Navigation
RADIUS Load Balancing Overview
Two-factor authentication to NetScaler Gateway requires the RADIUS protocol to be enabled on the two-factor authentication product.
On your RADIUS servers you’ll need to add the NetScaler appliances as RADIUS Clients. When NetScaler uses a local (same appliance) load balanced Virtual Server for RADIUS authentication, the traffic is sourced from the NetScaler SNIP (Subnet IP). When NetScaler uses a direct connection to a RADIUS Server without going through a load balancing Virtual Server, or uses a remote (different appliance) Load Balancing Virtual Server, the traffic is sourced from the NetScaler NSIP (NetScaler IP). Use the correct IP(s) when adding the NetScaler appliances as RADIUS Clients. And adjust firewall rules accordingly.
For High Availability pairs, if you locally load balance RADIUS, then you only need to add the SNIP as a RADIUS Client since the SNIP floats between the two appliances. However, if you are not locally load balancing RADIUS, then you’ll need to add the NSIP of both appliances as RADIUS Clients. Use the same RADIUS Secret for both appliances.
When load balancing RADIUS, you’ll want a monitor that verifies that the RADIUS server is functional. The RADIUS monitor will login to the RADIUS server and look for a response. You will need static credentials that the RADIUS monitor can use to login to the RADIUS server.
If you don’t want your monitor to login to RADIUS, then the only other monitoring option is Ping. Adjust the firewall accordingly.
If you have RADIUS Servers in multiple datacenters, you can create multiple load balancing Virtual Servers and cascade them so that the local RADIUS Servers are used first and if they’re not available then the Virtual Server fails over to RADIUS Servers in remote datacenters.
RADIUS Monitor
The RADIUS Monitor attempts to successfully log into the RADIUS server. For RSA, create an account on RSA with the following parameters as mentioned by Jonathan Pitre:
- Setup a user with a fixed passcode in your RSA console.
- Ensure you login with that user at least once to the RSA console because you’ll be asked to change it the first time.
- There is no need to assign a token to your monitor user as long as you are using a fixed passcode. You don’t want to waste a token on a user just for monitoring.
Henny Louwers – Configure RSA RADIUS monitoring on NetScaler:
- In the NetScaler Configuration Utility, on the left under Traffic Management > Load Balancing, click Monitors.
- On the right, click Add.
- Name the monitor RSA or similar. Change the Type drop-down to RADIUS.
- On the Standard Parameters tab, you might have to increase the Response Time-out to 4.
- On the Special Parameters tab, enter valid RADIUS credentials. Make sure these credentials do not change or expire. For RSA, in the Password field, enter the fixed passcode.
- Also enter the RADIUS key configured on the RADIUS server for the NetScaler as RADIUS client.
- For Response Codes, add both 2 or 3. 2 means success while 3 indicates some kind of failure. Either result means that the RADIUS server is responding and thus is probably functional. But 2 is the ideal response.
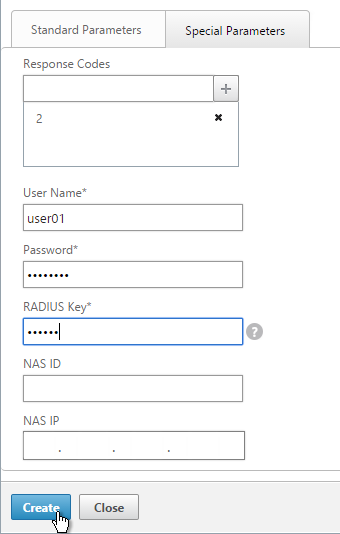
- Click Create when done.
add lb monitor RSA RADIUS -respCode 2-3 -userName ctxsvc -password Passw0rd -radKey Passw0rd -resptimeout 4
Servers
- On the left, expand Traffic Management, expand Load Balancing, and click Servers.
- On the right, click Add.
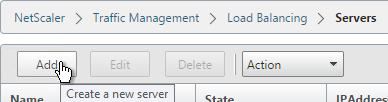
- Enter a descriptive server name; usually it matches the actual server name.
- Enter the IP address of the server.
- Enter comments to describe the server. Click Create.
add server RSA01 192.168.123.13 add server RSA02 192.168.123.14
- Continue adding RADIUS servers.
Service Groups
- On the left, expand Traffic Management, expand Load Balancing, and click Service Groups.
- On the right click Add.
- You will create one Service Group per datacenter. Enter a name reflecting the name of the datacenter.
- Change the Protocol to RADIUS.
- Click OK.
- On the right, in the Advanced column, click Members.
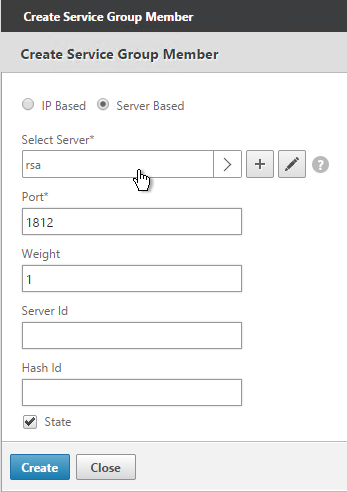
- On the left, in the Service Group Members section, click where it says No Service Group Member.
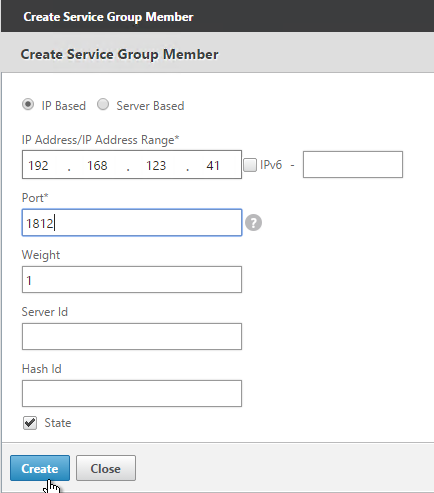
- If you did not create server objects then enter the IP address of a RADIUS Server in this datacenter. If you previously created a server object, then change the selection to Server Based, and select the server object.
- In the Port field, enter 1812 (RADIUS).
- Click Create.
- To add more members, in the Service Group Members section, click where it says 1 Service Group Member.
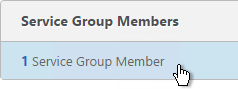
- Click Add to add another member. Click Close when done.
- On the right, in the Advanced column, click Monitors.
- On the left, in the Monitors section, click where it says No Service Group to Monitor Binding.
- Click the arrow next to Click to select.
- Select your new RADIUS monitor, and click OK.
- Click Bind.
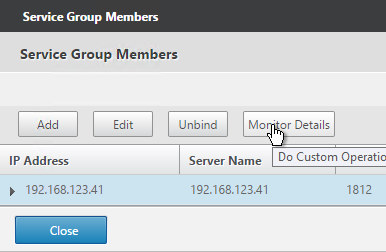
- To verify the member is up, click in the Service Group Members section.
- Highlight a member and click Monitor Details.
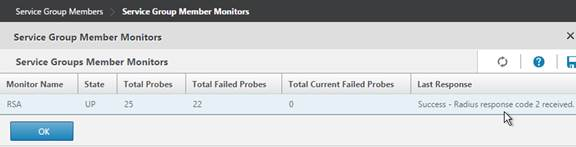
- It should say Radius response code 2 (or 3) received. Click OK.
- Click Done to finish creating the Service Group.
add serviceGroup svcgrp-RSA RADIUS bind serviceGroup svcgrp-RSA RSA01 1812 bind serviceGroup svcgrp-RSA -monitorName RSA
- The Service Group is displayed as UP.
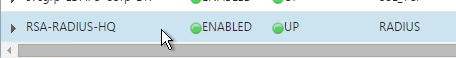
- Add additional service groups for Radius servers in each data center.
Virtual Server
- On the left, expand Traffic Management, expand Load Balancing, and click Virtual Servers.
- On the right, click Add.
- Name it lbvip-RADIUS-HQ or similar. You will create one Virtual Server per datacenter so include the datacenter name.
- Change the Protocol drop-down to RADIUS.
- Enter a Virtual IP. This VIP cannot conflict with any other IP + Port already being used. You can use an existing VIP if the VIP is not already listening on UDP 1812.
- Enter 1812 as the Port. Click OK.
- In the Services and Service Groups section, click where it says No Load Balancing Virtual Server ServiceGroup Binding.
- Click the arrow next to Click to select.
- Select a previously created Service Group and click OK.
- Click Bind.
- Click OK.
- Configuring RADIUS Load Balancing with Persistence at Citrix Docs recommends Rule Based Load Balancing. On the right, in the Advanced Settings column, add the Method section.
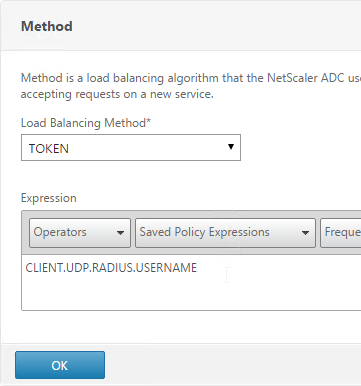
- Change the Load Balancing Method to TOKEN.
- In the Expression field, enter UDP.RADIUS.USERNAME and click OK.
- Click Done to finish creating the Virtual Server.
- If you are configuring this RADIUS Load Balancer for more than just NetScaler Gateway, you can add another Load Balancer on port 1813 for RADIUS Accounting. Then you need a Persistency Group to tie the two load balancers together. See Configuring RADIUS Load Balancing with Persistence at Citrix Docs.
add lb vserver lbvip-RSA RADIUS 10.2.2.210 1812 -persistenceType RULE -lbMethod TOKEN -rule CLIENT.UDP.RADIUS.USERNAME bind lb vserver lbvip-RSA svcgrp-RSA
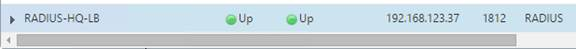
- The new Virtual Server should show as Up.
- Create additional Virtual Servers for each datacenter. These additional Virtual Servers do not need a VIP so change the IP Address Type to Non Addressable. Only the first Virtual Server will be directly accessible.
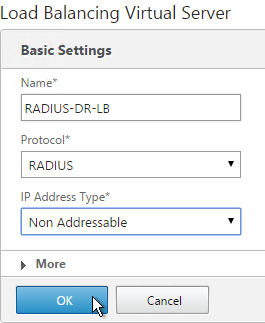
add lb vserver lbvip-RSA-Backup RADIUS 0.0.0.0 0 -persistenceType NONE -cltTimeout 120
- Notice that the additional datacenter Virtual Servers show up with an IP Address of 0.0.0.0 and port of 0.
- After you are done creating a Virtual Server for each datacenter, right-click the primary datacenter’s Virtual Server, and click Edit.
- On the right, in the Advanced column, click Protection.
- On the left, in the Protection section, change the Backup Virtual Server to one of the other datacenter Virtual Servers. If all of the services in this datacenter are DOWN, the backup Virtual Server will be used instead. You can cascade multiple Virtual Servers using this method. Click OK and Done.
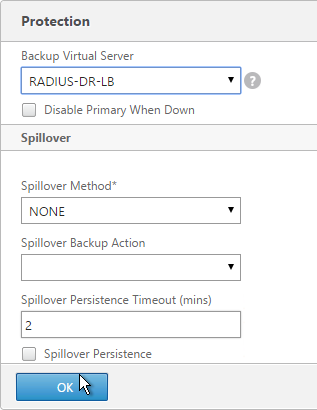
set lb vserver lbvip-RSA -backupVServer lbvip-RSA-Backup
- You may now use this Virtual IP in your RADIUS authentication policies for NetScaler Gateway or NetScaler management login.
Hey Carl,
I would like to ask a question about Radius and snips. I have created the loadbalancer with my VIP IP and setup all the ports however when pointing my Radius setup to this VIP it does not seem to work against the backend server. However If I use the NSIP it works without an issue.
I read this on a different page posted by your self:
“By default, NetScaler uses NSIP to communicate with RADIUS. You need to add the NSIP as the RADIUS Client and Authentication Host.
You can force the NetScaler to use SNIP instead of NSIP if you create a local load balancing vServer and then configure your RADIUS policy to use the local LB vServer. In that case the SNIP needs to be added as the RADIUS Client and Authentication Host. You can use Net Profiles to control which SNIP is used by the LB vServer.
In no case is the VIP used as the source IP. It is always NSIP or SNIP.”
where you say the SNIP needs to be added as the RADIUS Client and Authentication Host, Do you mean that should be the IP of the loadbalancer? Or do you mean something else? How do I set this up?
Thanks
RADIUS servers require RADIUS clients to be registered with them. When load balancing, the ADC SNIP is the RADIUS Client IP address.
When ADC load balancing communicates with a back-end server, ADC looks in its routing table for the next hop to reach the server. ADC then selects a SNIP on the same subnet as the next hop and uses the SNIP as the Source IP. The RADIUS server will see traffic coming from the SNIP.
Hey Carl,
So I have set the following up but it does not seem to communicate to the back-end server.
Radius server is set to receive comms from the SNIP address.
Netscaler has a LB with the VIP IP address, service is configured to use radius on the correct port, and has the service member of the Radius server.
When I do a test it says:
Server ‘VIP’ is reachable.
Either ‘VIP’ is not a valid Radius server
‘1812/udp’ is not a valid Radius authentication port or Radius client is not configured properly in the Radius server.
I have used the same VIP address as the Authentication server – Could that cause the issue? But the Radius is listening on a different port. I have had this issue and never been able to solve it.
The Radius logs does not show any communications coming in so it looks like the netscaler never sends over the request.
Thanks
Ignore my last I had to set a network profile for this to work. That fixed it.
Thanks
Carl good time..
i can’t understaund what is a RSA console and what is a RSA User?
i use Windows 2012 R2 NPS server with Active directory. i try to make wifi radius auth on our company. with one NPs it is as well but after i want use loadbalanser with netscalr my radius servers… this thoughts converted to nightmare.. i create cervice account and neverexpire password, fill this useracc and password plus radius client password on monitor, configure servers group server and loadbalanser virtual server… and now monitor cant login and user cant auth on wifi… of couse wifi controller ask domain login and password of user that joined to group and that group added to network policy with nap-wireless.
Network Policy Server denied access to a user.
Contact the Network Policy Server administrator for more information.
User:
Security ID: ALT\svc-wifi
Account Name: ALT\svc-wifi
Account Domain: ALT
Fully Qualified Account Name: ALT/Service accounts/svc-wifi
Client Machine:
Security ID: NULL SID
Account Name: –
Fully Qualified Account Name: –
OS-Version: –
Called Station Identifier: –
Calling Station Identifier: –
NAS:
NAS IPv4 Address: 172.29.129.125
NAS IPv6 Address: –
NAS Identifier: –
NAS Port-Type: –
NAS Port: –
RADIUS Client:
Client Friendly Name: smr-lm01
Client IP Address: 172.29.129.125
Authentication Details:
Connection Request Policy Name: Use Windows authentication for all users ( this connection request to has different name… why lb transefer to use that..
Network Policy Name: Connections to other access servers (My policy has different name, why lb catch this one…)
Authentication Provider: Windows
Authentication Server: msk-dc01.alt.local
Authentication Type: PAP
EAP Type: –
Account Session Identifier: –
Logging Results: Accounting information was written to the local log file.
Reason Code: 65
Reason: The Network Access Permission setting in the dial-in properties of the user account in Active Directory is set to Deny access to the user. To change the Network Access Permission setting to either Allow access or Control access through NPS Network Policy, obtain the properties of the user account in Active Directory Users and Computers, click the Dial-in tab, and change Network Access Permission.
have to choose different variant of Policy
thank you.
When you view the Monitor Details, what does it show as the return code?
“The Network Access Permission setting in the dial-in properties of the user account in Active Directory is set to Deny access to the user.”
I was solve problem, write about it in preveious post;) code 2 showing now;)
i’ll found resolv by myself %)
configure in conditions Nas ipv4 Address of my netscaler subnet IP and nas identifier from nps and thetn create monitor and get
Network Policy Server granted full access to a user because the host met the defined health policy.
Hi Carl, I have a question.
Do you have encounter a situation, radius server ip and NSIP are in different subnet, and everything works well.
When I configure a SNIP which has same subnet as radius server ip, NS will not send Radius request to radius server when I do the same login action?
SNIPs only apply if you are load balancing RADIUS. Otherwise it’s NSIP.
SNIPs can only be created on locally connected subnets. If RADIUS server is on a remote subnet, then create a static route using a router on one of your local subnets. A SNIP on the same subnet as the router will be used.
Well, Radius Server is in their internal network, and we want to apply a SNIP with same subnet as Radius Server to connect. But when we deploy this SNIP bind with vlan and interface, it will not send Radius request while we input token.
That’s really strange, we have created a service to 1812 and it is up, we dont know why it does not send request to backend server.
Are you load balancing RADIUS? Then did you configure the RADIUS policy to send RADIUS requests through the RADIUS load balancer?
You can run nstcpdump.sh port 1812 to see the RADIUS traffic.
Thanks for your reply, it recover good when next remote support. That’s strange. Anyway, thanks, could you leave some contact methods for further communication?
It recover work next remote support…. I think it may some network issue for freebsd level
Thanks anyway.
Dear Carl,
I have gone thru the step-by-step configuration. I have created an account in the RSA Server and assigned a fixed passcode. My monitor configured with fixed passcod. My monitor showing as down and the response is “Failure – Radius response code 11 received”
I think response 11 means RADIUS Challenge. In other words, RSA is asking the user for more information. You’ll need to check your RADIUS config to determine what it’s asking. Or try to login to a different RADIUS client using that ID and see what challenge it shows you.
A tip to investigate further more on your response code 11. You could try to use NTRadPing utility . Surf on the net and download it. You can test your challenge request/response with your radius server. Don’t forget to set at minum the radius server and port, the Radius secret key , the username and the password. For request type choose Authentication-Request.
Carl, How can you force the netscaler to bypass the radius authentication if both nodes of the load-balanced radius config are down?
I don’t think that’s possible.
Hi Carl , great article.
I would like to contribute to your documentation . My enviroment is , two Radius RSA in active/passive mode. One VIP to lb both of RSA. So under the LB Method section change the Method to Token and in the Rule box enter CLIENT.UDP.RADIUS.USERNAME and under the Persistence section change the Persistence to RULE and in the Expression enter CLIENT.UDP.RADIUS.USERNAME. These settings for me works well and i can see the incoming request going to both of RSA.
Hi, Carl!
Once again I’m having to mooch off your ~vast~ know-how of all things NetScaler – one day maybe I’ll actually get to contribute back! 🙁
Til then, a question: You didn’t really tackle the topic of persistence here, and I’m a little confused on whether Citrix’s docs are saying to evaluate the RADIUS username as part of the token in the Method or as part of the rule for persistence… or both? Also, I’ve noticed there’s a service type of “RADIUSListener,” but I’m not finding any real description of what it is or when/why to use it – any insights there?
I’m taking my first stab at load balancing some Cisco ISE appliances, in case that’s helpful. The plan is to get the test LB RADIUS 1812 and RADIUS AUTH 1813 VIP’s set up with basic settings, enable USIP on them, and see what happens.
Thanks!
I usually only use NetScaler as my RADIUS client. The other persistence/method settings are for other RADIUS clients that are using NetScaler to load balance RADIUS servers.
Hey Josh, did you ever get load balancing to work with your ISE appliances? I am starting to go down that road now and any info would be helpful.
Ben or Josh did you guys get this working? I’m having issues getting CoA to work.
With Netscaler 11. I am finding the opposite behavior in traces. Load balanced radius traffic appears to source from the NSIP, and non-load balanced appears to source from the SNIP.
In my opinion there is one fact missing here (at least if the RSA Active / Passive Cluster is identicaly confgured as ours are). Our RSA Cluster has a 15 min sync lag between the two systems in the Cluster using the RADIUS-protocoll (which occures only using RADIUS, but not using native RSA-protocoll accoring the RSA-Admins). Thus it is not smart to bind them together to one loadbalancer (even not with the correct affinity and loadbalance algorythms).
Using this it is difficult for support staff to analyse the RSA logs (well, they don’t now on which RSA system the authentication was done).
I am using one loadbalancer using only one RSA target server (the RSA-Master), and one loadbalacer as backup loadbalancer with the passive RSA-System. This solved me a lot of authentication tickets from the support. Of course I have to change the RSA-Systems on the loadbalancers when the RSA-Admins are changing the passive to the active. But this is not done by them often. In my opiniton, it is worth to anyone having problems with RSA to doublecheck if he has not the same issue. I did not find this fact anywhere in the internet. But for shure for us binding two RSA servers together to one loadbalancer is simply false.
Hi Carl,
I am having trouble with the RADIUS monitor and I think it is because I am using the wrong account. Should I be using a domain account? Do I need to put the domain in front of the user name if so? domain\user
Any help regarding what type of account I should be using for the monitor is appreciated.
What account is your RADIUS server expecting? What is the account database? If NPS then yes you need a domain account. If a two-factor authentication product then you need whatever account that product supports.
Sorry I should have mentioned I am using RSA SecurID Two Factor Authentication.
You need to add an account to RSA that has a static password. Then use that account. Or you can simply accept response code 3.
Hi Carl
Cool site you have here.
IMO there should be the token based LB method configured also.
If not you will get probmes with the users sinde the default method is leastconnection.
Perhaps I’ve read over it?
Thank you
Thanks for pointing this out. I found http://docs.citrix.com/en-us/netscaler/11/traffic-management/load-balancing/load-balancing-persistence/radius-persistence.html#par_richtext_1. For generic RADIUS load balancing it definitely makes sense but I’m not sure it’s needed for NetScaler Gateway. I’ll make a note in the instructions.
Carl, You have a great wealth of information proving to be very helpful. Thank you so much.
I do have a problem I’m trying to resolve. From the “Release Notes for Build 56.12 of NetScaler 10.5 Release” Im seeing this issue “The RSA Pin change fails if RSA radius servers are load-balanced with the RADIUS type protocol service.”
The workaround is to change the load-balance protocol service type to UDP or ANY.
Did you experience this problem in your setup? If so, do you suggest their workaround or another?
I have not see encountered this problem yet. If you are seeing it then you can try their workaround or call Support.
But what if your 2 radius servers are hosted by a third party with internet ip addresses ? The fact the netscaler uses the subnet ip address as the source address for radius authentication traffic means this solution will not work. The subnet ip address is not externally routeable as far as i know ???
You can configure the NetScaler to use any SNIP or NSIP as the source IP. For external, you can either configure a one-to-one NAT or you can use the default NAT’d IP. Then enter the NAT’d IP in your external RADIUS server as the RADIUS client.
To get the response code 2 working, you need to setup a user with a fixed passcode in your RSA console. Also ensure you login with that user at least once to the RSA console because youll be asked to change it the first time.
Also no need to assign a token to your monitor user as long as you are using a fixed passcode. You don’t want to waste a token on a user just for monitoring anyway.
That passcode needs to be input in the ns rsa monitor password field afterwards.
Since the Netscaler password field just says password with absolutely no explication its very confusing.
Added. Thanks.
I decided to do some digging to find out why I was getting access challenge 11 . I ran a trace and loaded it into wireshark, it turns out the radius server was requesting a new pin.
I then used a windows agent to test the connection and sure enough it requested a new pin. I decided to add a new pin and was informed to use pin + passcode on next login. When I tried this I got an authentication failure (passcode format error).
When you are told to add new pin you are actually resetting the passcode . rsa article number 000027160. I change the passcode on the monitor to the new pin and I am now getting access-accept 2.
If anybody is looking for this it might help.
Hi Carl
What did you configure on the RSA server to get this working? I followed the link above but I am getting access-challenge 11 not access-accept 2.
I usually configure the monitor to look for Response Code 3. I’m guessing 11 is also sufficient. If you’re getting something back then that means RADIUS is at least doing something.