This article applies to NetScaler Gateway 14.1, Citrix Gateway 13.x, Citrix Gateway 12.1, and NetScaler Gateway 12.0.
Navigation
💡 = Recently Updated
Change Log
- 2024 Aug 3 – Delivery Group Access Policy page redesigned in CVAD 2407
- 2023 Aug 15 – added link to CTX572334 Eliminate Advanced Endpoint Analysis scans on Mobile devices/iOS
- 2020 Sep 8 – nFactor EPA – added info from CTX278960 AAA GROUP expressions in Gateway Vserver (CVPN, Full VPN and ICA Proxy) use-cases
- 2020 Jun 28 – added nFactor EPA section describing how to do SmartAccess using nFactor EPA.
- 2020 Apr 20 – renamed NetScaler Gateway to Citrix Gateway
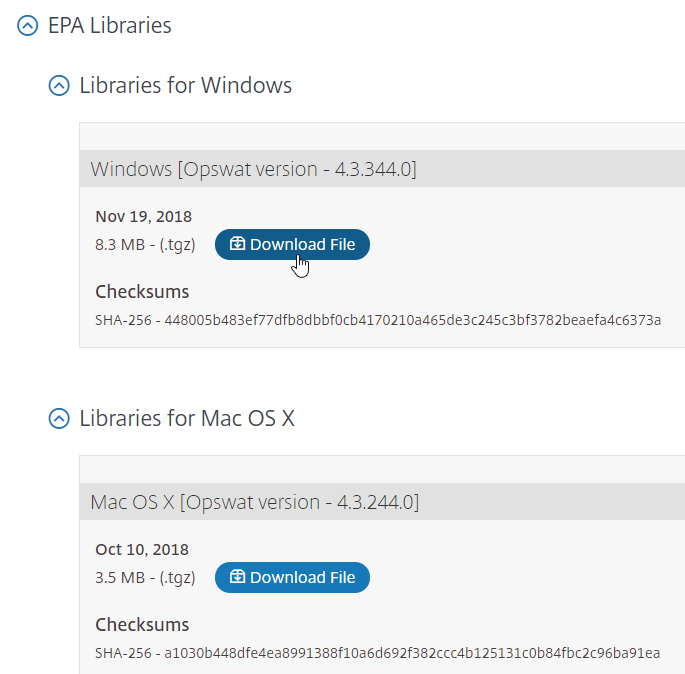
- 2018 Nov 24 – EPA Libraries – updated for Windows version 4.3.344.0
- 2018 Oct 10 – EPA Libraries – updated for Mac version 4.3.244.0
- 2018 Sep 28 – EPA Libraries – updated for versions 4.3.204.0 and 4.3.57.0
- 2018 June 4 – new EPA Libraries section to upgrade EPA libraries
SmartAccess / SmartControl
SmartAccess and SmartControl let you change ICA connection behavior (e.g. disable client device mappings, hide icons) based on how users connect to Citrix Gateway. Decisions are based on Citrix Gateway Virtual Server name, Session Policy name, and Endpoint Analysis scan success or failure.
SmartAccess vs SmartControl:
- SmartAccess lets you control visibility of published icons, while SmartControl does not.
- SmartControl is configured exclusively on Citrix Gateway, while SmartAccess requires configuration on both Citrix Gateway, and inside Citrix Studio.
- SmartControl requires Citrix ADC Premium Edition licensing, while SmartAccess is available in all Citrix ADC Editions.
- Both features require Citrix Gateway Universal licenses for every concurrent connection.
Prerequisites
Both SmartAccess and SmartControl have the same prerequisites. You can configure SmartAccess in Citrix Virtual Apps and Desktops (CVAD) at any time, but it won’t work, until you do the following:
- Citrix ADC appliance license: See Feature Licensing in the Gateway Tweaks post. In summary:
- SmartAccess is available in all editions of Citrix ADC appliances.
- SmartControl is available only in Citrix ADC Premium Edition.
- Citrix Gateway Universal Licenses – On the Citrix ADC, go to System > Licenses, and make sure you have Citrix Gateway Universal Licenses allocated to the appliance.
- Most Citrix ADC Editions (except Citrix Gateway Enterprise VPX) come with built-in Gateway Universal licenses: Citrix ADC Standard Edition = 500 licenses, Citrix ADC Advanced Edition = 1,000 licenses, and Citrix ADC Premium Edition = unlimited licenses.
- Additional Citrix Gateway Universal licenses can be acquired through other means. See Feature Licensing in the Gateway Tweaks post for details.
- The Universal licenses are allocated to the hostname of the appliance (click the gear icon to change it), not the MAC address. In a High Availability pair, if each node has a different hostname, then you can allocate the licenses to one hostname, then reallocate to the other hostname. See Feature Licensing in the Gateway Tweaks post for details.
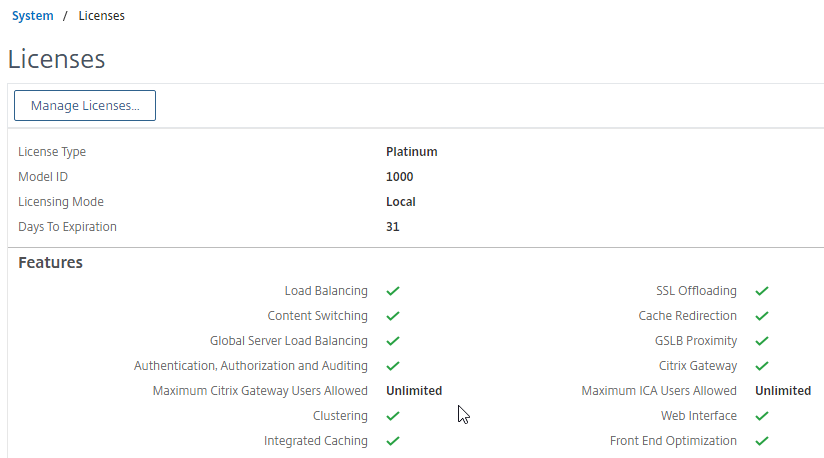
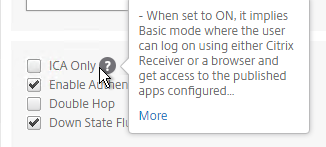
- Citrix Gateway must have ICA Only unchecked.
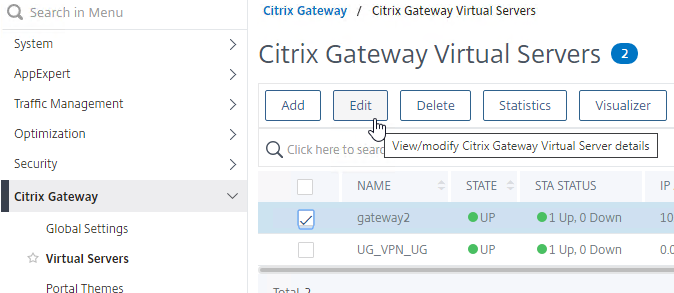
- On the Citrix ADC, go to Citrix Gateway > Virtual Servers, and edit your Gateway Virtual Server.
- In the Basic Settings section, click the pencil icon.
- Click More.
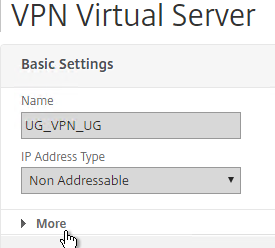
- Uncheck the box next to ICA Only, and click OK. This tells Citrix Gateway to start using Universal licenses and enables the SmartAccess and SmartControl features.
- On the Citrix ADC, go to Citrix Gateway > Virtual Servers, and edit your Gateway Virtual Server.
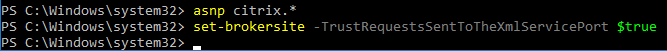
- Enable Trust XML on the Citrix Virtual Apps and Desktops (CVAD) Site/Farm:
- On a CVAD Controller, run PowerShell as Administrator.
- Run asnp citrix.* to load the snapins.
- Run Set-BrokerSite -TrustRequestsSentToTheXmlServicePort $true to enable Trust XML.
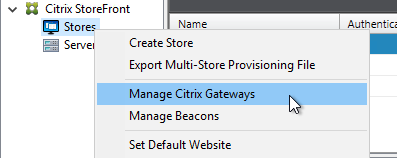
- Configure Callback URL in StoreFront:
- In StoreFront Console, right-click the Stores node, and click Manage Citrix Gateways.
- Edit a Gateway.
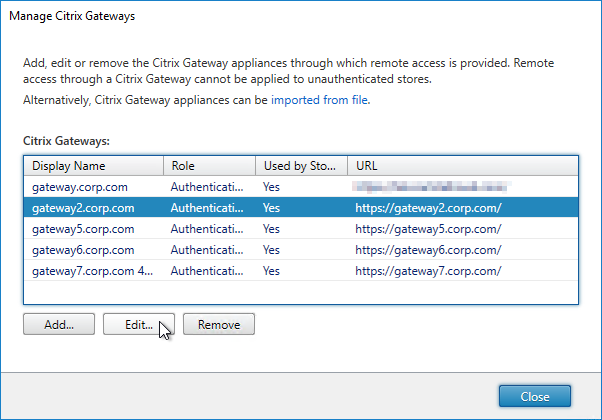
- On the Authentication Settings page, make sure a Callback URL is configured. The Callback URL must resolve to a Citrix Gateway VIP on the same appliance that authenticated the user. The Callback Gateway’s certificate must match the FQDN entered here. If you are configuring Single FQDN for internal and external, then the Callback FQDN must be different than the Single FQDN.
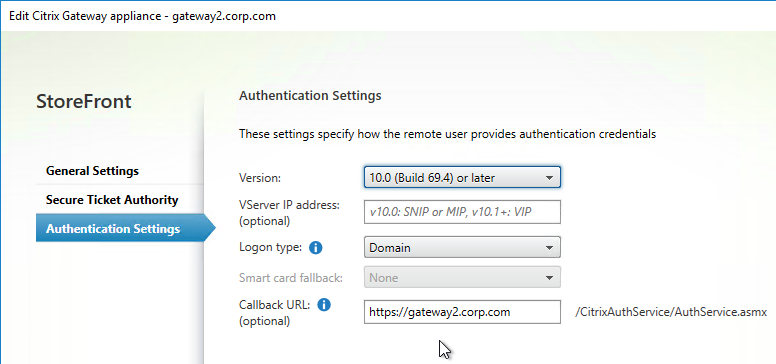
- In StoreFront Console, right-click the Stores node, and click Manage Citrix Gateways.
Once the prerequisites are in place, do the following as detailed below:
- Optionally, configure Endpoint Analysis.
- Configure either SmartControl or SmartAccess.
Endpoint Analysis
Endpoint Analysis (EPA) scans are completely optional. You can configure SmartControl and SmartAccess without implementing any Endpoint Analysis.
Endpoint Analysis is supported on Windows and Mac devices. Other devices, like iOS and Android, do not support Endpoint Analysis. If you want to allow mobile device connectivity, then make sure you have an access mechanism (e.g. ICA Proxy) that works if the Endpoint Analysis scan fails.
Citrix ADC 12.1 and newer support two methods of doing EPA: nFactor EPA, or Classic EPA. Classic EPA will no longer be supported in ADC 13.1 and newer so you should eventually switch to nFactor EPA.
Workspace app on Windows supports EPA when configured using nFactor EPA. Workspace app does not support Classic EPA.
nFactor EPA
EPA can be one of the factors of an nFactor flow. EPA can be performed before authentication, or after authentication.
EPA doesn’t work on iOS/Android. To skip those platforms, see CTX572334 Eliminate Advanced Endpoint Analysis scans on Mobile devices/iOS.
- Create an nFactor EPA Action.
- The easiest way to find EPA is to use the Search box on the top of the left menu. Or, navigate to Security > AAA > Policies > Authentication > Advanced Policies > EPA.
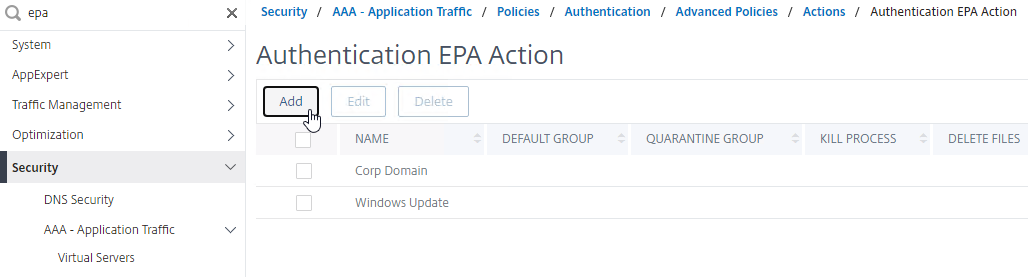
- The EPA Editor link on the right-side of the Expression box lets you configure EPA Expressions. See OPSWAT EPA Expressions below for more details on how to configure an Opswat expression.
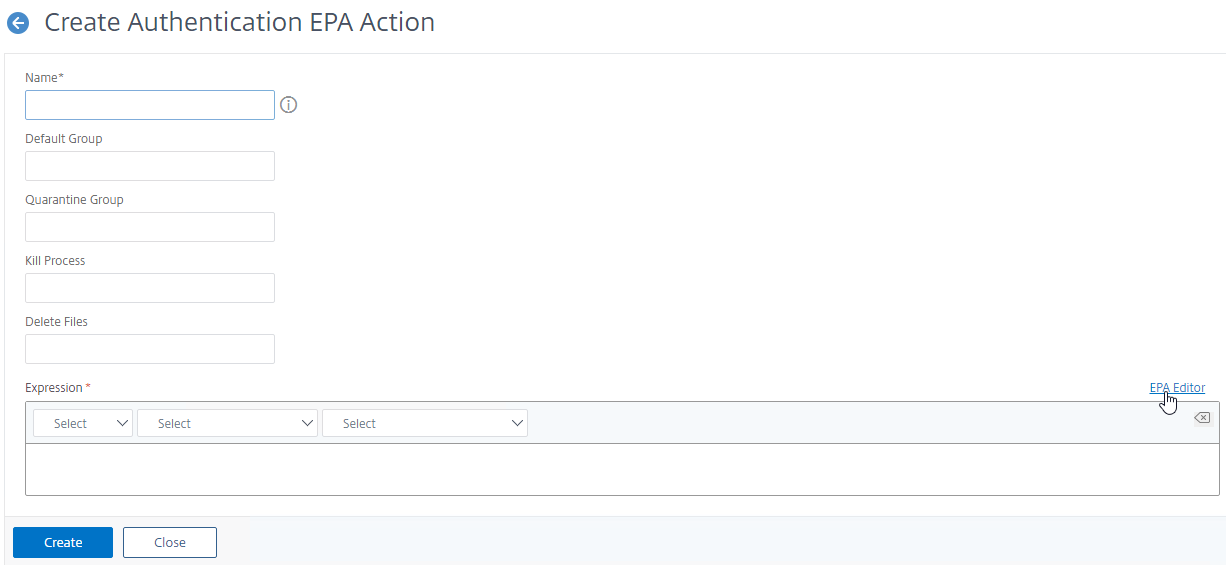
- For SmartAccess based on the results of the EPA scan, configure the Default Group field with a new group name (doesn’t exist in Active Directory). You’ll later use the Group name in a Session Policy and use the Session Policy name in your Citrix Policy Access Filters or Delivery Group Access Control. Default Group probably only works if the EPA Factor is performed after authentication.
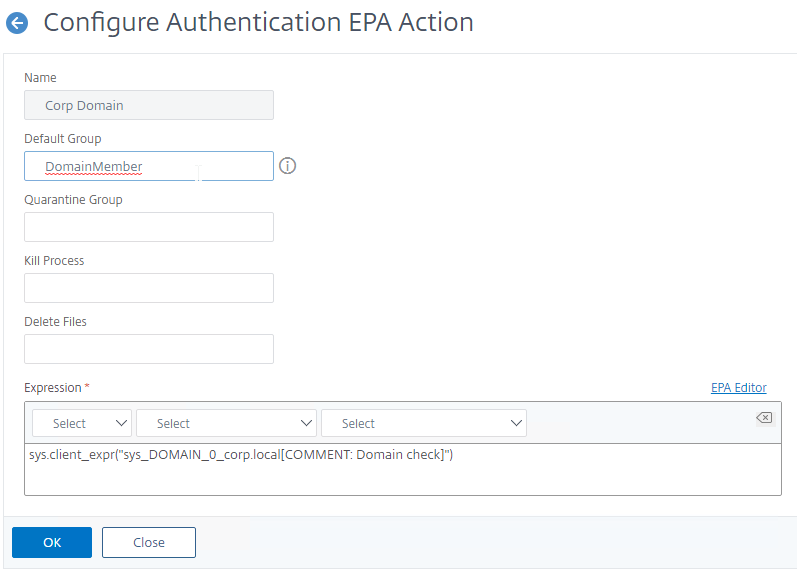
- The easiest way to find EPA is to use the Search box on the top of the left menu. Or, navigate to Security > AAA > Policies > Authentication > Advanced Policies > EPA.
- After creating an EPA Action, create an Advanced Authentication Policy of type EPA and select the EPA Action you created earlier.
- The expression is either true, or an expression that defines who needs EPA scanning. If you are configuring post-authentication EPA, then you can use group membership (e.g. AAA.User.Is_Member_Of()) expressions.
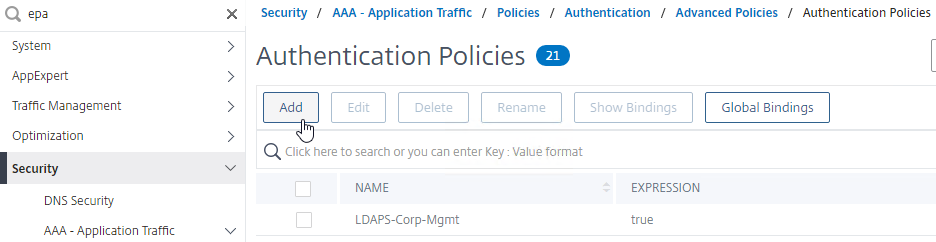
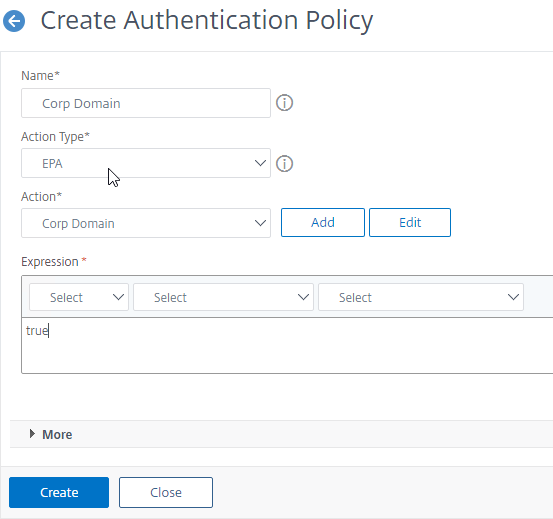
- The expression is either true, or an expression that defines who needs EPA scanning. If you are configuring post-authentication EPA, then you can use group membership (e.g. AAA.User.Is_Member_Of()) expressions.
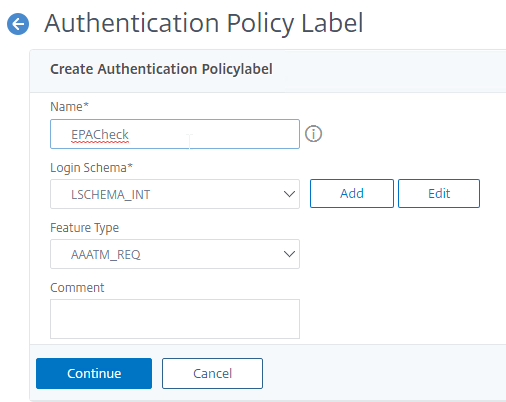
- Create a Policy Label for the EPA Factor. Login Schema should be LSCHEMA_INT.
- Bind the EPA Policy to your Policy Label.
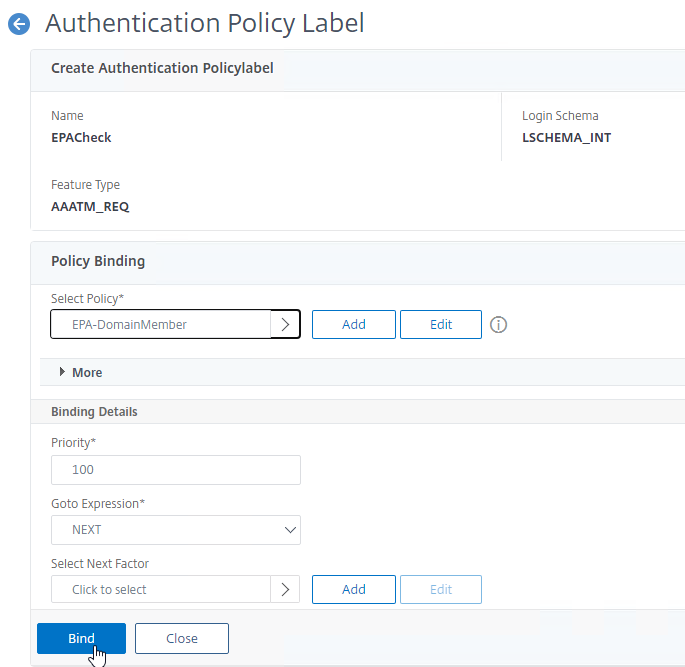
- If you don’t bind any other policies, then if EPA fails, then the user shown the Access Denied page. If you want authentication to continue even with a failed EPA scan, then bind another policy to the Policy Label.
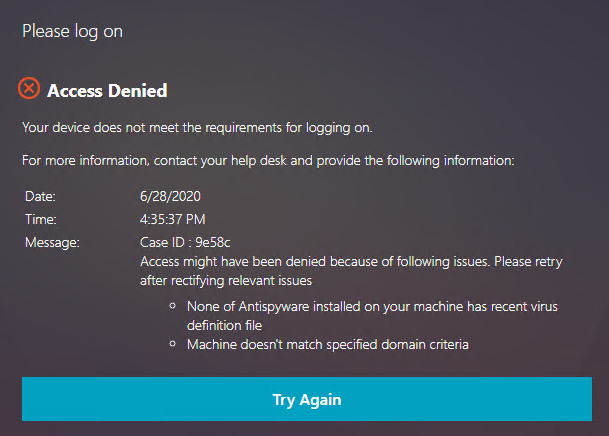
- Create an Advanced Authentication Policy named similar to NoAuth and change Action Type to NO_AUTHN. Expression = true. Bind the NoAuth policy to the Policy Label.
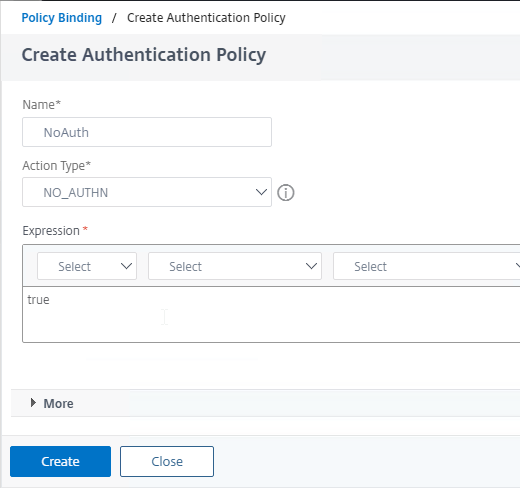
- The final Policy Label should have an EPA Factor with Goto = NEXT and the second policy as NoAuth.
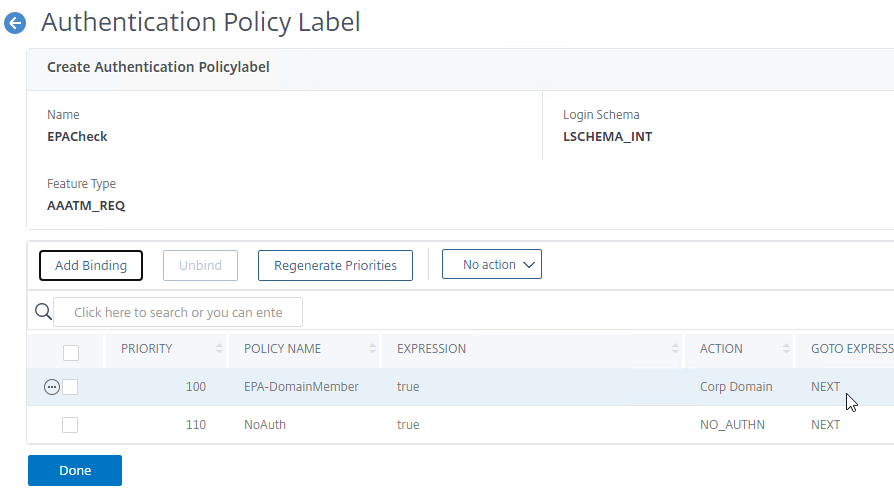
- Bind the EPA Policy to your Policy Label.
- In earlier factors that authenticate the user, when binding an authentication policy, click in the Select Next Factor field and select your EPA Policy Label.
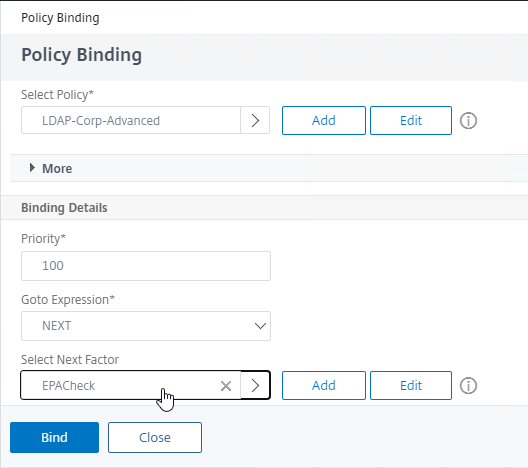
- In the earlier authentication factor, edit the Login Schema Profile, click More, and check the box next to Enable Single Sign On Credentials. EPA as later factor overrides the password collected in earlier factors causing Single Sign-on to StoreFront to fail and this checkbox fixes that problem.
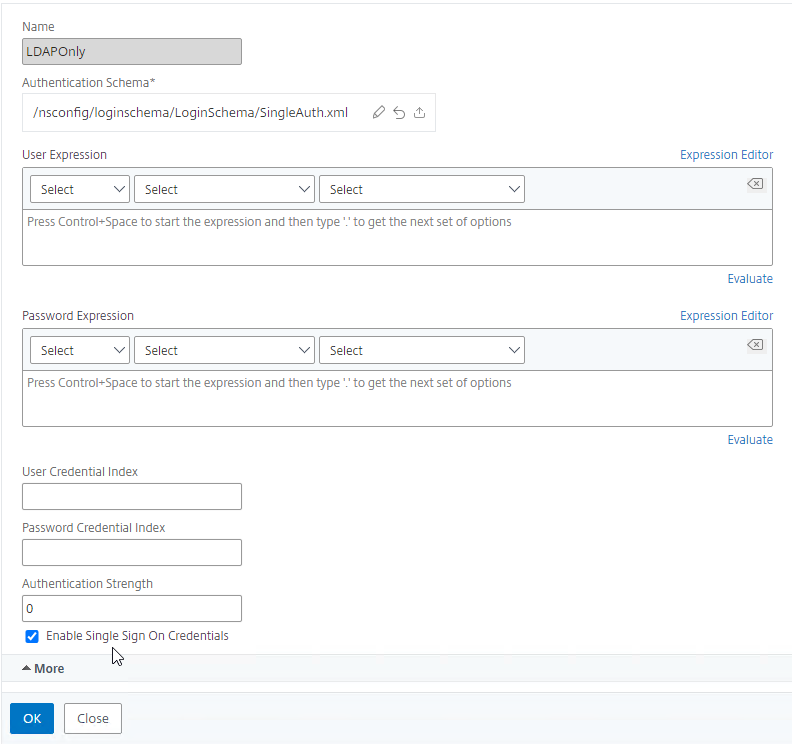
- In the earlier authentication factor, edit the Login Schema Profile, click More, and check the box next to Enable Single Sign On Credentials. EPA as later factor overrides the password collected in earlier factors causing Single Sign-on to StoreFront to fail and this checkbox fixes that problem.
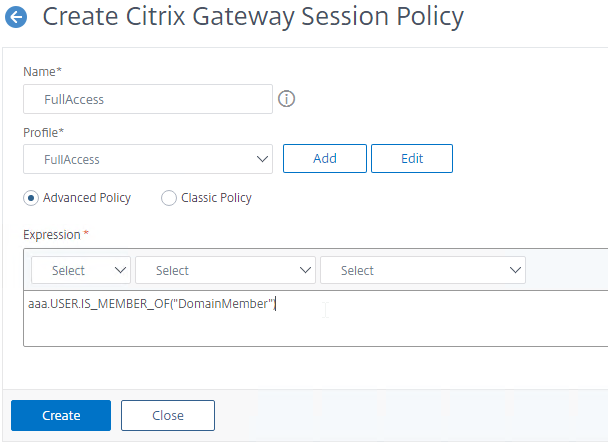
- Create a Citrix Gateway Session Policy that is applied when the EPA factor succeeds.
- Go to Citrix Gateway > Policies > Session.
- On the tab named Session Profiles, click Add.
- Name it FullAccess or similar and click Create. The Session Profile does not need any settings.
- Switch to the tab named Session Policies and click Add.
- Select the Profile you just created.
- If you are doing Advanced Policies, then the Expression is AAA.USER.IS_MEMBER_OF(“GroupName”) where “GroupName” is the name of the Default Group you specified when you created the EPA Action. Click Create. If you are doing Classic Policies, then the expression is ns_true.
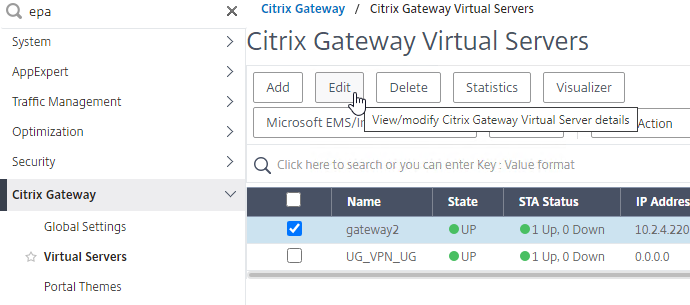
- If your session policy is Advanced syntax, then bind the Session Policy to your Gateway vServer.
- Go to Citrix Gateway > Virtual Servers and edit an existing vServer.
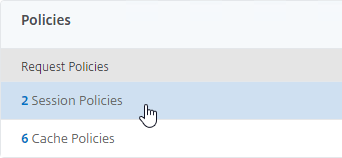
- Scroll all the way down to the Policies section and click the Session Policies line.
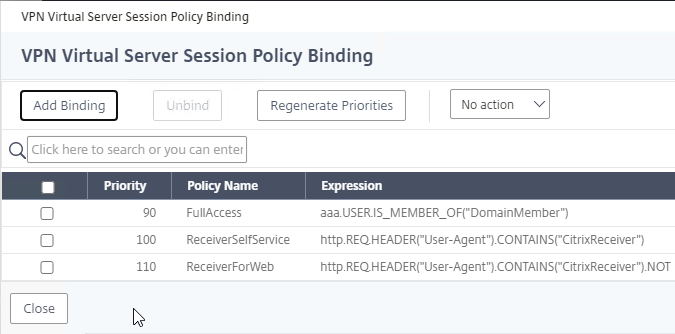
- Add Binding and select the Session Policy you will use for SmartAccess. Priority doesn’t matter.
- Go to Citrix Gateway > Virtual Servers and edit an existing vServer.
- For both Advanced Session Policies and Classic Session Policies, create a AAA Group that matches the Default Group you specified in the EPA Action. CTX278960 says this is also required for IS_MEMBER_OF expressions.
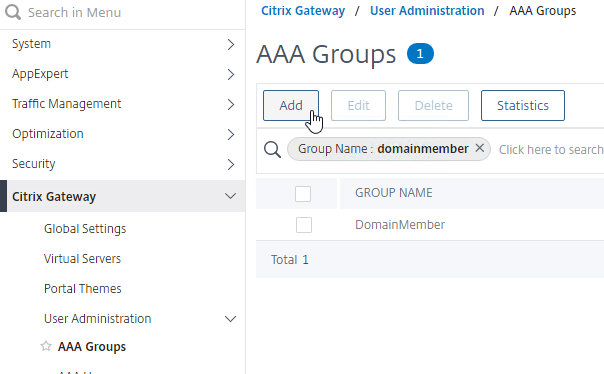
- If you are doing Classic Session Policies, then create bind the Session Policy to the AAA Group. If you are doing Advanced Session Policies bound directly to the Gateway Virtual Server, then you don’t need to bind anything to the AAA Group.
- You can now use the Session Policy in your SmartAccess configuration. See the SmartAccess section below for more details.
Classic EPA Policies
There are two methods of Classic Endpoint Analysis: pre-authentication and post-authentication. For pre-authentication, configure an Endpoint Analysis expression in a Preauthentication Policy. For post-authentication, configure the Endpoint Analysis expression on one or more Session Policies.
- With a Preauthentication Policy, if the Endpoint Analysis scan fails, then users can’t login.
- With a Postauthentication Policy, Endpoint Analysis doesn’t run until after the user logs in. Typically, you create multiple Session Policies. One or more Session Policies have Endpoint Analysis expressions. Leave one policy without an Endpoint Analysis expression so there’s a fallback in case the client device doesn’t support Endpoint Analysis (e.g. mobile devices). The name of the Session Policy is then used later in Citrix Policies and Citrix Delivery Groups.
- Inside the Session Profile is a field for Client Security expression, which supports an EPA expression. This field is for VPN only, and does not affect SmartAccess.
Preauthentication Policies and Profiles are configured at Citrix Gateway > Policies > Preauthentication.
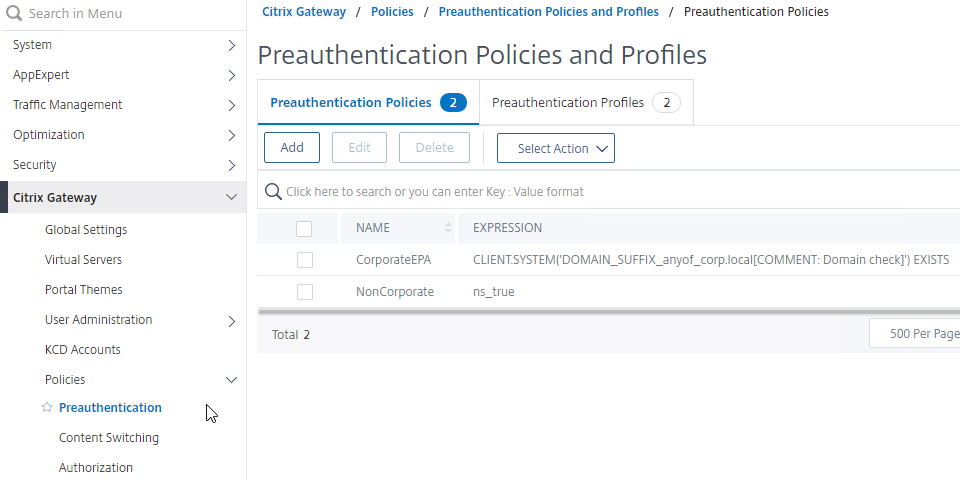
- On the right, switch to the Preauthentication Profiles tab, and create a Preauthentication Profile to allow access.
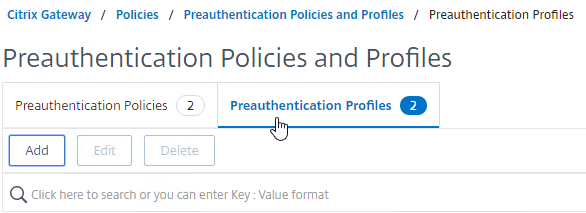
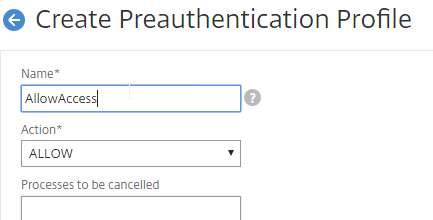
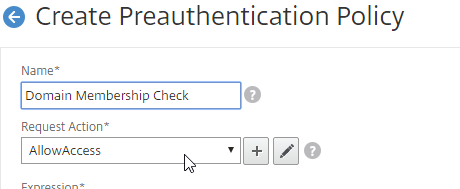
- Switch to the Preauthentication Policies tab, and create a Preauthentication Policy with an EPA expression. Select the Request Action that allows access.
- The right side of the Expression box has links to create EPA expressions, as detailed below.
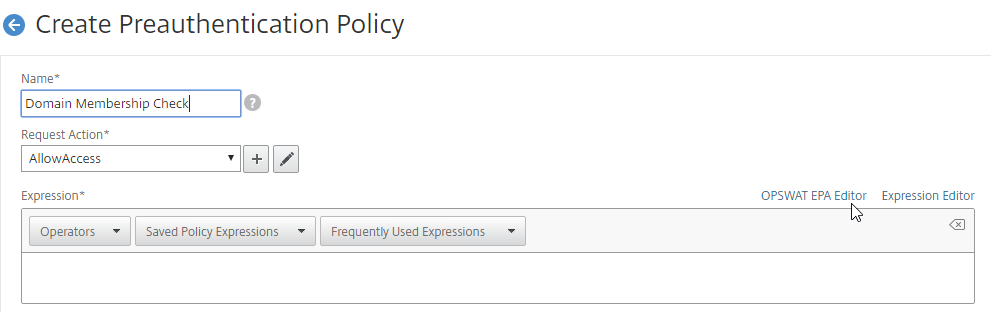
Classic Post-authentication Policies and Profiles are configured at Citrix Gateway > Policies > Session.
- When creating a Session Policy, the right side of the Expression box has links to create EPA expressions, as detailed below.
- Classic Syntax vs Default Syntax – EPA expressions can only be added to Classic Syntax Policies. If you click Switch to Default Syntax, then the OPSWAT EPA Editor disappears. Use nFactor EPA instead.
- If you edit a Session Profile, on the Security tab…
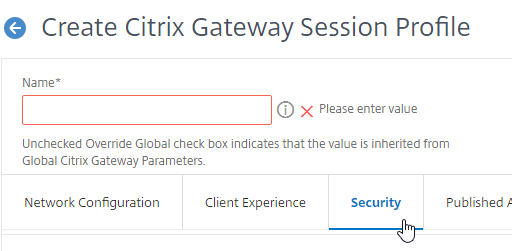
- Under Advanced Settings, you will see a Client Security Check String box that lets you enter an EPA Expression. This field applies only to VPN and does not affect SmartAccess. Also, this field does not function if your Session Policy is Advanced instead of Classic.
EPA Expressions
Citrix ADC has two Endpoint Analysis engines: the original Client Security engine, and the newer OPSWAT EPA engine.
OPSWAT EPA Expressions
To configure OPSWAT EPA expressions:
- When creating an nFactor EPA Action, click the EPA Editor link.
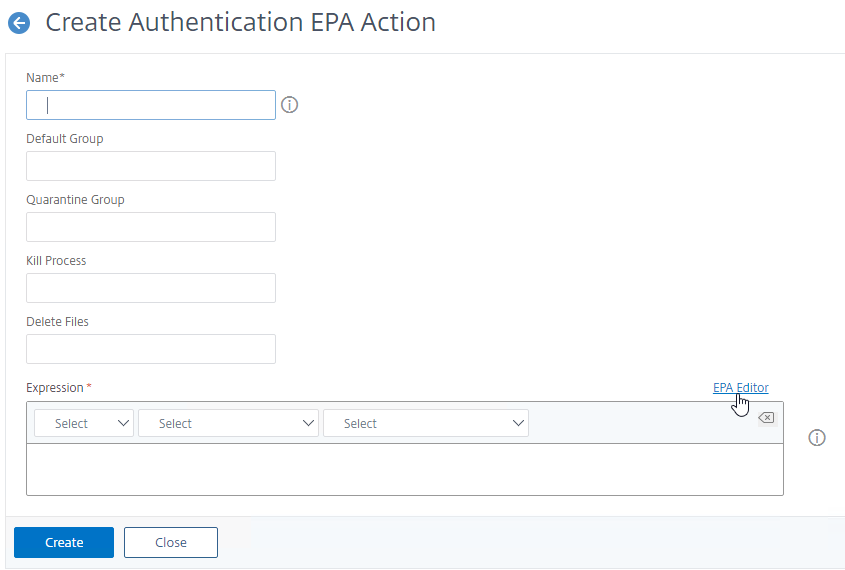
- When creating a Classic Preauthentication Policy, or Session Policy, click the OPSWAT EPA Editor link.
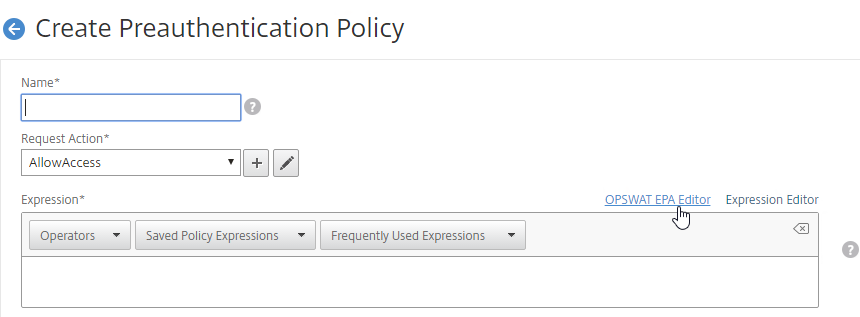
- When creating a Classic Preauthentication Policy, or Session Policy, click the OPSWAT EPA Editor link.
- Use the drop-down menus to select the scan criteria.
- You will see some fields with a plus icon that lets you configure more details for the scan.
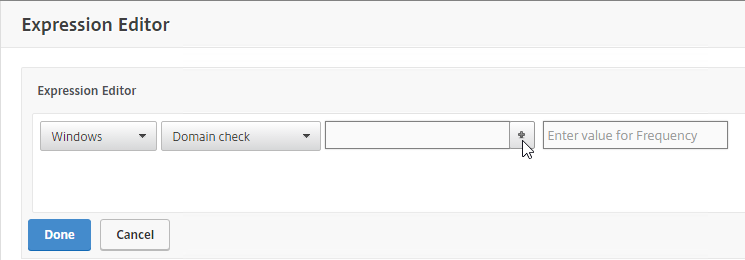
- Note: the text in these policy expressions is case sensitive.
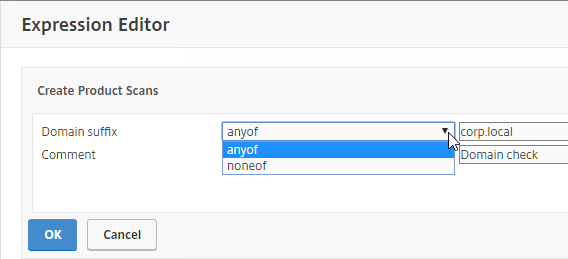
- Note: the text in these policy expressions is case sensitive.
- Then click Done.
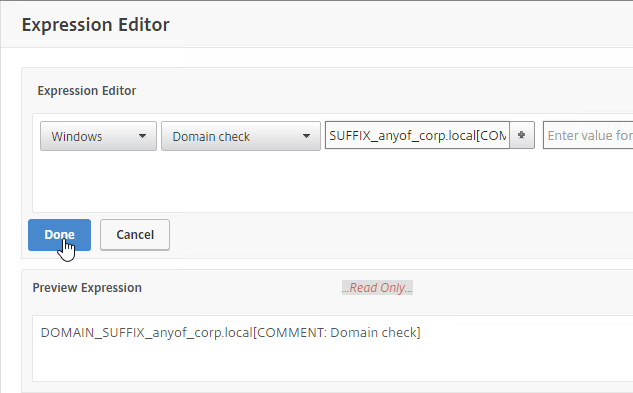
Additional OPSWAT EPA Info
See the following links for more Advanced EPA information:
- Advanced Endpoint Analysis Policy Expression Reference at Citrix Docs
- Advanced Endpoint Analysis Scans at Citrix Docs
- Citrix CTX220961 Pre authentication scan on Netscaler gateway for domain check
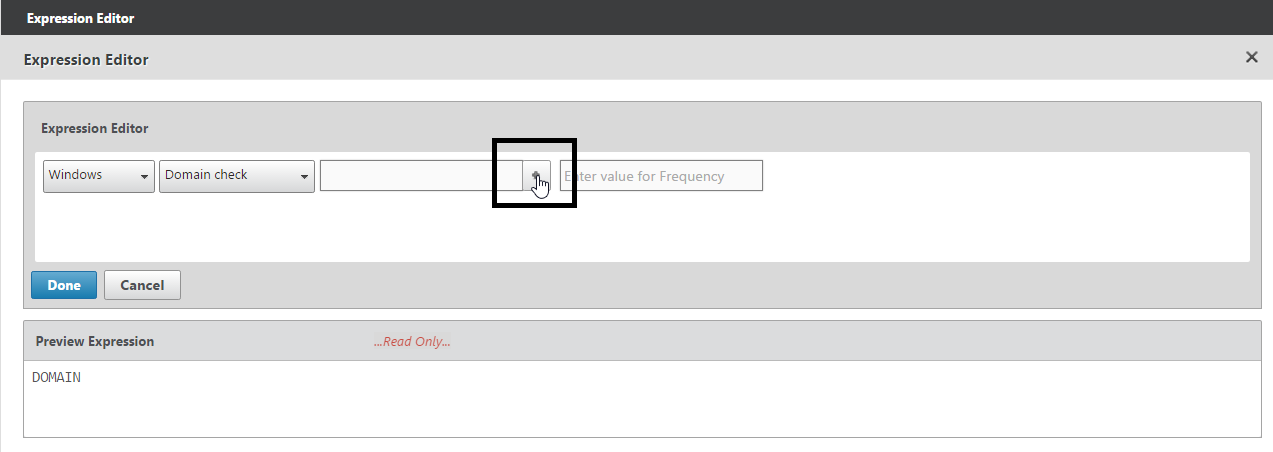
- Citrix CTX204764 Expression for EPA scan through NetScaler Gateway to check a generic antivirus and a generic firewall
CLIENT.APPLICATION('ANTIVIR_0_RTP_==_TRUE[COMMENT: Generic Antivirus Product Scan]') EXISTS && CLIENT.APPLICATION('FIREWALL_0_ENABLED_==_TRUE[COMMENT: Generic Firewall Product Scan]') EXISTS - Citrix Blog Post Patch Management Endpoint Analysis on NetScaler Gateway
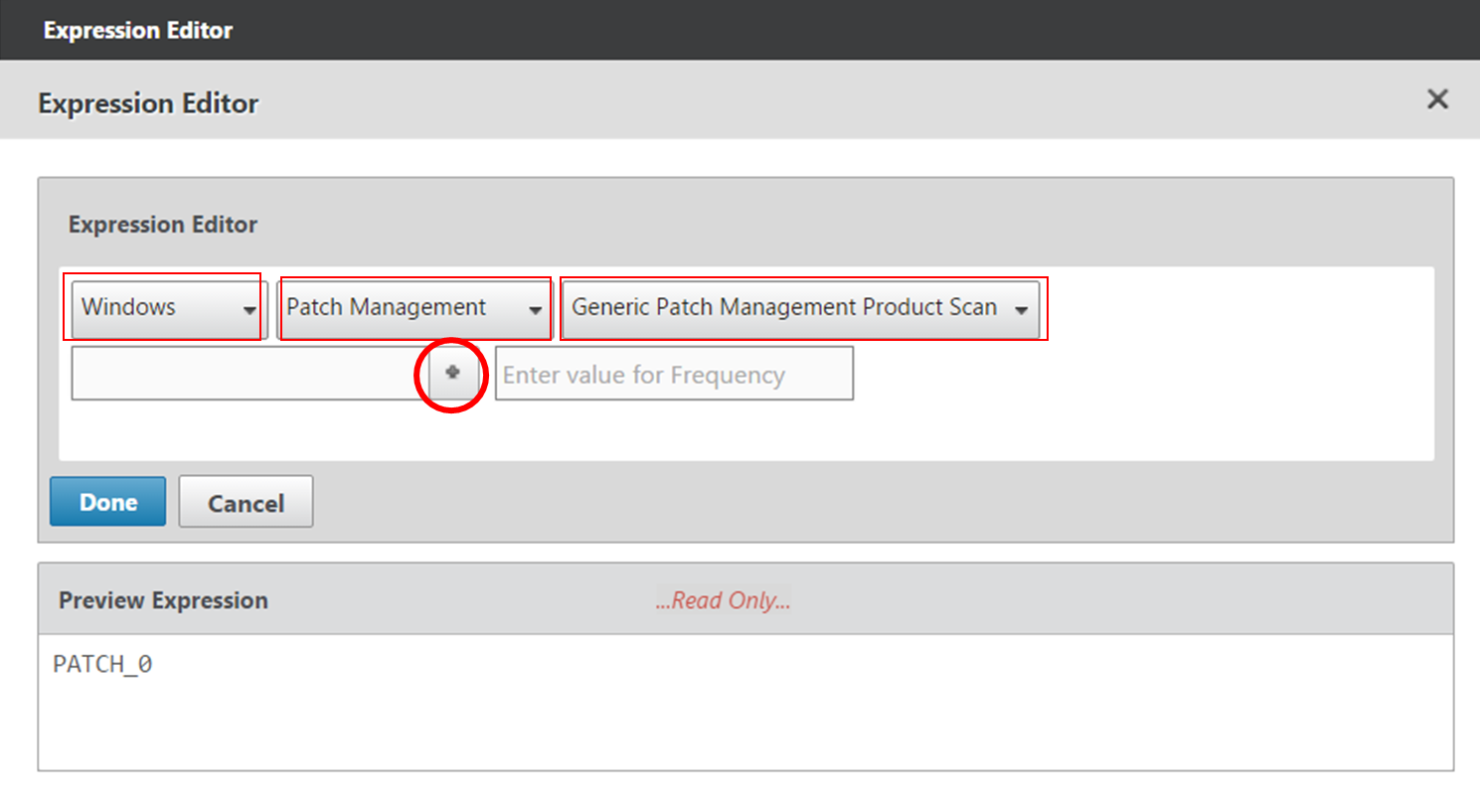
- Citrix CTX207623 Windows and macOS Supported Applications by OPSWAT Version 3 for NetScaler EPA Scans contains a list of applications supported by OPSWAT Windows and MAC EPA Scan
- Citrix CTX219296 How to configure EPA Expression to validate if the “Windows update” date is within specific time period.
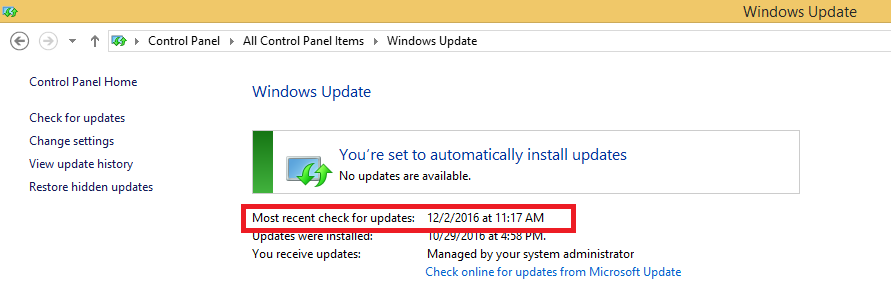
- Note: Automatic Updates must be enabled for this scan to work. See Citrix CTX219293 NetScaler Gateway EPA Scan Fails When Checking for “Windows Update” on Client Machine
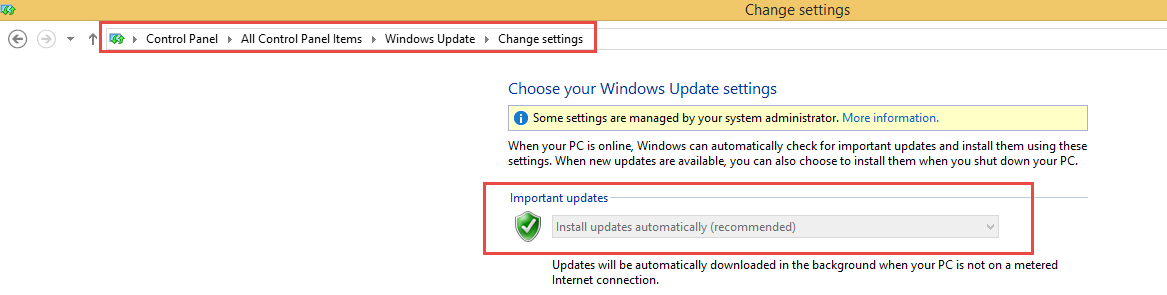
- Note: Automatic Updates must be enabled for this scan to work. See Citrix CTX219293 NetScaler Gateway EPA Scan Fails When Checking for “Windows Update” on Client Machine
- Citrix CTX228922 Configure EPA Scan for Windows Update – Critical or Automatic – shouldn’t have missing patch
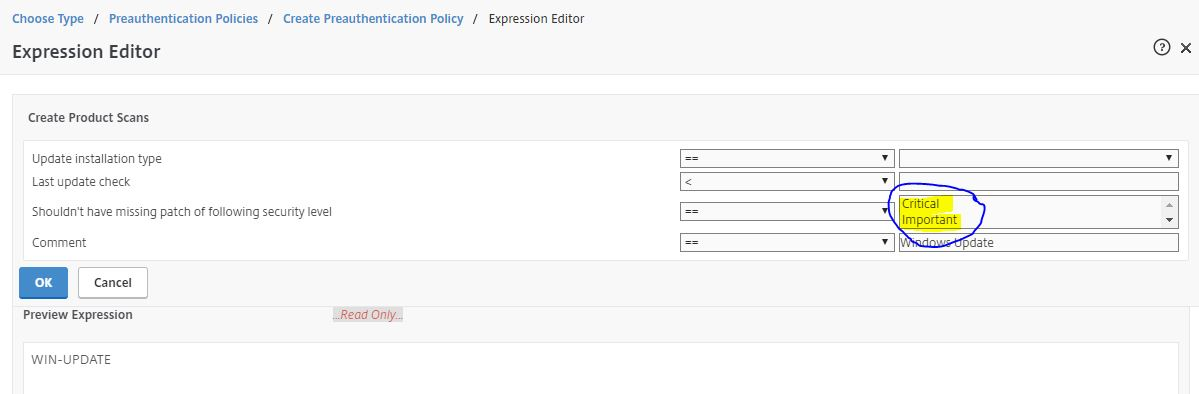
- Citrix CTX205267 How Do I Configure EPA for Registry Check?
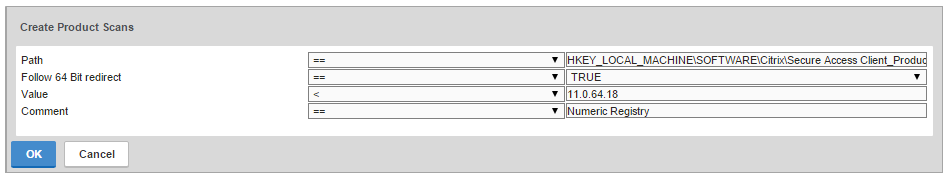
- CTX221121 Create EPA Scans to Detect Receiver on Clients. Clients without Workspace app or Receiver installed are sent to the a page with a link to the Workspace app Download page, and Clients with Workspace app or Receiver are allowed through to their ICA applications
CLIENT.SYSTEM('REG-NON-NUM_HKEY_LOCAL_MACHINE\\SOFTWARE\\Wow6432Node\\Citrix\\Install\\ICA Client\\InstallFolder') EXISTS
Original Client Security Expressions
To configure the original Client Security expressions:
- When creating a Classic Preauthentication Policy or Classic Session Policy, click the Expression Editor link.
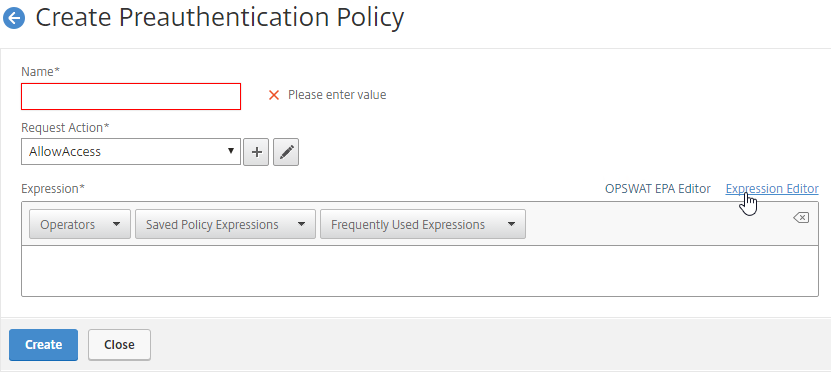
- Change the Expression Type to Client Security.
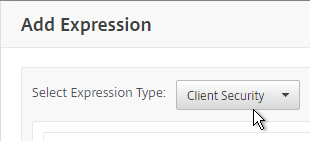
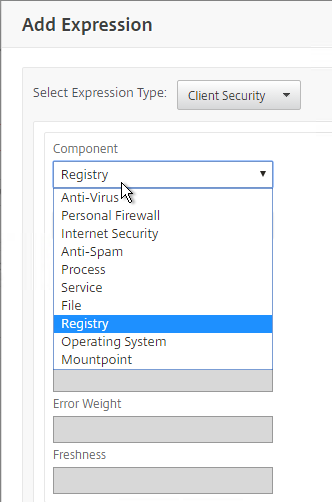
- Use the Component drop-down to select a component.
- A common configuration is to check for domain membership as detailed at Citrix CTX128040 How to Configure a Registry-Based Scan Expression to Look for Domain Membership.
- Citrix CTX128039 How to Configure a Registry-Based EPA Scan Expression on NetScaler to Look for the Active Device or Computer Name of an Explicit Workstation
Once the Classic Preauthentication and/or Classic Session Policies are created, bind them to your Citrix Gateway Virtual Server:
- Edit a Citrix Gateway Virtual Server.
- Scroll down to the Policies section, and click the plus icon.

- Select either Preauthentication or Session, and select the policy you already created. Then click Bind.
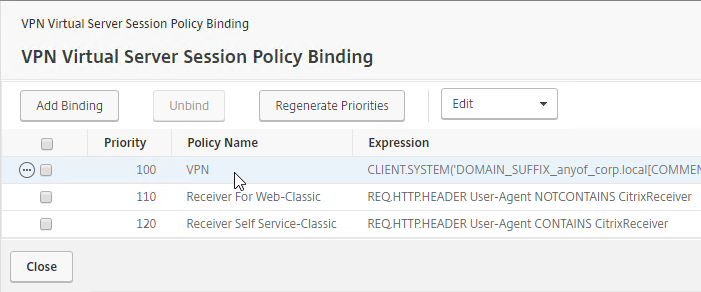
- Session Policies with EPA Expressions are typically higher in the list (lower priority number) than non-EPA Session Policies.
EPA Libraries
In NetScaler 12.0 build 57 and newer, the EPA Libraries are updated out-of-band.
- Download the latest EPA libraries.
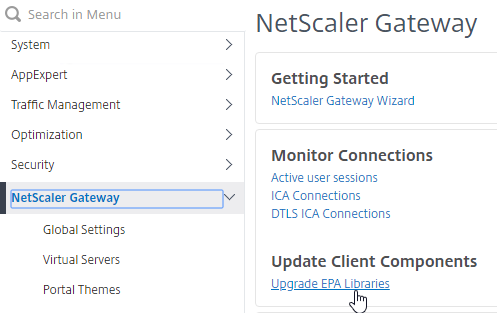
- In the Citrix ADC menu, click the Citrix Gateway node.
- On the right, in the left column, click Upgrade EPA Libraries.
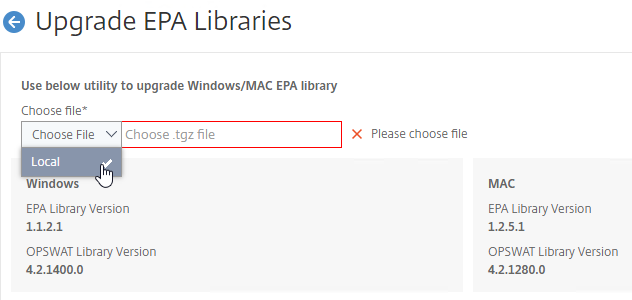
- Click Choose File
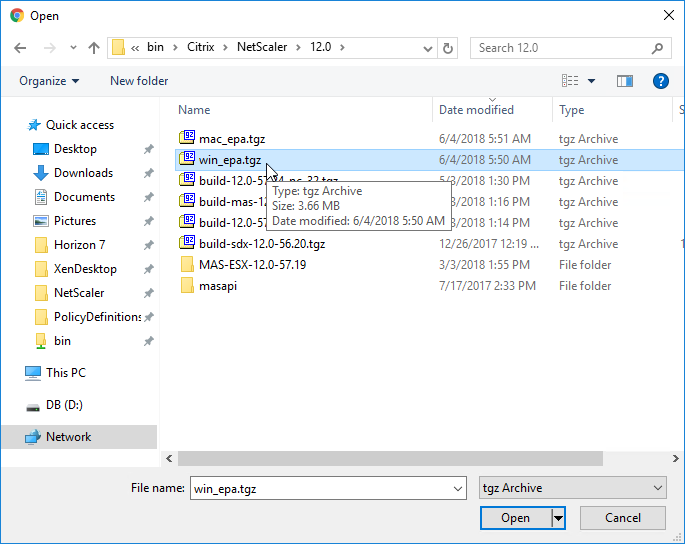
- Browse to one of the .tgz library files, and click Open.
- Click Upgrade.
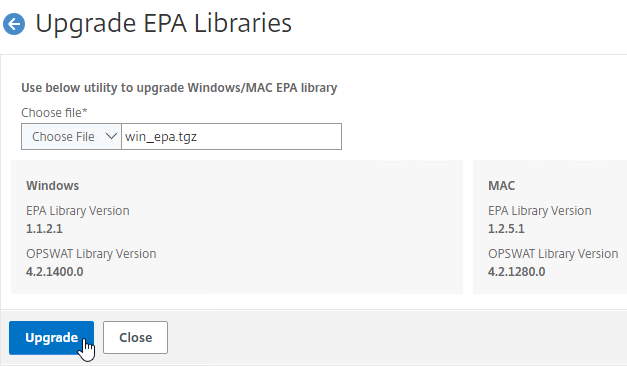
- Click OK when prompted that EPA Library upgraded successfully.
- Click Upgrade EPA Libraries again.

- Click Choose File.
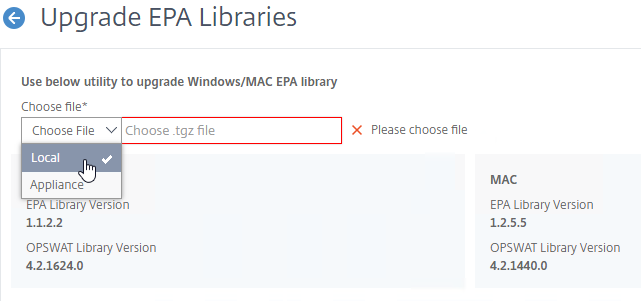
- Browse to the other .tgz EPA library file, and click Open.
- Click Upgrade.
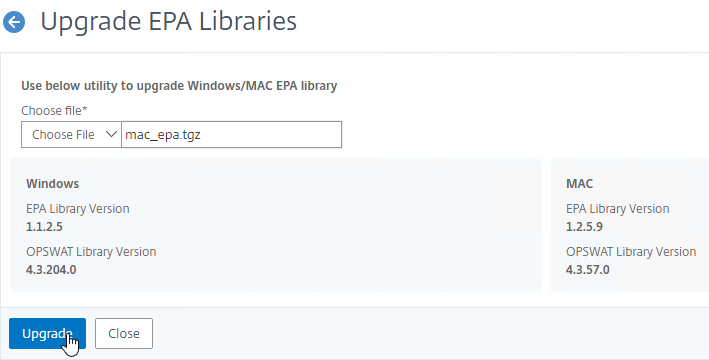
- Click OK when prompted that upgraded successfully.

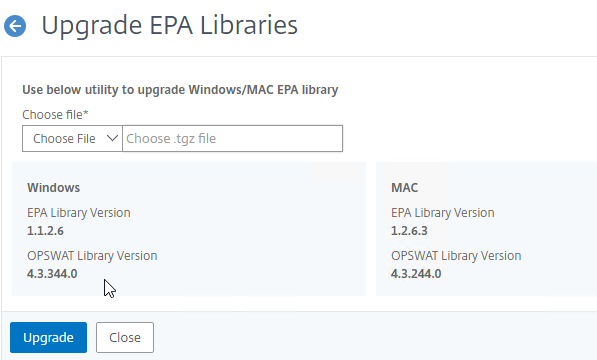
- To see the versions, click Upgrade EPA Libraries.

EPA Plug-in
The EPA plug-in is automatically deployed when the user connects to Citrix Gateway – either before the logon page, or after the logon page.
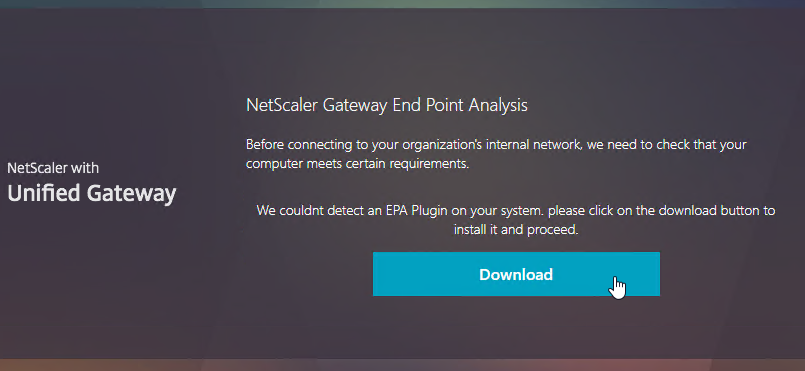
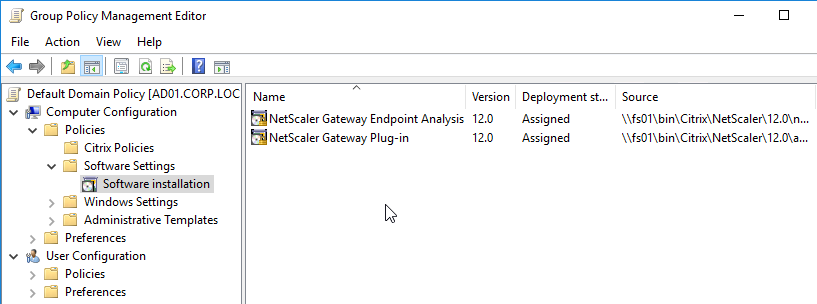
To pre-deploy EPA plug-in, see CTX124649 How to Deploy NetScaler Gateway Plug-in and Endpoint Analysis Installer Packages for Windows by Using Active Directory Group Policy. This article describes how to extract the plug-in .msi file, and deploy using Group Policy.
EPA and Portal Themes
The webpages displayed to the user when downloading the EPA plug-in and running the EPA plug-in can be customized by editing a Portal Theme.
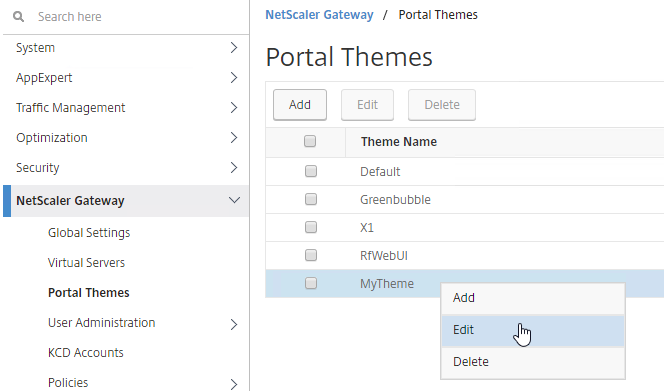
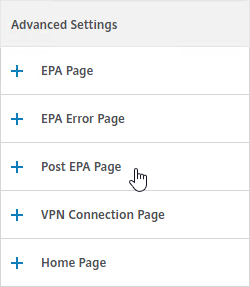
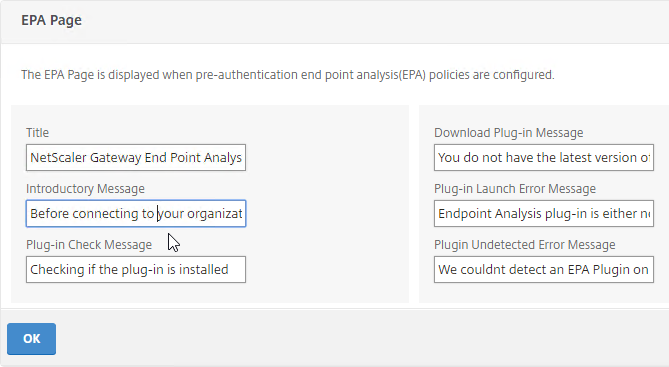
Look in the Advanced Settings column on the right for the three EPA pages. Citrix CTX222812 How to Customize Custom Error Messages for NetScaler Gateway EPA Scans.

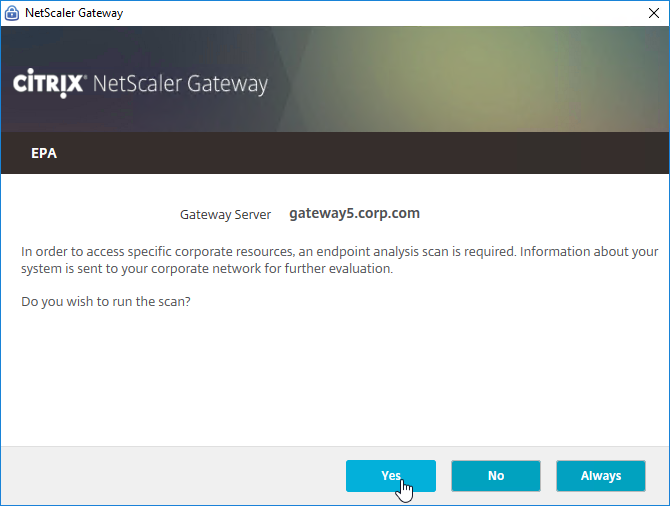
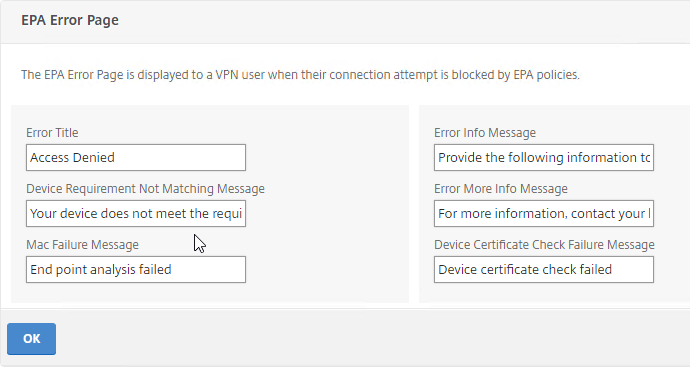
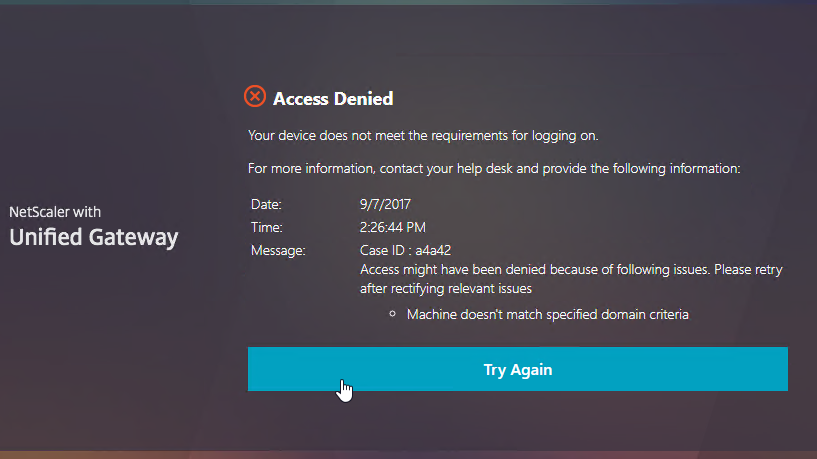
EPA Troubleshooting
From Citrix CTX209148 Understanding/Configuring EPA Verbose Logging Feature:
- Go to Citrix Gateway > Global Settings.
- On the right, click Change Global Settings.
- On the Security tab, click Advanced Settings.
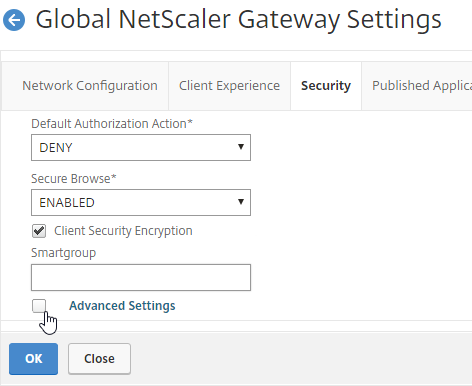
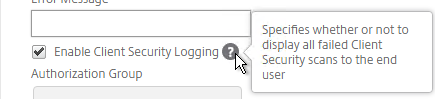
- Scroll down, check the box next to Enable Client Security Logging, and click OK.
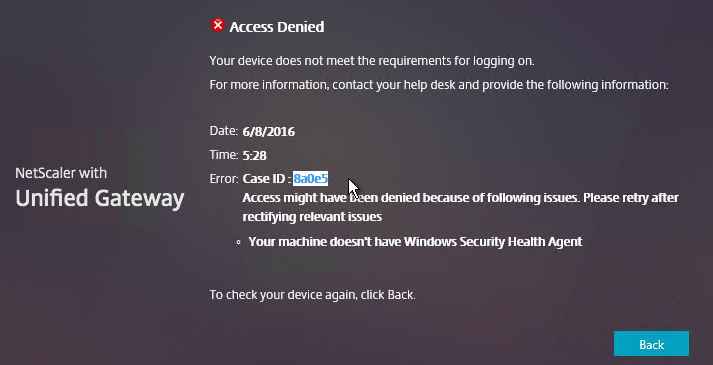
- When the scan fails, the user is presented with a Case ID.
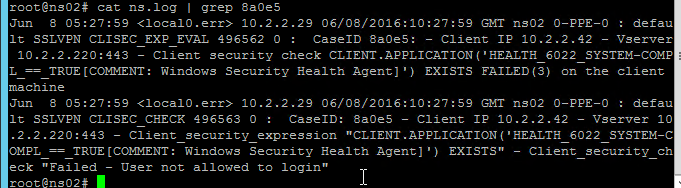
- You can then grep
/var/log/ns.logfor the Case ID. Or search your syslog.
For client-side logging, on the client machine, go to HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Secure Access Client.
- Make a DWORD value named “EnableEPALogging“, and set the value to 1.
- After attempting the scan again, you’ll find the file %localappdata%\Citrix\AGEE\epaHelper_epa_plugin.txt with details for each scan expression.
NetscalerAssasin EPA OPSWAT Packet flow and Troubleshooting shows a Wireshark trace of an EPA scan.
SmartAccess
Links:
- CTX138110 How to Configure the SmartAccess feature on Access Gateway Enterprise Edition Appliance
- CTX227055 Smart Access Guide for NetScaler Gateway, StoreFront and XenDesktop contains packet traces of the StoreFront Callback URL and XML Broker communication.
Make sure the prerequisites are completed. This includes:
- ICA Only unchecked on Citrix Gateway Virtual Server
- Gateway Universal licenses installed
- Callback URL configured at StoreFront
- Trust XML enabled on Delivery Controllers
SmartAccess is configured in two places:
- Delivery Group > Access Policy page in Web Studio in CVAD 2407 and newer has been redesigned. There are built-in Access Policies that you can edit. And you can add Access Policies. They support both inclusions and exclusions. See Citrix Docs for details.
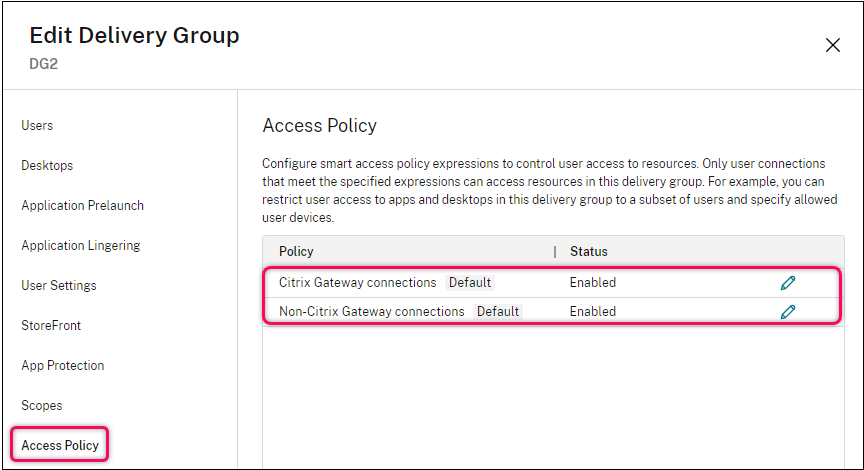
- CVAD 2402 and older looks like the screenshot below.
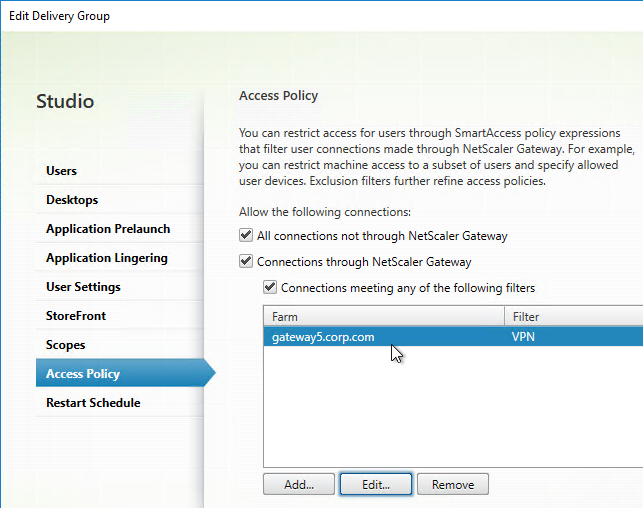
- CVAD 2402 and older looks like the screenshot below.
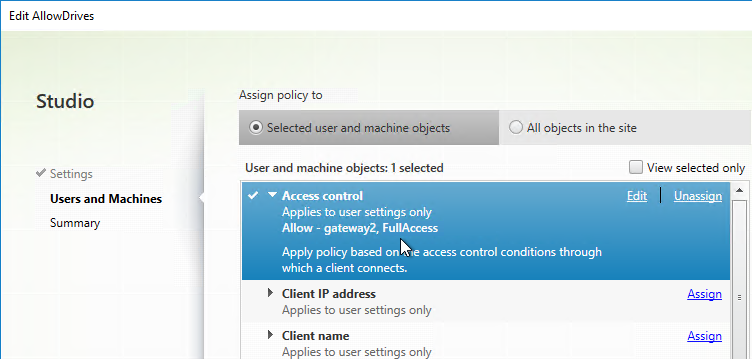
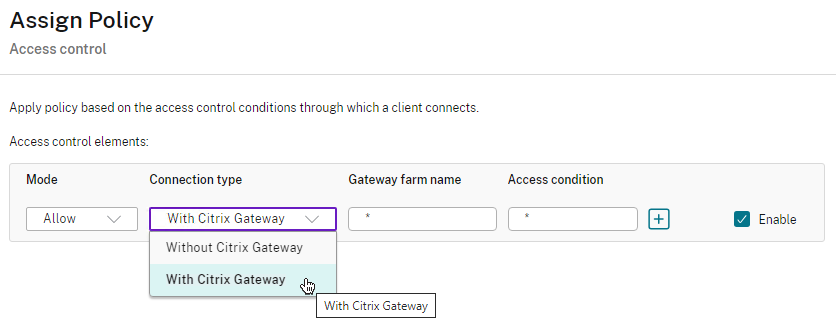
- Citrix Policy (user settings only) > filters > Access control in Web Studio looks like the screenshot below.
- Group Policy looks like the screenshot below.
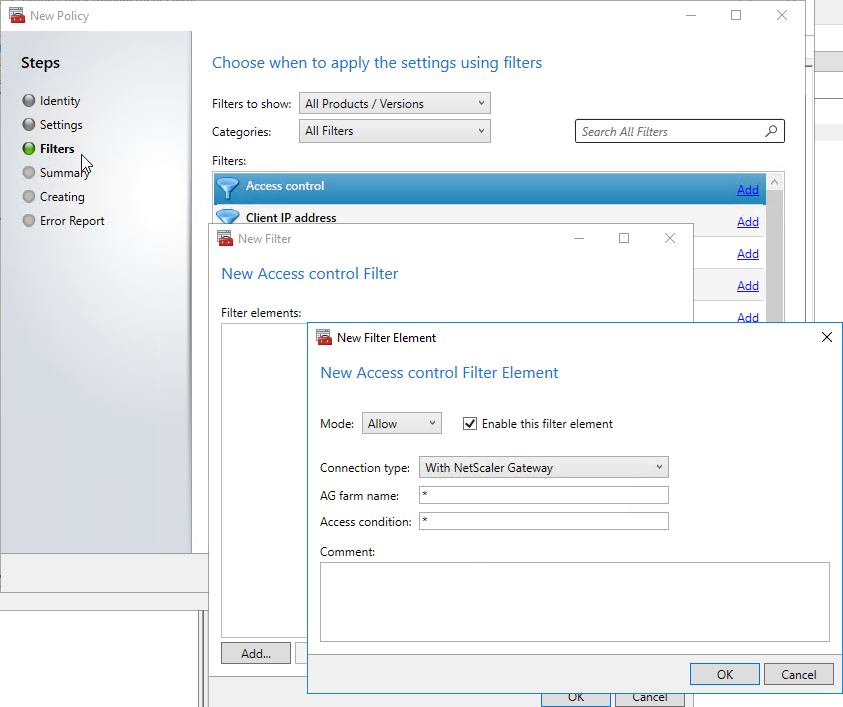
- Group Policy looks like the screenshot below.
In any case, you enter the name of a matching Gateway Virtual Server, and the name of a matching Session Policy (or Preauthentication Policy).
- Set AG farm name or Site or Farm name to the name of the Citrix Gateway Virtual Server.
- Set Access condition or Filter to the name of the Citrix Gateway Session Policy (or Preauthentication Policy).
- You can use * as a wildcard in either field.
- The matching Citrix Gateway Session Policy typically has an EPA Factor in an nFactor flow that puts the user in a AAA Group that has a group-specific Session Policy bound to the AAA group. That way the Session Policy only applies to connections that match the EPA Expression.
Icon visibility – Access Control at the Delivery Group controls visibility of icons published from that Delivery Group.
- Access Control on a Delivery Group is Allow only. Icons are hidden from non-matching connections.
- You can uncheck Connections through Citrix Gateway to hide the published icons from all Citrix Gateway connections.
- It’s not possible to hide individual published applications. You can hide all applications from a single Delivery Group, or none of them. If you need more granularity, then you’ll have to split the applications onto different Delivery Groups.
- App Groups do not have an Access Control option. It’s Delivery Groups only.
Citrix Policy Settings – Access Control filter on a Citrix Policy determines if the Policy settings apply or not.
- Access Control filter applies to User Settings only. It’s not configurable for Computer Settings.
- You typically configure the Unfiltered Citrix Policy to block all client device mappings. Then you configure a higher priority Citrix Policy with Access Control filter to re-enable client device mappings for endpoint machines that match the Session Policy and EPA Expression.
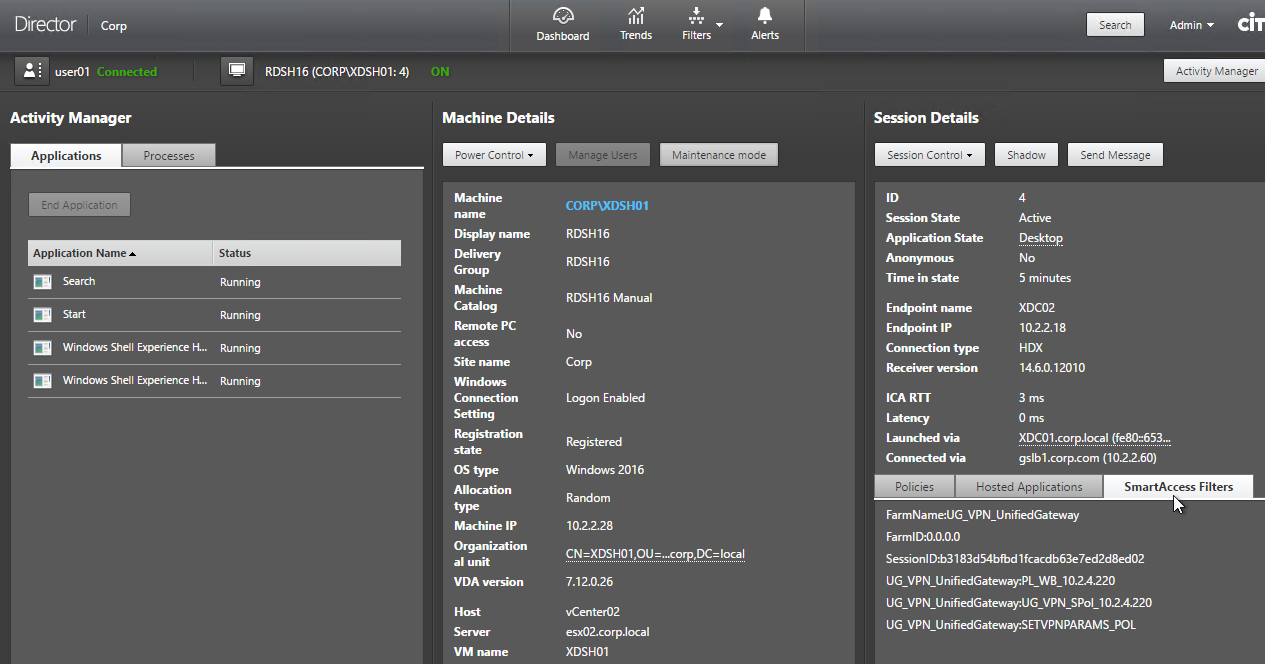
When connected to a session, Director shows SmartAccess Filters on the Session Details page. Notice the Farm Name (Gateway Virtual Server name) and Filter Name (Session Policy name)
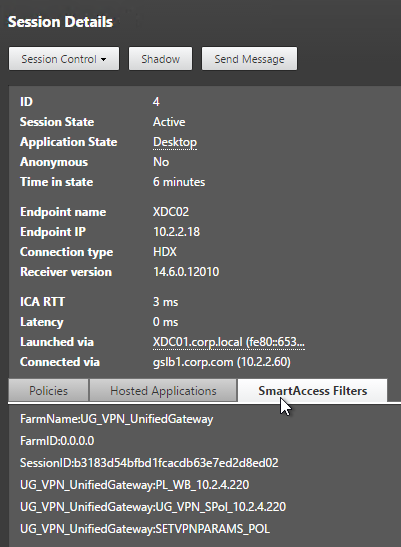
SmartControl
The SmartControl feature lets you configure some of the SmartAccess functionality directly on the appliance. See Configuring SmartControl at Citrix Docs for detailed instructions.
- Note: SmartControl requires Citrix ADC Premium Edition. If you don’t have Premium Edition, you can instead configure SmartAccess.
- SmartControl cannot hide published icons. If you need that functionality, configure SmartAccess, either as a replacement for SmartControl, or as an addition to SmartControl.
To configure SmartControl:
- Make sure the Prerequisites are completed. This includes: ICA Only unchecked and Gateway Universal licenses installed. Callback URL and Trust XML are not needed.
- If you are using a Preauthentication Policy to run an Endpoint Analysis scan:
- Edit the Preauthentication Profile.
- Configure the Default EPA Group with a new group name. You’ll use this group name later.
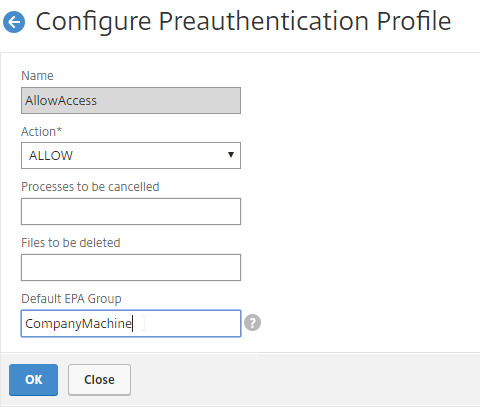
- Edit the Preauthentication Profile.
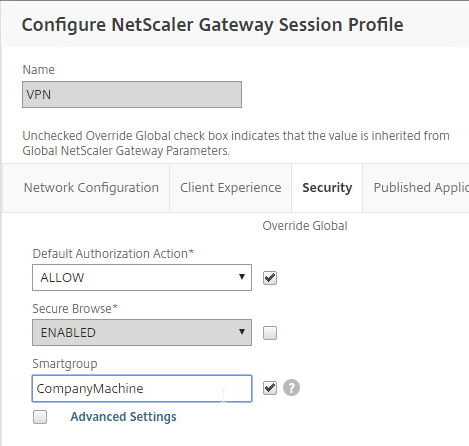
- If you are instead using a Session Policy to run the post-authentication Endpoint Analysis scan:
- Edit the Session Profile
- On the Security tab, use the Smartgroup field to define a new group name for users that pass the scan. You’ll use this group name later.
- On the left, expand Citrix Gateway, expand Policies, and click ICA.
- On the right, switch to the Access Profiles tab, and click Add.
- Configure the restrictions as desired, and click Create.
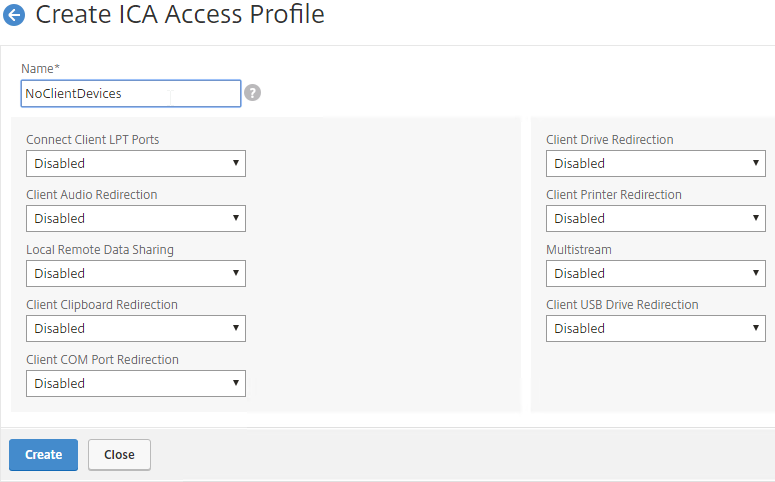
- Configure the restrictions as desired, and click Create.
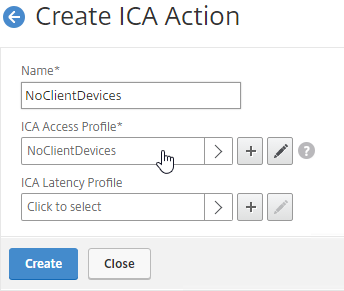
- Switch to the ICA Action tab, and click Add.
- Give the ICA Action a name.
- Select the ICA Access Profile.
- Click Create.
- Switch to the ICA Policies tab, and click Add.
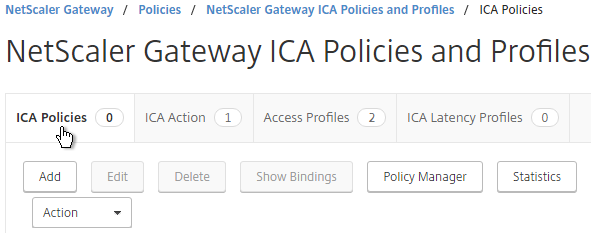
- In the Create ICA Policy page, do the following:
- Give the ICA Policy a name.
- Select the previously created ICA Action.
- Enter an expression. You can use HTTP.REQ.USER.IS_MEMBER_OF(“MyGroup”).NOT where MyGroup is the name of the SmartGroup you configured in the session profile or preauth scan.
- Click Create when done.
- Edit your Gateway Virtual Server.
- Scroll down to the Policies section, and click the plus icon.

- Change the Choose Type drop-down to ICA, and click Continue.
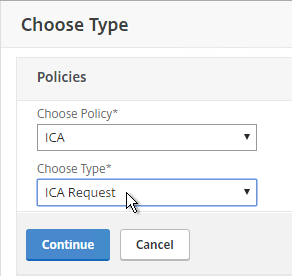
- Select the SmartControl policy you created earlier, and click Bind.
- Scroll down to the Policies section, and click the plus icon.
Hi,
I would like to check if a device is EntraID joined and if so place them in a AAA group. Does this also work with the built-in domain check in EPA?
Kind regards
Erwin
You might be able to let SAML to Entra ID verify device compliance using Conditional Access policies.
I don’t think the NetScaler has Intune integration unless it’s for MDM VPN. However, Device Posture in Citrix Cloud has Intune Integration. https://docs.citrix.com/en-us/device-posture/device-posture-third-party-integrations#microsoft-intune-integration-with-device-posture
Hello, Carl:
I would like to ask you a question about setting up NetScaler’s EPA to scan the user’s MAC address. Even though the user’s MAC address is already on the list, it fails the scan. I found an error message in the nslog:
NetScaler 0-PPE-0: default SSLVPN Message 2018 0: “ns_aaa_nfactor_epa_eval: Evaluation to deny, Reason:2, Sending logs to ADM if configured”
How should I handle this?
Hello, Carl!
How can I add certificate template validation on Citrix Gateway? It is necessary that only certificates written to a USB token are accepted, and those issued for other purposes are rejected.
Thx for an answer!
I don’t see Template in this list – https://docs.netscaler.com/en-us/citrix-adc/current-release/appexpert/policies-and-expressions/advanced-policy-expressions-parsing-ssl.html
Maybe you can create a CA that is the only CA allowed to issue the one template and then check for certs that come from that one CA.
I’m not sure if a HTTP callout would work.
We have configured Citrix Posture (EPA) check policy on Citrix ADC VPX on premises ADC. Now we want to bypass posture check for some set of users.
We want to understand how can we bypass posture check for specific users using any of the option IP\User Name\Security Groups Based.
how the rule can be configured?
We have nFactor followed by EPA scan policy.
Kindly provide policy configuration details.
First factor is LDAP. Next factor is a decision factor with NoAuth policies. If user is not member of the group, then Next Factor (3rd factor) is your EPA scan. Otherwise, 2nd factor should be a NoAuth with “true” expression without Next Factor for the remaining users to let them in.
Any reference article for configuration steps
Can we deploy EPA Library using Intune, if yes do you have step by step procedure which can help.
in our case EPA Library are always missing hence we have to manually copy to desired location each time user reports issue.
What could be the reason for missing EPA Libraries error on end users machine,
EPA agent deployed but always get EPA libraries missing error while EPA posture check is performed.
We had to manually copy & past required files from any of the working machine @ “C:\Users\\AppData\Citrix\AGEE\”, or in some cases we usually extract content of epaPackage.exe binary @ this location.
2023-04-21 13:08:57.563 | Tid: 15416 | DEBUG | ns_verifyfile: called
2023-04-21 13:08:57.743 | Tid: 15416 | ERROR | ns_verifyTrustedCert | 162 | WinVerifyTrust failed -2146762496, err -2146762496
2023-04-21 13:08:57.743 | Tid: 15416 | ERROR | downloadEpaLib | 382 | Failed to verify downloaded EPA library
2023-04-21 13:08:57.743 | Tid: 15416 | DEBUG | ns_verifyfile: called
2023-04-21 13:08:57.747 | Tid: 15416 | ERROR | ns_verifyTrustedCert | 162 | WinVerifyTrust failed -2146762496, err -2146762496
2023-04-21 13:08:57.747 | Tid: 15416 | ERROR | checkAndLoadEPALib | 604 | Failed to verify EPA DLL
2023-04-21 13:08:57.747 | Tid: 15416 | ERROR | initEPAlib | 796 | Failed to load EPA library
2023-04-21 13:08:57.747 | Tid: 15416 | ERROR | epaLibScan | 889 | Failed to initialize EPA library
2023-04-21 13:08:57.747 | Tid: 15416 | DEBUG | ns_EvalPolicy: DOMAIN_SUFFIX_anyof.ab.abc.local returns 2003
2023-04-21 13:08:57.747 | Tid: 15416 | EVENT | ns_EvalPolicy returns 2003
2023-04-21 13:08:57.747 | Tid: 15416 | DEBUG | ns_free_dependspol:num_mallocPolicyBuffer=0
2023-04-21 13:08:57.747 | Tid: 15416 | EVENT | Making GET request to https://workplace.in.abc.com:443epas
2023-04-21 13:08:57.747 | Tid: 15416 | VERBOSE | [<GET epas HTTP/1.1
Cookie: NSC_TMAS=****
CSEC: 2
I know it’s been a while, but did you end up solving this?
Hi Carl,
There’s and additional requirement for the Smart Access that comes up in more complex scenarios, but it’s currently not documented properly:
In cases where Citrix Gateway vServer used for Callback URL is different that the one used for access, ICA Only needs to also be disabled on the Callback Gateway vServer.
This is especially relevant in environments with a common Callback Gateway used for multiple Gateways.
It can take quite a while to troubleshoot if one is not aware of this dependency and so far there seems to be only one mention of this in Citrix documentation – https://support.citrix.com/article/CTX547204/
I’m just putting this here in case others hit the same issue.
Thank you and regards
Luke
smart control is not working when using private/incognito tab of any browser,
Any points will be appreciated.
Is it possible to use Smart Access / Smart Control on the NetScaler to check the OS Version (e.g Windows 7 or Windows XP) and if these OS’s are connecting, to let the user login, but not provide access to any resources / show a page stating “Access Denied due to OS Not Supported” – We cannot do this with an EPA scan, as we do not own / control all end user devices – some do not have install rights for the EPA client. I need to do the OS check for Cyber Essentials Plus certification.
EPA is required to determine OS version. Or maybe the User-Agent header might indicate the OS.
I’ve got a question and I’m not sure if its possible. We want to use Azure AD with conditional access = device is compliant or not. Both will allow login regardless of result but depending on the outcome, it will apply mapped drives. Can Netscaler Access leverage this type of response? or is Smart Access/Control only via expressions that the NetScaler can do? I was unsure if there is a expression string or if Azure AD would simply block on non-compliance and not passthrough
Can Azure AD send back SAML attributes based on the results of Conditional Access?
Carl, once again you are a lifesaver
In our environment the NetScaler has the universal license, the ICA only box on the Gateway vserver is unchecked, Trust XML enabled on Delivery Controllers and Storefront has the callback URL. In the CVAD polices I have given the gateway name as farm name and the access condition as * . But in the director under “SmartAccess Filter” its says “none”. Any assistance would be much appreciated.
Hi Carl,
when i want to use the “AAA.USER.IS_MEMBER_OF(“GroupName”)” in the advanced session policy, i get always an “Expression syntax error”. Also using the expression editor i cannot find the AAA.USER…..
Using the CLI i have the same issue (add vpn sessionPolicy FullAccess AAA.USER.IS_MEMBER_OF(“Groupname”) FullAccess).
Greets Hilmar
What build of ADC?
In the GUI, make sure you select Advanced Policy or click “Switch to Default Syntax”.
Hi Carl,
When you say “The final Policy Label should have an EPA Factor with Goto = NEXT and the second policy as NoAuth”. The noAuth policy should have assigned the next factor ? (i.e LDAP) or both? or only the EPA?
I’m seeing the following message in the ns.log “nFactor EPA: Skip the following Authentication factor due to epa failed and quarantine group is configured”. I configured a quarantine group in the initial EPA policy. When the EPA fails I want to assign the users to a different AAA group but the NetScaler seems to bypass the next factor when quarantine group is configured. Any ideas?
I am trying to implement EPA for Windows/MAC devices as a session policy. ADC is 12.1.57.18, Standard license so I do NOT have nFactor. Am I correct in understanding that this wiil NOT work on a Windows client with the most current Workspace app? I can login, see EPA startup as a post auth process but it always allows the client to connect, even when the is a client expression that should cause the client to fail.
Preauth policy can prevent failed clients from logging in.
Postauth Session policies don’t apply to clients that can’t run EPA but other Session Policies that don’t have EPA expressions still apply.
Browsers can always run EPA.
Thanks Carl. Just trying to determine the best route. I have Windows/Mac/iOS/Android devices that all connect to this gateway. I can make my Win/Mac scan correctly with a preauth policy but then all of my iOS/Android devices fail. If it do it as a session policy, I can bypass EPA on IOS/Android but my Windows/Mac devices don’t seem to observe the EPA expression I have.
Hi Carl,
Thanks for this, great job!! So for the StoreFront configuration you mentioned “If you are configuring Single FQDN for internal and external, then the Callback FQDN must be different than the Single FQDN.”. Does this need to be a website accessible from the StoreFront? We get an IIS error when using a different Callback then the Single FQDN. What kind of testing can you do to confirm your new Callback is working if you can’t use the single FQDN?
Also, if not using EPA, what Session Policy would you use (In the delivery group/policy) filter if you are just using ICA Proxy (Receiver Self Service or Receiver Web)
Callback FQDN needs to resolve to a Gateway VIP on the same appliance that authenticated the user. The certificate on the Gateway VIP must match the Callback FQDN. On StoreFront, open a browser and enter the callback FQDN to see the Gateway logon page with no certificate errors.
EPA is not strictly necessary for SmartAccess. If you want to block all Gateway connections, then enter * to match all Gateway Session Policies.
Thanks Carl. If we already have a single Gateway VIP accessible via FQDN for authenticating users internal and external, should we set up a second one (fake), used for Callback? Just asking because it says we can’t use the same single FQDN (“If you are configuring Single FQDN for internal and external, then the Callback FQDN must be different than the Single FQDN.”)
Yes.
Or you can add the new callback FQDN to your existing Gateway certificate and then resolve the Callback FQDN to your existing Gateway VIP.
Hey guys, maybe this will spare you some time,
if you want to deny for example external GW Usersessions access to their local clientdrives through a set of Studio policies and have assigned “Access Control” to your Citrix Studio Policy correctly, but it still does not work, check your Store configuration.
Under “Configure Store Settings”->”Advanced Settings” for the option “Require Token Consistency”. Once activated and replicated to all of your Storefront Servers it should work immediately.
https://support.citrix.com/article/CTX136669
Cheers
Thanks Sascha this save me today
Hi Carl. I am huge fan of your and I propably do nothing without checking out your blog.
One of my clients would like to use CVAD Advanced with Smart Access, however Citrix’s feature matrix shows that it is only included in Premium edition, just because it includes de Citrix Gateway Universal License.
My understanding is that this feature is much more related to the ADC license than CVAD Licensing.
My question is: Is there a CVAD requirement for that?
I’m not aware of any reason it won’t work in CVAD Advanced.
It seems Smart Access is available only for Premium CVA or CVAD Licenses https://www.citrix.com/products/citrix-daas/feature-matrix.html
Hi Carl,
Excellent post as always, i’m wondering if you know how the smart access can be used in order to limit the access to VAD only from managed devices (CEM/Xenmobile). Thanks!
See https://docs.citrix.com/en-us/xenmobile/server/apps/smart-access-to-hdx-apps.html
Hi Carl, big fan or your blog. one question about the EPA. I want to setup a expression to limit the minimum version of local installed receivers on clients PC. However I can not find anything useful. I can check registry for receiver’s existence but not versions. Can you point me to the right directions please?
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Citrix\Dazzle has a Version value. However, this might only be there if Workspace app is installed as administrator.
Another option is to right a VDA login script that checks HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Ica\Session\{ID}\Connection\ClientVersion.
Hello Carl,
I tried to work with CTX209148 configure verbose logging on ADC 13.0! I will not find the Case-ID in the ns.log.
Do you know how I can design verbose logging to check failed EPA scan on ADC? Just client logging is not usefull. With EPA as first factor I can’t find out which user failed EPA Scan.
Nice Regards
Tobias
Hi Carl,
I have a problem implementing EPA checks.
I have configured an AAA vserver in front of my Citrix Gateway with EPA next factor and I have configured some different policies and Policylabels with specific EPA actions, depending on users groups or User-Agents.
I wrote an exclusion for all non-windows devices, preventing any kind of EPA checks.
All works fine except with IOS devices, when I configure Workspace App in automatic/native mode (XenApp Services) I get a generic error “no apps available at this time”. If I use the manual configuration with web interface mode, Workspace App prompts for credentials and all works fine, but I lose some good feature (eg Face id authentication for login).
I have read in some posts and docs that IOS does not support NetScaler nFactor Authentication nor Advanced Authentication methods (really????) https://www.citrix.com/content/dam/citrix/en_us/documents/data-sheet/citrix-workspace-app-feature-matrix.pdf.
is there a way to bypass advanced auth only for IOS devices or I have to configure another logon point for mobile devices pointing directly to a Gateway?
I tried to configure a Policylabel (higher priority) with only a policy with an LDAP action but of course it does not work.
Thank you in advance
Hi Carl,
just a quick update on my request. I tried CR01 on IOS instead of Workspace App and I was able to display and launch my applications. I opened a case, I’m waiting for support’s analisys.
Thank you
Harald
Hi Carl,
I’ve been able to setup SmartAccess and I was going to test it by creating AAA user and Session policy with EPA expression under Security -> AAA Application Traffic -> Policies -> Session and bind that to AAA User, but for some reason the Session Policy does not accept e.g. the following classic syntax policy:
CLIENT.APPLICATION(‘FIREWALL_0_ENABLED_==_TRUE[COMMENT: Generic Firewall Product Scan]’) EXISTS
I get the following error: Expression syntax error [CLIENT.^APPLICATIO, Offset 7]
Also the OPSWAT EPA Editor link is not available when configuring session policy. I had similar difficulties with session policies under Citrix Gateway, but after trying for couple of times it eventually accepted the expression, and only after being able to create the first session policy with the EPA Expression the OPSWAT EPA Editor link became visible in new policies. Should I be able to configure the Classic EPA Expression under Security -> AAA Application Traffic -> Policies -> Session?
NetScaler VPX 12.1 55.13 with Enterprise license
Not under AAA, but under Gateway, yes. At Gateway -> Policies -> Session you can create a Classic Session Policy. Note: VPN Session Policies are different from TM (aka AAA) Session Policies. For Gateway connections, you want VPN Session Policy, not TM Session Policy.
Hi Carl,
I have configured pre-authentication policy on my Netscaler VPX appliance. While downloading EPA plugin I am getting following error
– Forbidden
You don’t have permission to access /epa/scripts/win/nsepa_setup.exe on this server.
I need your help to fix this issue
Regards,
Ilyas Ahmed
Maybe this – https://support.citrix.com/article/CTX263565
Hi Carl,
Is it possible to access 1 Delivery Group via 2 different VIP (one VIP is for public and Second VIP for client specific) through Access Policy (Edit Delivery Group)?
Thanks,
AJ
Are you asking if you can add more than one Filter to the Delivery Group > Access Policy page? The GUI seems to indicate that you can.
Hi, Carl
Cloud you please help us, when i update epa Libraries get this error info”Required files are missing. Check whether the tar ball “mac_epa.tgz” is valid”
Platform NSMPX-5500 /NS12.0 53.13.nc
Maybe you need to upgrade firmware before it will work?
OK,I will try it .
Hi Carl,
I can’t really understand.
what license do I need to use NetScaler Gateway ICA policies and profiles?
for example: I want to apply ICA Access Profile to disable LPT printers redirection.
what license do I need to use this capability.
standard/enterprise/platinum?
NetScaler needs to be Platinum Edition to use SmartControl.
Hi Carl,
According to CTX204764, it is possible to check the presence of an antivirus without mentioning specific vendors
add aaa preauthenticationpolicy “CLIENT.APPLICATION(‘ANTIVIR_0_RTP_==_TRUE[COMMENT: Generic Antivirus Product Scan]’) EXISTS”
Is there a way to check whether the antivirus in place is active ? (in order to handle cases where the end user could have admin privileges on his machine and be able to disable the antivirus)
Have a great day 😉
Kind regards
Yvan
Hello Carl,
Thanks so much for clarifying this. Could you please help us in a scenario where we have 4 access profiles,3 with different permit rules. one for Clipboard, one for printer, one for Drive map and last one is Block_ALL. each permit looks membership of user into separate AD group. Allow_printer , Allow_Drive, Allow_Clipboard. Then we created 4 ICA policy 3 for the the permits Action/Access profile for printer clipboard and Drive. Last one for Block_All. 3 permits policy (clipboard, drive and ) are binded to Override_Global with priority 80 90 and 100. Block_All is binded to Default Global. but when we login only the first one in permit takes affect when user is part of all 3 permit AD group. other are being ignored.
Something similar to below thread but in context of ICA policy.
https://discussions.citrix.com/topic/347876-access-gateway-session-policy-bound-to-ad-group/?_ga=2.149900534.1966599676.1516636603-707661493.1513697800
When you bind the policy and set priority, what is the «goto expression» value? Default is END, try setting NEXT to continue evaluating policies after the first hit.