Navigation
This article applies to StoreFront versions 2402, 2203 LTSR CU4, 1912 LTSR CU8 Update 1, and all other versions 3.5 and newer.
- Change Log
- StoreFront Versions
- StoreFront Installation / Upgrade
- Store Name – Rename
- SSL Certificate
- Base URL – Change
- Default Web Page
- Authentication Configuration
- Receiver for Web (browser interface)
- Favorites, Categories, and Default View – Default to Categories view instead of All
- Beacons
- Propagate Changes
- Export/Import StoreFront Configuration
- Logon Simulator
💡 = Recently Updated
Change Log
- 2024 April 24 – Deploy Workspace app – updated for Workspace app 2403 for Windows
- 2024 April 19 – Deploy Workspace app – updated for Workspace app 2402 for Mac
- 2024 April 18 – HTML5 Workspace app – updated with Workspace app for HTML5 version 2404
- 2024 April 17 – Updated Versions and Install sections for StoreFront 2402 LTSR
- 2024 Jan 24 – Versions – StoreFront security vulnerability
- 2023 Dec 20 – Next Generation Experience in StoreFront 2311
- 2023 Dec 20 – Citrix Workspace web extensions at Citrix Docs
- 2023 Dec 6 – Updated Versions section for StoreFront 2203 LTSR CU4 Update 1
- 2023 Sept 11 – Updated Versions and Install sections for StoreFront 1912 LTSR CU8
- 2023 June 5 – added link to CTX559036 Storefront 2302 CU2 – All Apps are now showing on initial landing page instead of categories view.
- 2022 July 9 – updated Versions section with 3.12.9000 (from 7.15 LTSR Cumulative Update 9)
- 2022 Apr 21 – Updated Versions and Install sections for StoreFront 2203 Hotfix 1
- 2022 Mar 30 – CTX399424 Gateway Callback and / or XML Communication fails after upgrade to Storefront 2203 for a workaround.
- 2022 Mar 27 – Updated Versions and Install sections for StoreFront 2203 LTSR
- Apps tab – uncategorized applications in CU5
StoreFront Versions
The most recent StoreFront release is version 2402.
- Starting with version 1811, the version numbering changed to a YYMM (year/month) format.
- Versions 2402, 2203, and 1912 are Long Term Service Releases (LTSR).
The default user interface in StoreFront 1811 and newer is now the “purple” interface, which is different from versions 3.16 and older. Be aware of this change before you upgrade StoreFront. Customizations might not work in the new interface. There doesn’t appear to be any way to revert to the older user interface. The Next-gen experience in 2311 and newer is not enabled by default but can be enabled manually.

Download one of the following versions of StoreFront. For LTSR versions of Citrix Virtual Apps and Desktops (CVAD), deploy the StoreFront that comes with your version of LSTR CVAD.
- Download StoreFront 2402 LTSR. StoreFront 2311 and StoreFront 2308.1 and later fix a security vulnerability.
- For CVAD 2203, download StoreFront 2203 LTSR CU4 Update 1. StoreFront 2203 LTSR CU4 Update 1 and later fix a security vulnerability.
- For CVAD 1912 LTSR, download StoreFront 1912 LTSR CU8 (Cumulative Update 8) Update 1. StoreFront 1912 LTSR CU8 hotfix 3.22.8001.2* and later fix a security vulnerability.
StoreFront Installation / Upgrade
For small environments, it might be OK to install StoreFront on the Delivery Controller machines. But usually StoreFront and Delivery Controllers are separate machines.
- If StoreFront will pull icons from multiple Citrix Virtual Apps and Desktops sites/farms, then StoreFront should be installed on its own machines.
To automate the installation of StoreFront, see Dennis Span Citrix StoreFront unattended installation with PowerShell.

The default user interface in StoreFront 1811 and newer is now the “purple” interface, which is different from versions 3.16 and older. Be aware of this change before you upgrade StoreFront. There doesn’t appear to be any way to revert to the older user interface.

Citrix Blog Post StoreFront 3.0 Scalability recommends StoreFront servers to be sized with 4 vCPU and 8 GB RAM.
- If upgrading, do the following before beginning the upgrade:
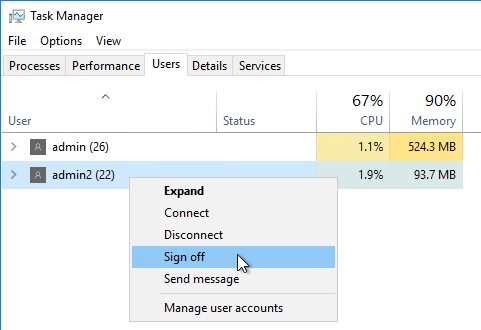
- Other Users – Use Task Manager > Users tab to logoff any other user currently logged into the machine.
- Export the StoreFront configuration so you can restore it if something goes wrong.
- Stop the World Wide Web Publishing Service.
- Stop all StoreFront services.
- Close all PowerShell and StoreFront consoles.
- Citrix CTX226419 StoreFront upgrade fails to keep the setting in default ICA file. Take a backup of default.ica and usernamepassword.tfrm from C:\inetpub\wwwroot\Citrix\StoreName\App_Data. After upgrading StoreFront, replace the new default.ica and usernamepassword.tfrm with the old default.ica and usernamepassword.tfrm files to ensure you retain the old settings.
- If Microsoft SCOM Agent is installed, then stop the Microsoft Monitoring Agent service.
- See Patrick van den Born Avoid 1603 errors when upgrading Citrix StoreFront 2.x to Citrix StoreFront 3.5
- Other Users – Use Task Manager > Users tab to logoff any other user currently logged into the machine.
- Operating system support:
- StoreFront 2203 and newer are supported on Windows Server 2022.
- StoreFront 2203 is not supported on Windows Server 2012 R2.
- StoreFront 1912 and newer are supported on Windows Server 2019.
- Run CitrixStoreFront-x64.exe from the CVAD ISO at /x64/StoreFront. Or download it separately.
- In the License Agreement page, check the box next to I accept the terms, and click Next.
- In the Review prerequisites page, click Next.
- In the Ready to install page, click Install.
- In the Successfully installed StoreFront page, click Finish.
- Click Yes if prompted to reboot.
- FAS – If you upgraded a StoreFront server that was connected to Citrix Federated Authentication Service (FAS), then also upgrade Citrix Federated Authentication Service.
If this is a new install, skip to the Initial Configuration.
If you are upgrading from StoreFront 3.8 or older, then do the following to add SAML Authentication as an option. This feature lets you perform SAML against StoreFront without needing Citrix Gateway. If you did a fresh deployment of 3.9 or newer, then SAML is already added.
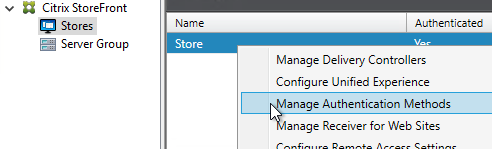
- Right-click your Store, and click Manage Authentication Methods.
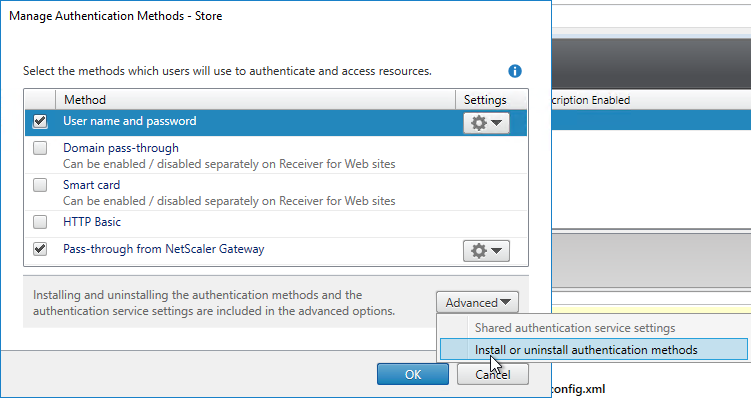
- On the bottom, click the Advanced button, and click Install or uninstall authentication methods.
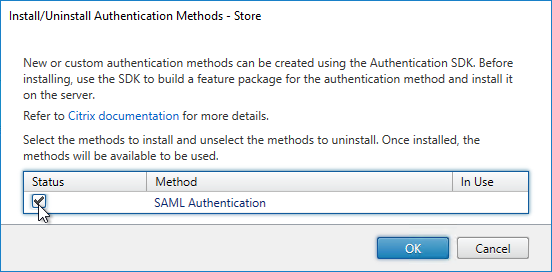
- Check the box next to SAML Authentication, and click OK.
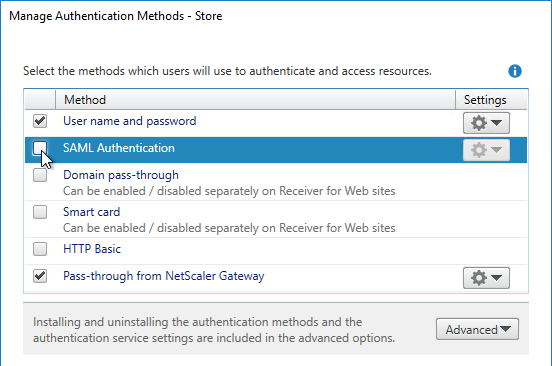
- If you don’t want to configure SAML at this time, then uncheck the authentication method. See the Federated Authentication Service article for SAML details.
Initial Configuration
In StoreFront 3.8 and newer, you can create multiple stores in different IIS websites. This functionality is not exposed in the GUI and instead the entire StoreFront configuration must be performed using PowerShell. See Citrix Blog Post StoreFront 3.8 is Available NOW! for sample PowerShell commands to create the stores.
You can also use PowerShell to create a store and configure it as detailed at CTX206009 How to configure a Store via Powershell.
If this is a new deployment of StoreFront, do the following to perform the initial configuration:
- In PowerShell, run Set-ExecutionPolicy RemoteSigned.
- The management console should launch automatically. If not, launch Citrix StoreFront from the Start Menu.
- In the middle, click Create a new deployment.
- In the Base URL page, if you installed an SSL certificate on the StoreFront server, then the Hostname should already be filled in. For now, you can leave it set to the server’s name and then change it later once you set up SSL and load balancing. Click Next.
- In the Getting Started page, click Next.
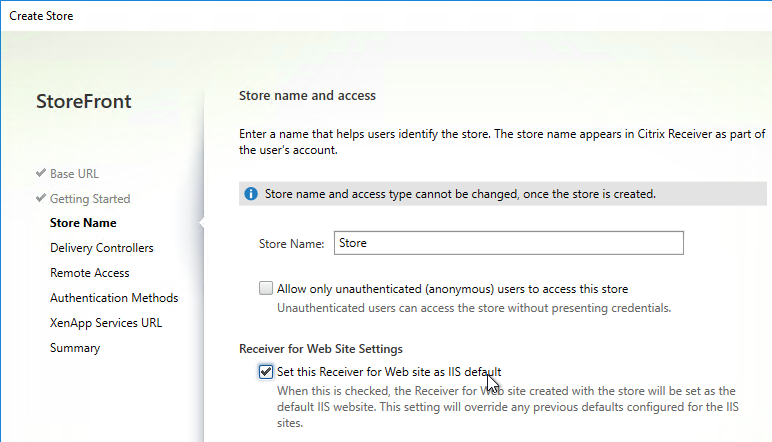
- In the Store Name page, enter a name for the store. The name entered here is part of the URL path (e.g. /Citrix/CorpStoreWeb)
- Check the box next to Set this Receiver for Web site as IIS default and click Next.
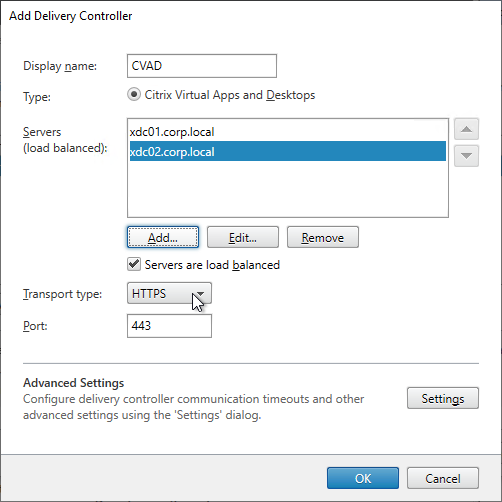
- In the Delivery Controllers page, click Add.
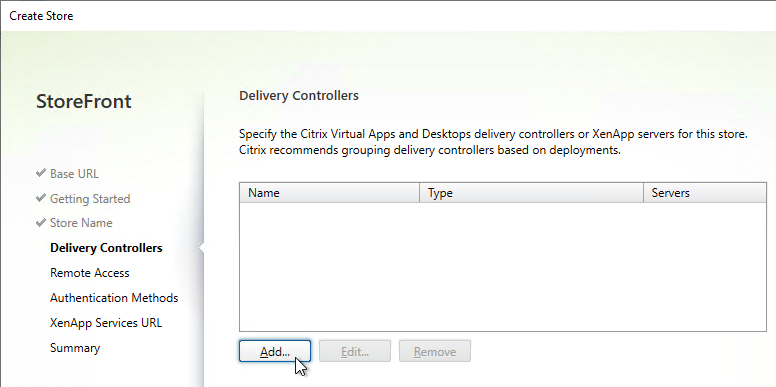
- Enter a descriptive name for the Citrix Virtual Apps and Desktops (CVAD). This name does not need to match the actual farm name.
- Add the two Delivery Controllers. Change the Transport Type to HTTP. Click OK. You can set it to HTTPS is you have valid certificates (trusted by StoreFront) installed on your Delivery Controllers.
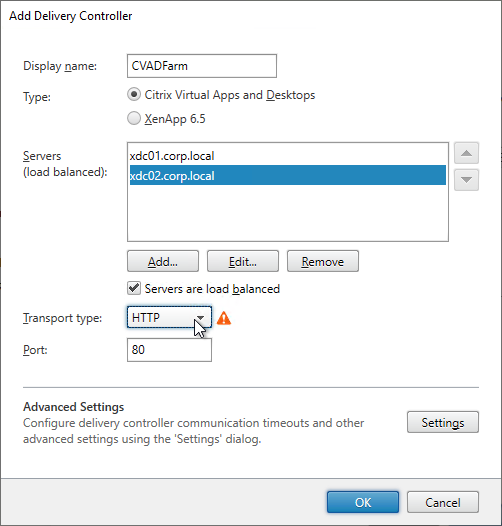
- If you have multiple Citrix Virtual Apps and Desktops sites/farms, feel free to add them now. You can also add older XenApp 6.5 farms. Click Next when done.
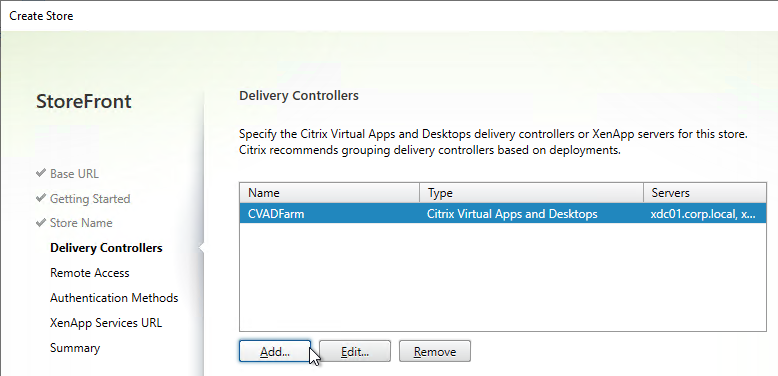
- In the Remote Access page, don’t check the box. Just click Next. You can set this up later.
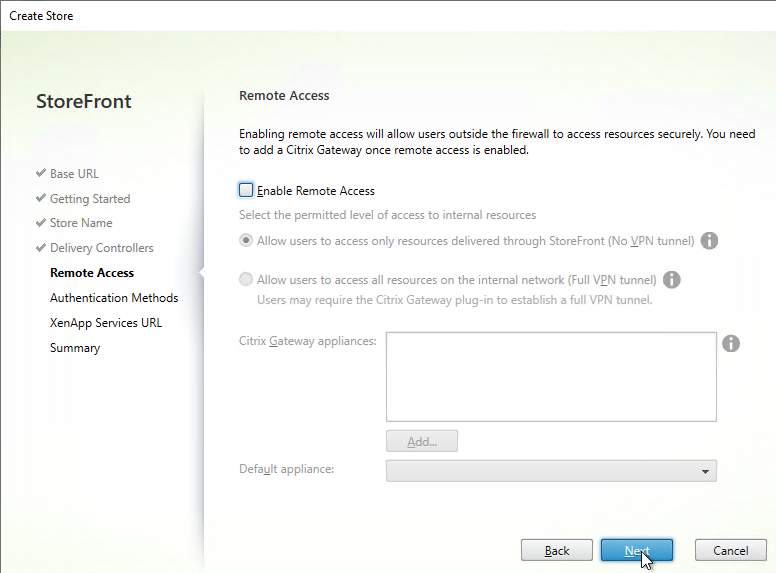
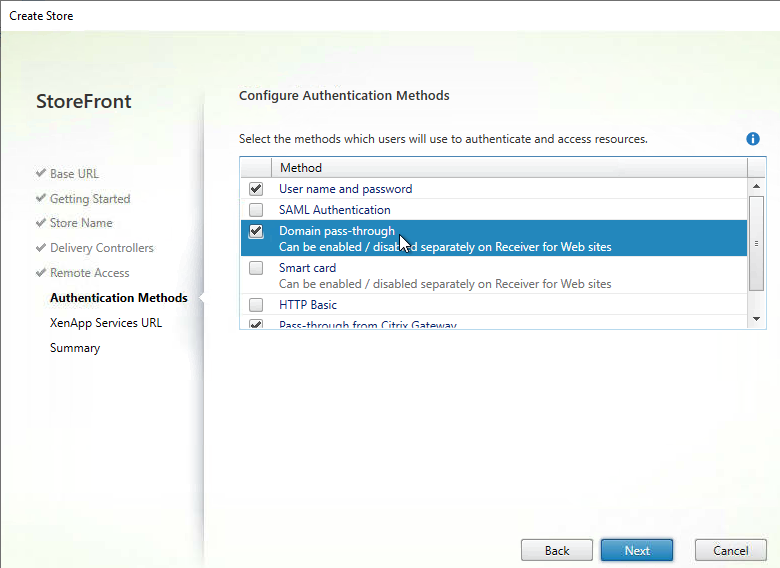
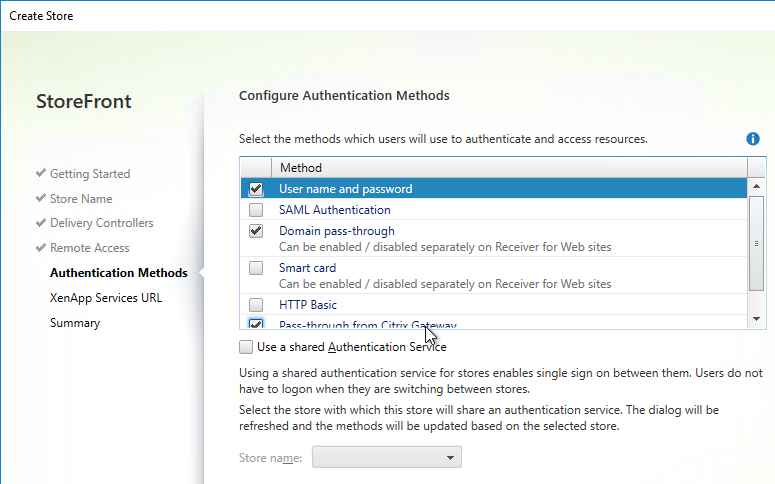
- In the Authentication Methods page, check the boxes next to Domain pass-through and Pass-through from Citrix Gateway. Click Next.
Note: if you want Domain pass-through authentication for browser users, you also need to enable it for Receiver for Web as detailed later in this article.
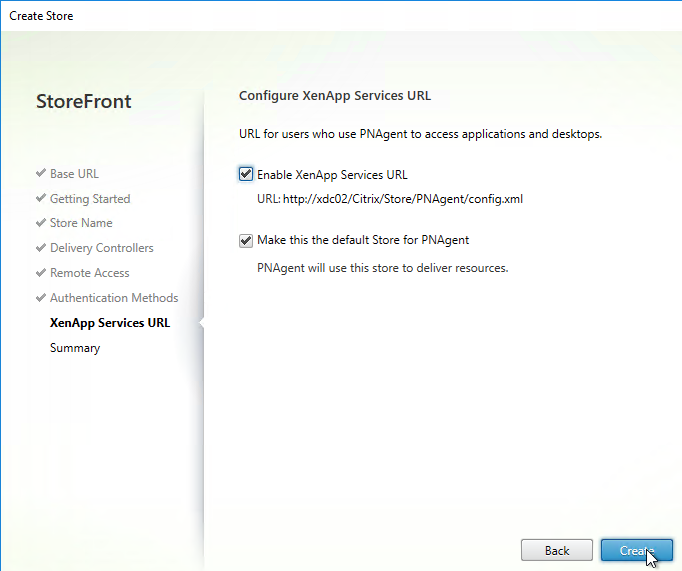
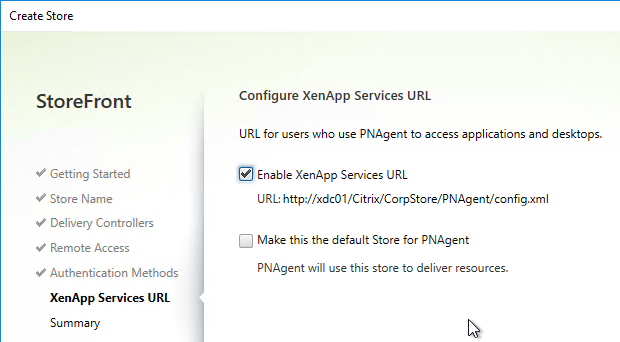
- In the XenApp Services URL page, click Create.
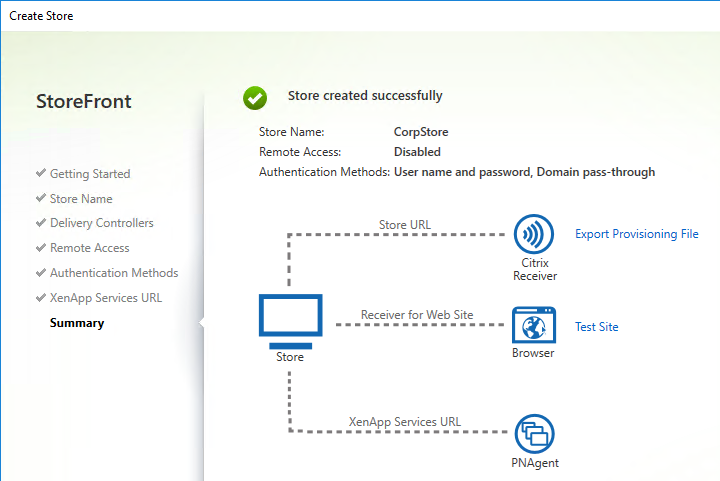
- In the Summary page, click Finish.
Second StoreFront Server
After the server group is created, NT SERVICE\CitrixConfigurationReplication and NT SERVICE\CitrixClusterService must remain in the Administrators group on both StoreFront servers or propagation will fail.
- Install StoreFront on the second server.
- Create/Import an SSL certificate and bind it to the Default Web Site.
- Login to the first StoreFront server. In the StoreFront management console, right-click Server Group and click Add Server.
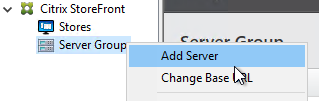
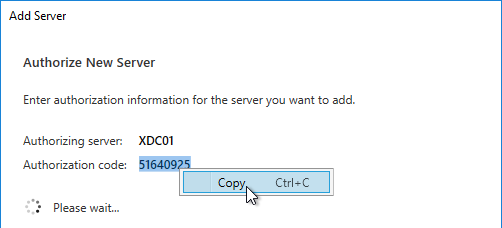
- Copy the Authorization code.
Note: the Please wait message means it is waiting on you to add the 2nd server. You don’t actually have to wait.
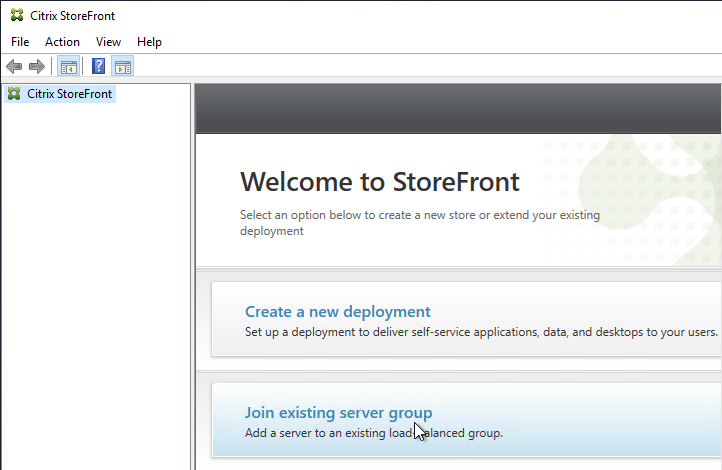
- Login to the second StoreFront server and launch the management console. In the middle, click Join existing server group.
- In the Join Server Group page, enter the name of the first StoreFront server and enter the Authorization code copied earlier. Click Join.
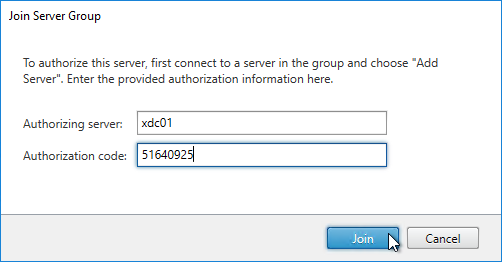
- Then click OK.
- Go back to the first server. Click OK.
- Notice this message. It is good advice.
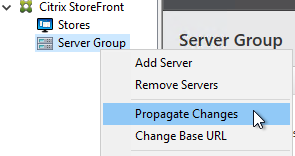
- All changes made on one StoreFront server must be manually propagated to the other StoreFront server. You do that by right-clicking Server Group, and clicking Propagate Changes.
- When you propagate changes, the default web page might not be replicated to the other nodes. Copy C:\inetpub\wwwroot\web.config manually to each node.
Customer Experience Improvement Program
StoreFront 3.9 and newer enable Customer Experience Improvement Program (CEIP) by default. To disable it, create the registry value HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Telemetry\CEIP\Enabled (DWORD) and set it to 0 (zero). Also see CEIP at Install, set up, upgrade, and uninstall at Citrix Docs.
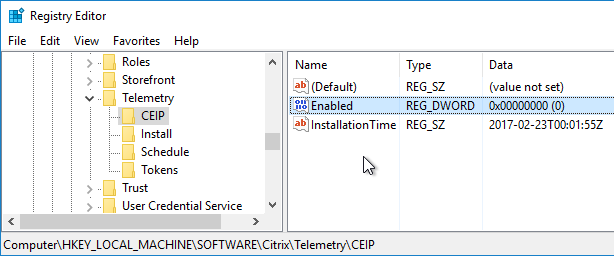
See https://www.carlstalhood.com/delivery-controller-2203-ltsr-and-licensing/#ceip for additional places where CEIP is enabled.
Citrix Analytics
StoreFront 1906 and newer supports uploading data to Citrix Analytics.
The client devices must be running Workspace app 1903 and newer.
See Enable Analytics on Virtual Apps and Desktops on-premises at Citrix Docs.
Store Name – Rename
If you installed StoreFront on your Delivery Controller, it will have a default store named Store. If you don’t like the default Store Name (/Citrix/Store) then you will need to remove the store and re-add it.
Note: Some at Citrix Discussions (A protocol error occurred while communicating with the Authentication Service) have reported authentication issues after following this procedure. It’s probably cleaner to uninstall StoreFront and reinstall it.
- In the StoreFront console, on the left, click Stores.
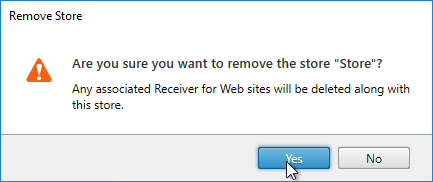
- Right-click your store, and click Remove Store.
- Click Yes.
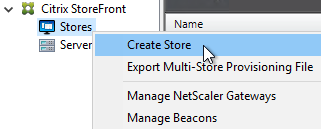
- On the left, right-click Stores, and click Create Store.
- In the Getting Started page, click Next.
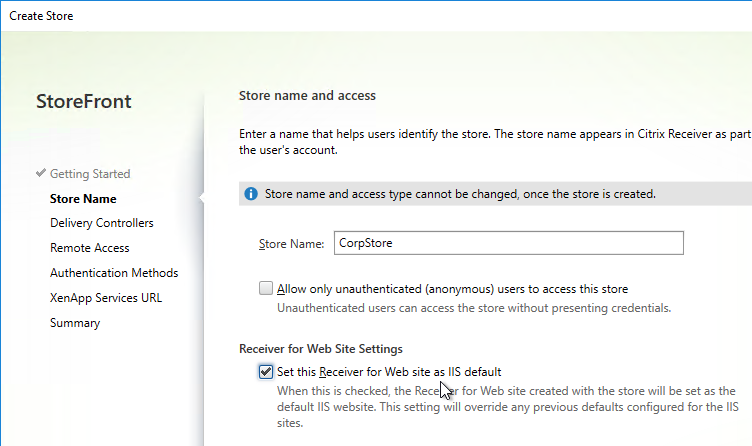
- In the Store Name page, enter a name for the store. The name entered here is part of the URL path (e.g. /Citrix/CorpStoreWeb).
- Check the box next to Set this Receiver for Web site as IIS default and click Next.
- In the Delivery Controllers page, click Add.
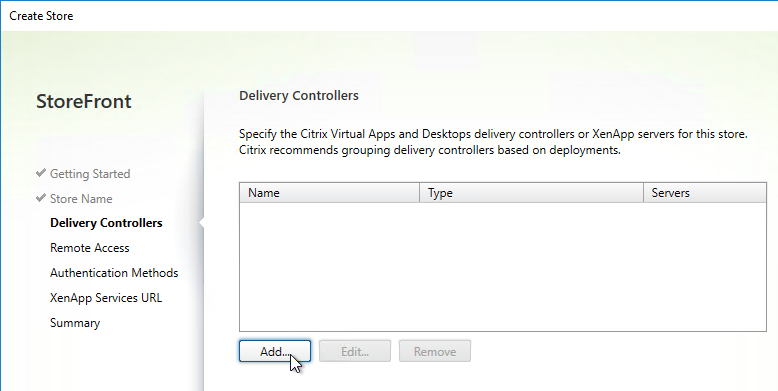
- Enter a descriptive name for the Citrix Virtual Apps and Desktops farm. This name does not need to match the actual farm name. (If StoreFront 3.5, don’t put spaces or periods in the farm name)
- Change the Type to XenDesktop or Citrix Virtual Apps and Desktops.
- Add the two Delivery Controllers.
- Change the Transport Type to HTTP. Click OK. You can leave it set to HTTPS (recommended) if you have valid certificates (trusted by StoreFront) on your Delivery Controllers.
- If you have multiple Citrix Virtual Apps and Desktops farms, feel free to add them now. You can also add older XenApp farms. Or later, you can add farms in Store > Manage Delivery Controllers. Click Next when done.
- In the Remote Access page, don’t check the box and click Next. You can set this up later.
- In the Authentication Methods page, check the boxes next to Domain pass-through and Pass-through from Citrix Gateway. Click Next.
- In the XenApp Services URL page, click Create.
- In the Created Successfully page, click Finish.
SSL Certificate
StoreFront requires SSL. You will save yourself much heartache if you install valid, trusted certificates on the StoreFront servers or your load balancer. There are two options for StoreFront SSL.
- SSL Offload: Use Citrix ADC to do SSL Offload and load balancing. In this scenario, install the SSL certificate on the load balancer. You can leave the StoreFront servers listening on HTTP and no IIS server certificate. The SSL certificate on the Citrix ADC must match the DNS name that resolves to the load balancing VIP.
- SSL End-to-end: Install an SSL certificate on each StoreFront server and bind it to IIS. This allows you to use SSL protocol between the load balancer and the StoreFront servers.
If your load balancer cannot terminate SSL, then the StoreFront IIS certificate must match the DNS name that resolves to the load balancing VIP.
For load balancers that can terminate SSL (e.g., Citrix ADC), the StoreFront IIS server certificate should match the StoreFront server name. If StoreFront is installed on the Delivery Controllers, with server-specific certificates you can later enable HTTPS in the StoreFront Store Delivery Controller configuration.
Another option is to create an SSL certificate with Subject Alternative Names for the load balanced DNS name and each of the StoreFront server FQDNs. Then import this one certificate on all StoreFront servers. Or a wildcard certificate could match all of these names.
In either case, be aware that Email-based discovery in Citrix Receiver requires the certificate to not only match the StoreFront load balanced DNS name but the certificate must also match discoverReceiver.email.suffix for every email domain. Usually, the only option to match multiple email domains is with Subject Alternative Names. If you have multiple email suffixes, then you will need multiple Subject Alternative Names, each beginning with discoverReceiver. If you don’t plan on implementing email-based discovery, then you don’t have to worry about these discoverReceiver Subject Alternative Names.
If the certificate does not match discoverReceiver.email.suffix, then users will see this message when attempting to use email discovery in Citrix Workspace app.
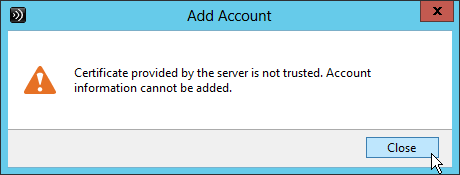
When adding Subject Alternative Names to a certificate, the first Subject Alternative Name should be the same as the Load Balancing FQDN. The remaining Subject Alternative Names should be discoverReceiver.email.suffix for every email domain.
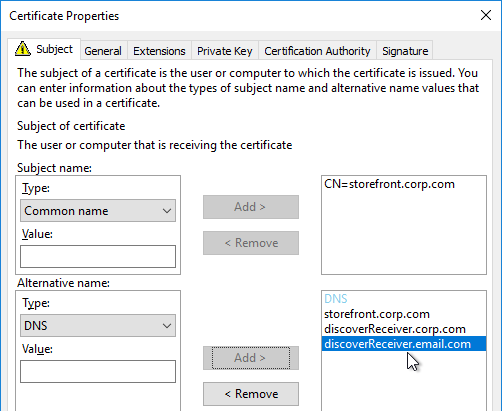
When you view a Subject Alternative Name certificate, on the Details tab, click Subject Alternative Name to verify that all names are listed including the DNS name that resolves to the load balancing VIP.
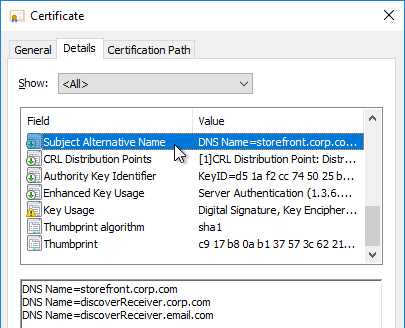
There are several methods of creating a certificate for StoreFront.
- If you are implementing Single FQDN for internal and external users, then the certificate for external Citrix Gateway can also be used for internal StoreFront.
- Single FQDN has additional Subject Alternative Name certificate requirements, including Internal Beacon FQDN and Callback FQDN.
- If you will support non-domain-joined machines (e.g., iPads, thin clients) connecting to your internal StoreFront, then the StoreFront certificate should be signed by a public Certificate Authority. You can use IIS to request the certificate. You can then export the certificate from IIS and import it to Citrix ADC (for Load Balancing and Citrix Gateway). Public Certificate Authorities (e.g., GoDaddy, Digicert, etc.) let you enter additional Subject Alternative Names when you purchase the certificate.
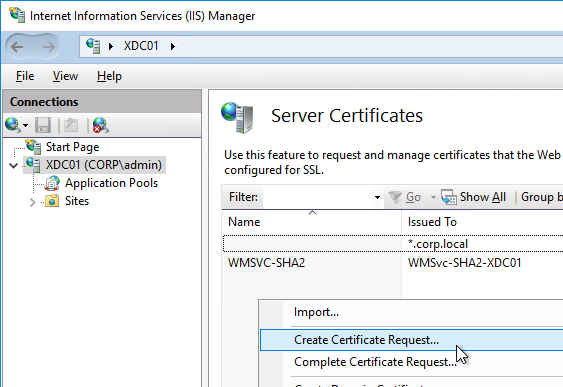
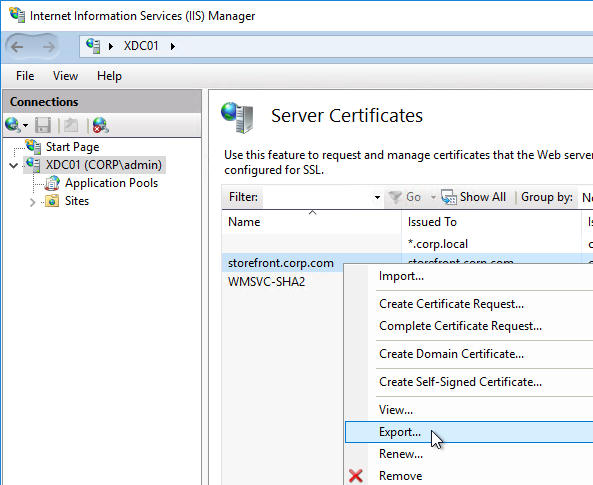
- If all internal machines are domain-joined, then you can use an internal Certificate Authority to create the StoreFront certificate. The Certificates MMC snap-in can be used to create an internal certificate signed by a Microsoft Certificate Authority. The MMC method allows you to specify Subject Alternative Names.

Once the certificate is created or imported, bind it to IIS:
- In IIS Manager, right-click the Default Web Site, and click Edit Bindings.
- Click Add.
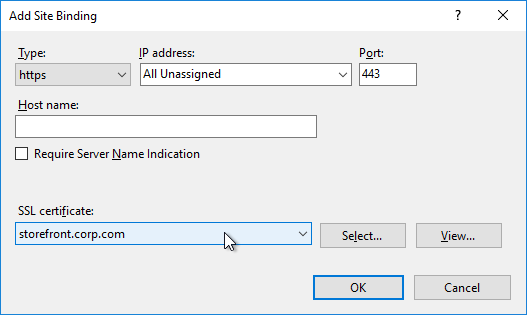
- Change the Type to https and select the SSL certificate. Do NOT put anything in the Host name field. Click OK, and then click Close.
Delivery Controllers – SSL
Delivery Controllers can be SSL enabled by using one of two methods:
- If IIS is installed on the Delivery Controller, simply install/create a certificate, and bind it to the Default Web Site.
- If IIS is not installed on the Delivery Controller, then you need to run a command line program as described at SSL for Delivery Controller.
Once SSL certificates are installed on the Delivery Controller servers, then you can configure the StoreFront Store to use SSL when communicating with the Delivery Controllers.
- In the StoreFront Console, on the left click Stores.
- In the middle, right-click your store, and click Manage Delivery Controllers.
- Highlight the deployment and click Edit.
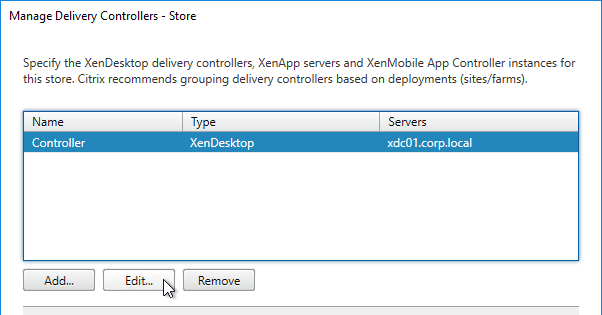
- The Servers list must contain FQDNs that match the certificates installed on those Delivery Controller servers.
- Change the Transport type to HTTPS.
- Click OK twice.
- See CTX399424 Gateway Callback and / or XML Communication fails after upgrade to Storefront 2203 for a workaround. The fix is included in StoreFront 2203.1.
Base URL – Change
- Configure load balancing of the StoreFront servers, including SSL certificate.
- In the Citrix StoreFront console, right-click Server Group, and click Change Base URL.
- Enter the StoreFront Load Balancing FQDN as the new Base URL in https://storefront.corp.com format.
- Receiver requires that the Base URL is https. It won’t accept http.
- If you want the StoreFront Base URL to be the same as your Gateway FQDN, then see the Single FQDN instructions.
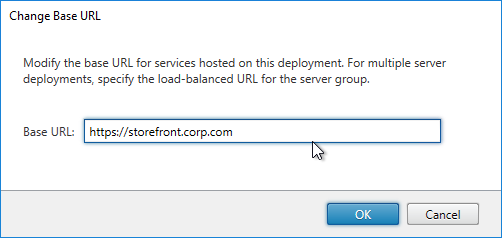
- Click OK.
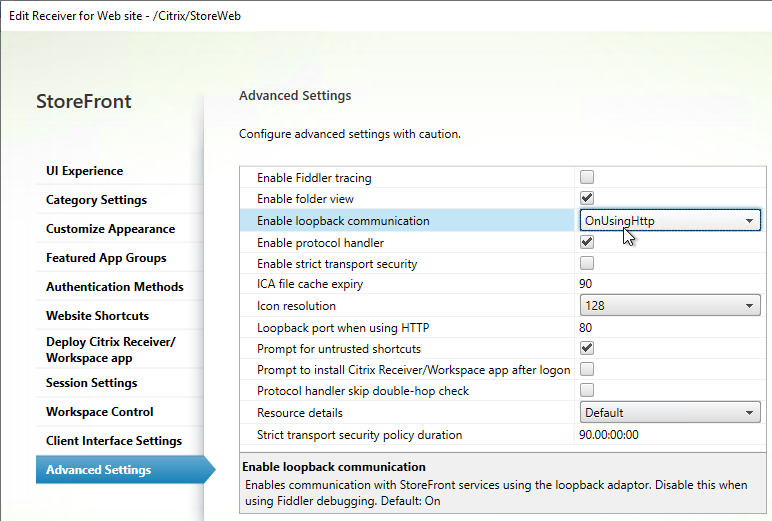
If the Base URL is https, but you don’t have certificates installed on your StoreFront servers (aka SSL Offload), then you’ll need to do the following:
- On the left, click the Stores node.
- In the middle, right-click your store, and click Manage Receiver for Web Sites.
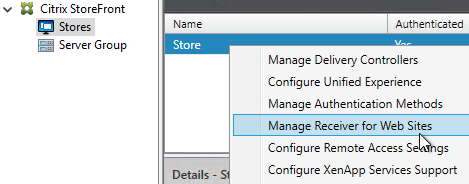
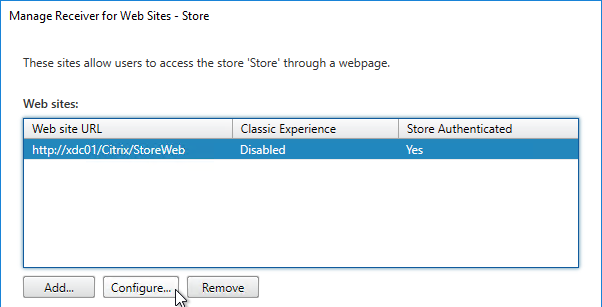
- Click Configure.
- On the Advanced Settings page, change Enable loopback communication to OnUsingHttp. Click OK, and then click Close.
Default Web Page
After changing the Base URL, you’ll need to update the IIS Default Website.
- On the left, right-click Stores, and click Set Default Website.
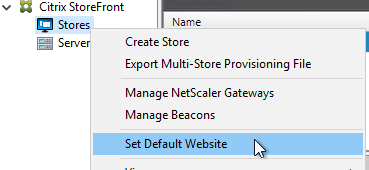
- Check the box next to Set a Receiver for Web site as the default page in IIS and click OK.
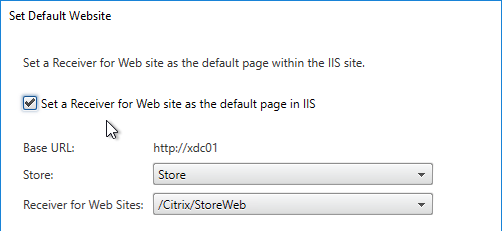
- Click Yes to overwrite.
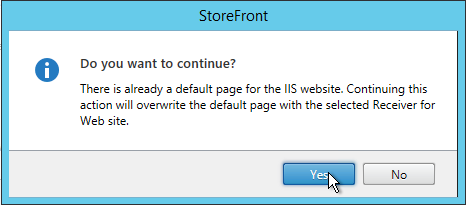
- If you go to C:\inetpub\wwwroot and edit the file web.config, you’ll see the redirect.

Authentication Configuration
- In the Citrix StoreFront console, on the left, click the Stores node.
- In the middle, right-click your store, and click Manage Authentication Methods.
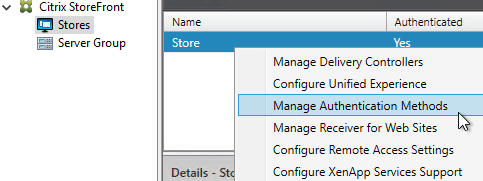
- Check the boxes next to Domain pass-through and Pass-through from Citrix Gateway.
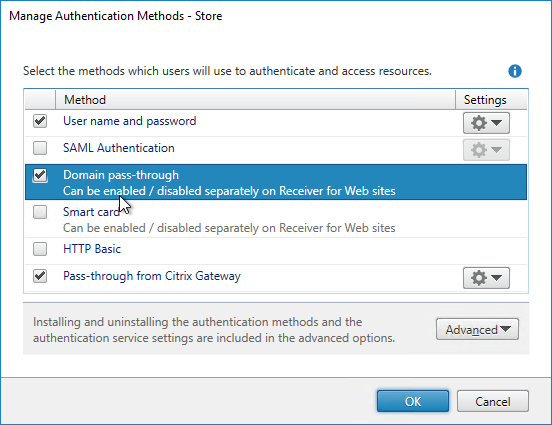
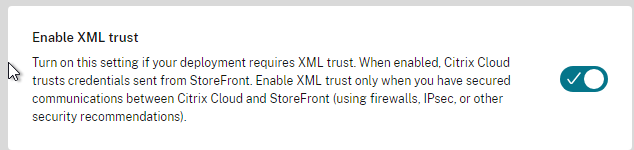
- If you intend to enable pass-through authentication from Receiver Self-Service (native Workspace app) or from Receiver for Web (web browser), then in Web Studio (CVAD 2212 and newer), go to Settings and Enable XML trust.
- Or go to a Delivery Controller and run the command
Set-BrokerSite -TrustRequestsSentToTheXmlServicePort $Truefrom a Windows PowerShell command prompt. You might have to runasnp citrix.*first.
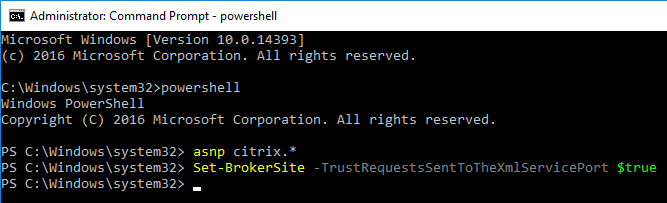
- Or go to a Delivery Controller and run the command
- If StoreFront is not in the same domain (or trusted domain) as the users, then you can configure StoreFront to delegate authentication to the Delivery Controllers. See XML service-based authentication at Citrix Docs.
- StoreFront 3.6 and newer can be workgroup members without joining a domain.
- Click the top gear icon, and then click Configure Trusted Domains.
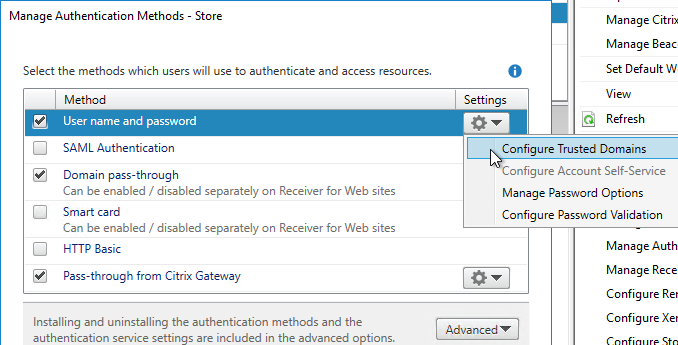
- Select Trusted domains only, click Add, and enter the domain names in DNS format. The DNS suffix is needed if doing userPrincipalName authentication from Citrix Gateway.
- Select one of the domains as the default.
- If desired, check the box next to Show domains list in logon page. Click OK.
- Click the top gear icon, and then click Manage Password Options.
- Make your selection, and click OK.
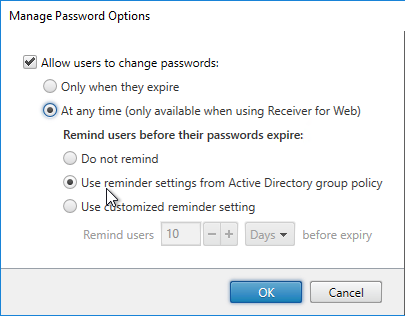
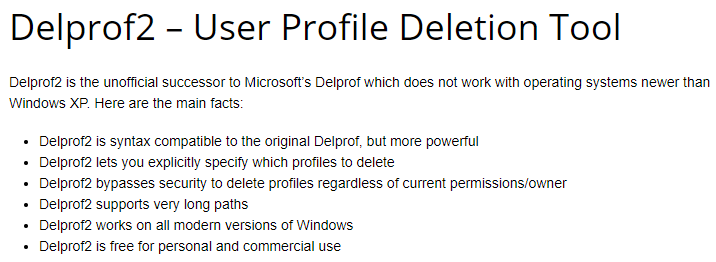
- Be careful with password changes. Any time somebody changes their password through StoreFront, a profile will be created for that user on the StoreFront server. Use a tool like delprof2.exe to periodically delete these local profiles.
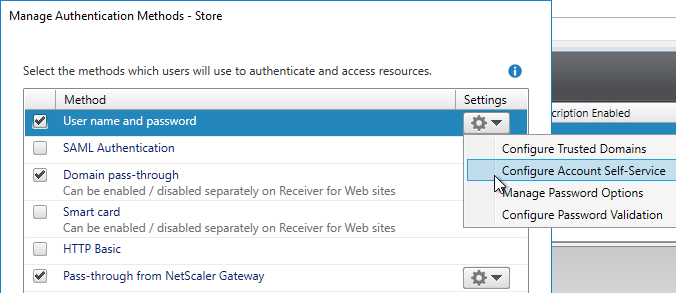
- If you have Citrix Virtual Apps and Desktops and installed Self-Service Password Reset, you can integrate SSPR with StoreFront 3.7 or newer by clicking the top gear icon and clicking Configure Account Self-Service. This option is only available if your Base URL is https (encrypted). See the following for detailed implementation guides.
- Citrix CTX217143 Self-Service Password Reset Central Store Creation Tool
- Citrix CTX224244 How Do I Deploy Self-Service Password Reset For the First Time
- George Spiers Citrix Self-Service Password Reset
- Change the selection to Citrix SSPR, and click Configure.
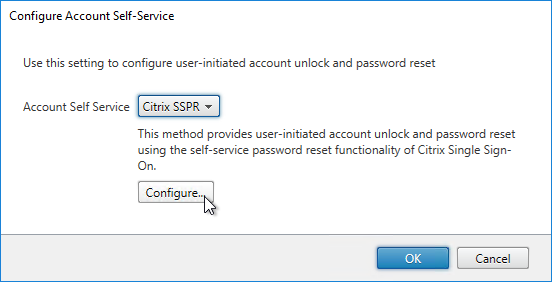
- Check both boxes and enter the URL of the SSPR server using the displayed example (with /MPMService on the end). Click OK three times.
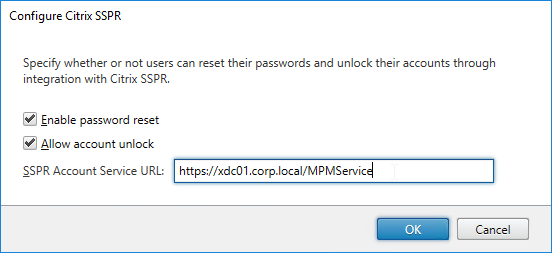
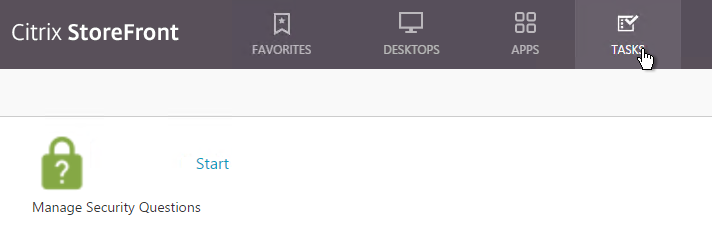
- With SSPR enabled, a new Tasks tab lets users enroll with SSPR.
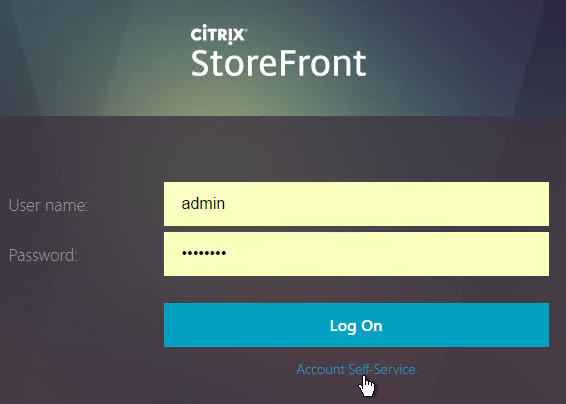
- The logon page also has an Account Self-Service link.
Next Generation Experience
In StoreFront 2311 and newer, you can do the following to enable the Next-gen experience theme, which looks the same as Workspace in Citrix Cloud, including the Activity Manager. 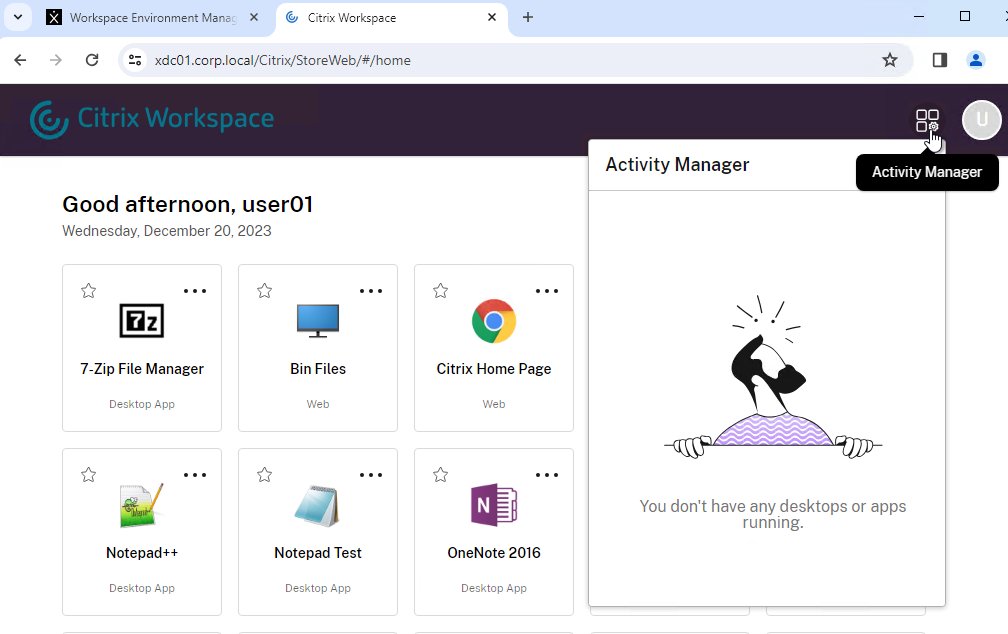
- In the StoreFront Console, on the left, click the Stores node.
- In the middle, right-click your store, and click Manage Receiver for Web Sites.
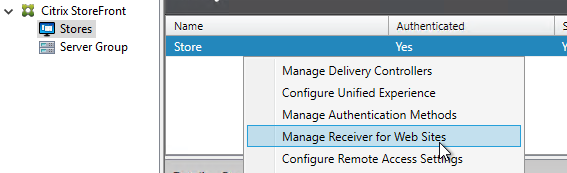
- Click Configure.
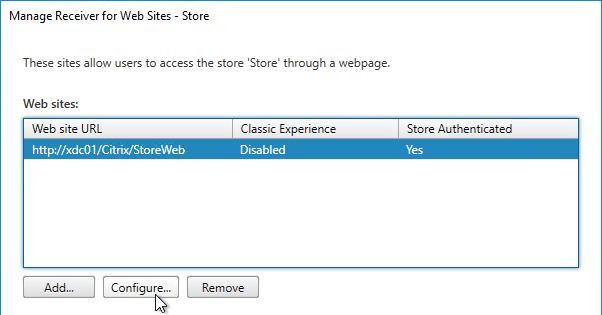
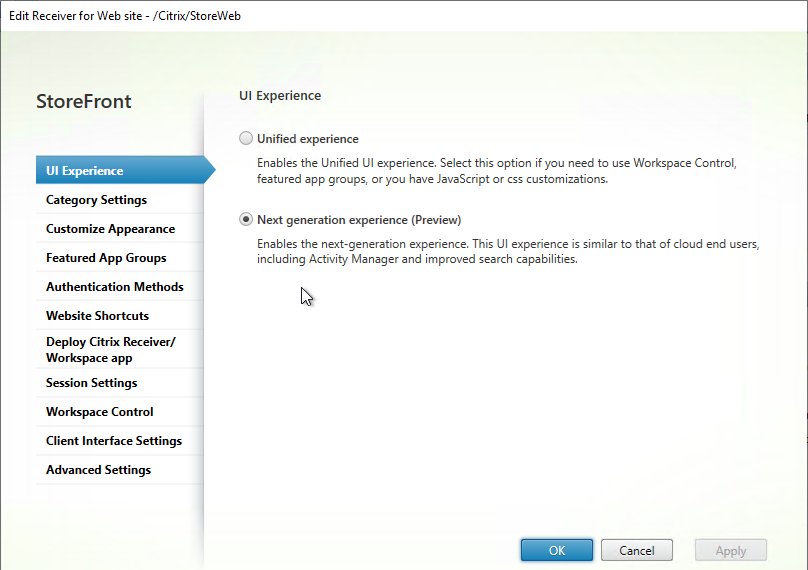
- On the UI Experience page, select Next generation experience and click OK.
Customize Receiver Appearance
You can go to Stores > Manage Receiver for Web Sites > Configure > Customize Appearance to change logos and colors. Additional customization can be performed using the SDK.
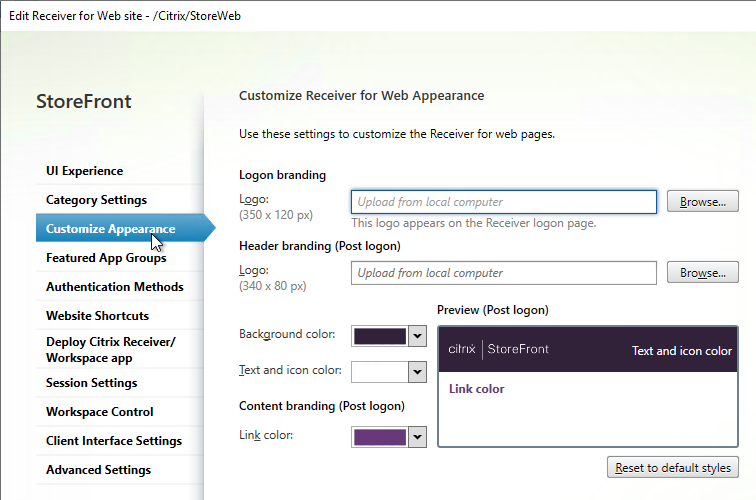
You can also Manage Featured App Groups.
In StoreFront 1811 and newer, Featured App Groups are shown in the user interface as Collections.
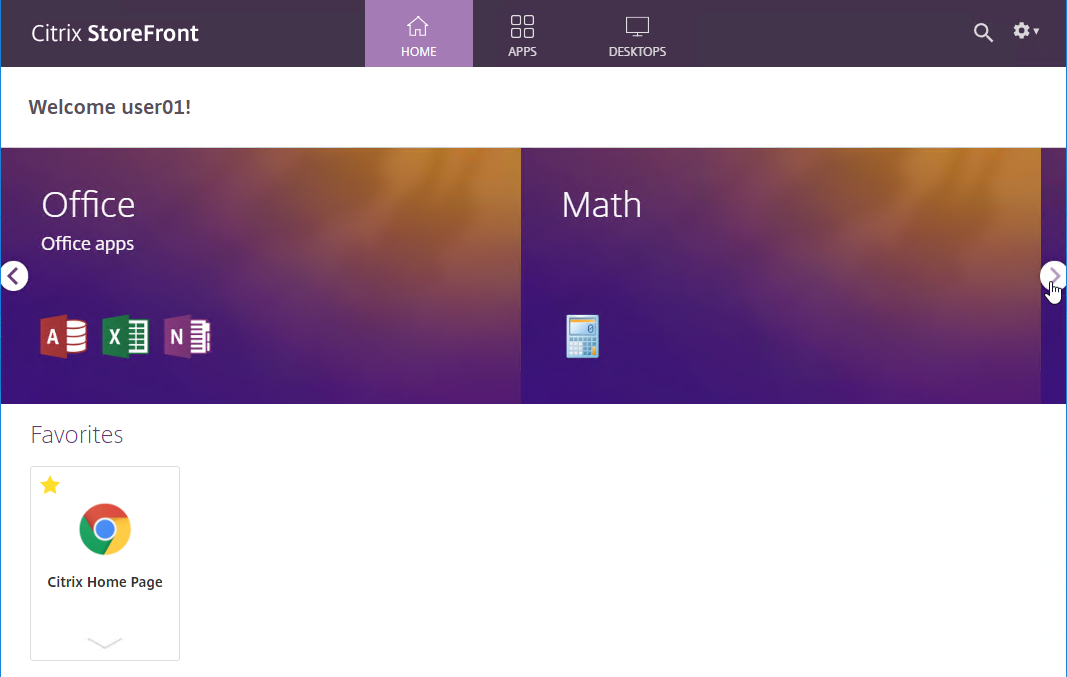
- The HOME page shows the Feature App Groups in a ribbon with arrows to let the user see more Featured App Groups. The ribbon view is limited to three icons per Featured App Group. When the user clicks a Featured App Group, every icon in the Featured App Groups is shown.
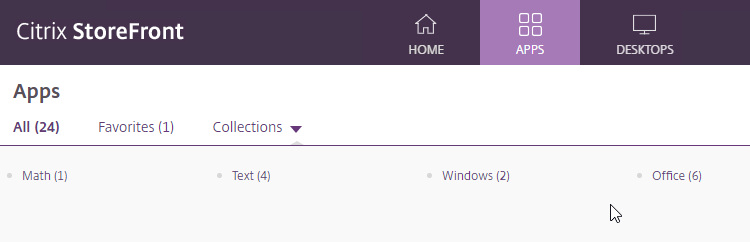
- The APPS page has a Collections tab showing all collections and the number of icons in each Collection.
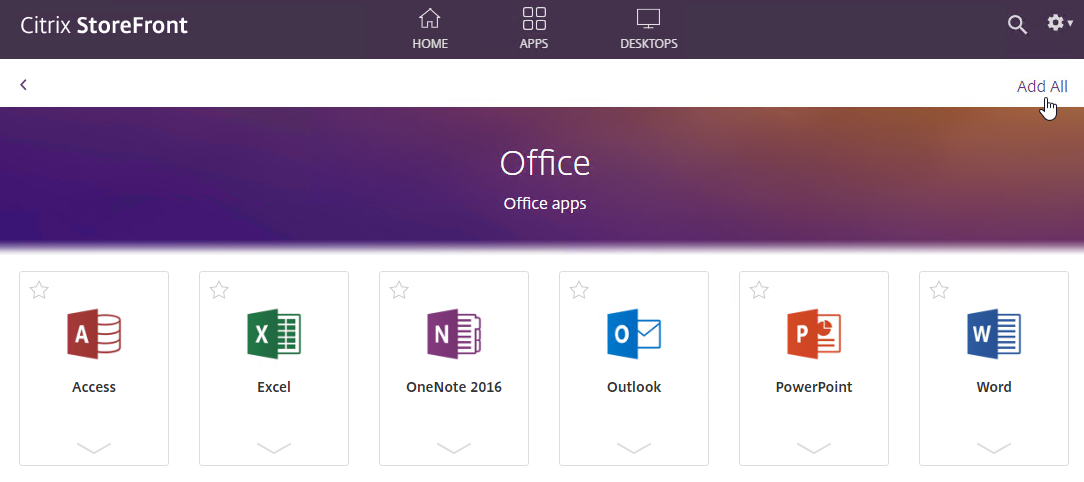
- When the user clicks a collection, all icons in the collection are shown. The user can click Add All on the top right to mark all of the icons as Favorites.
To create Featured App Groups:
- Go to Stores > myStore > Manage Receiver for Web Sites > Configure.
- In the Edit Receiver for Web site window, on the Featured App Groups page, click Create.
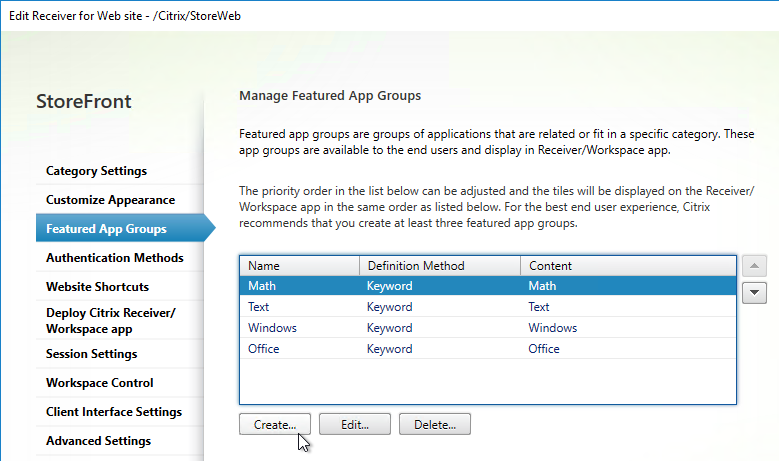
- Give the Collection a name and a description.
- At the bottom, there are three methods of adding icons to the Feature App Group.
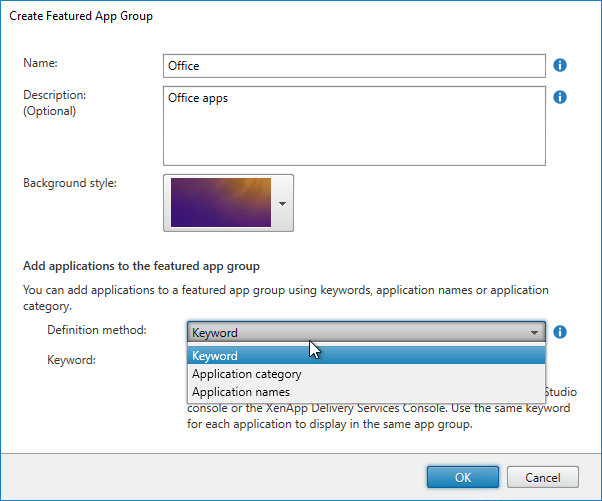
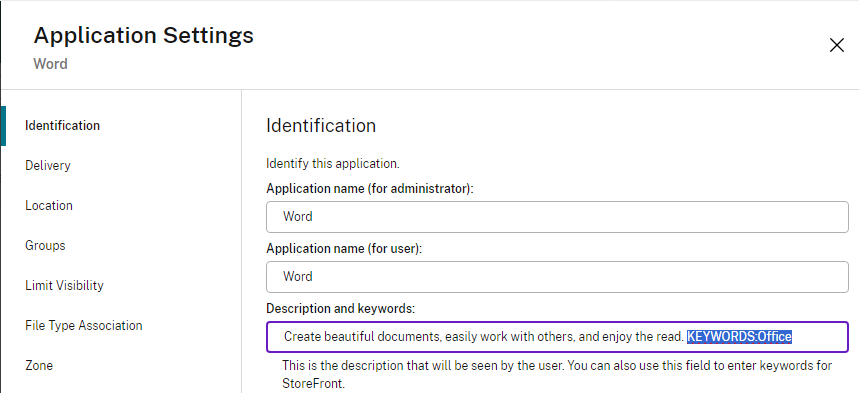
- If you select the Keyword option, then enter a keyword that will be added to the published apps that are in this collection.
- In Citrix Studio, go to the Properties of a published application. In the Description field, at the end, enter KEYWORDS:myCollectionKeyword.
In StoreFront older than version 1811:
- Featured App Groups are displayed at the top of the Apps > All page.
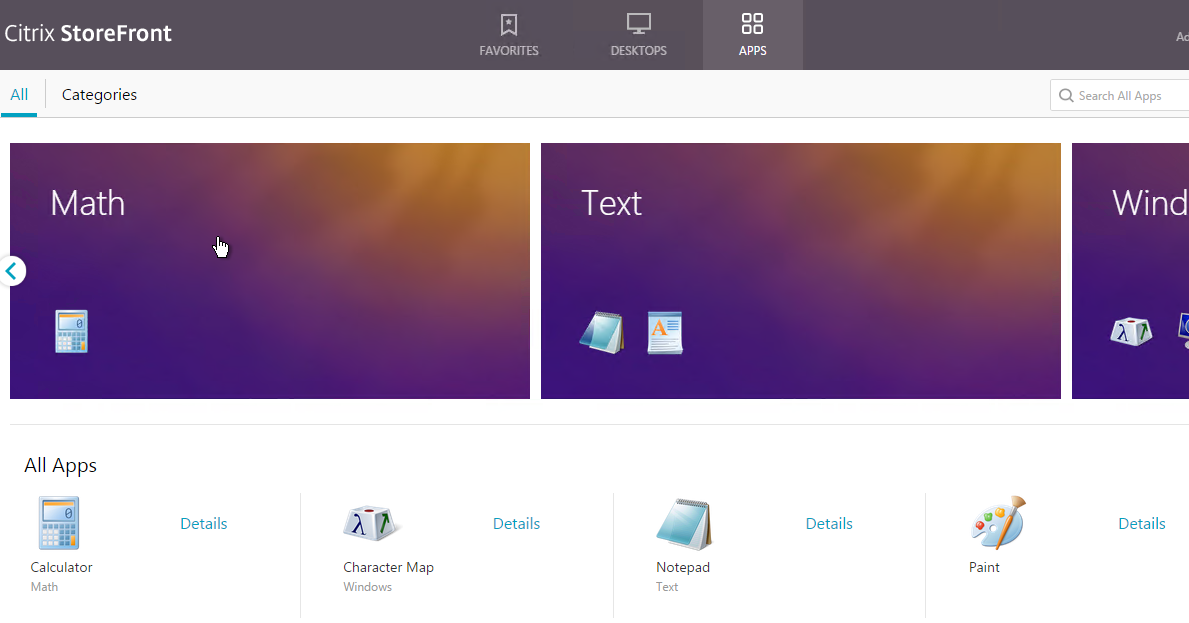
- By default, Featured App Groups are displayed with continual horizontal scrolling. This is OK if you have several Featured App Groups but doesn’t look right if you only have one Featured App Group.
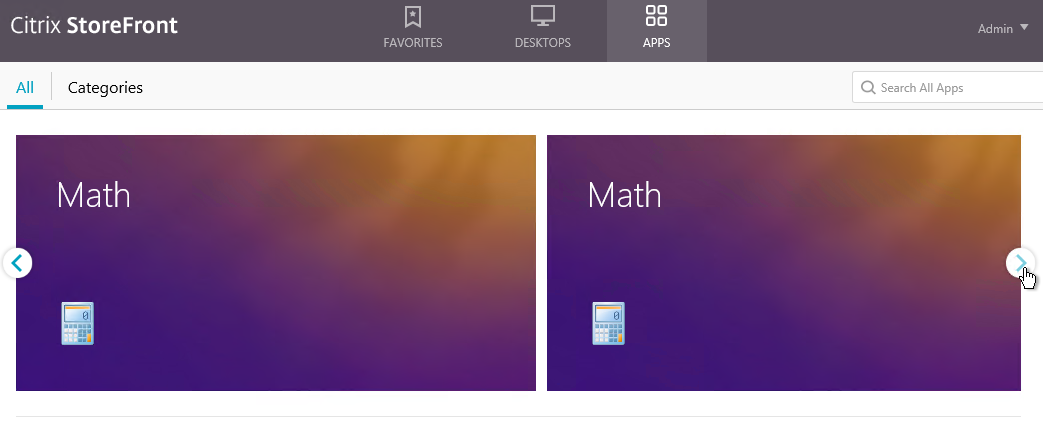
- Michael Bednarek has posted some code at Citrix Discussions to disable the continuous horizontal scrolling.
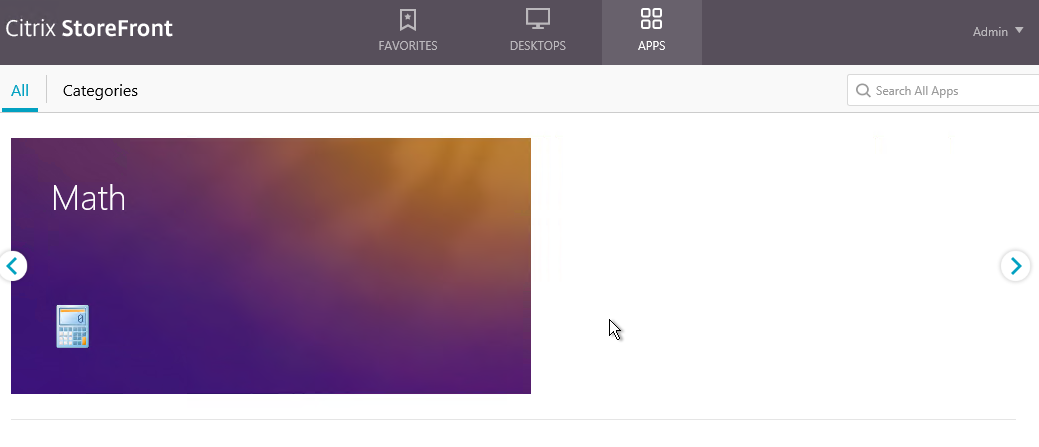
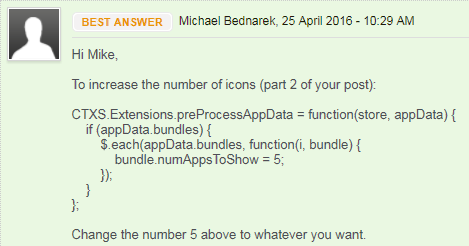
- If you want to display more than 3 apps per group, see Michael Bednarek at Modify Receiver for Web site at Citrix Discussions.
Receiver for Web (browser) Pass-through Authentication
- On the left, click the Stores node.
- In the middle, right-click your store, and click Manage Receiver for Web Sites.
- Click Configure.
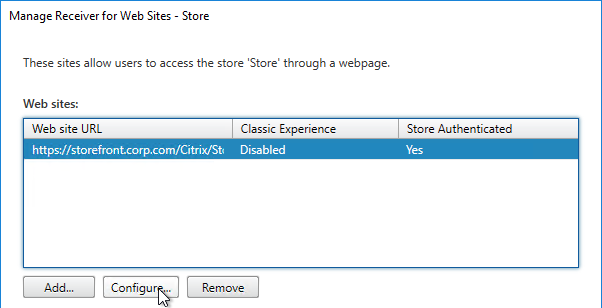
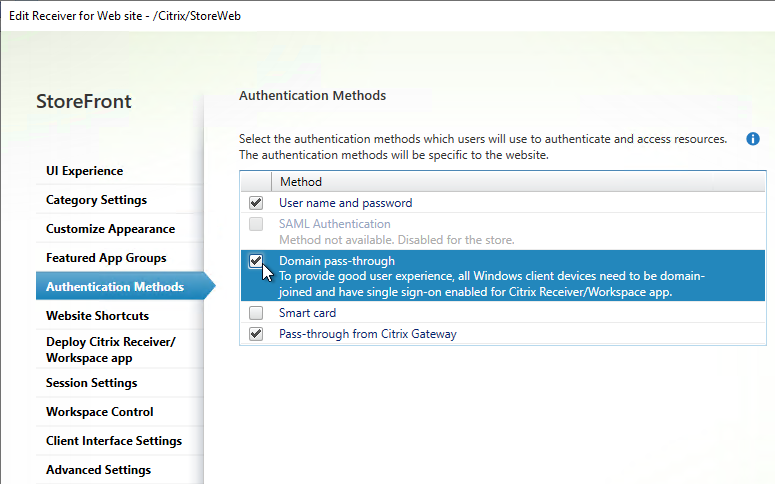
- On the Authentication Methods page, if desired, check the box next to Domain pass-through. Click OK.
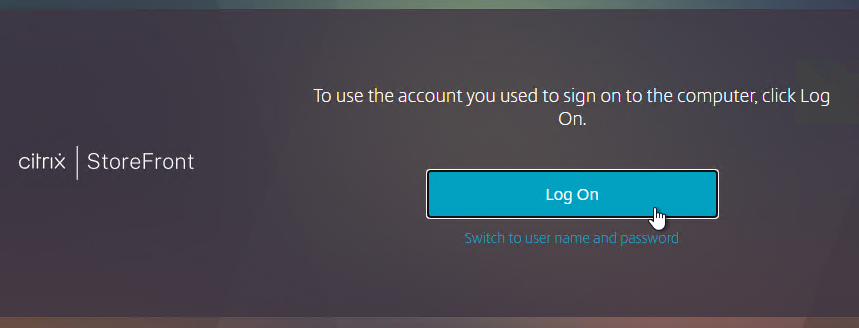
- If the StoreFront URL is in the browser’s Local Intranet zone, then you’ll see a prompt to automatically Log On. This only appears once.
- If you want to default to Pass-through without any user prompt, then see Citrix Blog Post Configuring domain pass-through as your default authentication method.
Workspace app for HTML5 2404
- On the left, click the Stores node.
- In the middle, right-click your store, and click Manage Receiver for Web Sites.

- Click Configure.

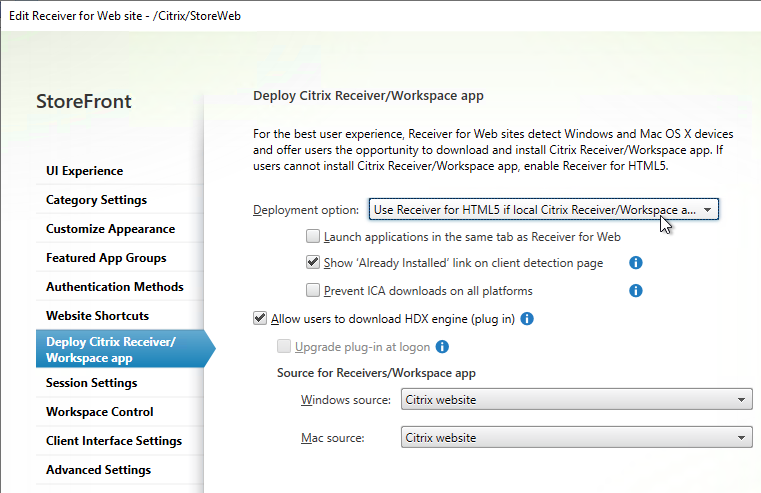
- On the Deploy Citrix Receiver / Workspace app page, change the drop-down to Use Receiver for HTML5 if local Citrix Receiver/Workspace is unavailable.
- By default, the HTML5 session opens in a new tab. You can optionally enable Launch applications in the same tab as Receiver for Web. See Configure Citrix Receiver for HTML5 use of browser tabs at Citrix Docs for more information.
- Click OK, and then click Close.
- Download the Workspace app 2404 for HTML5.
Note: new versions of Workspace app for HTML5 are released frequently. For example, 2306 and newer support the new launch experience.
- Install the HTML5 Workspace app (CitrixHTML5Client-x64.exe) on one of the StoreFront servers. It installs without prompting. Repeat this step on all StoreFront servers in the Server Group since Propagate Changes doesn’t seem to propagate the new Workspace App.
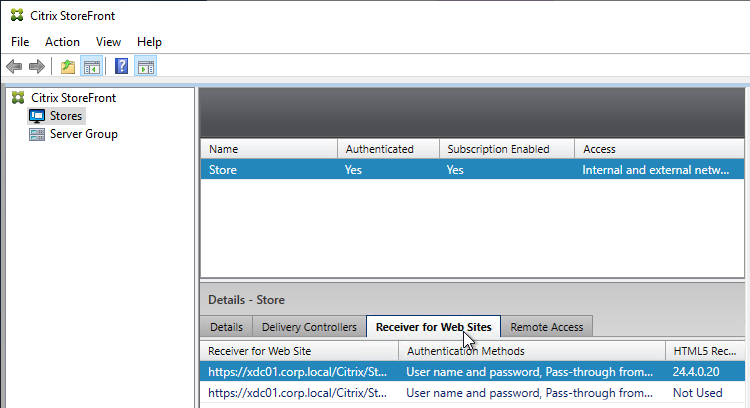
- To see the installed version of HTML5 Workspace app, in StoreFront console, click the Stores node on the left.
- In the middle pane, in the bottom half, switch to the Receiver for Web Sites tab. You might have to click Refresh to see the new version.
HTML5 Workspace app configuration
- Copy/paste of text using Ctrl+C and Ctrl+V – HTML5 Workspace app version 1907 app adds support for copy/paste of text using Ctrl+C and Ctrl+V and the feature is enabled by default. More info at Enhanced clipboard experience at Citrix Docs.
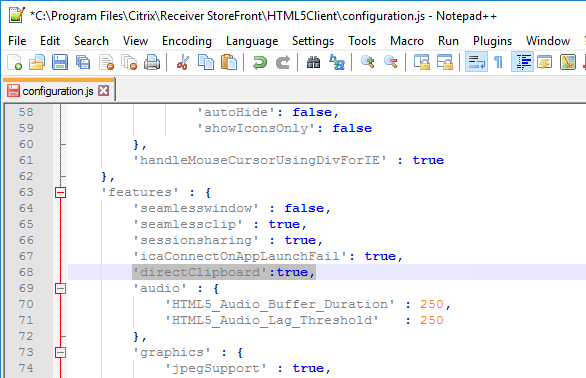
- Multi-monitor – HTML5 Workspace app has a multi-monitor feature, which is enabled by default.

- To configure HTML5 Workspace app, edit the file “C:\Program Files\Citrix\Receiver StoreFront\HTML5Client\configuration.js”.
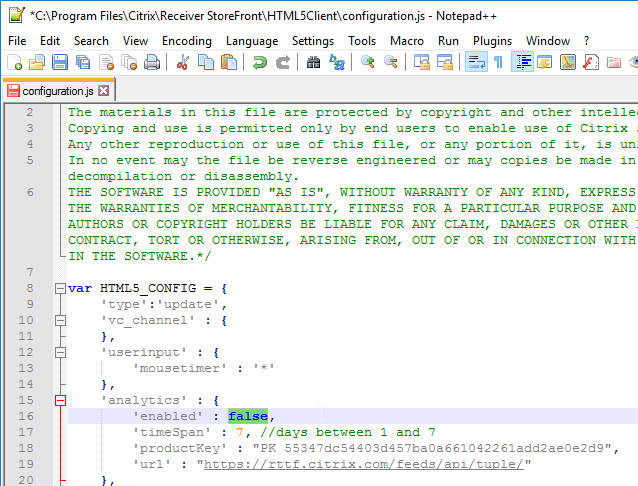
- Customer Experience Improvement Program (CEIP) is enabled by default. To disable CEIP in HTML5 Workspace App 1906 and newer, find the first analytics section and change enabled to false.
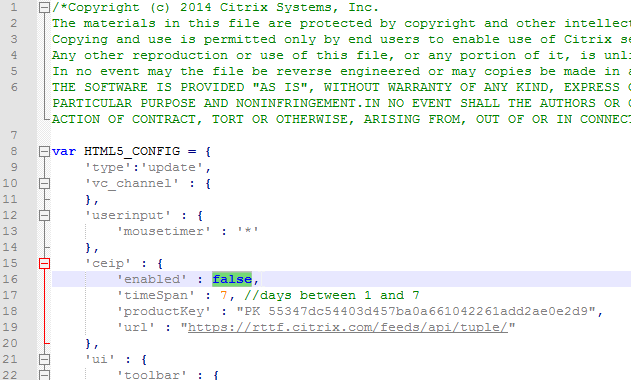
- To disable CEIP in HTML5 Workspace App 1905 and older, search for the ceip section, and change it to false.
- Customer Experience Improvement Program (CEIP) is enabled by default. To disable CEIP in HTML5 Workspace App 1906 and newer, find the first analytics section and change enabled to false.
- In the StoreFront console, on the left, right-click Server Group, and click Propagate Changes.

- For VDA 7.15 and older, optionally, install Citrix PDF Printer on the VDAs. The PDF printer is in the Additional Components section of the HTML5 Workspace app download page.
Note: in VDA 7.16 and newer, the PDF Printer is included with the VDA installation and no longer needs to be installed separately.
Other HTML5 Receiver configurations you can change by either editing C:\Program Files\Citrix\Receiver StoreFront\HTML5Client\configuration.js, or use the Citrix Workspace app (earlier known as Citrix Receiver) for Chrome and HTML5 – Configuration Utility downloadable from CTX229141.
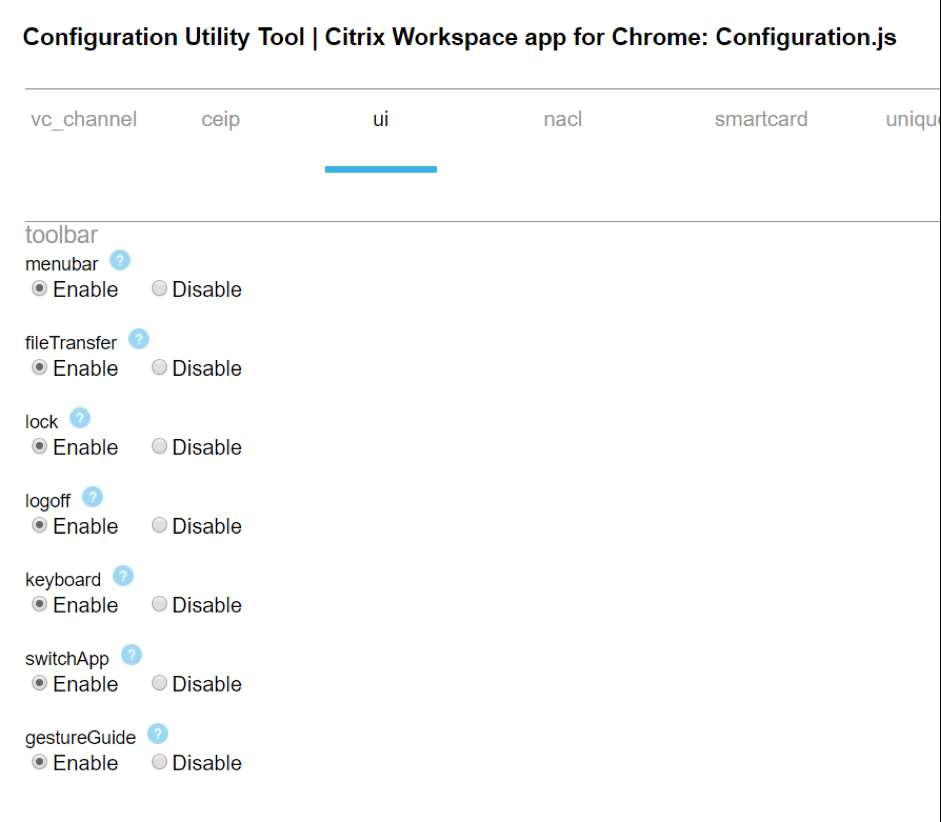
- HTML5 Workspace app has improved PDF printing in Chrome and Firefox. Enable it by setting supportedBrowsers to true.
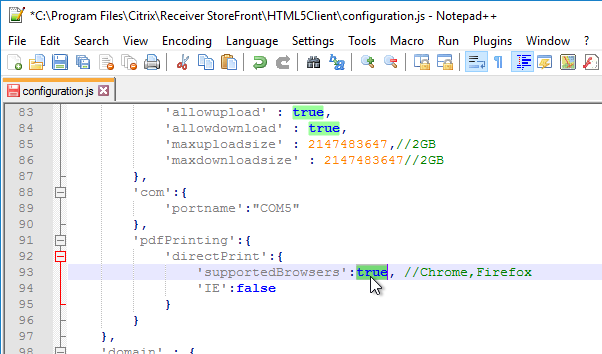
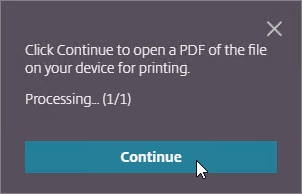
- When printing from HTML5 Workspace app to the Citrix PDF Printer, the user must click Continue to show the PDF. You can get rid of this prompt. In the configuration.js file, scroll down to the line containing printDialog and set it to true.
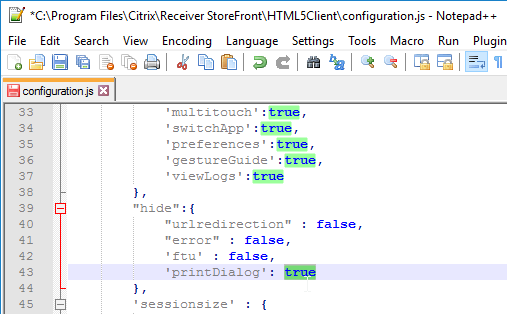
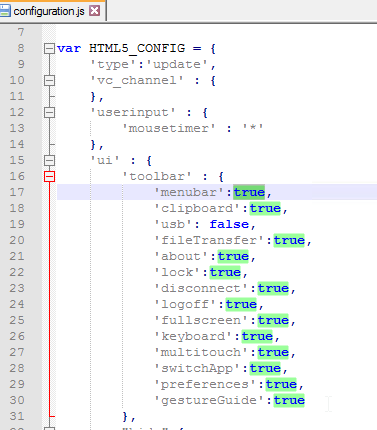
- The new HTML5 Workspace app toolbar can be disabled or customized by editing the file C:\Program Files\Citrix\Receiver StoreFront\HTML5Client\configuration.js.
If HTML5 Workspace app is enabled, users have the option of selecting either native or HTML5 by clicking Change Citrix Receiver or Change Citrix Workspace app.
- In StoreFront 1912 and newer, click the gear icon on the top right and then click Account Settings.
- Click either Change Citrix Workspace app or Change Citrix Receiver..
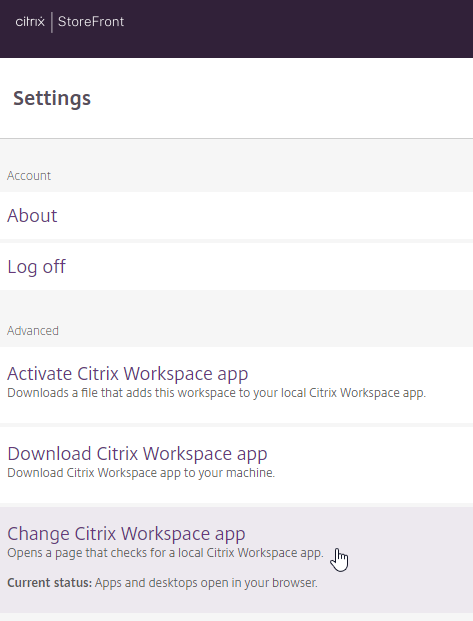
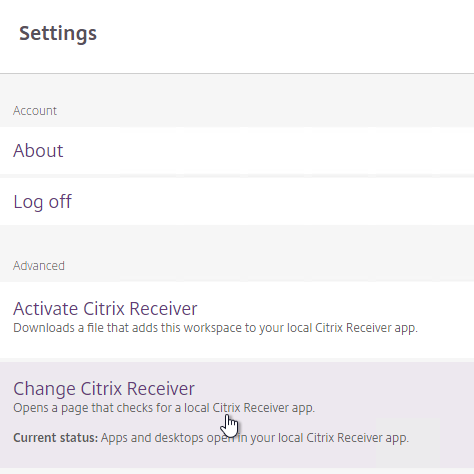
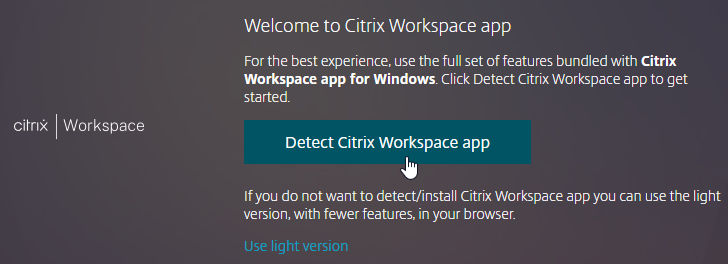
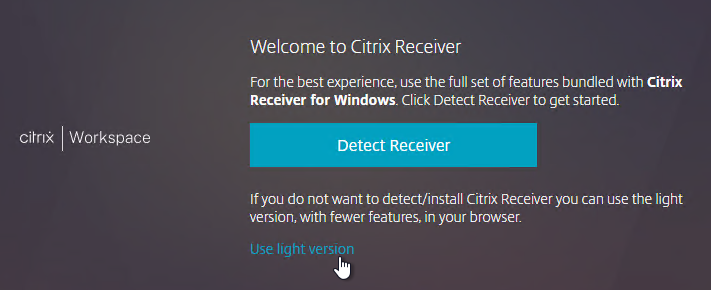
- If you want to use the locally installed Workspace app, then click the blue Detect Citrix Workspace app or blue Detect Receiver button. If you want to use the HTML5 Client, click Use light version.
Citrix Blog Post Receiver for HTML5 and Chrome File Transfer Explained:
- How to use the toolbar to transfer files
- Citrix Policy settings to enable/disable file transfer
- VDA registry settings to control file transfer
- HTML5Client\Configuration.js settings for client-side configuration
- How to view HTML5Client log file
Deploy Citrix Workspace app
- Citrix recommends that all users install the Citrix Workspace Web Extension in their endpoint browsers. This extension eliminates the need for StoreFront to detect the locally installed Workspace app and enables .ica files to be downloaded to memory instead of to disk. StoreFront support for the extension is enabled by default in StoreFront 2311 and newer. See Citrix Workspace web extensions at Citrix Docs.
- StoreFront can deploy Workspace app to users that don’t have Workspace app installed. In StoreFront console, on the left, click the Stores node.
- In the middle, right-click your store, and click Manage Receiver for Web Sites.

- Click Configure.

- On the Deploy Citrix Receiver/ Workspace app page, check the box next to Allow users to download HDX engine (plug in).
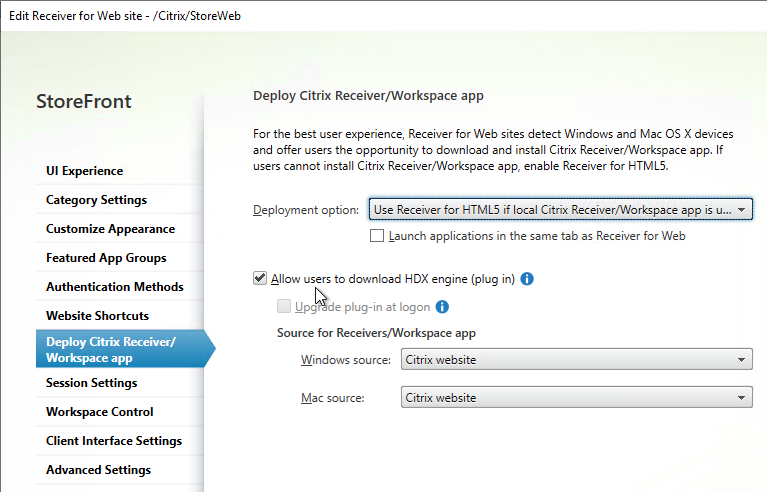
- Change both source drop-downs to Local files on the StoreFront server.
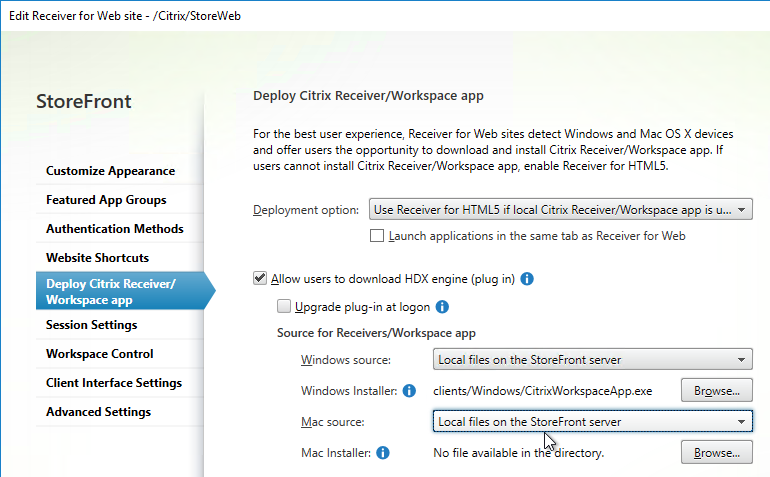
- For Windows, download one of the following:
- For Mac, download Workspace app 2402 for Mac.
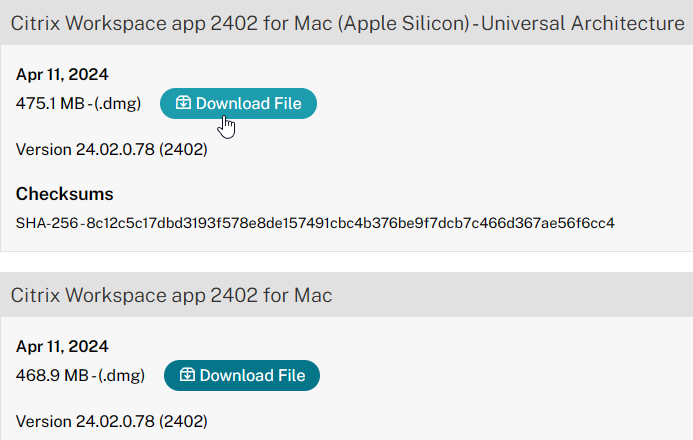
- Click each of the Browse buttons and browse to the downloaded Workspace app.
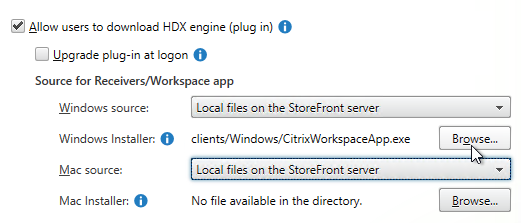
- You can optionally enable Upgrade plug-in at logon.
- Click OK when done, and Close when done.
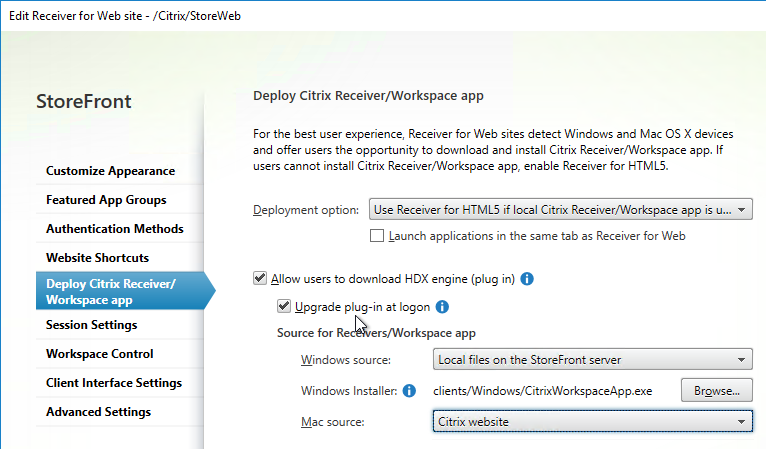
- If you prefer for users to download Workspace app from the Citrix website, then note that StoreFront might default to downloading Receiver instead of Workspace app. To change it to Workspace app, do the following:
- In StoreFront Console, in the Deploy Citrix Receiver/ Workspace app page, change Windows source and Mac source to Files on remote server (through URL).
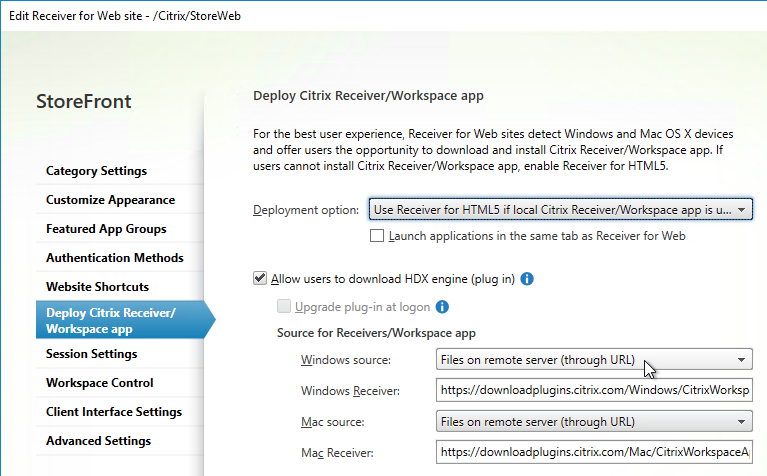
- Enter the following paths. The default paths might be http instead of https and you should change them to https.
Windows Receiver = https://downloadplugins.citrix.com/Windows/CitrixWorkspaceApp.exe Mac Receiver = https://downloadplugins.citrix.com/Mac/CitrixWorkspaceApp.dmg
- In StoreFront Console, in the Deploy Citrix Receiver/ Workspace app page, change Windows source and Mac source to Files on remote server (through URL).
- When users connect to Receiver for Web, they will be prompted to install or upgrade. In StoreFront 2203 and newer, the screens say Workspace app.
- In older versions of StoreFront, the screens might say Citrix Receiver instead of Citrix Workspace app.
- You can change it to Citrix Workspace app by following the instructions at CTX221097 How to rename items on StoreFront?.
- Search the list of strings in the KB article for any string containing the word Receiver, copy the string to C:\inetpub\wwwroot\Citrix\StoreWeb\custom\strings.en.js, and change it to Workspace app. A few of the strings are shown below. Make sure there are commas between each item except the last item.
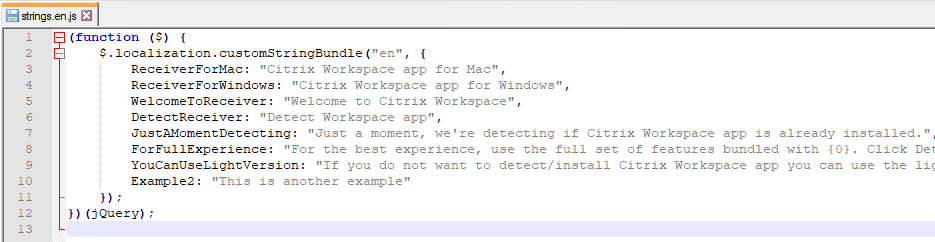
- Search the list of strings in the KB article for any string containing the word Receiver, copy the string to C:\inetpub\wwwroot\Citrix\StoreWeb\custom\strings.en.js, and change it to Workspace app. A few of the strings are shown below. Make sure there are commas between each item except the last item.
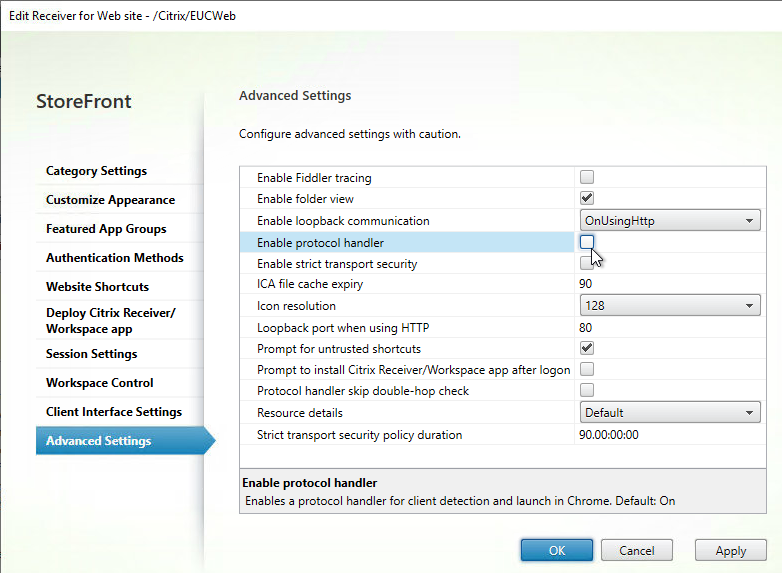
- If you don’t want StoreFront to detect the locally installed Workspace app, then edit the Receiver for Web site, switch to the Advanced Settings page and uncheck the box next to Enable protocol handler. This disables the button that asks users to Detect Workspace app.
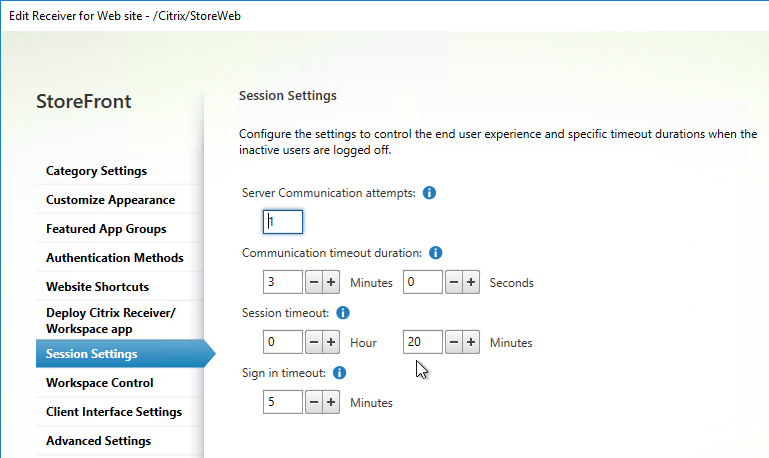
Receiver for Web Timeout
- On the left, click the Stores node.
- In the middle, right-click your store, and click Manage Receiver for Web Sites.

- Click Configure.

- On the Session Settings page, set the Session timeout as desired, and click OK.
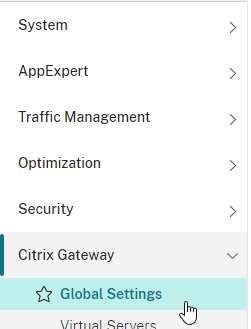
- If you are using a Citrix ADC, you will need to change the Global Session Timeout located at Citrix Gateway => Global Settings => Change Global Settings (right pane) => Client Experience (tab) => Session Time-out (mins).
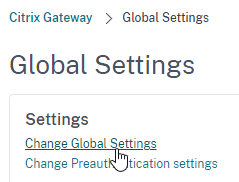
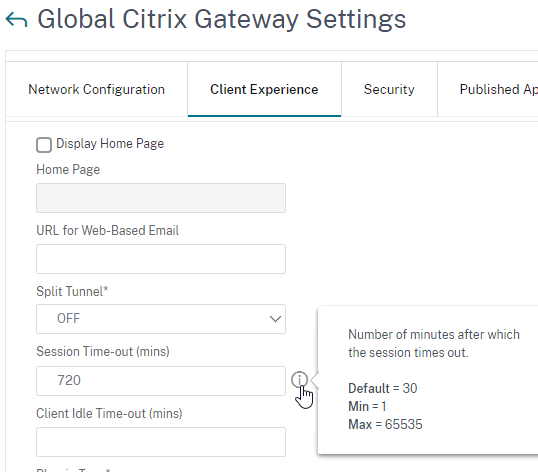
- This Citrix Gateway Session Time-out only applies to StoreFront and AAA. If you want it to also apply to ICA sessions, then on the Network Configuration tab, set ICA Session Timeout to ON. Source = CTX218008 How to configure ICA Proxy Connection Termination upon AAA Session Time Out.
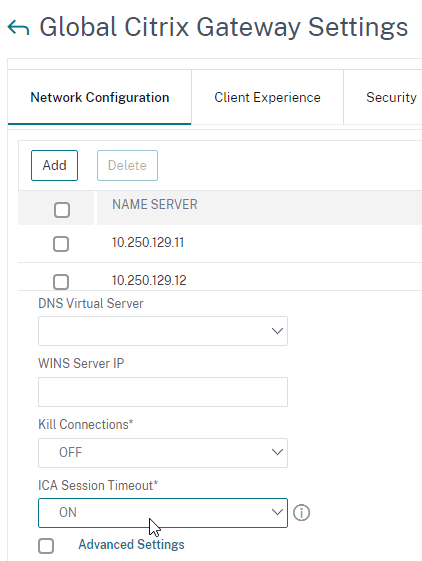
- This Citrix Gateway Session Time-out only applies to StoreFront and AAA. If you want it to also apply to ICA sessions, then on the Network Configuration tab, set ICA Session Timeout to ON. Source = CTX218008 How to configure ICA Proxy Connection Termination upon AAA Session Time Out.
- From Change the session time-out of Citrix Receiver for Web at Citrix Docs: If you increase the session timeout for RfWeb to be more than 1 hour, you must also increase the maxLifetime appropriately in c:\inetpub\wwwroot\Citrix\Authentication\Web.config.
- If your desired timeout value is greater than 8 hours, you should also edit tokenLifeTime in c:\inetpub\wwwroot\Citrix\StoreWeb\web.config.
Favorites, Categories, and Default Tab
By default, when a user logs into StoreFront, the HOME tab or Favorites tab is selected. Users can go to other tabs to add icons to the list of Favorites.
In StoreFront 1811 and newer:
- Favorites are shown on the HOME tab.
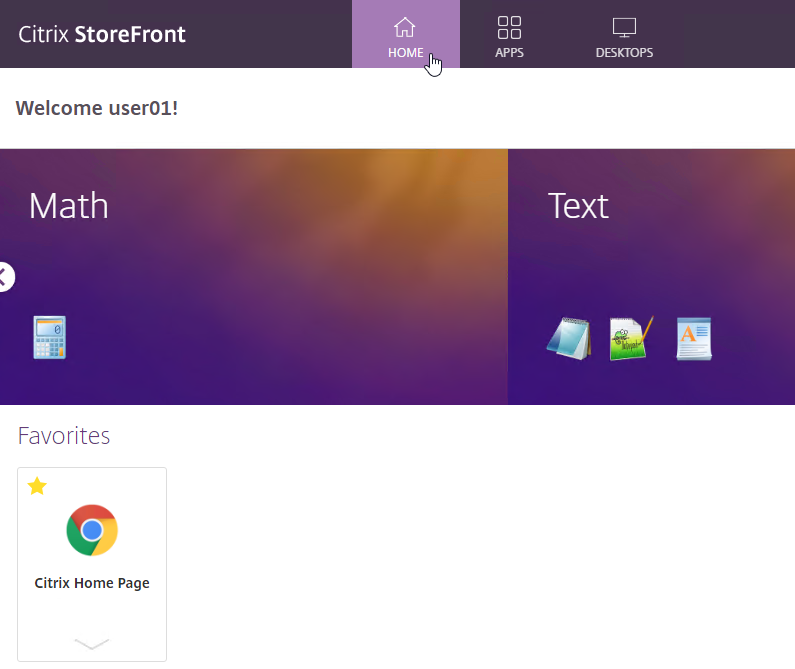
- Favorites are also shown on the APPS view on the Favorites tab.
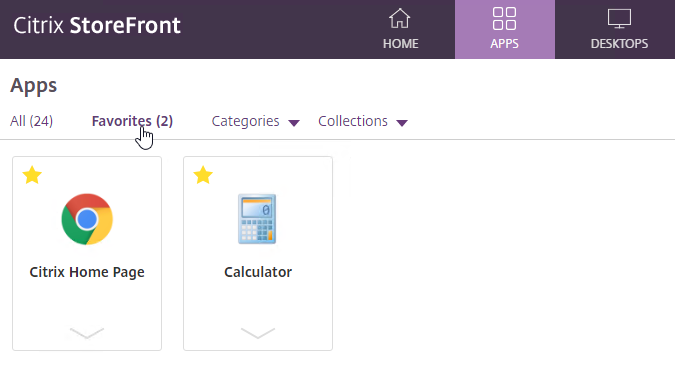
- The user can click the star icon next to a published icon to mark that published icon as a Favorite and add it to the HOME view and Favorites tab.
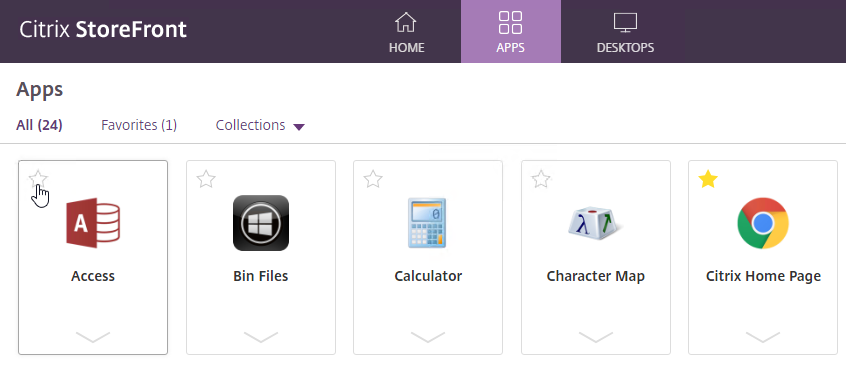
- On the APPS view, the user can expand the Categories drop-down and select a Category to view all icons in that Category.
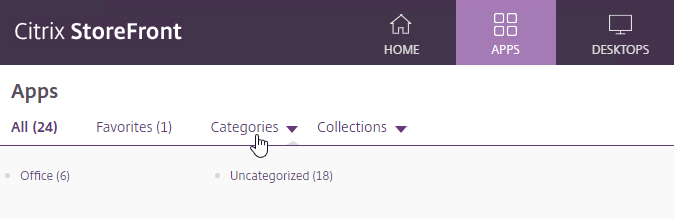
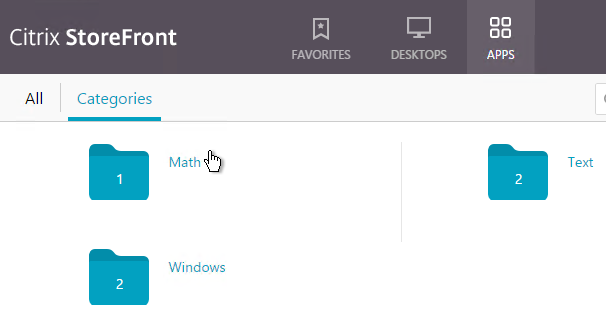
- To default to the Categories view, see the custom code at CTX559036 Storefront 2302 CU2 – All Apps are now showing on initial landing page instead of categories view.
- StoreFront 1912 CU2 and newer has an option to collapse the categories after one is selected. Notice the Uncategorized folder.
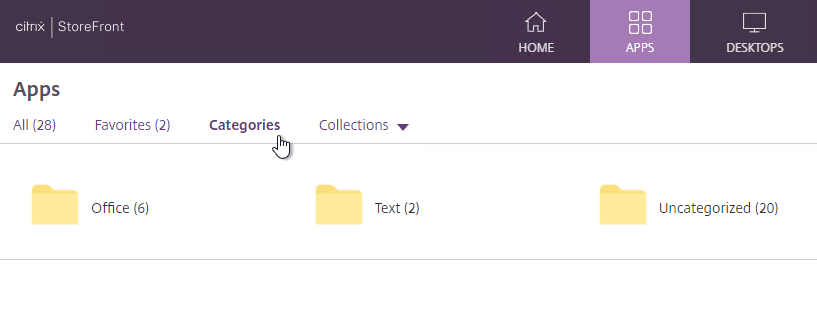
- After clicking a category, the user must click Categories again to switch to a different category.
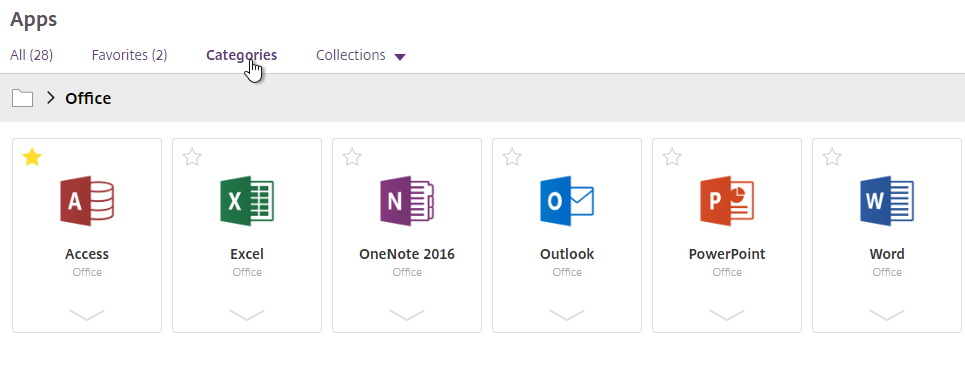
- StoreFront 1912 CU5 and StoreFront 2203 have an option to show Uncategorized icons directly below the Categories list if no Category is selected by the user.
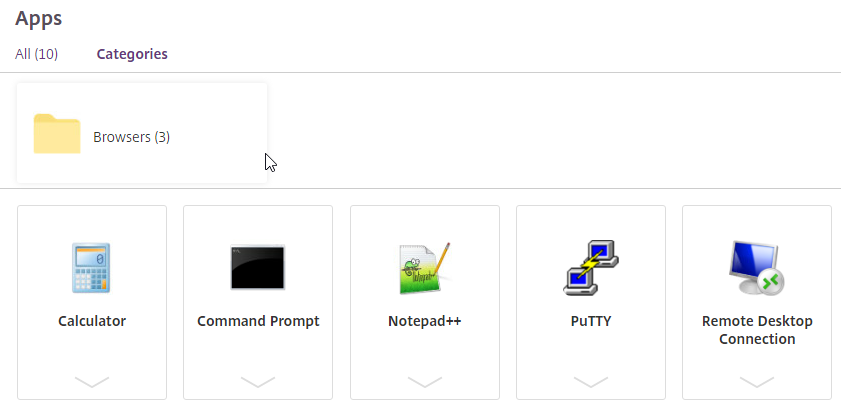
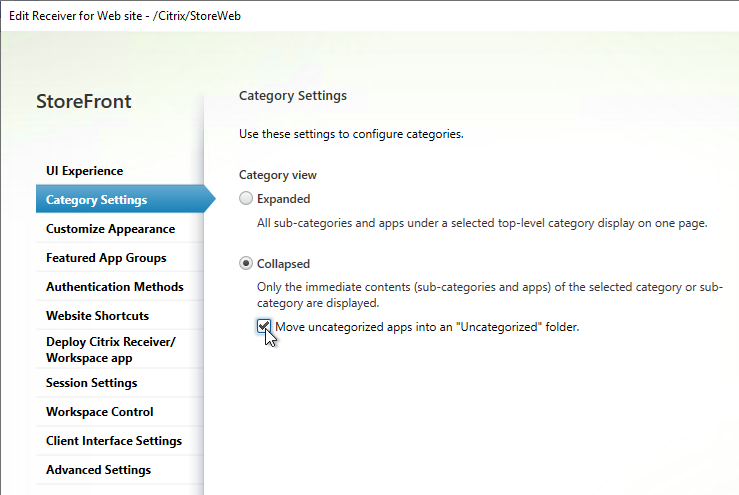
- This feature is configured in StoreFront console > click your store > Manage Receiver for Web sites > Configure > Category Settings. 1912 CU5 and 2203 adds the checkbox option to Move uncategorized apps into an Uncategorized folder. It’s checked by default, but you can uncheck it.
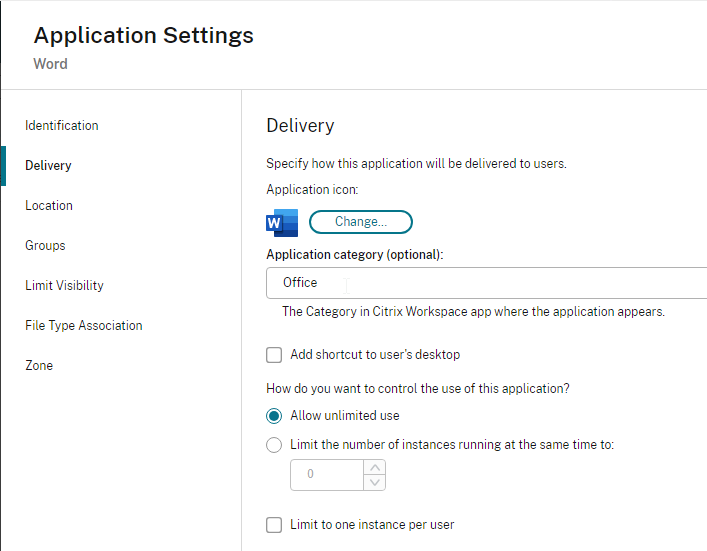
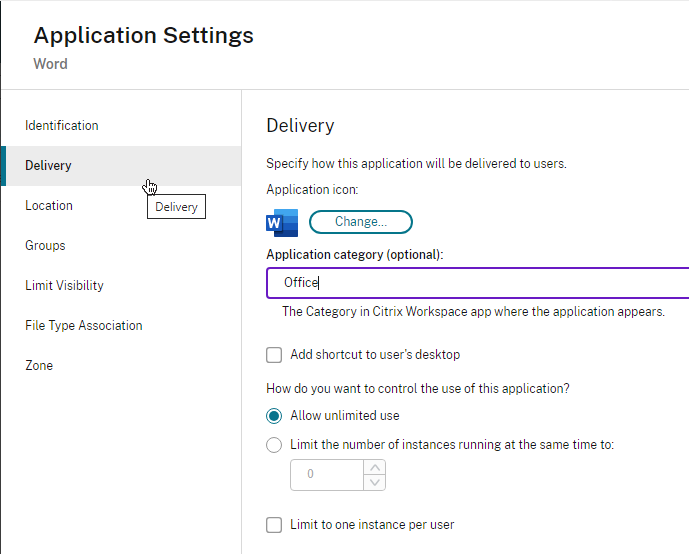
- Categories are configured in the Properties of the published application on the Delivery page.
- Collections are configured as Featured App Groups.
In StoreFront older than 1811:
- There’s a FAVORITES view.
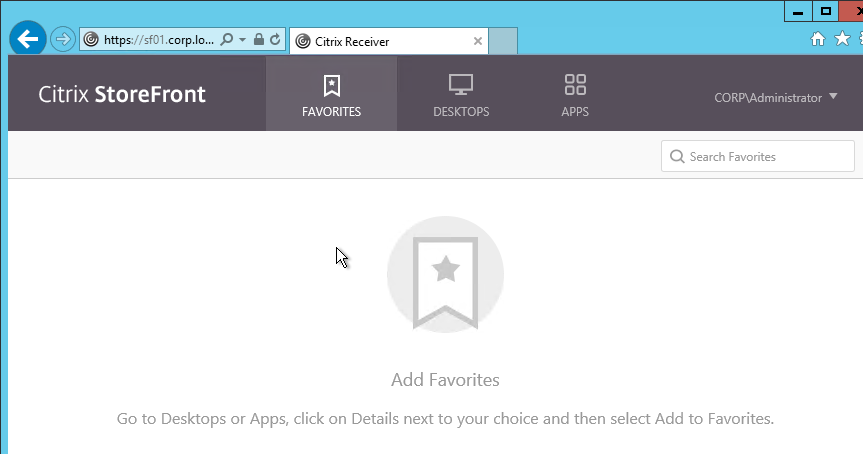
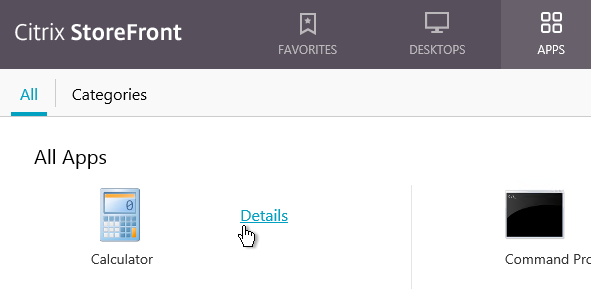
- On the APPS or DESKTOPS views, the user can click the Details link next to a published icon.
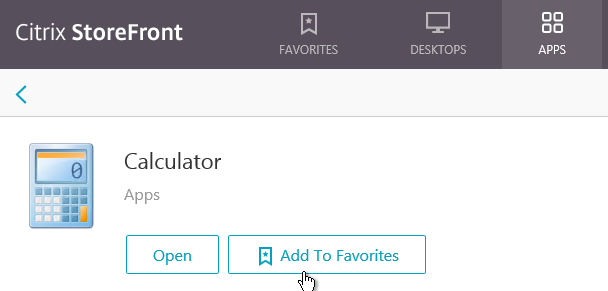
- Then the user can click Add to Favorites to add the icon to the FAVORITES view.
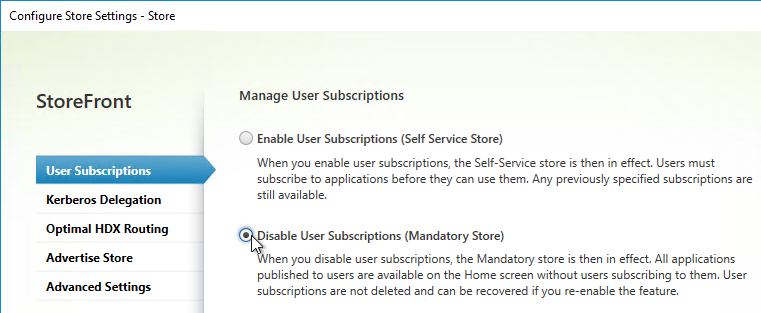
Favorites can be controlled by the administrator:
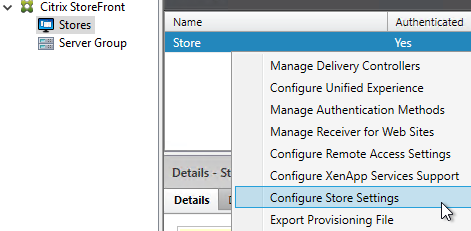
- You can completely remove the FAVORITES or HOME views by going to Stores > myStore > Configure Store Settings > User Subscriptions, and choose Disable User Subscriptions (Mandatory Store).
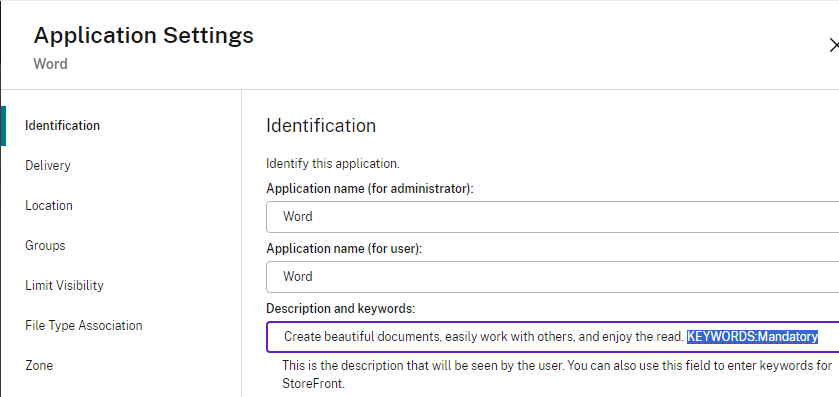
- To force a published application to be favorited (subscribed), use one of the following keywords in the published application description:
- KEYWORDS: Auto = the application is automatically subscribed. But users can remove the favorite.
- KEYWORDS: Mandatory = the application is automatically subscribed, and users cannot remove the favorite.
- With Mandatory applications there is no option to remove the application from Favorites.
- Citrix Blog Post How to implement dynamic landing pages in StoreFront has code for the following: If favorites exist, go to favorites tab. If favorites do not exist, go to the store tab. 💡
//If favorites exist, go to favorites tab. If favorites do not exist, go to the store tab. var favoritesExist = false; CTXS.Extensions.sortMyAppList = function (app_array,defaultSortFn) { //This version checks if the amount of user favorites are greater than or equal //to "favoriteThreshold". var favoriteThreshold = 1; var favoriteCount = 0; for (var i = 0; i < app_array.length; i++){ if (app_array[i].canBeRemoved()){ favoriteCount++; } } if (favoriteCount >= favoriteThreshold){ favoritesExist = true; } //This should always be called at the end defaultSortFn(); }; CTXS.Extensions.afterDisplayHomeScreen = function (callback) { if (favoritesExist == false){ CTXS.ExtensionAPI.changeView("store"); } }; - Trentent Tye has a simple customization for C:\inetpub\wwwroot\Citrix\StoreWeb\custom\script.js to default to the APPS view if the user doesn’t have any favorites. See Citrix Storefront – Adventures in customization – Default to “Store” view if you have no favourited app’s.
CTXS.Extensions.afterDisplayHomeScreen = function (callback) { /* If the user has no favorited apps, set the view to the apps view */ if (CTXS.Store.getMyApps().length == 0) { CTXS.ExtensionAPI.changeView("store") } }; - You can change the default view and view visibility by going to the Stores > myStore > Manage Receiver for Web Sites > Configure > Client Interface Settings page.
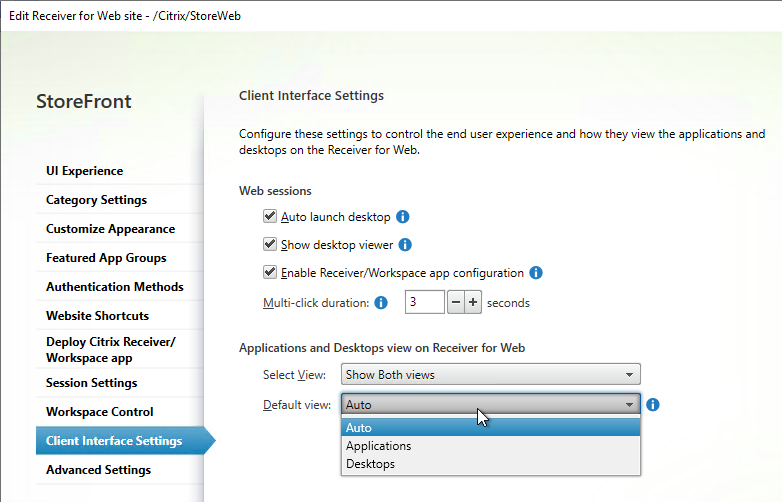
- In StoreFront 1811 and newer, if you want to default to the APPS tab with Categories view expanded, then see CTP Sam Jacobs at Storefront 1811 – Default to Categories view at Citrix Discussions. Or see Citrix Blog Post How to land on the categories view in StoreFront 1811+.
- Add the following to C:\Inetpub\wwwroot\Citrix\StoreWeb\custom\script.js.
Note: if you already have afterDisplayHomeScreen in your script.js file, then you’ll need to merge them.
function categoriesDelay() { $('#categoriesTabBtn').click(); } CTXS.Extensions.afterDisplayHomeScreen = function (callback) { CTXS.ExtensionAPI.changeView('store'); window.setTimeout(categoriesDelay,250); callback(); };
- Add the following to C:\Inetpub\wwwroot\Citrix\StoreWeb\custom\script.js.
- In StoreFront older than version 1811, if you change the default view to APPS, then you might also want to default to the Categories view instead of the All view.
- When publishing applications in Citrix Studio, on the Delivery page, specify an Application category so that the applications are organized into folders.
- To default the Apps view to the Categories view instead of the All view, add the following code to the end of the file C:\Inetpub\wwwroot\Citrix\StoreWeb\custom\script.js. More details at Storefront 3.0 – change default view at Citrix Discussions.
CTXS.Extensions.afterDisplayHomeScreen = function (callback) { CTXS.ExtensionAPI.navigateToFolder('/'); }; CTXS.Extensions.onViewChange = function (viewName) { if (viewName == 'store') { window.setTimeout(function () { CTXS.ExtensionAPI.navigateToFolder('\\'); }, 0); } };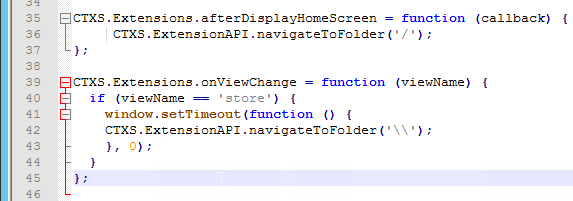
- Then when you login to StoreFront, you’ll see Apps > Categories as the default view. This works in Workspace app too.
- When publishing applications in Citrix Studio, on the Delivery page, specify an Application category so that the applications are organized into folders.
Beacons
- On the left, right-click Stores, and click Manage Beacons.
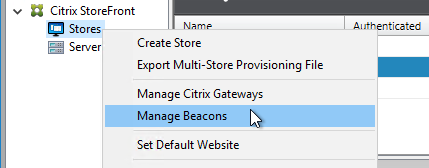
- Configure an Internal Beacon. Receiver Self-Service (Workspace app native interface) tries to connect to the Internal Beacon to determine if Workspace app is currently internal or not. If the Internal Beacon is reachable then Receiver Self-Service assumes it is internal, and thus connects to the StoreFront Base URL. If the Internal Beacon is not reachable, then Receiver Self-Service assumes it is external and thus connects to Citrix Gateway. For this to work properly, the Internal Beacon must not be resolvable externally.
If you are not doing Single FQDN, then the Internal Beacon can be the StoreFront FQDN since the StoreFront FQDN is usually only available internally.If you are doing Single FQDN, then you can’t use the StoreFront FQDN. Instead, you must use a different internal website for the beacon. If you need to support internal iPads, due to differences in how iPads determine location, the Internal Beacon should be a new FQDN that resolves to the StoreFront Load Balancing VIP, thus requiring the StoreFront certificate to match both the Internal Beacon and the Base URL. If internal iPads are not needed, then the Internal Beacon can be any internal website.If you want to force internal Receiver Self-Service users to connect through Citrix Gateway (for AppFlow reporting), you can set the Internal Beacon to a fake URL. Since the Internal Beacon is never resolvable, Receiver Self-Service always uses Citrix Gateway. Or you can use Optimal Gateway to achieve the same goal.
- The External beacons are used by Workspace app to determine if Workspace app has Internet access or not. You can use any reliable Internet DNS name. http://ping.citrix.com is no longer valid and should be changed to some other address. Click OK when done.
Propagate Changes
Any time you make a change on one StoreFront server, you must propagate the changes to the other StoreFront server.
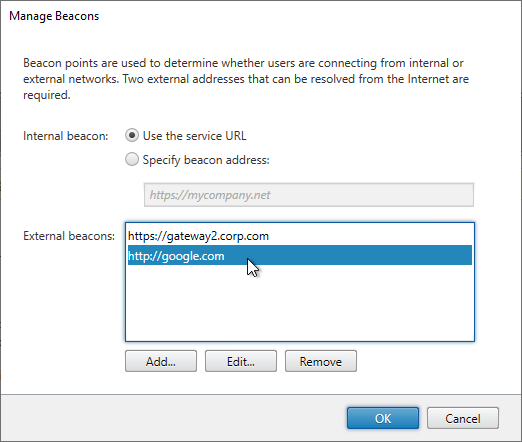
- In the StoreFront console, on the left, right-click Server Group, and click Propagate Changes.

- You might see a message saying that you made changes on the wrong server.
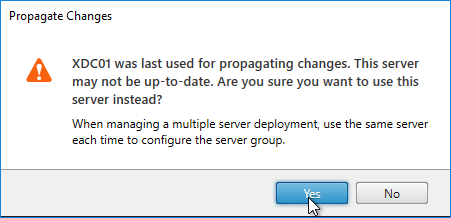
- Click Yes when asked to propagate changes.
- Click OK when done.
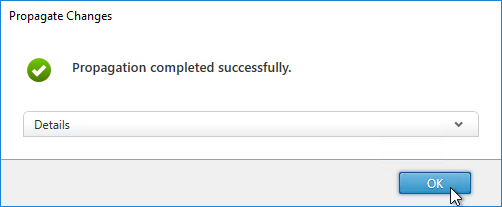
- When you propagate changes, the default web page is not replicated to the other nodes. Copy C:\inetpub\wwwroot\web.config manually to each node.

Export/Import StoreFront Configuration
Use the following PowerShell cmdlets to export StoreFront Configuration into a .zip file (encryption optional) and import to a different StoreFront server group:
- Export-STFConfiguration
- Import-STFConfiguration
See Export and import the StoreFront configuration at Citrix Docs for details.
Logon Simulator
ControlUp has ScoutBees logon simulator for StoreFront and Citrix Gateway.
eG Innovations has a free Logon Simulator for Citrix XenApp and XenDesktop.
Hi carl
Your blog provides this script download link address, but the sharing has expired, can not download now,Can you provide this script?
“Or see Citrix Blog Post Delete Local User Profile Folders on StoreFront Servers for a script to delete local profiles.”
Carl, with 2311, I’m not seeing any session information in the Activity Manager which works fine in the cloud. Are there any necessary additional steps?
When configuring Citrix storefront, I added pnagent will use this store to deliver resources without checking it. Can I add pnagent will use this store to deliver resources to the completed store?
thank you
In StoreFront console, click the Store. On the bottom right, click Configure XenApp Services Support.
Hi Carl,
I installed 2203 LTSR CU2 on a store front server, should I upgrade with CU3? I tried to install the upgrade but it keeps comin back with the error message, It says :
“StoreFront cannot be upgraded because the following folders are in use by another program. CLose the Program and try again.
C:\inetpub\wwwroot\Citrix\Roaming
I am not sure what needs to be close. I stop all citrix services, and also stopped IIS service as well as Application Pool.
Please let me know how I can do the upgrade.
Thank you,
Adnan
Disable it on the load balancer to prevent user traffic.
Procexp.exe (Process Explorer) can show you what’s keeping files open. Click the binoculars icon to search for the path.
Hi Carl, you mentioned Operating system support:
StoreFront 2203 and StoreFront 1912 CU4 and newer are supported on Windows Server 2022.
But unfortunately 1912 is not supported on 2022. I tried CU6 and CU7, both not supported – said by the installer.
Have to move to 2019 then…
Regards
I’m sure I read that somewhere but now I can’t find it. I just updated that text. Thanks for catching it.
Just wanted to throw out a longshot here to see if maybe you’ve seen this before or heard of this. We will be opening a case Monday but figured I’d start here. Our org is moving to 2019 Domain Controllers and we pointed our dev ADC’s to the new DC’s for ldap auth. We’ve made no other changes to the ADC’s or Storefront and auth is working, however, on the SF servers we are now seeing a new error. Citrix Domain Services Event ID 100 anytime we auth through the gateway using the new DC’s. “Failed to get user data to determine password expiry: denied to server: SERVERNAME”. The Citrix Default Domain Services Windows service may require to be run with a service account. I’m assuming this is something new on the domain controller side but not sure where to start. Any thoughts?
Mayb this – https://support.citrix.com/article/CTX466084/cvad-access-is-denied-error-displayed-for-all-new-ica-sessions
Thanks. I’ll take a look. We aren’t having any issues launching apps though or anything. In all honesty, we wouldn’t have even known anything was going on had we not been trying something completely unrelated on the SF servers and just happen to come across the domain errors.
Hello Carl,
We are seeing weird issue where users are not able to see the icons for their published applications on app switcher taskbar (it shows blank icons with app name) while accessing it through HTML5 citrix workspace. We have 1912 CU3 configured in our environment. Version for HTML5 receiver is 21.3.0.4172.
Is there something
I would upgrade the Workspace app for HTML5 and see if that helps.
Starting the “Citrix Default Domain Services” service seemed to sort this for me
Hi Carl, is there anything special when it comes to adding a second store to a storefront? For example, we have workspace control enabled on our original store, so as we are doing a project to onboard android devices to published apps, session roaming is kicking in and pulling over open sessions from the original store to the Android phones. The original store serves VDI.
I’m thinking we need a new store to point the android phones at, and I’m wondering if I can just add a store in storefront GUI and still be able to manage everything from the GUI. I keep seeing articles that talk about having to manage multi store with different urls through powershell. I do not want multiple URLs if possible.
Thanks!
You can add a second store, but new Workspace app users would then be prompted to select between the old store and the new store, unless you hide the new store. If the new store is hidden, then there’s special syntax to discover the hidden store.
Is the special syntax only needed for discovering the store? We are using web receiver for the most part.
If using Workspace app (not browser), and if the store is hidden, then you need the special syntax. If browser, just enter /Citrix/StoreNameWeb after the FQDN.
2203 Storefront does not have the Receiver User Experience you are displaying with the checkbox. Now, there is no checkbox so there is no way to turn it off that I can see. Now it is just Unified Experience with a dropdown to select the Receiver For Web site. Can you not use Classic experience in 2203 ?
BrokerAccessPolicyRule and ClientNameFilter not working and saw a discussion where disabling Unified Experience fixes this. Any help you can provide me and my customer would be greatly appreciated.
I think the old interface was removed from newer StoreFront.
Does it work in Workspace app but not in the browser?
Wasn’t expecting a response this fast from rockstar Carl. It’s great to meet you. I’m a Tech Lead in Citrix Support. We have posted the question in our Storefront Slack channel as well.
Here is the setup and I read in a citrix discussion that disabling the unified experience fixes this.
From the case:
Cx has a requirement to make specific delivery groups available only to certain machine names. To achieve that requirement he used the Set-BrokerAccessPolicyRule comdlet to enable client name filtering (-IncludedClientNameFilterEnabled $True), end users still unable to see the DG and not able to connect, endpoints Wyse Thin Client 5470 and all in one with ThinOS 9.x
So I assume everyone is using workspace app for Linux
Some info on Client Name Filter – https://support.citrix.com/article/CTX128232/how-to-configure-xendesktop-for-a-teaching-lab-or-classroom-environment
Now the engineer is telling me it was working before they upgraded from Receiver to WSA.
hi carl
I wanted to ask
I want to do some things in the new version of the StoreFront that I can’t apply
1. Set as default that the first page to open is the page containing the folders inside the applications tab
2. Under the apps tab there are 2 pages 1. ALL and the other is folders I want it to say ALL apps instead
3. When defining folders, define that the number of icons that are in the folder that number will appear inside the icon of the folder (as it appears on this page in the middle of the page)
I would appreciate your help on this matter
Getting a 404 – File or directory not found when trying to authenticate to the Store via the ADC. Direct connection to the storefront server works. Please help.
In your Session Policy/Profile, on the Published Apps tab, what do you see in the Web Interface address field? Is it a valid URL?
Hello Karl,
I would like to know if it is possible to force the StoreFront and Delivery Controller to do LDAPS and if so what would be the implementation procedure?
I did some research on the web but couldn’t find anything on the subject.
Thanks in advance for the feedback
Which loopback option should I use if internally I load balance the base url on an ADC. Clients connect to my ADC on HTTPS and my ADC creates a connection to my Storefront servers on HTTPS too? HTTP on my ADC only redirects to HTTPS.
Your StoreFront servers should have an https listener in IIS Bindings so setting Loopback to On is fine. If you don’t have https listeners, then set it to OnUsingHttp.
Excuse me, I have one ddc and two storefronts, can I integrate the two storefronts into one storefront url for use
You can load balance the two StoreFront servers into a single URL. Citrix ADC Express is free for simple load balancing.
Hi Carl,
Is it possible to configure storefront HTML5 so that every application launches in a new browser tab and for this to be done with session sharing turned on. Turning session sharing off allows this, however it causes printing problems where intermittently the pdf is not generated. Unless you have an idea for how to take care of that Generating PDF issue?
Hi Carl, I am getting below error when joining storefront server to the group. Servers are running 2203LTSRCU1 and they were upgraded from 1912LTSRCU4. Servers were part of group and were taken out before upgrading them.
Join failed. Exception attempting to obtain Server Group details from the Authorizer.
System.ArgumentNullException, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089
Value cannot be null.
Thanks
Mustufa
Maybe this – https://discussions.citrix.com/topic/402099-cant-add-2nd-win2016-ltsr-715-to-servergroup/
Thanks Carl, I have seen that article and have tried the suggestion but no luck. The only difference in error is I am getting Value cannot be null where as the user getting Keyset does not exist.
Regards
Mustufa
how did you fixed the error “Keyset does not exist”
Hi, I restore the server to it’s original state and then did in place upgrade without removing from the group.
Regards
Mustufa
Good day Carl. Quick question, can we mix CR CVAD versions and Storefront versions? If we have a machien catalog with CVAD 2112.0.0.32068 (yes, its going to be updated), can we install 2206 of Storefronts before we update the CVAD software?
Thank you
Hey Carl. Quick question about the supported version of Storefront with a specific version of CVAD. Does it matter? Or can we mix? If we have 2112.0.0.32068 as CVAD (we are upgrading soon) can we go to Storefront 2206 first? Or do we have to wait for the CVAD to be upgraded?
I’m not aware of any incompatibilities between versions, but LTSR has specific version requirements for support.
Hi Carl, do you have any idea why I experience this error in event viewer of storefront? I enabled loopback communication OnUsingHttp an set the user groups (AD) read and allow to authenticate security rights to the SF and DDC’s AD-Objects.
An unexpected response was received during the authentication process.
Citrix.DeliveryServicesClients.Authentication.Exceptions.ExplicitAuthenticationFailure, Citrix.DeliveryServicesClients.Authentication, Version=3.22.0.0, Culture=neutral, PublicKeyToken=null
General Authentication Failure
ExplicitResult.State: 5
AuthenticationControllerRequestUrl: https://gateway.elimkirche.de/Citrix/StoreWeb/ExplicitAuth/LoginAttempt
ActionType: LoginAttempt
at Citrix.Web.AuthControllers.Controllers.ExplicitAuthController.GetExplicitAuthResult(ActionType type, Dictionary`2 postParams)
For any reason I can open the link (AuthenticationControllerRequestUrl with HTTPS) but it says this on that page:
Server Error in ‘/Citrix/StoreWeb’ Application.
The resource cannot be found.
Description: HTTP 404. The resource you are looking for (or one of its dependencies) could have been removed, had its name changed, or is temporarily unavailable. Please review the following URL and make sure that it is spelled correctly.
Requested URL: /Citrix/StoreWeb/ExplicitAuth/LoginAttempt
Version Information: Microsoft .NET Framework Version:4.0.30319; ASP.NET Version:4.7.3770.0
Is there any way to hide the Desktop Viewer when using Local App Access as well? We have some computers that require Local App Acess and others that do not, but we are trying to hide the desktop viewer for all. When we edite teh Default.ica to have ConnectionBar=0, the desktop viewer disappears, however Local App Access no longer works
i am trying to upgrade Citrix SF 3.13 to 1912 LTSR/1912LTSR Cu4 and it is getting failed with below errors in event logs
Could you please suggest ?
Event code: 3005
Event message: An unhandled exception has occurred.
Event time: 1/25/2022 6:52:09 AM
Event time (UTC): 1/25/2022 6:52:09 AM
Event ID: 041b056b0e054c58b19d5888f9c2e307
Timestamp: 1/25/2022 6:52:04 AM
Category:Error, WinError
Message:Installation of ‘..\CitrixStoreFront-x64.msi’ failed with error code 1603. Fatal error during installation
Ending a Windows Installer transaction: C:\Users\test\AppData\Local\Temp\7\CitrixStoreFrontSelfExtractor0\CitrixStoreFront-x64.msi. Client Process Id: 15200.
Windows Installer installed the product. Product Name: Citrix StoreFront. Product Version: 3.22.4000.6. Product Language: 1033. Manufacturer: Citrix Systems, Inc.. Installation success or error status: 1603.
An error occurred while running a PowerShell command.
Citrix.DeliveryServices.PowerShell.Command.RunnerInterfaces.Exceptions.PowerShellExecutionException, Citrix.DeliveryServices.PowerShell.Command.RunnerInterfaces, Version=3.13.0.0, Culture=neutral, PublicKeyToken=e********6
An error occurred while running a PowerShell command.
System.Exception, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b*********9
Exception of type ‘Citrix.DeliveryServices.Framework.Utilities.Exceptions.CannotGetExclusiveAccessException’ was thrown.
Error writing to the event log
System.NullReferenceException, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089
Object reference not set to an instance of an object.
at Microsoft.Practices.ServiceLocation.ServiceLocator.get_Current()
at Citrix.DeliveryServices.Logging.Common.Logger.LogMessageInternal(UInt16 eventId, UInt16 categoryId, MessageType severity, Exception ex, String message)
Is this server behind a load balancer? Did you disable the server in the load balancer? Also reboot it before trying the upgrade.
I did after the taking the server out of load from load balancer
I have tried upgrading the SF after taking it offline from Load balancer but still it is getting failed. Also I could see few event logs error related to event id 1309 for asp.net 4.0.
Let me know if you can suggest something else.? If possible share your id, I can share you few more logs from my end
Hi. I tried to upgrade Storefront from version 3.14 to 1912. The upgrade completed without errors. But the Xenapp Portal page is not showing XA Desktops or Apps. I tried to upgrade from 3.14 to 1909, and it is working fine. Any suggestions how to fix this?
What errors do you see in StoreFront Server > Event Viewer > Applications and Services > Citrix Delivery Services?
Wondering if you can help with an issue. I have an ADC setup with StoreFront. In trying to setup the single FQDN everything works except when I set the internal beacon to a valid internal domain. The internal beacon is a domain that is only resolvable inside the network, it just points to an internal HTTP server.
When the internal beacon is set how it should be (to indicate the user is inside the network) everything works, except that the user is prompted to login twice. The first prompt I believe is coming from the Gateway, the second (which requests domain\username) I believe is coming from the DDC/Storefront.
If the client is external, or going through the web, they are not prompted twice. If I change the internal beacon to something invalid (a completely invalid URL) internal and external clients are only prompted once. I suspect this is because it’s treating internal clients as external.
I’ve checked several things but can’t seem to get past the double prompt when the internal URL is set correctly. Any help is appreciated.
Internally, the Single FQDN should resolve to StoreFront, not Gateway.
Sorry if this is a double post, not sure if it went though the first time.
Setting the Single FQDN to resolve to StoreFront nets a “This store doesn’t exist. Please retry or contact support.” message from the Workspace app…?
Wait, your post on Single FQDN says that the SFQDN needs to point to the “StoreFront Load Balancing VIP” which it is. The ADC has 3 IPs, NSIP, SNIP, VIP
Internally, I have the SFQDN pointes to the VIP of the ADC/Netscaler.
Thanks for your help
Single FQDN means that your StoreFront Base URL and your Gateway FQDN are identical. But they are separate VIPs. Internally, StoreFront Load Balancing VIP is just normal load balancing of StoreFront Servers. Externally, the Gaateway VIP does ICA Proxy.
Right, ok so… let’s say that I have the NSIP, SNIP, and VIP on the ADC/Netscaler. The VIP is 192.168.1.100
Internally I have the SFQDN pointed to the VIP (192.168.1.100) on the ADC.
Externally the SFQDN resolves to a public IP, which is NATd to the ADC VIP (192.168.1.100).
Are you saying that I need to make a separate VIP for internal clients and internal point the SFQDN to that VIP?
Thanks again.
Load Balancing Virtual Server and Citrix Gateway Virtual Server are completely different. You must have separate VIPs for each function.
“Load Balancing Virtual Server and Citrix Gateway Virtual Server are completely different. You must have separate VIPs for each function.”
Ok, I’m not doing any load balancing, I just have a Citrix Gateway configured on the ADC. Internally I have the domain pointed to the VIP of the Citrix Gateway, Externally in resolves to the public IP (which is NATd to the same internal VIP as internally).
This all works as long as I set the internal beacon to something bogus, something that does not resolve at all internally or externally. If I set the internal beacon to anything valid, regardless if it’s only resolvable internally, internal clients (Workspace app users) get prompted twice, once with just username/password prompt and again with a domain\username and password prompt. If you login both times, everything works, it’s obviously just annoying.
If you don’t have load balancing, then internally the Single FQDN should resolve to the IP Address of the StoreFront server.
“If you don’t have load balancing, then internally the Single FQDN should resolve to the IP Address of the StoreFront server.”
Ok, if I set the domain to the IP of the StoreFront/DDC server I get the “This store doesn’t exist. Please retry or contact support” error… So I must have something misconfigured there…
Hi Carl,
I need that all StoreFront logins use only the Web Site (C:\inetpub\wwwroot\Citrix\StoreWeb\customWeb).
I have configured “Receiver for Web Sites” and “Unified Experience” as indicated but if I access from Workspace APP (Mobile or PC Client Receiver) use the App Site (C:\inetpub\wwwroot\Citrix\StoreWeb\custom).
Android allows the “Add account type as web interface” configuration which is the desired mode, but since iOS does not allow it.
How can I configure the StoreFront to make it use only the Web Site?
Carl, both links under the Delivery Controllers – SSL section are invalid. Here is an updated Citrix article: https://support.citrix.com/article/CTX218986 and a Ferroque article: https://www.ferroquesystems.com/resource/howto-enable-ssl-on-citrix-delivery-controllers-easy-method/
Thanks for pointing this out. The links should be updated now.
Hello Carl, I have 4 node SF servers in server group. We are planning to upgrade from 7.15 ltsr to 7.19 ltsr. Can I upgrade SF servers directly without removing from worker group. Please help me. Thank you.
Yes, it usually works for me. However, Citrix advises a different upgrade method.
Thanks for all you do Carl. Your articles are great. I have a question. We are in the process of planning to change our external URL DNS, to access Citrix. For example, our URL will be going from citirx.home.com to citrix.away.com We are currently using a Netscaler gateway running version nc13. We are running storefront 3.12. I think all we would need to do is create the new DNS record externally and attach the certificate to the VIP. In Storefront, update the stores remote access URLs and that would be it. The question I have is based around the Citrix workspace clients for our external users. There will be some that are on domain joined laptops and others that are using their personal machines to access Citrix. Is there a way we can programmatically update their Citrix clients to use the new external URL?
For corporate-managed machines, did you use GPO to push the discovery URL to the Workspace app clients? If so, does changing the GPO work? You might want to test it.
Otherwise, users would have to manually remove the old account and add the new account.
There is a GPO set, but this is for our internal users, which includes users using our vpn client connecting to our network. The internal URL will not change, just our external connection, going through the Netscaler. It sounds like users using personal machines will have to manually remove the old account and add the new account?
If you’re changing the Gateway in StoreFront, then the provisioning file also changes. You’ll have to test if the Workspace apps automatically update their registry with the new Gateway info.
Does storefront 3.12.7000 (i.e 7.15 CU 7) is compatible for Thin client users with IE 10?
It’s definitely not supported and I doubt it would work. https://docs.citrix.com/en-us/storefront/3-12/system-requirements.html
Hi Carl
In domain passthrough.
– Before the enumeration phase, in which format , users credentials are forwarded by the Storefront to the DDC (Kerberos/XML)?
– After the enumeration phase, when the user launch an application or desktop, who will send the authentication token to the VDA? is it the DDC , or the workspace app (receiver)? and in which format?
In smartCard authentication
what is exchanged as user credentials betwwen the storfront and DDC ? AUthentication token or user certificate?
DUring the launch process, who send credential to the VDA? the receiver or the DDC.?
If you can give more detail about how user credentials are forwarded during the domain passthrough and Smart card authentication process , i’ll be gratefull.
Many thanks
Domain Passthrough = Kerberos/NTLM to StoreFront. StoreFront sends only username to DDC. That’s why Trust XML must be enabled on DDC.
On client machine is ssonsvr.exe, which captures credentials during logon to Windows. When launching session, ssonsvr.exe sends the credentials to the VDA.
Smart card certificate is used to authenticate with Domain Controller to get a Kerberos ticket to authenticate to StoreFront. During session launch, the VDA uses the typical interactive logon smart card process to get a Kerberos ticket to logon to lsass.exe on the VDA machine. If ssonsvr.exe is running on the client, then the user doesn’t need to enter a PIN during session launch because ssonsvr.exe already captured the PIN.
Hi Carl, when I upgraded Citrix Workspace for HTML5 and propagated changes, the new version didn’t apply to the other Storefront servers on the server group. I just manually updated them so it’s not really a big deal, though I wonder if the propagate change actually worked for you and I just missed doing something?
I’m pretty sure it used to work but maybe not any more. I’ll update the article.
Hi Carl. What has your experience been with socket pooling? I just ask because I saw a Citrix article mentioning cases of resource exhaustion. Thanks
I don’t enable it so I don’t have any experience but I have heard from some others reporting issues with it.
Hi,
I have trouble on a fresh install to join storefrontsrv to an existing storefrontsrv:
STOREFRONTSRV01 is the main storefrontsrv and it’s new
STOREFRONTSRV02 is the secondary server (new too)
Here the error I have in the windows log from STOREFRONTSRV01 (and I have same on STOREFRONTSRV02):
Une erreur s’est produite lors de l’exécution de la commande : ‘Remove-DSClusterMember’
L’accès est refusé.
Au caractère C:\Program Files\Citrix\Receiver StoreFront\Management\Cmdlets\ConfigurationReplicationModule.psm1:146 : 5
+ Clear-DSConfigurationReplicationClusterMemberCache
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
L’accès est refusé.
Citrix.DeliveryServices.PowerShell.Command.RunnerInterfaces.Exceptions.PowerShellExecutionException, Citrix.DeliveryServices.PowerShell.Command.RunnerInterfaces, Version=3.22.0.0, Culture=neutral, PublicKeyToken=e8b77d454fa2a856
Une erreur s’est produite lors de l’exécution de la commande : ‘Remove-DSClusterMember’
L’accès est refusé.
Au caractère C:\Program Files\Citrix\Receiver StoreFront\Management\Cmdlets\ConfigurationReplicationModule.psm1:146 : 5
+ Clear-DSConfigurationReplicationClusterMemberCache
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
System.Management.Automation.ActionPreferenceStopException, System.Management.Automation, Version=3.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35
L’exécution de la commande s’est arrêtée, car la variable de préférence « ErrorActionPreference » ou le paramètre courant a la valeur Stop : L’accès est refusé.
System.Management.Automation.Interpreter.InterpretedFrameInfo: System.Management.Automation.Interpreter.InterpretedFrameInfo[]
à System.Management.Automation.Internal.PipelineProcessor.SynchronousExecuteEnumerate(Object input, Hashtable errorResults, Boolean enumerate)
à System.Management.Automation.PipelineOps.InvokePipeline(Object input, Boolean ignoreInput, CommandParameterInternal[][] pipeElements, CommandBaseAst[] pipeElementAsts, CommandRedirection[][] commandRedirections, FunctionContext funcContext)
à System.Management.Automation.Interpreter.ActionCallInstruction`6.Run(InterpretedFrame frame)
à System.Management.Automation.Interpreter.EnterTryCatchFinallyInstruction.Run(InterpretedFrame frame)
Une exception s’est produite lors de la restauration suite à l’échec du déploiement du groupe de serveurs.
Citrix.DeliveryServices.PowerShell.Command.RunnerInterfaces.Exceptions.PowerShellExecutionException, Citrix.DeliveryServices.PowerShell.Command.RunnerInterfaces, Version=3.22.0.0, Culture=neutral, PublicKeyToken=e8b77d454fa2a856
Une erreur s’est produite lors de l’exécution de la commande : ‘Remove-DSClusterMember’
L’accès est refusé.
Au caractère C:\Program Files\Citrix\Receiver StoreFront\Management\Cmdlets\ConfigurationReplicationModule.psm1:146 : 5
+ Clear-DSConfigurationReplicationClusterMemberCache
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
à Citrix.DeliveryServices.PowerShell.Command.Runner.PowerShellCommandRunner.RunCommand(IPowerShellCommand command)
à Citrix.DeliveryServices.ClusterService.PowerShell.DeploymentSteps.DeploymentBase.Deploy()
System.Management.Automation.ActionPreferenceStopException, System.Management.Automation, Version=3.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35
L’exécution de la commande s’est arrêtée, car la variable de préférence « ErrorActionPreference » ou le paramètre courant a la valeur Stop : L’accès est refusé.
System.Management.Automation.Interpreter.InterpretedFrameInfo: System.Management.Automation.Interpreter.InterpretedFrameInfo[]
à System.Management.Automation.Internal.PipelineProcessor.SynchronousExecuteEnumerate(Object input, Hashtable errorResults, Boolean enumerate)
à System.Management.Automation.PipelineOps.InvokePipeline(Object input, Boolean ignoreInput, CommandParameterInternal[][] pipeElements, CommandBaseAst[] pipeElementAsts, CommandRedirection[][] commandRedirections, FunctionContext funcContext)
à System.Management.Automation.Interpreter.ActionCallInstruction`6.Run(InterpretedFrame frame)
à System.Management.Automation.Interpreter.EnterTryCatchFinallyInstruction.Run(InterpretedFrame frame)
L’association a échoué. Une exception s’est produite lors de la tentative de confirmation de la configuration de la machine que vous associez.
Citrix.DeliveryServices.PowerShell.Command.RunnerInterfaces.Exceptions.PowerShellExecutionException, Citrix.DeliveryServices.PowerShell.Command.RunnerInterfaces, Version=3.22.0.0, Culture=neutral, PublicKeyToken=e8b77d454fa2a856
Une erreur s’est produite lors de l’exécution de la commande : ‘Add-DSClusterMember’
L’accès est refusé.
Au caractère C:\Program Files\Citrix\Receiver StoreFront\Management\Cmdlets\ConfigurationReplicationModule.psm1:146 : 5
+ Clear-DSConfigurationReplicationClusterMemberCache
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
à Citrix.DeliveryServices.PowerShell.Command.Runner.PowerShellCommandRunner.RunCommand(IPowerShellCommand command)
à Citrix.DeliveryServices.ClusterService.PowerShell.DeploymentSteps.DeploymentBase.Deploy()
à Citrix.DeliveryServices.ClusterService.Service.ServiceController.ExecuteSetupAuthorizer(ClusterConfirmRequest clusterRequest)
System.Management.Automation.ActionPreferenceStopException, System.Management.Automation, Version=3.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35
L’exécution de la commande s’est arrêtée, car la variable de préférence « ErrorActionPreference » ou le paramètre courant a la valeur Stop : L’accès est refusé.
System.Management.Automation.Interpreter.InterpretedFrameInfo: System.Management.Automation.Interpreter.InterpretedFrameInfo[]
à System.Management.Automation.Internal.PipelineProcessor.SynchronousExecuteEnumerate(Object input, Hashtable errorResults, Boolean enumerate)
à System.Management.Automation.PipelineOps.InvokePipeline(Object input, Boolean ignoreInput, CommandParameterInternal[][] pipeElements, CommandBaseAst[] pipeElementAsts, CommandRedirection[][] commandRedirections, FunctionContext funcContext)
à System.Management.Automation.Interpreter.ActionCallInstruction`6.Run(InterpretedFrame frame)
à System.Management.Automation.Interpreter.EnterTryCatchFinallyInstruction.Run(InterpretedFrame frame)
Do you have an idea of the problem ?
1912 CU2?
I’ve seen a couple threads at Citrix Discussions reporting a similar problem that seems to be only on non-English systems. E.g. https://discussions.citrix.com/topic/411515-storefront-second-server-initial-join-failed/. You might have to call Citrix Support.
Hi Carl, Thanks for the hint, I have change the language (back to english) but I always have the same error, think I have no other choice to call citrix support
For information, it works, all is needed is to REMOVE language pack (not only change to english), after uninstalling language pack, just reboot, and do it again, all work fine now. Thanks Carl 😉
how do you uninstall 2203 language packs with exception of English?
Hello sir , hope you are doing well
Please advise if we can upgrade directly from 1906 to 1922 CU2
Yes, you can upgrade directly to 1912 CU2.
Hi Carl, we really need to modify the hosts file ?
It depends. If you enable Loopback in Receiver for Web then you don’t need to. If the callback resolves to the Gateway VIP then you don’t need to.
Hi Carl,
Is it possible to upgrade storefront version 3.0.1.56 -> straight to -> 3.12.6000.8, or does this require an upgrade to a version in between first ?
You can upgrade directly. https://docs.citrix.com/en-us/storefront/3-12/install-standard.html#upgrade-storefront
Hi Carl, when configuring external beacon should we add all of our citrix gateway addresses in there along with http://ping.citrix.com ?
It only needs enough to confirm that the Workspace app has Internet access.
Right but sometimes we get “Cannot Contact Store” when logging externally.
we have 3 gateway addresses
Hi Carl , How we can avoid the Prompt for users at NetScaler gateway while we choose “Use receiver for html5 if Citrix receiver fails ” . I wanted to use html5 as default but if user has Citrix Receiver then it should use Receiver to launch .
StoreFront needs to detect local Receiver. Modern browsers require the user to click a button before a website can access a local app.
we have issues with new installations of Storefront 1912 CU2 on Server 2019 (german language version, reproducable). Always got errors when trying to add a cluster member.. Installation auf 1912 CU1 and update to CU2 works..
Hello Carl,
One item i noticed post 1912 CU2 that it would not expand categories view if Collapsed Category view was selected. It seems the btn changed from categoriestabbtn to folderHierarchyFilterBtn. Once i updated in script.js, this seem to bring me closer to what i was looking for. I just wanted to share this, with anyone else that may be running across this.
Thanks!
Thank you Thank you Thank you. This was driving me crazy.
Hello
I am deploying a storefront using PowerShell.
I don’t know why the webapplication field is empty?
when I deploy using the GUI the webapplication will be:
Citrix.DeliveryServices.Web.IIS8.Impl.WebApplication8
PS C:\Users\administrator> Get-STFWebReceiverService
WebReceiverSettings : {}
WebReceiver : Citrix.StoreFront.Model.ReceiverForWeb.WebReceiver
DefaultIISSite : False
ServiceId : 5b16e797-fd33-46fd-ba36-1c6c95b50dd4
ProducerService : Receiver for Web Token Producer
ConsumerService : Receiver for Web Token Consumer
ServiceTokenCertificate : 043CC6C5F54E27A6A6871B1E8A3D4420A081302C
AuthenticationServiceVirtualPath : /Citrix/auth
StoreServiceVirtualPath : /Citrix/Store
HostingEnvironment : Citrix.StoreFront.Model.WebServices.HostingEnvironment
RunAllManagedModulesForAllRequests : False
SiteId : 1
VirtualPath : /bahonar
FriendlyName : Store Receiver
FeatureData : {[SiteID, 1], [VirtualPath, /bahonar], [ApplicationPool,
Citrix Receiver for Web], [DefaultDocuments,
Default.htm]…}
Name : bahonar
Hmacs : {appShortcuts:Vi2NqFB6kPFYgek60K8eKFrNJYo9Ciyd7eSlj6VW2FGPs
GFdK2bK7tdGmMEbxxBki0O5qIWEpWoBB4awW789lA==, rfWebGeneric:/
grau/2sIV1TGwg/iQb6Skirp3YhHtenQ29BqIDhrIyBJmHrKVmZOG69ocPT
SVhmdRNtwCW5o1dQrzs6tj5KZA==}
Certificates : {043CC6C5F54E27A6A6871B1E8A3D4420A081302C,
DA6EFFF06F81DD2BE38E0B97C1802ABB3609FF1F}
TokenManagers : {Receiver for Web Token Consumer, Receiver for Web Token
Producer}
Routing : :
CredentialWallet :
WebApplication :
ServiceRef : 1__bahonar
PhysicalPath : C:\inetpub\wwwroot\bahonar
Diagnostics : Citrix.StoreFrontConfiguration.Model.Common.ServiceDiagnost
ics
ApplicationInitialization : Citrix.StoreFrontConfiguration.Model.Common.ApplicationInit
ialization
FeatureInstanceId : c06a12fe-c13f-434d-82fe-15c778d846a4
Configuration : System.Configuration.Configuration
ConfigurationFile : C:\inetpub\wwwroot\bahonar\web.config
TenantId : 860e9401-39c8-4f2c-928d-34251102b840
I don’t know how to change webapplication field using command line interface.
Best regards
I have installed Virtual Apps and Desktops components using commandline.
during VDA installation when entering Delivery Controller address, I see this error:
No running instance of a controller was found on ‘server1’.
I have checked the The following items and all of them is ok:
-telnet
-network connection
-ping (ip and fqdn)
-dns
-firewall
The command I used to install Virtual Apps and Desktops:
.\XenDesktopServerSetup.exe /quiet /components controller,desktopstudio,licenseserver /configure_firewall
The commands I used to create databases:
New-XDDatabase -SiteName MySite -DatabaseServer server1\sqlexpress -DatabaseName MySite_SiteConfig -DataStore Site
New-XDDatabase -SiteName MySite -DatabaseServer server1\sqlexpress -DatabaseName MySite_Log -DataStore Logging
New-XDDatabase -SiteName MySite -DatabaseServer server1\sqlexpress -DatabaseName MySite_Monitoring -DataStore Monitor
The command I used to setup the site:
New-XDSite -SiteName MySite -SiteDatabaseServer server1\sqlexpress -SiteDatabaseName MySite_SiteConfig -LoggingDatabaseServer server1\sqlexpress -LoggingDatabaseName MySite_Log -MonitorDatabaseServer server1\sqlexpress -MonitorDatabaseName MySite_Monitoring
Output of Get-BrokerSite command:
BaseOU :
BrokerServiceGroupUid : cfb2c787-d539-42ae-bf3f-525557d08a44
BypassAuthForCachedResources : False
ColorDepth : TwentyFourBit
ConfigLastChangeTime : 11/8/2020 12:31:17 AM
ConfigurationServiceGroupUid : eae39b43-8bab-4cbe-ae31-9078e2944f30
ConnectionLeasingEnabled : False
CredentialForwardingToCloudAllowed : False
DefaultMinimumFunctionalLevel : L7_9
DeleteResourceLeasesOnLogOff : False
DesktopGroupIconUid : 1
DnsResolutionEnabled : False
IsSecondaryBroker : False
LicenseEdition : PLT
LicenseGraceSessionsRemaining :
LicenseModel : UserDevice
LicenseServerName :
LicenseServerPort : 27000
LicensedSessionsActive : 0
LicensingBurnIn : 2020.0515
LicensingBurnInDate : 5/14/2020 5:00:00 PM
LicensingGraceHoursLeft :
LicensingGracePeriodActive : False
LicensingOutOfBoxGracePeriodActive : False
LocalHostCacheEnabled : True
MetadataMap : {}
Name : MySite
PeakConcurrentLicenseUsers : 0
PeakConcurrentLicensedDevices : 0
RequireXmlServiceKeyForNFuse : False
RequireXmlServiceKeyForSta : False
ResourceLeaseValidityPeriodInDays : 0
ResourceLeasingEnabled : False
ReuseMachinesWithoutShutdownInOutageAllowed : False
SecureIcaRequired : False
TotalUniqueLicenseUsers : 0
TrustManagedAnonymousXmlServiceRequests : False
TrustRequestsSentToTheXmlServicePort : False
UseVerticalScalingForRdsLaunches : False
XmlServiceKey1 :
XmlServiceKey2 :
Where does the problem probably come from?
I posted this question under this topic by mistake
Hi Carl,
How to force users to use HTTPS connecting to Storefront. Only one storefront and no Netscaler.
TIA
In IIS, you can configure a redirect. StoreFront’s Default Web Site feature will do that for you.
Or in IIS, go to Edit Bindings and remove the http binding.
Carl,
I’m having an issue in an existing VDA Deployment with regards to WebCam functionality.
It seems they are not being detected or available for use in Video Conferencing Software such as WebEx. I’ve ensured that the Hooks are Whitelisted and even tried excluding the Citrix hooks altogether for “atmgr.exe” (Cisco Webex)…. Then I noticed something…
When using Citrix Receiver HTML5 ,we don’t even see the devices detected in device manager on the VDAs themselves. Is this a limitation of Workspace app for HTML5/Citrix Receiver for HTML5? I can’t seem to find product docs which state support for USB/Device redirection outside of generic Video/Content redirection etc..
I would like to rule this out, but can’t seem to find information about Compatibility or Feature limitations.
HTML5 Workspace app does support generic USB. https://www.citrix.com/blogs/2020/03/24/citrix-workspace-app-for-html5-now-supports-generic-usb-device-redirection/
Hi Carl, after updating from 7.15 CU3 to CU6 now when I launch what should be a single-monitor Published Desktop it shows fine on one monitor but on my second monitor shows half black and half white. I have opened a case with Citrix support (they already spun their wheels for two hours) but if you have some magic it would be much appreciated!
Dear Guys,
Thank you very much for your efforts for helping us to make everything simple and clear. I did everything as mentioned above BUT while using HTML5 I got “Error
Citrix Workspace app cannot create a secure connection in this browser. Please refer to Citrix Knowledge Center article CTX134123”
Kindly, How can I fix this problem in details without deploying Citrix ADC (Gateway) ?
You would have install certificates on your VDAs and enable HDX SSL. https://www.carlstalhood.com/virtual-delivery-agent-vda-cr/#sslvda
Hello Carl,
There are keywords: Primary and Secondary. This keyword is useful when using a dual site setup. e.g. you have an application published in both sites and published using the same name but you want the users of that app to stay in site A. Only when Site A is not able to delivery the app from Site a the App displayed will be from site B. can you please add steps to configure the parameters.
Cheers
Kunal
I mention them at https://www.carlstalhood.com/storefront-cr-configuration-for-citrix-gateway/#aggregation
Hello Carl,
I updated to storefront 1912 – It functions well with one exception the workspace app is not showing the new storefront without a reset(The web is updated and working). I doubt this is expected behavior but was curious if this is something that you have seen before? This doesn’t affect user functionality of course but I wanted to see if perhaps there was something I could do on the storefront server to resolve this without saying to users – “reset the workspace app”. The workspace app is 2002.
It doesn’t surprise me that a reset might be needed. You can script the reset. https://support.citrix.com/article/CTX140149