Navigation
- Change Log
- Create Group Policy Objects (GPOs)
- Windows Group Policy ADMX Templates
- Microsoft Edge (Chromium)
- Microsoft Teams
- Microsoft FSLogix
- OneDrive ADMX Template
- Group Policy Computer Settings for VDAs
- VDA Receiver Configuration
- Group Policy User Settings for VDAs (separate article)
💡 = Recently Updated
Change Log
- 2023 July 22 – Windows GPO ADMX Templates – added Administrative Templates (.admx) for Windows 11 2023 Update (23H2)
- 2023 Aug 23 – FSLogix– updated group policy screenshots for FSLogix 2210 Hotfix 2
- 2021 Mar 15 – Edge – updated link for Kasper Johansen Microsoft Edge in Citrix – Revamped
- 2021 Feb 25 – OneDrive – added link to CTP James Rankin Managing OneDrive on Citrix Virtual Apps and Desktops
- 2020 Oct 15 – Teams – Citrix script to disable GPU for each user
- 2020 Sep 18 – OneDrive .admx – updated for machine-wide installation
- 2020 July 9 – Computer Settings – Use WDDM graphics display driver for Remote Desktop Connections = Disabled for Windows 10 version 2004 with VDA earlier than VDA 2006. Source = Windows 10 v2004 – Citrix Known Issues
- 2020 Jun 23 – Group Policy Computer Settings for VDAs – added Audit process tracking for Director.
- 2020 May 28 – FSLogix – added link to CTP James Kindon Navigating Azure Storage options for FSLogix Containers
- 2020 May 7 – Teams – Microsoft recommends excluding the Media-Stack folder from profile roaming.
- 2020 Apr 23 – Teams – added Don’t install Microsoft Teams with new installations or updates of Office to prevent the per-user install.
- 2020 Apr 23 – Teams – added Prevent Microsoft Teams from starting automatically after installation
- 2020 Apr 22 – GPO Computer Settings – added Show clear logon background setting – source = Citrix Discussions
- 2020 Apr 10 – FSLogix – added link to CTP James Rankin and CTP Ryan Revord Spreading users over multiple file shares with FSLogix Profile Containers.
- 2020 Apr 7 – FSLogix – added link to FSLogix in a Citrix Provisioning environment
- 2020 Mar 29 – FSLogix and Citrix – multi-session write-back for FSLogix Profile Container
- 2020 Mar 16 – FSLogix – added links to CTX270433 Outlook Search Indexing Fails on Windows Server 2019 VDA and CTP James Kindon Windows Search in Server 2019 and Multi-Session Windows 10.
Create Group Policy Objects
- Within Active Directory Users and Computers (dsa.msc), create a parent Organizational Unit (OU) to hold all VDA computer objects.
- Then create sub-OUs, one for each Delivery Group. The VDA computer objects for each Delivery Group should be placed in these sub-OUs. Notes:
- The only objects that belong in these VDA OUs are the VDA computer accounts.
- There’s no need to put any user accounts in these VDA OUs since Group Policy Loopback Processing mode will handle user settings.
- The computer objects for the Citrix brokering infrastructure machines (Controllers, StoreFront, Director, etc.) should go in normal server OUs, and not in the VDA OUs.
- Separate VDA sub-OUs for each Delivery Group lets you apply different GPO settings to each Delivery Group.
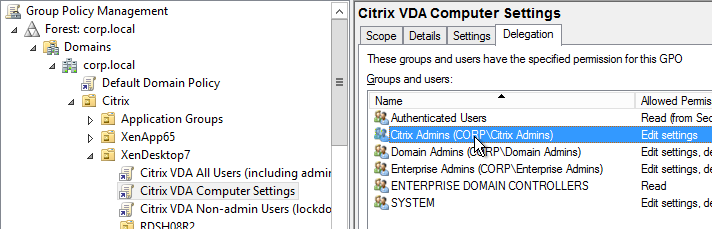
- Grant Citrix Admins the permission to add computer objects to the VDA OUs.
- Grant Citrix Admins the permission to link GPOs to the VDA OUs.
- Master images should be placed in the VDA OUs so the VDA GPO Computer Settings can be burned into the master image. This avoids timing issues when non-persistent machines reboot and GPO settings haven’t applied yet.
- The only objects that belong in these VDA OUs are the VDA computer accounts.
- Move the VDAs from the Computers container to one of the Delivery Group OUs.
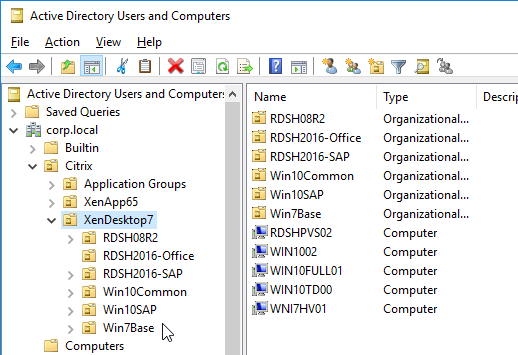
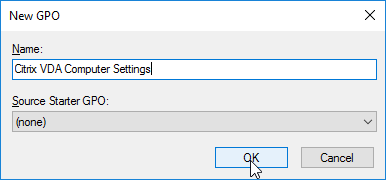
- Within Group Policy Management Console (gpmc.msc), create a Group Policy Object (GPO) called Citrix VDA Computer Settings, and link it to one of the Citrix OUs. This particular GPO usually applies to all Delivery Groups, and thus should be linked to the parent OU. Or you can link it to Delivery Group-specific sub-OUs.
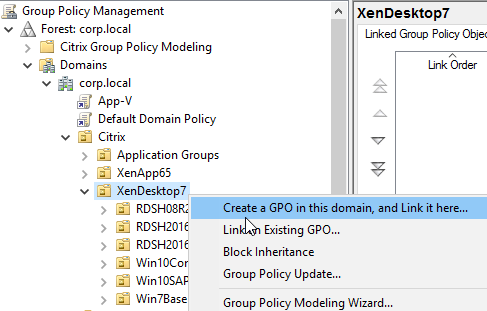
- On the left, click the new VDA Computer Settings GPO to highlight it.
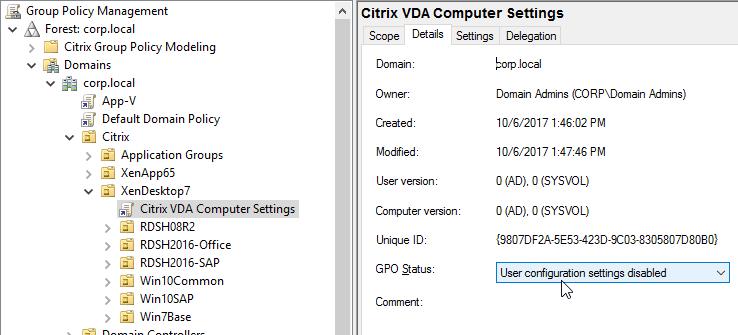
- On the right, switch to the Details tab.
- Change the GPO Status drop-down to User configuration settings disabled. This GPO will only contain computer settings.
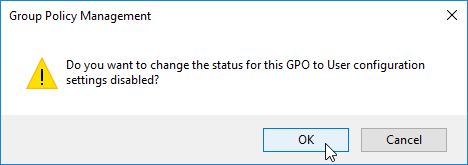
- Create and link two new Citrix-specific GPOs (in addition to the Citrix VDA Computer Settings GPO).
- One of the GPOs is called Citrix VDA All Users (including admins), and the other is called Citrix VDA Non-Admin Users (lockdown).

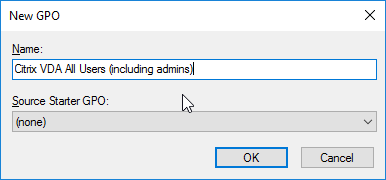
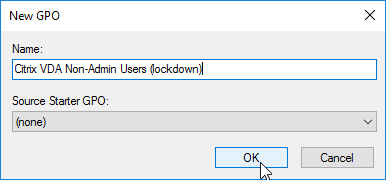
- Modify the Details page of both of these GPOs, and set GPO Status to Computer configuration settings disabled. These GPOs will only contain user settings.
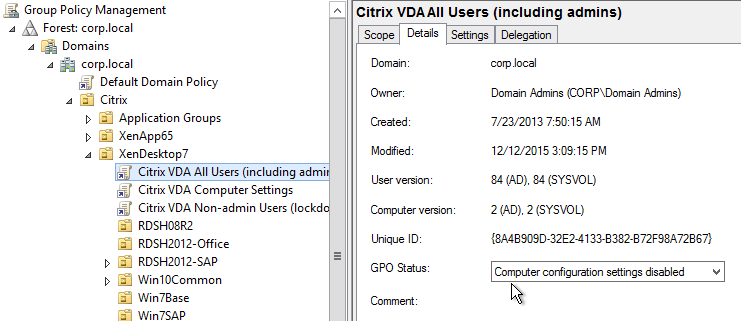
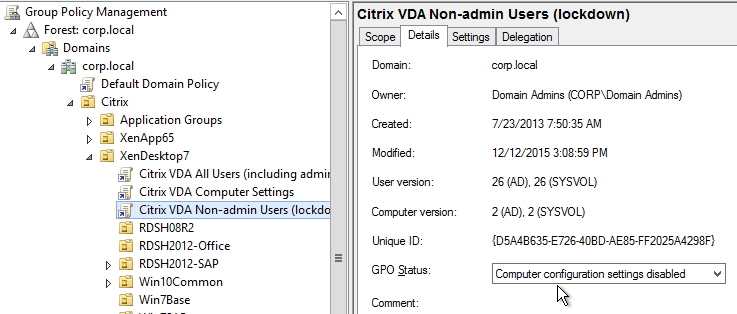
- On the left, click the Citrix VDA Non-Admin Users GPO to highlight it.
- To delegate administration of this GPO to Citrix Admins:
- On the right, switch to the Delegation tab, and click Add.
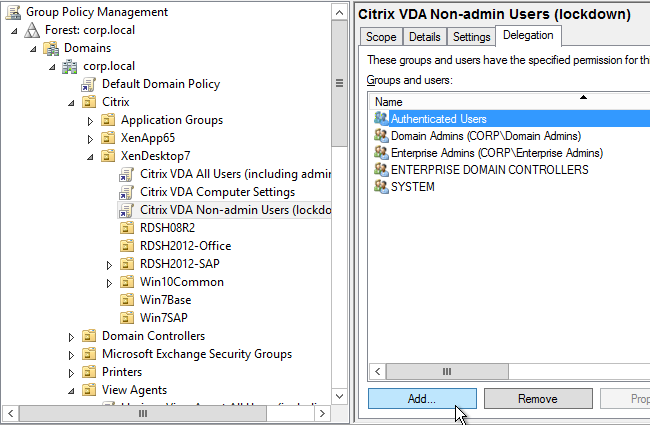
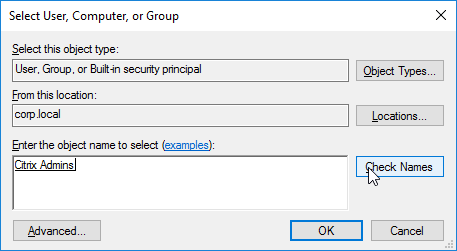
- Find your Citrix Admins group, and click OK.
- In the Add Group or User window, change the Permissions to Edit settings, and click OK.
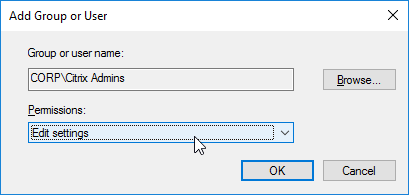
- On the right, switch to the Delegation tab, and click Add.
- To prevent the user lockdown GPO from applying to administrators:
- On the Delegation tab, click Advanced.
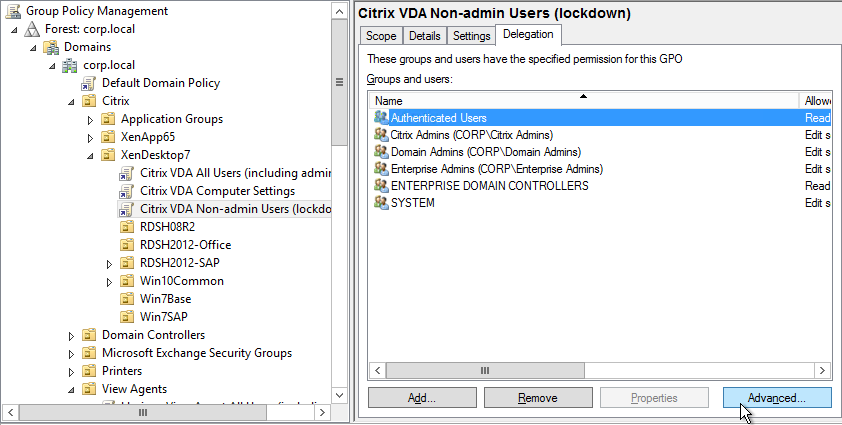
- On the top half, click the Citrix Admins group to highlight it.
- Scroll down to reveal the Apply Group Policy row, and then place a check mark in the Deny column.
- If desired, you can also deny the GPO to Domain Admins and Enterprise Admins.
- Click OK to close the Security Settings window.
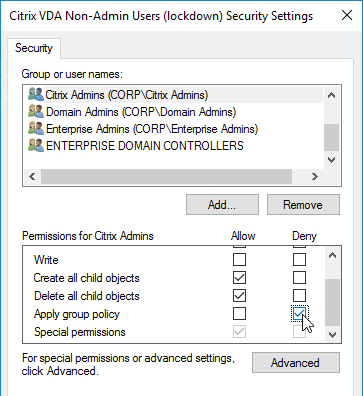
- Click Yes when asked to continue.
- On the Delegation tab, click Advanced.
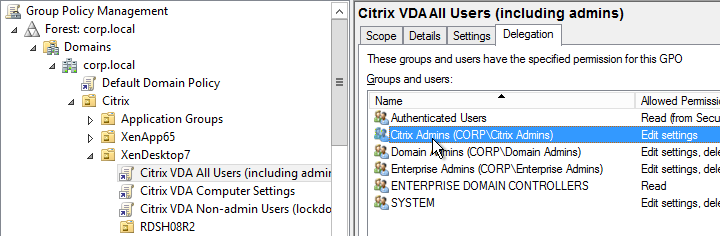
- To delegate the other two GPOs, add the Citrix Admins group with Edit Settings permission. But don’t deny Apply Group Policy. The deny entry is only needed on the Lockdown GPO.
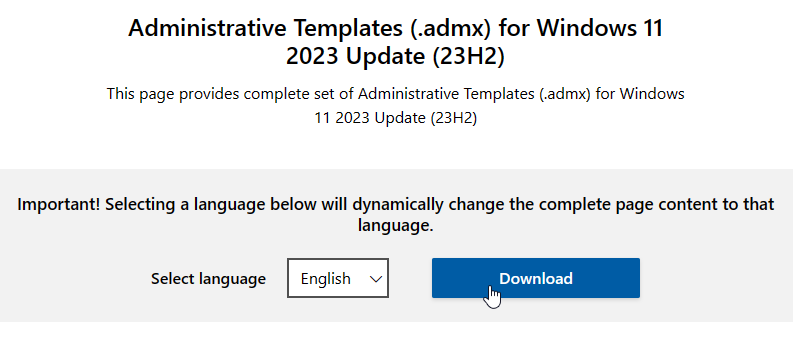
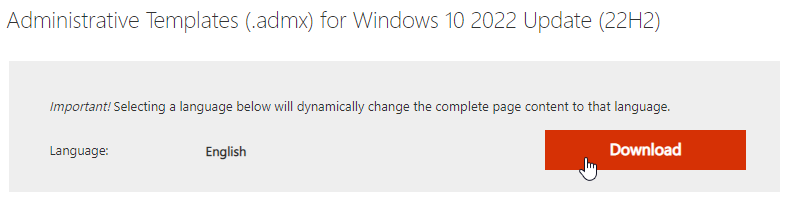
Windows Group Policy Templates
The latest Windows 10 or Windows 11 GPO templates includes the GPO settings for Windows Server.
- Download the Administrative Templates (.admx) for Windows 10 2022 Update (22H2) or Administrative Templates (.admx) for Windows 11 2023 Update (23H2).
- Run the downloaded Administrative Templates (.admx) for Windows.msi file.
- In the Welcome to the Administrative Templates (.admx) for Windows Setup Wizard page, click Next.
- In the End-User License Agreement page, check the box next to I accept the terms and click Next.
- In the Custom Setup page, record the Location field since you’ll need to go there later. Click Next.
- In the Ready to install Administrative Templates (.admx) for Windows page, click Next.
- In the Completed the Administrative Templates (.admx) for Windows Setup Wizard page, click Close.
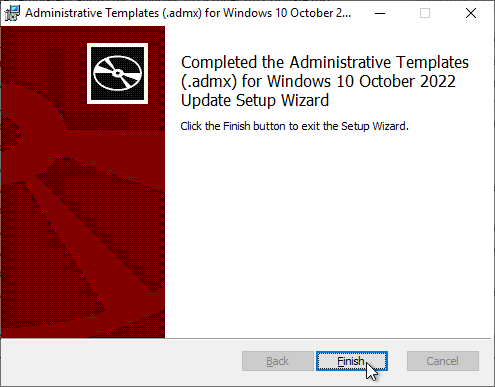
- In File Explorer, go to C:\Program Files (x86)\Microsoft Group Policy\Windows 11 October 2023 Update (23H2) or C:\Program Files (x86)\Microsoft Group Policy\Windows 10 October 2022 Update (22H2).
- Copy the PolicyDefinitions folder.
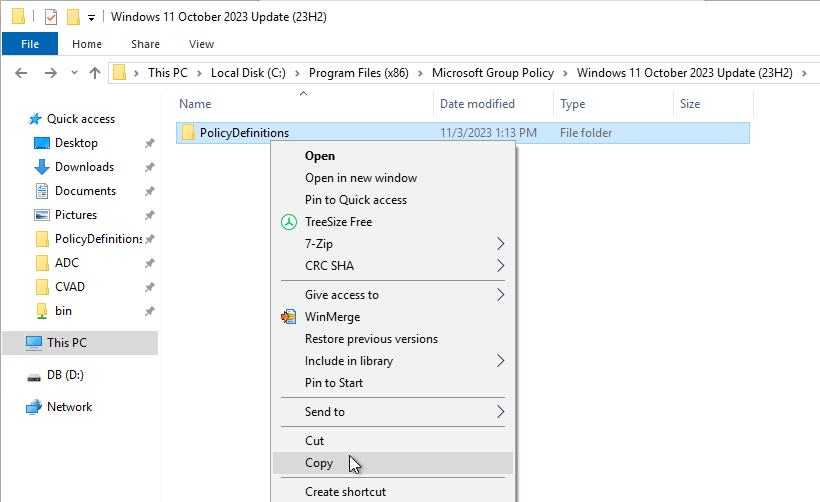
- Go to your domain’s sysvol (e.g., \\corp.local\sysvol) and in the corp.local\Policies folder, paste the PolicyDefinitions folder. If you don’t have this folder, then you can create it. Or copy the files to C:\Windows\PolicyDefinitions as detailed next.
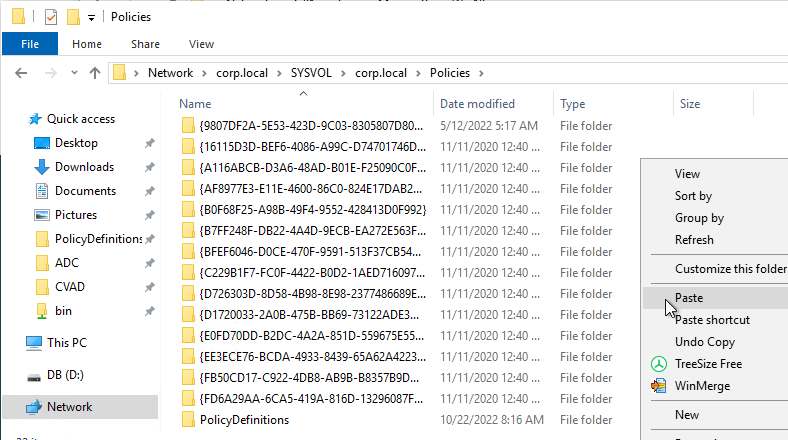
- If prompted, replace the existing files.
- If prompted, replace the existing files.
- If your Sysvol does not have a PolicyDefinitions folder, then instead go to C:\Windows\ and paste the folder. Overwrite the existing files.

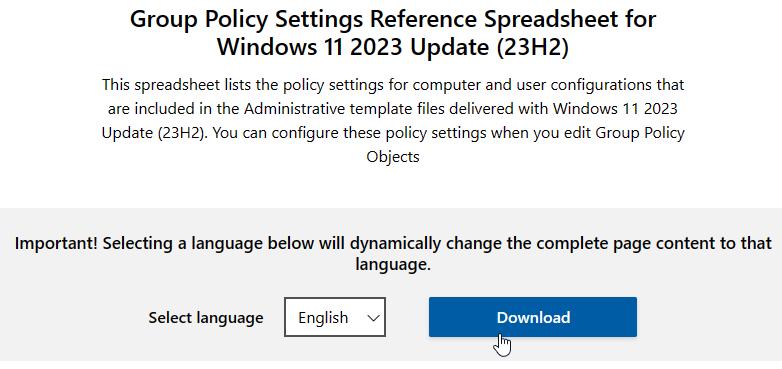
See Group Policy Settings Reference Spreadsheet for Windows 11 2023 Update (23H2) for a spreadsheet containing all GPO settings in Windows.
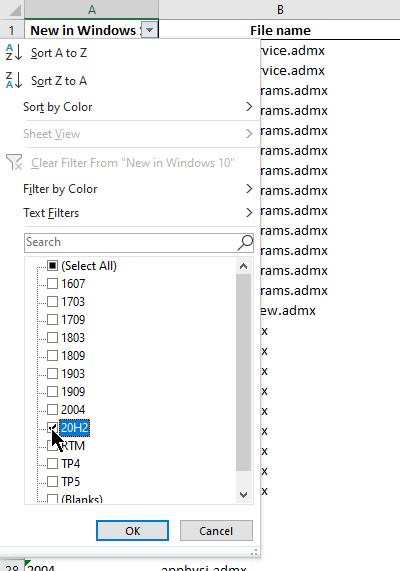
The spreadsheet can be filtered to only show the newest settings.
Microsoft Edge (Chromium)
Download and install Microsoft Edge for Business on your VDA machines or Horizon Agent machines.

Installation and Configuration instructions can be found at Kasper Johansen Microsoft Edge in Citrix – Revamped. The article details group policies for Edge.
Avanite Roaming Edge Chromium details the folders that should be roamed by Citrix Profile Management (UPM) or VMware Dynamic Environment Manager (DEM).
Microsoft Teams
Prevent the per-user version of Teams from installing with Office 365 (aka Microsoft 365 apps). Configure this GPO setting before installing Office. Then you can later install the machine-wide version of Teams. More details at Microsoft Docs.
This setting requires the latest Office GPO templates to be installed.
- Edit a GPO that contains Computer Settings.
- Updates – Computer Configuration | Policies | Administrative Templates | Microsoft Office 2016 (Machine) | Updates
- Don’t install Microsoft Teams with new installations or updates of Office = enabled
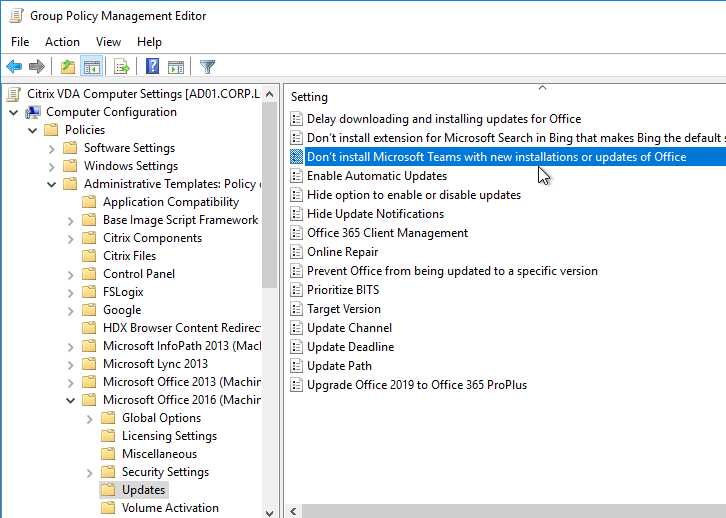
- Don’t install Microsoft Teams with new installations or updates of Office = enabled
Prevent Microsoft Teams from starting automatically after installation. Set this GPO setting before you install Teams. This setting requires the latest Office GPO templates to be installed.
- Edit a GPO that contains User Settings. These User Settings probably won’t apply unless you enable Group Policy Loopback Processing in a computer settings GPO.
- Teams – User Configuration | Policies | Administrative Templates | Microsoft Teams
- Prevent Microsoft Teams from starting automatically after installation = enabled
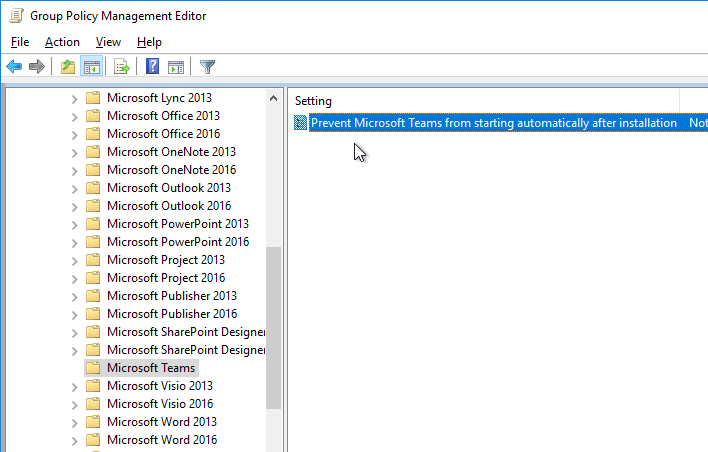
- Prevent Microsoft Teams from starting automatically after installation = enabled
Install Teams using the machine-based installer. See Manuel Winkel Install Teams & OneDrive in Citrix (Machine-Based) and CTP James Rankin Microsoft Teams on Citrix Virtual Apps and Desktops, part #1 – installing the damned thing.
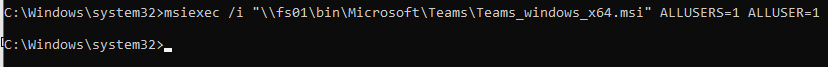
- The Machine-wide installer does not update itself. You must periodically download the latest version, uninstall the Machine-wide installer, and install the latest version.
Microsoft recommends excluding the Media-Stack folder from roaming. Add the exclusion for AppData\Roaming\Microsoft\Teams\media-stack\ to Citrix Profile Management’s Exclusion List – Directories setting.
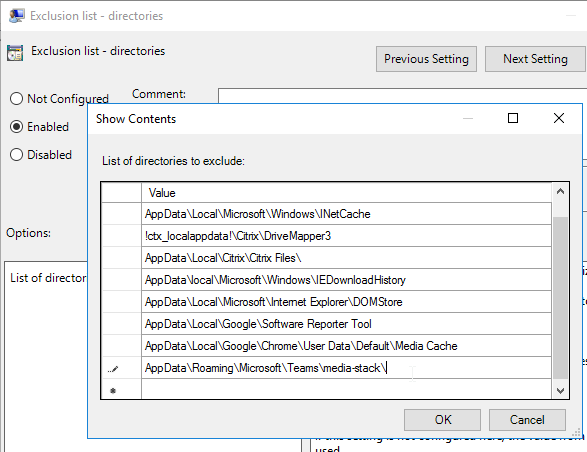
If your VDAs don’t have GPUs, then disable GPU in Teams to reduce CPU. Citrix has a PowerShell script that can disable this setting for each user. Also see:
- CTP James Rankin Microsoft Teams on Citrix Virtual Apps and Desktops, part #2 – default settings and JSON wrangling
- CTP James Rankin Microsoft Teams on Citrix Virtual Apps and Desktops, part #3 – 18 tips for optimizing performance
Microsoft FSLogix
If you need to roam the user’s Outlook .OST file (Outlook Cached Mode), Outlook Search Index, OneDrive cache, OneNote data, SharePoint data, Skype data, and/or Teams data, then download, install, and configure Microsoft FSLogix. FSLogix has more Office roaming features than Citrix Profile Management. A common architecture is to enable FSLogix Office Container for the Office cache files and use Citrix Profile Management for all other roaming profile files and registry keys.
Microsoft FSLogix is free for all Microsoft RDS CALs, Microsoft Virtual Desktop Access per-user CALs, and all Microsoft Enterprise E3/E5 per-user licenses. Notice that per-device licenses are excluded. See Licensing Requirements at Microsoft Docs.
G0-EUC tested FSLogix Profile Container (not Office Container) and found that it reduces capacity by 27%. (source = The impact of managing user profiles with FSLogix)
Do the following to install Microsoft FSLogix on the VDA machine:
- Go to https://aka.ms/fslogix_download.
- Extract the downloaded .zip file.
- In the FSLogix \x64\Release folder, run FSLogixAppsSetup.exe.
- Check the box next to I agree to the license terms and conditions and click Install.

- In the Setup Successful page, click Restart.

FSLogix is configured through Group Policy or by editing registry values on each FSLogix Agent machine. Here is some info on group policy configuration:
- The FSLogix .zip file contains fslogix.admx and fslogix.adml files for configuration of FSLogix through Group Policy. Copy these files to your PolicyDefinitions folder. The .adml file goes in the en-US folder.

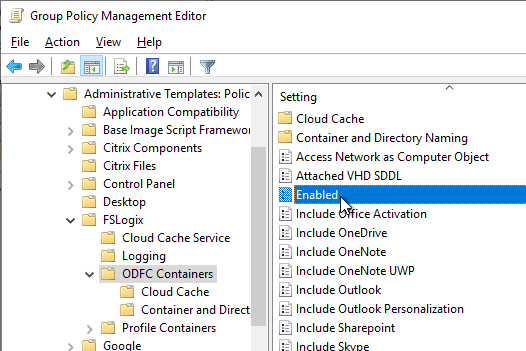
- Find the settings in Group Policy Editor at Computer Configuration | Policies | Administrative Templates | FSLogix
- Note that FSLogix 2210 Hotfix 2 (2.9.8612.60056) and newer have a different group policy structure than older versions.
- The ODFC Containers node controls Office Containers only. The Profile Containers node lets you capture the entire profile and not just Office. You can also configure both as detailed at FAQ: How to use Office 365 Containers and Profile Containers together. Citrix environments typically combine FSLogix Office Containers with Citrix Profile Management. VMware Horizon environments typically use FSLogix Profile Container to replace DEM Personalization.
- You’ll need a file share with appropriate permissions to store the Office containers or Profile Containers.
- See CTP Aaron Parker A Practical Guide to FSLogix Containers Capacity Planning and Maintenance.
- See CTP James Kindon Architecting for FSLogix Containers High Availability: VHD Location vs Cloud Cache
- See CTP James Kindon Navigating Azure Storage options for FSLogix Containers – Azure Files, Azure NetApp, file servers
- See FSLogix in a Citrix Provisioning environment for Cloud Cache with Citrix PVS.
- Then configure either the VHD location setting, or the Cloud Cache Locations setting, but not both. See Configure Cloud Cache at Microsoft Docs.
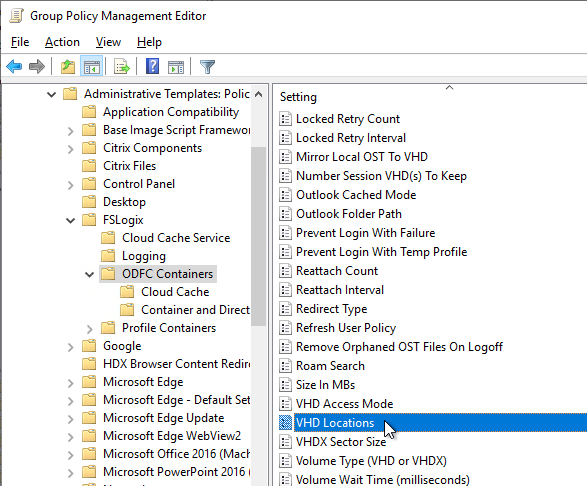
- VHD Location is a machine setting that applies to all users that log into the machine. If you want different paths for different users, then configure the ObjectSpecific registry key as detailed at Microsoft Docs. CTP James Kindon uses this configuration at Designing Profile Management with Active-Active Resource Locations.
- VHDLocations can have multiple values. See CTP James Rankin and CTP Ryan Revord Spreading users over multiple file shares with FSLogix Profile Containers.
- VHDX Profile Cleanup – Aaron Parker’s Github
- VHDX Compaction – See Invoke-FslShrinkDisk.ps1 at Github
- Set Volume Type to VHDX.
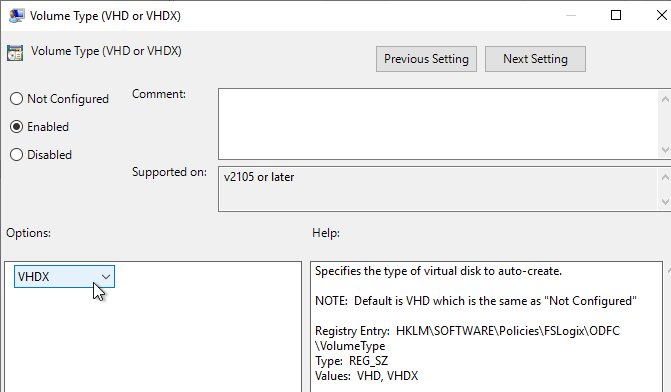
- The .vhdx files are thin provisioned and can grow up to the maximum Size in MBs, which defaults to 30 GB. Newer versions of FSLogix let you increase this size later.
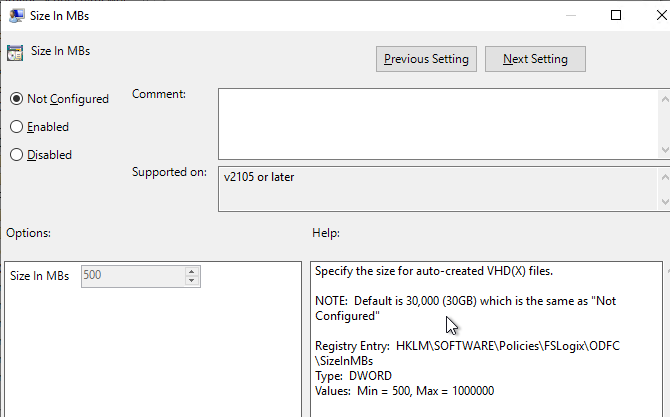
- Under Container and Directory Naming enable the setting Flip Flop Profile Directory Name.
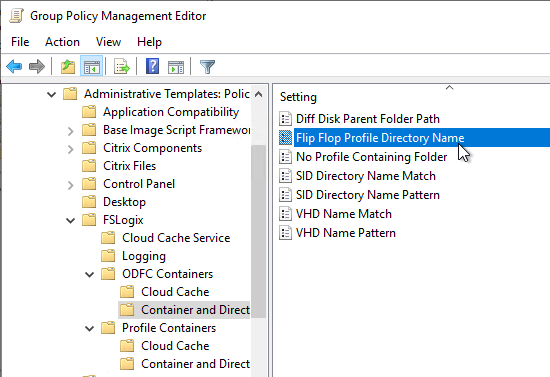
- For Office Containers, back in the ODFC Containers node, review each of the Include settings and enable whichever data you want to include in the Office Container. More details at Configure ODFC Container at Microsoft Docs.
- Since an FSLogix Container can only be mounted on one machine, consider setting Prevent login with failure. This causes the user to see a window if the container is already mounted and the user will have to call the help desk to clear the other session.
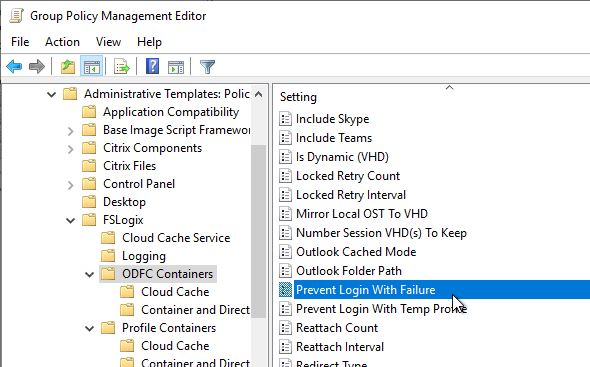
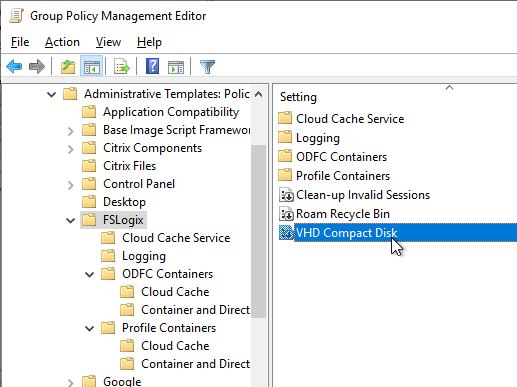
- FSLogix 2210 and newer automatically compact .vhdx files when they have free space. It’s enabled by default and is configurable on the left, directly under the FSLogix node. On the right, configure the VHD Compact Disk setting.
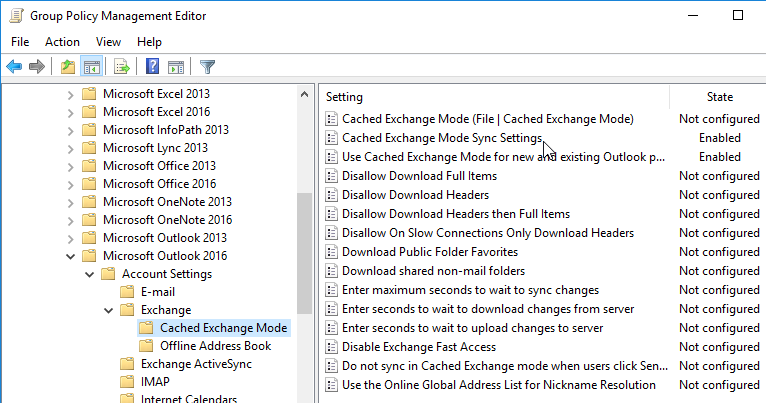
- In a Group Policy that applies to Citrix users, you might want to configure Cached Exchange Mode Sync Settings to reduce the size of the .ost files. You’ll need to install the Office GPO templates if you haven’t already. Then find the setting at User Configuration | Policies | Administrative Templates | Microsoft Outlook 2016 (also applies to 365 and 2019) | Account Settings | Exchange | Cached Exchange Mode.
Other FSLogix Configurations and Links
- Citrix Profile Management – To avoid conflicts with Citrix Profile Management, configure Citrix Profile Management to exclude the Office cache folders. See Office Container Exclusions for details.
- Citrix App Layering – The FSLogix driver might conflict with Citrix’s App Layering drivers. See Adjust driver (frxdrvvt) altitude with UniDesk.
- Citrix Blog Post Citrix App Layering and FSLogix profile containers
- See FSLogix Forum FAQs
- Microsoft Teams – When installing Microsoft Teams, use the per-machine Teams installer instead of the normal per-user Teams installer. Dale Scriven explains the per-machine Teams installer in more detail. Note that the per-machine Teams installer does not auto-update so administrators must manually install updates.
- Microsoft OneDrive – Install the sync client per machine instead of the normal per-user installer.
- Migrate existing OST/PST files – Aaron Parker’s Github
- How to open an FSLogix Support Request
Full Profile Container (not just Office):
- CTP Aaron Parker Crowd Sourced Redirections.xml for FSLogix Profile Containers.
- FSLogix in a Citrix Provisioning environment for more Redirections.
- Copy an existing user profile into an FSLogix full profile container – FSLogix Docs
- VHDX Profile Cleanup – Aaron Parker’s Github
- VHDX Compaction – FSLogix 2210 Hotfix 1 and newer have compaction built in. Or see Invoke-FslShrinkDisk.ps1 at Github
- In FSLogix 2210 Hotfix 1 and newer, enable Roam Identity.
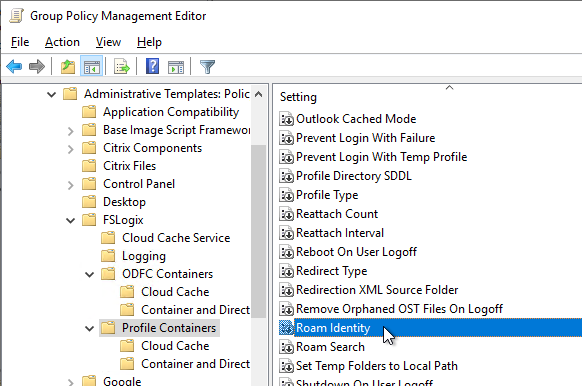
- Citrix Profile Management 2003 has a feature to perform multi-session write-back for FSLogix Profile Container.
OneDrive ADMX Template
See CTP James Rankin Managing OneDrive on Citrix Virtual Apps and Desktops 💡
Microsoft has a per-machine installation of the OneDrive sync client. To reduce the size of your roaming profiles, the per-machine install is strongly recommended over the normal per-user install of OneDrive.
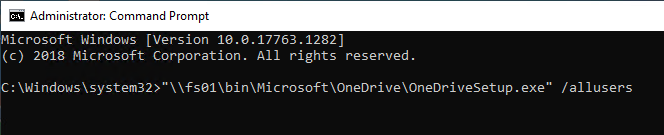
To enable Files-on-demand, you’ll need the OneDrive ADMX Template.
- Go to a Windows 10 1709 or Windows Server 2019 or newer machine that has OneDrive installed.
- If machine-wide installation, go to C:\Program Files (x86)\Microsoft OneDrive.
- If per-user installation, go to %localappdata%\Microsoft\OneDrive.
- Double-click the latest version.
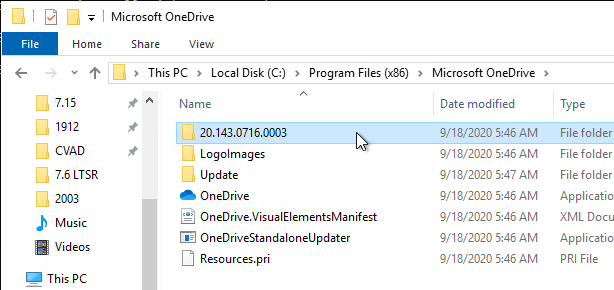
- Then open the adm folder.
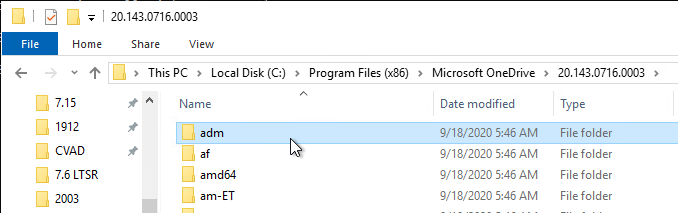
- Right-click the OneDrive.admx file and copy it.
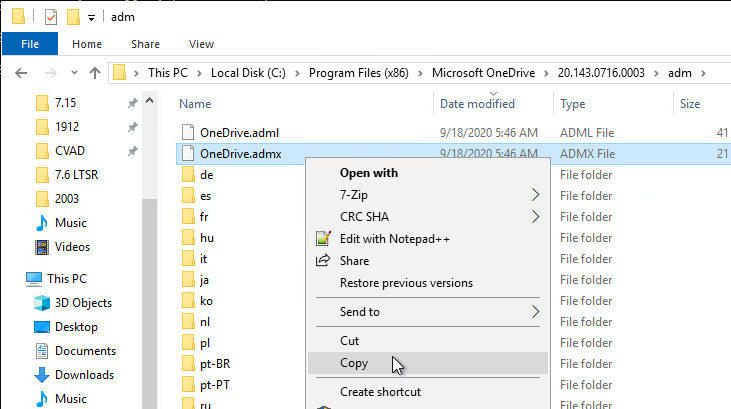
- If your domain has PolicyDefinitions in SYSVOL (\\corp.local\sysvol\corp.local\Policies\PolicyDefinitions), paste the .admx file there.

- If you don’t have SysVol PolicyDefinitions, then go to C:\Windows\PolicyDefinitions and paste the .admx file.

- If you don’t have SysVol PolicyDefinitions, then go to C:\Windows\PolicyDefinitions and paste the .admx file.
- Go back to the OneDrive files and copy OneDrive.adml.
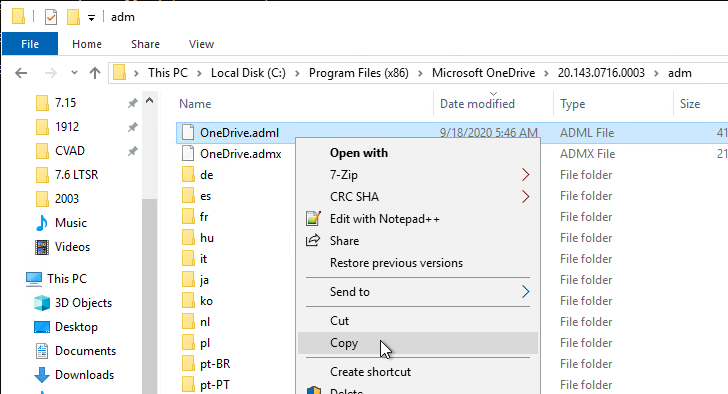
- If your domain has a PolicyDefinitions central store in SYSVOL, paste the .adml file to the en-us folder in PolicyDefinitions in SYSVOL. en-US is a subfolder of the PolicyDefinitions folder.

- If you don’t have SysVol PolicyDefinitions,, then go to C:\Windows\PolicyDefinitions\en-US and paste the .adml file. en-US is a subfolder of the PolicyDefinitions folder.

- If you don’t have SysVol PolicyDefinitions,, then go to C:\Windows\PolicyDefinitions\en-US and paste the .adml file. en-US is a subfolder of the PolicyDefinitions folder.
Group Policy Computer Settings
Edit the Citrix VDA Computer Settings GPO and enable the settings shown below. All settings are located under Computer Configuration > Policies.
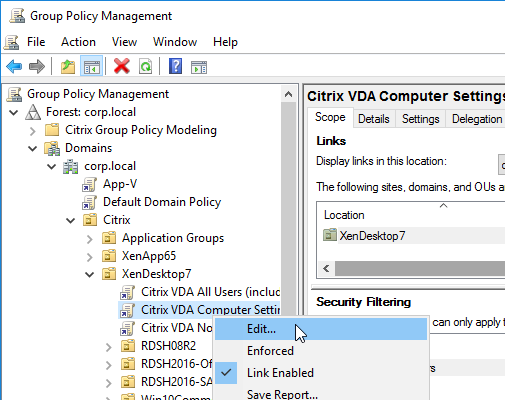
Some of the settings in this section might require the newer Windows Group Policy Templates.
Process tracking for Director
- Audit Policy – Computer Configuration | Policies | Windows Settings | Security Settings | Local Policies | Audit Policy
- Audit process tracking = success – Source = Diagnose user logon issues at Citrix Docs.
Idle Time to Lock Session
- Security Options – Computer Configuration | Policies | Windows Settings | Security Settings | Local Policies | Security Options
- Interactive logon: Machine inactivity limit – Windows 8/2012 and newer – published desktops only – seconds of idle time before session locks
Control Panel
- Settings Page Visibility – Computer Configuration | Policies | Administrative Templates | Control Panel
- Settings Page Visibility
- Windows Server 2016 and Windows 10 1607 support was added with the September 2018 Windows patches. Otherwise, it’s only available in Windows 10 1703 and newer.
- Also with the September 2018 patches, the Settings Page Visibility setting is added to the User half of the GPO. See https://www.carlstalhood.com/group-policy-objects-vda-user-settings/#settingspage for details. Before September 2018, this setting is Computer half only, which means it applies to all users, including administrators.
- Winaero How To Hide Settings Pages in Windows 10 describes this new setting. Also see TechNet Hiding pages in Settings with Windows 10 1703.
- Settings Page Visibility
Teams
Prevent the per-user version of Teams from installing with Office 365 (aka Microsoft 365 apps). Configure this GPO setting before installing Office. Then you can later install the machine-wide version of Teams. More details at Microsoft Docs.
This setting requires the Office GPO templates to be installed.
- Updates – Computer Configuration | Policies | Administrative Templates | Microsoft Office 2016 (Machine) | Updates
- Don’t install Microsoft Teams with new installations or updates of Office = enabled

- Don’t install Microsoft Teams with new installations or updates of Office = enabled
Network
- Network – Computer Configuration | Policies | Administrative Templates | Network | Network Isolation
- Subnet definitions are authoritative = enabled – Windows 10 setting – Source = CTX232340 Windows 10 PVS target devices experience poor performance
OneDrive Files-on-demand
For Windows 10 1709 and newer or Windows Server 2019 and newer. Make sure the OneDrive .admx file is installed first.
- OneDrive – Computer Configuration | Policies | Administrative Templates | OneDrive
- Use OneDrive Files On-Demand = enabled
Verbose Messages
- System – Computer Configuration | Policies | Administrative Templates | System
- Display highly detailed status messages = enabled. Windows 10. Shows what’s happening during logon.
Group Policy Settings
- Group Policy – Computer Configuration | Policies | Administrative Templates | System | Group Policy
- Configure Group Policy Caching = disabled. Windows 8.1/2012 R2 and newer setting
- Configure Logon Script Delay = enabled, 0 minutes. Windows 8.1/2012 R2 and newer setting.
- Configure User Group Policy loopback processing mode = Enabled, either Merge or Replace depending on the desired result
User Group Policy loopback processing mode changes in Windows Server 2008 R2. Make sure the VDA computer accounts have Read access to the loopback user GPOs, even if those GPOs only contain user settings.
Logon Settings
To get rid of the Windows 10 “we’re happy you’re here” message:
- Logon – Computer Configuration | Policies | Administrative Templates | System | Logon
- Show first sign-in animation = disabled
- Show clear logon background = enabled – for Win10 1903 and newer – source = Citrix Discussions
DelayedDesktopSwitchTimeout. Create a Group Policy Preferences Registry Item (Computer Configuration | Preferences | Windows Settings | Registry) to set HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\DelayedDesktopSwitchTimeout (REG_DWORD) = 2. On Windows 10, this might cause the desktop to appear sooner. (Source = VMware Communities)
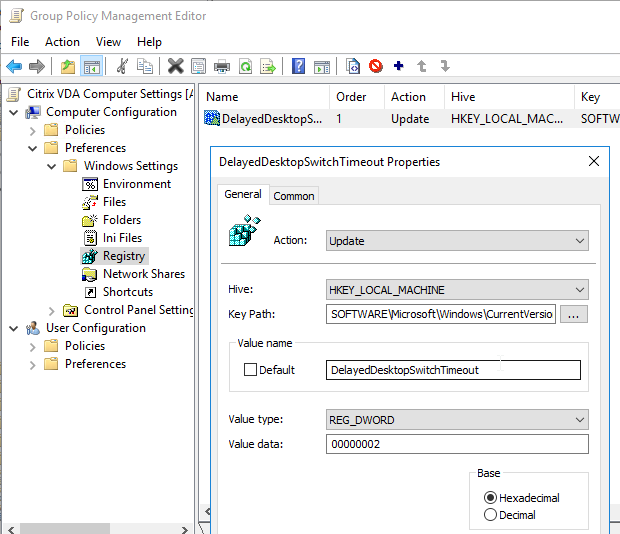
Power Settings
The following are more applicable to virtual desktops than session hosts:
- Hard Disk Settings – Computer Configuration | Policies | Administrative Templates | System | Power Management | Hard Disk Settings
- Turn Off the hard disk (plugged in) = enabled, 0 seconds
- Sleep Settings – Computer Configuration | Policies | Administrative Templates | System | Power Management | Sleep Settings
- Specify the system hibernate timeout (plugged in) = enabled, 0 seconds
- Specify the system sleep timeout (plugged in) = enabled, 0 seconds
- Turn off hybrid sleep (plugged in) = enabled, 0 seconds
- Video and Display Settings – Computer Configuration | Policies | Administrative Templates | System | Power Management | Video and Display Settings
- Turn off the display (plugged in) = enabled, 0 seconds
Remote Assistance Settings
Configure the following so you can shadow users using Director:
- Remote Assistance – Computer Configuration | Policies | Administrative Templates | System | Remote Assistance
- Configure Solicited Remote Assistance = disabled
- Configure Offer Remote Assistance = enabled, specify the Help Desk and Administrator groups that can offer remote assistance
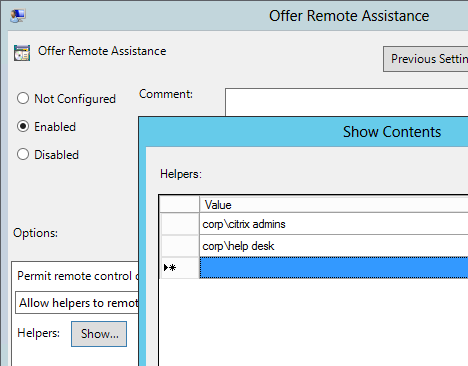
User Profiles Settings
- User Profiles – Computer Configuration | Policies | Administrative Templates | System | User Profiles
- Add the Administrators security group to roaming user profiles = enabled
- Delete cached copies of roaming profiles = enabled (only enable on persistent session hosts)
- Do not check for user ownership of Roaming Profile Folders = enabled
- Set maximum wait time for the network if a user has a roaming user profile or remote home directory = enabled, 0 seconds
- Source = MasterXen at “Please wait for User Profile Services” – Logon delay
Cloud Content
- Cloud Content – Computer Configuration | Policies | Administrative Templates | Windows Components | Cloud Content (Windows 10 1511 and newer)
- Turn off Microsoft consumer experiences = enabled
File Explorer Settings
Citrix CTX203658 Start Menu Icons Set to Default (Blank Document) After Update to Receiver 4.3.100 – Windows 8 and newer
- File Explorer – Computer Configuration | Policies | Administrative Templates | Windows Components | File Explorer
- Allow the use of remote paths in file shortcut icons = enabled
Event Viewer Settings
If you are using Provisioning Services, it might be desirable to move the event logs to a persistent cache disk. This allows you to review the event logs even after the Target Device reboots. Use Group Policy Preferences to create the folder on the cache disk.
- Application – Computer Configuration | Policies | Administrative Templates | Windows Components | Event Log Service | Application
- Control the location of the log file = enabled, D:\EventLogs\Application.evtx
- Security – Computer Configuration | Policies | Administrative Templates | Windows Components | Event Log Service | Security
- Control the location of the log file = enabled, D:\EventLogs\Security.evtx
- System – Computer Configuration | Policies | Administrative Templates | Windows Components | Event Log Service | System
- Control the location of the log file = enabled, D:\EventLogs\System.evtx
- Folder – Computer Configuration | Preferences | Folder
- Action = update
- Path = D:\EventLogs
Microsoft Account – Windows 10 (1703 and newer)
- Microsoft account – Computer Configuration | Policies | Administrative Templates | Windows Components | Microsoft account
- Block all consumer Microsoft account user authentication = Enabled
OneDrive Settings – Windows 10
- OneDrive – Computer Configuration | Policies | Administrative Templates | Windows Components | OneDrive
- Prevent the usage of OneDrive for file storage = enabled
Remote Desktop Services Settings
- Connections – Computer Configuration | Policies | Administrative Templates | Windows Components | Remote Desktop Services | Remote Desktop Session Host | Connections
- Restrict Remote Desktop Services users to a single Remote Desktop Services session = disabled
- More details at http://support.citrix.com/article/CTX131245
- Restrict Remote Desktop Services users to a single Remote Desktop Services session = disabled
- Device and Resource Redirection – Computer Configuration | Policies | Administrative Templates | Windows Components | Remote Desktop Services | Remote Desktop Session Host | Device and Resource Redirection
- Allow time zone redirection = enabled
- Do not allow smart card device redirection = enabled
- Licensing – Computer Configuration | Policies | Administrative Templates | Windows Components | Remote Desktop Services | Remote Desktop Session Host | Licensing
- Set the Remote Desktop license mode = enabled, Per User
- Use the specified Remote Desktop license servers = enabled, your RDS Licensing Servers (e.g. the XenDesktop Controllers)
- Remote Session Environment – Computer Configuration | Policies | Administrative Templates | Windows Components | Remote Desktop Services | Remote Desktop Session Host | Remote Session Environment
- Use the hardware default graphics adapter for all Remote Desktop Services sessions = Enabled
- Source = Marco Hofmann Basic XenApp HDX 3D Pro Proof of Concept – What I missed
- Use WDDM graphics display driver for Remote Desktop Connections = Disabled
- For Windows 10 version 2004 with VDA earlier than VDA 2006. Source = Windows 10 v2004 – Citrix Known Issues
- Use the hardware default graphics adapter for all Remote Desktop Services sessions = Enabled
- Security – Computer Configuration | Policies | Administrative Templates | Windows Components | Remote Desktop Services | Remote Desktop Session Host | Security
- Always prompt for password upon connection = disabled (to override other GPOs where it might be enabled)
- Session Time Limits – Computer Configuration | Policies | Administrative Templates | Windows Components | Remote Desktop Services | Remote Desktop Session Host | Session Time Limits
- Set a time limit for active but idle Terminal Services sessions = enabled, 3 hours or similar
- Set time limit for disconnected sessions = enabled, 3 hours or similar
- CVAD 2206 and newer also let you set RDSH timers in the user half of a Citrix Policy under the Server Limits category. Citrix Docs says: Timer settings for multi-session machines configured using Citrix policies are expected to override timer settings configured through Microsoft Group Policies. To avoid unexpected behavior, we recommend you configure timer settings using one of the two methods.
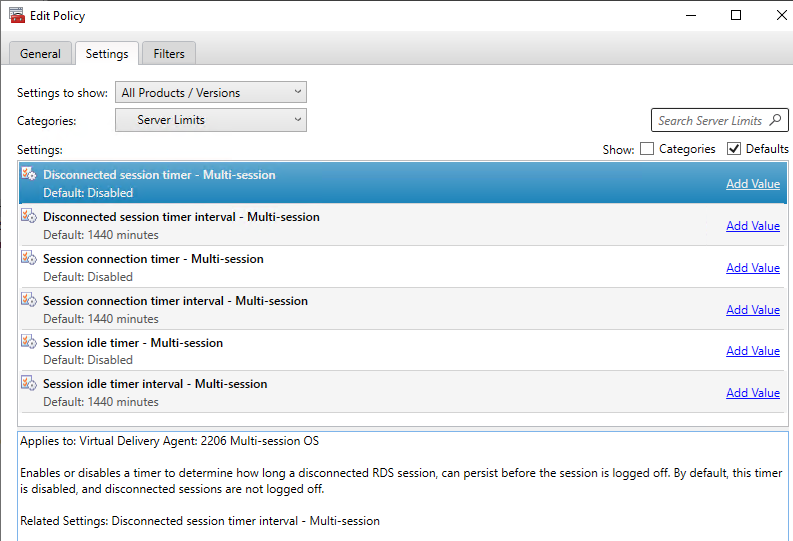
Search Settings – Windows 8.1 / 2012 R2, Windows 10
- Search – Computer Configuration | Policies | Administrative Templates | Windows Components | Search
- Allow Cortana = disabled (Windows 10)
- Don’t search the web or display web results in search = enabled
- Additional search settings can be found here
Store Settings – Windows 8.1 / 2012 R2, Windows 10
- Store – Computer Configuration | Policies | Administrative Templates | Windows Components | Store
- Turn off the Store application = enabled
Windows Update Settings
- Windows Update – Computer Configuration | Policies | Administrative Templates | Windows Components | Windows Update
- Allow non-administrators to receive update notifications = disabled
- Windows Update for Business – Computer Configuration | Policies | Administrative Templates | Windows Components | Windows Update | Windows Update for Business
- Select when Preview Builds and Feature Updates are received = Enabled, Semi-Annual Channel, 365 day deferral
Additional Settings
Windows 10 group policy settings for controlling Internet connectivity and Privacy Settings can be found at Microsoft Technet Manage connections from Windows operating system components to Microsoft services.
James Rankin Five tips for dealing with Windows 10 telemetry: disable Modern apps, disable Cortana, disable services, block DNS domains.
After modifying the GPO, use Group Policy Management Console to update the VDA machines.
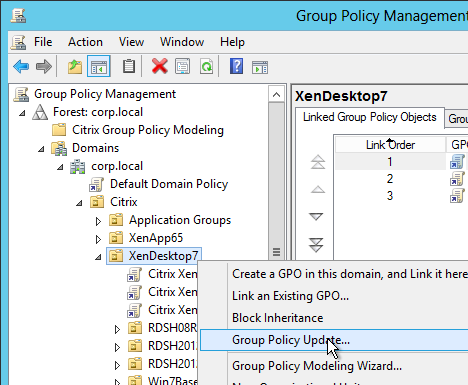
Or run the command gpupdate /force. Or wait 90 minutes.
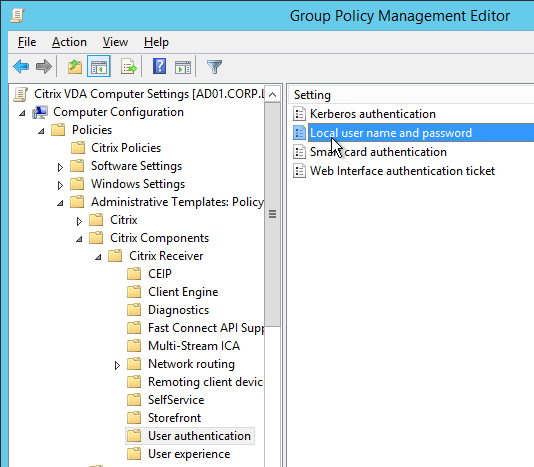
Citrix Receiver
If you want pass-through authentication for the Citrix Receiver that is installed on your VDAs, use receiver.admx to enable pass-through authentication.
- See the instructions at https://www.carlstalhood.com/receiver-for-windows/#admx to copy the receiver.admx file to PolicyDefinitions.
- Edit the Citrix Computer Settings GPO.
- Go to Computer Configuration > Policies > Administrative Templates > Citrix Components > Citrix Receiver > User Authentication. On the right, open Local user name and password.
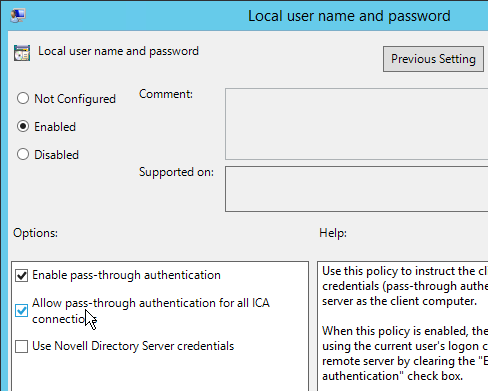
- Enable the setting.
- Check the top two boxes and click OK.
Hi
We config the “Cached Exchange Mode Sync Settings” to six mounth
and config the fslogix
for some reasone it is set the Sync Settings on the outlook to ALL
Hi Carl,
Thank you for all your help throughout the years. I’m struggling with redirecting “the event logs to a persistent cache disk. This allows you to review the event logs even after the Target Device reboots”. We have a nonpersistent vDisk cache setting of, Cache in device RAM w/overflow on hard disk and it didn’t work. Changed to, Cache on server in hopes it would resolve the issue and it did not. Any suggestions?
Hello Carl,
The Citrix Desktop Service(Brokeragent) i have to configure as auto delayed start on PVS master server. But, once i configure and reboot the server it went to the same state like Automatic, Is any way i can configure and not discard after the reboot .
Hi Carl,
do you have any suggestions for Microsoft Intune onboarding for non-persistent VDI?
Are your machines hybrid-joined?
I’m not sure that Intune is effective with non-persistent. What do you want Intune to manage or deploy that you aren’t already doing in your gold image?
Hey Carl,
Really appreciate your blog it’s been super helpful with getting Horizon setup. One question that maybe you’ve run into. We have OneDrive files on demand enabled with silent sign in, that works well. The VDI’s are non-persistent so on each sign in OneDrive signs in, then processes the full OneDrive file sync for the user (just the shortcuts). We’ve tried enabling the OneDrive ODFC, but cannot get it to work (same with using the profile instead) so that on each log on the user doesn’t have to wait for the full OD sync. The Outlook OST is in the profile, and that works great. Have you ever run into or got this to work? We’ve gotten no where with MS support and cant find anything searching.
Hi Carl,
Wish I new about your site before!
I am deploying AVD on Win11 22H2 and looking for best practices for GPO to lock the Win11 Desktop to the max.
Do you have any advice for me please?
Also about this article in step 10. copy new admx files to corp.local\Policies – will Replace command mess up the old ADMX files and GPOs or just update them?
Thanks
ADMX files are separate from the GPOs. Updating ADMX files does not affect existing GPOs.
For lockdowns, look for industry security baselines (https://learn.microsoft.com/en-us/windows/security/operating-system-security/device-management/windows-security-configuration-framework/windows-security-baselines) like DISA STIG (https://public.cyber.mil/stigs/downloads/), CIS (https://www.cisecurity.org/), etc.
Carl Stalhoodsays:
November 16, 2022 at 9:54 am
How are you confirming that it works or doesn’t work? Are you looking in the file share?
If you add an exclusion, make sure LogonExclusionCheck is enabled in your UPM config.
The OneDrive folder is normally named OneDrive – Company Name.
Carl is there any way to hide this OneDrive-Company Name from the Citrix Admins that logon and manage the Citrix Profiles. We have OnDemand enabled but the Citrix Admins can see the user’s files when they have launched OneDrive on the server.
Hello Carl.
To the Loopback-Policy I have a question to you.
In my old job I used Terminalservers (XenApp 7). In this enviroment we configured a policy, where the Loopback configuration was the only setting. The policy was processed first.
Now we configure a new VDI enviroment.
Is my old setting recommended here, or makes it no difference, where policy is placed?
Thx in advance for your answer.
Regards
Dirk
It’s a computer setting so just make sure that at least one GPO is enabling it. However, you might have different GPOs setting it to Merge or Replace so try to limit the number of GPOs that are setting it.
Thanks for anwser, Carl 🙂
Have a nice weekend
Best regards
Dirk
Carl,
A customer has issues on Server 2022, with VDA 7 2203 LTSR CU2 and FSLogix 2.9.8228.50276
Several times a day, the receive EventID 1000 – Application Error
Faulting application name: frxsvc.exe, version: 2.9.8228.50276, time stamp: 0x62cdc08f
Faulting module name: ntdll.dll, version: 10.0.20348.1487, time stamp: 0x04ff1d20
Exception code: 0xc00000fd
Fault offset: 0x000000000001c799
Faulting process id: 0xd02c
Faulting application start time: 0x01d93ae001355e79
Faulting application path: C:\Program Files\FSLogix\Apps\frxsvc.exe
Faulting module path: C:\Windows\SYSTEM32\ntdll.dll
Report Id: 697e5253-2f37-4b51-b7a3-f87811b19f8e
Faulting package full name:
Faulting package-relative application ID:
Any idea what is wrong in this setup?
That’s FSLogix 2201 hotfix 2. Does the same happen with FSLogix 2210?
I am having issues with FSlogix where the onedrive credentials are not persisting between logins. I have O365 credentials working and I do not have to log them in every time for that but OneDrive requires a login every time the user logs off of the XenApp machine. The rest of the configuration is still there, it is just the credentials.
Try one of these – https://learn.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-sso#sso-via-primary-refresh-token-vs-seamless-sso
As we are migrating our M drive content which consists of Appdata, Documents,Desktop folder to OneDrive, we wanted to know how we can migrate AppData folder in Upm Profile store.
Configure Folder Redirection to move AppData into the local OneDrive path. If your Folder Redirection tool can move the files, then you’re done. If not, then write a logon script to move the files.
But we can’t move it to our OneDrive as there can be concurrent session of Desktop Opened on which OneDrive won’t work properly in multiple session.
Is there any other way to move it some other place,
I usually leave AppData in its default location at %userprofile%\AppData and let my roaming profile tools capture it.
So, it means AppData does not need to be kept in UPM profile folder for roaming profile case. If it is kept in Default location, then it would need storage space of C Drive, correct?
Yes. The purpose of roaming profiles is to backup files under %userprofile% and restore them at next logon.
Hi Carl,
We are really stuck in a situation that we have excluded Onedrive folder from Citrix profile UPM folder by using citrix policy but it still folder is getting created. we have used the below command:
Users\%Username%\
can you please help us if we are giving the wrong format for exclusion in citrix policy
OneDrive probably creates the folder on each logon. Excluding folders from UPM only prevents it from being saved at logoff. It doesn’t prevent it from being created while the user is logged in.
what syntax should i use for excluding onedrive from upm for getting save on logg off.
we have tried %userprofile%\OneDrive –
but its not working.
How are you confirming that it works or doesn’t work? Are you looking in the file share?
If you add an exclusion, make sure LogonExclusionCheck is enabled in your UPM config.
The OneDrive folder is normally named OneDrive – Company Name.
Hello,
after installing the citrix 2203 LSTR farm, and I installed 3 VDAs to make desktop published in RDHS, everything works fine but the 3 VDAs freeze and get stuck when logging in on the step: Wait for remote desktop configration.
So I have to reboot the 3 VDAs from the vcenter to make it work.
recurring problem every day.
do you have any idea please ?
Is it common or not to use Microsoft’s Security Baselines in VDI? Would you advise for or against it? We are attempting to but it is proving quite difficult and time consuming to go through all the settings, and when we run into trouble figure out which setting it is that needs to be changed.
Thanks!
The only baselines I’ve done are DISA STIGs. But I’ve spent many hours reversing security settings to get Citrix working.
Hi Carl, curious if you have some documentation on conflicting STIG policies with a Citrix environment.
Citrix Blogs has some info – https://www.citrix.com/blogs/2018/06/08/deploying-storefront-ltsr-with-disa-stigs-server-2012-edition/
Hello, Carl, can group policy templates be exported and shared?
Are you asking about .admx files? If so, copy them from the PolicyDefinitions folder.
Carl,
We are setting up a new Horizon VDI environment. I’ve followed your guides, but for some reason when users login to a VDI session, all apps are missing. If I remove the Horizon Computer Settings GPO, everything seems to work as intended and all apps show. Any ideas of what GPO setting could be causing this before I go and troubleshoot each setting one at a time?
Did you enable the “Hide Common Program Groups from Start Menu”? If so, remove that setting.
Is there anything on the Start Menu or Desktop?
Yes, but that is part of the Horizon Non-Admin Users (lockdown) GPO, which is still being applied and currently working. Something else within the Computer GPO is causing the entire desktop and start menu to not have any of the apps showing installed, including apps like AutoCAD. Here’s everything that is applied: https://structurepoint-my.sharepoint.com/:b:/p/adailey/EXcaAGNOLYRNpqaV37o3fpQB-p-4VpvwR2nDpD2FvWViNA?e=Hxcbgx
This GPO enables Loopback Processing, which enables your user policies to start working. Without loopback, user policies assigned to the computer won’t do anything. Check the user policies that are assigned to the computer.
Okay, I re-enabled the computer GPO and then removed the “Remove common program groups from Start Menu” setting in the user GPO. All seems to be working now, thanks!
Carl, I apologize and I am sure you have answered this but I need some guidance. Currently when users switch between VDA servers Acrobat will constantly ask them to sign in. Only 2 servers they can log on to but everyday they are asked to sign in. Log them off Citrix, back on to the same server and again, asking to log in. Can you help guide me on what I am missing to make this work?
What roaming profile tool are you using? Are you excluding locations that Adobe uses, like AppData\Roaming\Adobe\SLData?
I believe Windows GPO under Citrix Profile Management. However we are using a NUL license so does that cause an issue? Is there a potential way around this?
Hey Mercer, not sure if you figured it out yet or not but I went through the same problem. The solution is rather simple, add these keys in the registry. Once done the user will be prompted to log in again and it will store the info in the user profile so it roams around.
[HKEY_LOCAL_MACHINE\SOFTWARE\Adobe\Licensing\UserSpecificLicensing]”Enabled”=”1″ (REG_SZ)
[HKEY_LOCAL_MACHINE\SOFTWARE\Adobe\Identity\UserSpecificIdentity]”Enabled”=”1″ (REG_SZ)
Sournce – https://www.adobe.com/devnet-docs/acrobatetk/tools/VirtualizationGuide/citrix.html
I have not deep dived into this page before or those registry keys. I did make the changes to the keys but then users were not able to even log into Adobe. I will review more about this page those.
Hi Carl, or anybody 🙂
I’m looking for recommendations on migration of FSLogix profiles from W2K16 to W2K19 servers.
We currently have a W2K16 farm, about 200 users with FSLogix profiles + ODFC, I’ve now setup new W2K19 servers, with all the same software (latest versions if available).
Can I simply point the W2K19 servers to the same FSLogix folder, so that profiles are re-used (and worst-case scenario, also the other way round, should we want to fall back to W2K16)?
Or should I simply create a new file share and migrate only the needed configuration? I.e. let user logon to W2K19 server with a fresh profile, via script mount their W2K16 VHDX, copy the needed files(/registry settings) and dismount the VHDX again?
Already did some first tests with test-accounts, simply pointing to the W2K16 profile and didn’t get any errors, but would like confirmation if anybody did that before.
Thanks!
Peter
They both use .v6 profiles so they’ll probably work, just like profiles work after a Windows 10 version upgrade.
The World of EUC Slack team has an active FSLogix channel.
Thanks for the quick reply. Will do further tests and maybe register to World of EUC.
Hello, I have a frozen “welcome screen” when users reconnect to their published desktop. (OS Servers 2016).
We have Ivanti, app layering.
DelayedDesktopSwitchTimeout key?
ApplicationLaunchWaitTimeoutMS key?
Hello Carl,
we are preparing a new master with W10 1909 and now have the problem that our Startup Script (*.cmd) which is working with our 1803 master are not executed on 1909 – the error in GPO Result is “The system can not find the stated file” (german translation)
we call the startup command file from Networkshare: \\Fileserver\Skripts$\W10XDSTARTUP.cmd
there are the same Policy but I cannot find the problem – any ideas?
are ther more restriced settings/policy in 1909 which I have to take care?
robert
Computer script? Or user script?
Try doing a procmon during logon and search for that script to see the issue.
Carl, when implementing FSLogix do i ignore these GPO settings for Office products ? https://www.carlstalhood.com/group-policy-objects-vda-user-settings/#office2013
No. You’ll at least want to set the cached mode duration (e.g. 3 months).
Thanks Carl, Any reason to go ahead and Manage profiles with a FSLogix Profile container and leave UPM behind ?
FSLogix easily handles Outlook search index. But FSLogix needs disk space.
thanks Carl, i get it. Everything comes at a cost
Hi
We are trying to implement FSLogix in our VMWare Horizon environment. Setup is simple, FSLogix agent, Instant Clone pool and a share for the VHDX files. When implementing the redirections.xml configuration with a GPO, the user profile is unable to get reattached (Status 0x00000017 Reason: 0x00000000 Error Code: 0x0000000D). If we do not implement the redirection.xml, we do not have that issue. I’ve tried with an empty XML only containing the following:
But we are still getting the error. So here are the scenarios:
1. New VHDX, no redirections.xml, it works. Sign-out and sign-in, still works.
2. New VHDX, redirections.xml, first sign in works, sign-out and sign-in, User profile failed to attach. After that, even when I remove the redirections.xml GPO, the VHDX is unusable.
Thank you
Dash
FSLogix policy settings are burned into the registry and removing the GPO does not remove the setting. You have to look in HKLM\Software\FSLogix\Profile to find the registry key.
Anything interesting in C:\Programdata\FSLogix\Logs\Profile?
Hi Carl,
Thanks for all your helpful information. Just a note to say that in the latest OneDrive ADMX file as of 17/09/20 the option for OneDrive Files on Demand is now called “Use OneDrive Files On-Demand” rather than “Enable OneDrive Files on Demand”.
Thanks for pointing that out. I also found problems in the OneDrive .admx section and hopefully fixed them.
HI Carl,
we are using OneDrive with FSLogix for Citrix server Desktops and we configured folder redirection policy through GPO to redirect document and downloads to OneDrive but it is not working. could you please suggest correct settings.
Have you tried Known Folder Move? https://docs.microsoft.com/en-us/onedrive/redirect-known-folders
the link for the FXLogix exclusions seems to lead no where that they provide adn clear definded list
Are you referring to the Antivirus exclusions. That seems to be an old link that is no longer valid. I just removed it. Thanks for pointing it out.
Hi Carl, made the switch to FSLogix. Love the product, but see one major flaw. It does not retain user printers after they set them. Can you guide me on a workable solution for this?
Same problem as this thread? https://social.msdn.microsoft.com/Forums/en-US/2a46831d-9ad0-426f-8119-48d5ceecb10c/fslogix-and-printers-on-printserver?forum=FSLogix
Yes, but I have that policy configured. We provide a VDI to our users. There local printers are mapped, but they are also able to map certain printers on their VDI. The printers they map on the VDI are the ones not being retained by the FSlogix profile
Hi Carl – so we are running into an issue with session lock ups. This seems to happen when only accessing Citrix from external network sources. I am running XenApp 7.15 LTSR on Windows 2016 VDA’s We are utilizing F5 LB but right now they are not hitting the F5 externally.
User seem to be working fine for 5 to 10 minutes then sessions lock and they are no longer able to access the published application. Only resetting session clears.
Wondering if there is something you know of that could be causing session locks or somewhere to check to see what could be the issue.
Can you run other applications (e.g Notepad) in the same session? Need to determine if the whole session is locked, or just the app.
According to the users experiencing these issues is the whole session. So if user has two applications running both applications are in a locked state
I was able to reproduce this issue. Seems sessions lock up after 2 to 3 minute period of idle time. It locks up all applications I have open. Is there a policy I do not have set correctly? I followed your policy setting almost to the letter with regard to time out session. I followed the settings for Application presentation that applied to my environment.
Is there any NAT or other security device between the user and the Horizon Agent? Maybe one of those devices has a short timeout for TCP/UDP connections.
For external users, how are you proxying the ICA connection?
Hi Carl,
When the user session is idle for 15 mins application went locked state,Citrix session is locked not the local machine,can you helpe to fix it?
Iam using 7.15 CU2 environment
Hi Mat,
Iam facing the same issue ,do u have the solution
Hi Mohanraj -I believe the issue to be a Network driver on our particular laptops. We have Dell Lattitude E4740’s. We don’t have issues with other types of hardware like Microsoft Surface laptops. If you do use Dell laptops update the Wireless drivers to latest Intel driver. (Also use the INTEL driver). Also make sure the following
Wireless Properites
Advanced Tab
802.11a/b/g Wireless Mode – 5. Dual Band 802.11a/g/\
Preferred Band – 3 Prefer 5GHZ
Also
Power Management Tab
Uncheck “Allow the computer to turn off this device to save power”
Great article(s) – you are a true lifesaver! Maybe you can help me one more time 😉 Sometimes my users get an error saying they need the right to sign in through remote desktop services when starting an app on VDA 7.15. My delivery controllers are both configured and activated Windows Server 2016 licensing servers, even the GPO is configured to contact them for per User CALs. Basic troubleshooting and license diagnosing says all fine and it doesn’t happen all the time, just sometimes and on different servers. We don’t use MCS or PVS, all servers are running Windows Server 2016 and VDA 7.15LTSR is in use. Do you have any idea how to get this right?
If it’s an RDS Licensing problem, then there are normally events in Event Viewer when licensing is not working.
The same symptom might happen if you run out of Citrix licenses.
Hello Carl, we are still in the build phase of our new environment and made the decision to move the Citrix Computer and User policies in Active Directory instead of storing them in the SQL Database. The problem I can’t seem to figure out is that I do not see those policies in the registry or on the linked clones. Where would those be written to in the VDA and Master templates’ registry?
I think they only apply when you perform a Citrix connection. Then you should see them under HKLM\Software\Policies\Citrix. Some will be under HDX nodes. Others will be under the nodes that are numbered based on session ID.
I do know about the registry key that would show under .\Policies\Citrix then folders named after the session ID but nothing of the sort matches up. I did find a folder named “2” that had my session info but on the server I am session 12. Either way, I do not see any of our policies applying in the folder.
Does the Group Policy Management console need to be installed on a delivery controller for managing the Citrix policies in Active Directory? In Active directory using GPMC, I picked the user portion of Citrix Policies and wanted to apply a Citrix policy to a delivery group using the Delivery Group filtering. When I attempted to do that, I typed in the name of the DDC and it prompted me for Citrix Cloud credentials. After getting passed that, I got a drop-down box to see the names of the Delivery Groups. Nothing is listed and I cannot manually type it in. Is what I am attempting to perform a supported operation?
We have opened a case with Citrix on this issue. Policies are not applying to the VDAs using GPO. If we set the policies in the Studio console to store in the SQL Database, that works. According to Citrix , we have everything setup correctly and meeting the criteria. We have a single GPO that only contains Citrix policies only. We have full control to that policy as well as Group Policy Modeling permissions and they do not seem to apply. We have confirmed the permissions are set correctly on the policy itself for delegation and scope. Now it is just trying to figure out how to capture the logging in process to see where it skips the policy or refuses to apply it. BTW – this is not even working for the Unfiltered policy set in the GPO.
I was able to figure it out as to why the policies set in GPO were not applying. At our top level Citrix OU, we have inheritance turned off. The users reside in a different OU not in the Citrix OU’s. We forgot to enable Group Loopback Processing in the GPO and that corrected our issue.
Hi Carl,
Can the Remote Desktop Services settings apply to Windows 10 too?
I am also doing dedicated full desktop for Windows 10, any specific settings from there that could help for that setup?
Would this work – Delete cached copies of roaming profiles = enabled (only enable on persistent session hosts) as I plan to use Appsense and Local Profiles and Personalization on Persistent Desktop.
Many thanks in advanced.
Hi Carl. I have XenApp 7.15 with Windows 2016 VDA Shared Desktops. I configured the GPO Interactive logon: Machine inactivity limit, but only works if the conection is via RDP. No works over ICA.
Any suggest?
Interesting. Here’s another option – https://msfreaks.wordpress.com/2018/01/13/enforcing-lock-screen-after-idle-time-windows-server-2016-rds-session-host/
Hi Carl,
I have a scenario in my VDI environment. I uninstalled OneDrive 17.x and installed 18.x version in my master image and when publishing a non-persistent desktop pool using it, on every user launch, version 17.x gets installed again in it as a fresh setup.
It starts automatically and I noticed in the Windows startup “Microsoft OneDrive Setup” on user session launch under Task Manager -> Startup.
I need version 18.x for on-demand feature and be available to take the user login configuration automatically on launch.
Your inputs will surely help.
Regards,
Pravin
What version of Windows?
hi carl,
I have Xenapp 7.13 with one controller and three separate VDAs. there is a problem with the VDA server. every user accesses the published application, the user automatically becomes the local administrator group on the VDA server so that the user can remote desktop the VDA server. please help me..
If you run Group Policy Results, it should show you which GPO is adding users to the local administrators group. Citrix does not do that, so it has to be something else.
Carl and others,
Does the event log policy create the folder or does that need to be pre-created. Also how does this work for custom logs from an application under application logs. For example if I have an app that writes its log under applications and services (win2k16) How do I redirect that? Does the policy allow me to create a custom entry. Forgive me if these are newbie questions.
Hi Carl,
is it possible to save or store the event logs to some kind of persistent storage (like a persistent disk for PvS, for example) when I want to provide non persistent VDAs (Server VDAs in my case) with MCS?
In case it is possible, how should I do that?
Thanks
Ewald
Unfortunately no. I think you’ll need some kind of monitoring agent to collect event logs.
https://support.citrix.com/article/CTX231757
Hey Carl, pasting the Win10 1803 objects to C:\Windows\Policy Definitions won’t allow overwrite even logged in as the default admin and running Explorer as an admin. The individual policy objects in the folder do not inherit parent permissions. I am assuming that I would need to do this on any domain controller or build a central store. What do you recommend? Thanks.
Hello carl, digging through my huge mess of GPO’s and seems like my event log redirection GPO is not working correctly, seems like every night the logs get refreshed, I have a GPO that creates the folder on E:\ and then redirects the event logs, Every night when the machine reboots that’s when the logs get created for the first time so I only have one days worth of logs. Do have an idea of what to check? thanks in advance
Carl,
Don’t see any mention this this issue for Windows 10/2016 server OS VDA’s in regards to XenApp 7.XX;
https://docs.microsoft.com/en-us/windows/application-management/per-user-services-in-windows
Seems with latest updates to 2016, Microsoft has created per user Services, which flood the event log and show pop-up errors to users on XenApp on occasion.
“Per-user services are services that are created when a user signs into Windows or Windows Server and are stopped and deleted when that user signs out. These services run in the security context of the user account – this provides better resource management than the previous approach of running these kinds of services in Explorer, associated with a preconfigured account, or as tasks”
There a best practice for this yet?
Excellent post.
So I found this post as I was facing issues with XA7.13 running on Windows 2016.
Cortana and SearchUI are filling the event logs full of errors when a user log into the Desktop.
Event ID’s 1000, 5973, 10, are showing numerous times.
Also, left clicking on the start menu brings up nothing which of course is a problem but right clicking does bring up the context menu.
I have disabled redirecting the start menu but that didn’t seem to help.
So far I haven’t found much. Any ideas?
Thanks!
Start Menu is quite the challenge. My Profile Management article has info on how to roam it. https://www.carlstalhood.com/citrix-profile-management/
Thank you very much for this Carl and all the excellent articles on your site, you should include a Donate button somewhere on your front page as you are making a lot of peoples lives a lot easier….
Hi Carl,
Now that I solved my issue with a parent domain policy not applying in a XA76/2012R2 context, I find that your advice “make sure the VDA computer has read permission on the policy” is clear and sufficient but at first glance I must admit I did not see it as clearly as now 😉
The issue I had led me to this article https://blogs.technet.microsoft.com/askpfeplat/2016/07/05/who-broke-my-user-gpos/ which describes in details why in a certain scenario, some policies may no longer apply after having installed a security patch.
Have a great day !
Yvan
Hello Carl,
Hope you are doing well and thanks for the instructions.
I just want to know if three policies above will be the same to all the OU’s? I.E. RDSH as well as VDI’s?
Thanks,
Pavan
For the most part, yes. There are some minor differences (e.g. delete cached profiles on logoff). If a setting doesn’t apply to a particular VDA, there’s usually no harm in applying it. I usually have a parent OU for common settings (everything in this article) and sub-OUs for Delivery Group-specific settings.
Thanks Carl. The GPO applied to the parent OU applies to all the sub OU’S as it has been applied at the top level? If you say delivery group specific settings will that be application related?
Yes.
Great Article . I dont know how I would survive without these easy to use guides. One question though.. do we have a tuning/optimization GPO for Xenapp 7.6 like we have had in the past ie. 6.5? setting like TCPMasDataRetransmissions etc for windows server 2012/R2
I usually just do the optimizations built into the VDA. I have a colleague that tested many optimizations and noticed no difference in performance. Also see https://labs.vmware.com/flings/vmware-os-optimization-tool
Known issue after updating the Windows 10 ADMX templates https://support.microsoft.com/en-us/kb/3077013
Added. Thanks.