Navigation
- Changelog
- Overview
- Monitor to verify that LDAP server is UP
- Server Objects
- Service Groups
- Virtual Server
- CLI Commands
💡 = Recently Updated
Changelog
- 2017 Dec 25 – updated entire article for 12.0 build 56. Monitor section has new build 56 instructions.
Overview
If you plan to use LDAP (Active Directory) for Citrix Gateway, or Citrix ADC management authentication, then load balance the Domain Controllers that are used for authentication. A single LDAP Policy/Server points to the load balanced VIP.
Premature lockout – An alternative to load balancing is to bind multiple LDAP Policies, with each Policy pointing to a single Domain Controller in the same domain. However, Citrix ADC will try each authentication policy until it finds one that works. If the user enters a wrong password, and if you have three authentication policies pointing to different Domain Controllers in the same domain, then three different failure attempts will be recorded, thus causing premature account lockout. Use Load Balancing to avoid this behavior.
LDAPS and certificates – This page details LDAPS, aka Secure LDAP. This protocol requires certificates to be installed on the Domain Controllers. When a user’s password expires, Active Directory does not allow password changes over clear text LDAP, so LDAPS must be used instead. Make sure you have certificates installed on your Domain Controllers. The easiest way to accomplish that is to deploy a Microsoft Certificate Authority in Enterprise Mode, which allows the Domain Controllers to request certificates automatically.
Monitor -An ldaps monitor can be used to verify that the Domain Controller is functional.
- The ldaps monitor will login as an account, perform an LDAP query, and look for a successful response. The ldaps monitor uses a service account to login. Make sure the service account’s password does not expire. Domain User permissions are sufficient.
- Since this monitor is a Perl script, it uses NSIP as the source IP. You can use RNAT to override this as described in Configure to source Citrix ADC FreeBSD data traffic from a SNIP address at Citrix Docs.
Multiple datacenters – If you have Domain Controllers in multiple datacenters, you can create multiple load balancing Virtual Servers, and cascade them so that the local Domain Controllers are used first, and if they’re not available, then the Virtual Server fails over to Domain Controllers in remote datacenters.
Load Balancing Protocol – The Load Balancing Virtual Server for LDAPS can be TCP protocol or SSL_TCP protocol:
- TCP – If the protocol is TCP, then SSL-encrypted LDAP traffic is not terminated on the Citrix ADC, and is simply forwarded to the LDAP servers. If your LDAP client (e.g. Linux machine) needs to verify the LDAP server certificate, then this Load Balancing configuration will not work, since each back-end LDAP server will have a different certificate.
- SSL_TCP – If your Load Balancing Virtual Server is protocol SSL_TCP, then a certificate must be installed on the Citrix ADC and bound to the Load Balancing Virtual Server. SSL is terminated at the Citrix ADC and re-encrypted before sending it to the destination Domain Controller. The primary benefit of Citrix ADC SSL termination is that your LDAP clients can verify the Virtual Server SSL certificate.
Source IP – When Citrix ADC uses a local (same appliance) load balanced Virtual Server for LDAPS authentication, the traffic is sourced from the Citrix ADC SNIP (Subnet IP). When Citrix ADC uses a direct connection to a Domain Controller without going through a local Load Balancing Virtual Server, or if Citrix ADC uses a remote (different appliance) Load Balancing VIP, then the traffic is sourced from the Citrix ADC NSIP (NetScaler IP). Adjust firewall rules accordingly.
LDAPS Monitor
Note: Perl (scriptable) monitor uses NSIP as the source IP. You can use RNAT to override this as described in Configure to source Citrix ADC FreeBSD data traffic from a SNIP address at Citrix Docs.
12.0 build 56 and newer
Instructions for creating the monitor changed in 12.0 build 56 and newer. If your build is older, skip to the older instructions.
- In the Citrix ADC Configuration Utility, expand Traffic Management, expand Load Balancing, and click Monitors.
- On the right, click Add.
- Name the monitor ldaps-Corp or similar. The ldaps monitor logs into Active Directory, performs an LDAP query, and looks for a successful response. The monitor configuration has domain-specific information, so if you have multiple Active Directory domains, then you will need a separate ldaps monitor for each domain. Include the domain name in the monitor name.
- In the Type field, click where it says Click to select.
- Scroll down and click the circle next to LDAP.
- At the top of the window, click the blue Select button.
- Scroll down the Basic Parameters section, and check the box next to Secure. This checkbox instructs the monitor to connect to the Domain Controllers using LDAPS instead of LDAP.
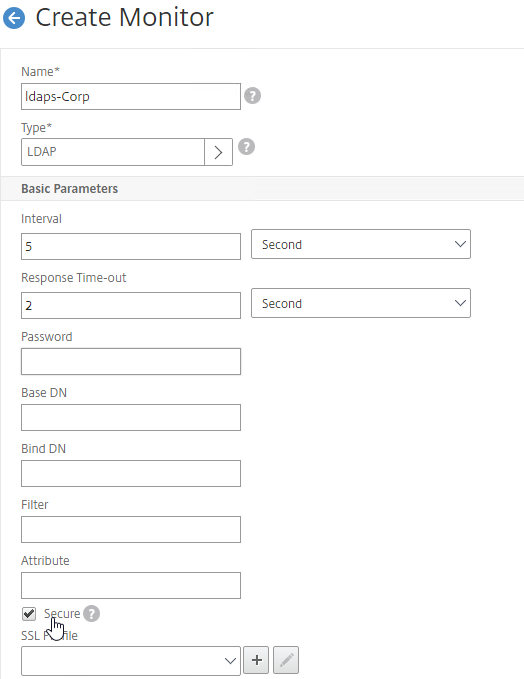
- Scroll back up, and configure the following:
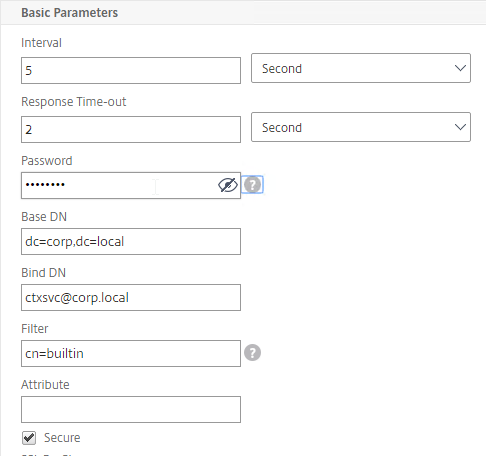
- In the Base DN field, enter your domain name in LDAP format (e.g. dc=company,dc=com).
- In the Bind DN field, enter the UPN login (e.g. ctxsvc@company.com) of a service account in the domain that can browse all objects. Any normal Domain User should be sufficient. Just make sure the password doesn’t expire.
- In the Filter field, enter cn=builtin. This limits the search results so it’s not returning the entire domain.
- In the Password field (higher in the list), enter the password for the service account. Make sure there is no semicolon in the password or the Perl script will be unable to parse the parameters.
- Scroll down and click Create.
add lb monitor LDAP-Corp LDAP -scriptName nsldap.pl -dispatcherIP 127.0.0.1 -dispatcherPort 3013 -password Passw0rd -secure YES -baseDN "dc=corp,dc=local" -bindDN "corp\\ctxsvc" -filter cn=builtin
- If you have multiple domains, then create additional monitors: one for each domain.
- Jump to the Servers section.
12.0 older than build 56
- In the Citrix ADC Configuration Utility, expand Traffic Management, expand Load Balancing, and click Monitors.
- On the right, click Add.

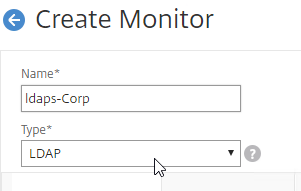
- Name the monitor ldaps-Corp or similar. The ldaps monitor logs into Active Directory, performs an LDAP query, and looks for a successful response. The monitor configuration has domain-specific information, so if you have multiple Active Directory domains, then you will need a separate ldaps monitor for each domain. Include the domain name in the monitor name.
- Change the Type drop-down to LDAP.
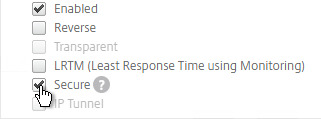
- Scroll down the Standard Parameters tab, and check the box next to Secure. This checkbox instructs the monitor to connect to the Domain Controllers using LDAPS instead of LDAP.
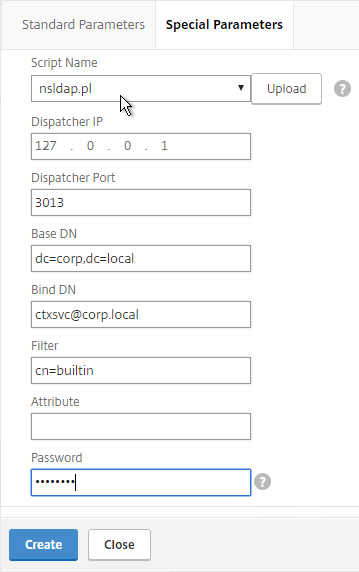
- Scroll back up, and switch to the Special Parameters tab.
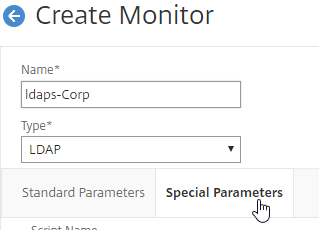
- Configure the following on the Special Parameters tab:
- Use the Script Name drop-down list to select the nsldap.pl file.
- In the Base DN field, enter your domain name in LDAP format (e.g. dc=company,dc=com).
- In the Bind DN field, enter the UPN login (e.g. ctxsvc@company.com) of a service account in the domain that can browse all objects. Any normal Domain User should be sufficient. Just make sure the password doesn’t expire.
- In the Filter field, enter cn=builtin. This limits the search results so it’s not returning the entire domain.
- In the Password field, enter the password for the service account. Make sure there is no semicolon in the password or the script will be unable to parse the parameters.
- Click Create.
add lb monitor LDAP-Corp LDAP -scriptName nsldap.pl -dispatcherIP 127.0.0.1 -dispatcherPort 3013 -password Passw0rd -secure YES -baseDN "dc=corp,dc=local" -bindDN "corp\\ctxsvc" -filter cn=builtin
- If you have multiple domains, then create additional monitors: one for each domain.
Servers
- On the left, expand Traffic Management, expand Load Balancing, and click Servers.
- On the right, click Add.
- Enter the following in the Create Server section.
- In the Name field, enter a descriptive server name. Usually it matches the actual server name.
- In the IPAddress field, enter the IP address of the server. Note: you can alternatively change the selection to Domain Name and enter a FQDN. This requires the Citrix ADC the be able to resolve the FQDN.
- Enter comments to describe the server.
- Click Create.
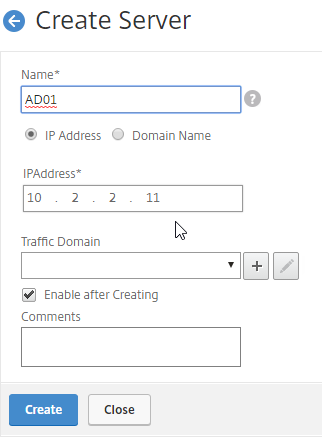
add server AD01 10.2.2.11 add server AD02 10.2.2.12
- Continue adding Domain Controllers. You usually want at least two per domain.
Service Groups
- On the left, expand Traffic Management, expand Load Balancing, and click Service Groups.
- On the right, click Add
.
- In the Basic Settings section, do the following:
- In the Name field: You will create one Service Group per datacenter. Enter a name reflecting the name of the data center. Also, you will create a set of service groups per Active Directory domain, so include the domain name.
- Change the Protocol drop-down to SSL_TCP.
- Scroll down, and click OK to close the Basic Settings section.
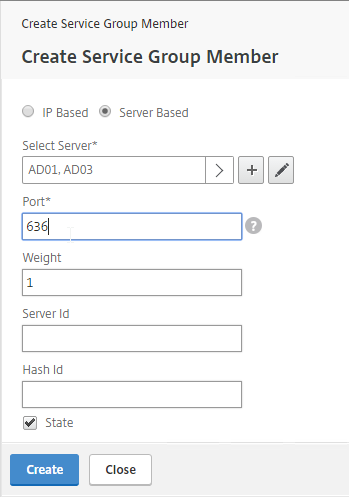
- On the left, in the Service Group Members section, click where it says No Service Group Member.
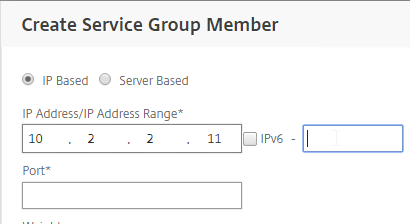
- If you did not create server objects, then leave the selection set to IP Based, and enter the IP address of a Domain Controller in this datacenter.
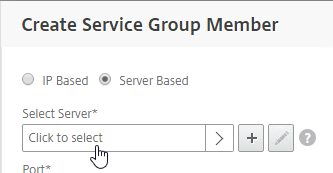
- If you previously created server objects, then change the selection to Server Based, and select the server objects.
- In the Port field, enter 636 (LDAPS). This assumes the Domain Controllers have certificates installed.
- Click Create.
- If you did not create server objects, then leave the selection set to IP Based, and enter the IP address of a Domain Controller in this datacenter.
- Click OK to close the Service Group Members section.
- On the right, in the Advanced Settings column, click Monitors.
- On the left, in the Monitors section, click where it says No Service Group to Monitor Binding.
- In the Select Monitor field, click where it says Click to select.
- Click the circle next to the LDAPS monitor you created earlier. The monitor might be on Page 2.
- The circle must be clicked exactly (no room for error). If you click outside the circle, then the monitor will open for editing. If this happens, click Close to return to the selection screen.
- At the top of the window, click the blue Select button.
- Click Bind.
- In the Select Monitor field, click where it says Click to select.
- To verify the members are up, click in the Service Group Members section.

- Right-click a member, and click Monitor Details.
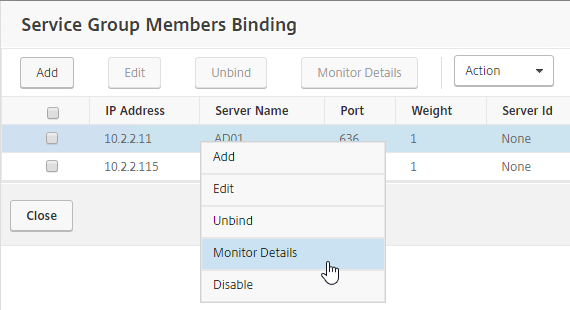
- The Last Response field should say Success – Probe succeeded. Click Close. It’s too bad you can’t edit the monitor from here.
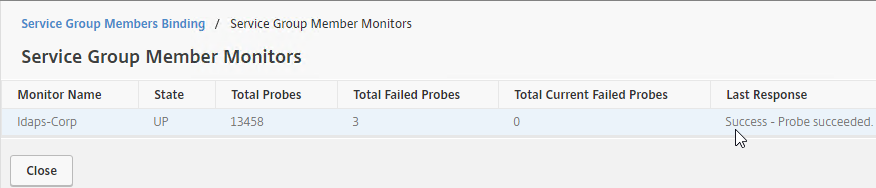
- If the monitor doesn’t work, use ldp.exe to verify the Domain Controller certificate.
- Right-click a member, and click Monitor Details.
- Click Close and Done to finish creating the Service Group.
add serviceGroup svcgrp-LDAP-Corp SSL_TCP bind serviceGroup svcgrp-LDAP-Corp AD01 636 bind serviceGroup svcgrp-LDAP-Corp AD02 636 bind serviceGroup svcgrp-LDAP-Corp -monitorName LDAP-Corp
- Add additional service groups for Domain Controllers for each domain in each data center.
Load Balancing Virtual Server
- Create or import a certificate that matches the FQDN that resolves to the new Load Balancing VIP for LDAPS.
- On the left, expand Traffic Management, expand Load Balancing, and click Virtual Servers.
- On the right, click Add.
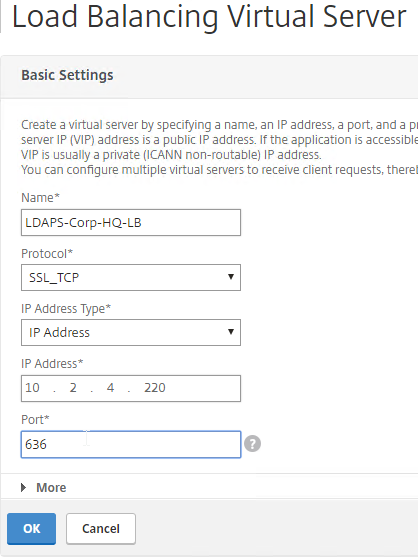
- In the Basic Settings section, do the following:
- Name it LDAPS-Corp-HQ-LB or similar. You will create one Virtual Server per datacenter, so include the datacenter name. Also, each domain has a separate set of Virtual Servers, so include the domain name.
- Change the Protocol drop-down to SSL_TCP.
- Enter a Virtual IP. This VIP cannot conflict with any other IP + Port already being used. You can use an existing VIP that is not already listening on TCP 636.
- Enter 636 as the Port.
- Click OK to close the Basic Settings section.
- On the left, in the Service Group section, click where it says No Load Balancing Virtual Server ServiceGroup Binding.
- Click where it says Click to select.
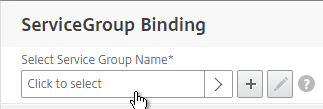
- Click the circle next to a previously created Service Group. It might be on page 2.
- The circle must be clicked exactly (no room for error). If you click outside the circle, then the Service Group will open for editing. If this happens, click the x on the top right, or the Done button on the bottom, to return to the selection screen.
- At top of the screen, click the blue Select button.
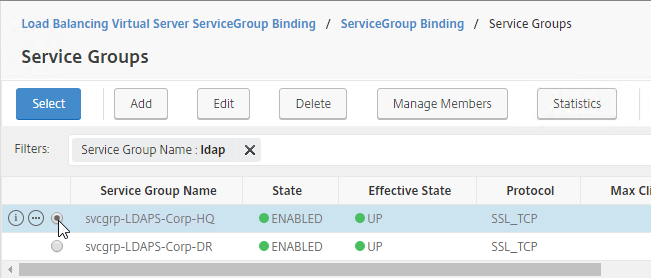
- Click Bind.
- Click where it says Click to select.
- Click Continue to close the Services and Service Groups section.
- On the left, in the Certificates section, click where it says No Server Certificate.
- Click where it says Click to select.
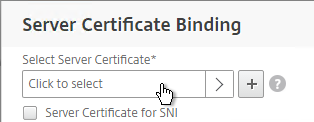
- Click the circle next to a certificate that matches the FQDN that resolves to this VIP. It might be on page 2.
- At the top of the window, click the blue Select button.
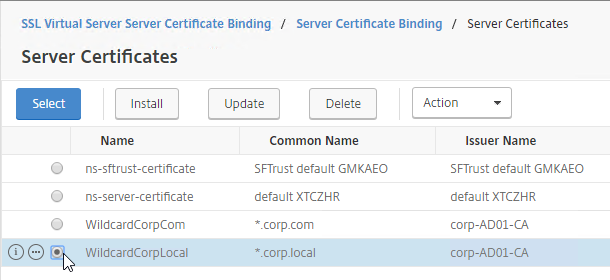
- Click Bind.
- Click where it says Click to select.
- Click Continue to close the Certificates section.
add lb vserver lbvip-LDAP-Corp SSL_TCP 10.2.2.210 636 -persistenceType NONE -cltTimeout 9000 bind lb vserver lbvip-LDAP-Corp svcgrp-LDAP-Corp
- There’s no need to configure Persistence for LDAP.
- If you haven’t enabled the Default SSL Profile, then perform other normal SSL configuration including: disable SSLv3, and bind an A+ Cipher Group.
- Click Done to finish creating the Virtual Server.
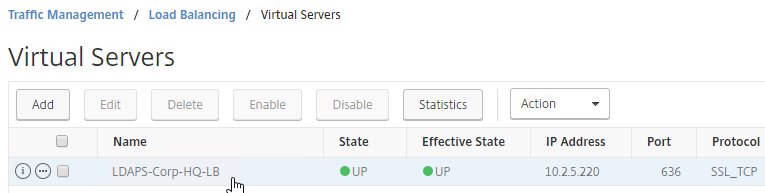
- The new Virtual Server should show as UP.
Backup Virtual Server
You can optionally configure this Load Balancing Virtual Server to failover to a different Load Balancing Virtual Server. This allows you to load balance Domain Controllers in this datacenter, and if down, failover to the other datacenter.
- Create additional Load Balancing Virtual Servers for each datacenter.
- These additional Virtual Servers do not need a VIP, so change the IP Address Type to Non Addressable. Only the first Virtual Server will be directly accessible.
add lb vserver lbvip-LDAP-Corp-Backup SSL_TCP 0.0.0.0 0
- Notice that the additional datacenter Virtual Servers show up with an IP Address of 0.0.0.0 and port of 0.
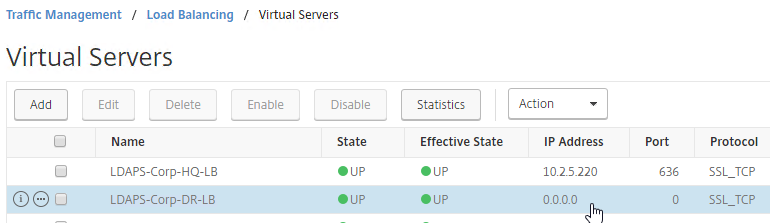
- These additional Virtual Servers do not need a VIP, so change the IP Address Type to Non Addressable. Only the first Virtual Server will be directly accessible.
- After you are done creating a Virtual Server for each datacenter, right-click the primary datacenter’s Virtual Server, and click Edit.
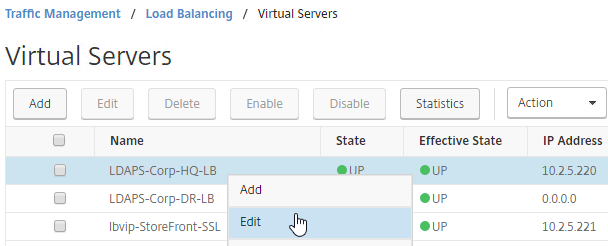
- On the right, in the Advanced Settings column, click Protection.
- On the left, in the Protection section, change the Backup Virtual Server to one of the other datacenter Virtual Servers. If all of the services in this datacenter are DOWN, the backup Virtual Server will be used instead. You can cascade multiple Virtual Servers using this method. Click OK and Done.
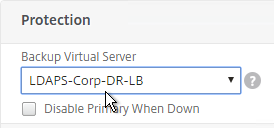
set lb vserver lbvip-LDAP-Corp -backupVServer lbvip-LDAP-Corp-Backup
CLI Commands
Here is a list of CLI Commands for Domain Controller Load Balancing.
# SSL Global Parameters # --------------------- set ssl parameter -denySSLReneg NONSECURE # Certs # ----- add ssl certKey WildcardCorpCom -cert WildcardCorpCom.pfx -key WildcardCorpCom.pfx -inform PFX -passcrypt "Passw0rd" # Load Balancing Global Parameters # -------------------------------- enable ns mode FR L3 Edge USNIP PMTUD ULFD set lb parameter -sessionsThreshold 150000 set ns param -cookieversion 1 -timezone "GMT-06:00-CST-America/Chicago" set dns parameter -dns64Timeout 1000 set ns tcpParam -WS ENABLED -SACK ENABLED set ns httpParam -dropInvalReqs ON set ns tcpbufParam -memLimit 390 # Monitors # -------- add lb monitor ldaps-Corp LDAP -scriptName nsldap.pl -dispatcherIP 127.0.0.1 -dispatcherPort 3013 -password Passw0rd -encrypted -encryptmethod ENCMTHD_3 -LRTM DISABLED -secure YES -baseDN "dc=corp,dc=local" -bindDN admin@corp.local -filter cn=builtin # Servers # ------- add server AD01 10.2.2.11 add server AD03 10.2.2.115 # Service Groups # -------------- add serviceGroup svcgrp-LDAPS-Corp-HQ SSL_TCP -maxClient 0 -maxReq 0 -cip DISABLED -usip NO -useproxyport YES -cltTimeout 9000 -svrTimeout 9000 -CKA NO -TCPB NO -CMP NO bind serviceGroup svcgrp-LDAPS-Corp-HQ AD01 636 bind serviceGroup svcgrp-LDAPS-Corp-HQ AD03 636 bind serviceGroup svcgrp-LDAPS-Corp-HQ -monitorName ldaps-Corp set ssl serviceGroup svcgrp-LDAPS-Corp-HQ -sslProfile ns_default_ssl_profile_backend # Load Balancing Virtual Servers # ------------------------------ add lb vserver LDAPS-Corp-DR-LB SSL_TCP 0.0.0.0 0 -persistenceType NONE -cltTimeout 9000 bind lb vserver LDAPS-Corp-DR-LB svcgrp-LDAPS-Corp-HQ add lb vserver LDAPS-Corp-HQ-LB SSL_TCP 10.2.5.220 636 -persistenceType NONE -cltTimeout 9000 -backupVServer LDAPS-Corp-DR-LB bind lb vserver LDAPS-Corp-HQ-LB svcgrp-LDAPS-Corp-HQ # SSL Virtual Servers # ------------------- set ssl vserver LDAPS-Corp-DR-LB -sslProfile ns_default_ssl_profile_frontend bind ssl vserver LDAPS-Corp-DR-LB -certkeyName WildcardCorpCom bind ssl vserver LDAPS-Corp-DR-LB -eccCurveName P_256 bind ssl vserver LDAPS-Corp-DR-LB -eccCurveName P_384 bind ssl vserver LDAPS-Corp-DR-LB -eccCurveName P_224 bind ssl vserver LDAPS-Corp-DR-LB -eccCurveName P_521 set ssl vserver LDAPS-Corp-HQ-LB -sslProfile ns_default_ssl_profile_frontend bind ssl vserver LDAPS-Corp-HQ-LB -certkeyName WildcardCorpCom bind ssl vserver LDAPS-Corp-HQ-LB -eccCurveName P_256 bind ssl vserver LDAPS-Corp-HQ-LB -eccCurveName P_384 bind ssl vserver LDAPS-Corp-HQ-LB -eccCurveName P_224 bind ssl vserver LDAPS-Corp-HQ-LB -eccCurveName P_521
Next Steps
You may now use this Virtual IP in your Citrix Gateway LDAP authentication policies, or Citrix ADC management login.
Hey Carl…we have an LDAP load balancer setup, our company wireless also used LDAP. If there is a change to the wireless, and many devices need to check in, the LDAP VIP seems to deny requests. Do you know which configuration I should look at for that type of limit?
Hi Carl, we have a Virtual Server that is tied to load balance LDAP Policy and started having issues with users logging in twice. It seems that the load balanced service group is partially up with two DCs. If I look at the details of the specific service member it says “Failure – Failed to contact server – Connection reset by peer.” It seems to have started recently and we have tried rebooting server with no luck.
Firewall?
I don’t think it is the firewall. I do see some logs in system event viewer in relation to Schannel and it points to not having no suitable default server credential exists on this system on the DC that is having the ldap issue.
The Domain Controllers have LDAP certificates? Use ldp.exe to connect to each LDAP server using SSL protocol and see if it connects.
I followed the instructions for configuring ldap and storefront Load balancing but the state is still showing down. My service group is up and running and all my servers also. I followed the instructions, also load balancing is active. What could be wrong?
Did you bind a cert to the Load Balancing Virtual Server? Under Traffic Management > SSL, is the SSL feature enabled?
thx, i had the ssl offloading not enabled. Now the state is green!
Hi Carl,
Thanks for the great blog!
I am pretty new to netscalers and have a query.
In our environment we have ldaps load balancing virtual server configured for 2 backend DC servers and we user – protocol SSL_TCP.
We already have a SSL certificate binded to the virtual service and status is UP.
Now the question is, with SSL_TCP, since SSL termination happens at netscaler, does it still require certificate on the backend DC servers for LDAPS service?
I don’t think I’ve tried it without cert on LDAP server.
Hi carl is there any way to find the SRC of account lockout for example if any service account being used at multiple automation scripting and any script using the wrong password resulted in account lockdown. It is hard to find the SRC IP cause on AD servers it will always be SNIP as SRC for locout for that svc account
NetScaler can send TCP Connection info to Syslog. I’m not sure if you can link that data with the lockout.
Would you be able to pass the IP in the header using X-forward-for? This is supported by Microsoft in Windows 2019 and newer but I only see the HTTP documentation for X-Forward-For in Citrix documentation.
Hi Carl,
Thank you for creating this article, it’s incomparably better than what Citrix has in their docs right now.
I have two questions regarding the settings you recommend:
– Why do you recommend to disable session reuse (-sessReuse DISABLED) for the SSL profile? I haven’t seen this recommendation anywhere else so it’s a bit surprising.
– Citrix recommends to disable L3 and Edge modes (https://community.netscaler.com/s/article/best-practices-netscaler-adc-deployments) since those are not required in most situations – is there any particular reason why you leave them enabled?
Thank you and regards
There used to be a bug that required disabling session reuse. Thanks for pointing it out so I can remove the sessreuse commands.
L3 and Edge are enabled by default. A secure configuration would definitely disable them.
Hi Carl,
just a quick question: when using a loadbalanced LDAP vServer for Mgmt-Auth in a HA pair, you cannot login to the passive instance because traffic is sourced from SNIP. How do I overcome this?
Kind regards
Hi Holgi, I am exactly facing the same problem, is it by design did you found a solution
If the SNIP is in the DMZ and NSIP is internal, you can use PBR to route the LDAP auth traffic through the NSIP.
Hi
I have green light on my LB_VS for LDAPS in Traffic Management
But when I add the Authentication server, pointing to the IP address of the LB_VS and test connection i dont get connection
what have I missed ?
Many builds of ADC don’t test correctly but they still work when users authenticate to a Gateway or AAA vServer. What error are you seeing?
Hi Carl,
is there any option to use a ldap information as a stickiness (persistance) to keep the line constant. Two backend Server, multiple clients. If there is any new connection to the vserver use roundrobin, but if there is a reused connection, they need to get the information out of the packet. Is this useable with a persistence Setting?
You can do persistence based on a rule, which can use any of the policy syntax. If you do authentication on the ADC, then you might be able to use AAA expressions for the persistence rule.
Thank You, but can you give me an example?
Hi Karl,
We have on the Citix ADC a LDAPS Vserver, hierr question the various data for the phone book that works all fine but we get from time to time reset by peer and on the ad servers I can read the following info would you have an idea maybe 🙂 i am pretty new to citrix adc
The following client performed a SASL (Negotiate/Kerberos/NTLM/Digest) LDAP bind without requesting signing (integrity verification), or performed a simple bind over a clear text (non-SSL/TLS-encrypted) LDAP connection.
SSL (636) load balancing should not cause that. TCP 389 might cause it but SSL 636 should not.
Hello Karl,
Thanks for the quick feedback, the funny thing is we only connect via LDAPS 636, could it be that the Citrix ADC somehow changes that when it passes the request to the AD server, it also rarely occurs.
Greetings Patrick
We have had a VIP for LDAPS (Port 636) for a while.. but after setting
LdapEnforceChannelBinding on the Domain Controllers to “When Supported” and
LDAPServerIntegrity : RequireSigning
We see an issue where connections from clients (like Windows) that support Channel Binding fail going through the VIP, but succeed when talking directly to a domain controller. The reason seems to be because the intent of Channel Binding is to prevent MITM attacks.. and Netscaler being a MITM is causing the CBT (Channel Binding Token) to show up as invalid. If it is a client that does not support Channel Binding, everything works normally.
test results through ldp.exe:
53 = ldap_set_option(ld, LDAP_OPT_ENCRYPT, 1)
res = ldap_bind_s(ld, NULL, &NtAuthIdentity, NEGOTIATE (1158)); // v.3
{NtAuthIdentity: User=’myaccount’; Pwd=; domain = ‘MYDOMAIN’}
Error : ldap_bind_s() failed: Invalid Credentials.
Server error: 80090346: LdapErr: DSID-0C090590, comment: AcceptSecurityContext error, data 80090346, v2580
Error 0x80090346 Client’s supplied SSPI channel bindings were incorrect.
———–
Does it work with a Simple Bind?
Yes, Simple binds work on the TLS port 636 through the netscaler. Windows clients that support CBT (Channel Binding Token) are the only ones that fail because they detect a Man in the middle tampering with the session.
Did anyone figure out how to solve this on the load balancer so that you don’t have to disable channel binding on the domain controller?
The whole point of channel binding is to detect a man in the middle. Netscaler is man in the middle. There is one way you could get it to work if you use the exact same cert with the same thumbprint on all your DCs and load balancer. Haven’t tested, but should work given how Channel binding works.
Hey Carl!
First of all, thank you so much for your great work, your blog is simply amazing and helped us so many times, thank you for that.
We now facing a problem we couldn’t find any help and hope maybe you could help us find the right direction:
We got 2 Domaincontroller:
DC1: 10.10.10.10 – test.lab
DC2: 10.20.20.20 – test2.lab2
Both are fully independent and don’t got any trust or something.
We’ve created 2 LB for the DCs
LB1 : 10.10.10.11
Protocol: TCP
Port: 389
1 Service: DC1
LB1 : 10.20.20.11
Protocol: TCP
Port: 389
1 Service: DC2
We can send LDAP request to both LBs and get correct answers, so these two are working correctly.
We now thought we could build a CS-Server in front of them to build something like a LDAP “dispatcher”
CS1: 10.30.30.30
Protocol: TCP
Port 389
Persistence: None
No default cs policy
We’ve created two CS-Policies:
CS-Pol1, CLIENT.TCP.PAYLOAD(300).CONTAINS(“dc=test,dc=lab”) –> LB1 – Prio 100
CS-Pol2, CLIENT.TCP.PAYLOAD(300).CONTAINS(“dc=test2,dc=lab2”) –> LB2 — Prio 110
No the problem.
In this scenario, I can send a LDAP request with dn “cn=x,ou=y,dc=test,dc=lab” to 10.30.30.30 and it works perfectly, is get the correct response and I can see the hit of CS-Pol1 with nsconmsg -d current -g _hits
When I try “cn=x,ou=y,dc=test2,dc=lab2”, I don’t see a hit or something with wireshark on the DC2.
Now the funny part:
When I switch the prio for the CS-policies to
CS-Pol1, CLIENT.TCP.PAYLOAD(300).CONTAINS(“dc=test,dc=lab”) –> LB1 – Prio 100
CS-Pol2, CLIENT.TCP.PAYLOAD(300).CONTAINS(“dc=test2,dc=lab2”) –> LB2 — Prio —-90—–
then only the CS-Pol2 works and the CS-Pol1 not anymore. So basically the policies are correct and everything around that, but only the CS-Server seems to only try the first policy and ignores everything afterwards.
I’m absolutly clueless where to find a solution for this. My guess is that there are some settings in the tcp profiles which could help, but no luck so far….
Do you got any idea?
Thank you for reading and your time!!!
Christopher
Hi Carl,
thank you for the many great guides :).
Could you help me with some information?
If creating the Virtual Server for LDAPS to be TCP, the authentication might fail as the end server will have a different name than the VS. Would I use a certificate issued for the VS name and having the DC names as SAN work?
For example:
VS = ldapVip.mycomp.com
DC1: dc1.mycomp.com
DC2: dc2.mycomp.com
Certificate issued for ldapVip.mycomp.com with SAN dc1.mycomp.com and dc2.mycomp.com. Certificate installed on the DCs.
Thank you.
Maybe. Or you can do SSL_TCP vServer and put the cert on the ADC.
Thank you. We use SSL_TCP atm, however for security reasons, I would need to see the client IP in the DC logs. Currently, I can only see the Netscaler IPs. I tried to enable “Use Client IP” but that killed the authentication completely.
Did you have a solution for this? I have the same requirements, and this is becoming problematic.
Hi TK,
not a direct solution. I got the following from one of the Citrix Engineers that I’ve discussed the issue with:
“We don’t see the username and password as its just TCP Proxy we are doing here.
IF you have an external SYSlog server to use, you COULD turn on TCP Auditing for the LDAP Vip which will capture the TCP stats of client -> VIP and SNIP -> backend in a Syslog message. You can then correlate this against your LDAP log. To make the correlation easier, it would be best to make sure that the LDAP server and ADC are using the same NTP server.
https://support.citrix.com/article/CTX226058
”
So pretty much my plan is to use a SIEM solution to address the issue.
I hope it helps.
Good Morning, I am setting up a lab this time round, with Srv 2019 and NS 13.0. Latest build 79_64. I go through all the motions, HA and stuff. When I get to setup ldaps, I get “Valid Credentials are not provided” for the bind dn section. Double checked pw and even made sure I have no special characters. I had it all setup on 12.1 and all was working, then did the upgrade on secondary to 13.0 79_64, force failover, then went to ldap server settings and retried test, failed when on 13.0.
I think there’s a bug in the latest 13.0 builds. But it might still work when you try to use it with Gateway or AAA.
I noticed this as well with 13.0-79.64. I upgraded our test environment first (thank God) per best practice. I noticed that LDAP completely broke in that version. As you noted in the GUI – it shows the LDAP server and port are accessible, but the credential isn’t valid (which I know to be a good cred). Luckily, the only thing on this ADC using LDAP is the test Citrix XenApp environment. I checked logs while I was doing the tests and saw in the logs that the Status was “Success”, but still shows fail in the GUI. Tried both LDAPS and LDAP – same result. So I don’t know if the “Success” in the log is just that the Netscaler was able to communication with the LDAP server over the ports, or if the full LDAP test using the account was a “Success”. Either way, there is definitely something wrong with this ADC version and LDAP. Applicable log entries below (sanitized)
Apr 19 13:06:40 {NetscalerVIP} 04/19/2021:13:06:40 GMT NSAAF2 0-PPE-1 : default GUI CMD_EXECUTED 6389 0 : User {NetscalerUser} – Remote_ip {MyPcIP} – Command “probe server -type LDAP -IP {LdapServerIP} -port 636 -ldapBase {baseDN} -ldapBindDn {LdapAccountDN} -password {LdapPw} -secType SSL” – Status “Success”
Apr 19 12:47:31 {NetscalerVIP} 04/19/2021:12:47:31 GMT NSAAF2 0-PPE-1 : default GUI CMD_EXECUTED 6275 0 : User {NetscalerUser} – Remote_ip {MyPcIP} – Command “probe server -type LDAP -IP {LdapServerIP} -port 389 -ldapBase {baseDN} -ldapBindDn {LdapAccountDN} -password {LdapPw} -secType PLAINTEXT” – Status “Success”
Other than the test, does actual LDAP authentication work?
Citrix Discussions says that Citrix Support has a fix that can be installed to resolve this.
I’ve noticed a bug with LDAP server configuration in the GUI for a long time–even opened TAC case for this. In the connection settings, the password for the LDAP bind DN you’re using cannot contain odd characters. I was even getting JSON errors in the gui when the password was a random password that contained square brackets. This issue was even preset in the last release of 13 I’ve used.
I usually ignore the testing tool in the GUI. Instead I bind the policy to a Gateway and test login that way.
So I’ve got this working with a VIP at 2 different datacenters. Each works fine. Trying to implement GSLB for site redundancy and once I start using the CName it fails. any ideas?
Does the certificate match the cname?
We are using a wildcard certificate of “*.domain.com”. our cname record points “ldap.domain.com” to “ldap.gslbprd.domain.com”.
I think ldp.exe requires the domain controller FQDN to be in the Common Name or Subject Alternative Name of the certificate so wildcard probably won’t work.
Weird thing is that it’s the same certificate whether we use GSLB or not. and it works just fine if we just go straight ldap.domain.com –> ip address. once we add the Cname is where it acts up. If we can’t use GSLB for site redundancy do you have any other possible thoughts?
Some apps will require that you have ldap.gslbprd.domain.com in the SAN.
Just a little note to anyone browsing…. if you have a big domain, do NOT miss the “Filter:” step on your LDAPS monitor. I just noticed the health of our LDAPS VIP has been terrible for some time, with DCs UP and DOWN randomly, even though they’re all online. The reason for this was we were missing the “cn=builtin” filter, and the monitor was pulling the whole domain. Sometimes results weren’t coming back in the 15s timeout window, showing a probe failure. Adding the filter immediately corrected this.
tl;dr – Never skip a step that Carl documents. 🙂
Good day.
We’d like to load balance our AD servers using TLS instead of SSL, is the procedure basically the same except we use port 389 (documents online seem to point to TLS will use port 389 with a start_tls command to encrypt connections)?
I seem to run in the issue where the Citrix ADC will say, when testing connectivity, that the server is not and ldap server or the port is not an ldap port, even though all servers in the load balancer group are DCs, and they each work when I create an action for them.
I’m expecting my issue is with the load balancer configuration.
I’ve tried with SSL_TCP and TCP port types.
TCP is the protocol since Start_TLS doesn’t do certificate exchange until after the TCP connection is established.
The “test” button uses NSIP as the source IP to reach your VIP whereas your load balancing vServer uses SNIP. When I have a dedicated management network I ignore the test button. You can do “nstcpdump.sh port 389” to see the traffic.
Hi Carl
iv followed your instructions and spent an hour or two fiddling and still cant get this to work on 12.1, GUI shows as up and all SG group members are up and monitor probe is successful but I get the following when testing using ldp:
Server error:
0x55 = ldap_unbind(ld);
ld = ldap_sslinit(“dc.company.ie”, 636, 1);
Error 85 = ldap_set_option(hLdap, LDAP_OPT_PROTOCOL_VERSION, 3);
Error 0 = ldap_connect(hLdap, NULL);
Error 0 = ldap_get_option(hLdap,LDAP_OPT_SSL,(void*)&lv);
Host supports SSL, SSL cipher strength = 256 bits
Established connection to dc.company.ie.
Retrieving base DSA information…
Server error:
Error: ldap_parse_result failed: No result present in message
Server error:
Getting 0 entries:
tested using a wildcard cert and a created cert that includes all DC’s as alt DNS entries, where am I going wrong?
If you disable all servers except one, does it work?
no, same issue
If you point ldp.exe directly to the LDAP server, does it work?
pointing directly at any 4 of my existing LDAP servers connects fine (port 636, SSL ticked), all 4 group members show as UP and monitor details on all 4 “success – probe succeeded”
In ref to the link to this: https://docs.citrix.com/en-us/citrix-adc/13/networking/source-citrix-adc-freebsd-traffic-from-snip.html
The commands here do not seem to work. I am getting an error saying no such argument exists (-natIP)
(VPX 50 plat – latest ver 13.58.32)
its either something really stupid on my part, or ill have to create a ticket once they fix my partner account.
Hi Carl,
I have one issue if u can guide, We have VPX in AWS .
1) If we use VPX without any load balance , everything works fine
2) But if we put AWS load balancer in front of VPX , Application can be launched only using light version .If workspace or received used it gives error protocol drive error . Issue with Citrix Support Since one week but i don’t they can help further here.
Are you doing ALB with SSL termination? Does NLB work?
Thanks Carl,
It is ALB and yes SSL termination done there
That might be the problem. Gateway doesn’t like SSL termination prior to reaching the Gateway.
Hi Carl, I have an issue with our NetScaler 12.1 VPX, and specific programs like DLP not working with LDAPS.
LDP.exe shows the VIP as functioning, and if DLP points directly at the DC it works fine. Only when it points to the NetScaler does it error out. This also happens to our Palo Alto but other applications are working fine. We used your writeup and several variations of ssl-tcp and just tcp to test and basically they all work and fail in a similar way. Currently the NetScaler has the root cert from the DC and a Digicert Wildcard cert on the VIP.
I have a question if this will still work after enabling LDAP channel binding on Domain Controller (this will become default after March 2020). I’ve read on reddit ( https://www.reddit.com/r/sysadmin/comments/ec3coe/microsoft_ldap_channel_binding_changes_pushed/ ) this statement:
This change really only negatively affects LDAPS connections where you may be doing TLS interception like putting a load balancer in front of LDAP with the load balancer terminating TLS.
Any thoughts on this?
I think that if LDAPS is configured (not LDAP), then it’s probably fine.
Hey Carl, why is the client idle timeout set at 9000? does that keep aaa sessions active for that duration?
I think that applies to TCP connections, not web sessions. Whenever a client sends an HTTP request or LDAP request to a vServer, the client must first start a TCP connection with the ADC. The HTTP or LDAP request is then sent across the TCP connection. Keeping that TCP connection active reduces latency if the client needs to send more traffic. the idle timeout clears inactive TCP connections from ADC’s TCP connections table.
Hello Carl – I’ve not done this for a couple of years but I’m pretty convinced I used to load balance LDAPS on port 636 using TCP and connect the NetScaler Authentication service to it. I am trying to do this now – the Load Balancing VIP is setup fine with an intelligent LDAP monitor authenticating with the Bind DN, but the NetScaler authentication service refuses to accept it as a valid LDAPS server. If I add the server on it’s own it works fine here. I do not have ‘Validate LDAP Server cert’ checked. All I want to do it pass the traffic on to the domain controller, and use the certificate there, I do not wish to import certificates onto the NetScaler.
The LDAP Server entity uses NSIP to communicate with whatever address you put in the LDAP Server IP Address field. If that’s a VIP, then the NSIP must be able to communicate with the VIP. You can verify this by running nstcpdump.sh. Do you have PBRs configured? You can make an exception for NSIP-to-VIP.
Hello, I sorted this out minutes after writing this, I had set TCP_SSL Service group with a TCP vServer. I just had to recreate my service group to using plain TCP – Doh.
Firstly, thanks for the wonderful site – it is a great help to many.
I too am trying to set this up using TCP rather than SSL_TCP as I do not want to install certificates on the Netscaler. I have followed the instructions above, substituting “SSL_TCP” for “TCP”. The virtual server and service group show as up but when I point the ldp.exe tool to the VIP, I get error 81. when I point the tool direct to the domain controller, it works. What am I doing wrong?
ldp.exe verifies the certificate. Each domain controller has a unique certificate. When NetScaler connects to LDAPS, NetScaler does not verify the certificate, so it might work, even though ldp doesn’t work.
Hi Carl!
First of all I want to thank you for all the support you’ve offered so far. Your website and your commitment to helping others is priceless! I would have a another question, this time regarding LDAP load balancing:
On our Virtual Apps and Desktops setup users login from another domain in another forest. So user accounts are in domain corp.com, and our Citrix-environment is in domain lab.com, both in a separate forests. There’s a one-way trust between these domains so that lab.com trusts corp.com but corp.com does not trust lab.com
The corp.com LDAP-servers have been added to our Netscaler but there is no load balancing in place. So few individual LDAP-servers from corp.com have been added to Auhentication -> Dashboard -> Authentication Server. Each server is bind to a particular LDAP policy which is then bind to particular Gateway vServer. Netscaler is currently connecting the corp.com LDAP-servers through SSL port 636.
I would like to load balance corp.com LDAP-server (add LDAP-servers from another datacenter as backup virtual server) because there have been times when one of their server has been down, and our users have not been able to login. What confuses me are the certificates.
So when creating the load balancing vServer I need to give it a name in DNS, like corp-ldap.lab.com, and then create a certificate for that, either wildcard *.lab.com or corp-ldap.lab.com. Is that correct and is that all I need to do?
Do the end users in corp.com domain need to be able to connect the load balancing VIP directly, meaning do I need a new firewall rule for this? Right now in lab.com firewall only outside traffic is allowed to Gateway vServer.
And what would be the downside of using port 389 for this (not using LDAPS)? We don’t allow users to change passwords even now at the gateway.
If your only LDAP Client is the ADC (e.g. Gateway LDAP Policy), then the certificates don’t matter because ADC does not verify certificates by default.
If you have external LDAP Clients (e.g. Linux machines) that connect to the LDAP VIP, then if you set the LDAP VIP to SSL_TCP, then you can bind a single certificate to the LDAP VIP and the LDAP Clients only need to trust that one certificate. The Domain Controller certificates can be anything because ADC load balancing does not verify the certificate identity.
Most security professionals would encourage you to encrypt everything possible. 389 is clear text, including the user’s password.
Hey Carl,
I created a LB for LDAP to force the traffic out of the SNIP rather than the NSIP. However LDAP traffic is still going out via the NSIP and not the SNIP any ideas?
The LB VS also shows as down when pointing towards the VIP (Created a brand new VIP and still get the same problem)
Any thoughts on this? I am still troubleshooting but it should be working and is not:
Running NS12.1 50.28.nc
Thanks
HI Cer, I am new in Netscaler and just want to know, i case my primary DC LDAP goes down, how LDAP authentication will redirect to DR DC LDAP as backup virtual servers is non addressable and there no DR LDAP server is configured?
Thanks,
Are you saying that you created a backup LDAP load balancing Virtual Server but you didn’t bind any services to it?
Yes, I need to know, do we need to configure and add service group & monitoring as we do for primary LDAP virtual server ?
If you want active/passive load balancing of LDAP, then yes. Another option is to add all of your Domain Controllers to a single Load Balancing vServer and skip the backup vServer.
Okay, but I need to know, if using backup LDAP vServer method, do i need to configure and add service group & monitoring as well in Back vServer?
Hi Carl, I was upgrading to 7.6 and when I disabled the CS traffic kept being sent to the disabled connection server.
NS engineers says all is fine on their end. When I shut down server or stop connection windows service NS redirects as expected. What I fail to understand is why it does not work when I disable the connection server in the admin interface?
I am also trying to understand what disable does under the hood? Whatever it is it does not seem to be working. NS monitors TCP 443 to two replicated connection server. Have talked to VMware support but feel I am not getting answer to this question
“When you disable a View Connection Server instance, users who are currently logged in to View desktops are not affected.” https://pubs.vmware.com/view-51/index.jsp?topic=%2Fcom.vmware.view.administration.doc%2FGUID-B079D888-1C5D-4A0B-ADD9-99310FDB6BF6.html
Tks Carl, I was able to create lb virtual server but I can’t bind this into Xendesktop gateway. Do you have a guide on how to do this?
https://www.carlstalhood.com/netscaler-gateway-12-ldap-authentication/ explains how to create a LDAP Policy/Server and point it to your LDAP Load Balancing VIP.
Hi Carl, when configuring the certificate to use with SSL_TCP what does the common name need to be? I notice you use a wildcard for the domain but if that’s not possible is it the NetScaler or the DC’s that the common name should refer to?
It should match whatever DNS name resolves to the VIP. The LDAP client initiates a SSL connection to the VIP, not the Domain Controller.