This article applies to Citrix Gateway 13.0, Citrix Gateway 12.1, and NetScaler Gateway 12.0. Citrix ADC is the new name for NetScaler. Citrix Gateway is the new name for NetScaler Gateway.
Navigation
💡 = Recently Updated
Change Log
- 2021 Apr 16 – changed NetScaler Gateway to Citrix Gateway and updated screenshots accordingly.
- 2019 Sep 27 – Create Bookmarks – RemoteApp info from Citrix Discussions
- 2018 Nov 18 – updated screenshots for ADC 12.1
- Added some configuration instructions for RDS Connection Broker servers.
- 2018 Mar 11 – in RDP Proxy Profile section, added RDP Cookie info from CTX233207 RDP Session Fail to Reconnect after NetScaler HA failover, Error “This computer can’t connect to the remote computer.”
- 2018 Jan 2 – in Session Profile section, added link to CTX220499 How to Configure Authorization Policies for RDP Proxy
RDP Proxy Overview
Citrix ADC supports RDP Proxy through Citrix Gateway. No VPN required. RDP can connect through Citrix Gateway on port 443.
There are several ways of launching RDP sessions through Citrix Gateway RDP Proxy:
- Bookmarks on the Clientless Access portal page.
- Bookmarks can be defined by the administrator.
- Or users can add their own RDP bookmarks.
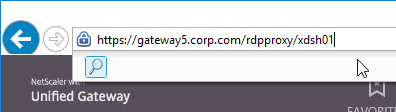
- After logging in, change the URL in the browser to /rdpproxy/MyRDPServer. MyRDPServer can be IP or DNS.
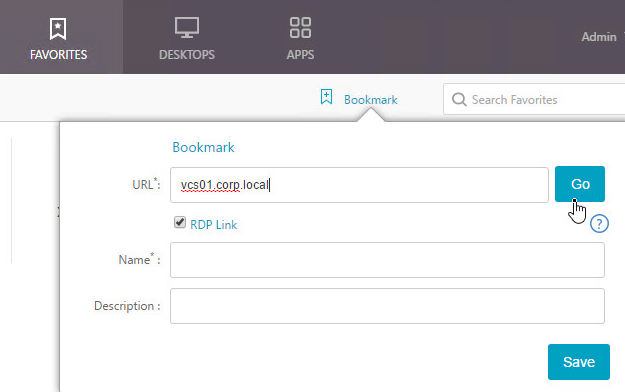
- In the RfWebUI Portal Theme, the Bookmark link lets users enter an RDP address, and click Go.
Links:
- RDP Proxy at Citrix Docs
- Kenny Baldwin blog post RDP-Proxy on NetScaler!
- Citrix CTX200853 How to Configure RDP Profile on NetScaler Gateway
- Anton van Pelt NetScaler Gateway = RD Gateway
- NetScaler 12.1 RDP Connection Redirection at Citrix Discussions
Requirements
Here are some requirements for RDP Proxy:
- Citrix ADC Advanced Edition or Premium Edition.
- Citrix Gateway Enterprise VPX is not sufficient. It must be a full ADC license.
- Citrix Gateway Universal Licenses for each user.
- Most Citrix ADC Editions come with built-in Gateway Universal licenses: Citrix ADC Standard Edition = 500 licenses, Citrix ADC Advanced Edition = 1000 licenses, and Citrix ADC Premium Edition = unlimited licenses. See Feature Licensing in the Gateway Tweaks post.
- TCP 443 opened to the Citrix Gateway Virtual Server.
- TCP 3389 opened from the Citrix ADC SNIP to the RDP Servers.
Configuration
Enable RDP Proxy Feature
- Go to System > Settings, and click Configure Advanced Features.
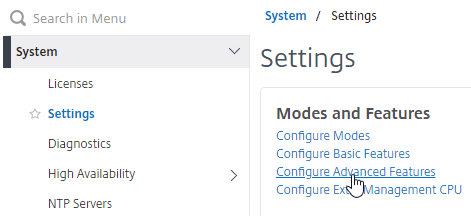
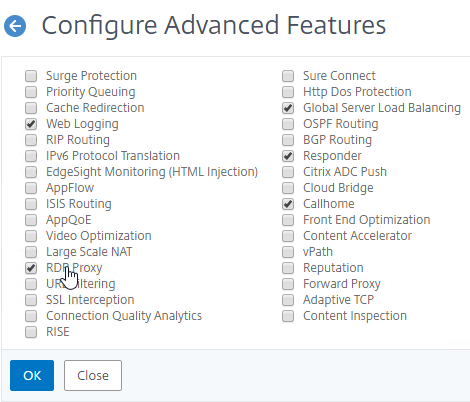
- In the left column, near the bottom, check the box for RDP Proxy and click OK.
Create RDP Server Profile
You do not need a RDP Server Profile if the machines you want to RDP to are not members of any RDS Connection Broker Infrastructure. Skip to the next section to create the RDP Client Profile.
If you want Citrix Gateway to RDP Proxy to a RDSH machine that is part of an RDS Connection Broker Infrastructure (aka RDS Collection, or member of RDS Broker Farm), then you’ll need the following:
- Citrix ADC 12.1 or newer
- NetScaler 12.0 does not support RDSH machines connected to RDS Connection Broker.
- RDP Server Profile to enable the 3389 listener on your Gateway Virtual Server.
RDP connections through Citrix Gateway to RDP Connection Broker members requires that the Remote Desktop Session Hosts are configured to disable the GPO setting Use IP Address Redirection located in a GPO at Computer Configuration | Policies | Administrative Templates | Windows Components | Remote Desktop Services | Remote Desktop Session Host | RD Connection Broker. Disable this setting on the RDSH machines, not the Connection Broker machine. Disabling this setting enables token-based redirection instead of IP-based redirection, which is required by RDP Proxy in Citrix Gateway.
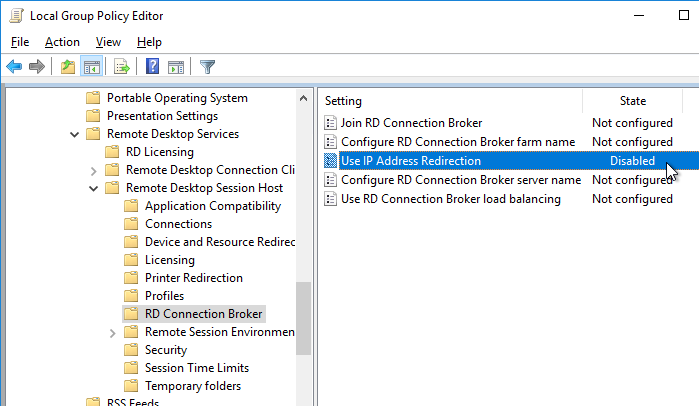
To create the RDP Session Profile on Citrix ADC:
- Expand Citrix Gateway, expand Policies, and click RDP.
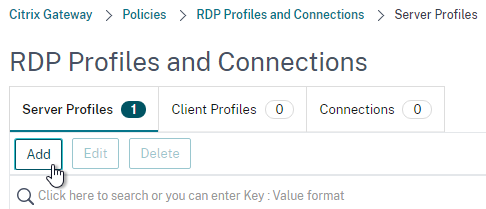
- On the right, on the Server Profiles tab, click Add.
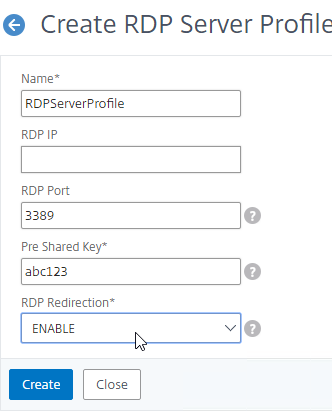
- In the Create RDP Server Profile window:
- Give the RDP Server Profile a name.
- If you don’t enter an RDP IP, then it will use the Gateway VIP.
- If you don’t enter a RDP Port, then it will default to 3389. This is an additional port that must be opened on the firewall.
- Enter a new Pre Shared Key.
- Change RDP Redirection to ENABLE. This is a new feature in ADC 12.1. This setting enables RDS Infrastructure to work.
- Click Create.
Create RDP Proxy Client Profile
All RDP Proxy configurations need an RDP Client Profile.
- Expand Citrix Gateway, expand Policies, and click RDP.
- On the right, switch to the Client Profiles tab, and click Add.
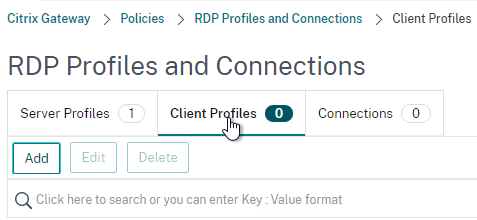
- Give the RDP Client Profile a name, and configure the client device mappings as desired. Scroll down.
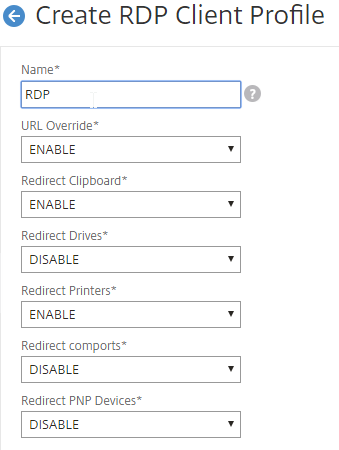
- For the RDP Cookie Validity field, Citrix CTX233207 says that after a HA failover, RDP Proxy session will not reconnect if the cookie has expired.
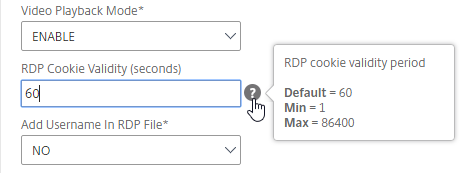
- If you are running ADC 12.1 or newer and need to allow RDP connections to RDS Infrastructure member machines, then enter the same Pre Shared Key that you configured in the RDP Server Profile. If you don’t need to RDP to any member of any RDS Infrastructure, then you don’t need these settings.
- Also, for RDP Host, enter the FQDN of the Gateway Virtual Server. This is only needed for RDP Server Profiles.
- Click Create.
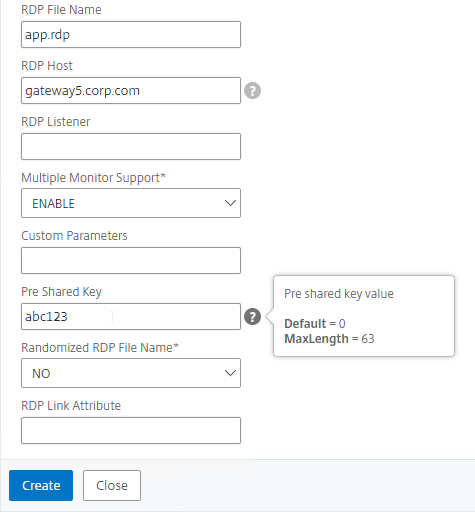
- Give the RDP Client Profile a name, and configure the client device mappings as desired. Scroll down.
Create RDP Bookmarks
You can create administrator-defined bookmarks that can be assigned to everybody or can be assigned to specific Active Directory groups. Another option is to let each user create their own bookmarks.
- On the left, expand Citrix Gateway, expand Resources, and click Bookmarks.
- Alternatively, Simon Gottschlag Publish RDP Proxy Link via StoreFront shows how Citrix ADC Rewrite can insert an RDP Proxy link into a StoreFront web page.
- On the right, click Add.
- Give the Bookmark a name.
- For the URL, enter rdp://MyRDPServer using IP or DNS (FQDN).
- For RDS Collections, enter the address of any RDP member of the collection. The RDP server will ask the Connection Broker to load balance across the Collection and then redirect the RDP connection to the least busy RDP server in the Collection.
- For RemoteApp, see Citrix Discussions. Example URL:
rdp://rdshost1.comtoso.com?alternate shell:s:||win32calc&remoteapplicationprogram:s:||win32calc&remoteapplicationname:s:Calculator&remoteapplicationcmdline:s:&remoteapplicationmode:i:1
- Check the box next to Use Citrix Gateway As a Reverse Proxy,
- Click Create.
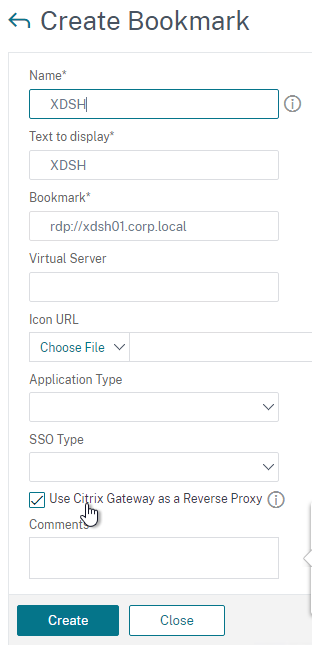
- Create more bookmarks as desired.
Edit a Session Profile
- Create or edit a Gateway Session Profile (Session Profiles tab).
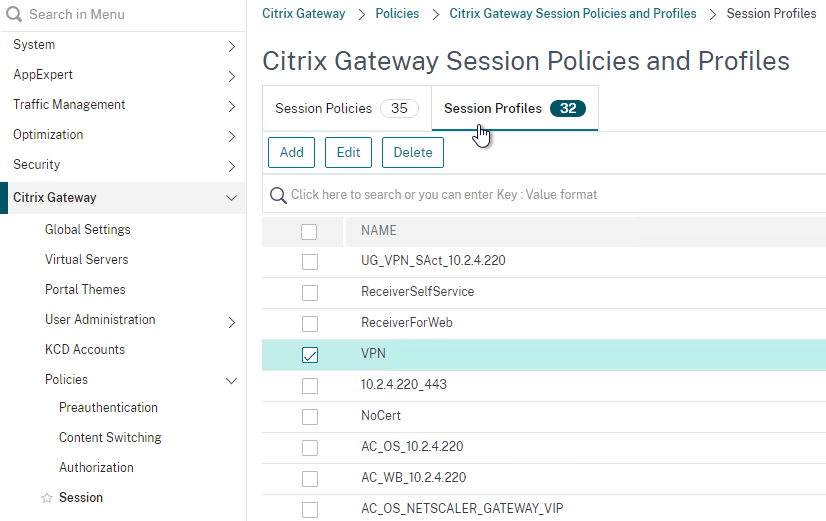
- On the Security tab, set Default Authorization Action to ALLOW. Or you can use Authorization policies to control access.
- CTX220499 How to Configure Authorization Policies for RDP Proxy states that Authorization Policy expressions for RDP Proxy must be HTTP Request-based, not TCP-based. For example: REQ.HTTP.URL CONTAINS 10.107.202.67.
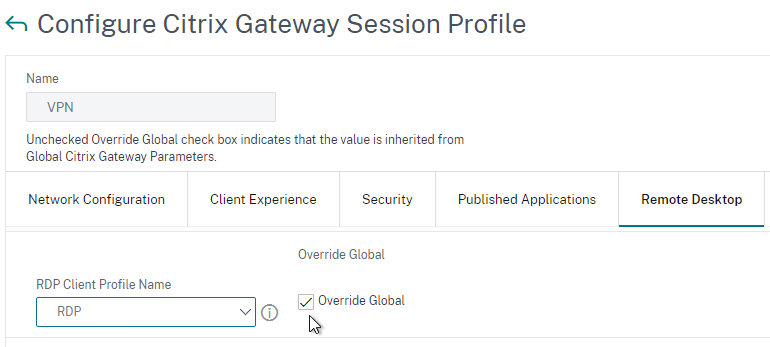
- On the Remote Desktop tab, check Override Global, and select the RDP Client Profile you created earlier.
- On the Client Experience tab, set Clientless Access to On. This enables the clientless access portal that can display administrator-defined bookmarks and lets users add their own bookmarks.
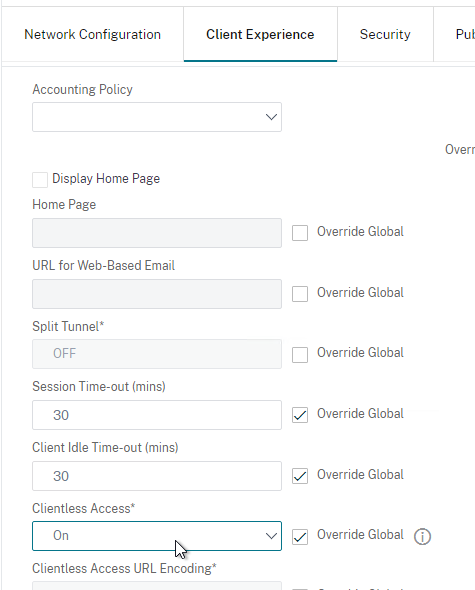
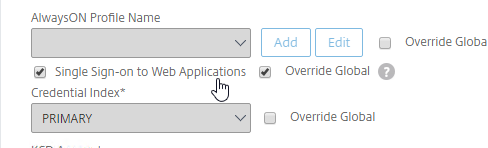
- On the Client Experience tab of the Session Profile, decide if you want Single Sign-on to Web Applications or not. It’s required for RDS Collections but optional for RDP machines that are not members of an RDS Infrastructure. If not checked then the user will be prompted to login again when launching an RDP session.
- On the Published Applications tab, make sure ICA Proxy is OFF so the clientless portal is displayed.
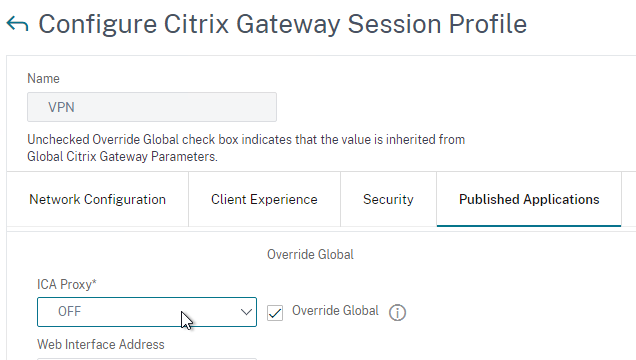
- Click OK when done.
Edit Citrix Gateway Virtual Server
- Edit or Create your Gateway Virtual Server.
- In the Basic Settings section, click the pencil icon on the top right to edit it.
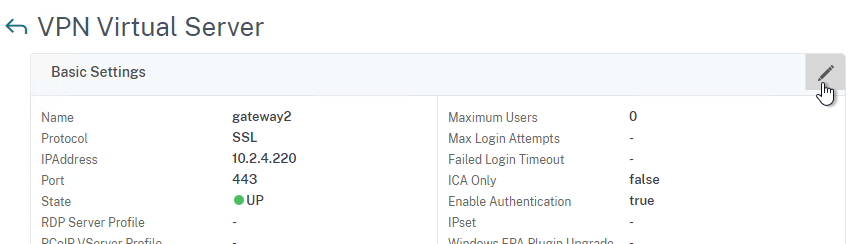
- Click More to show more settings.
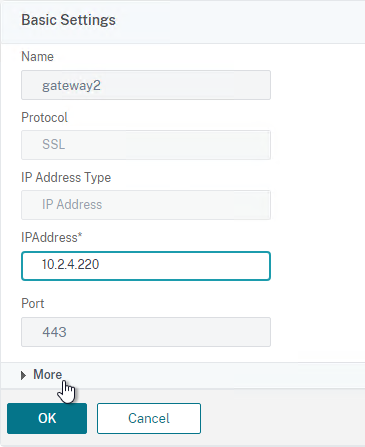
- If the machines you are RDPing to are not members of an RDS Collection, then don’t configure RDP Server Profile. With no RDP Server Profile configured the RDP connections will be 443 to the Gateway. If you instead configure an RDP Server Profile then the RDP Connections will be 3389 or whatever port number you put in the RDP Server Profile.

- If you want to allow RDP to RDS Collection members, then select the RDP Server Profile that you created earlier. The RDP Server Profile enables port 3389 on the Gateway VIP. If you don’t select a RDP Server Profile, then RDP is proxied through 443 on the Gateway, but this won’t work for RDS Collection members.
- Scroll down. Make sure ICA Only is not checked. This means you’ll need Citrix Gateway Universal licenses for each user that connects through this Gateway.
- Click OK to close the Basic Settings section.
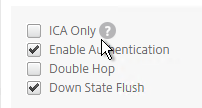
- If the machines you are RDPing to are not members of an RDS Collection, then don’t configure RDP Server Profile. With no RDP Server Profile configured the RDP connections will be 443 to the Gateway. If you instead configure an RDP Server Profile then the RDP Connections will be 3389 or whatever port number you put in the RDP Server Profile.
- Bind a certificate.
- Bind authentication policies.
- In the Policies section, bind the Session Policy that has the RDP Client Profile configured. Be mindful of policy priority.

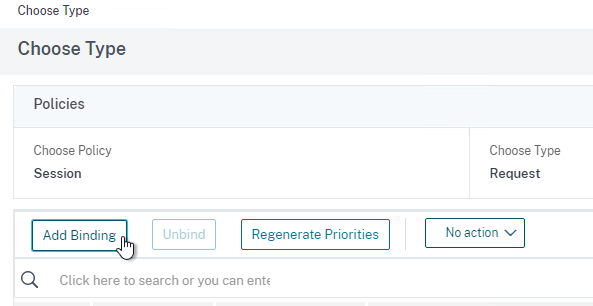
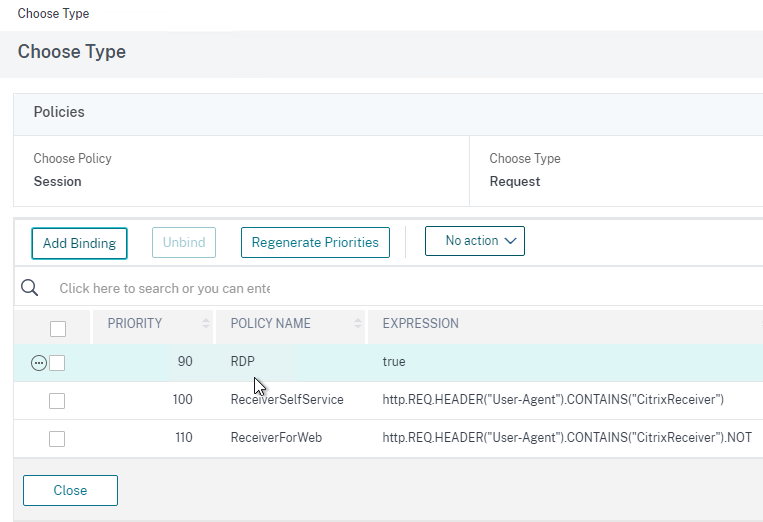
- You can bind RDP Bookmarks to either the Citrix Gateway Virtual Server, or to a AAA group. To bind to the Citrix Gateway Virtual Server, on the right, in the Advanced Settings section, click Published Applications.
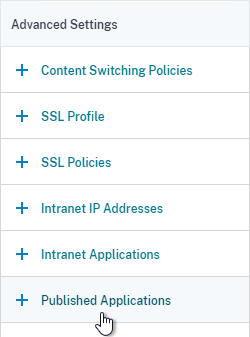
- On the left, in the Published Applications section, click where it says No Url.
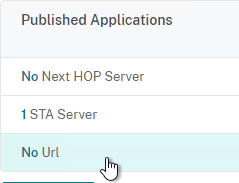
- Bind your Bookmarks.
- While editing your Gateway vServer, you can also set the Portal Theme to RfWebUI. This is strongly recommended for the clientless access portal that displays the RDP bookmarks.
Configure DNS
- If you want to connect to RDP servers using DNS, make sure DNS servers are configured on the appliance (Traffic Management > DNS > Name Servers).
- If you want to use the short names instead of FQDNs, add a DNS Suffix (Traffic Management > DNS > DNS Suffix).
Use RDP Proxy
- Connect to your Citrix Gateway and login.
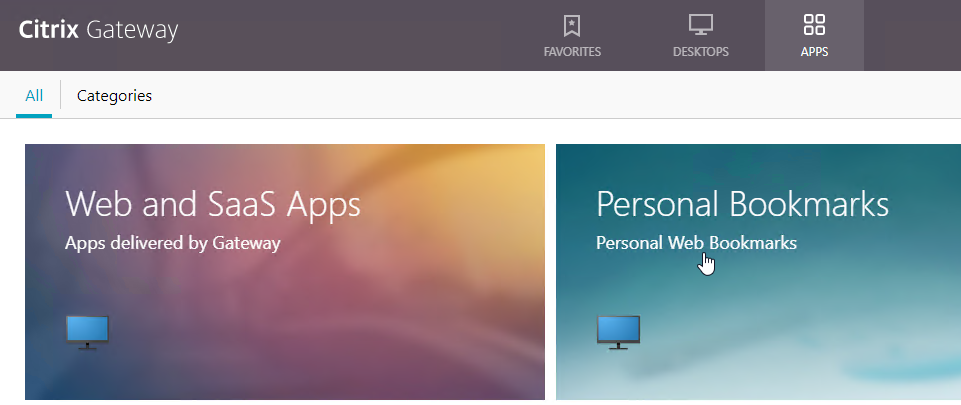
- If you configured Bookmarks, if RfWebUI theme, on the Apps tab, click Web and SaaS Apps.
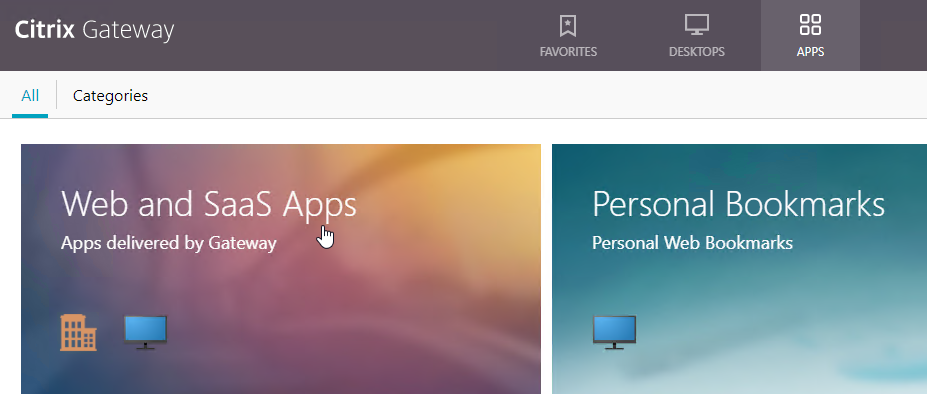
- If X1 theme, the bookmarks are on the Web Apps page.
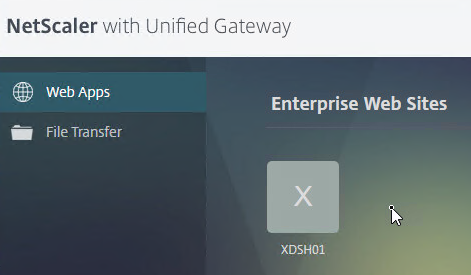
- If X1 theme, the bookmarks are on the Web Apps page.
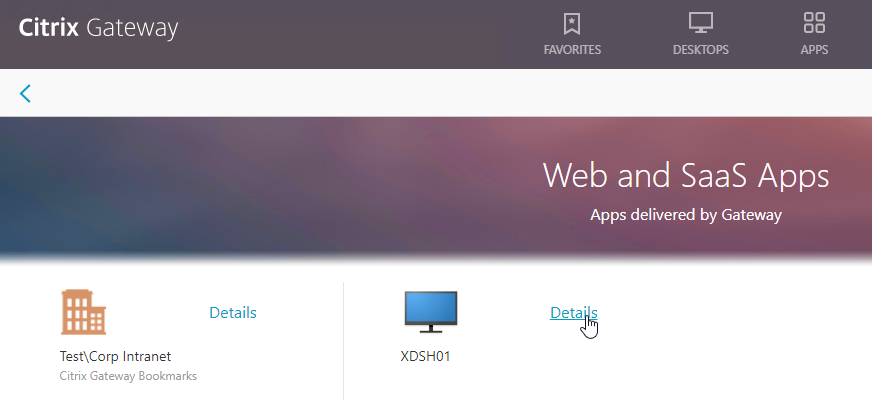
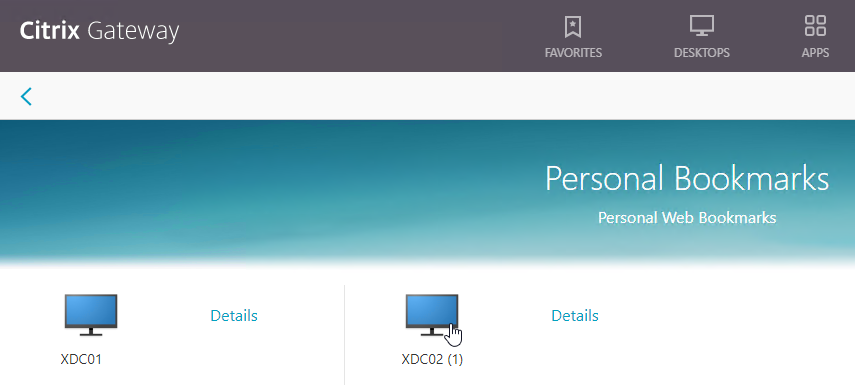
- If RfWebUI theme, you can click Details to mark the Bookmark as a Favorite.
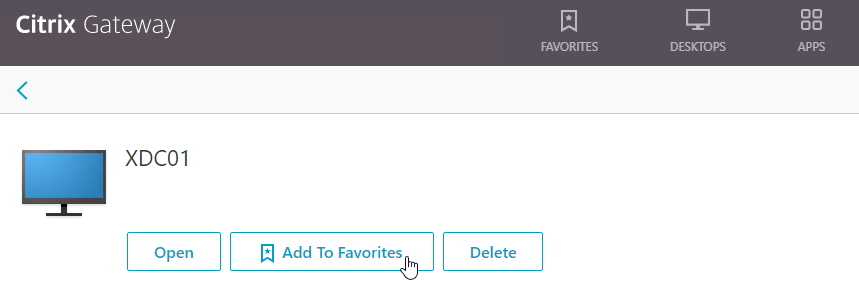
- Or you can change the address bar to /rdpproxy/MyRDPServer. You can enter an IP address (e.g. rdpproxy/192.168.1.50) or a DNS name (/rdpproxy/myserver).
- If you edit the downloaded .rdp file, notice that it’s connecting on port 443.
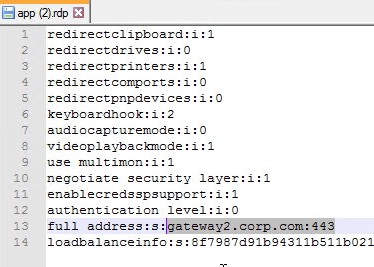
- Then open the downloaded .rdp file.

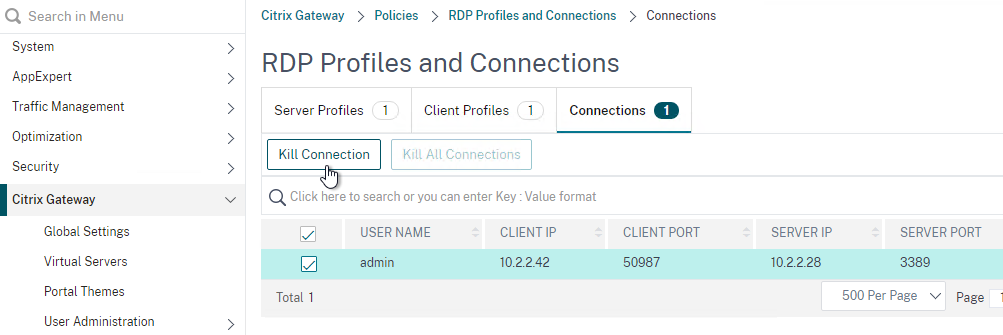
- You can view the currently connected RDP users by going to Citrix Gateway > Policies > RDP, and on the right is the Connections tab.
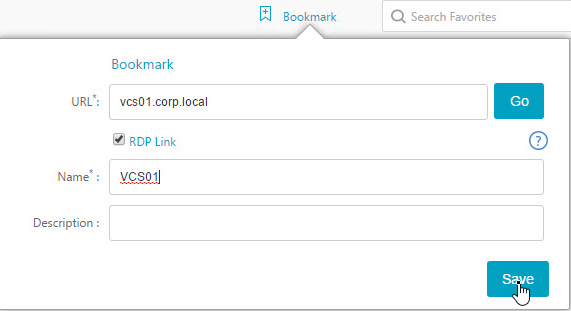
Personal Bookmarks
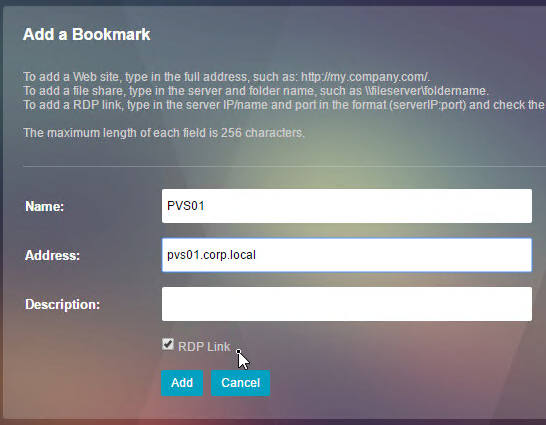
- If using the RfWebUI theme, another way to launch RDP sessions is to click the Bookmark link, enter a destination DNS/IP, check the box next to RDP Link, and click Go.

- You can also give the Bookmark a name and Save it.
- Then access the saved bookmark from Apps > Personal Bookmarks.
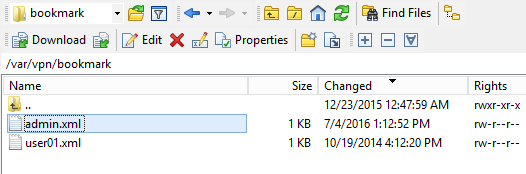
- Personal bookmarks are stored in
/var/vpn/bookmarkon the appliance. You might want to back these up and replicate them to other Gateway appliances participating in GSLB. See NetScaler 11.1 Personal Bookmarks at Citrix Discussions.
- The X1 theme has an Add button on the Web Apps page.
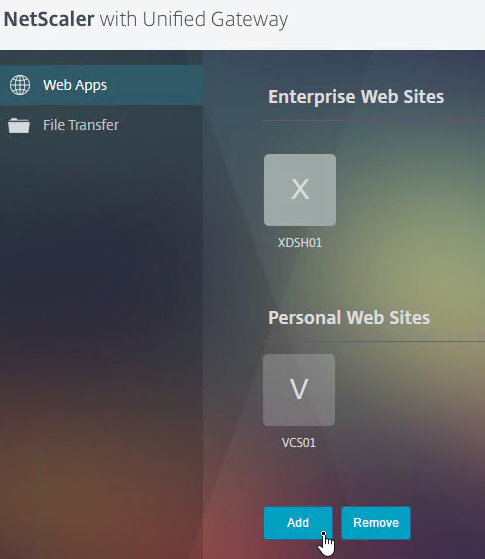
- But there is no Go button. Instead, you save the Bookmark and launch it from the list.
I was configuring this to replace our existing Windows RDWeb and what I found is that I need to add the machine IP’s which we need to RDP to the Services under Load Balancing. Basically followed the guide and it did not work at all until I have added all the IP’s of the machines that we have in the bookmark.
My Question: What if the users who had created Personal Bookmark to RDP to their personal desktop in the office? Do we need to add every desktop IP’s in the Services? I have logged a case to Citrix and it seems like we cant add a range of IP’s in the services.
Hello Carl,
I want to allow clipboard option. It doesn’t work if I enabled the clipboard in RDP client profile. I have checked with direct RDP connection, which works.
Anything I’m missing in gateway configuration?
Dear Carl,
Thank you indeed for this useful content.
What if I would like to use a RDP collections for each different user group. How should I do the configuration then?
Thank you in advance for your reply!
Are you referring to Bookmarks on the NetScaler? If so, create AAA Groups and assign Bookmarks to the AAA Groups.
If you’re referring to RDS Connection Broker, see https://docs.netscaler.com/en-us/netscaler-gateway/current-release/rdp-proxy/rdp-redirection.html#deploy-rdp-proxy-in-the-presence-of-a-connection-broker
Hi Carl, Great content as always. I have a requirement when using RDP proxy some users require multiscreen and some require single screen even though they have multiscreen machines. I know you can configure the client profile for a virtual server then assign a bookmark url to the virtual server but it will always use that one client profile. Is there a way you can use one VS with multiple bookmarks and assigning different client profiles to each bookmark one that supports single monitor and one that supports multiscreen monitor. Users are authenticating using a radius server as well. thanks.
Depending on users preferences, either turn on or off MultiMonitor for all users.
Then create individual Bookmarks for the devices that need to use the other option.
Bookmark:
rdp://workstationname?use%20multimon:i:1
or define which monitors to use as well..
rdp://workstationname?use%20multimon:i:1&selectedmonitors:s:0,2
Hi, the folder I download RDP files to is really full, is there a way to click on the BOOKMARK ICON and the login window will open immediately (without downloading an RDP file)?
Hi Carl,
• Secure RDP traffic through clientless VPN or ICA Proxy mode (without Full Tunnel).
https://docs.netscaler.com/zh-cn/citrix-gateway/current-release/rdp-proxy.html
do you guide the ICA Proxy mode RDP proxy?
I had set this up last year and it was working fine. Went to try it out again recently but we’re getting an “Http/1.1 Internal Server Error 43549” error now when we load up the url https://adc.domain.com/rdpproxy/MyServerName
Haven’t been able to figure out why yet. Any suggestions?
Can NetScaler resolve the hostname? Does it work with IP instead of hostname?
It can resolve ‘servername.domain.internal’, but not just ‘servername’.
Same error occurs when we try the IP address.
Any update to this?
We are having the same issue after an upgrade to 13.1 49.13
Similar to this thread? https://discussions.citrix.com/topic/417036-rdp-proxy-http11-object-not-found/page/3/
Or this? https://support.citrix.com/article/CTX475152/mac-users-are-getting-http11-internal-server-error-43549-after-upgrading-adc-to-1313352
Hello Carl!
We use the RDP proxy for our customer and authenticate ourselves against the customer’s Azure. Then we start the RDP connection and get a login dialog because the login to the RDP server should be done with different credentials. So far so good!
But now it is necessary to change the credentials when logging in for the first time, namely for access to the RDP server, i.e. not the credentials from Azure. Now my idea was to provide RDWeb access for changing passwords. The RDWeb works fine on the RDP server, but when I make it available via a bookmark URL to the RDWeb, I cannot call it. Does anyone here have an idea?
Hi Carl, great article and I’m looking to publish RD session host sessions (yes part of a collection) through the ADC because I need to also implement 2FA using in-platform RSA (the customer is PCI-DSS).
I must be reading this bit wrong though because it reads to me like I should open tcp:3389 to the internet which is never going to happen. Can you clarify this bit for me please?
If the machines you are RDPing to are not members of an RDS Collection, then don’t configure RDP Server Profile. With no RDP Server Profile configured the RDP connections will be 443 to the Gateway. If you instead configure an RDP Server Profile then the RDP Connections will be 3389 or whatever port number you put in the RDP Server Profile.
If you want to allow RDP to RDS Collection members, then select the RDP Server Profile that you created earlier. The RDP Server Profile enables port 3389 on the Gateway VIP. If you don’t select a RDP Server Profile, then RDP is proxied through 443 on the Gateway, but this won’t work for RDS Collection members.
Sorry, I haven’t done this in years. I remember some threads in Citrix Discussions about this, but I currently can’t find the threads.
Also see: https://www.thomaspreischl.de/citrix-adc-as-rds-gateway-with-rds-broker/
Hi, I am having the same issue as you. Did you find any workaround for this? I can change the port on the RDP Server Profile to another IP (eg 5566) but I end up unable to connect to any RDS in RDS collection, only standalone are fine.
We plan to open up this feature to replace our existing RDWeb (we change our RDP port) but this are the show stopper. Fixed one issue, create another.
Hi Carl, thank you for your research, rdp proxy is working fine. We want to use it for publishing an mstc . The only issue is, that, if you connect to the gateway with an linux or max client and open the published app you will be directly connected to the desktop of the terminalserver. This issue consists only on linux or mac clients.
Is it possible to prevent that somehow?
Thanks a lot!
Jens
One other question if you have a moment, my applications are mostly working except for some that get hung on “Estimating connection quality…” and popup a window RemoteApp Disconnected “Because of a protocol error, this session will be disconnected. Please try connecting to the remote computer again.” I have upgraded from 12.1 to 13.1 and it started happening after the upgrade. Any ideas? I run through a great number of things and can’t isolate the issue.
Same problem here. Did you find any solution?
We have an RD broker environment. Session establishment is successful if session establishment on RD host as specified by bookmark. If the connection is redirected by the broker to another RD host, the connection will fail (“Estimating connection quality…” and popup a window RemoteApp Disconnected “Because of a protocol error”)
Erik, after spending a couple hours we figured out that all links in the bookmarks that are directed at a set of apps hosted on multiple hosts must be all directed to only one of those hosts. Eg. if host1 and host2 are serving app1, app2, and app3 then the bookmarks must all point either to host1 or host2, but not a mix. Once we made sure all the addresses pointed to one host in a collection, all was good again.
Hi Erik, we have the same problem at the moment when we upgraded our ADC. Did you find a solution to this?
Hi Daniel, we opened a case at citrix last days. Citrix assumes a bug in their Netscaler firmware: “…known issue on the Citrix ADC 13.1 version with bug ID: NSHELP-33063. The fix will be on version Citrix 13.1 37.x which has tentative release date of mid November 2022. However this issue is not seen in Citrix 13.0 version”
Issue is seen on 13.0 88.14 and 88.16!
Carl, everything is setup per your instructions, and we continue to get “estimating connection quality” when trying to launch RDP icons. Specifically with RDP itself. Other RemoteApps work intermittent. We are running on ADC 13.1-33.47nc.
This was working previously in 13.0.
Your articles are great and very much appreciated. Is is possible to use SAML for an authentication policy instead of LDAP? I see you have an article for setting up the ADC as a SAML SP https://www.carlstalhood.com/citrix-federated-authentication-service-saml/#samlgateway111 could that be used? I’m trying to configure our RDP Proxy to use a 3rd party IdP. Any help is appreciated.
One problem with SAML is lack of user password so users would be prompted to login again when connecting to the RDP session. I have not tested this.
Thanks for the response. Another engineer I asked said “From my understanding you are using RDWeb. RDWeb is not claims aware and does not support SAML. It might be possible with RD Gateway within Azure, but I have never heard of a success story yet.” Sounds like there’s several reasons it’s not possible. That’s too bad.
Hi,
If you use Devolutions RDM, please vote for RDP Proxy integration feature request https://forum.devolutions.net/topics/36847/launch-rdp-connections-via-citrix-netscaleradc-rdp-proxy
Thanks
Gold mine of a page, thank you for the information!
The user profiles in the /var/vpn/bookmark/ folder. If we delete one of those, do they automatically get recreated when the user logs back in? Also I noticed that some of the files have ‘root’ as the owner, but most of them have ‘nobody’ as the owner. Any reason for that? Thank you !
When the user creates another bookmark it should re-create.
There were some vulnerabilities a couple years ago. Maybe they weren’t cleaned up after fixing the vulnerability.
Hi Carl,
I have an interesting issue and not sure how I can resolve this. I have a GSLB configuration that splits users internally on the network between Netscaler A (North) and NetScaler B (South). Whenever we use RDP Proxy internally from the South is works great. When we use it from the North it errors out with a security error.
I figured out that when using RDP Proxy via North (I believe this is what’s happening) the RDP connection attempts to go via the South NS and gets dropped because the connection was originated in the North NS. If I change the server RDP Profile to include the Listener IP for the North then it works fine.
I would like to have it where I don’t have to add the RDP Listener to the North NS. I’m also sure this was working fine when first configured. It was recently just brought to my attention.
If you have any ideas how I can do this or have seen this issue before any advise is always appreciated.
Thanks and have a great weekend.
Is there a GSLB persistence problem? What persistence do you have configured?
Have you tried the stateless configuration? https://docs.citrix.com/en-us/netscaler-gateway/12/rdp-proxy.html#stateless-dual-gateway-compatibility
That was it, it was persistence. It was configured to use the source IP, but I changed to use HTTP Persistence and that did the trick. Now it works correctly every time and I don’t need the Listener IP.
You’re the man! Thanks a bunch. 🙂
Hi Carl,
I previously used this article to configure RDP Proxy. That has worked great! However, more recently I have added GSLB to the mix. GSLB is working, but now I am getting an “Internal error has occurred” when I use an RDP Proxy link. This only happens externally, internally on the network the RDP Proxy works great. Any chance you may have encountered this RDP Error when using GSLB?
Appreciate your help and knowledge!
Hi Carl, I have been able to get RDPProxy working as per your helpful instructions. However, I am running into an issue when I try to also integrate StoreFront/VAD apps into the same Gateway.
I have 2 separate session policies: 1 for RDP PRoxy, and One for ReceiverforWeb, same as your guide. If I bind only one policy to the server, it works. But if I bind both policies to the vserver, RDPRoxy fails to work. MY RDP bookmarks are there (under Desktops), and my VAD apps are in the Apps tab. I can launch the app fine. But when I download the RDP file from the bookmark and launch it, RDP client just generates message: “An internal error has occurred”.
So far I have stumped Citrix support, but in your guide it looks so simple! Any help appreciated.
I am using RFWebUI on ADC 12.1, and VAD 1912.
Hi Carl, when creating the RDP Proxy and creating an RDP Listener on port 3389 (default), enabling Clientless Access, etc, when the RDP client makes a connection to the RDP Listener on the NetScaler, how is the data encrypted between the mstsc.exe client and the NetScaler? There is very little Citrix-supplied info on how secure this configuration is for users coming in over the internet. Can someone sniff the data while it’s in transit?
Regards
Ken Z
Hi Carl
it’s OK, did some packet sniffing myself and confirmed that it connects to the RDP Listener using TLS 1.2.
Regards
Ken
Hi Carl,
Have you seen any issues with connecting to Windows 7 machines with SSO? We can connect to Win 10 fine, and a fresh WIn7 PC fine. But when we install all the WIndows Updates it now gives an error on the client “An internal error occurred”.
If we disable SSO it works too…
Are you aware of any specific Win 7 hotfixes that break RDP Proxy SSO?
Thanks!
With RDP proxy set up, I click the RDP bookmark, I download the RDP file, and then when I try to connect I get a warning message from the RDP app essentially saying “Unknown publisher.” My gateway virtual server has a 3rd party certificate bound, and the certificate chain appears correct from the browser. Is the RDP file using a different cert and if so, any idea where I would configure that?
We have the same issue. For managed laptops I can suppress the warning by enabling “Specify SHA1 thumbprints of certificates representing trusted .rdp publishers” GPO and entering SHA1 thumbprint from the certificate in capitals. But for 3rd party contractors we have no control over this. A solution would be appreciated.
Did you ever find a resolution to this?
Hi Carl, Great article, as always.
Is connecting through Windows the only way this RDP will work? What about mobile devices like iPad, iPhone, Android?
What happens when you integrate 2 factor authentication and try to use direct link/url? Do you get a second prompt for the second factor?
Thanks!
Martin
Hi Carl – Good evening! Just wanted to confirm something with you, if I want to use RDS Collection via an RDS connection broker then I will need to allow port 3389 to the NSG VIP from the Internet, correct? There is no way to force this to use 443 the way you can with individual RDP connections, right? I just wanted to confirm as most customers cringe at the thought of opening up 3389 on their external firewalls. I guess we could use a custom port instead, what have you done in this scenario? Thanks!
Hi Carl
is there a way to show the hostname in the connection bar?
Thanks
Daniel
HI Daniel,
Did you were you able to fix this issue?
Hi Carl,
Why would you recommend an NetScaler RDP proxy in the front end instead of a directly connected RDS Gateway, connection broker to the outside? Is the only benefit a custom login page and with load balancing so you don’t need Windows Network Load Balanvind and DNS round robin?
Stefan
Hey Carl,
Any change you might be able to shed some light on a problem I am having. I have configured the RDP proxy and everything shows up and works. It is sharing a VS that also has a Citrix implementation, using the RFWeb theme.
The Citrix desktop logs on without an issue. However when I launch the RDP it prompts users to enter there credentials rather than just using the logged on details.
Any ideas on how to fix that?
Thanks
Just to add I have also enabled Single Sign-on to Web Applications, Credential Index is set to primary and Single sign-on with windows is also set to on.
Have you seen this? https://docs.citrix.com/en-us/netscaler-gateway/12/rdp-proxy/stateless-rdp-proxy.html
Hi All, I configured the RDP Proxy for an RDS farm, everything is working correctly. Just one little issue.
It doesn’t seem to be possible to expand the rds session over multiple screens. Is this a limitation, setting we can change?
Kind regards
Go to Netscaler Gateway -> Policies -> RDP-> Client Profiles. Edit your profile set Multiple Monitor Support to Enable.
Carl, thanks for another great article!
I have a question though concerning different RDP profiles using RDP proxy, perhaps you see a way to fit this gap in documentation.
All articles cover the setup of one or more RDP bookmarks, but never connections with multiple RDP settings. (Read RDP client profiles)
In my case I need users to have 2 bookmarks to the same RDS server/farm: one bookmark starts an RDP session on all available monitors and one starts RDP session on a single monitor.
This setting can in my opinion only be configured in Netscaler on a RDP client profile.
So I created 2 RDP client profiles, set up 2 Netscaler Gateway Session profiles and policies each linked to one of the RDP client profiles.
Then I’ve set up 2 AAA Groups and linked the corresponding Session policies and RDP bookmarks to it.
When a user is member of both groups, they see both bookmarks but all .rdp files downloaded have the same monitor setting. (So only 1 session applies for all bookmarks).
Put the user in only one of both AAA groups and the single bookmark shown has correct .rdp config.
Is there a way to prevent the session policy conflict? Or is this approach totally wrong?
I’m using a custom Greenbubbles theme with a UG virtual server. My users log in with CVPN, then under websites, they’ll have an RDP bookmark that is automatically populated based off an LDAP attribute. That works fine, but how can I change the icon of that automatically generated RDP bookmark so users will actually know it’s a RDP bookmark as opposed to a web bookmark? I’m leaning towards trying to figure it out with CSS or JavaScript, I was just hoping there’s an easier way.
I know that this is an old post but there is a way to do this in 13.0.
https://docs.citrix.com/en-us/citrix-gateway/current-release/rdp-proxy/populate-rdp-url-based-on-ldap-attribute.html
Did you try the “RDP connection redirection” in netscaler version 12.1?
Everything works for me unless when I trying to connect a WIN2012 SERVER with Connection Broker enabled.
“Your computer can’t connect to the remote computer because the Connection Broker couldn’t validate the settings specified in your RDP file.”
Hi, have you ever been able to solve this issue?
Have you tested out using the new RDP Redirection setting in the RDP Server Profile to add support for an RDS farm with a Connection Broker that ‘redirects’ the user to a different RDS Server? I haven’t managed to get it working with a 2016 RDS Farm.
Not yet. But several others have not been successful.
I’m testing RDP Proxy in NetScaler as a replacement for a PulseSecure (Juniper) SSL-VPN. With the SSL-VPN, we could automatically create a link, similar to the RDP Proxy in NetScaler, for user’s PC and populate the info based on an AD attribute. So for example, we have an AD attribute for a user’s workstation, then the existing solution would dynamically create an RDP link (proxy) to that workstation. This assisted users because they wouldn’t have to remember their PC name when then wanted to RDP to it.
Is there someway to dynamically create RDP bookmarks for users in NetScaler based on an AD attribute on their user account? That way 1) Users don’t have to create the RDP bookmark themselves and 2) It makes a transition off of the old SSL-VPN to NetScalers close to the same user experience.
I think 12.1 can do this – https://docs.citrix.com/en-us/netscaler-gateway/12-1/rdp-redirection.html#populate-rdp-urls-based-on-ldap-attribute
Thanks! I’ll give it a shot. Appreciate the response.
Hi Carl, is it possible to use the RDP Proxy as an alternative for WAP passthrough or direct RD Gateway access? So the users will see the RemoteApp’s created in their collection from RDS in het web page of Netscaler? I read your article and you didn’t mention anything about RDS RemoteApp’s. Best regard, Peter
Hi,
you can use RemoteApp special parameters in the bookmark. this allow you to publish multiple RemoteApp + RDP desktop to your users.
here’s an example :
add vpn url RemoteApp RemoteApp “rdp://10.10.10.10?alternate shell:s:||ServiceCenter&remoteapplicationprogram:s:||ServiceCenter&remoteapplicationname:s:ServiceCenter&remoteapplicationcmdline:s:&remoteapplicationmode:i:1” -clientlessAccess ON
All you have to do, is to open the RDP RemoteApp file within a notepad and then extract those parameters and use & to append them after the ? in the bookmark
I used those 5 parameters to make it works. Nothing to change in the RDP ClientProfile. I had RDP Redirection = Enabled in the RDP ServerProfile on NS 12.1
HTH
Hi,
I tested this as you instructed but could not get it working.
Do you have more detailed instructions somewhere posted?
Hi, have you setup and make the regular RDP proxy working before you tried RemoteApp ? this help you https://www.carlstalhood.com/netscaler-gateway-12-rdp-proxy/#configuration
also, if you are pointing to a MS broker, you have to use NS 12.1 with the Connection redirection feature enable https://docs.citrix.com/en-us/netscaler-gateway/12-1/rdp-proxy/rdp-redirection.html
if you could provide more details about the error you are facing, it might help to troubleshoot this
Hi, Yes i have setup the RDP proxy and it is working. Broker is not enabled on the target machine.
I tried to add those custom parameters but it just opened the regular remote desktop connection without the remoteapp window. Maybe the parameters were incorrect or something wrong with the connection string but i did not get it working.
Hi,
this is a bit late but if you have spaces in parameters like screen mode you have to use %20 instead of space.
Like rdp://rdp.test.net?screen%20mode%20id:i:1&displayconnectionbar:i:1&disable%20full%20window%20drag:i:1&desktopwidth:i:1920&desktopheight:i:1080
Regards
Burt
Yan
have you tried this with Chrome or Mozilla? You can start RemoteApp apps this way if you use Internet Explorer, but connecting via Chrome or Mozilla with the same account, and these are ignored and a full desktop starts up. Examining the .rdp file that gets downloaded using IE and Chrome, these extra setings are not inserted into the the .rdp file if using Chrome/Mozilla.
regards
Ken Z
Yan, update to my previous post… looks like a bug in 12.1 Build 51.19. Updated to 13.0 Build 36.27 and Chrome/Firefox now starts the rdp file as a seamless app.
Regards
Ken Z
Hi Carl – based on the article we have been able to configure a working RDP Proxy solution. We have configured the RDP Client profile with options such as redirect clipboard disabled (to prevent users from copying data out of the session / Data leakage requirements). We have found that if you download the rdp session file from the Netscaler page, there is a small window (approx 60 – 120 sec) where you can manipulate the downloaded rdp session file and revert the redirectclipboard:i:0 parameter to 1, thus re-enabling clipboard copy. There appears to be some time element involved as post 2 minutes, launching the ‘hacked’ session file again fails to connect (as does renaming the file and the like). Is there any way to prevent user manipulation of the Netscaler’s session file. Thanks
I would equally like to understand if there is a way to prevent this, something on the Citrix Gateway side which detects the difference in the connection parameters compared to the RDP Profile and denies it. Right now this is a huge security problem for us.
Matt
What happens if you disable the Clipboard in the Session Collection Properties?
Regards
Ken Z
Hi Carl. Excellent tutorial as always. Is there a way to set color quality to “High – 16 bit color” and turn off Themes, Wallpaper, Windows Drag, Menu Animation and High Quality Fonts to improve connection performance? One can customize the RDP config file when publishing the RD client as a Citrix app. Can something similar be done with the RDP Proxy? Thank you, sir.
If these are RDP file parameters, then you should be able to use “Custom Parameters” field in the RDP Client Profile.
Hi Carl
I have this setup and intermittently working. I find I’m having to click the RDP bookmarks multiple times, in order to establish a connection with the backend servers. Most of the time I get the message “This computer can’t connect to the remote computer”. If I click the bookmark again, I can connect no issue. Also intermittently but only on Server 2008 R2 backed servers, the session just disconnects for no apparent reason. Have you come across any issues like these?
I am seeing this exact same error message. The only difference is that no matter how many times we try, we can’t launch the desktop. There is an event on the server (2016), ID 1306, it says: Remote Desktop Connection Broker Client failed to redirect the user xxx\domain. Any ideas appreciated.
Did you find any solution for this issue?Even i am facing the same issue in my environment.
Do you need to deploy StoreFront + XenServers to get this RDP gateway ?
No. But you do need NetScaler Enterprise Edition.
Hello, Carl!
Thank you for a nice write-up! Have anybody had issues with the RDP session getting disconnected multiple times in a relatively short time?
I’ve tried to look for session timeout values, but there are none that impact my issue. Any clues are greatly appreciated.
Hi Carl,
First, thanks for the awesome documentation! Now, I used your documentation before and got RDP Proxy working, I found it to be really easy to do. However, I recently upgraded (actually it’s been several months) the NetScaler to version 12.0.53.13.nc and setup RDP proxy once again.
Everything went well like before, but this time I get an error when I connect to any server via RDP through the NetScaler.
The Error is “An authentication error has occurred (Code: 0x80005005)”
Have you seen this before? Seems like the NetScaler is not sending the creds along to the server, not sure what to try or changes to make.
Thanks for any assistance you can provide.
Rob
I’m trying to do RDP Proxy and having a little problem. I follow all of the steps but when I go to bind the RDP session policy to my NetScaler Gateway, I get the following error.
Classic VPN Session Policy cannot be bound if Advanced VPN Session Policy is already bound to any entity (i.e. aaa user, aaa group, vpn vserver, vpn global)
I have been trying to do research online but can’t find much with this error message. Can you explain what this means?
I’m guessing you have Session Policies already bound to your Gateway vServer and they use Default Syntax instead of Classic Syntax. But the new Session Policy you created for RDP is in Classic Syntax (ns_true instead of true). You can’t mix the two types.
I’ve followed these steps, and after logging in (clientless, RfWebUi), I got the actual RDPfile by clicking on the bookmark, that seems pretty much the same as yours.
Similarly, when I use https://unified.domain.com/proxy/server, I also get the RDP file. So I’d say ‘m pretty close to having it going.
allas…
When I try to actually connect to the server, I get an “connecting to: unified.domain.com:443”, and eventually it errors out, not being able to connect.
Slightly clueless what ‘m doing wrong here. I’m running NetScaler 12.0 53.13.
Are you Content Switching to the Gateway vServer?
Authorization Policies allow the connection?
Yeap, there is a content switch in front of the UG; CS refers to it as
HTTP.REQ.HOSTNAME.SERVER.TO_LOWER.CONTAINS(“unified”) || is_vpn_url
Session Profile Security has the default authorization action “Allow”
The SNIP is also in the same VLAN as the server to be connected to, so no firewall in between NetScaler and RDP Host
Maybe try it without content switching?
Tried to do it this time on a clean netscaler VPX, without any further configurations. First ran the normal UG wizard to create the entire set of the normal config, then executed the steps above.
Then tried – as suggested – to remove the content switch, the CS Policy and Action and recreate the vpn server with a fixed address. Still no show.
I am able to access everything else that I bookmark.
Hi Carl, thanks for the very informative guide. I’ve followed the guide and got this working up successfully, just had a question:
In my setup, when the user clicks the downloaded .rdp it prompts for username and password. The user then has to enter domain\username, then their password.
What I wanted to know was, is there a way to insert the domain name into the .rdp files, so the user just types their username and password when prompter.
Or better yet is there a way to set it that when they click on the .rdp file, it automatically logs them in using the credentials they used to log into the netscaler initially?
Thanks
Ben
Managed to figure it out, I didn’t select the option “Single Sign-on to Web Applications”, in the RDP profile, under
the Client Experience tab. Enabling this and now when clicking on the RDP file, the desktop opens without prompting for username and password. Might be useful for anyone else using RDP proxy.
Thanks for the advice. Got this request during testing.
HI Carl, from the article i gather that if i change the url rdpproxy/myserver a smart user can connect basically to every rdp server (assuming the traffic between netscaler and rpd server is enabled). Is there a way to constrain users to connect to only one or some predefined RDP Server without using the netscaler ACL function ? Regards Christian
Set Default Authorization to DENY. Then create Authorization Policies. You can create them an bind them to AAA Groups. Or the new PI for Authorization Policies might allow HTTP.REQ.USER.IS_MEMBER_OF() expressions.