to CU5, but not sure what else to try. Any ideas/suggestions you may have would be greatly appreciated.
Yes. You can also upgrade the VDA software to version 2402 while leaving Delivery Controller as is.
Hi Carl, We have a published application which has a option to open chat bot window. But when user open chatbot window its showing black screen.
Please help on this.
Does it work from a published desktop?
You might be able to configure Seamless Flags to fix it https://support.citrix.com/s/article/CTX101644-seamless-configuration-settings?language=en_US but it’s probably easier to call Citrix Support.
It’s not working from published desktop as well , but it’s working fine from rdp.
I have already tried seamlessflags=0x1000 , also ctxhooks excludeimagwnames, ctxuvi exclusions but nothing helped
Does it work for admin vs non-admin? Does it work for the user that installed the app but not for other users? Does it work for users with new profiles but not for users that have existing profiles?
It’s working for admin and non admin from rdp only , it’s working in rdp only for user who installed it .issue happens with new or old profiles through Citrix
Vda 2203 cu4
That usually means that the app was installed to a per-user location instead of machine-wide. Either every user will have to do their own install, or ask the vendor if they have a machine-wide option.
It’s not a per user installation, as exe is available In program files and not in appdata.
It’s working for other users also when they rdp. So there are some tweaks needs to be performed on server to make app to work in ica session. I will ask Citrix support to help on this and update the resolution here
I usually use process monitor to figure out what the app is doing.
Thanks for the great article, Carl,
In case I have FAS configured and VDA auth is happening through certificates.
Will the “Prompt for Password” GPO policy prompt a login for users or it will be a seamless experience. (Assuming Policy is enabled)
is VDA 2203 compatible with 7118 delivery controller
It should be.
Hi Carl! Again great articles from you as always. I’m searching for compatibility proof when having a VDA 2203 LTSR against 7.15 LTSR delivery controller. That should be fine as well, right? If yes, where should I find the official Citrix documentation for? Cheers for the answer.
There used to be documentation showing that VDAs can be upgraded prior to upgrading Controllers but I can’t find it. There might be some posts from Citrix employees at Citrix Community.
Hi Carl,
I’m on the way to create a parallel Citrix Farm to pass from 1912 LTSR to 2203 LTSR CU4 with Storefront and VDA (windows 11) with CU4 SP1.
We had Nutanix Virtual environment.
When i logoff the VDI shutdown and not reboot as expected, do you have any suggestion in what could be the issue?
Hi
Brand new Citrix farm with 2 Windows Server 2022 VDA’s, Citrix 2203 LTSR CU4, Profile Management with FSLogix 2210 HF 2. Users are accessing Published Desktops.
Users are having a strange issue :
When they disconnect their sessions from the Desktop Viewer Toolbar at the top of their Citrix sessions, they are able to reconnect properly to their disconnected session.
When they dosconnect their sessions from the “Disconnect” button on the start menu, a new blank session is created.
This registry keys are already published by GPO to the VDA :
EnforceUserPolicyEvaluationSuccess : 0
FastReconnect : 0
DisableGPCalculation : 0
Does anyone have an idea ?
2203 CU 4 Update 1 applied this week to my VDAs. I appear to have lost Logon Duration Director metrics since and just wanted to post here to see if anyone experienced the same?
Fresh install of 2203 CU4 Update 1 resolved this issue. I previously installed update 1 over VDA 2203 CU4 and noted the ‘Additional Components’ section of the install wizard includes options that did not display Citrix Personalization for App-V – VDA, Citrix User Profile Manager and Citrix User Profile Manager WMI Plugin.
When doing a fresh install instead of in-place upgrade these optional components are available to select and the Logon Duration data once again displays in Director.
Hi Carl, we have citrix environment running on 2203 CU2 LTSR with more than 2000 Windows10 VDA machines, We use PVS severs to manage their OS and updates.
There was no changes in the environment, but all of sudden users sessions are disconnecting and VDA machines started unregistering intermittently.
No clue what is happening with PVS servers and VDA machines. Whole company VDI environment is down now.
An suggestions from your end to check the configuration/Settings to get identify and resolve this issue.
Are the machines rebooting? If so, then seems like a blue screen. Look at any software that uses drivers, including VDA, antivirus, and other security tools. Did one of your security tools update itself?
Yes rebooted, and image wont load immediately and dont see any blue screen. They are trying to get the image from PVS servers.
Avoid VDA 2203 CU4 at this time. Citrix just posted this yesterday (12/14/23). My organization updated and as soon as the servers are under load they blue screen. Multiple other organization we work with have also reported this. We have reverted back to VDA 2203 CU1.
https://support.citrix.com/article/CTX584794/cvad-2203-cu4-vda-may-experience-bsod-with-bugcheck-code-0x96-invalidworkqueueitem
Hi,
I have the same problem
Windows Server 2016 (mcs, multiuser non persistent) After updating from cu3 to c4, the VMs crash. A question about rollback. Do the delivery controllers, Sotorefront and the databases also have to be rolled back, or is it enough to roll the master image (VDA) back to CU3.
I am running CVAD 2203 LTSR CU2, vSphere 7.0, Windows Server 2016. I cant remember the steps to get a single session vda installed. For some reason i cannot load the VDA agent. Here is what i have done so far,
regedit
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server
DWORD fSingleSessionPerUser = 1
Removed RDSH from Server Manager
CMD with admin
XenDesktopVdaSetup.exe /quiet /servervdi
What error are you seeing? Check the install logs.
Hi Carl,
Looking at the Enable-SSLVDA.ps1 script.
I can script the execution of the script based on the event ID triggering the renewal, however I’m guessing that this will drop/hang active sessions if the renewal occurs during hours where there are active users.
What is the best approach for persistent VDA’s. If there is a user impact, i’m thinking along the lines of task scheduler to set the execution of the script at next boot to swap the certificate? Or do you usually schedule the script to execute on boot for the lifetime of the VM, as long as it’s rebooted before a certificate expiry it’ll rotate.
Carl, just want to say I appreciate your blog. It’s so detailed and helpful.
Hi,
We are managing around 30 Citrix farms with different sizes, from one multisession Windows server VDA (around 15 users) to 12 multisession Windows Server VDAs (around 200 users).
All farms are running the same versions of Citrix : 2203 CU2 LTSR
The user profiles are managed with FSLogix if profiles need to roam between several VDAs, or local profiles when there is only one VDA.
A scheduled task is configured to reboot the VDAs every night at 2am. (shutdown -r -t 00)
We have a problem with several VDA’s on different farms :
At 2am when the VDAs are scheduled to reboot, it happens randomly that one VDA doesn’t reboot properly. It remains powered on in VMware with a black screen and we have to reset it in the morning to reboot it properly. There are no logs in the Event viewer from the moment where the server tries to reboot with the scheduled task and when we restart it manually from VMware. This problem happens randomly, from once a week to once a month and everytime one a different server.
The only impacted VDAs are running Windows Server 2019. Some of them are running FSLogix but others have local profils.
We also have Windows server 2019 VDA (With FSLogix or not) where the problem never happened.
Does someone already experience this issue?
Hi Carl,
I’ve got two Profile Management policies (Policy A and Policy B) set in Citrix Studio for two different sets of users and each of them store the profiles in different locations (Location 1 and Location 2) . However when running the modelling wizard for a user in which Policy B is being applied which should go to location 2 (I can see the correct policy is being applied) the actual location that is being shown is Location 1. I’ve tested logging in at this user and the profile is being saved in this location. Any ideas that you think may be causing this?
Profile Management settings are computer settings, not user settings. See https://docs.citrix.com/en-us/profile-management/current-release/configure/enable-configure-user-level-settings.html
Hi Carl,
after updating the VDA from 2303 to 2305 (W2022) and starting the Session in WorkspaceApp 2305 it starts and disappears immediately. Only some Eventlogs:
TdIca 1019, “The Citrix TDICA Transport Driver connection from xxx.xxx.xxx.xxx: to port 2598 received an invalid packet during its SSL handshake phase.”
Citrix Desktop Service 1050, citrix connection validation failed on domain “for user” for reason ‘hashexchangefailed’
I have once have had this after an update, new installation fixed it – but ther must be a way to manage it without that. I expect this will happen also when I run the next update.
Maybe you have an idea?
kind regards
|Hello Juergen, Same here, with CU1, CU2 and CU3. Downgrade or use W2019 and everything is working just fine.
Hi,
same issue after update from 2203 LTSR CU2 to 2203 LTSR CU3 on Windows 2022 Standard.
Turning on maintenance on updated VDA I can lunch again all application on other VDA ( not updated and still on 2203 LTSR CU2… )
Could be a bug of 2203 LTSR CU3?
Thanks,
Fabio.
Hi,
we have the same issue 🙁 since 2203 LTSR CU3.
VG Holger.
Hello Holger,
at the moment it looks like you can´t update VDAs running on Windows Server 2022. If you want a new Version install a new machine.
Hope this will be fixed either by citrix or microsoft or together ;-(
kind regards
Hi Jurgen,
but is there anything official Citrix that says this? I upgraded to fix the security issues of CVE-2023-24483. Some VDAs upgraded to 2203 LTSR CU3 on Windows 2022 Standard work, but this seems random, while others don’t.
If as you say it is NOT possible to update the VDAs on Windows 2022 Citrix should officially declare it. In a production environment it is NOT possible to remake VMs and this is NOT an acceptable solution.
Thank you,
Fabio.
Sorry, I updated following what is indicated in the following secutiry bulletin:
https://support.citrix.com/article/CTX559370/windows-and-linux-virtual-delivery-agent-for-cvad-and-citrix-daas-security-bulletin-cve202324490
It’s not written here that you can’t upgrade the VDAs on Windows 2022…
Thank you,
Fabio.
HI,
strange that no one at Citrix has reported this yet. I searched the KB but found nothing. The problem is really annoying. In the logs, also client and server side Event Viewer, DDC, VDA I have no trace of errors. I have uninstalled the VDA 2203 LTSR CU3 component and reinstalled several times but this does not solve the problem. It looks like something due to negotiation because the application always crashes at that stage, or the very few times it seems to launch it doesn’t show up.
Hello Fabio,
update does not work on W2022 server is my opinion, not an official statement. I have installed and tested: W2022, MS update, VDA 2303 (the simplest Config.) – Desktop Session Logon possible – VDAupdate to 2305 (installation says OK, reboot) – Logon impossible. The same test with W2019 ->no problem. But you are right, you can´t find a statement in Forum, Knowledgebase, internet, … W2022 is not a brand new OS?
kind regards
Hi Jurgern,
thank you very much for your suggestion.
I solved the issue following this:
https://discussions.citrix.com/topic/417832-cvad-connectionfailure-after-install-ltsr-2203-cu2-on-server-2022/page/3/
Running the powershell script of post: On 2/23/2023 at 5:17 PM, Jan Klimek said:
This worked form me on Windows 2022 Standard ( August Microsoft Patches ) with 2203 LTSR CU3 VDA upgraded from 2203 LTSR CU2.
Fabio.
Hi Holger,
I found this solution:
https://support.citrix.com/article/CTX572393/server-2022-vda-upgrade-vidddll-driver-does-not-copy-over-to-upgraded-vda
I set the registry and rebooted, but unfortunately it doesn’t work for me…
Fabio.
Hi Fabio,
I set also this key and it seams to be working today. All our VDAs are up and connections are working.
Thank your for your hint.
Holger.
Hi Holger,
glad to hear you fixed it!
Fabio.
Hi Holger,
finally I solved the problem using the script found on this forum:
https://discussions.citrix.com/topic/417832-cvad-connectionfailure-after-install-ltsr-2203-cu2-on-server-2022/page/3/
on post of: On 2/23/2023 at 5:17 PM, Jan Klimek said:
I used the script and now the applications on VDA 2203 CU3 on Windows 2022 Standard (plus Microsoft August patches) work properly!!!
Fabio.
I tried to launch app on Citrix App Workspace but received fail message of “cannot start application” with the version of 2203 LTSR CU2 , the delivery controller showing registered in machine catalog. When I check the event log of one of the delivery controller server, the log showed the following message “Failed to launch the resource ‘XXXXXXX-Farm.Notepad’ using the Citrix XML Service at address ‘http://xxxxxx/scripts/wpnbr.dll’. The XML service returned error: ‘no-available-workstation’.” and “No available resource found for user domainName\xxxxx when accessing desktop group Notepad. This message was reported from the Citrix XML Service at address “. Any idea to solved this issues? Thanks!
The Delivery Controller event log might have more info.
Your published app has a Groups tab indicating the Delivery Group it should launch from. Make sure it’s correct and that at least one machine is powered on, registered, and not in maintenance mode.
Hi Carl,
In your section on Remote Desktop Licensing Configuration, step 3, you parenthetically mention the RDS Licensing role is typically installed on the Delivery Controllers. Are you extrapolating that from Microsoft’s architectural diagram indicating that in an RDSH deployment they recommend installing the Licensing role on the Remote Desktop Connection Broker server? It makes sense to me considering the Delivery Controller is Citrix’s corollary to the RDCB server. However, I ask because working in a Healthcare enterprise environment, I’ve not seen that done where I’ve worked. The RDS Licensing role has typically been installed on a standalone server or multiple servers. And I noticed that Citrix’s Prepare to Install section since release 2103 calls out setting up the RDS Licensing role on an available server that must always be available, but it does not mention that server being the Delivery Controller.
The idea is to avoid building a whole server for this small role.
I’ve also seen it on separate servers if it’s used for more than just Citrix. Or they put in on the Citrix License Server but that usually means a single server.
Our controllers run 1912 CU3 and our VDAs run 2203 CU1. We’ve run into a problem where several VDAs become unregistered (maybe 1-5%) throughout the day. This leaves the current sessions on the VDA hung and they have trouble reconnecting to a new server. Occasionally, controllers will continue to try to send sessions to VDAs that have become unregistered and we have to find and reboot those VDAs to get sessions connecting again. We have a case open and are collecting CDF traces. Any ideas?
Here’s a thread – https://discussions.citrix.com/topic/416254-2203-ltsr-issues/page/9/
We have 4 VDAs, We want to clean up the user profile after log off published apps, have you any ideas? or any better ways, because we want to make user no left any files in VDA. Thank you Carl!
Both UPM and Microsoft Group Policy have a setting to delete cached profiles on logoff.
We are not using UPM or gpo for profile roaming, would like to use the local policy to detele user profile after logoff vda. Thanks.
Schedule a task to run delprof2 periodically. https://helgeklein.com/free-tools/delprof2-user-profile-deletion-tool/
Finally, User accept to use the Local Policy “Delete user profiles older than a specified number of days on system restart”. Thank you.
And I got the CCE-V last week \^o^/ ,learned lots of Citrix knowledge from your posts.
Congratulations! I’m glad you found it useful.
Hi, Carl
We’ve got a very annoying problem.
No. 2 VDAs, some 40 users around, VMs rebooted every night:
MS Windows 2019 with latest WU
CVAD 2203 LTSR CU1
20 vCPU – 40 GB RAM
VMware ESX 6.7.0
Maybe one of the VDA is OK, when all of a sudden the svchost process hosting the termsvcs begins increasing its memory usage, and it doesn’t stop till it reaches 100% and eventually crashes the VM, or, miracoulously, a user originating the problems disconnects (with no chance for us to guess who this user is before).
With Process Explorer we saw that svchost deals with several threads based on picadd.sys and tdica.sys.
We couldn’t find nothing around related on our problem, but CTX463756 talking about problems with tdica.sys on 2203 CU1, solved with 2203 CU2, is the closest thing to our problem we could find.
Do you guess the upgrade to CU2 (to do of course in any case) could help us ? We’re going to carry it out in the next days.
I would start with CU2. If that doesn’t help, then Citrix Support would need to analyze it.
Hi Carl,
I encounter an issue since I have updated my VDA from 1912Cu6 to 2203CU2.
I have created the key shellbridge to fix password prompt issue for Office product (and it works) but after that user session won’t logoff aymore.
If I delete the shellbridge key then the user session can logoff.
Seems i’am not the only one :
https://discussions.citrix.com/topic/416863-sessions-not-logging-out-after-vda-2206-installed/
Do you habe an idea ?
What processes are still running? Does adding them to LogoffCheckSysModules help?
Hello Carl,
Can we install Citrix components (DDC, SF, VDA, Cloud Connector) on Data Disk (separate disk e.g. D drive) instead of OS disk?
Regards,
Dipak.
Not sure about Cloud Connector but the others let you choose the install location.
Has anyone noticed Win10 single session screen lock timer no longer being honored in 2203 CU2? I upgraded my image from CU1 after putting on the Feb 14th Windows patches. The existing GP is coming down for interactive logon/machine inactivity limit (verified in the registry). Also have the SetDisplayRequiredMode = 0 in the golden image. Can’t find anything different, but these published desktops just aren’t locking. OS is win10 enterprise LTSC 21H2 19044.2604.
Did you make sure your other policies are still set? I had the same issue but adding the reg key is all i needed since these other settings were handled via GPO instead of LGPO.
https://support.citrix.com/article/CTX205214
Yep, literally nothing else had changed 😀 I can go into the registry and see everything is set in there… just seems to not be honoring it. I might crack open the golden image and reboot it once or twice just to make sure everything has sunk in…
I only have the CU2 image in our small pilot test group of about 35 machines. The previous image is unaffected (machines are in the same OU/same policies applied across the board).
Encountering the same issue AFTER upgrade from 2203 LTSR CU1 to CU2
I am also having this issue. Any fix? I double checked all the previous gpo’s are being applied and show up in the registry, and I’ve added back the SetDisplayRequiredMode=0, but screensaver still isn’t locking.
It has to be applied to the vdisk itself in registry, not via GPO. It worked for me.
Carl,
I’ve recently started the upgrade from 19.12 to 2203 and I ran across your notes on the Virtual Channel Whitelist setting being enabled by default. We’ve disabled the setting via policy and our Zoom VDI channel works without issue now, but our RTME pack will not connect at all.
We’ve tried whitelisting the process manually and disabling the Virtual channel allow list. If I revert back to 1912 the realtime connect will connect without issue. I’m currently using version 2.9.400. Any ideas?
Did you follow this? https://docs.citrix.com/en-us/hdx-optimization/2-9-ltsr/troubleshooting.html#add-the-realtime-optimization-pack-virtual-channel-to-the-virtual-channel-allow-list
Yes, but we figured it out. The RTME worked fine for windows and macs, only not on our igel, seems like the HDX camera option must be enabled on the igel for RTME to connect properly. All good now.
Hi Carl,
https://support.citrix.com/article/CTX331367/how-to-update-vda-registration-port-on-ddc
I run all cmd and it can register, the it could be used.
But the
cd “C:\Program Files\Citrix\Broker\Service”
BrokerService.exe /show
BrokerService.exe -vdaport 8443
HighAvailabilityService.exe /show
HighAvailabilityService.exe -vdaport 8443
HighAvailabilityService.exe /show
BrokerService.exe /show
but the Citrix Health Assistant show :Warning:Not all Controllers are reachable.Check log for details..
i found it use 80 to test DDC.
Becuse our user don’t want to see any 80 port in firewall taffic.
Could you help to guide me where 80 port be used, and how to modify it. Thanks you.
Did you change the port number on each VDA? Go to Apps and Features. Find VDA and click Change. There’s a page to change the port number.
Thank for Carl.
I also change the port 8443 in VDA. It could registeration in DDC, and could be used as normal.
I found below Port DDC between VDA 80 port (i change to 8443) is Bidirectional.
But i find
199 is VDA:
TCP 10.1.11.199:49805 10.1.11.194:8443 ESTABLISHED 4252
194 is DDC:
TCP 10.1.11.194:8443 10.1.11.199:49805 ESTABLISHED 4
Seem it just need open firewall DDC:8443to VDA , no need VDA:8443 to DDC.
Virtual Delivery Agent (5.x and later) to Controller Port TCP 80(Bidirectional) Used by process WorkstationAgent.exe for communicating with Controller
Hi Carl,
End user require to use 8443 for VDA registration with DDC.
BrokerService.exe -vdaport 8443
I follow below guide, but get red warning.
I should fallback to 80 then the red warning miss.
Could you help to try? THanks.
https://support.citrix.com/article/CTX331367/how-to-update-vda-registration-port-on-ddc
The following service endpoints must be identical between the BrokerService.exe.config and HighAvailabilityService.exe.config files but currently differ: ;;;
Error updating 2203.CU1 MultiOS VDA to 2203.CU2 WS2019
First book ok, then “error in installation”
anyone with same problem ? solution ?
Anyone having these issues after VDA upgrade into 2203 CU1 ?
– random msedge.exe crash + BSOD (kernelbase.dll)
There’s a tdica.sys crash. https://support.citrix.com/article/CTX463756/2203-or-2206-server-os-vda-may-experience-bsod-on-tdicasys
also the same problem?
TDICA event id 1019 “received an invalid packet during its SSL handshake ”
Logon is very slow
just upgraded the vda to 2209, still getting the tdica event id 1019 under system and getting a short grey screen on launch…any updates on this?
Do you make use of Adaptive Transport? What happens when you disable it?
no using TCP, internal and external, still getting the message…
Hi, Carl we have a situation with Windows 10 Multisesion with GPU Nvidia over Azure and VDA 22.03 CU1, the behaivor is that the user logon to Citrix AG and then launch the desktop with a Gray Window at the Citrix Workspace. If the user wait 1 minute and reconnect to them, can see their desktop and can work, but only fails the first time of the session, if reconnect no problem.
Same issue here over since VDA 2203CU1 upgrade host on WS2019
We have the issue with Windows 10 Multisesion, and citrix with 3 cases doesn’t find any solution, we reinstalled the VDA, installed the 2209, we moved some regedit and still has the issue.
Where do I configure BIS-F GPO? Template OU or VDA OU? I can not find any step by step guide for BIS-F for Citrix environment
Having some trouble on a Citrix environment where I am presenting Windows 10 desktops. I have just upgraded the environment from 1912 CU4 to 2203 CU1. I am getting this error: the session will be disconnected due to a policy evaluation error. Try to connect again. If the problem persists, contact your administrator. The session doesn’t even start. I get disconnected and then the VDA reboots.
I have the same problem, did you find the solution?
I am seeing the same thing, did you find the solution?
Can anyone confirm normal behavior with Workspace for Mac when using virtual apps on multi-session server VDA version 2203 CU1? Seeing some strange app switching behavior here.
Is CVAD 2203 ltsr compatible with VDA 7.15 ?
Yes. VDA 7.15 should register with Delivery Controller 2203.
Restore on failure option fails due to AV, has anyone tested that with AV running and has a recommendations around exclusions for Citrix VDA?
Same here.
tdica.sys happen a few times now since installing the 2203 VDA agent
Has anyone resolved the tdica.sys bsod issue? I use VDA 2203, PVS 2203, Virtual Apps 2203 and Target Device SW 2203 since june with no issues. Since vSphere has been updated to 7.0.3 we have several server crashes every day (2 – 10 per day out of 150). I assume a compatibility issue between VMware and Citrix.
Same problem in 2203 CU1?
vda 2203 cu1, yes. Virtual Apps 2203 cu0.
Here’s a thread – https://discussions.citrix.com/topic/417125-citrix-vms-crashes-tdicasys-blue-screen-2203/page/2/#comment-2093594
We made no change to vmware what so ever. Only updated the VDA on our GMs from LTSR 1912 CU4 to LTSR 2203 CU1. BSOD with tdica.sys stop code: system thread exception not handled seems to only be multisession VDA. No BSOD in single session VDA. Tried everything, no resolution. Reverting back to 1912 CU4 LTSR VDA
Have you enabled html5 access (receiver for web) in StoreFront? Disable it and check again. In my case the bsod crashes stopped immediately after I’ve disabled it.
Hi. After upgrade the master image of mcs to 2203 ltsr version, the deployed machines dont get ip from dhcp. Gets the same ip that master.
Hi,
I have the same problem. I have open a case #81241400. If you use a DHCP adress on the master this work but with a static adress is doesn’t work.
https://discussions.citrix.com/topic/416374-2203-ltsr-mcs-provisioning-dhcp-not-set/#comment-2091338
Any one having these issues on 2203 LTSR?
1. TdIca.sys BSOD
2. ChromeOS no audio through Windows Media Player (if you wait 2 minutes it starts playing)
3. Mac workspace app frequent disconnects
https://www.citrix.com/downloads/workspace-app/betas-and-tech-previews/workspace-app-tp-for-mac.html might fix the Mac workspace app issue.
I’ve seen the tdica.sys happen a few times now since installing the 2203 VDA agent. Have not currently experienced the other issues.
Trying to get anonymous sessions working on a new 2019 image. Normal named sessions seem fine. But when i launch an anonymous session it gives me the “There is a problem with your license for Remote Desktop and the session will end in 60 minutes.” message. Any ideas on that one? Logging in as a named user and checking RDS License diagnoser says everything is fine. Tried editing local gpo to select per use and specify a license server, etc.
The VDA virtual machine sizing for Windows Server 2019 RDSH as recommended in your post has increased a fair chunk. Is there a reason behind this recommendation?
You mean CPUs and Memory assigned to each RDSH VM? 2019 is more efficient at multi-CPU scheduling than prior versions.
Ideally you take the physical hardware and divide it by the number of desired VMs per host keeping in mind NUMA boundaries. E.g., 40 physical cores over 4 VMs = 10 vCPUs per VM. Or 40 physical cores over 8 VMs = 5 vCPUs per VM. Then you divide memory by the same number of VMs.