Navigation
- Change Log
- VPX Virtual Hardware – VMXNET3
- Customer User Experience Improvement Program (CUXIP)
- Welcome Wizard
- Licensing:
- 100% CPU
- Upgrade Firmware
- High Availability
- Networking
- DNS Servers
- NTP Servers
- Syslog Server
- SNMP Configuration
- Call Home
- Change nsroot password
- TCP, HTTP, SSL, and Security settings
- Management Authentication – LDAP
- CLI Prompt
- Backup and Restore
💡 = Recently Updated
Change Log
- 2025 Jan 14 – Flex Licensing
- 2024 April 25 – added info from Dynamically increase the primary disk size on NetScaler VPX
- 2023 Dec 9 – VPX hardware – added link to Manually adjust NetScaler VPX Disk Space
- 2022 Nov 8 – Upgrade firmware – verify date in /nsconfig/license before upgrading
- 2022 May 30 – VPX Hardware – added second disk in 13.1 build 22.50 and newer
- 2021 Nov 9 – Upgrade firmware – added additional configuration after security update.
- 2021 Sep 2 – Upgrade firmware – added script to check for features removed from ADC 13.1
- 2021 Feb 22 – Upgrade firmware – added HA Sync VLAN for ISSU support
- 2019 Sep 26 – Multiple subnets – added link to Best practices for network configurations at Citrix Docs
VPX Virtual Hardware
Magnus Andersson Deploy Citrix ADC VPX On Nutanix AHV
VMware Compatibility (source = Support matrix for Citrix ADC at Citrix Docs)
- Citrix ADC 13.1 build 21.50 and newer support VMware ESXi 7.0 update 3c.
- Citrix ADC 13.0 build 71 and newer supports ESXi 7.0.
Download and import VPX:
- Download Citrix ADC VPX Release 13.1 or NetScaler Release 14.1 Virtual Appliance.
- Download one of the VPX Packages for New Installation.
- Extract the downloaded .zip file.
- In vSphere Client, Deploy OVF template.
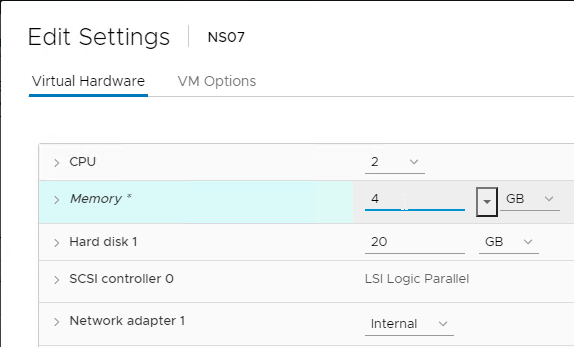
Before powering on the appliance, edit the virtual hardware.
- If you are licensed for VPX 1000 or higher, increase the CPU count. VPX 1000 is licensed for 4 vCPUs.
- Consider setting Memory to 4 GB for each packet engine. A VPX 200 has one packet engine. A VPX 1000 has three packet engines.
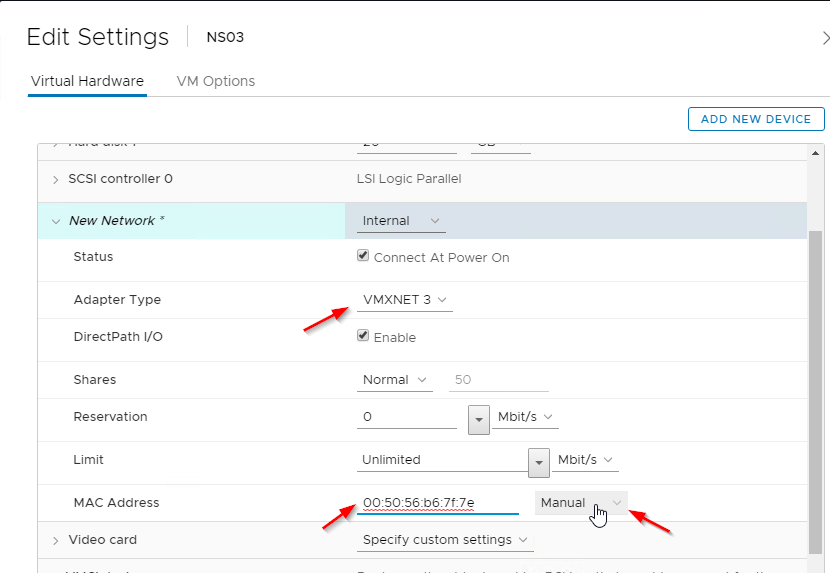
- Change the NIC Adapter type to VMXNET3 or SR-IOV.
- Citrix CTX224576 NetScaler VPX Loses Network Connectivity Intermittently on VMware ESXi After Upgrading to Version 12.0 recommends VMXNET3 as a workaround to network connectivity issues in recent Citrix ADC VPX builds.
- If you choose to use VMXNET3 instead of E1000, make sure all of the NICs are VMXNET3. You cannot mix NIC types.
- If you already licensed your appliance, jot down the E1000 MAC address, and configure the new VMXNET3 NIC with the same MAC address as the E1000 NIC so you don’t have to redo your license file.
- To change the NIC Adapter Type, remove the existing NIC, click OK to close Edit Settings, then go back into Edit Settings and Add New Device.
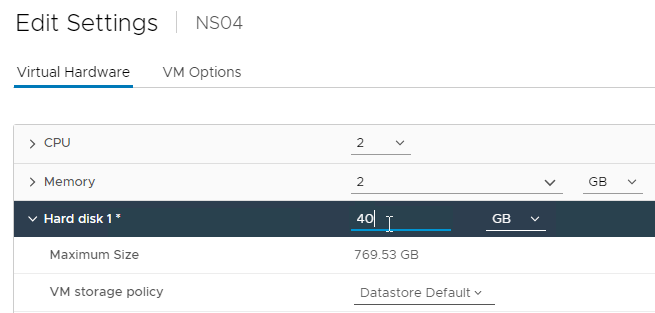
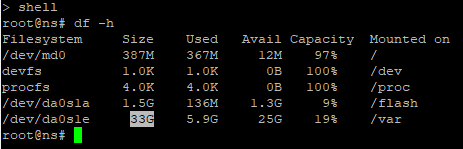
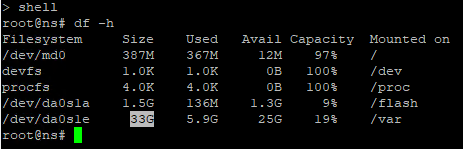
- NetScaler 14.1 build 21 and later let you expand size of Hard Disk 1 and after the reboot NetScaler will automatically expand the /var partition, which you can see by running
df -hin the shell.
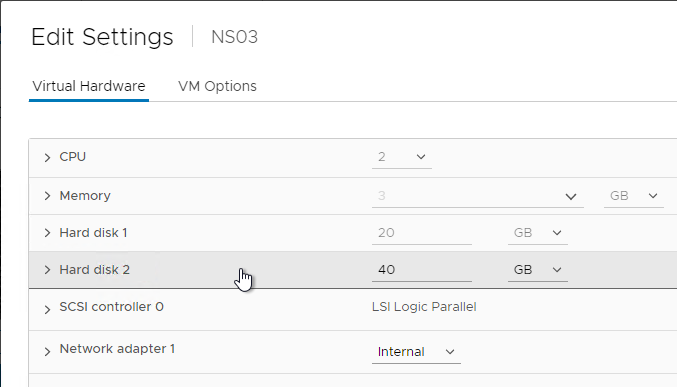
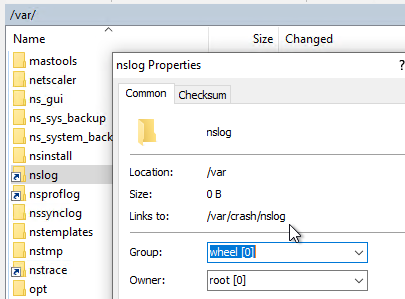
- ADC 13.1 build 21.50 and later let you add a second disk to the ADC for storage of logs and crash files. These log and crash files tend to consume disk space on the main drive, which prevents firmware updates, so moving them to a second disk should allow firmware updates to succeed. You can add the second disk at any time, but pre-existing files will not be moved, so it’s best to add the second disk when the VPX is first deployed.
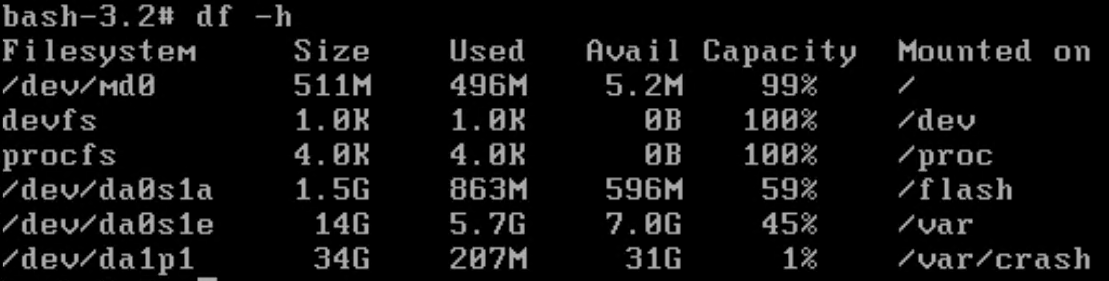
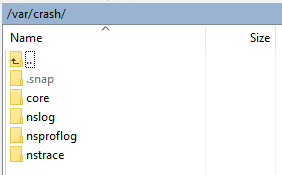
- The new disk is mounted under
/var/crash.
- The
/var/crashdirectory has several folders that are symlinked from the first drive to the second drive.
- The new disk is mounted under
- NetScaler 14.1 build 21 and later let you expand size of Hard Disk 1 and after the reboot NetScaler will automatically expand the /var partition, which you can see by running
df -hin the shell.
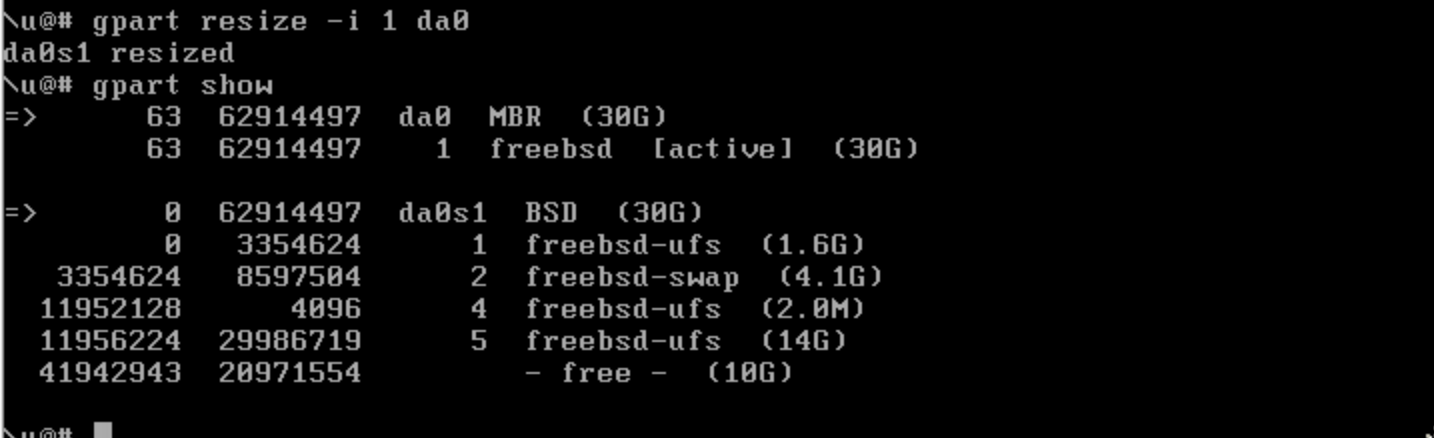
- Or see NetScaler Article Manually adjust NetScaler VPX Disk Space to use gpart to increase the partition size.
Auto-Provision IP Address
When importing VPX into a hypervisor, you can use VM advanced configuration parameters to set the NSIP. See CTX128250 How to Auto-Provision NetScaler VPX Appliance on a VMware ESX or ESXi Host, and CTX128236 How To Auto-Provision NetScaler VPX on XenServer.
Power On VPX and configure NSIP
- After importing the VPX OVF file and changing the NICs to VMXNET3, power on the Citrix ADC VPX appliance.
- Configure the management IP from the VM’s console.
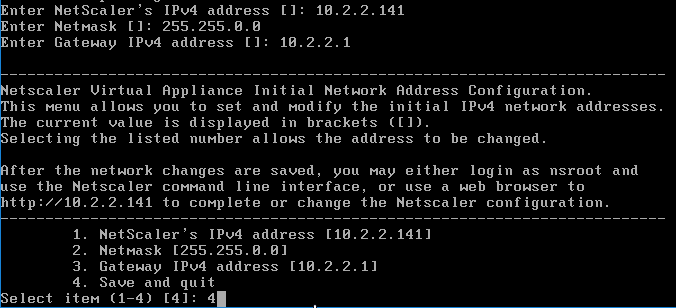
- Then point your browser to the management IP using either http or https and login as nsroot with password nsroot.
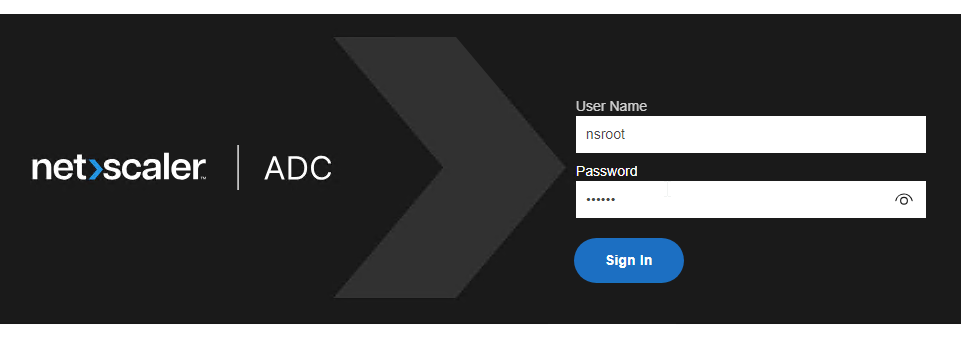
- In ADC 13.0 build 67 and newer, you’ll be prompted to change the default nsroot password.
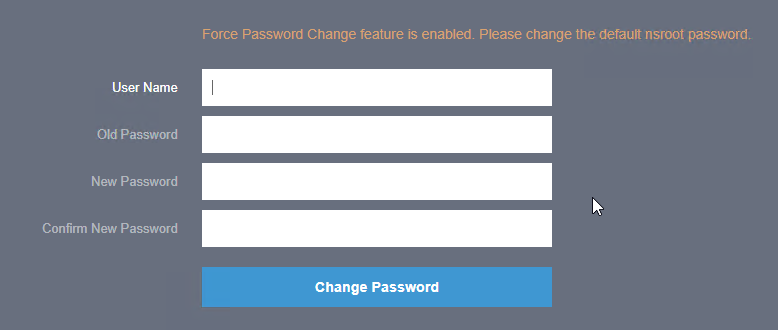
Customer User Experience Improvement Program
- You might be prompted to enable the Customer User Experience Improvement Program. Either click Enable, or click Skip.
- You can also enable or disable the Customer Experience Improvement Program by going to System > Settings.
- On the right is Change CUXIP Settings.
- Make your selection and click OK.
- See https://www.carlstalhood.com/delivery-controller-cr-and-licensing/#ceip for additional places where CEIP is enabled.
set system parameter -doppler ENABLED
Welcome Wizard
Citrix ADC has a Welcome! Wizard that lets you set the NSIP, hostname, DNS, licensing, etc. It appears automatically the first time you login.
- Click the Subnet IP Address box.
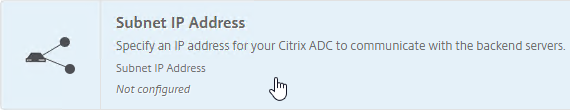
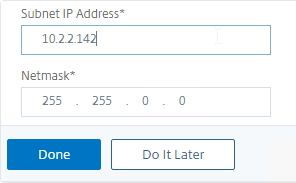
- You can either enter a SNIP for one of your production interfaces, or you can click Do it later and add SNIPs later after you configure Port Channels and VLANs.
Note: If you have a dedicated management network, to prevent the management network from being used for outgoing traffic, don’t put a SNIP on the management subnet.
add ns ip 10.2.2.60 255.255.255.0 -type SNIP
- Click the Host Name, DNS IP Address, Time Zone and NTP Server box.
- Enter a hostname. In a High Availability pair each node can have a different hostname. You typically create a DNS record that resolves the hostname to the NSIP (management IP).
- Enter one or more DNS Server IP addresses. Use the plus icon on the right to add more servers.
- Change the time zone to GMT-05:00-CDT-America/Chicago or similar.
- Add one or more NTP Servers.
- Click Done.
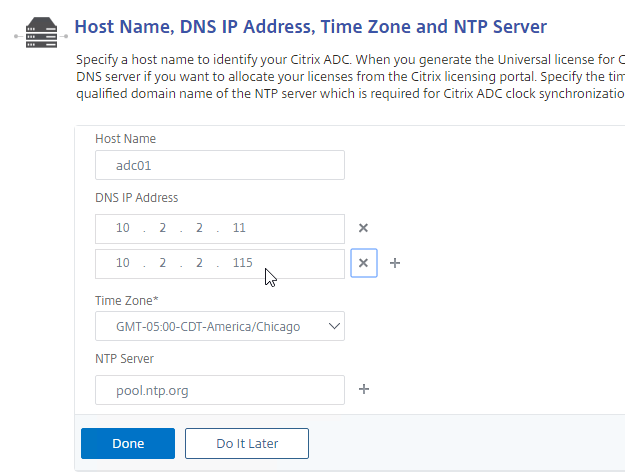
set ns hostname ns02 add dns nameServer 10.2.2.11 set ns param -timezone "GMT-06:00-CST-America/Chicago
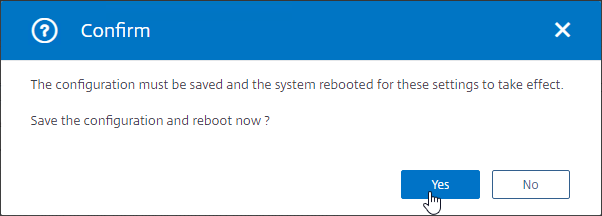
" - Click Yes to save and reboot.
- Click the Licenses box.
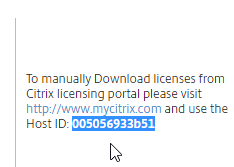
- On the far right side of the screen you’ll see the Host ID. You’ll need this to allocate your licenses at mycitrix.com. See below for detailed instructions on how to allocate the license to this Host ID.
- On the left, select Upload license files, and click Browse.
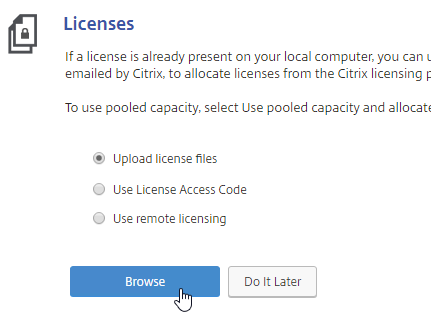
- Browse to the license file, open it, and click Reboot when prompted.
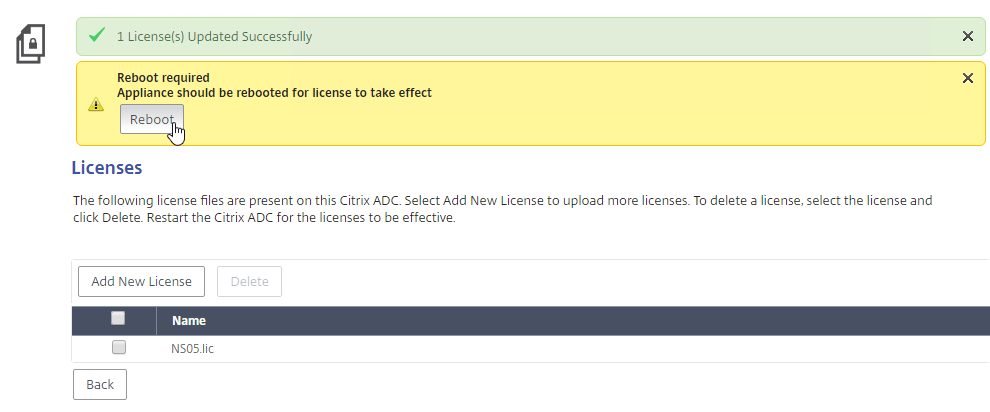
- License files are stored in /nsconfig/license.
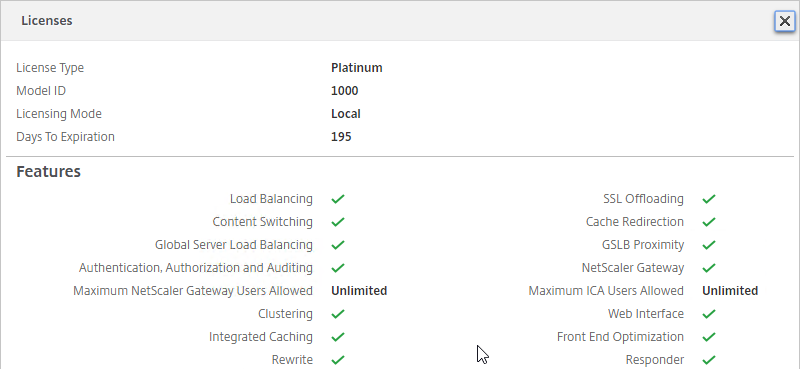
- After the reboot and logging in, a box will pop up showing you the installed license, including Days to Expiration.
- Also look in the top left corner to make sure it doesn’t say ADC VPX (Freemium). The number in the parentheses should match the MPX or VPX model number.
- 30 days prior to license expiration will be a banner at the top of the GUI. It also sends an SNMP trap.
- In ADC 13.1 build 24 and newer, you can adjust the number of days before expiration by clicking Manage Licenses, and then edit the Notification Settings on the bottom.
Flex Licensing
Owners of Citrix Universal Hybrid Multi Cloud or Citrix Platform licenses probably own NetScaler Flex licenses. Here’s a high-level procedure for installing Flex licenses.
- Use NetScaler Console at Citrix Cloud. Or deploy NetScaler Console on-prem. Both are free.
- If NetScaler Console at Citrix Cloud, then deploy a NetScaler Agent to each datacenter that contains a NetScaler that needs licensing. Currently only a single NetScaler Agent per datacenter hosts licensing. The NetScaler appliances are configured to point to a single NetScaler Agent.
- TCP Ports 27000 and 7279 must be open between the NetScaler NSIPs and either NetScaler Agent or NetScaler Console on-prem Floating IP.
- Install Flex Licenses on NetScaler Console:
- In NetScaler Console, go to NetScaler Licensing > License Management and note the Mac address on the far right.
- Go to https://citrix.com/account > Manage Licenses, find all licenses with the word “Flex“, and allocate all of them to the NetScaler Console MAC address.
- In NetScaler Console, go to NetScaler Licensing > License Management, and install the license file containing the “Flex” licenses.
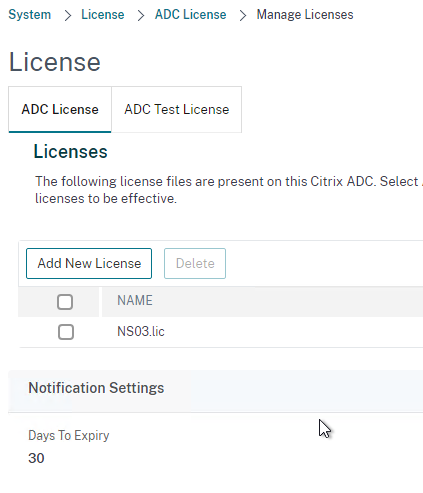
- Note the expiration date of the licenses. At the bottom of the screen is a section to enable Notifications prior to expiration. You will need to manually install newer licenses before they expire.
- If MPX or SDX appliances, go to https://citrix.com/account > Manage Licenses, search for “Zero” licenses and allocate each of them to the MAC address of the MPX or SDX appliances. This unlocks remote licensing.
- You can get the MPX/SDX Mac address at System > Licenses > Add New License at the right side of the screen.
- In any NetScaler, go to System > Licenses > Add New License, change it to Use remote licensing, select Pooled Licensing, and enter the address of a NetScaler Agent or NetScaler Console on-prem Floating IP.
- Registering the NetScaler with NetScaler Console is optional. I normally enter fake credentials to skip it and register it later for monitoring, backups, etc.
- Eventually you should see a pop-up showing the available capacity of Flex Licenses. For VPX or MPX, allocate one instance and desired throughput (e.g., 1000 Mbps). For SDX, allocate multiple instances and cumulative throughput for all VPXs on the SDX.
- You can see license usage in NetScaler Console at NetScaler Licensing > Pooled Capacity > Throughput Capacity.
Licensing – VPX Mac Address
To license a Citrix ADC VPX appliance, you will need its MAC address.
- Go to the Configuration tab.
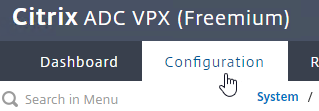
- In the right pane, look down for the Host Id field. This is the MAC address you need for license allocation.
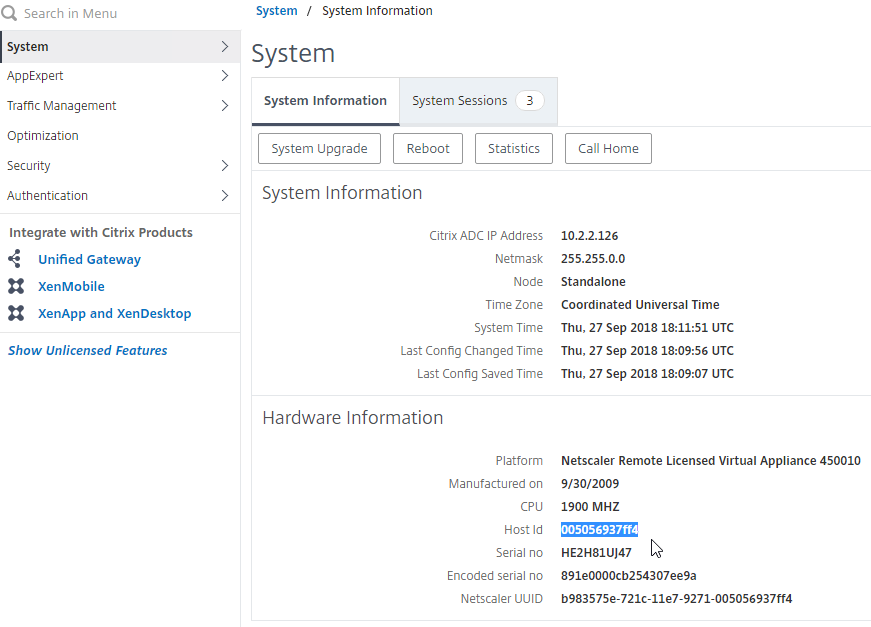
- Another option is to SSH to the appliance and run
shell. - Then run
lmutil lmhostid. The MAC address is returned.
License Allocation at MyCitrix.com
Allocate a Citrix ADC VPX license:
- Login to http://mycitrix.com.
- On the left, click Manage Licenses.
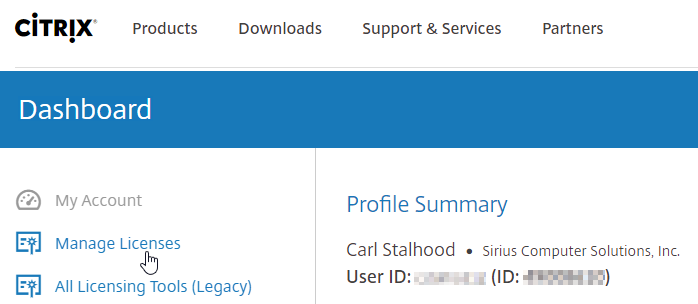
- If you are activating an eval license, at the bottom of the page, click Don’t see a new license and enter the eval license key.
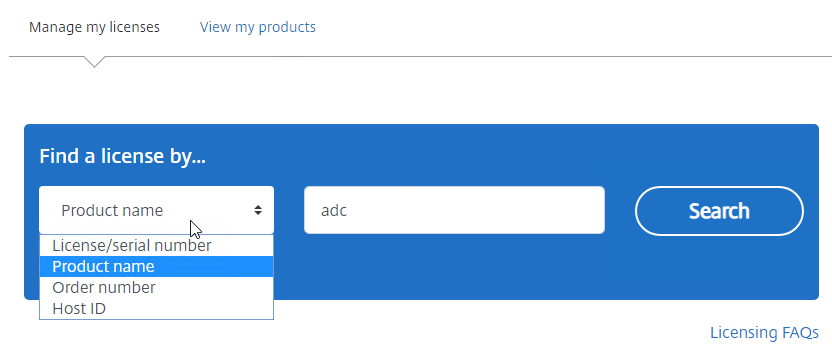
- In the blue Find a license by… box, change the drop-down to Product name, enter adc in the text box, and click Search.
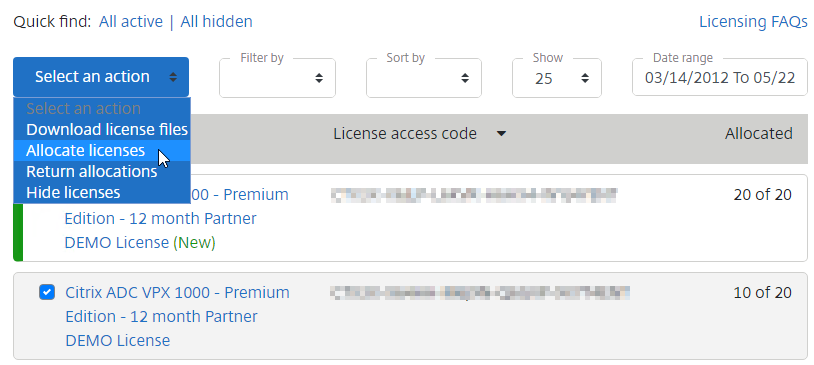
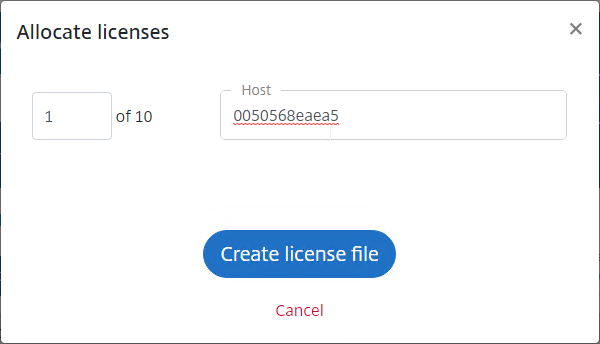
- Select one of your ADC VPX licenses, open the Select an action menu, and click Allocate licenses.
- Change the quantity to 1.
- In the Host field, enter the Host ID (Mac Address) you got from your VPX appliance.
- Click Create license file.
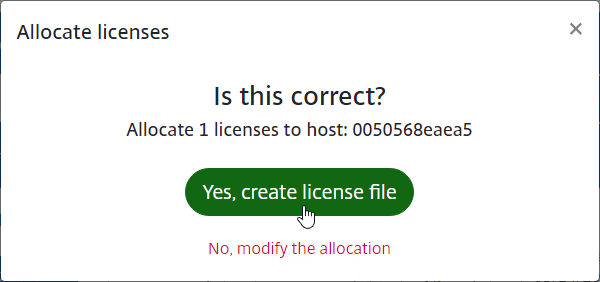
- Click Yes, create license file.
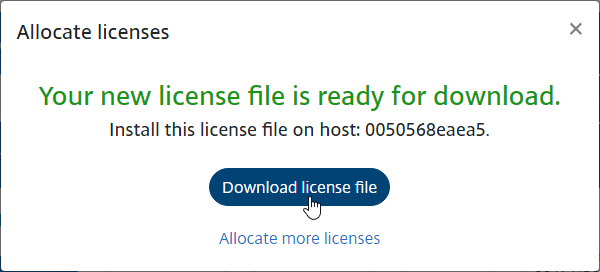
- Click Download license file and save it somewhere.
In Citrix ADC Standard Edition or higher, some Citrix Gateway Universal Licenses are included in your Citrix ADC platform license. There is no need to allocate a license file for these built-in licenses.
- Citrix ADC Standard Edition comes with 500 Gateway Universal licenses
- Citrix ADC Advanced Edition comes with 1,000 Gateway Universal licenses
- Citrix ADC Premium Edition comes with unlimited Gateway Universal licenses
Citrix Gateway VPX Enterprise Edition does not come with any Gateway Universal Licenses. Citrix Gateway VPX Enterprise Edition is a Gateway-only edition that has fewer features than Citrix ADC Standard Edition.
If you need more Gateway Universal licenses than your ADC Edition provides, then you can acquire Gateway Universal licenses by purchasing Citrix Virtual Apps and Desktops (CVAD) Premium Edition, Citrix Endpoint Management Enterprise Edition, or a la carte. Then allocate the additional Citrix Gateway Universal licenses at mycitrix.com.
- Search for gateway licenses, select Citrix Gateway Universal License, open the Select an action menu, and click Allocate licenses.
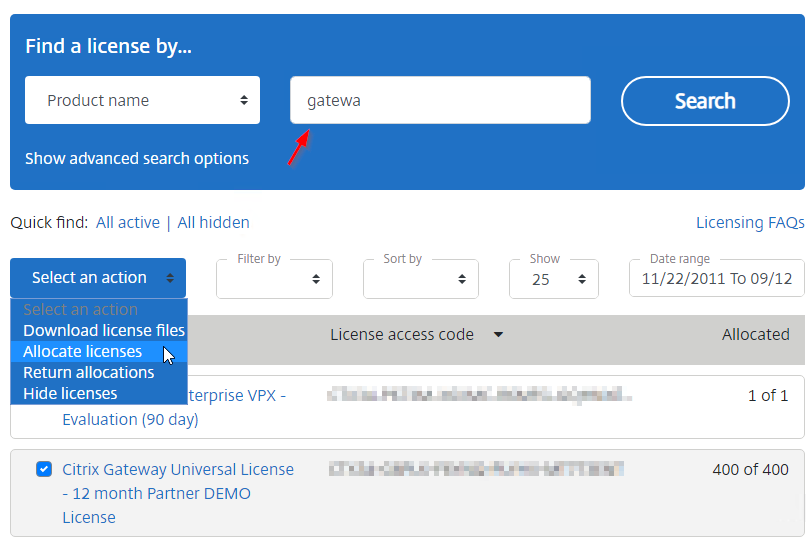
- Change the quantity, or leave it set to allocate all licenses.
- Enter your appliance hostname (not Mac address). If you have two appliances in a HA pair, allocate these licenses to the first appliance hostname, then reallocate them to the second appliance hostname.
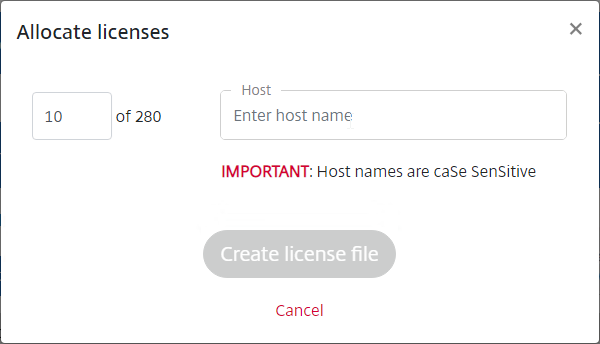
- To get a Citrix ADC’s hostname, login to the ADC as nsroot, and then click the gear icon on the top right.
- In the third row, notice the case sensitive Host Name.
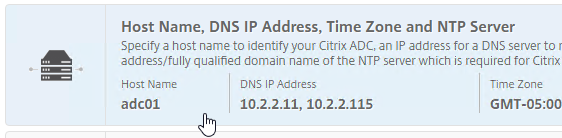
- To get a Citrix ADC’s hostname, login to the ADC as nsroot, and then click the gear icon on the top right.
- Click Create license file.
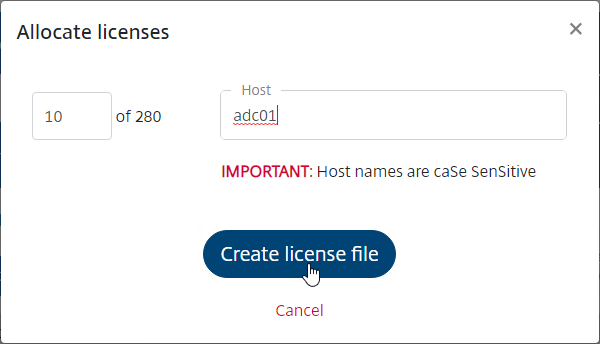
- Click Yes, create license file.
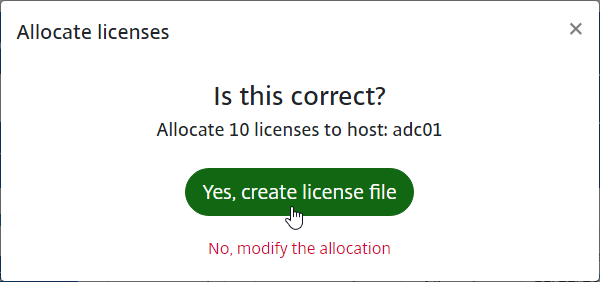
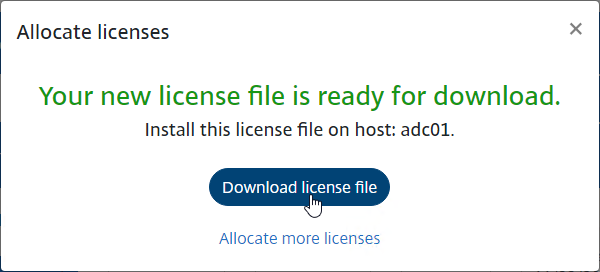
- Click OK when prompted to download your license file. Save it somewhere you know where you are saving it.
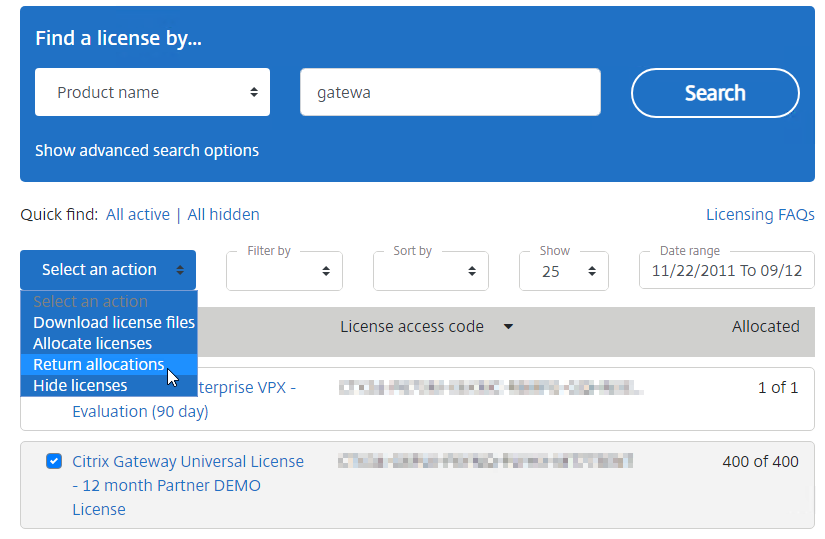
- If you have two appliances in a High Availability pair with different hostnames then you will need to return the Citrix Gateway Universal licenses and reallocate them to the other hostname. The Select an action menu has a Return allocations option.
Install Licenses on Appliance
If you haven’t already installed licenses on your appliance, then do the following:
- If the Setup wizard is open, click the fourth row for Licenses.
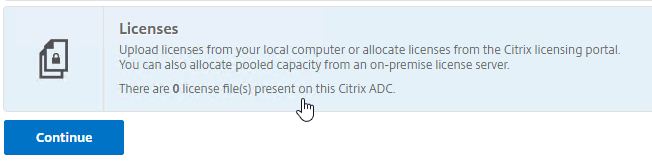
- Otherwise, in the Citrix ADC Configuration GUI, on the left, expand System, and click Licenses.
- On the top right, click Manage Licenses.
- Click Add New License.
- If you have a license file, select Upload license files, and then click Browse. Select the license file(s), and click Open.
- License files are stored in
/nsconfig/license.
- License files are stored in
- Click Reboot when prompted.
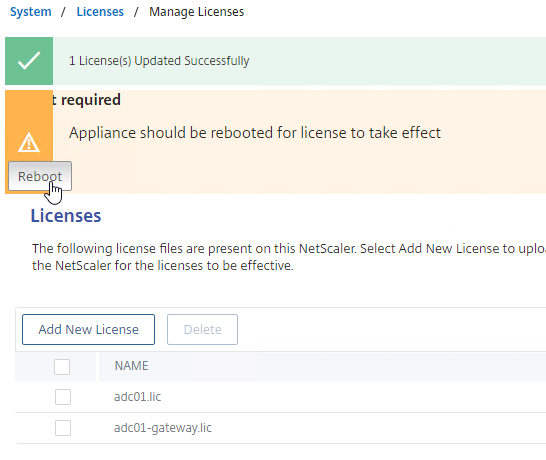
- After reboot, log in. If you allocated and installed your license correctly, then the top left should no longer say Freemium.
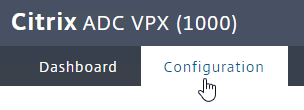
- A window will appear showing the installed license.
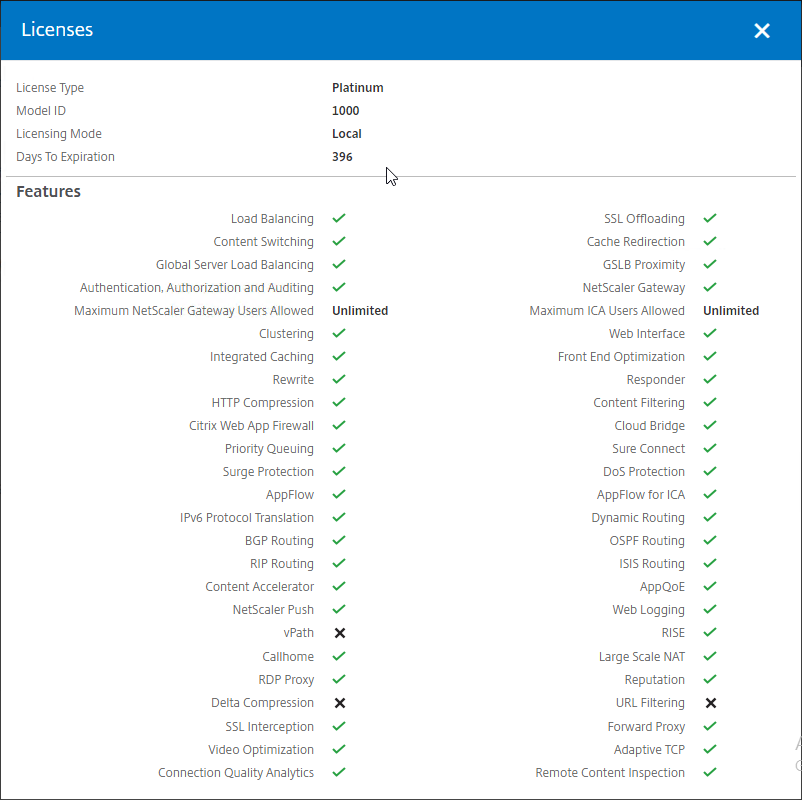
- Notice that Maximum ICA Users Allowed is set to Unlimited.
- Maximum NetScaler Gateway Users Allowed will vary depending on your Citrix ADC Edition.
- Days to Expiration is shown.
- Note: the Citrix ADC SNMP counter allnic_tot_rx_mbits must remain less than the licensed bandwidth or packets will drop.
VPX 100% CPU
Citrix ADC VPX packet engine consumes 100% of the hypervisor CPU. VPX 200 and lower only have one packet engine, so it’s probably consuming around 50% CPU.
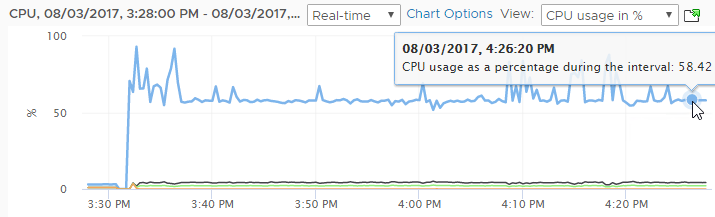
You can change this behavior by doing the following:
- On the left, go to System > Settings.
- On the right, in the bottom of the second column, click Change VPX Configuration Settings.
- Change the CPU Yield drop-down to YES, and click OK.

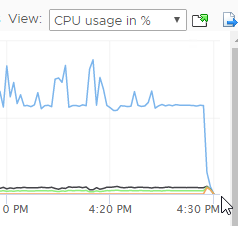
- After making this change, you can see an immediate drop-off in CPU consumption.
Upgrade Firmware
Citrix CTX241500 Citrix ADC Firmware Release Cycle:
- Versions that end in x.1 (e.g. 11.1, 12.1, 13.1, 14.1 etc.) get three years of maintenance releases after one year of feature releases (new features).
- Versions that end in x.0 (e.g. 12.0, 13.0, 14.0, etc.) get one year of maintenance releases after one year of feature releases (new features).
See the Health Check article for the latest firmware versions that resolve security vulnerabilities.
License – Newer firmware is enforcing license subscription dates in the license file. If you don’t have pooled licensing, then check the CSS dates in your license file:
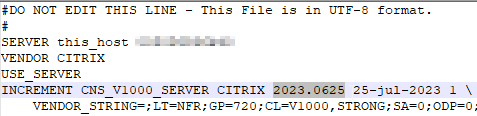
- On NetScaler ADC, go to /nsconfig/license and edit your license file.
- Make sure the left date is newer than today. If not, then you’ll need to go to http://citrix.com/account and re-download the license file for this appliance. The newer license file should have a newer date.
Classic Policies – Gateway Classic Policies (classic authentication policies, classic Session Policies, classic Authorization Policies, etc.) still work in NetScaler 14.1, so it’s not necessary to convert your Gateway Classic Policies to Gateway Advanced Policies before you upgrade.
In ADC 13.1 and newer, some non-Gateway features have been removed. To verify that your config does not use the removed features, see Citrix’s Github for a validation script. NetScaler 14.1 build 17 and newer have an upgrade option in the GUI to Enable NSPEPI Tool to check the config before upgrading.
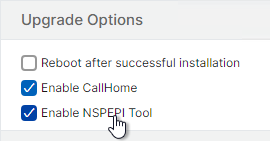
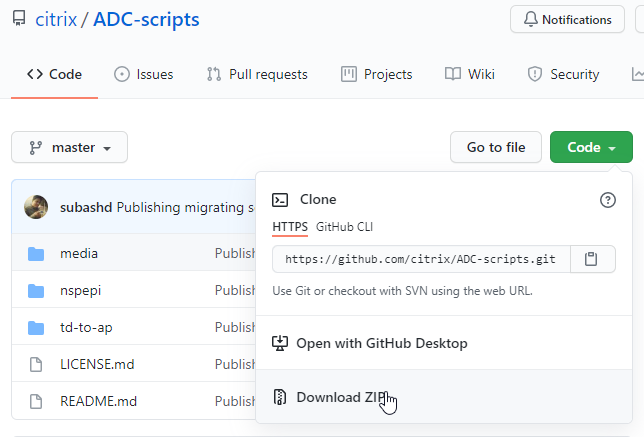
- Go to the root of the Github ADC-scripts repository, click the green Code button and then click Download ZIP. Unzip it after downloading.
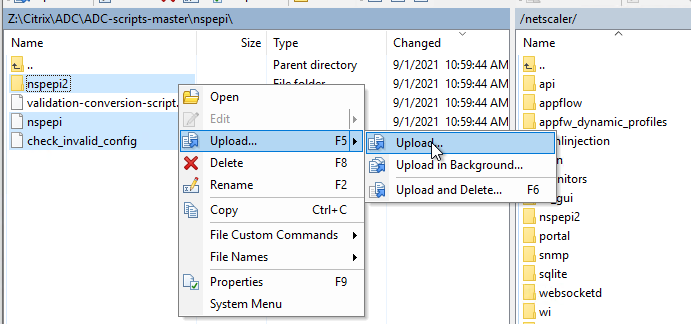
- Use WinSCP or similar to upload the files to the ADC. In the nspepi folder, upload the files nspepi and check_invalid_config to /netscaler on the ADC. Also upload the \nspepi\nspepi2 folder to the /netscaler/nspepi2 folder on the ADC. Replace the existing files.
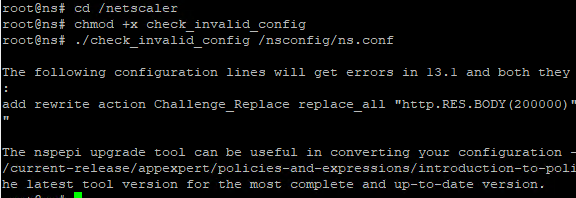
- SSH to ADC and run shell.
- Run the following commands and then review the output:
cd /netscaler chmod +x check_invalid_config ./check_invalid_config /nsconfig/ns.conf
NetScaler Console (formerly known as Citrix ADM) can upgrade firmware. NetScaler Console can also schedule the firmware upgrade instead of doing it immediately. NetScaler Console does a precheck to make sure there are no upgrade issues. For more details, see Creating Maintenance Tasks at NetScaler Docs.
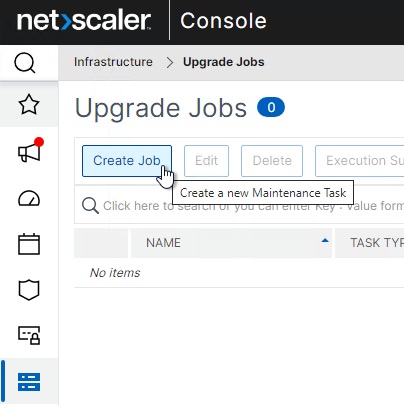
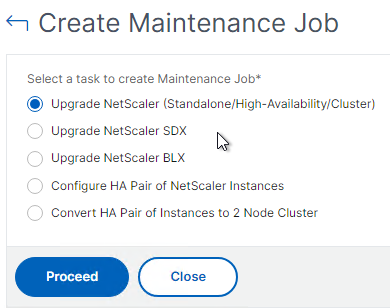
To upgrade firmware using the NetScaler GUI (source = Upgrade a high availability pair at NetScaler Docs):
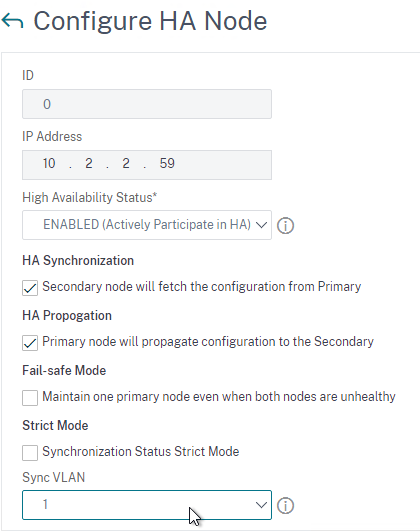
- To do an ISSU upgrade (zero downtime, no TCP disconnects), NetScaler Docs says that HA Sync VLAN should be configured. In a typical deployment where NSIP is not on a tagged VLAN, set it to VLAN 1. Set it on each node at System > High Availability > Nodes > 0 > Edit.
- Download firmware. Ask your Citrix Partner or Citrix Support for recommended versions and builds. You want the Firmware Build, not the VPX (Virtual Appliance).
Note: Firmware for NetScaler Gateway is identical to firmware for NetScaler. Either one will work on either appliance type.
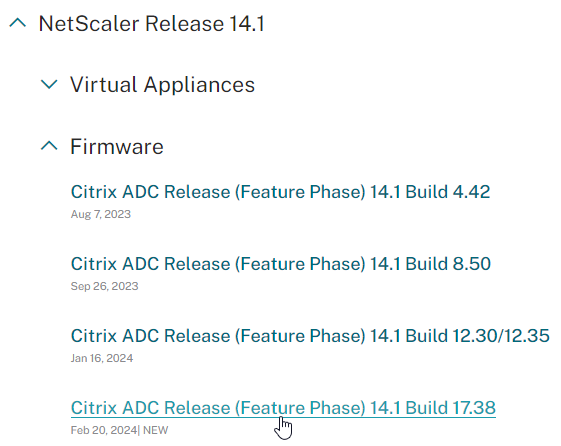
- Watch the Security Bulletins to determine which versions and builds resolve security issues. You can subscribe to the Security Bulletins at http://support.citrix.com by clicking your avatar on the top right after logging in and then clicking My support alerts.
- Some security updates require additional configuration. For example, CTX330728 requires the nsapimgr_wr.sh command.
nsapimgr_wr.sh -ys maxclientForHttpdInternalService=30
- Some security updates require additional configuration. For example, CTX330728 requires the nsapimgr_wr.sh command.
- Save config – Make sure you Save the config before beginning the upgrade. If you do this on the Primary, then both nodes will save their configs.
- License – Transferring the firmware upgrade file to the appliance will be slow unless you license the appliance first. An unlicensed appliance will reduce the maximum upload speed to 20 Mbps.
- Backup – Before upgrading the appliance, consider using WinSCP or similar to back up the /flash/nsconfig directory.
- Start with the Secondary appliance.
- Disk Cleanup – VPXs usually don’t have enough free space to perform the upgrade.
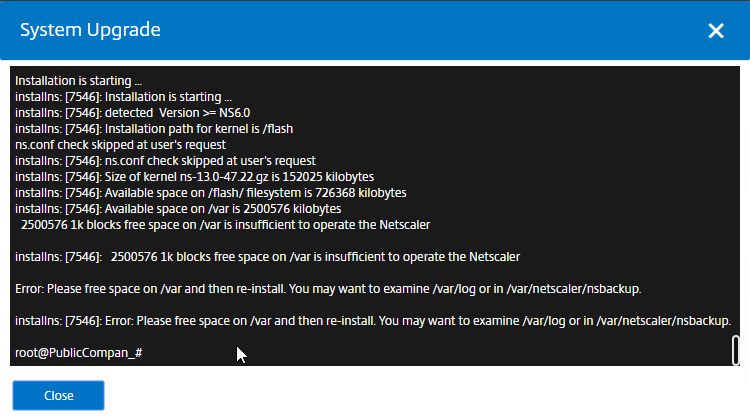
- NetScaler 14.1 build 21 and later let you expand size of Hard Disk 1 and after the reboot NetScaler will automatically expand the /var partition, which you can see by running
df -hin the shell.

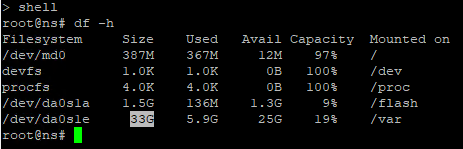
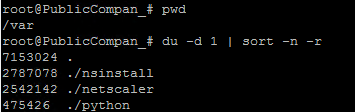
- If you SSH to the appliance, run
shell, runcd /var, then you can run the following command to see disk space consumption sorted by highest:du -d 1 | sort -n -r
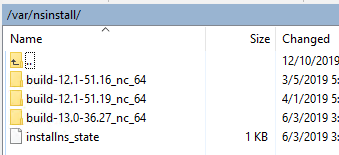
- /var/nsinstall has old firmware upgrades that can be deleted.
- Check /var/netscaler/nsbackup for old backup files.
- A common consumer of disk is the counter files located in /var/nslog.
- Also look in /var/core for crash dumps.
- NetScaler 14.1 build 21 and later let you expand size of Hard Disk 1 and after the reboot NetScaler will automatically expand the /var partition, which you can see by running
- In the Citrix ADC GUI, with the top left node System selected, on the right, click System Upgrade.
- Click Choose File and browse to the build…tgz file.
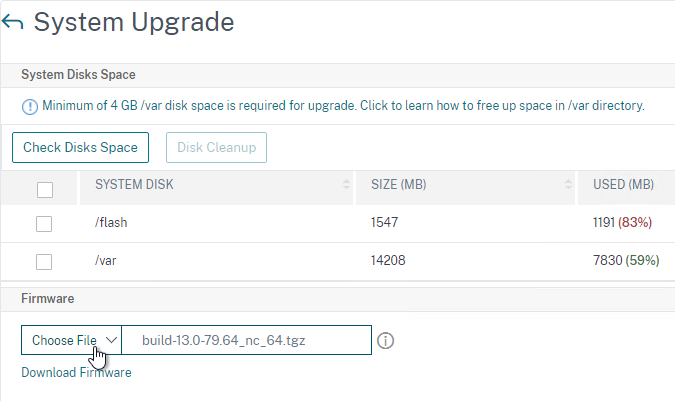
- NetScaler 14.1 build 17 and newer have an upgrade option to Enable NSPEPI Tool to check the config before upgrading.

- Click Upgrade.
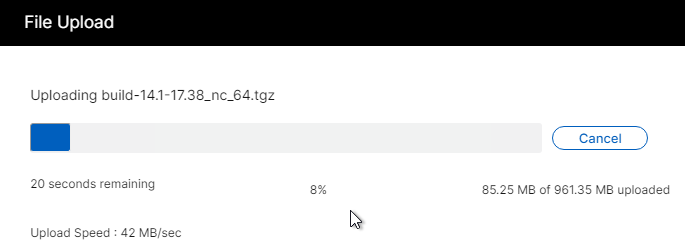
- The firmware will upload.
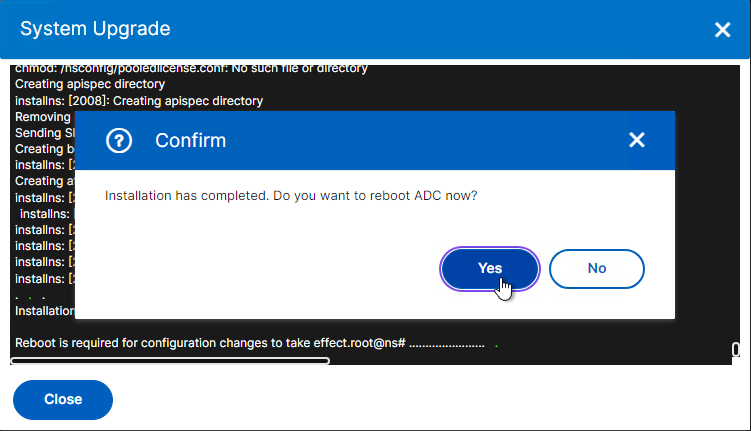
- You should eventually see a System Upgrade window with text in it. If you previously saved your config, then click Yes when asked to reboot. Otherwise, click No, save your config, and then click Reboot.
- Go back to the System node. On the right, click the Reboot button.
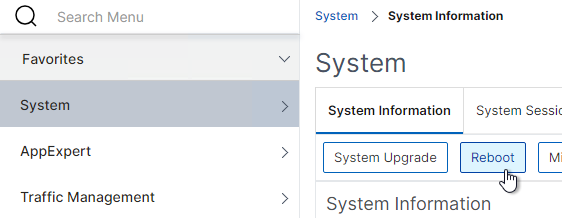
- Click OK to reboot.
- After the reboot, after you login, you can see the firmware version by clicking your name on the top right of the browser window.
- Once the Secondary is done, login, go to System, and click the Migration button to start the zero downtime upgrade as detailed at NetScaler Docs. This is a new feature in ADC 13.
- Or go to System > High Availability > Nodes and do a Force Failover.
- Or go to System > High Availability > Nodes and do a Force Failover.
- Click Start Migration. It will take some time for client connections to drain off of the Primary and move to the upgraded appliance.
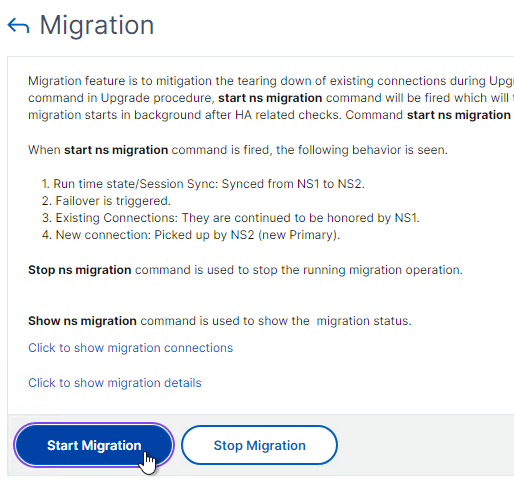
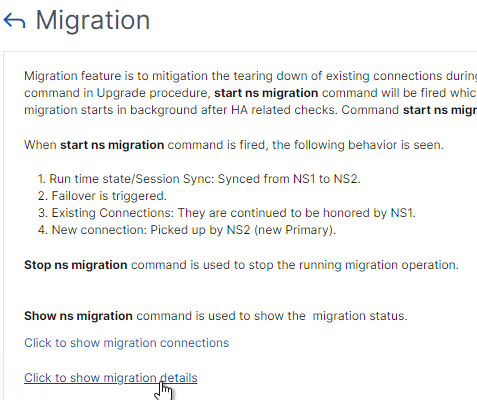
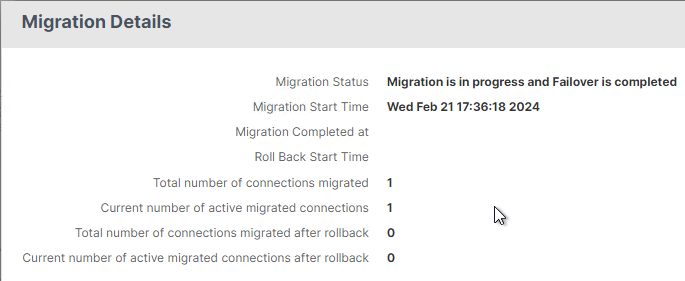
- You can go back into the Migration window and click the link labelled Click to show migration details to see if the failover is complete or not.
- Then upgrade the firmware on the former Primary.
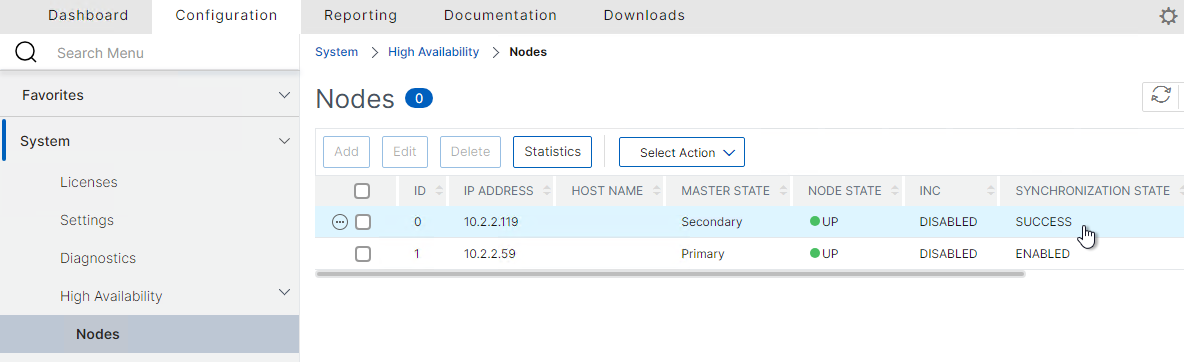
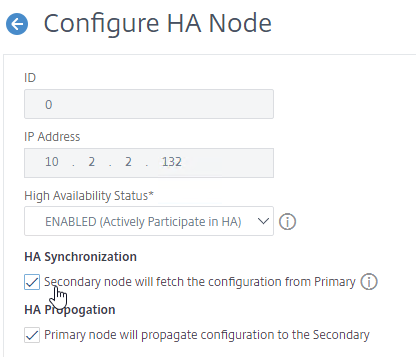
- Go to System > HA > Nodes and verify the Synchronization State. If one of them is disabled, then edit the node, and check the box next to Secondary node will fetch the configuration from Primary.
To install firmware by using the command-line interface
- To upload the software to the Citrix ADC, use a secure FTP client (e.g. WinSCP) to connect to the appliance.
- Create a version directory under
/var/nsinstall(e.g. /var/nsinstall/14.1.36.27). - Copy the software from your computer to the
/var/nsinstall/<version>(e.g. /var/nsinstall/14.1.26.27) directory on the appliance. - Open a Secure Shell (SSH) client (e.g. Putty) to open an SSH connection to the appliance.
- At a command prompt, type
shell. - At a command prompt, type
cd /var/nsinstall/<version>to change to the nsinstall directory. - To view the contents of the directory, type
ls. - To unpack the software, type
tar -xvzf build_X_XX.tgz, wherebuild_X_XX.tgzis the name of the build to which you want to upgrade. - To start the installation, at a command prompt, type
./installns. - When the installation is complete, restart Citrix ADC.
- When the Citrix ADC restarts, at a command prompt type
whatorshow versionto verify successful installation. - To failover the pair without downtime, enter
migrate nsand wait for connections to drain off the former primary appliance. - Then repeat these steps to upgrade the former primary appliance.
High Availability
Configure High Availability as soon as possible to ensure that almost all configurations are synchronized across the two appliances. The synchronization exceptions are mainly network interface configurations (e.g. LACP).
High Availability will also sync files between the two appliances. See CTX138748 File Synchronization in NetScaler High Availability Setup for more information.
- Prepare the secondary appliance:
- The secondary appliance must be the same hardware as the primary appliance.
- Login to the second appliance and configure a NSIP.
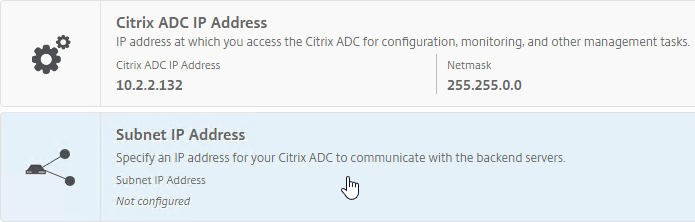
- Don’t configure a SNIP. In Step 2, Subnet IP Address, you can click Do It Later to skip the wizard. You’ll get the SNIP later when you pair it with the primary.
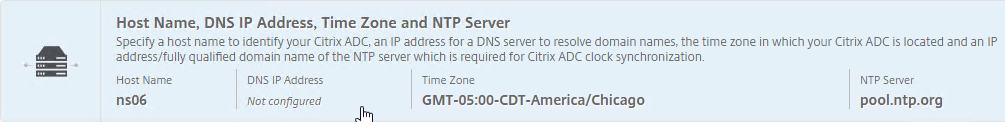
- Configure Hostname, Time Zone, and NTP Servers.
- Don’t configure DNS since you’ll get those addresses when you pair it. However, if NTP points to a DNS name, then NTP won’t work until you pair the appliance.
- License the secondary appliance. The new secondary appliance must be the same edition (License Type) as the former primary appliance.
- Upgrade firmware on the secondary appliance. The firmware of both nodes must be identical.
- On the secondary appliance, go to System > High Availability > Nodes.
- On the right, edit the local node.
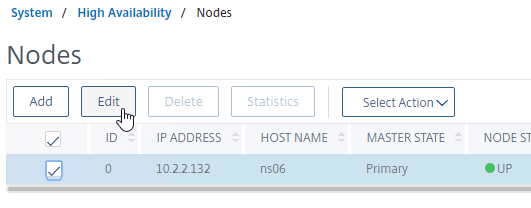
- Change High Availability Status to STAY SECONDARY and click OK. If you don’t do this then you run the risk of losing your config when you pair the appliances.
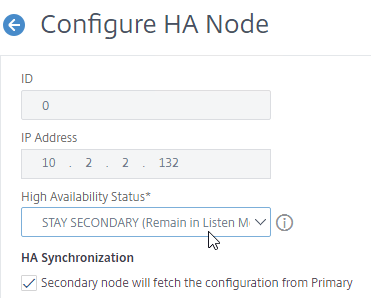
set ha node -hastatus STAYSECONDARY
- Change High Availability Status to STAY SECONDARY and click OK. If you don’t do this then you run the risk of losing your config when you pair the appliances.
- On the primary appliance, on the left, expand System, expand Network, and click Interfaces.
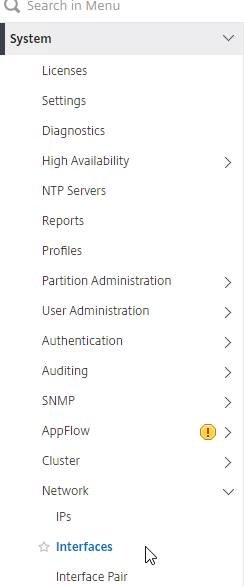
- On the right, look for any interface that is currently DOWN.
- You need to disable those disconnected interfaces before enabling High Availability. Right-click the disconnected interface, and click Disable. Repeat for the remaining disconnected interfaces.
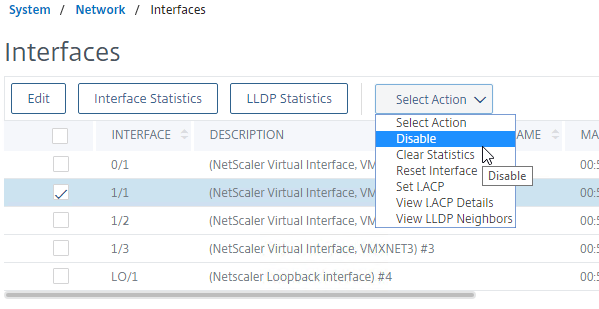
show interface disable interface 1/1
- On the primary appliance, on the left, expand System, expand High Availability, and click Nodes.
- On the right, edit node 0.
- Change the High Availability Status to STAY PRIMARY, and click OK.
- Change the High Availability Status to STAY PRIMARY, and click OK.
- On the right, click Add.
- Enter the other Citrix ADC’s NSIP address.
- Enter the other Citrix ADC’s login credentials, and click Create.
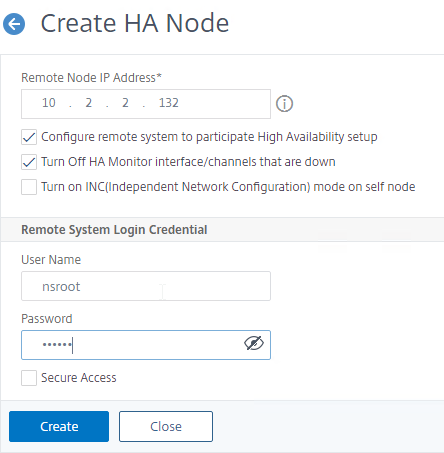
add ha node 1 192.168.123.14
Note: this CLI command must be run separately on each appliance.
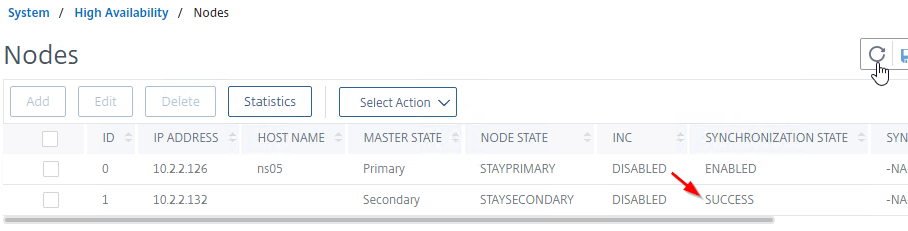
- If you click the refresh icon near the top right, Synchronization State will probably say IN PROGRESS. Keep refreshing until it says SUCCESS.
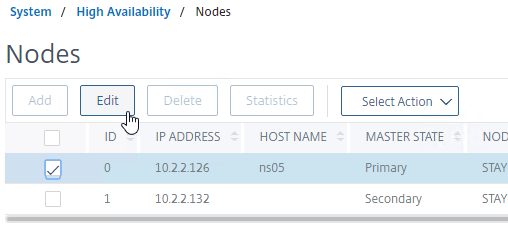
- Edit Node ID 0 (the local appliance).
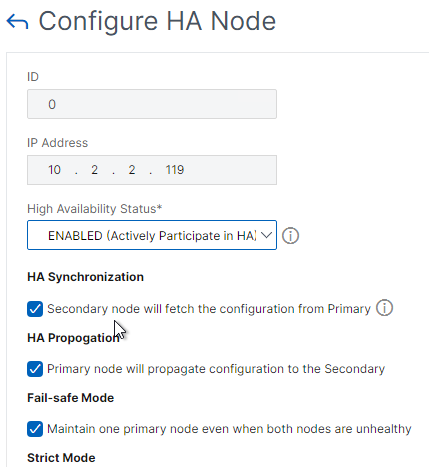
- Change High Availability State back to ENABLED.
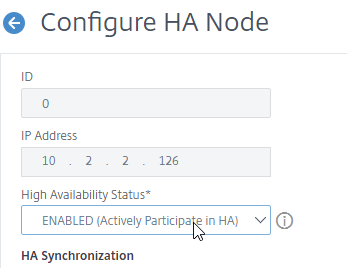
- Under Fail-safe Mode, check the box next to Maintain one primary node even when both nodes are unhealthy.
- Scroll down, and click OK.
set ha node -failSafe ON
- Change High Availability State back to ENABLED.
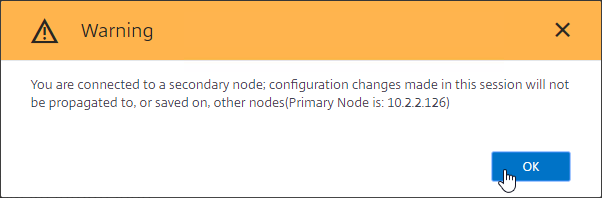
- If you login to the Secondary appliance, you might see a message warning you against making changes. Always apply changes to the Primary appliance.
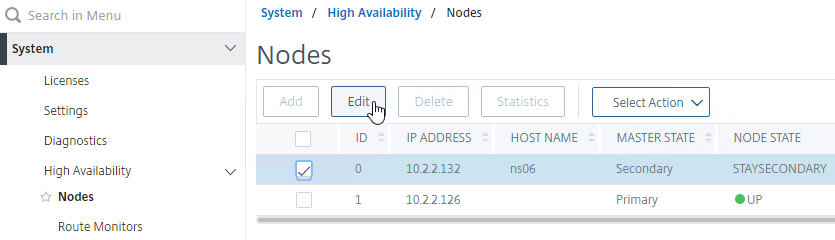
- On the secondary appliance, go to System > High Availability > Nodes and edit the local node 0.
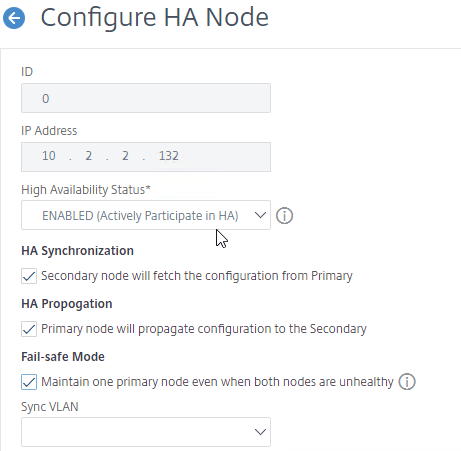
- Change it from STAY SECONDARY to ENABLED. Also enable Fail-safe Mode. Click OK.
- On the new secondary appliance, go to System > Network > Routes, and make sure you don’t have two 0.0.0.0/0.0.0.0 routes. Joining an appliance to an HA pair causes the default route on the primary appliance to sync to the secondary appliance. But, it doesn’t delete the default gateway that was formerly configured on the secondary appliance.
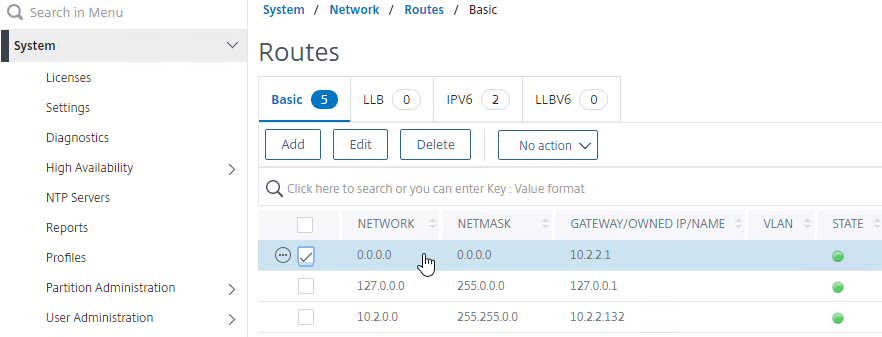
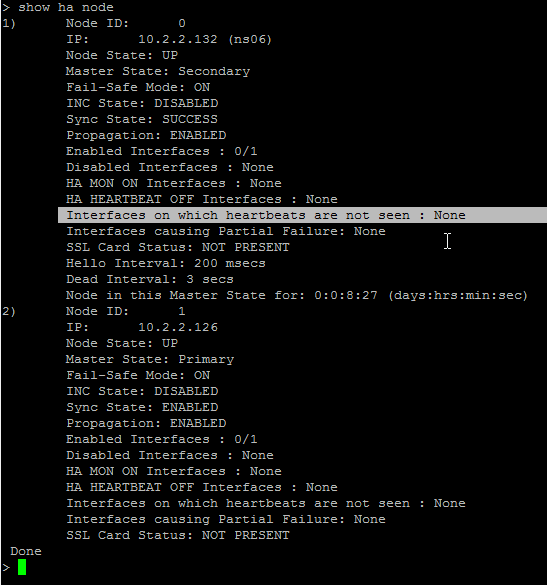
- From the Citrix ADC CLI (SSH), run “sh ha node” to see the status. You should see heartbeats on all interfaces. If not, configure VLANs as detailed later..
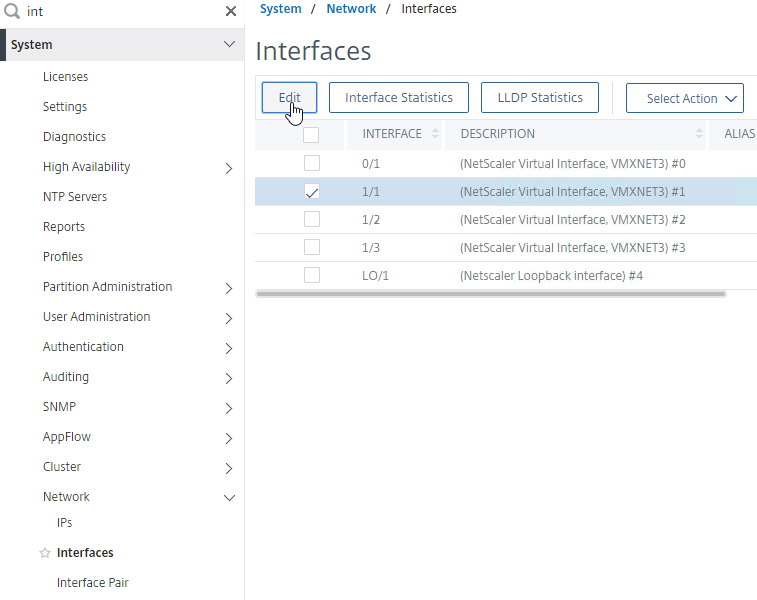
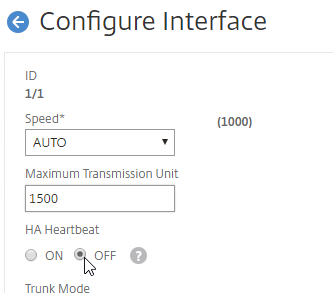
- You can also disable HA heartbeats on specific network interfaces (System > Network > Interfaces).
- Note: Make sure HA heartbeats are enabled on at least one interface/channel.
- Note: this is an interface configuration, which means this configuration change is not propagated to the other node.
- To do an ISSU upgrade (zero downtime, no TCP disconnects), Citrix Docs says that HA Sync VLAN should be configured. In a typical deployment where NSIP is not on a tagged VLAN, set it to VLAN 1. Set it on each node at System > High Availability > Nodes > 0 > Edit.

HA Failover
- HA Failover changes the MAC address associated with VIPs and SNIPs. If your firewall (e.g. Cisco ASA) doesn’t like Gratuitous ARP, then see CTX112701 – The Firewall Does not Update the Address Resolution Protocol Table
- ADC 13 adds a graceful node Migrate operation which drains sessions instead of drops sessions.
- Once migration is started, the two nodes no longer synchronize their configurations. The only way to clear the migration status is to reboot the Secondary. See zero downtime upgrade at Citrix Docs.
- Go to System, and click the Migrate button to start the Migrate operation.
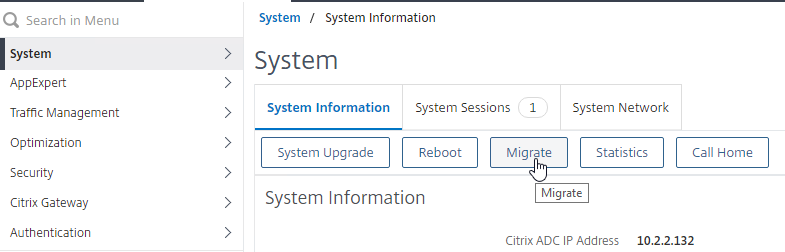
- Click Start Migration. It will take some time for client connections to drain off of the Primary and move to the upgraded appliance.
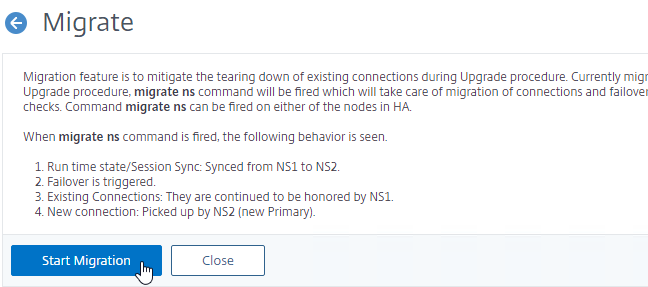
migrate ns
- To clear the migration and allow nodes to be failed over again, reboot the secondary.
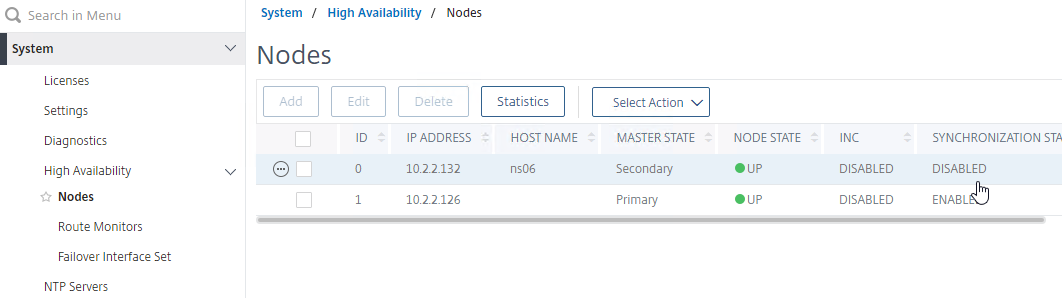
- Go to System > HA > Nodes and verify the Synchronization State. If one of them is disabled, then edit the node, and check the box next to Secondary node will fetch the configuration from Primary.
- Instead of Migrate, you can do a Force Failover, which does not require a reboot, and the nodes continue synchronizing.
- Go to System > High Availability > Nodes, open the menu named Select Action, and do a Force Failover.
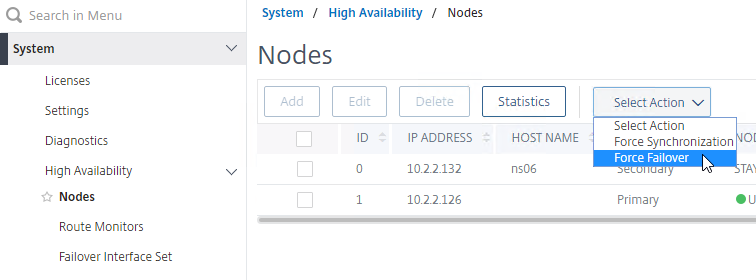
force ha failover
- Go to System > High Availability > Nodes, open the menu named Select Action, and do a Force Failover.
Port Channels on Physical Citrix ADC MPX
If you are configuring a Citrix ADC MPX (physical appliance), and if you plugged in multiple cables, and if more than one of those cables is configured on the switch for the same VLAN(s), then you must bond the interfaces together by configuring a Port Channel.
- On the switch, create a Port Channel, preferably with LACP enabled.
- The Port Channel can be an Access Port (one VLAN), or a Trunk Port (multiple VLANs).
- On the Citrix ADC, configure LACP on the network interfaces, or create a Channel manually. Both methods are detailed below.
Also see Webinar: Troubleshooting Common Network Related Issues with NetScaler.
LACP Port Channel
To configure Port Channels on a Citrix ADC, you can either enable LACP, or you can configure a Channel manually. If your switch is configured for LACP, do the following on Citrix ADC to enable LACP on the member interfaces.
- Go to System > Network > Interfaces.
- On the right, edit one of the Port Channel member interfaces.
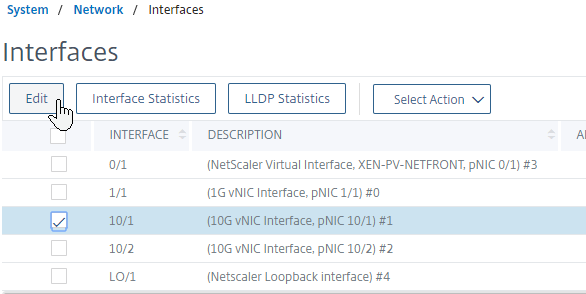
- Scroll down.
- Check the box next to Enable LACP.
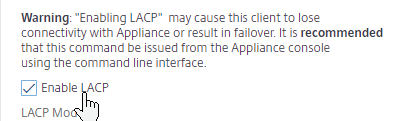
- In the LACP Key field, enter a number. The number you enter here becomes the channel number. For example, if you enter 1, Citrix ADC creates a Channel named LA/1. All member interfaces of the same Port Channel must have the same LACP Key. Click OK when done.
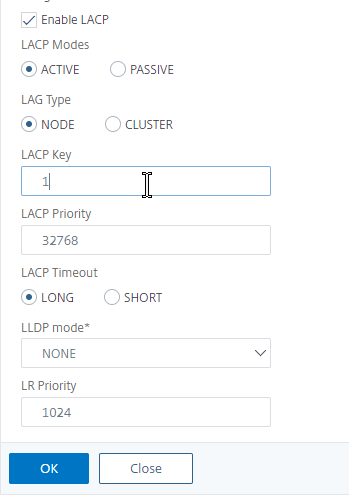
- Continue enabling LACP on member interfaces and specifying the key (channel number). If you are connected to two port channels, one set of member interfaces should have LACP Key 1, while the other set of member interfaces should have LACP Key 2.
- In an HA pair, you must perform this interface configuration separately on both nodes. The LACP commands are not propagated across the HA pair.
- If you go to System > Network > Channels.
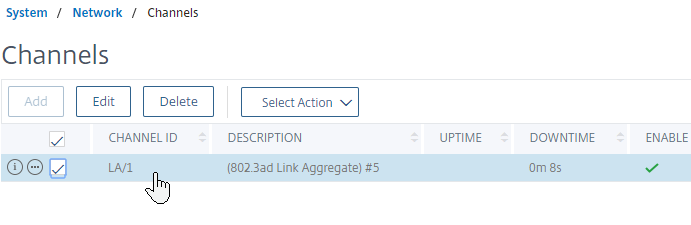
- You’ll see the LACP Channels on the right. These were created automatically after you set the LACP Key on the interface.
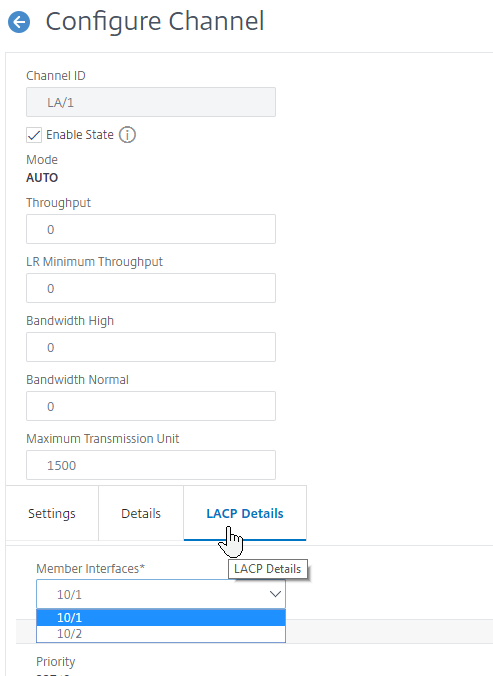
- If you edit a Channel, there’s a LACP Details tab that shows you the member interfaces.
Manual Channel
If your switch ports are not configured for LACP, then you can instead create a Channel manually.
- Go to System > Network > Channels.
- On the right, click Add.
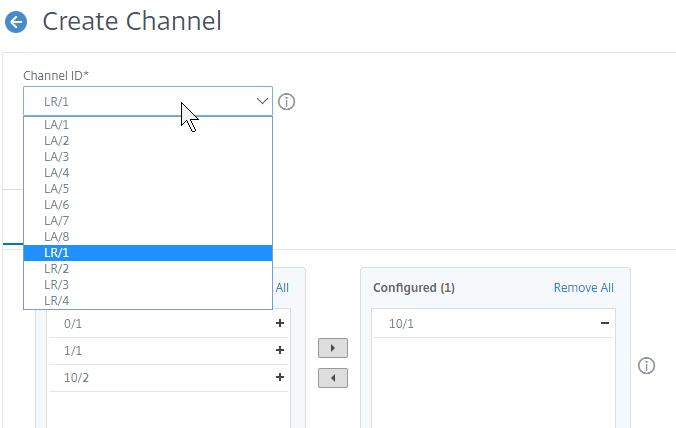
- At the top, choose an unused Channel ID (e.g. LA/1).
- On the bottom, in the Bind/Unbind section, click Add.
- Click the plus icon next to each member interface to move it to the right. Then click Create.
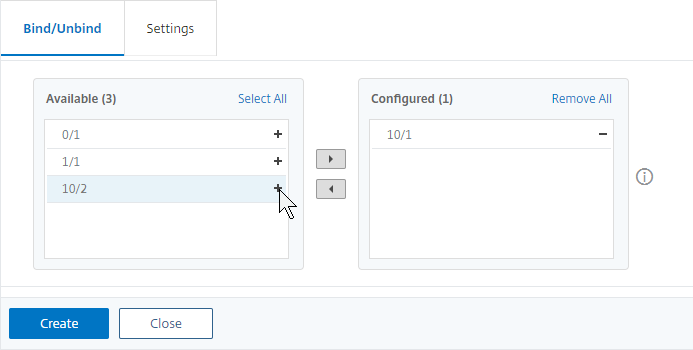
Redundant Interface Set
You can also configure the Citrix ADC for switch-independent teaming. Create a Channel manually, but select a Channel ID starts with LR instead of LA. This is called Link Redundancy or Redundant Interface Set.
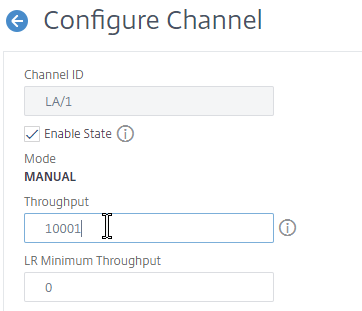
Channel Minimum Throughput
Channels can be configured so that a High Availability failover occurs when the Channel throughput drops below a configured value. For example, if you have four members in a Channel, you might want a High Availability failover to occur when two of the member interfaces fail.
- Go to System > Network > Channels, and edit a Channel.
- Near the top, enter a minimum threshold value in the Throughput field. If the total bonded throughput drops below this level, a High Availability failover will occur.
Trunk Port and High Availability
If you are trunking multiple VLANs across the channel, and if every VLAN is tagged (no native VLAN), then a special configuration is needed to allow High Availability heartbeats across the channel.
- Go to System > Network > VLAN.
- Add a VLAN object.
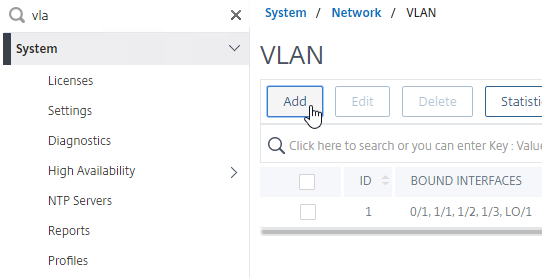
- Bind the VLAN to a channel or interface. To bind multiple VLANs to a single interface/channel, the VLANs must be tagged.
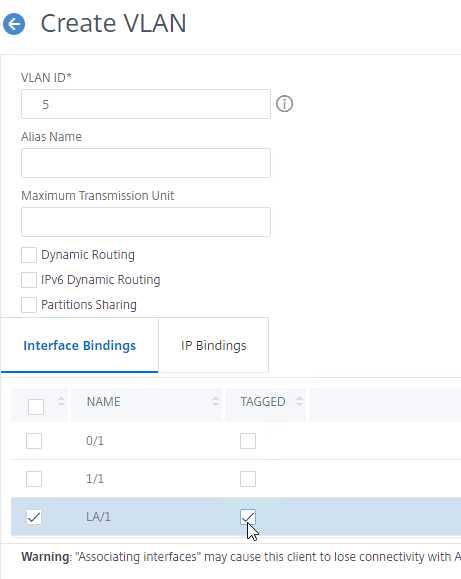
- Configure one of the VLANs as untagged. Only untag one of the VLANs. Which one you untag doesn’t matter. If your switch doesn’t allow untagged packets, don’t worry, we’ll fix that soon.
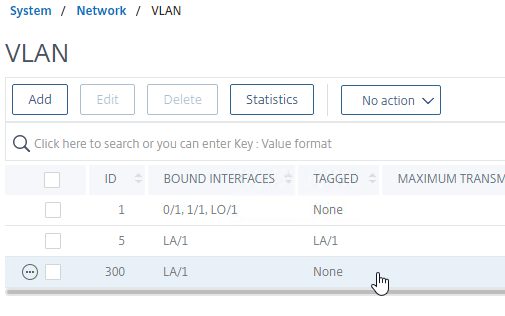
- If your switch doesn’t allow untagged packets, go to System > Network > Channels, and edit the channel.
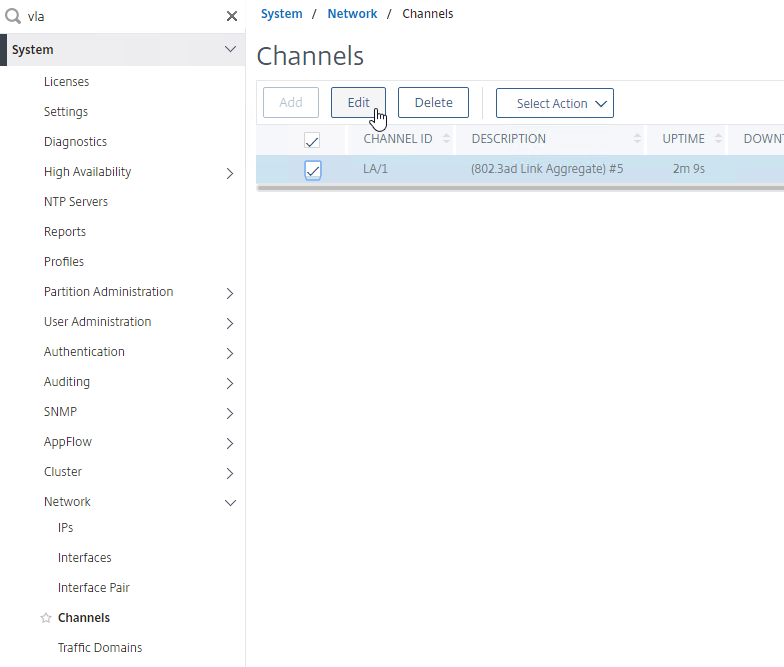
- Scroll down and switch to the tab named Settings.
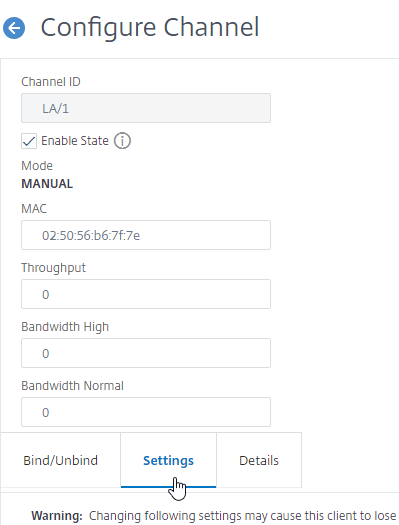
- Set Tag all VLANs to ON to cause Citrix ADC to tag all packets, including the VLAN you formerly marked as untagged.
- We essentially moved the VLAN tagging from the VLAN to the Channel/Interface, which means VLAN tagging happens lower in the network stack so High Availability heartbeat packets are also tagged.
- Note: in an HA pair, you must perform this Tagall configuration separately on both nodes. The Tagall command is not propagated across the HA pair.
Common physical interface configuration
Here is a common Citrix ADC networking configuration for a physical Citrix ADC MPX that is connected to both internal and DMZ.
Note: If the appliance is connected to both DMZ and internal, then be aware that this configuration essentially bypasses (straddles) the DMZ-to-internal firewall. That’s because if a user connects to a public/DMZ VIP, then Citrix ADC could use an internal SNIP to connect to the internal server: in other words, traffic comes into a DMZ VLAN, but goes out an internal VLAN. A more secure approach is to have different appliances for internal and DMZ. Or use Citrix ADC SDX, partitioning, or traffic domains.
- 0/1 connected to a dedicated management network. NSIP is on this network.
- No data on 0/1 – 0/1 is not optimized for high throughput so don’t put data traffic on this interface. If you don’t have a dedicated management network, then put your NSIP on one of the other interfaces (1/1, 10/1, LA/1, etc.) and don’t connect any cables to 0/1.
- No SNIP on management network – To prevent Citrix ADC from using this dedicated management interface for outbound data traffic, don’t put a SNIP on this management network, and configure the default gateway (route 0.0.0.0) to use a router on a different data network (typically the DMZ VLAN). However, if there’s no SNIP on this VLAN, and if the default gateway is on a different network, then there will be asymmetric routing for management traffic, since inbound management traffic goes in 0/1, but reply traffic goes out LA/1 or LA/2. To work around this problem, enable Mac Based Forwarding, or configure Policy Based Routing. Both of these options are detailed in the next section.
- Management VLAN tagging – It’s easiest if the switch port for this dedicated management interface is an Access Port (untagged). If VLAN tagging is required, then NSVLAN must be configured on the Citrix ADC.
- 10/1 and 10/2 in a LACP port channel (LA/1) connected to internal VLAN(s). Static routes to internal networks through a router on one of these internal VLANs.
- Access Port – If only one internal VLAN, configure the switch ports/channel as an Access Port.
- Trunk Port – If multiple internal VLANs, configure the switch ports/channel as a Trunk Port. Set one of the VLANs as the channel’s Native VLAN so it doesn’t have to be tagged.
- Tag HA heartbeat packets – If the networking team is unwilling to configure a Native VLAN on the Trunk Port, then Citrix ADC needs special configuration (tagall) to ensure HA heartbeat packets are tagged.
- 1/1 and 1/2 in a LACP port channel (LA/2) connected to DMZ VLAN(s). The default gateway (route 0.0.0.0) points to a router on a DMZ VLAN so replies can be sent to Internet clients.
- Access Port – If only one DMZ VLAN, configure the switch ports/channel as an Access Port.
- Trunk Port – If multiple DMZ VLANs, configure the switch ports/channel as a Trunk Port. Set one of the VLANs as the channel’s Native VLAN so it doesn’t have to be tagged.
- Tag HA heartbeat packets – If the networking team is unwilling to configure a Native VLAN on the Trunk Port, then Citrix ADC needs special configuration (tagall) to ensure HA heartbeat packets are tagged.
Dedicated Management Subnet
If your Citrix ADC is connected to multiple subnets, then one of those subnets could be a Dedicated Management Subnet. If you have a subnet that is for NSIP only, and if you don’t want to use the NSIP subnet for data traffic, then you’ll want to move the default route off of the NSIP subnet and onto a different data subnet. However, moving the default route breaks traffic from the NSIP. To work around this problem, create PBRs for the NSIP traffic, including both replies from NSIP, and traffic sourced by the NSIP (e.g. Syslog).
Citrix Blog Post Separating NetScaler Management and Data Traffic for DISA STIGs also uses PBRs.
- Go to System > Network > PBRs. You can also search the menu for PBRs.
- On the right, click Add.
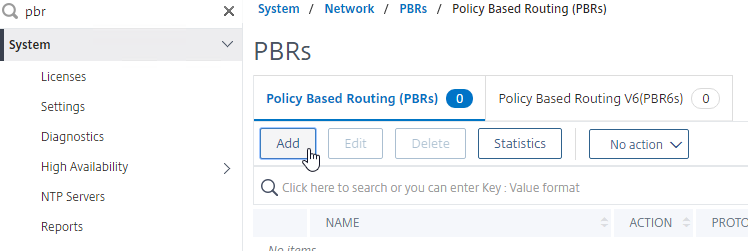
- Give the PBR a name (e.g. NSIP)
- Set the Next Hop Type drop-down to New.
- In the Next Hop field, enter the router IP address that is on the same network as the NSIP.
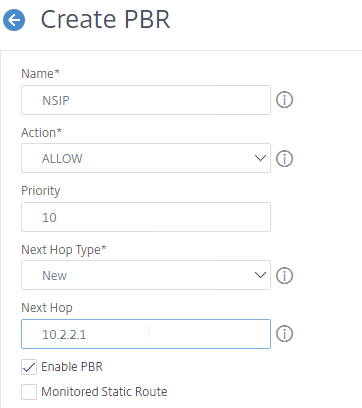
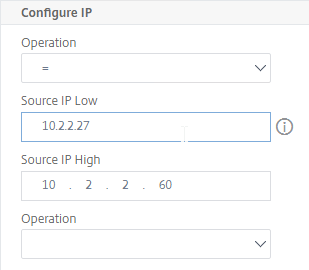
- In the Configure IP section, set the first Operation drop-down to =.
- In the Source IP Low field, enter the NSIP. This causes the PBR to match all traffic with NSIP as the Source IP address.
- In an HA pair, the PBR command is synced and applied to both nodes in the pair. To accommodate this, in the Source IP Low field, enter the lower NSIP address. Then in the Source IP High field, enter the higher NSIP address.
- You don’t need anything else.
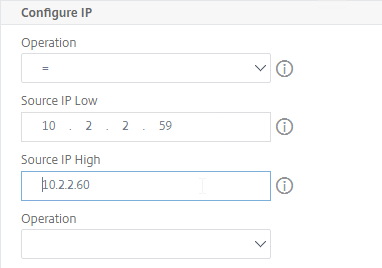
- Scroll down, and click Create. This rule routes any traffic with NSIP as source IP address through a router on the NSIP subnet. The default route will be ignored, but only for NSIP traffic.

- DNS traffic is special. To handle DNS traffic sourced by the NSIP, create another PBR by right-clicking the existing one, and clicking Add.
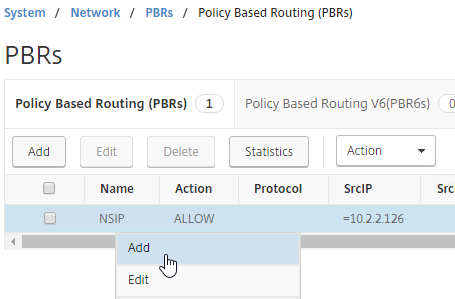
- Change the name to NSIP-DNS or similar.
- Change the Action drop-down to DENY, which tells ADC that traffic matching this PBR should use normal routing instead of overriding to a different gateway.
- Change the Priority to a lower number than the original PBR so this rule is matched before the general NSIP rule. Scroll down.
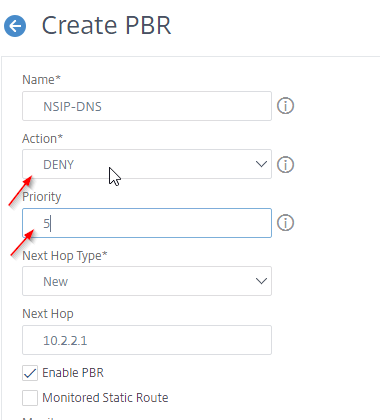
- In the Configure IP section, remove all settings.
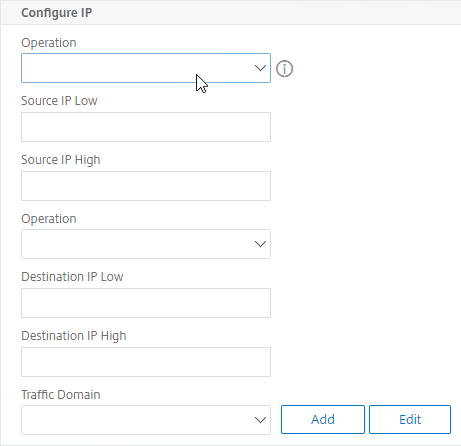
- In the Configure Protocol section, click the Protocol drop-down, and select UDP (17).
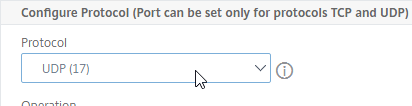
- Above the two Destination port fields, change the Operation to =.
- In the Destination port Low field, enter 53.
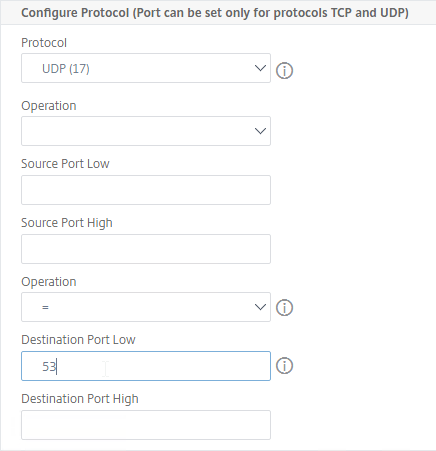
- Scroll down, and click Create.

- Make sure the DENY PBR is higher in the list (lower priority number) than the ALLOW PBR.
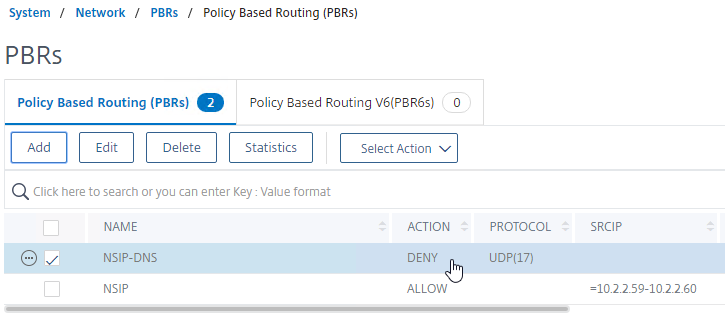
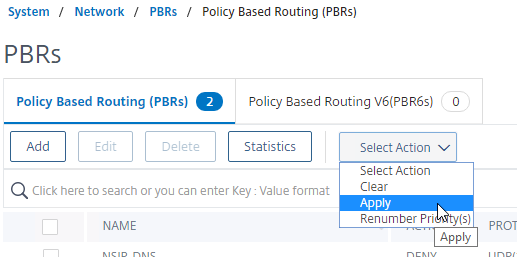
- Then open the Action menu, and click Apply.
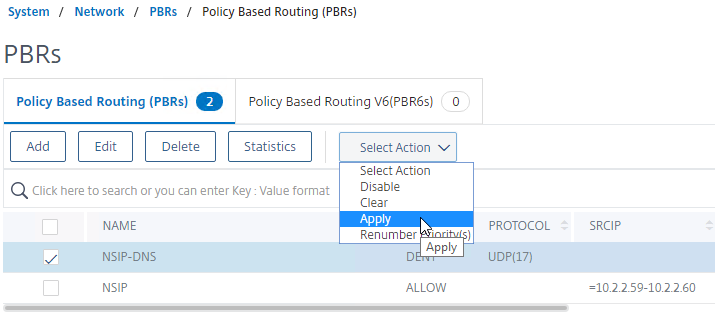
- Click Yes to apply.
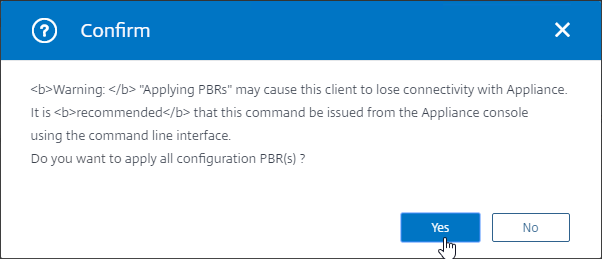
add ns pbr NSIP-DNS DENY -destPort = 53 -nextHop 10.2.2.1 -protocol UDP -priority 5 add ns pbr NSIP ALLOW -srcIP = 10.2.2.126-10.2.2.127 -nextHop 10.2.2.1 apply ns pbrs
Floating Management IP
If you want a floating management IP that is always on the Primary appliance, here’s a method of granting management access without adding a SNIP to the management subnet:
- Create a Load Balancing Service on HTTP 80 on IP address 127.0.0.1. Note: Citrix ADC doesn’t allow creating a Load Balancing service on IP address 127.0.0.1 and port 443 (SSL).
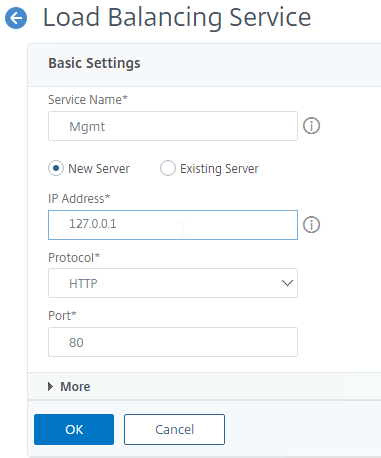
- The IP address you enter is 127.0.0.1. When you view the Load Balancing Service, it shows the local NSIP. After a HA failover, the IP Address will change to the other NSIP.
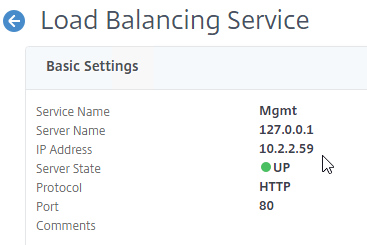
- The IP address you enter is 127.0.0.1. When you view the Load Balancing Service, it shows the local NSIP. After a HA failover, the IP Address will change to the other NSIP.
- Create a Load Balancing Virtual Server using a VIP on the management subnet. Protocol = SSL. Port number = 443. Bind a certificate.
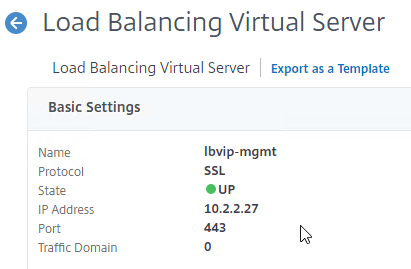
- Bind the loopback:80 service to the Load Balancing Virtual Server. In summary: the front end is 443 SSL, while the LB Service is 80 HTTP.
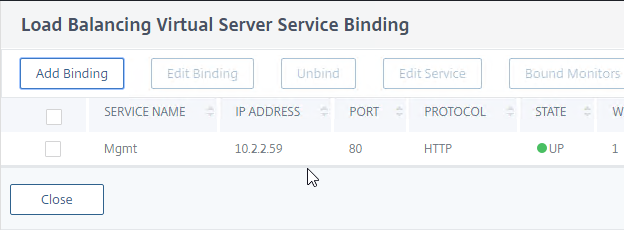
- Bind the loopback:80 service to the Load Balancing Virtual Server. In summary: the front end is 443 SSL, while the LB Service is 80 HTTP.
- Add the new VIP to the PBRs so the replies go out the correct interface. Re-apply the PBRs after you modify them.
- You should then be able to point your browser to https://Step2VIP to manage the appliance.
- You can perform the same loopback trick for 22 SSH. Create a Load Balancing Service on TCP 22 on IP address 127.0.0.1.
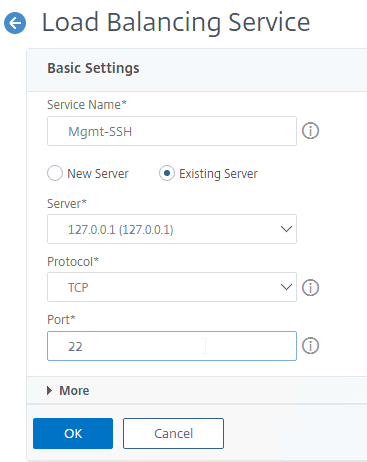
- Create a Load Balancing Virtual Server using the same management VIP specified earlier. Protocol = TCP. Port number = 22.
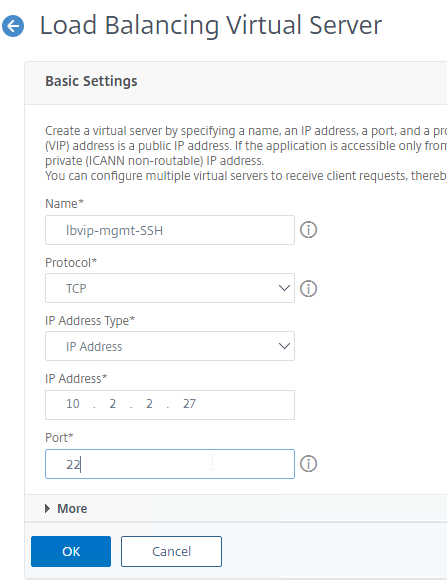
- Bind the loopback:TCP:22 service to the Load Balancing Virtual Server.
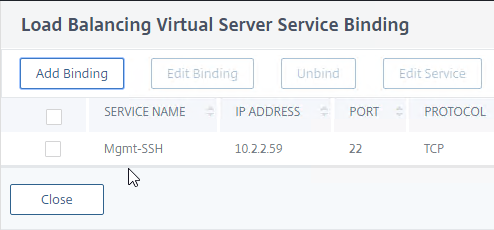
- Bind the loopback:TCP:22 service to the Load Balancing Virtual Server.
- You should then be able to point your SSH Client to <Step2VIP> to manage the appliance.
- CLI Commands for the floating management VIP:
add service mgmt 127.0.0.1 HTTP 80 add service mgmt-SSH 127.0.0.1 TCP 22 add lb vserver mgmt-SSL SSL 10.2.2.128 443 add lb vserver mgmt-SSH TCP 10.2.2.128 22 bind lb vserver mgmt-SSL mgmt bind lb vserver mgmt-SSH mgmt-SSH set ns pbr NSIP-DNS DENY -srcIP = 10.2.2.126-10.2.2.128 -destPort = 53 -protocol UDP -priority 5 set ns pbr NSIP ALLOW -srcIP = 10.2.2.126-10.2.2.128 -nextHop 10.2.2.1 apply ns pbrs
Multiple Subnets / Multiple VLANs
Best practices for network configurations at Citrix Docs and Citrix CTX214033 Networking and VLAN Best Practices for NetScaler discusses many of the same topics detailed in this section.
If this is a physical MPX appliance, see the previous Port Channel section first.
If you only connected Citrix ADC to one subnet (one VLAN) then skip ahead to DNS servers.
Configuration Overview
The general configuration process for multiple subnets is this:
- Create a SNIP for each subnet/VLAN.
- Create a VLAN object for each subnet/VLAN.
- Bind the VLAN object to the SNIP for the subnet.
- Bind the VLAN object to the Port Channel or single interface that is configured for the VLAN/subnet.
SNIPs for each VLAN
You will need one SNIP for each connected subnet/VLAN. VLAN objects (tagged or untagged) bind the SNIPs to particular interfaces. Citrix ADC uses the SNIP’s subnet mask to assign IP addresses to particular interfaces.
NSIP Subnet
The NSIP subnet is special, so you won’t be able to bind it to a VLAN. Use the following SNIP/VLAN method for any network that does not have the NSIP. The remaining interfaces will be in VLAN 1, which is the VLAN that the NSIP is in. VLAN 1 is only locally significant so it doesn’t matter if the switch is configured with it or not. Just make sure the switch has a native VLAN configured, or configure the interface as an access port. If you require trunking of every VLAN, including the NSIP VLAN, then additional configuration is required (NSVLAN or Tagall).
Configure Subnets/VLANs
To configure Citrix ADC with multiple connected subnets:
- Add a subnet IP for every network the Citrix ADC is connected to, except the dedicated management network. Expand System, expand Network, and click IPs.
- On the right, click Add.
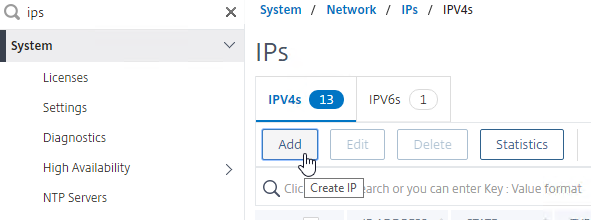
- Enter the Subnet IP Address for this network/subnet. The SNIP will be the source IP address the Citrix ADC will use when communicating with any other service/server on this network. The Subnet IP is also known as the Interface IP for the network. You will need a separate SNIP for each connected network (VLAN).
- Enter the netmask for this network.
- Ensure the IP Type is set to Subnet IP. Scroll down.
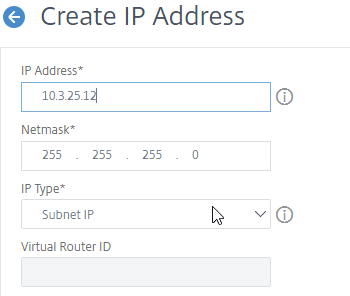
add ns ip 172.16.1.11 255.255.255.0 -type SNIP
- Under Application Access Controls, decide if you want to enable GUI management on this SNIP. This feature can be particularly useful for High Availability pairs, because when you point your browser to the SNIP, only the primary appliance will respond. However, enabling management access on the SNIP can be a security risk, especially if this is a SNIP for a DMZ network.
- Click Create when done. Continue adding SNIPs for each connected network (VLAN).
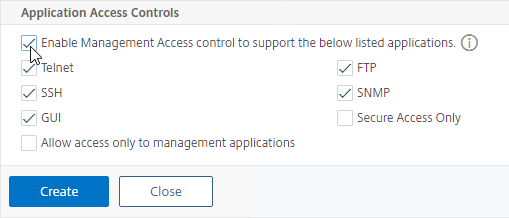
set ns ip 172.16.1.11 -mgmtAccess ENABLED -telnet DISABLED -ftp DISABLED
- On the left, expand System, expand Network, and click VLANs.
- On the right, click Add.
- Enter a descriptive VLAN ID. The actual VLAN ID only matters if you intend to tag the traffic. If not tagged, then any ID (except 1) will work.
- In the Interface Bindings section, check the box next to one physical interface or channel (e.g. LA/1) that is connected to the network.
- If this is a trunk port, select Tagged if the switch port/channel is expecting the VLAN to be tagged.
- If your switches do not allow untagged packets, then you will need to use the tagall interface option to tag Citrix ADC High Availability heartbeat packets. See CTX122921 Citrix NetScaler Interface Tagging and Flow of High Availability Packets
- If you don’t tag the VLAN, then the Citrix ADC interface/channel is removed from VLAN 1, and instead put in this VLAN ID.
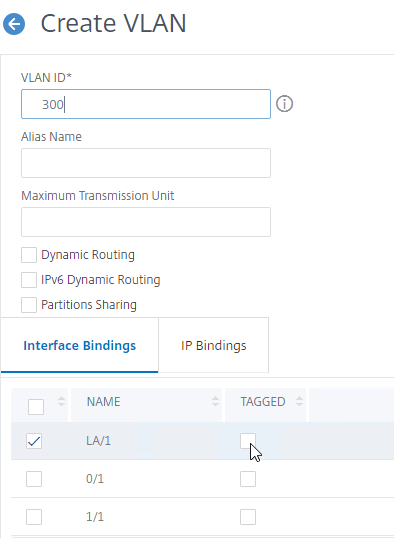
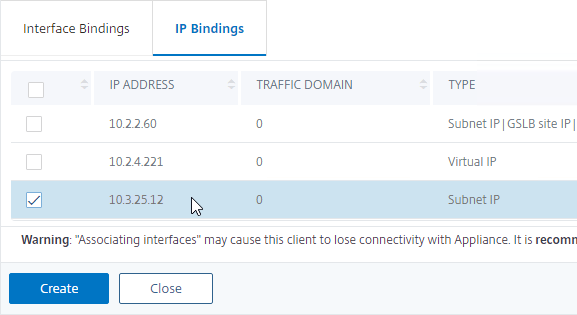
- Switch to the tab named IP Bindings.
- Check the box next to the Subnet IP for this network. This lets Citrix ADC know which interface is used for which IP subnet. Click Create when done.
add vlan 50 bind vlan 50 -ifnum LA/1 -IPAddress 172.16.1.11 255.255.255.0
- Add static routes to the internal networks through an internal router.
- On the left, expand System, expand Network, and click Routes.
- On the right, click Add.
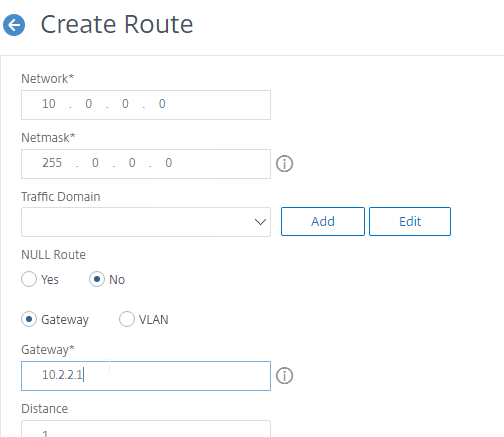
- Make sure NULL Route is set to No.
- Set the Gateway (next hop) to an internal router.
- Then click Create.
add route 10.2.0.0 255.255.0.0 10.2.2.1
- The default route should be changed to use a router on the DMZ network (towards the Internet). Before deleting the existing default route, either enable Mac Based Forwarding, or create a Policy Based Route, so that the replies from NSIP can reach your machine. You usually only need to do this for dedicated management networks.
- Note: PBR is recommended over MBF, because PBR can handle traffic sourced by NSIP (e.g Syslog traffic), while MBF cannot.
- Mac Based Forwarding sends replies out the same interface they came in on. However, MBF ignores the routing table, and doesn’t handle traffic sourced by the NSIP (e.g. LDAP traffic). To enable MBF:
- On the left, expand System, and click Settings.
- On the right, in the left column, click Configure modes.
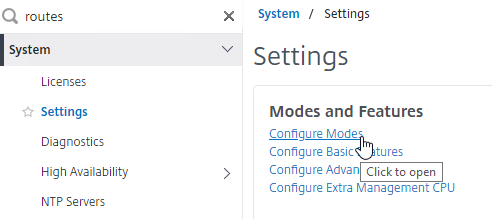
- Check the box next to MAC Based Forwarding (MBF), and click OK. More info on MAC Based Forwarding can be found at Citrix CTX1329532 FAQ: Citrix NetScaler MAC Based Forwarding (MBF).
enable mode mbf
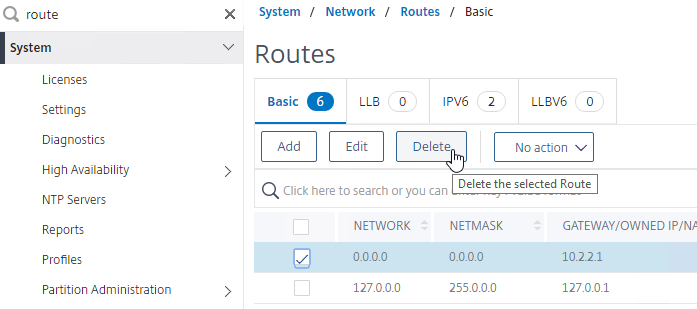
- Go back to System > Network > Routes.
- On the right, delete the 0.0.0.0 route. Don’t do this unless the Citrix ADC has a route, PBR, or MBF to the IP address of the machine you are running the browser on.
rm route 0.0.0.0 0.0.0.0 10.2.2.1 - Then click Add.
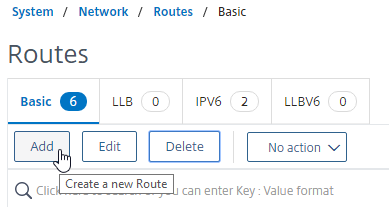
- Set the Network to 0.0.0.0, and the Netmask to 0.0.0.0.
- Make sure NULL Route is set to No.
- Enter the IP address of the DMZ (or data) router, and click Create.
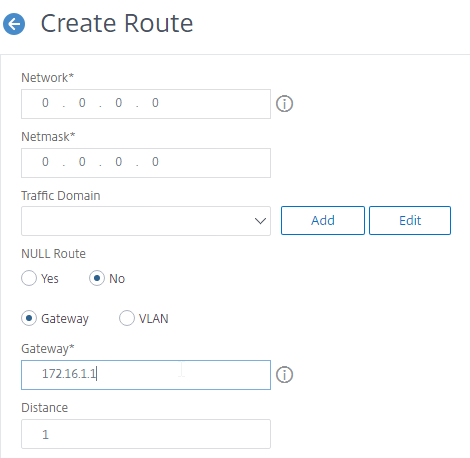
add route 0.0.0.0 0.0.0.0 172.16.1.1
- On the right, delete the 0.0.0.0 route. Don’t do this unless the Citrix ADC has a route, PBR, or MBF to the IP address of the machine you are running the browser on.
DNS Servers
- To configure DNS servers, expand Traffic Management, expand DNS, and click Name Servers.
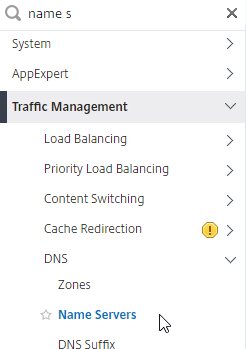
- On the right, click Add.
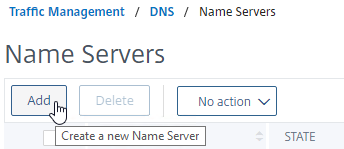
- Enter the IP address of a DNS server, and click Create.
- Note: The Citrix ADC must be able ping each of the DNS servers, or they will not be marked as UP. The ping originates from the SNIP.
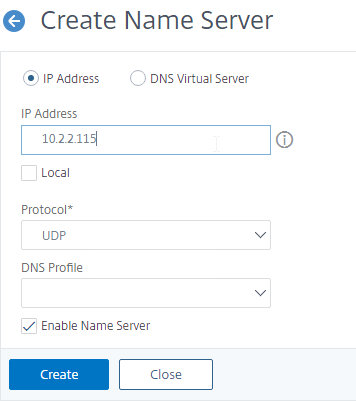
add dns nameServer 10.2.2.11
- Citrix ADC includes DNS Security Options, which are useful if you use this Citrix ADC to provide DNS services to clients (e.g. DNS Proxy/Load Balancing, GSLB, etc.). You can configure them at Security > DNS Security.
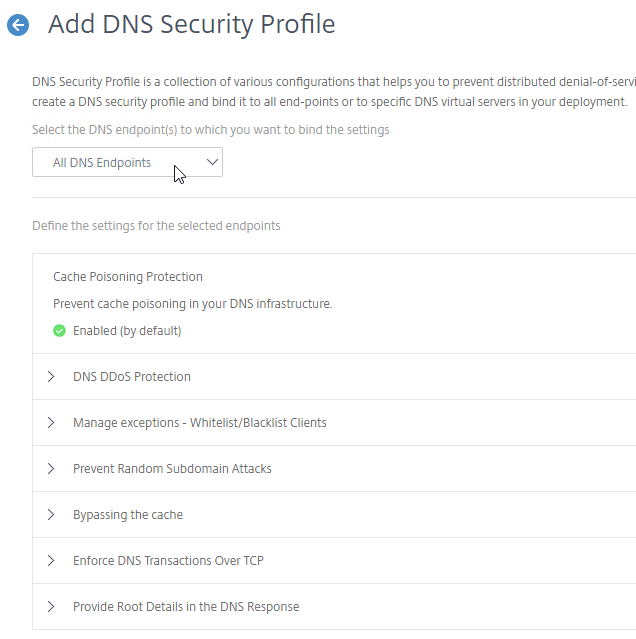
- Additional DNS Security Options are detailed at DNS security options at Citrix Docs.
NTP Servers
- On the left, expand System, and click NTP Servers.
- On the right, click Add.
- Enter the IP Address of your NTP Server (or pool.ntp.org), and click Create.
add ntp server pool.ntp.org - On the right, open the Action menu, and click NTP Synchronization.
- Select ENABLED, and click OK. This starts the NTP daemon in BSD to perform the NTP sync.
enable ntp sync - You can click the System node to view the System Time.
- If you need to manually set the time:
- SSH (Putty) to the Citrix ADC appliances.
- Run shell to access BSD.
- Run date to manually set the time. Run date –help to see the syntax.
- Ntpdate –u pool.ntp.org will cause an immediate NTP time update. You’ll need to disable NTP Sync before you can run this command.
SYSLOG Server
Citrix CTX120609 NetScaler Log Rotation and Configuration Using Newsyslog
The Citrix ADC will, by default, store a few syslogs on the local appliance. You can create a syslog policy to also send the syslog entries to an external server, like Citrix Application Delivery Management (ADM).
- On the left, expand System, expand Auditing, and click Syslog.
- On the right, switch to the Servers tab, and click Add.
- Enter a name for the Syslog server.
- You can change Server Type to Server Domain Name, and enter a FQDN.
- Enter the IP Address or FQDN of the SYSLOG server, and 514 as the port.
- Configure the Log Levels you’d like to send to it by clicking CUSTOM – typically select everything except DEBUG.
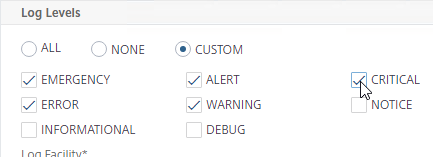
- Select your desired Time Zone and Date Format.
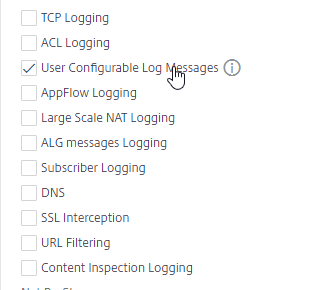
- You can optionally enable other logging features. User Configurable Log Messages lets you use Responder policies to generate log entries.
- Then click Create.

add audit syslogAction MySyslogServer 10.2.2.12 -logLevel EMERGENCY ALERT CRITICAL ERROR WARNING -timeZone LOCAL_TIME -userDefinedAuditlog YES add audit syslogAction MySyslogServer syslog.corp.local -logLevel EMERGENCY ALERT CRITICAL ERROR WARNING -timeZone LOCAL_TIME -userDefinedAuditlog YES
- On the right, switch to the Policies tab, and then click Add.
- Give the policy a descriptive name,
- Change the Expression Type selection to Advanced Policy.
- Select the previously created Syslog server.
- And then click Create.
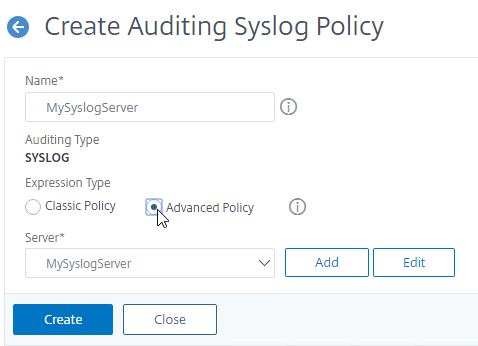
add audit syslogPolicy MySyslogServer true MySyslogServer
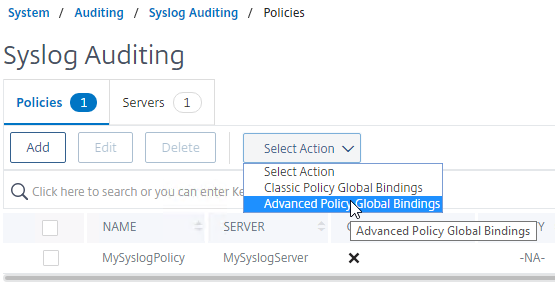
- While still on the Policies tab, open the Actions menu, and click Classic Policy Global Bindings or Advanced Policy Global Bindings, depending on which one you chose when creating the Syslog policy.
- Click Add Binding.
- Click where it says Click to select.
- Click the radio button next to the Syslog policy you want to bind, and then click the blue Select button at the top of the page.
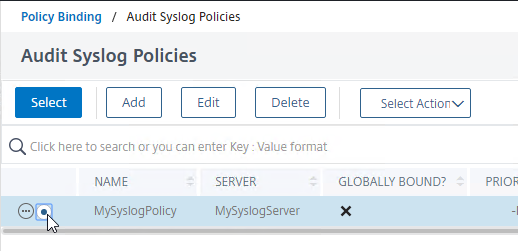
- Change the Priority to 100 or similar.
- If you don’t select anything in Global Bind Type, then it defaults to SYSTEM_GLOBAL.
- Click Bind.
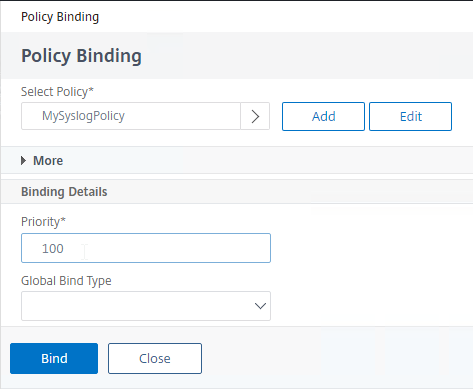
- Click Done.
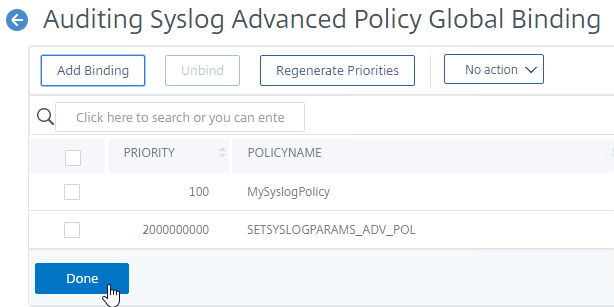
bind audit syslogGlobal -policyName MySyslogServer -priority 100 bind system global MySyslogServer -priority 100
- Click Add Binding.
SNMP – MIB, Traps, and Alarms
- On the left, expand System, and click SNMP.
- On the right, click Change SNMP MIB.
- Change the fields as desired. Your SNMP tool (e.g. Citrix Application Delivery Management (ADM)) will read this information. Click OK.
- This configuration needs to be repeated on the other node.
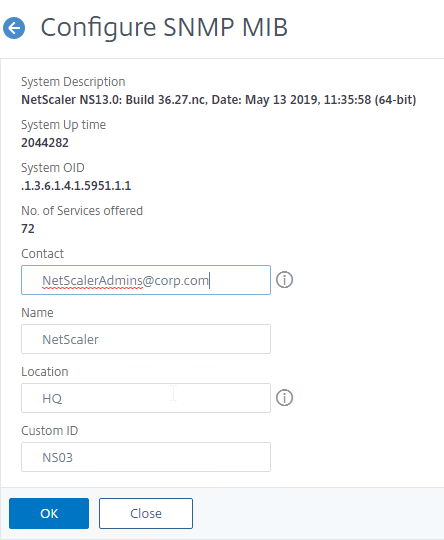
set snmp mib -contact NSAdmins@corp.com -name ns02 -location Corp
- Expand System, expand SNMP, and click Community.
- On the right, click Add.

- Specify a community string, and the Permission, and click Create.
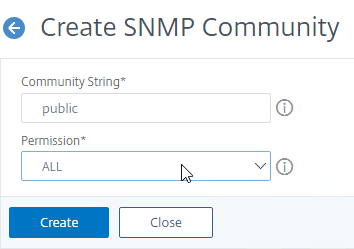
add snmp community public GET
- On the right, click Add.
- On the left, under SNMP, click Traps.
- On the right, click Add.
- Specify a trap destination. The fields will vary for V2 vs V3. Click Create. You’ll have to add the Trap Destinations twice so you can select both Generic and Specific.
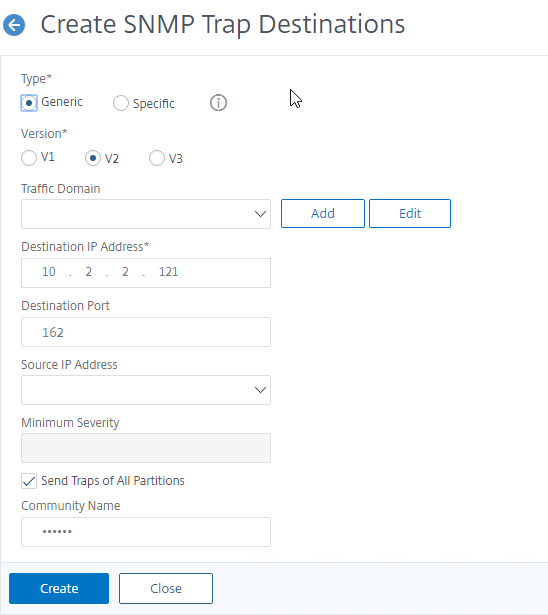
add snmp trap generic 10.2.2.12 -communityName public add snmp trap specific 10.2.2.12 -communityName public
- On the right, click Add.
- On the left, under SNMP, click Managers.
- On the right, click Add.
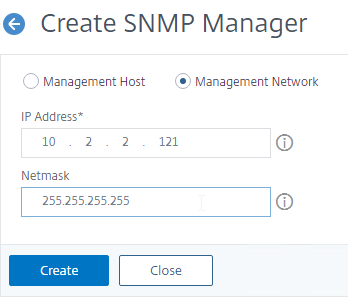
- Change the selection to Management Network.
- Specify the IP of the Management Host, and click Create.
add snmp manager 10.2.2.12
- On the right, click Add.
- The Alarms node allows you to enable SNMP Alarms and configure thresholds.
- You can Edit an alarm to set thresholds. For example, CPU-USAGE can be set to 90% alarm, and 50% normal, with a Critical severity.
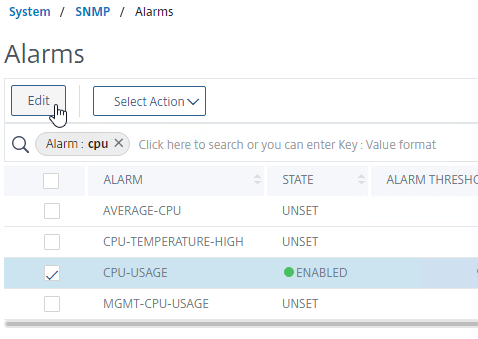
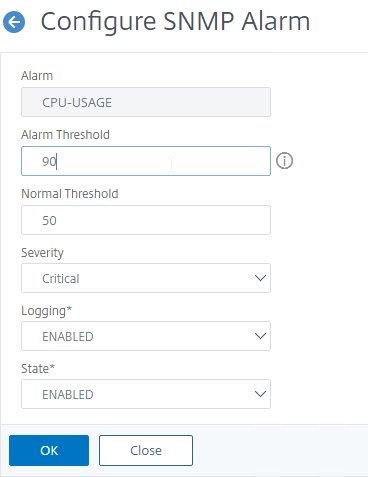
set snmp alarm CPU-USAGE -thresholdValue 90 -normalValue 50 -severity Critical
- You can also configure the MEMORY alarm.
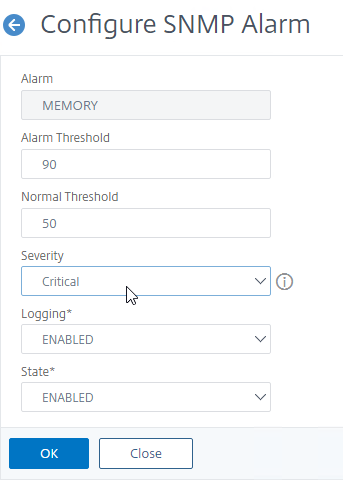
set snmp alarm MEMORY -thresholdValue 90 -normalValue 50 -severity Critical
- You can Edit an alarm to set thresholds. For example, CPU-USAGE can be set to 90% alarm, and 50% normal, with a Critical severity.
From http://www.slideshare.net/masonke/net-scaler-tcpperformancetuningintheaolnetwork: In addition to the usual OIDs, we have found these very useful to warn of potential problems.
- ifTotXoffSent – .1.3.6.1.4.1.5951.4.1.1.54.1.43
- ifnicTxStalls – .1.3.6.1.4.1.5951.4.1.1.54.1.45
- ifErrRxNoBuffs – .1.3.6.1.4.1.5951.4.1.1.54.1.30
- ifErrTxNoNSB – .1.3.6.1.4.1.5951.4.1.1.54.1.31
Call Home
Citrix Blog Post – Protect Your NetScaler From Disaster With Call Home!: If you have a physical Citrix ADC (MPX or SDX) with an active support contract, you may optionally enable Call Home to automatically notify Citrix Technical Support of hardware and software failures.
Call Home at Citrix Docs has information on how it work.
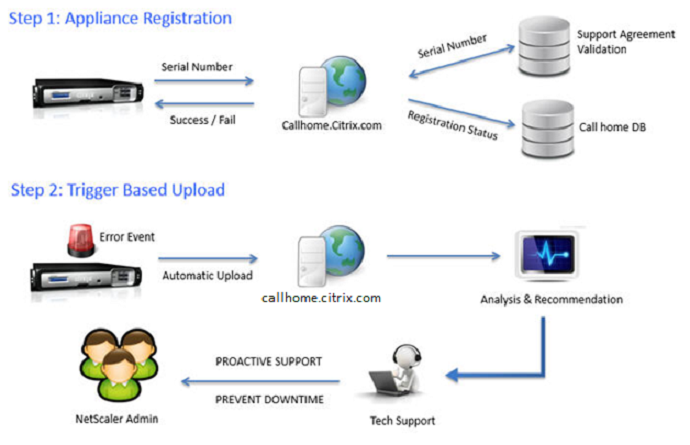
From the Citrix ADC release notes: Call Home is now enhanced to send Citrix ADC usage metrics to Citrix Insight Services (CIS) periodically. Citrix collects the data to understand how the appliance works and how to improve the product. By default, Call Home sends the metrics once in every 7 days. For more information, see Call Home at Citrix Docs.
To enable Call Home:
- On the left, expand System, and click Diagnostics.
- On the right, in the left column, in the Technical Support Tools section, click Call Home.
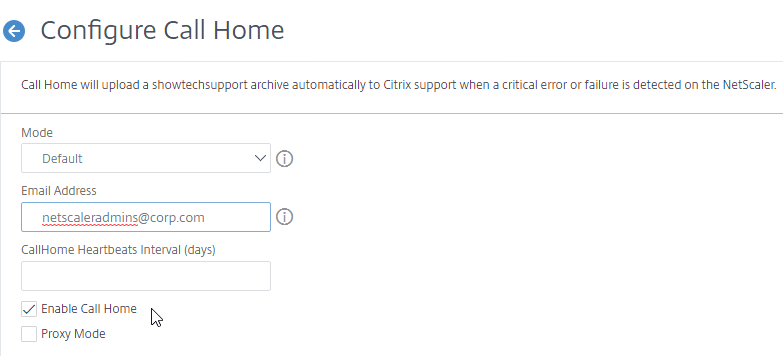
- Check the box next to Enable Call Home.
- Optionally enter an email address to receive notifications from Citrix Technical Support. Click OK.
- If you go back into Call Home, it should indicate if registration succeeded or failed. Successful registration requires an active support contract.
Change nsroot Password
- In ADC 13.0 build 67 and newer, you’ll be forced to change the default nsroot password.

- If you want to force strong passwords for local accounts, go to System > Settings, and on the right, click Change Global System Settings
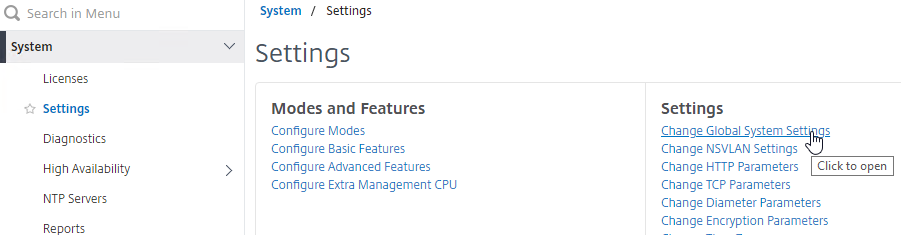
- Scroll down to the Password section.
- You can change Strong Password to Enable Local, and also specify a Min Password Length. Click OK.
- Expand System, expand User Administration, and click Users.
- On the right, right-click nsroot, and click Change Password.
- Specify a new password and click OK.
set system user nsroot Passw0rd
TCP, HTTP, SSL, and Security Settings
Citrix Docs Introduction to best practices for Citrix ADC MPX, VPX, and SDX security
Best practice settings:
- On the left, expand System, and click Settings.
- On the right, in the right column, click Change TCP parameters.
- Check the box for Window scaling (near the top) and set the Factor to 8.
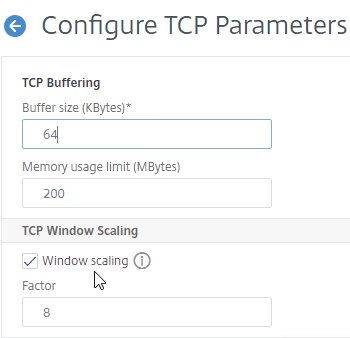
- Scroll down and check the box for Selective Acknowledgement.
- Nagle’s algorithm should not be checked.
- Click OK.
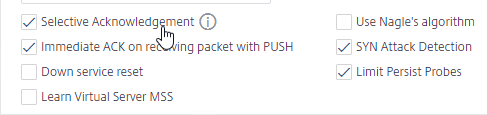
set ns tcpParam -WS ENABLED -SACK ENABLED
- Check the box for Window scaling (near the top) and set the Factor to 8.
- On the right, click Change HTTP parameters.
- Under Cookie, change the selection to Version1. This causes Citrix ADC to set Cookie expiration to a relative time instead of an absolute time.
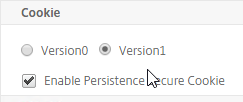
set ns param -cookieversion 1
- Check the box next to Drop invalid HTTP requests. Note: this might break some web sites.
- Scroll down, and click OK.
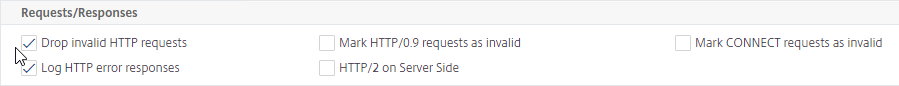
set ns httpParam -dropInvalReqs ON
- Under Cookie, change the selection to Version1. This causes Citrix ADC to set Cookie expiration to a relative time instead of an absolute time.
- From Citrix CTX232321 Recommended TCP Profile Settings for Full Tunnel VPN/ICAProxy from NetScaler Gateway 11.1 Onwards:
- Expand System, and click Profiles.
- On the right, on the tab named TCP Profiles, edit the nstcp_default_profile.
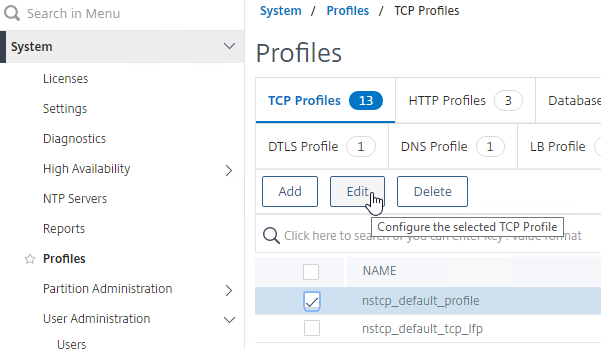
- Enable Window Scaling with a factor of 8.
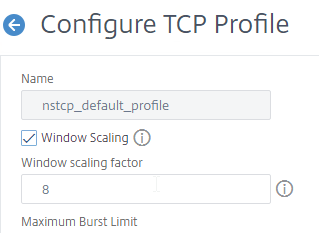
- Set Minimum RTO (in millisec) = 600.
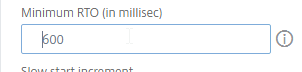
- Set TCP Buffer Size (bytes) = 600000
- Set TCP Send Buffer Size (bytes) = 600000
- Change TCP Flavor = BIC.
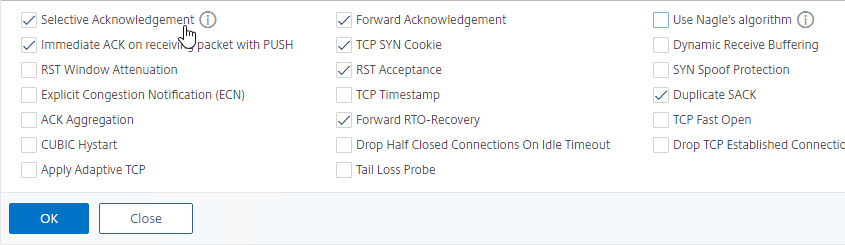
- Enable Selective Acknowledgement. Don’t enable Nagle’s algorithm.
- Click OK when done.
- You can run the following command to see statistics on the dropped packets:
nsconmsg -g http_err_noreuse_ -d stats
- See CTX209398 Addressing false positives from CBC and MAC vulnerability scans of SSHD to harden SSHD by editing /nsconfig/sshd_config with the following. Then run
kill -HUP `cat /var/run/sshd.pid`to restart SSHD.Ciphers aes128-ctr,aes192-ctr,aes256-ctr MACs hmac-sha1,hmac-ripemd160
Citrix Knowledgebase articles:
- CTX228148 How to Lock Down the NetScaler Management Interfaces with ACLs
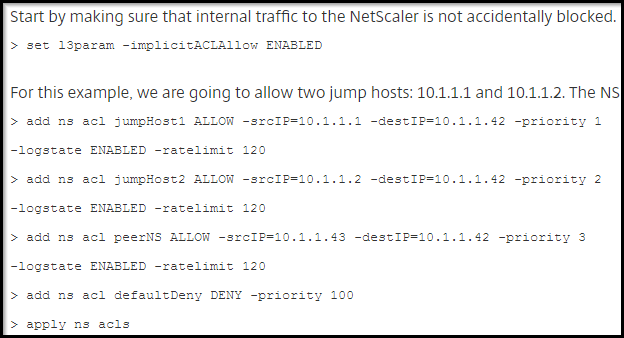
- Also see CTP George Spiers How to secure management access to NetScaler and create unique certificates in a highly available setup
- CTX109011 How to Secure SSH Access to the NetScaler Appliance with Public Key Authentication
- CTX127917 How to Configuring the Rate Limiting Feature of a NetScaler Appliance to Mitigate a DDoS Attack
- CTX131681 How to Use NetScaler Appliance to Avoid Layer 7 DDoS Attacks
- CTX209398 Addressing false positives from CBC and MAC vulnerability scans of SSHD
The following security configurations are detailed by Jason Samuel at Mitigating DDoS and brute force attacks against a Citrix Netscaler Access Gateway:
- Maximum logon attempts on Citrix Gateway Virtual Server
- Rate Limiting for IP.SRC and HTTP.REQ.URL.
- nstcp_default_XA_XD_profile TCP profile on the Citrix Gateway Virtual Server.
- Syslog logging
- External website monitoring
- Obfuscate the Server header in the HTTP response
- Disable management access on SNIPs
- Change nsroot strong password, use LDAP authentication, audit local accounts
- Don’t enable Enhanced Authentication Feedback
- SSL – disable SSLv3, deny SSL renegotiation, enable ECDHE ciphers, disable RC4 ciphers.
- 2-factor authentication
- Citrix Application Delivery Management (ADM)
- Review IPS/IDS & Firewall logs
Management Authentication – LDAP
Load balancing of LDAP servers is strongly recommended. If you bind multiple LDAP servers instead of load balancing them, Citrix ADC will try each of the LDAP servers, and for incorrect passwords, will lock out the user sooner than expected. But if you instead load balance your LDAP servers, the authentication attempt will only be sent to one of them.
- Expand System, expand Authentication, expand Basic Policies, and then click LDAP.
- On the right, switch to the Servers tab. Then click Add.
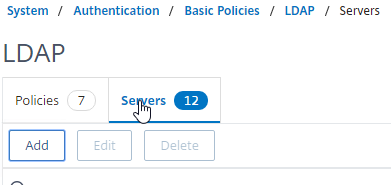
- Enter LDAPS-Corp-Mgmt or similar as the name. If you have multiple domains, you’ll need a separate LDAP Server per domain so make sure you include the domain name. Also, the LDAP policy used for management authentication will be different than the LDAP policy used for Citrix Gateway.
- Change the selection to Server IP. Enter the VIP of the Citrix ADC load balancing vServer for LDAP.
- Change the Security Type to SSL.
- Enter 636 as the Port. Scroll down.
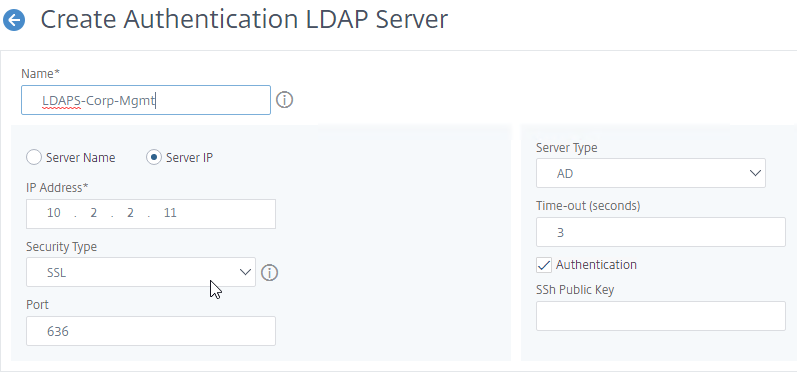
- In the Connection Settings section, in the Base DN field, enter your Active Directory DNS domain name in LDAP format.
- In the Administrator Bind DN field, enter the credentials of the LDAP bind account in userPrincipalName format.
- Enter the Administrator Password (bind account password). Click Test LDAP Reachability. Scroll down.
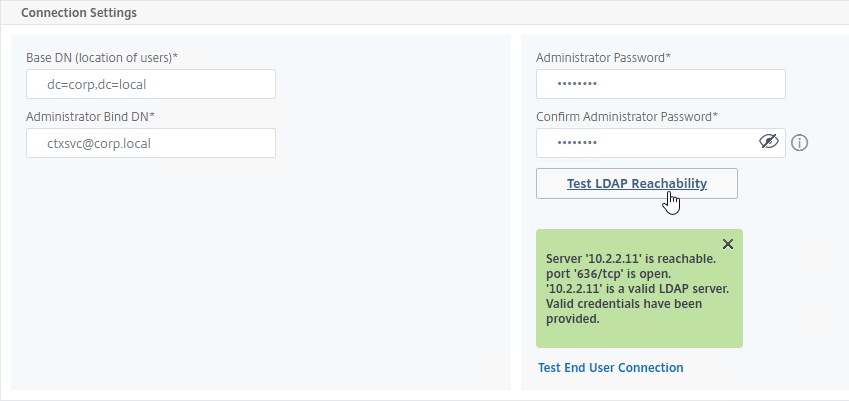
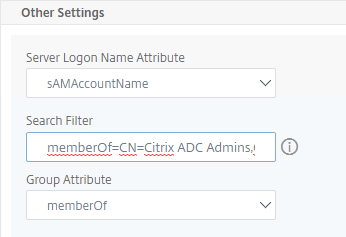
- In the Other Settings section, use the drop-down next to Server Logon Name Attribute, Group Attribute, and Sub Attribute Name to select the default fields for Active Directory.
- On the right, check the box next to Allow Password Change.
- It is best to restrict access to only members of a specific group. In the Search Filter field, enter memberOf=<GroupDN>. See the example below:
memberOf=CN=Citrix ADC Administrators,OU=Citrix,DC=corp,DC=localYou can add :1.2.840.113556.1.4.1941: to the query so it searches through nested groups. Without this, users will need to be direct members of the filtered group.memberOf:1.2.840.113556.1.4.1941:=CN=Citrix ADC Administrators,OU=Citrix,DC=corp,DC=local
 Citrix 132802 How to Use the ldapsearch Utility on the NetScaler Gateway Enterprise Edition Appliance to Validate a Search FilterAn easy way to get the full distinguished name of the group is through Active Directory Users & Computers. Make sure Advanced Features is enabled in the View menu. Double-click the group object. Switch to the Attribute Editor tab. Find Distinguished Name and copy it.Scroll down to distinguishedName, double-click it, and then copy it to the clipboard.
Citrix 132802 How to Use the ldapsearch Utility on the NetScaler Gateway Enterprise Edition Appliance to Validate a Search FilterAn easy way to get the full distinguished name of the group is through Active Directory Users & Computers. Make sure Advanced Features is enabled in the View menu. Double-click the group object. Switch to the Attribute Editor tab. Find Distinguished Name and copy it.Scroll down to distinguishedName, double-click it, and then copy it to the clipboard.
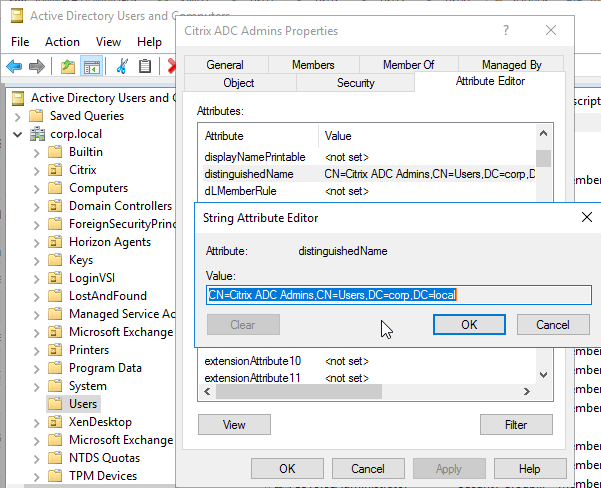 Back on the Citrix ADC, in the Search Filter field, type in memberOf=, and then paste the Distinguished Name right after the equals sign. Don’t worry about spaces.
Back on the Citrix ADC, in the Search Filter field, type in memberOf=, and then paste the Distinguished Name right after the equals sign. Don’t worry about spaces.
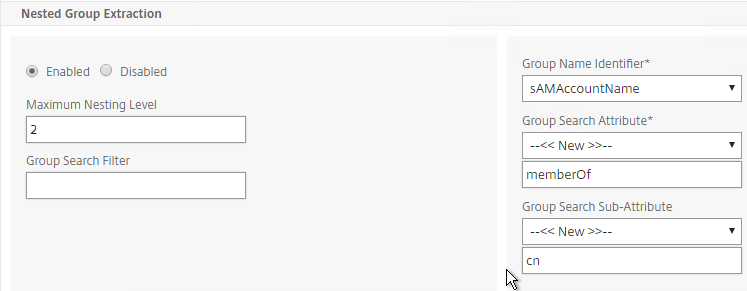
- Scroll down and click More to expand it.
- For Nested Group Extraction, if desired, change the selection to Enabled.
- Set the Group Name Identifier to samAccountName.
- Set Group Search Attribute to –<< New >>–, and enter memberOf.
- Set Group Search Sub-Attribute to –<< New >>–, and enter CN.
- Example of LDAP Nested Group Search Filter Syntax
- Scroll down, and click Create.

add authentication ldapAction Corp-Mgmt -serverIP 10.2.2.210 -serverPort 636 -ldapBase "dc=corp,dc=local" -ldapBindDn "corp\\ctxsvc" -ldapBindDnPassword Passw0rd -ldapLoginName samaccountname -searchFilter "memberOf=CN=Citrix ADC Admins,CN=Users,DC=corp,DC=local" -groupAttrName memberOf -subAttributeName CN -secType SSL -passwdChange ENABLED
- On the left, go to System > Authentication > Advanced Policies > Policy.
- On the right, click Add.
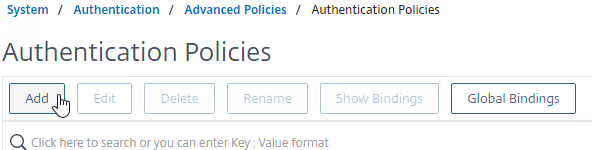
- Enter the name LDAPS-Corp-Mgmt or similar.
- Change the Action Type drop-down to LDAP.
- Select the previously created LDAPS-Corp-Mgmt server.
- On the bottom, in the Expression area, type in true.
- Click Create.
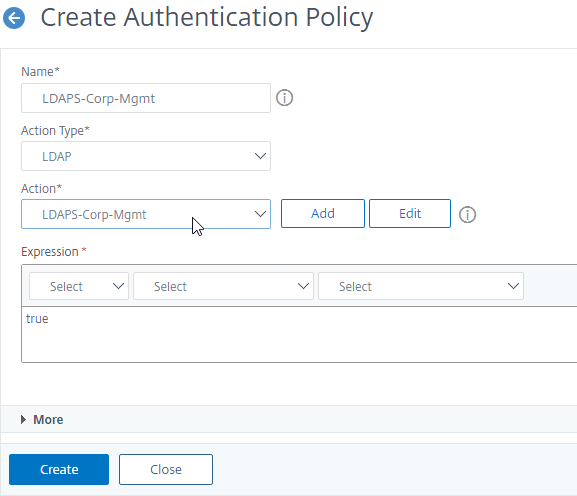
add authentication Policy LDAPS-Corp-Mgmt -rule true -action LDAPS-Corp-Mgmt
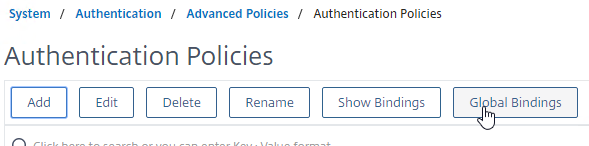
- Click Global Bindings in the right pane.
- Click where it says Click to select.
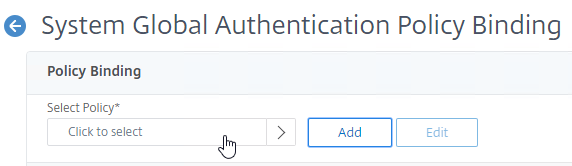
- Click the radio button next to the newly created LDAP policy, and then click the blue Select button at the top of the page.
- Click Bind.
- Click Done.
bind system global LDAPS-Corp-Mgmt -priority 100 -gotoPriorityExpression NEXT
- Click where it says Click to select.
- Under System, expand User Administration, and click Groups.
- On the right, click Add.
- In the Group Name field, enter the case sensitive name of the Active Directory group containing the Citrix ADC administrators.
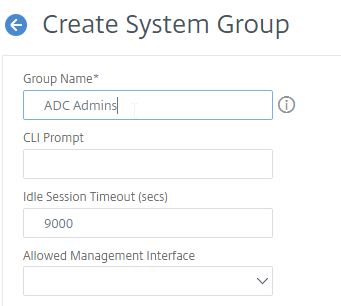
- ADC 13.0 build 41 and newer lets you restrict a group to the CLI only. Note that GUI access requires API permissions.
- ADC 13.0 build 41 and newer lets you restrict a group to the CLI only. Note that GUI access requires API permissions.
- In the Command Policies section, click Bind.
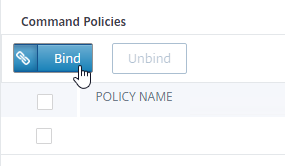
- Select the superuser policy, and click Insert.
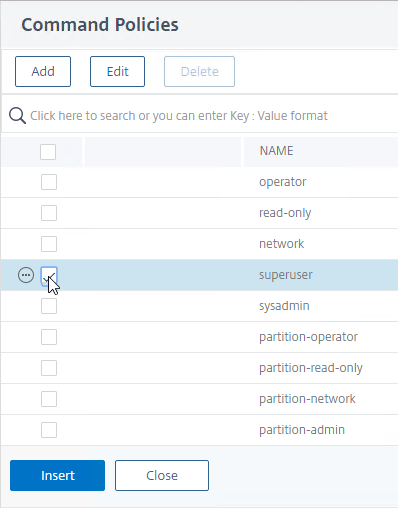
- Scroll down, and click Create.

add system group "Citrix ADC Admins" -timeout 900 bind system group "Citrix ADC Admins" -policyName superuser 100
- On the right, click Add.
- To prevent somebody from creating an nsroot account in LDAP (Active Directory) and then using that external nsroot account to login to ADC, disable external authentication on the local nsroot account.
- On the left, go to System > User Administration > Users.
- On the right, edit the nsroot user.
- At the top of the page, in the System User section, click the pencil icon.
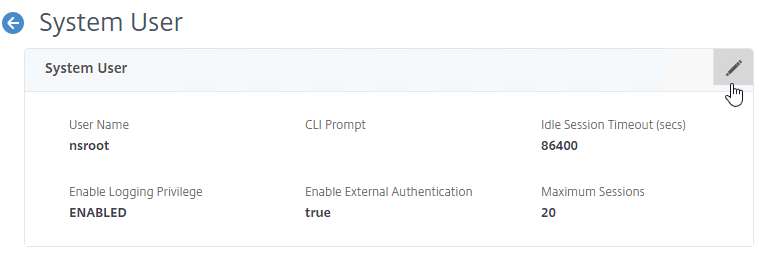
- Uncheck the box next to Enable External Authentication and then click Continue.
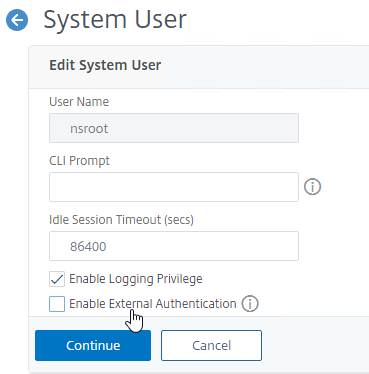
- Click Save and then click Done.
- On the left, go to System > User Administration > Users.
- If you logout:
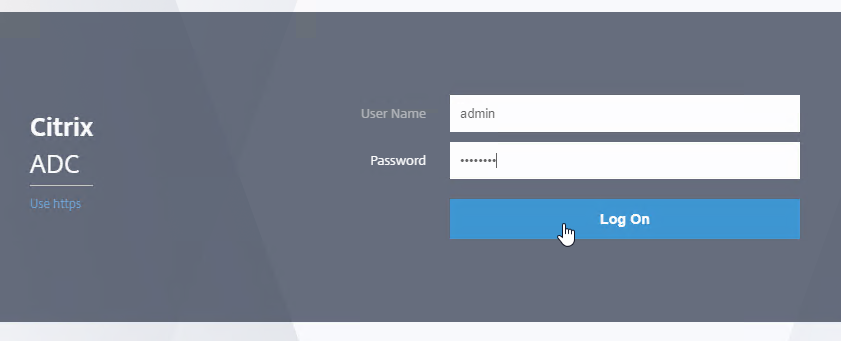
- You should be able to login to Citrix ADC using an Active Directory account.
Management Authentication – Two Factor
Citrix ADC supports two factor authentication for management access. The technology is based on nFactor but works in all editions of ADC (no licensing restrictions). Here’s a summary of the configuration steps with more detail coming later:
- The first authentication factor must be an Advanced Authentication Policy that is bound globally. Classic Authentication Policies will not work.
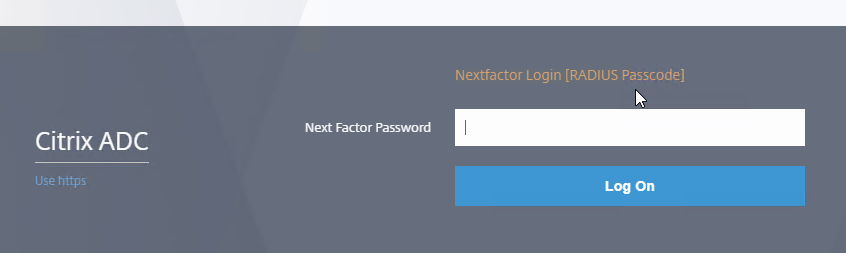
- Create a Login Schema to ask for the second factor password (i.e. passcode).
- This Login Schema is for second factor only and has no effect on the first factor. The second factor Login Schema should only ask for a single password prompt. It doesn’t appear to be possible to ask for both factors using the same Login Schema.
- Login Schema for the second factor does not use the normal nFactor language files and you instead must hard code the password prompt label for the second factor logon field directly in the Login Schema .xml file.
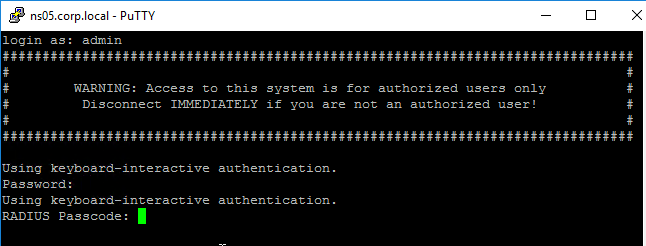
- Create an Advanced Authentication Server and Policy for the second factor (e.g. RADIUS).
- Create an Authentication Policy Label with Feature Type set to RBA_REQ. This is not the default so make sure you change the Feature Type drop-down field.
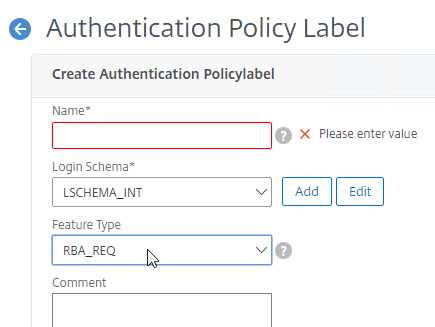
- When creating the Policy Label, select the Login Schema for the second factor.
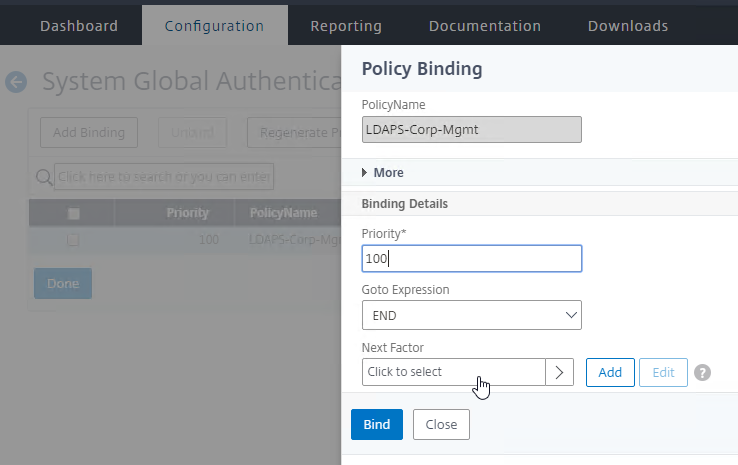
- Bind the second factor Advanced Authentication Policy to the Policy Label.
- Go to Global Bindings for Authentication, edit the existing authentication binding, click Next Factor, and select your new Policy Label. That’s it.
Here are detailed configuration instructions for adding a second authentication factor to the management logon page.
- Login Schema XML File:
- Point WinSCP to your ADC appliance.
- Navigate to /nsconfig/loginschema/LoginSchema and download the SingleAuth.xml file.
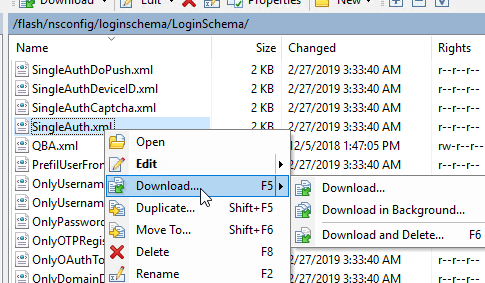
- Rename the file to MgmtNextFactor.xml or something like that.
- Edit the file.
- Look for the <Requirement> element with ID of passwd. Then look for the Label and set the Text field to whatever you want displayed on the second password page. Save the file when done.
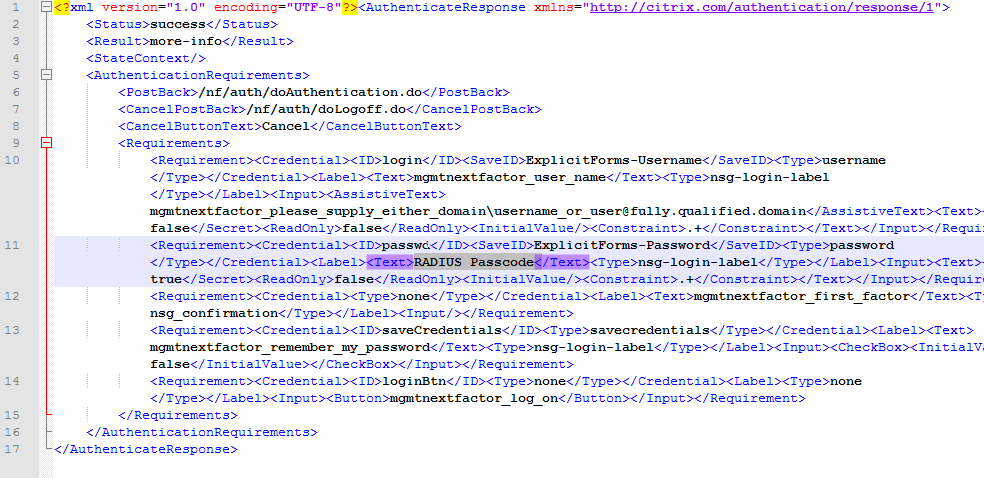
- The Label Text you enter will be shown on the second factor logon page.
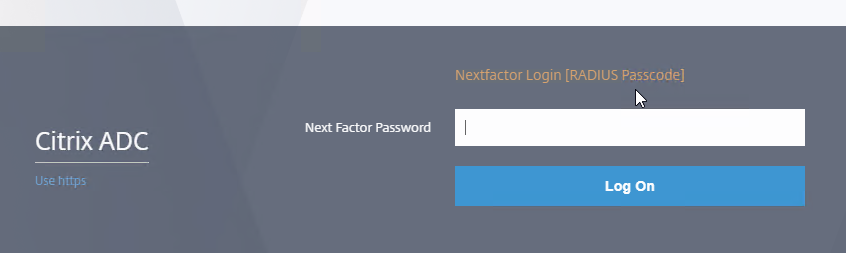
- In WinSCP, change the directory to /nsconfig/loginschema, which is one directory up from where you downloaded the file.
- Upload your modified file.
- RADIUS Authentication Server:
- Follow the link for instructions to create a RADIUS Server. Only create the Server object. The Policy object will be created later when creating the Authentication Policy Label.
add authentication radiusAction RADIUSMgmt -serverName 10.2.2.42 -serverPort 1812 -radKey b746744 -encrypted -encryptmethod ENCMTHD_3
- Follow the link for instructions to create a RADIUS Server. Only create the Server object. The Policy object will be created later when creating the Authentication Policy Label.
- On the left, go to System > Authentication > Advanced Policies > Policy Label.
- On the right, click Add.
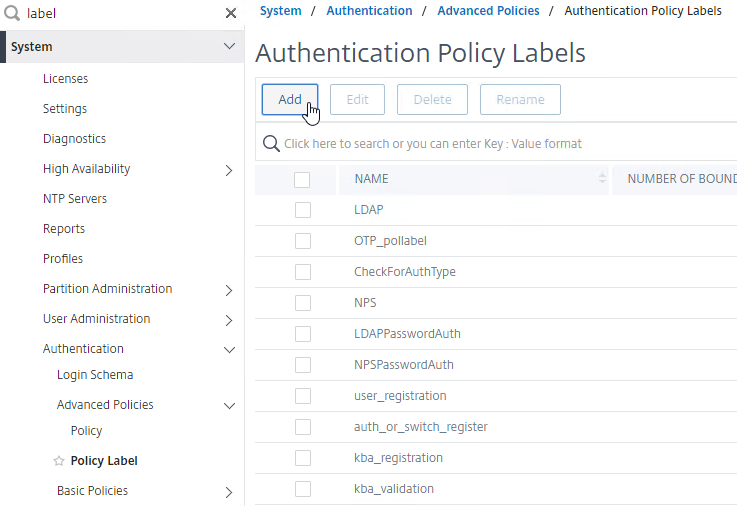
- Name the Policy Label MgmtNextFactor or similar.
- In the Login Schema field, click Add.
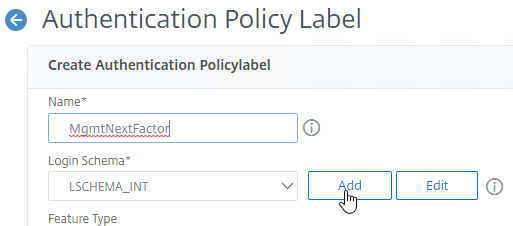
- Name the Login Schema MgmtNextFactor or similar.
- In the Authentication Schema field, click the pencil icon.
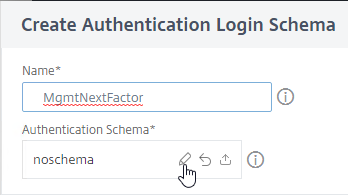
- On the left, select the Login Schema .xml file you uploaded earlier.
- On the top right, click the blue Select button. Do NOT click Create on the bottom left until you’ve clicked this blue Select button.
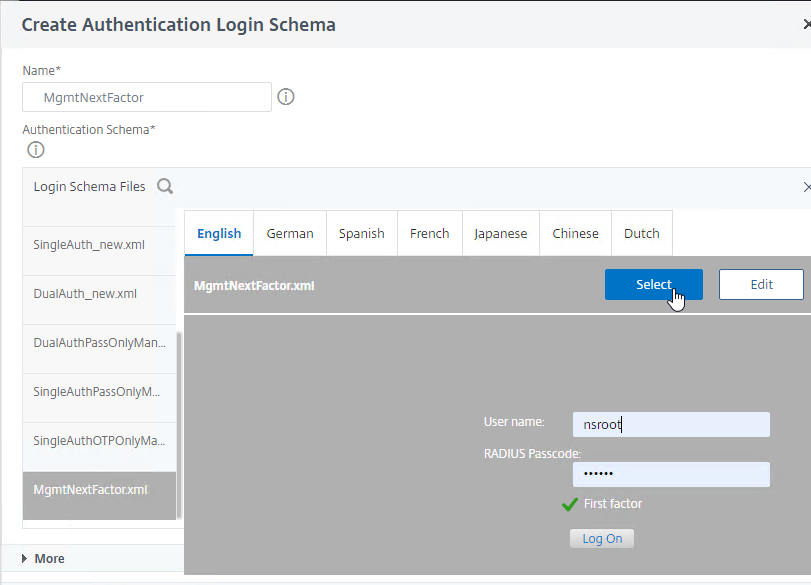
- The window collapses showing you the Login Schema file that you selected. Now you can click Create.
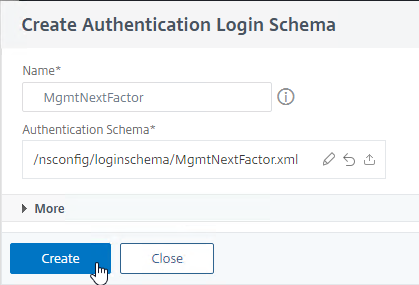
add authentication loginSchema MgmtNextFactor -authenticationSchema "/nsconfig/loginschema/MgmtNextFactor.xml"
- Back in the Authentication Policy Label screen, notice that you can edit the Login Schema object from here.
- Change the Feature Type drop-down to RBA_REQ. If you don’t do this, then you won’t be able to bind this later.
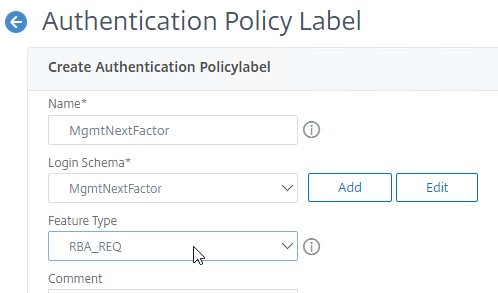
- Click Continue.
add authentication policylabel MgmtNextFactor -type RBA_REQ -loginSchema MgmtNextFactor
- In the Policy Label’s Policy Binding field, click Add.
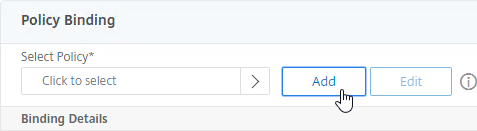
- Name the Authentication Policy RADIUSMgmt or similar.
- Change the Action Type drop-down to RADIUS.
- Select the RADIUS server that you created earlier. Or you can Add one from here.
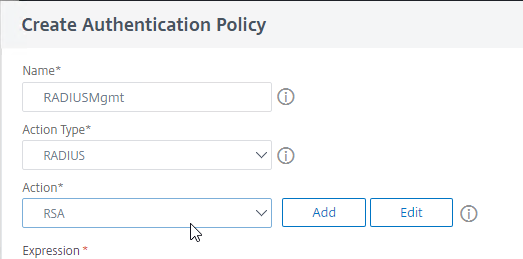
- In the Expression box, enter the word true and then click Create.
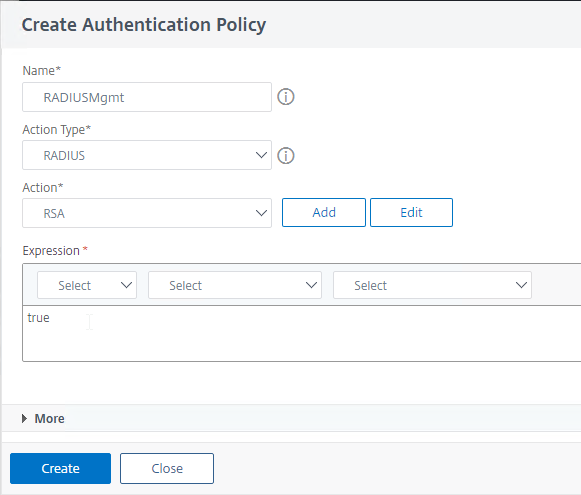
add authentication Policy RADIUSMgmt -rule true -action RADIUSMgmt
- Back in the Policy Label Policy Binding screen, click Bind.
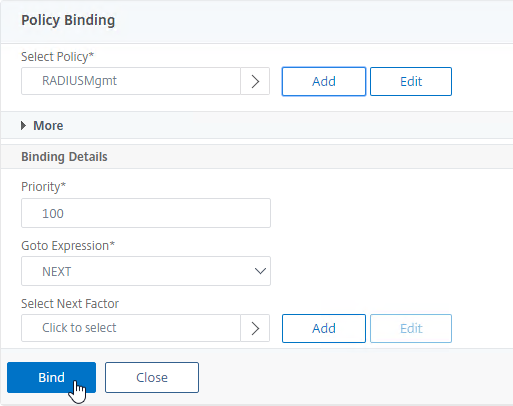
bind authentication policylabel MgmtNextFactor -policyName RADIUSMgmt -priority 100 -gotoPriorityExpression NEXT
- The Authentication Policy Label configuration is complete so click Done.
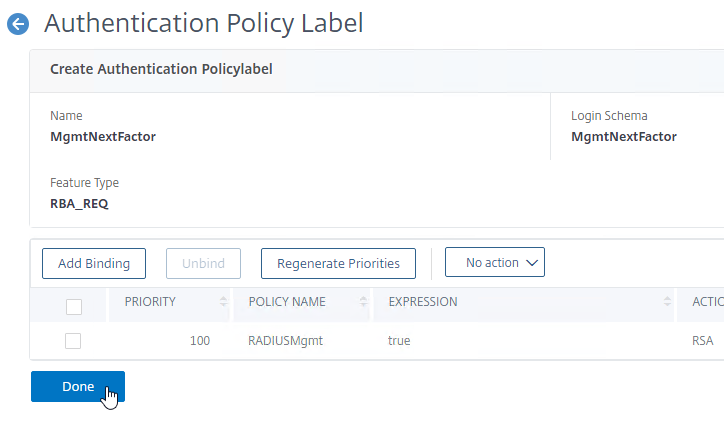
- On the left, go to System > Authentication > Advanced Policies > Policy.
- On the right, click the Global Bindings button.
- You should already have an Advanced Authentication Policy bound globally.
add authentication ldapAction LDAPS-Corp-Mgmt -serverIP 10.2.2.11 -serverPort 636 -ldapBase "dc=corp,dc=local" -ldapBindDn ctxsvc@corp.local -ldapBindDnPassword 5054fc33f673bf4c5c6 -encrypted -encryptmethod ENCMTHD_3 -ldapLoginName sAMAccountName -groupAttrName memberOf -subAttributeName cn -secType SSL -passwdChange ENABLED add authentication Policy LDAPS-Corp-Mgmt -rule true -action LDAPS-Corp-Mgmt bind system global LDAPS-Corp-Mgmt -priority 100 -gotoPriorityExpression END
- Right-click your existing global binding and click Edit Binding.
- In the Next Factor field, click where it says Click to select.
- Click the small circle next to your Management Next Factor Policy Label and then click the blue Select button at the top of the page.
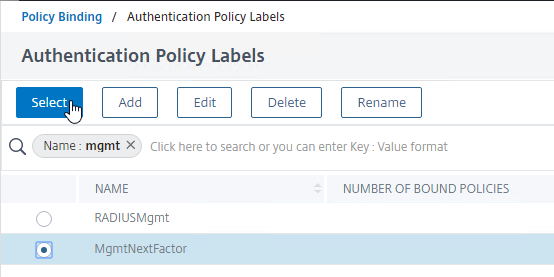
- Back in the Policy Binding screen, click Bind.
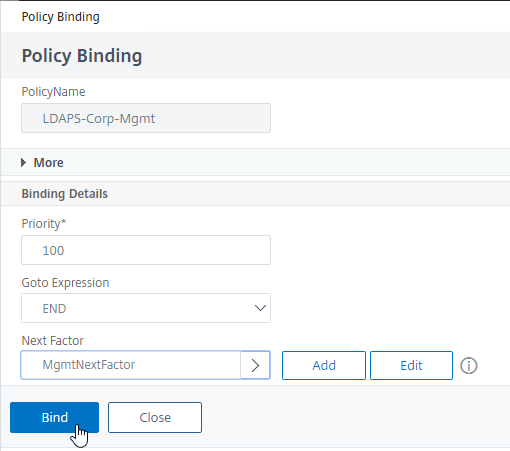
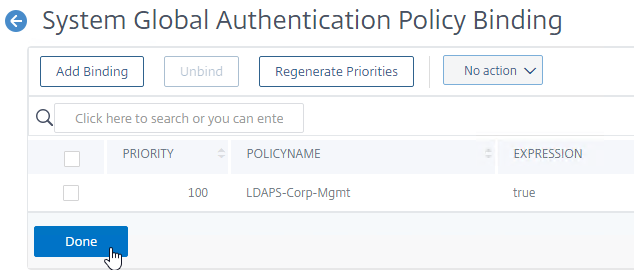
bind system global LDAPS-Corp-Mgmt -priority 100 -nextFactor RADIUSMgmt -gotoPriorityExpression END
- Click Done to close the Global Authentication Policy Binding screen.
CLI Prompt
- When you connect to the Citrix ADC CLI prompt, by default, the prompt is just a
>.

- You can run
set cli prompt %u@%hto make it the same as a UNIX prompt. See Citrix Docs for the cli prompt syntax.
Backup and Restore
Citrix Application Delivery Management (ADM) can automatically backup your instances. Or you can do it manually:
- Save the configuration.
- On the left, expand System, and click Backup and Restore.
- On the right, click Backup/Import.
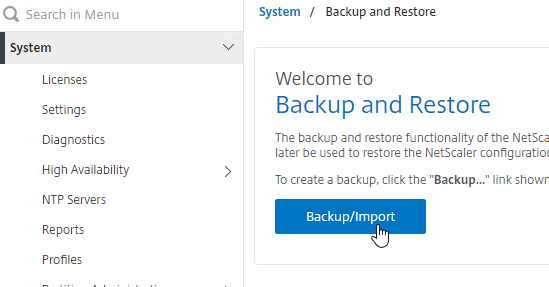
- Give the backup file a name.
- For Level, select Full, and click Backup.
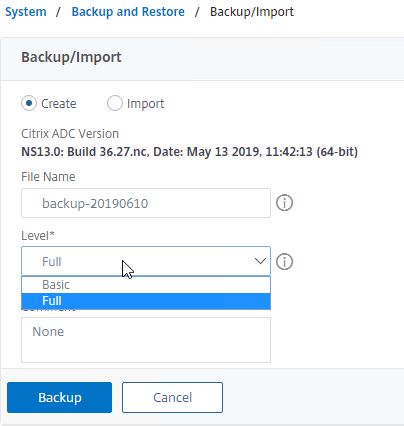
- Once the backup is complete, you can download the file.
For a PowerShell script, see John Billekens Create offline backups of the NetScaler config
To restore:
- If you want to restore the system, and if the backup file is not currently on the appliance, click the Backup/Import button.
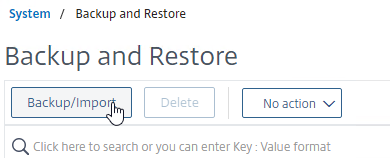
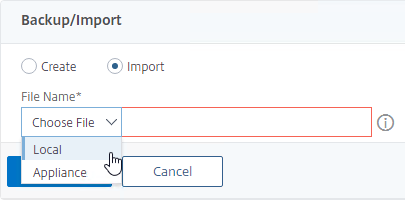
- Change the selection to Import.
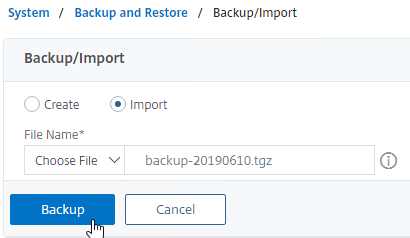
- Browse Local to the previously downloaded backup file.
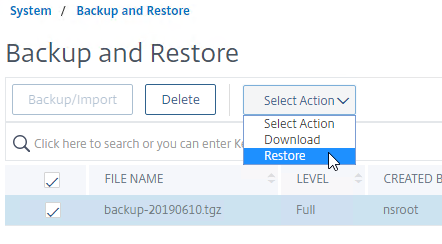
- Then click Backup. This uploads the file to the appliance and adds it to the list of backup files.
- Now you can select the backup, and click Restore.
Hi,
We currently run the latest Citrix ADC 13.1 on-prem in a HA Pair configuration and currently have both of them are running using fixed 200Mbp bandwidth licences on each one.
Our fixed bandwidth licences are due to expire in the near future.
What are our options moving forward? Do we need to upgrade both HA nodes to version 14.1, do we need to deploy Netscaler Console on-prem? If so what licences do we need to apply?
I am confused by the new licencing model, I see Flexed Licencing and Pooled Licencing mentioned but I not sure if we have to apply one or the other or both, also on our Citrix portal I can see we SW Instance license files and bandwidth licence files but I have have no ideal what to apply and how many to apply.
Can someone advise me on this please?
Is anyone able to advise me on this please?
I would talk to your rep who is going to know what you have and be able to give you a better idea of what you need. However, you need an instance license for the appliance itself, and then a bandwidth license for however much throughput you need. Also, flexed licensing is replacing pooled licenses. You can also look at the documentation starting here: https://docs.netscaler.com/en-us/netscaler-application-delivery-management-software/current-release/license-server/license-management On the left navigation menu, you will see more info about each type of license.
Thank you getting back to me. I will look into this.