Navigation
- RADIUS Overview
- Two-factor Policies Summary
- Create Two-factor Policies
- Bind Two-factor Policies to Gateway
RADIUS Overview
For two-factor authentication using Azure Multi-factor Authentication, see Jason Samuel How to deploy Microsoft Azure MFA & AD Connect with Citrix NetScaler Gateway
Citrix CTX125364 How to Configure Dual Authentication on NetScaler Gateway Enterprise Edition for Use with iPhone and iPad
Some two-factor products (e.g. SMS Passcode) require you to hide the 2nd password field. Receiver 4.4 and newer supports hiding the 2nd field if you configure a Meta tag in index.html. See CTX205907 Dual-Password Field Shows in First Authentication When Connecting to NetScaler Gateway from Windows Receiver for instructions.
Two-factor authentication to NetScaler Gateway requires the RADIUS protocol to be enabled on the two-factor authentication product.
On your RADIUS servers, you’ll need to add the NetScaler appliances as RADIUS Clients. When NetScaler uses a local (same appliance) load balanced Virtual Server for RADIUS authentication, the traffic is sourced from the NetScaler SNIP (Subnet IP). When NetScaler uses a direct connection to a RADIUS Server without going through a load balancing Virtual Server, or uses a remote (different appliance) Load Balancing Virtual Server, the traffic is sourced from the NetScaler NSIP (NetScaler IP). Use the correct IP(s) when adding the appliances as RADIUS Clients. And adjust firewall rules accordingly.
For High Availability pairs, if you locally load balance RADIUS, then you only need to add the SNIP as a RADIUS Client since the SNIP floats between the two appliances. However, if you are not locally load balancing RADIUS, then you’ll need to add the NSIP of both appliances as RADIUS Clients. Use the same RADIUS Secret for both appliances.
Two-factor Policies Summary
When configuring the NetScaler Gateway Virtual Server, you can specify both a Primary authentication policy and a Secondary authentication policy. Users are required to successfully authenticate against both before being authorized for NetScaler Gateway.
For browser-based StoreFront, you need two authentication policies:
- Primary = LDAPS authentication policy pointing to Active Directory Domain Controllers.
- Secondary = RADIUS authentication policy pointing to RSA servers with RADIUS enabled.
For Receiver Self-service (native Receiver on mobile, Windows, and Mac), the authentication policies are swapped:
- Primary = RADIUS authentication policy pointing to RSA servers with RADIUS enabled.
- Secondary = LDAPS authentication policy pointing to Active Directory Domain Controllers.
If you need to support two-factor authentication from both web browsers and Receiver Self-Service, then you’ll need at least four authentication policies as shown below.
Primary:
- Priority 90 = RADIUS policy. Expression = REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver
- Priority 100 = LDAP policy. Expression = REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver
Secondary:
- Priority 90 = LDAP policy. Expression = REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver
- Priority 100 = RADIUS policy. Expression = REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver
Create Two-factor Policies
Do the following to create the Two-factor policies:
- Create an LDAP policy/server.
- For RADIUS, on the left, expand NetScaler Gateway, expand Policies, expand Authentication, and click Radius.
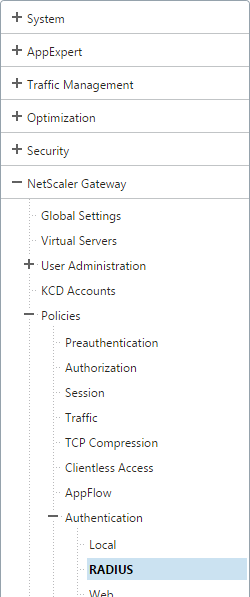
- On the right, switch to the Servers tab. Click Add.
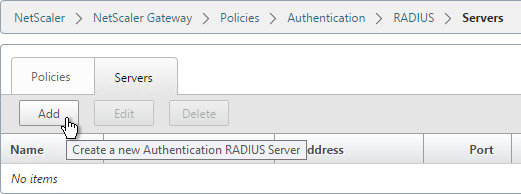
- Give the RADIUS server a name.
- Specify the IP address of the RADIUS load balancing Virtual Server.
- Enter the secret key specified when you added the NetScalers as RADIUS clients on the RADIUS server. Click Create.
add authentication radiusAction RSA -serverIP 10.2.2.210 -serverPort 1812 -radKey Passw0rd
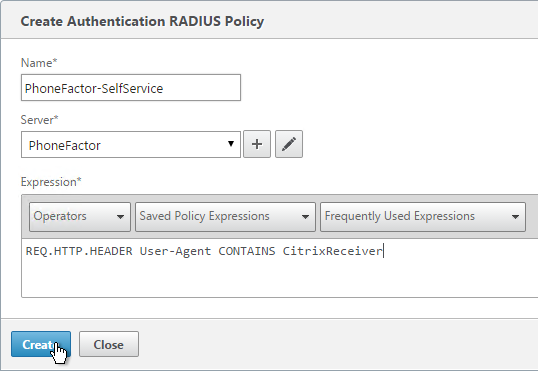
- On the right, switch to the Policies tab, and click Add.
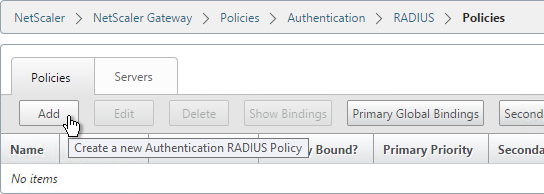
- Name it RSA-SelfService or similar.
- Select the RADIUS server created earlier.
- Enter an expression. You will need two policies with different expressions. The expression for Receiver Self-Service is HTTP.HEADER User-Agent CONTAINS CitrixReceiver.
- Click Create.
add authentication radiusPolicy RSA-ReceiverForWeb "REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver" RSA add authentication radiusPolicy RSA-ReceiverSelfService "REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver" RSA add authentication ldapPolicy Corp-Gateway-ReceiverForWeb "REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver" Corp-Gateway add authentication ldapPolicy Corp-Gateway-ReceiverSelfService "REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver" Corp-Gateway
- Create another policy to match the ones shown below. Both RADIUS policies are configured with the same RADIUS server. The only difference between them is the expression (CONTAINS vs NOTCONTAINS)
Name Expression Server RSA-SelfService REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver RSA RSA-Web REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver RSA 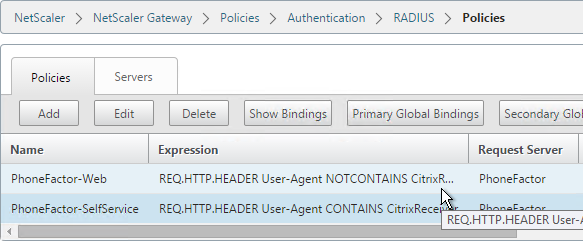
- Go to NetScaler Gateway\Policies\Authentication\LDAP. On the Policies tab, create two policies with the expressions shown below. Both LDAP policies are configured with the same LDAP server. The only difference between them is the expression (CONTAINS vs NOTCONTAINS).
Name Expression Server LDAP-Corp-SelfService REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver LDAP-Corp LDAP-Corp-Web REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver LDAP-Corp 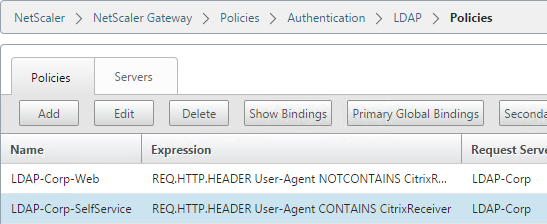
Bind Two-factor Policies to Gateway
- When you create the NetScaler Gateway Virtual Server, bind the policies as shown in the following table. Priority doesn’t matter because they are mutually exclusive.
Policy Name Type Bind Point LDAP-Corp-Web LDAP Primary RSA-SelfService RADIUS Primary LDAP-Corp-SelfService LDAP Secondary RSA-Web RADIUS Secondary 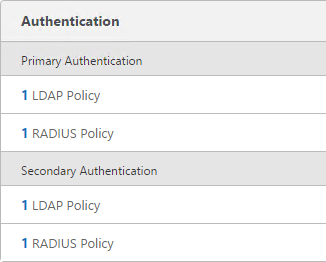
bind vpn vserver gateway.corp.com -policy Corp-Gateway-ReceiverForWeb -priority 100 bind vpn vserver gateway.corp.com -policy RSA-ReceiverSelfService -priority 110 bind vpn vserver gateway.corp.com -policy RSA-ReceiverForWeb -priority 100 -secondary bind vpn vserver gateway.corp.com -policy Corp-Gateway-ReceiverSelfService -priority 110 -secondary
- The session policy/profile for Receiver Self-Service needs to be adjusted to indicate which authentication field contains the Active Directory password. On the Client Experience tab or the Session Profile is Credential Index. This needs to be changed to SECONDARY. Leave the session policy for Web Browsers set to Primary.
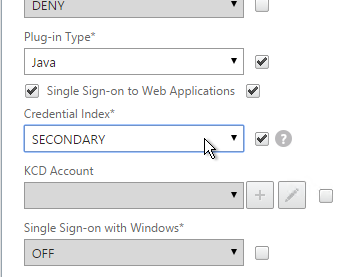
set vpn sessionAction "Receiver Self-Service" -ssoCredential SECONDARY
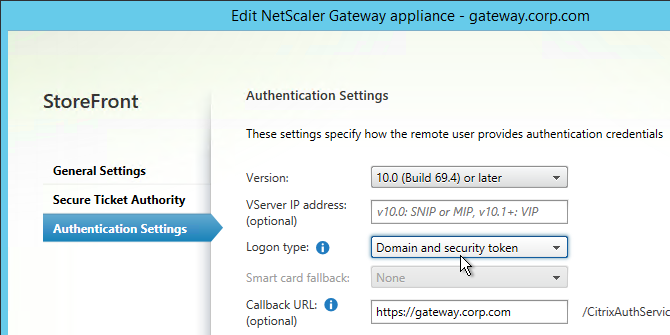
- On the StoreFront server, when creating the NetScaler Gateway object, change the Logon type to Domain and security token.
Hello Karl
Thanks for the introduction, everything seems to have worked.
Now I try it the other way around, so first factor OTP then LDAP , so that the LDAP factor can not be blocked by repeated failed attempts.
so I did the following:
1.authpol: LDAP no auth
2.polllabel: OTP verify
3.polllabel: LDAP auth
but unfortunately it did not work, I get the error message “Failure_reason “External authentication server denied access” on level polllabel: LDAP auth
Any idea what the reason is ? Looking forward for your comments. Thanks.
Hi Carl..
I have been using your post to assist with enabling my Netscaler to have Azure MFA authentication enabled through Radius Server. We currently use LDAP and it is working well. The NPS server has already been enabled with MFA, as there is another component through Fortigate that is using it and it works fine. We have created the conditional and networ policy as per the instructions and it is all good.
In the Netscaler, we have tried many method to make it happen, such as create the LDAP/RADIUS for both primary and secondary, or just radius policy and server binded to the existing gateway and etc, but we are just not getting through. It allows us to enter the username and AD password but nothing happens and it just comes back as user does not exist. If we remove the radius policy, the authentication through AD works fine and user can log in.
The netscaler is version NS 11.0 Build 70.114
Appreciate your advise on this.
Kavi
If there’s a long delay, then it means the user needs to respond to prompts on the user’s phone.
If the error appears quickly, then check your NPS logs and MFA plugin logs.
Hi Carl,
Good day!
Hope you are well. Thank you again for this.
Just have a question with regards to Citrix gateway on-premise identify management service which act as an authentication service to Citrix workspace cloud environment.
Currently we have successfully integrated the on-premise Citrix gateway using AAA authentication to citrix cloud and we add radius server(Cisco ACS) as the authentication method.
We have an issue accessing the cloud app using citrix gateway on-prem IDP.
The error message is ‘failed to login user due to insufficient claims. Please contact your administrator.’
Note: Cisco ACS is already integrated to Active Directory
aaad.debug states that the radius authentication is successful
Hope you can help me on this.. 🙂
Thanks Carl! 🙂
Regards
Did you enable the Send Password option?
Hi Carl,
Thanks for a great article as always, would there be an easy to way to disable the radius authentication, for emergency situations? is it a case of just disabling Radius so users would just log on with LDAP, or do i need to delete the radius polices and add them back in once we want to implement it again?
You would have to unbind the RADIUS policies from the bind point. You should be able to create some CLI commands to do this quickly.
Hi Carl,
thanks for a reply, appreciate the help, i tried this over the weekend by unbinding both the Radius Policies but i still couldn’t log in with just Username and password, do i need to change the logon type on the store front back to just domain as well?
Are you using Workspace/Receiver instead of a browser? Does it work in a browser?
If you have Session Policies/Profiles with Credential Index set to Secondary, you might have to change them to Primary.
Hi Carl, thanks for such a quick reply, really appreciate the help! It doesn’t work for receiver or browser, i have checked both the session profiles and they are already set to Primary.
What do you see in StoreFront Server > Event Viewer > Applications and Services > Citrix Delivery Services?
this is the log I get for citrix receiver for service
Unhandled exception thrown for route “DazzleResources/Image” System.ArgumentException, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089 Parameter is not valid. at System.Drawing.Bitmap..ctor(Stream stream) at Citrix.DeliveryServices.ResourcesCommon.Wing.WingAdaptors.Icons.Ico.WingIco.GetImageStreamForPngEntry(IcoImageEntry entry, ImageFormat targetFormat, Int32 targetSize) at Citrix.DeliveryServices.ResourcesCommon.Wing.WingAdaptors.Icons.Ico.WingIco.GetImage(ImageFormat desiredFormat, Int32 desiredSize, Nullable`1 desiredDepth) at Citrix.DeliveryServices.ResourcesCommon.Wing.WingAdaptors.Icons.ImageSet.CreateImage(ImageParametersQuery queryParameters) at System.Collections.Concurrent.ConcurrentDictionary`2.GetOrAdd(TKey key, Func`2 valueFactory) at Citrix.DeliveryServices.ResourcesCommon.Wing.WingAdaptors.Icons.ImageCache.TryGetImage(String thumbprint, ImageParametersQuery parameters, IImageContent& content) at Citrix.DeliveryServices.DazzleResources.Web.Controllers.DazzleResourcesController.d__3f.MoveNext() — End of stack trace from previous location where exception was thrown — at System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw() at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task) at Citrix.DeliveryServices.DazzleResources.Web.Controllers.DazzleResourcesController.d__25.MoveNext() — End of stack trace from previous location where exception was thrown — at System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw() at System.Runtime.CompilerServices.TaskAwaiter.HandleNonSuccessAndDebuggerNotification(Task task) at lambda_method(Closure , Task ) at System.Web.Mvc.Async.TaskAsyncActionDescriptor.EndExecute(IAsyncResult asyncResult) at System.Web.Mvc.Async.AsyncControllerActionInvoker.c__DisplayClass3f.b__3e(IAsyncResult asyncResult) at System.Web.Mvc.Async.AsyncControllerActionInvoker.EndInvokeActionMethod(IAsyncResult asyncResult) at System.Web.Mvc.Async.AsyncControllerActionInvoker.c__DisplayClass37.c__DisplayClass39.b__33() at System.Web.Mvc.Async.AsyncControllerActionInvoker.c__DisplayClass4f.b__49() at System.Web.Mvc.Async.AsyncControllerActionInvoker.c__DisplayClass4f.b__49() at System.Web.Mvc.Async.AsyncControllerActionInvoker.c__DisplayClass4f.b__49() at System.Web.Mvc.Async.AsyncControllerActionInvoker.c__DisplayClass4f.b__49() at System.Web.Mvc.Async.AsyncControllerActionInvoker.c__DisplayClass4f.b__49() at System.Web.Mvc.Async.AsyncControllerActionInvoker.EndInvokeActionMethodWithFilters(IAsyncResult asyncResult) at System.Web.Mvc.Async.AsyncControllerActionInvoker.c__DisplayClass25.c__DisplayClass2a.b__20() at System.Web.Mvc.Async.AsyncControllerActionInvoker.c__DisplayClass25.b__22(IAsyncResult asyncResult)
Maybe a published app has a bad icon file.
Ok thanks for all the help with this, any advice on where to start with the published app?
Just to confirm , once i unbind the Radius policies should i still have 1 LDAP for Primary and 1 LDAP for secondary?
You should only have one LDAP for Primary. The one for Secondary is only used by Workspace/Receiver if you’re also doing RADIUS.
thanks Carl that makes more sense now, appreciate your help on this.
Hi,
We have Netscaler Gateway with radius servers for authentication. We have configured the Netscaler to send the logs to a a external syslog server.
The problem we have is the external syslog server receives only Radius authentications with failures not the users who are successfully logging into the system. Is this expected?
What log levels are enabled in your Syslog policy/server?
We have ALL
Hi Carl
Is it possible to have 2 RADIUS authentication servers bound to the same Virtual Server and get the user directed to the correct one based on AD Group Membership?
Use case is when transitioning from MFA providers and having to use both during the transition.
Thanks
nFactor can do this. First factor would ask for the username and then use an LDAP policy/server to retrieve the user’s group membership. Then select the next factor (radius) based on group membership.
Hi,
Wonder is anyone has any ideas. We are just starting off with MFA and if the users have not registered they are in an AD group along the line MFA_UNregistered, Is there anyway we can check for membership of this group and if they are not a member then continue to the normal Radius authentication, and if they are to redirect them to an error advising them to login.
Hi, I need to configure the NetScaler to authenticate to MFA via radius protocol. However the MFA server require an additional radius attributes (filter-id) , is that possible to configure in the NetScaler to pass the filter-id radius attributes that contains the static string value ? Looking forward for your comments. Thanks.
Hi Carl
We’re looking to implement Azure MFA via NPS using radius. I have set this up on our test netscaler using a single RADIUS authentication policy and it seems to be working well.
However, we have a requirement to exclude a particular domain from MFA. All my reading shows that conditional access is not possible when using NPS i.e. all or none.
Can this somehow be done on the Netscaler side?
Sem
Hi Carl, Nice Article and I have followed the document and configured radius servers on LB. I am using 10.5 version. W have a new requirement to migrate the users to new radius servers hosted in AWS . The challenge here is phase by phase migration few users will still reside in old radius server and migrated users in new AWS environment. Just want to understand if I add the new AWS radius servers in load balancing will it go to the second radius server if user is not found on the first radius server ? If not what is the best option for this scenario
Are you doing RADIUS authentication on NetScaler? If so, create two separate RADIUS Policy/Servers and two separate Load Balancing VIPs. If first RADIUS policy fails, it should try the second.
Thanks for the reply Carl . I am using two factor authentication on netscaler , primary LDAP and secondary RADIUS. If my understanding is correct create two policy with different priority say 90 & 100 . 90 will have current RADIUS server and 100 will have new radius server configured. If user is not in the first radius server which has policy 90 then it will fail and will go to second radius server with priority 100 ? I am only a beginner in netscaler is my understanding correct ? Is there any additional parameter to be set so that it will go to second policy if it fails or is it default behaviour ?
This is called Cascade authentication. If the first fails, it tries the second.
Hi Carl,
Been following your articles and hoping you have a bit more of a clue here than we do as we’re struggling! We are moving from RSAID to Azure MFA but want to do it gradually if possible while retaining the second password box.
We’ve set up MFA NPS ext on 2 Server 2016 servers, it’s working as we have another F5 appliances using it now in test without issues. The production NetScaler (10.5) is configured today to use LDAP as Primary Auth and RADIUS (RSAID server) and that works. The test NetScaler we setup works with Azure MFA NPS just fine if we only put a RADIUS policy as first auth (LDAP may still be needed later possibly for AD Group based Authorization mind you, but first things first), the RADIUS request goes to the MFA NPS server and it processes BOTH the LDAP Authentication and MFA challenge (per MS docs) albeit only a Authenticator App verify or Phone call verify, and logs you in, grand.. things are good.
However when we put LDAP Policy as Primary, and Radius as Secondary (like the RSA config) but pointing to MFA NPS, the second password box appears on the NS Gateway as you’d expect, and when we enter the Token code generated on the MS Authenticator App, it sends an AccessReject RADIUS request to the MFA NPS server, and this is where we’re stuck because of course the MFA NPS extension ignores it and does nothing.
The reason we don’t want to roll with option A above is because we want to transition people over gradually, and present the same user experience they have today, where they enter either the RSAID token code OR the MFA Authenticator App code into the second password box, and using cascading RADIUS auth policies try the RSA server first, failing that the MFA NPS server. That’s the dream.
It does not work.
Do you know if this is even possible? I fear we may be barking up the wrong tree, and am certainly banging my head against a wall.
Can NPS be configured to not require AD authentication?
How are you determining which user does which authentication?
Are users authenticating with Receiver? If not, which means browsers only, then you might be able to do nFactor authentication with different authentication methods for different users.
NPS does AAD Auth by design, unlikely it can be turned off… although a good idea.
NS VPX us 10.5, nFactor doesn’t seem to be available until v11+
We determine how users auth by the method they have, if they still have an RSA token they’ll enter those token digits into 2nd password. If they’ve been moved to MFA and enrolled they’ll enter the MS Authenticator app code. Hoping it can cascade the digits entered into the second password box to RSA first then MFA NPS.
Hey Carl,
I have RADIUS authentication setup to proxy through our MS MFA on-prem server to our NPS server. Only using 1 authentication policy bound to the NSGW vServer. Authentication works good, but some users on the inside are being asked to confirm through the MFA (Some are not). Ideally MFA would only be used if the users were external and SSO for all logins internal. Any suggestions on what I should focus on?
Carl, I have a single VIP that I use for Xenmobile and also for Storefront access. Our customer would like to use Ldap + radius for Storefront access but for Xenmobile they dont want to use radius at all. No matter what policy I use on the secondary Radius authentication policy it still prompts for token in Xenmobile. Is there a way to set it up so Xenmobile doesnt try and use the Radius policy?
Unfortunately I don’t think that’s possible. Once you specify the second factor, mobile clients try to prompt for the second password. There’s also a Meta tag, but I don’t know if that would apply to XenMobile.
Thanks! That’s kind of what i was starting to figure.
Hello Carl,
Been a huge fan of your page. Straight, to the point, and works, when it comes to all things Citrix.
I do have a question, based with the way we are looking to handle RADIUS.
We are phasing out one product (RSA) and setting up another (Symantec VIP), however, we would like to get the transition done gradually. We would like one department to use VIP, another department to use RSA. Is it any way possible to setup some sort of a rule, if first RADIUS failed, try another one? Or direct people to different RADIUS servers based on their AD group membership?
If you bind multiple RADIUS policies to the same policy bank, it should try them in priority order until one succeeds. This is called cascade authentication.
Hello Carl,
I am currently having issues trying to use 2 Factor Authentication using SAML and also having a secondary LDAP policy for Receiver. I cannot use receiver because SAML uses Smart Card logon which prevents an LDAP profile from working when it hits the storefront. Do you have any advice?
Carl, we’re on a big push to move to PIV authentication and have configured the NetScaler and StoreFront for that successfully. A compliance part if this push is to have AD manage passwords for the user accounts.
As a backup for times when users forget or just don’t have PIV cards, I wanted to leverage RSA SecurID RADIUS as a secondary solution. We’ve used this for years in conjunction with LDAP for two factor authentication but I’d like to have just Username and RSA login fields at the Gateway and drop LDAP. This I’ve done but I can’t get authenticated to StoreFront from NetScaler without LDAP.
So I started down the path of Password Return for RADIUS to see if that would satisfy the StoreFront authentication requirements. I’m still trying to get this configured but do you know if this is possible with StoreFront? If so, what would I choose for “Logon Type” when configuring the NetScaler Gateway Appliance in StoreFront? (version 3.9)
If you want SSON to StoreFront but don’t have the user’s AD password, then you’ll need to implement Citrix Federated Authentication Service.
Or, you can configure StoreFront with disable SSON from NetScaler Gateway and instead prompt users for their Active Directory credentials. This would be in addition to the RSA authentication. https://support.citrix.com/article/CTX200066
For password return from RADIUS, you’d probably have to put the AD password in one of the Authentication Attributes and then use a Traffic Policy to use that attribute as the password field for SSON to StoreFront.
For Receiver, leave StoreFront set to Domain only. That basically means: only prompt for one password.
Hi Carl,
thanks for this document. Just a small question: Do you know why it’s not possible to use RADIUS as primary authentication for web and LDAP as secondery? That would avoid DDOS attacks, right?
Regards
Sandor
You certainly can. But users usually expect Password first. After reordering the authentication policies, you can edit the .js files to swap the Fields so password is first. Or use nFactor to swap them.
Many thanks for your fast reply Carl! I will test it out.
Regards:
Sandor
Hi Carl,
thanks for your quick support. Unfortunately after changing the auth order, Netscaler accepts RSA and Password, but after getting forwareded to Storefront Page we get the error: Cannot complete your request.
In the eventlog of SF i can find two entries:
– CitrixAGBasic single sign-on failed because the credentials failed verification with reason: Failed.
– A CitrixAGBasic Login request has failed.
Citrix.DeliveryServicesClients.Authentication.AG.AGAuthenticatorException, Citrix.DeliveryServicesClients.Authentication, Version=3.0.0.0, Culture=neutral, PublicKeyToken=null
Authenticate encountered an exception.
at Citrix.DeliveryServicesClients.Authentication.AG.AGAuthenticator.Authenticate(HttpRequestBase clientRequest, Boolean& passwordSupplied)
at Citrix.Web.AuthControllers.Controllers.GatewayAuthController.Login()
System.Net.WebException, System, Version=4.0.0.0, Culture=neutral, PublicKeyToken=a77b5c568549o089
The remote server returned an error: (403) Forbidden.
Url: https://127.0.0.1/Citrix/Authentication/CitrixAGBasic/Authenticate
ExceptionStatus: ProtocolError
ResponseStatus: Forbidden
at System.Net.HttpWebRequest.GetResponse()
at Citrix.DeliveryServicesClients.Utilities.HttpHelpers.ReceiveResponse(HttpWebRequest req)
at Citrix.DeliveryServicesClients.Authentication.TokenIssuingClient.RequestToken(String url, RequestToken requestToken, String primaryToken, String languages, CookieContainer cookieContainer, IEnumerable`1 acceptedResponseTypes, IDictionary`2 additionalHeaders)
at Citrix.DeliveryServicesClients.Authentication.AG.AGAuthenticator.Authenticate(HttpRequestBase clientRequest, Boolean& passwordSupplied)
Do you have any idea?
Regards
Sandor
In storefront console, right click your store, click manage receiver for web, click configure, click advanced, in the third row, change loopback to OnUsingHttp.
We are using 7.6 LTSR with SF 3.0.4000.1. So i think we have to check web.config.
But here i find:
So seems to be enabled already?
Sorry, this was missing:
communication attempts=”2″ timeout=”00:01:00″ loopback=”On loopbackPortUsingHttp=”80″
Hi Carl Stalhood
I’m doing RSA 2 factor authentication for multi domain. I can’t logon first factor Ldap only and Radius second
Do you have document guide or link configure ?
I need document guide for 2 factor multi-domain . Please send it me after you can
thanks you so much
nFactor can do LDAP first, and then RADIUS on a separate page. Is that what you’re asking?
I have done 2 factor RSA Authentication on Single domain ( domain HQ).
I have four domain name ( HQ, NORTH , SOUTH, MIDDLE ) in my production.
I have done 2 Factor in Single domain ( HQ), but I can’t setup 2 Factor with Multi Domain successfully
How to configure 2 Factor with multi domain ?
If you have resolved this problem , you send me some information and document guide to setup in multi-domain.
please help me to resolve this case now
Carl,
I have a customer that wants to use Duo with AD Groups. Only users in this AD group would get DUO. So instead of applying the policy to the Gateway vServer I was thinking of creating Session Policies and applying them to an AAA group. The problem I am seeing is its conflicting with other AAA groups when a user is part of multiple groups. Also how would Receiver work if we did it with this method (if its possible)?
To apply Duo to only specific AD groups, I suspect you’ll need nFactor.
For conflicting Session Policies, you’ll have to adjust the priority to what you want. I wonder if NetScaler 12’s Default Syntax for Session Policies can be used with HTTP.REQ.USER.IS_MEMBER_OF expressions.
Hi Carl,
great post, really helpful, i really like your blogs.
I just have a small question, did you ever noted or experienced that the auth.(approve over phone MS Authenticator) works only over WEB but not over the Citrix Receiver?
At the moment i have an issue, that i setup the account the receiver, im able to login, and a soon i approove the Token over my Phone, receiver try to connect to storfront, but at certain point i get the 3 Field auth and the Auth faild.
User
Passcode 1
Passcode 2
did you or some one have any idea/help?
I assume you followed the instructions to swap the fields?
I’m hoping that one of the days Citrix fixes Receiver so it behaves the same as web browsers.
Hi Carl
I’m trying to configure two-factor authentication in netscaler gateway .
I’m using freeradius and google authenticator.
I’m testing the freeradius+google authenticator using the radtest command
radtest rodrigo.brito@advrj.local 123456152087 localhost 0 testing123
User domain: rodrigo.brito@advrj.local
Domain Password:123456
Google token:152087
Bellow is the radius information
Received Access-Request packet from host 127.0.0.1 port 38368, id=82, length=95
(0) User-Name = ‘rodrigo.brito@advrj.local’
(0) User-Password = ‘123456152087’ ### domain password + Token ####
(0) NAS-IP-Address = 192.168.0.16
When I tried with NetScaler Gateway , the radius server reject the connection because only token is sent and not the password domain+token
see logs bellow
NAS-IP-Address = 192.168.0.10
User-Name = ‘rodrigo.brito@advrj.local’
User-Password = ‘006251’ ##### only token ##
Please, could you help?
Do you have an LDAP authentication policy set as well, I believe you need both LDAP and RADIUS policies to work. That’s how I have mine set up.
Hey Carl, we are using Ping MFA using radius. The Ping setup only requires user name and password. Not Passcode. I don’t want LDAP as a second factor because it seems pointless to put in the password twice . I would like to find a way to extract group information from the user ID but still only use Radius as bound to the vServer gateway.
You should be able to create an LDAP Policy/Sever with the Authentication checkbox unchecked. Then bind it to the Group Extraction bind point instead of Primary or Secondary. NFactor can also do it.
Thanks for your fast reply Carl. However, with Radius as primary and ldap as group extraction bound to my VPN vServer, it still fails to pull the group members from LDAP. Even with Authentication unchecked on my LDAP policy/server. The aaa debug shows it to be trying Radius for group extraction
/home/build/rs_111_51_11_RTM/usr.src/netscaler/aaad/radius_drv.c[2101]: process_radius extracted group string :(null)
Since my groups i need to use with AAA groups are defined in LDAP and not radius I need it to pull from LDAP but auth with Radius (Ping MFA). I’ll look into the nFactor option too.
“Bind the ldap policy as the secondary authentication”
https://discussions.citrix.com/topic/373144-netscaler-gateway-11-saml-group-extraction/
Hi Carl, I have a bit of an interesting requirement; i currently use a completely disparate MFA product from our hosted environment and a requirement to have different naming conventions between the AD and MFA. The original PoC did a redirect from the the vServer with the RADIUS policy to another vServer with an LDAP policy but that was deemed annoying.
what has been suggested is Username 1, Password 1, Username 2 and Password 2; username1 & Password 1 are LDAP binds and Username 2 & password 2 are RADIUS binds. Any thoughts on how this could be achieved?
Maybe nFactor with different login schemas for each factor?
Has someone tried SMS OTP with basic (401) authentication? I am getting troubles, the second 401 browser popup doesn’t appear, because NetScaler sends a 200-OK with message “sms otp is already sent”.
The application doesn’t allow the form based authentication.
I have setup my Netscaler to use OpenOTP (RCDevs) and it’s working fine. Recently they launched a OTP App with push functionality. I’ve got the Push functionality working on the OTP appliance. Has anybody integrated this in the Netscaler? (You enter your username and password, get a push message on your smartphone for the token code).
Do they have NetScaler specific instructions?
Does their product also handle Windows auth? Or is it OTP only? If OTP only, sometimes you have to hide the 2nd password field on NetScaler. If your product does both Windows and OTP, then you only need one auth server.
No Netscaler specific documentation. Have used your guides to get the normal OTP working. The OTP has a Windows AD interface. https://www.rcdevs.com/downloads/download/2/Radiusd/RadiusBridge_Manual.pdf/
Found the solution. Used the guide above. Normal OTP works. Force the OpenOTP to use LDAPOTP, otherwise it wil do only OTP. Fill in username + password + leave Code 2 or OTP field BLANK. Click logon and the push is send.
Hi Carl,
your post helped me a lot when needed most urgently! Thanks for that.
One more question:
How do I configure the text-box for the CITRIX Reciver logon box to display PASSCODE instead of Password 1 and Userpassword instead of Password 2?
cheers,
Stefan
My NetScaler Gateway Virtual Server pages have instructions for customizing the logon page labels. What version of NetScaler?
Hi Carl,
it is NS 11.1 50.10.nc
I was able to configure the Portal site for the Webbrowser but didn’t find the Settings for the Receiver
thanks
For Receiver, are you referring to after discovery? In that case, go to StoreFront > Manage NetScaler Gateways > edit the Gateway > change authentication to Domain and Security Token.
Otherwise, I don’t think the Receiver logon field names are customizable. There’s a razor file on StoreFront that can be changed but I’ve had difficulty after changing it.
I already made the settings in StoreFront.
On first attempt I only had 1 LDAP-policy and 1 RADIUS-policy for the virtual server.
At receiver logon I had USERID, Password and PASSCODE in this order. This didn’t work at all.
After applying your settings for LDAP/RADIUS policies in this very post and it works like a charm but now receiver logon displays USERID, PASSWORD 1, PASSWORD 2 where PASSWORD 1 is the TOKEN and PASSWORD 2 is the USERPASSWORD.
During Discovery, the fields should be correct.
After Discovery, it uses the Gateway configuration that came down from the StoreFront provisioning file. Are you maybe doing Single FQDN, and the Internal Beacon isn’t configured correctly, so it doesn’t use Gateway auth like it should?
You can change the logon properties of the page such as the labels for the page like Password 1 etc by editing the portal theme. You will need to create a custom Portal theme to edit it though.
Carl, This worked great with Entrust Identity Guard. One question, how do I get RADIUS logging/accounting enabled and configured on the Netscalers so I can do some much needed reporting. Thanks in advance
It was the cold boot that fixed my problem! Got the Netscaler working with OpenOTP. Thanks.
Hi Carl,
I’m having trouble with the authentication between Netscaler 11 and my Radius server. It seems to be a time setting but i can’t get my finger on the problem:
Log:
Oct 4 21:4403 192.168.1.123 10/04/2016:19:43:42 GMT NSGW 0-PPE-0 : default AAA Message 886 0 : “RADIUS auth: in process_radius: Authentication failed for user test from server 192.168.1.121 – Invalid Credentials”
192.168.1.123 = Netscaler appliance (NSGW)
192.168.1.121 = Radius server
Date on netscaler root:
TUE Oct 4 19:43:42 CEST 2016
If you run “date” on NetScaler, what time zone does it show?
When you change the time zone, you must do a “cold reboot” of the NetScaler. A warm reboot won’t copy the time zone file correctly.
Is your Syslog policy set to GMT instead of Local time?
I had a similar situation. We ran the “test Connection” on the Authentication RADIUS server and it informed us that the shared secret didn’t match the Radius server. We had to change to a simple password with no special characters to get them to work. Once that was configured everything worked.
Carl, do i need to install a radius server or do i have LDAP configured wrong on my netscaler, i continue to get this message with smart card logins. Thanks in advance
AAA LOGIN_FAILED 210 0 : User – Failure_reason “External authentication server denied access” – Browser WTOS/1.0
You can do “cat /tmp/aaad.debug” during login to see why the login is failing. I suspect that the certificate process is working but your LDAP might not be configured correctly.
Thanks again Carl, i ran that command and now it shows
ns_show_ldap_err_string LDAP error string: <>
s_ldap_check_result LDAP action failed (error 49): Invalid credentials
receive_ldap_user_bind_event Other invalid credentials: lctx->lflags = 00000000, lconf->flags = 00000004
Fri Aug 19 15:24:10 2016
/usr/home/build/rs_105_61_6_RTM/usr.src/netscaler/aaad/naaad.c[2263]: send_reject_with_code Rejecting with error code 4001
I could have many issues, do i have to create, change, or add a session policy in addition to the samaccount for smart cards?
This usually means the Bind account is invalid.
Or it extracted UPN from the certificate and you didn’t specify UPN as the logon attribute in LDAP.
OK, we may be getting close, I followed your guide of Netscaler gateway LDAP Authentication and verified the bind account can bind to ldap. I then scrolled down and found two ways to configure UPN, first i create a second ldap policy and used UPN in the server logon name attribute, do i fill in any other boxes in the other settings?
I now get this
receive_ldap_user_bind_event Other invalid credentials: lctx->lflags = 00000000, lconf->flags = 00000004
Fri Aug 19 16:24:37 2016
/usr/home/build/rs_105_61_6_RTM/usr.src/netscaler/aaad/naaad.c[2263]: send_reject_with_code Rejecting with error code 4001
Hi Carl…
Would like to know if its possible to use RADIUS as the only method of authentication with Citrix Netscalers for both Laptop/Desktop and mobile devices.
Note: We are planning to use PingID (Cloud Solution) as the Multifactor solution for Citrix Netscaler. Here I will be using the PingFederate (In-House) server to act as a RADIUS server. The PingFederate gets the RADIUS request and it forwards the same to the PingID for Second-Factor authentication. This is the reason as to why I would like to use the RADIUS as a single factor authentication.
Regards
Harish
If you are connecting to XenApp/XenDekstop, then ultimately, you must login to Windows, which is either password or certificate. Maybe Federated Authentication Services can handle the Windows authentication. Or maybe your RADIUS server can return the user’s AD password.
The RADIUS server can return the User’s AD password and we are using both XenDesktop/XenApp. So I would like to know on how do I proceed with the configuration.
Are you asking for the password return configuration? https://docs.citrix.com/en-us/netscaler-gateway/10-5/ng-configuration-mgmt-wrapper-con/ng-authen-authoriz-wrapper-con/ng-one-time-passwords-con/ng-password-return-sso-radius-tsk.html
Not sure. But I will look at this and let you know. I am new to Citrix Netscaler. I want users to authenticate using their username and password only. This authentication should go through the RADIUS instead of the LDAP. The second password / passcode option should not be visible to the users.
Then don’t bind the LDAP policy to the Gateway vServer. If the RADIUS password and the AD password are the same, then SSON to StoreFront should work. If they are different, then configure Password Return and NetScaler will use that password to SSON to StoreFront.
Perfect article, Carl !! You mentioning article CTX205907 – how to hide 2nd password field for Receiver 4.4; Any supported method to hide 2nd password field for Mobile Devices (iOS/Android)?
Great article! Saved me a lot of time!
Would this work for Web Interface as well for a site that’s setup to authenticate “Gateway Direct”
Yes.
“Gateway Direct” is how ICA is routed and has nothing to do with authentication.
When you create the Web Interface site, you’re asked where authentication is performed. You need to select “At Access Gateway”. If you didn’t do this, then you’ll have to delete the Web Interface site and re-create it.
Right, got it a little backwards. I’ve set this up with “At Access Gateway” as the authentication point with the authentication service URL pointing to https://gatewayfqdn:443/citrixauthservice/authservice.asmx. I’ve got the NetScaler LDAP and Radius polices in place and the RSA Radius Client and Agent setup on its portal. Since I’ve done this I can put in the user/pass/token and it authenticates but then dies at the web interface with a 401 – Unauthorized error. It works fine with out the RADIUS policies associated.
Not sure if I need to install the RSA Security Center on the Web Interface or not. I mostly wanted to make sure this was doable first and foremost before diving down a rabbit hole.
It should work. NetScaler should be sending the LDAP credentials to Web Interface.
What error are you seeing in Application Log in Event Viewer?
No errors are showing, I’ll make sure the policies are right and I didn’t mistype / attach them and see if that takes care of it.
Did you swap the the credentials so RADIUS is first? If RADIUS is first, make sure the session policy has Credential Index set to Secondary.
That’s pretty much exactly what it was! Thank you so much!
Hi Carl, thanks for your support, i done this implementation and all works well, ecept when the user lock the mobile device (ipda) and retry to reconnect the receiver prompt me only one password request and le login don’t works
thanks for your response
Carl,
New to NetScaler here. Can NetScalers and NetScaler Gateway be configured to where the Virtual instance that the users access (web portal) use multiple authentication methods such as:
If External users:
SmartCard
Radius
If Internal Users:
Smartcard
User ID Password
Also is there a way if this can be done the user has the ability to select which authentication method or if it does not detect Smartcard it goes to the other method?
Not in the current release. This can be done in AAA with nFactor but not on NetScaler Gateway.
For internal vs external, you can do split DNS. Or two Gateway vServers on the same VIP but with listener policies.
Thanks for the document Carl. Do you know if Netscaler keeps a log of all the authentication calls to RADIUS such as Azure. We had a user who was able to log onto Citrix without getting a phone call from Azure. There was no activity for this user at the time she logged on in Azure but we were able to see that she did log onto Citrix from the Windows Event Log. This is the only time its been reported to us that this has happened but it would be interesting to see if there was a log entry in Netscaler and a reason why this user was allowed to log on without two-factor authentication. We have not been able to reproduce.
Maybe in Syslog. Are you exporting Syslog to a remote Syslog server?
NetScaler 11 increases AAA logging. There’s an Authentication node where you can view the auth log.
Dear Carl,
I have implemented securenvoy to work with netscaler which is installed in different network.
I have Created Authontication Policy which is pointed to SecureEnvoy with this port 1812.
What is the communication port from securenvoy til Netscaler ?
Thank you in advance.
Regards,
Basem Shalabi
It should reply on whatever random port NetScaler uses for source port. This is no different than any other communication and your firewall should handle it automatically.
Thank you Carl for your response… I have an issue in Authontication part. It seems securenvoy does authonticate the user, i have this logs which i got it from wireshark also i saw goes from NSIP to securenvoy,
29245 11.862977010 172.20.21.86 10.200.230.15 RADIUS 114 Access-Reject(3) (id=82, l=20)
[truncated]Syslog message: LOCAL0.WARNING: 02/11/2016:14:43:19 GMT vpxgw 0-PPE-0 : AAA LOGIN_FAILED 555429 0 : User basemsh – Client_ip 62.92.69.221 – Failure_reason “External authentication server denied access” – Browser Mozilla/5.0.
Would you please advise.
Thank you for your cooperation.
Best Regards,
Basem
I can’t remember if the RADIUS monitor uses NSIP or not. But if you load balance locally then the RADIUS auth requests will definitely come from the SNIP.
Thank you Carl…
Carl, great post. Thank you for providing this. I have one question. Have you or know of anyone who has deployed MFA with the Symantec VIP solution. I am needing to obtain all the AD group information for the user once VIP authenticates them. VIP does not provide the group information to the netscaler.
thank you
Lorenzo
Not sure about VIP and Groups but you could always add an LDAP Directory just for Group Extraction.
Carl
I have a question for you. We are doing Displaying of Bookmarks based on AAA Groups linked to AD Groups. Want to use DUO/Radius Authentication only as Primary. No LDAP as doing both through DUO. Does not work out of the box. Thoughts on that?
Is your RADIUS server passing groups as RADIUS attributes? If so then you need to configure the RADIUS policy to use that attribute.
Citrix has a guide for integrating with Microsoft NPS that shows how RADIUS attributes are used for authorization.
Hi Carl,
I am facing the same issue of configuring a RADIUS attribute passed as response return list after a successful authentication from my RADIUS server. But, while debugging too, I could not find the returned attribute in Netscaler logs. If you could please guide me in configuring a returned RADIUS attribute, it would be great!
Thanks,
Vibhor
What RADIUS server/product? Different products have different configurations for including user groups in the RADIUS response. Then NetScaler can be configured to extra the RADIUS attribute that contains the groups. https://support.citrix.com/article/CTX222260 has NPS instructions.
Hi Carl,
I have found your articles very useful.
I am setting up multifactor radius auth on netscaler with safenet. The two servers are in the cloud.
Would it be better to setup a LB vip for these two servers, nat it at our firewall and add as a radius client ?
Atm I have both AG VIPs for Citrix storefronts Natted at the FW and the public IPs set as radius clients.
The RADIUS client IP will be SNIP or NSIP, depending on if load balancing or not. It won’t be the VIP. In a HA Pair, SNIP floats between the two appliances. NSIPs are unique to each node.
Excellent article – thankyou for posting.
Quick question regarding external RADIUS/Signify. Do you think its best to still create an Internal LB with the Primary / Secondary Signify Servers in the Service Group (using their external IPs) as you would with internal RSA servers?
This way the address going out the web is then the SNIP so you have a single source IP, also do you need to NAT you NS SNIP to a Public IP, or can you just specify the source address as the F/W address which would be the source of the traffic without the NAT? – this way irrespective of whether you use monitors/SNIP or MIP, or if you have a HA cluster, the source IP will remain the same?
I would probably load balance so single IP. You can use the default NAT if you’re willing at allow any internal IP to communicate with RADIUS. Or you can do a new NAT for the SNIP to restrict RADIUS to just the NetScaler.
Excellent, thanks Carl.
I have gone with the Single VIP (fronting two External Signify servers), with the Source IP being the f/w as the tier only has NetScalers within it, that way it will only be single source IP whether the monitors come from the BSD Kernel or not, and if the NetScalers failover.
Having a Single LB VIP for all RADIUS really simplifies the Profiles too, as you can have a single set rather that need different policies/profiles for each RADIUS server.
Thanks again, great Blog!!!
Hey there, Carl.
Thanks for all the great guides you’re writing, they’ve been a great help!
You have a small error though at the to. You wrote HTTP.REQ.HEADER instead of REQ.HTTP.HEADER.
You are correct. I must be spending too much time with the default syntax instead of classic syntax. 🙂
Hello Carl,
Its really a very helpful. I am new for AG and cant get understand where should need to put the rsa config file on netscaler? Please can you help me?
NetScaler doesn’t have native support for RSA so you must use RADIUS instead.
Hey Carl, love your work – it’s been a great help. I think I noted a typo in this one, where you have listed the auth policies for both browser and native connections under secondary you have listed LDAP for the browser which I think should be Radius.
It’s fixed now. Thanks for pointing it out.
Hi Carl, I need to send radius authentication to different radius servers based on users domain they select via drop down field.
Can I use the cookie CONTAINS “domain” like I’m using with the LDAP authentications?
That should work. Put the Cookie expression in in your RADIUS policy and it should only use the one that matches the cookie.