Navigation
💡 = Recently Updated
SmartAccess / SmartControl
SmartAccess and SmartControl let you change ICA connection behavior (e.g. disable client device mappings) based on how users connect. Decisions are based on NetScaler Gateway Virtual Server name, Session Policy name, and Endpoint Analysis scan success or failure.
SmartAccess can also control application/desktop icon visibility.
Prerequisites
Other than the NetScaler appliance license, both SmartAccess and SmartControl have the same prerequisites. You can configure SmartAccess in XenApp/XenDesktop at any time but it won’t work until you do the following:
- NetScaler appliance license – SmartAccess works with all editions of NetScaler appliances. However, SmartControl only works with NetScaler Platinum Edition.
- Gateway Universal licenses – Both SmartAccess and SmartControl require NetScaler Gateway Universal licenses. NetScaler 11.1 build 49 and newer come with a minimum of 500 Universal licenses so this might no longer be an issue. In 11.1 build 49 and newer, NetScaler Standard Edition comes with 500 licenses, NetScaler Enterprise Edition comes with 1,000 licenses, and NetScaler Platinum Edition comes with unlimited licenses.
- On the NetScaler, go to System > Licenses and make sure you have NetScaler Gateway Universal Licenses allocated to the appliance. The Universal licenses are allocated to the hostname of the appliance (click the gear icon), not the MAC address. In a High Availability pair, if each node has a different hostname then you can allocate the licenses to one hostname, then reallocate to the other hostname.
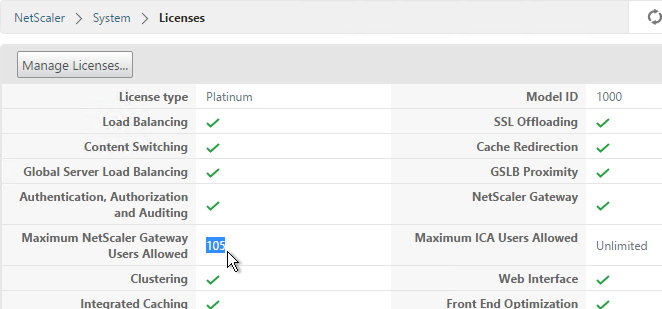
- After installing licenses, go to NetScaler Gateway > Global Settings.
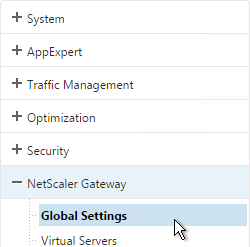
- On the top right, click Change authentication AAA settings.
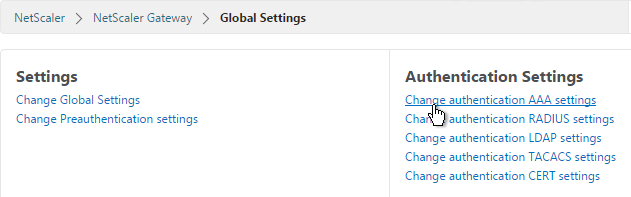
- At the top of the page, change the Maximum Number of Users to match your installed license count. Then click OK. This setting is commonly missed and if not configured it defaults to only 5 concurrent connections.
- On a XenApp/XenDesktop Controller, run PowerShell as Administrator.
- Run asnp citrix.* to load the snapins.
- Run Set-BrokerSite -TrustRequestsSentToTheXmlServicePort $true to enable Trust XML.
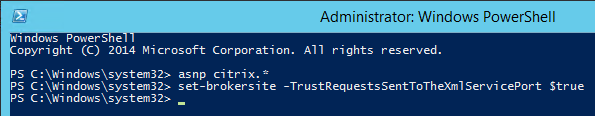
- In StoreFront Console, go to the NetScaler Gateway node and edit (Change General Settings) the existing Gateway object.
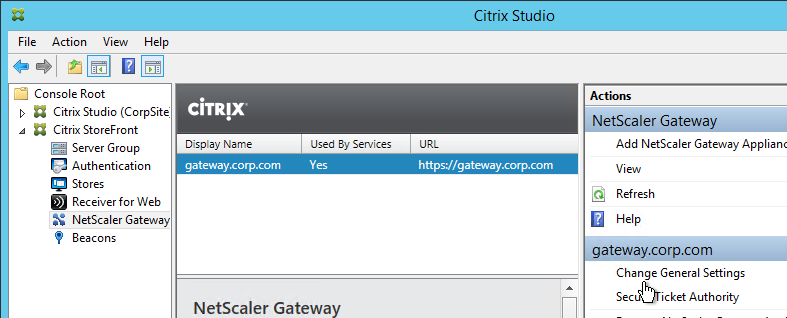
- Make sure a Callback URL is configured to resolve to a NetScaler Gateway VIP on the same appliance that authenticated the user. The Callback Gateway’s certificate must match the FQDN entered here. If you are configuring Single FQDN for internal and external then the Callback FQDN must be different than the Single FQDN.
- On the NetScaler, go to NetScaler Gateway > Virtual Servers and edit your Gateway Virtual Server.
- In the Basic Settings section, click the pencil icon.
- Click More.
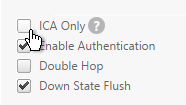
- Uncheck the box next to ICA Only and click OK. This tells NetScaler Gateway to start using Universal licenses and enables the SmartAccess and SmartControl features.
Once the prerequisites are in place, do the following as detailed below:
- Optionally, configure Endpoint Analysis.
- Configure either SmartControl or SmartAccess.
Endpoint Analysis
Endpoint Analysis scans are completely optional. You can configure SmartControl and SmartAccess without implementing any Endpoint Analysis.
Endpoint Analysis is supported on Windows and Mac devices. Other devices, like iOS and Android, do not support Endpoint Analysis. If you want to allow mobile device connectivity, then make sure you have an access mechanism (e.g. ICA Proxy) that works if the Endpoint Analysis scan fails.
There are two methods of Endpoint Analysis: pre-authentication and post-authentication. For pre-authentication, configure an Endpoint Analysis expression in a Preauthentication Policy. For post-authentication, configure the Endpoint Analysis expression on one or more Session Policies.
- With a Preauthentication Policy, if the Endpoint Analysis scan fails then users can’t login.
- With a Postauthentication Policy, Endpoint Analysis doesn’t run until after the user logs in. Typically, you create multiple Session Policies. One or more policies has Endpoint Analysis expressions. Leave one policy without an Endpoint Analysis expression so there’s a fallback in case the client device doesn’t support Endpoint Analysis (e.g. mobile devices). The name of the Session Policy is then used later in Citrix Policies and Citrix Delivery Groups.
NetScaler 11 has two Endpoint Analysis engines: the classic Client Security engine and the newer OPSWAT Advanced EPA engine.
To configure OPSWAT Advanced EPA expressions:
- When creating a Preauthentication Policy or Session Policy, click the OPSWAT EPA Editor link.
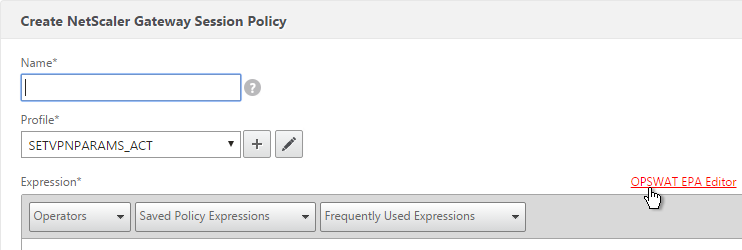
- Use the drop-down menus to select the scan criteria. Then click Done.
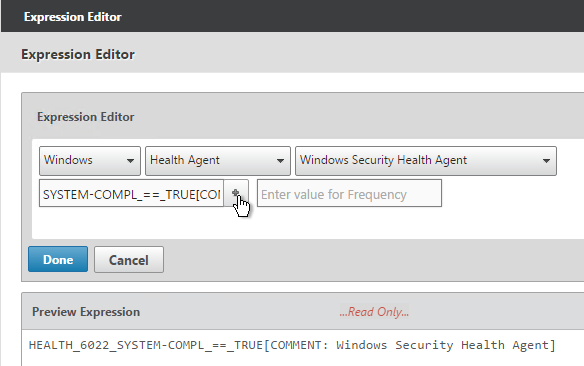
See the following links for more Advanced EPA information:
- Advanced Endpoint Analysis Policy Expression Reference at docs.citrix.com
- Citrix Blog Post Patch Management Endpoint Analysis on NetScaler Gateway
To configure Client Security expressions:
- When creating a Preauthentication Policy or Session Policy, click the Expression Editor link.
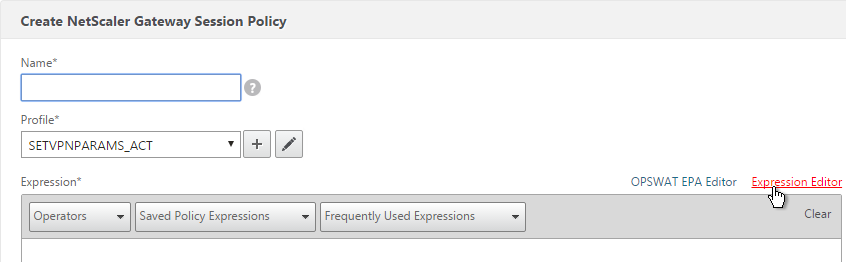
- Change the Expression Type to Client Security.
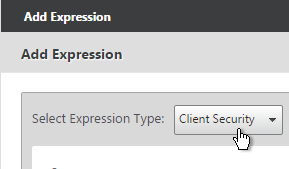
- Use the Component drop-down to select a component. A common configuration is to check for domain membership as detailed at CTX128040 How to Configure a Registry-Based Scan Expression to Look for Domain Membership.
- You can also use EPA expressions when configuring a Quarantine Group.
Once the Policies are created, bind them to your NetScaler Gateway Virtual Server:
- Edit a NetScaler Gateway Virtual Server.
- Scroll down to the Policies section and click the plus icon.

- Select either Preauthentication or Session and select the policy you already created. Then click Bind.
EPA Troubleshooting
Citrix CTX209148 Understanding/Configuring EPA Verbose Logging Feature: 💡
- Go to NetScaler Gateway > Global Settings.
- On the right, click Change Global Settings.
- On the Security tab, click Advanced Settings.
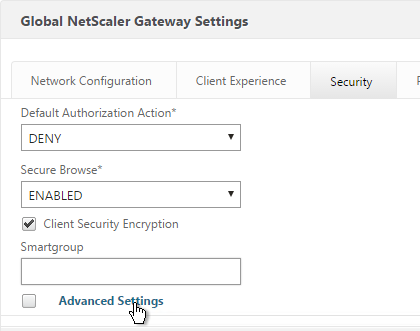
- Scroll down, check the box next to Enable Client Security Logging, and click OK.
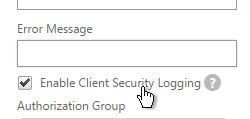
- When the scan fails, the user is presented with a Case ID.
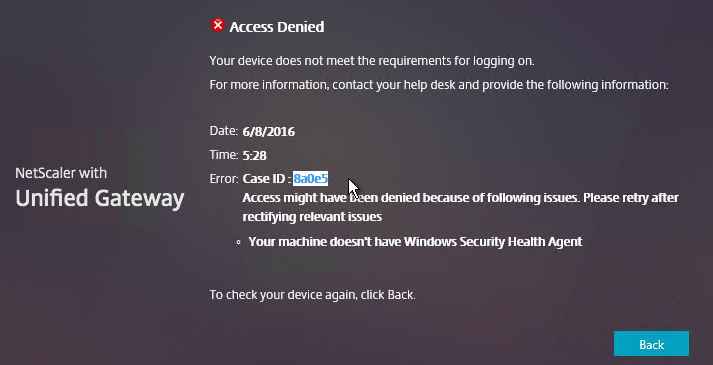
- You can then grep
/var/log/ns.logfor the Case ID. Or search your syslog.
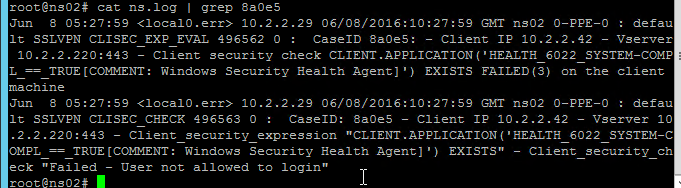
To determine why your EPA scans fail, on the client machine, go to HKEY_LOCAL_MACHINE\SOFTWARE\Citrix\Secure Access Client.
Make a DWORD value named “EnableEPALogging” and set the value to 1.
After attempting the scan again, you’ll find the file %localappdata%\Citrix\AGEE\epaHelper_epa_plugin.txt with details for each scan expression.
NetscalerAssasin EPA OPSWAT Packet flow and Troubleshooting shows a Wireshark trace of an EPA scan.
SmartControl
NetScaler 11.0 has a new SmartControl feature, where you can configure some of the SmartAccess functionality directly on the appliance. See Configuring SmartControl at docs.citrix.com for detailed instructions.
- If you are using a Preauthentication Policy to run an Endpoint Analysis scan, edit the Preauth profile.
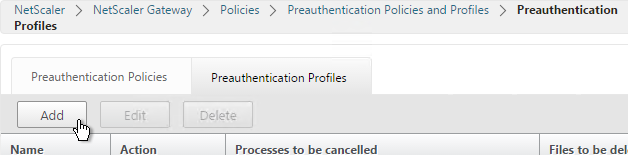
- Configure the Default EPA Group with a new group name. You’ll use this group name later.
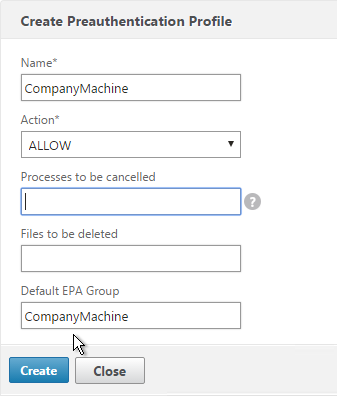
- If you are instead using a Session Policy/Profile to run the post-authentication Endpoint Analysis scan, on the Security tab, use the Smartgroup field to define a group name for users that pass the scan. You’ll use this group name later.
- On the left, expand NetScaler Gateway, expand Policies, and click ICA.
- On the right, switch to the Access Profiles tab and click Add.
- Configure the restrictions as desired and click OK.
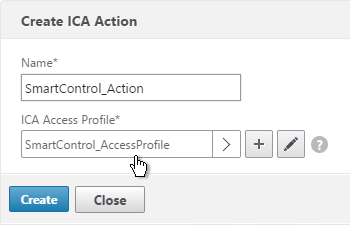
- Switch to the ICA Action tab and click Add.
- Give the Action a name and select the Access Profile. Click Create.
- Switch to the ICA Policies tab and click Add.
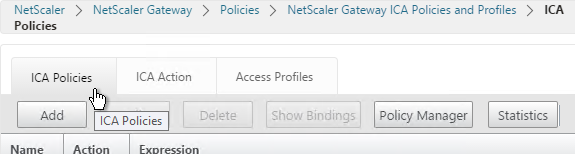
- Select the previously created ICA Action.
- Enter an expression. You can use REQ.USER.IS_MEMBER_OF(“MyGroup”) where MyGroup is the name of the SmartGroup you configured in the session profile or preauth scan. Click Create when done.
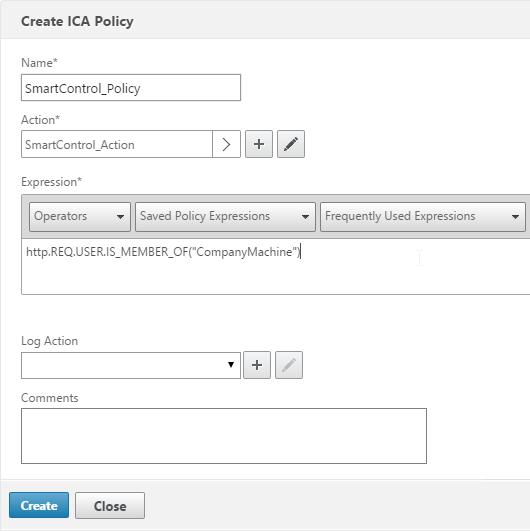
- Edit your Gateway Virtual Server.
- Scroll down to the Policies section and click the plus icon.

- Change the Policy Type to ICA and click Continue.
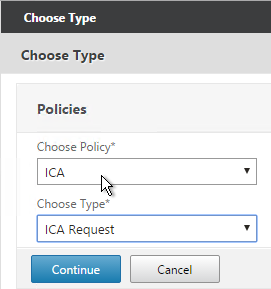
- Select the SmartControl policy you created earlier and click Bind.
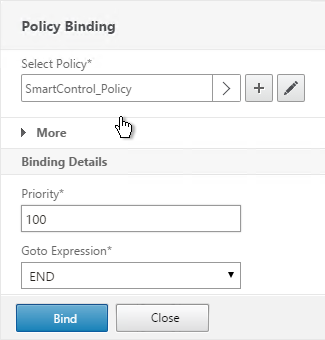
SmartAccess
CTX138110 How to Configure the SmartAccess feature on Access Gateway Enterprise Edition Appliance
In XenApp/XenDesktop, edit a Citrix policy and add the Access Control filter. If you are using GPO to deliver Citrix Policies, then only Citrix Policies in the user half of the GPO support Access Control filters.
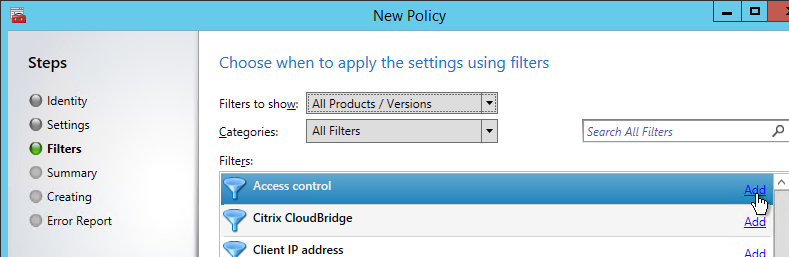
You can leave the default wildcards for farm name and condition to match all NetScaler Gateway connections. Or you can match specific NetScaler Gateway / Session Policy connections:
- AG farm name = name of the NetScaler Gateway Virtual Server.
- Access condition = name of the NetScaler Gateway Session Policy.
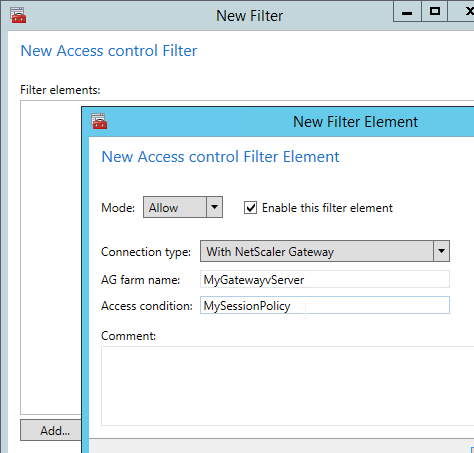
You typically create a Citrix policy to turn off all client device mappings for all external users. Then you create a higher priority Citrix policy that re-enables client device mappings for those users that passed the Endpoint Analysis scan expression on a particular Session Policy.
If you edit a Delivery Group, there’s an Access Policy page where you can hide or show the Delivery Group for all NetScaler Gateway connections or for specific NetScaler Gateway Virtual Server / Session Policy connections.
- Farm name = NetScaler Gateway Virtual Server name
- Filter = NetScaler Gateway Session Policy name
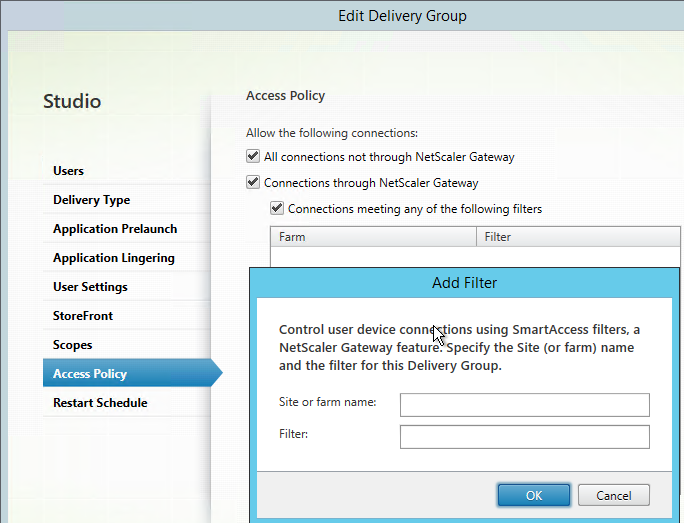
This configuration is only available at the entire Delivery Group. It is not possible to perform this configuration for only specific published applications unless they are on different Delivery Groups.
Hi Carl,
I have task to make access filtering by Source Network to specific Delivery Group (VDI machines).
It must be accessible only from local network. I feel SmartAccess is what I need, but cannot catch how it should be configure. Could you push me to right direction? 🙂
Currently I can access VDI desktops either from Internet or from LAN.
ICA access profile is looks like only about enabling features like printers etc? Can it be used to fully deny access and hide VDI icon from list in Workspace when connect form Internet?
Also at licenseng page I see “Maximum Citrix Gateway Users Allowed:1000”, but when I try to create Create ICA Access Profile I get error “Geature is not licensed”, which license do I need? My license type is Enterprise.
vServer is in ICA only mode..
Thakns in advance!
Do the users on the Source Network use a Citrix Gateway?
If not, then in powershell on delivery controller run “get-brokeraccesspolicyrule”. There’s a field for included client ips filtering.
Unfortunately, we use Citrix Gateway when connecting from local network. Do not have direct access by security policy. So have to manage access somehow on Gateway depending on source IP.
For Gateway, create a Session Policy with a blank Session Profile. The Policy expression would be something like CLIENT.IP.SRC.IN_SUBNET(x.x.x.x/24). Bind it to the Gateway.
In your Delivery Group, on the Access Policy tab, uncheck the top box. Click Add. Enter * for the Site/farm name, and in the Filter field enter the case sensitive name of your Session Policy.
Hi Carl: Great article. Please clarify… are the trust XML and callback steps needed for Smart Control or just for Smart Access? For Smart Control, I have set up an ICA policy and have bound it to my VPN server. I am platinum and not ICA only… Even if the policy is set to “TRUE,” it takes no hits and the solution does not work.
Firmware 11.0 68.12
License at default of 5 as this is dev.
Thanks in advance.
ICA Only definitely needs to be unchecked.
Regarding callback and trust xml, now that I think about it, I’m not sure. I should test that. Also see https://docs.citrix.com/en-us/netscaler-gateway/12/integrate-web-interface-apps/smart-control.html
Thanks for the quick response. i’ll try callback, though not feasible for Production, but I have no access to controllers to check XML, trust. Regarding Citrix docs… Read that. Their documentation quality is one of the many reasons for your popularity 🙂
It would appear I had a live ICA session, which is why the ICA policy was not taking hits. The policy takes hits on new connections only. Works fine. For the record, neither callback nor trust XML setting is required for Smart Control.
Regards
hi Carl, We have set up ICA policies for Permitting Clipboard and Permitting Printers on the Netscaler, but appears that in order for it to work we have to create a combined profile which enables both settings. There are some users who require both but a large proportion only need 1 or the other. Creating seperate profiles has not worked. 1 seems to filter out the other. Are there any other options for this other than creating an entirely new AD group for both actions ?
thanks in advance.
Hi Carl, I have a requirement to limit access to an application on a Citrix shared desktop based on membership of an AD group due to licensing of the application.
We have a perimeter Netscaler 5500 with Enterprise licensing on it, running a Citrix Gateway and an internal Netscaler load balancing the citrix farm.
If a user connects from outside the network and they are a member of a disallowed group they will be shown only a shared desktop without the application installed. If they are on the internal network and using the same URL (we are using split DNS) they will be allowed to get to a shared desktop with the application on it. Could you suggest a way of setting this up?
You might have to do two different Delivery Groups – one with app, one without. Then you can use SmartAccess (Edit Delivery Group > Access Policy) to identify if the user is connecting through Gateway or not. However, I think the Access Policy can allow (whitelist), but can’t deny. So you’d to put the allowed users in an allowed group instead of using a prohibited group.
Create a AAA Group on NetScaler for the allowed users. Bind a session policy for the allowed users. In the Delivery Group > Access Policy, specify the session policy name for allowed users.
Thanks for the quick reply I will have a look at this tomorrow.
Here’s our situation, we have a XenApp 6.5 Published Application that is published to everyone in the organization. In order to deliver better performance for our VDI users, we have XenDesktop 7.6 published desktops assigned to users with the same application installed locally on the image. The problem we are facing is getting users to use the locally installed application icon and not the XenApp 6.5 published application icon. How can I use SmartFilters to block the application from being published on the desktop of the XD 7.6? The goal is to have the users launch their XenDesktop 7.6 desktop and only have the locally installed application icon. But, if they use/logon to a workstation in the organization still have access to the XenApp 6.5 published application through normal PNAgent app enumeration from the Citrix Receiver. Thank you.
Are you saying that you have both a published app icon and a real icon on the same machine and you want to default to the real icon? In that case, use KEYWORDS:prefer in your published app description. My Receiver article details that keyword.
Or do you want to hide the published app icon from inside the published desktop? In that case, create a new StoreFront store and configure icon hiding on that store. Then point the published desktop Receiver to the new store.
Yes to both questions, we have both a published app icon and locally installed icon on the same published desktop and we’d only like the real (locally installed on image) to appear. If possible, we’d like a way to hide the published app on the published desktop but not affect users who use the same published app outside of the published desktop. Currently, the specific published app uses KEYWORDS:Mandatory so that it shows up in the users Favorites tab by default on StoreFront. For the second option, how do you configure icon hiding on a store in storefront? Thank you.
See https://www.citrix.com/blogs/2014/03/27/hiding-applications-in-citrix-storefront/
We wanted to try KEYWORDS:Prefer=”\Program Files\AppName\” to use the locally installed version of the app. The problem is the published app is installed on Server 2008 R2 64 bit, the published Desktop is 32 bit Windows 7 with the same application installed. So the paths don’t match because of Program Files vs Program Files (x86), is there a way to fix that?
Carl,
When setting up smart access. We have a netscaler vpx standard 11.1.47. if you just set up policy in studio to say when coming in on netscaler and leave it as wildcards. Will it still work? Do u have to set policies on the netscaler?
The prerequisites need to be completed. ICA Only unchecked. Callback URL configured. Then you can adjust the Delivery Group to show or hide apps through any Gateway.
Hi Carl,
I assume SmartAccess can not be used with Netscaler Gateway Enterprise licenses.
That license seems to be limited to Gateway functionality only, correct?
You are referring there to the Netscaler Standard, Enterprise and Platinum licenses, correct?
I have a Netscaler Gateway Enterprise license installed on an appliance running v11.1 Build 51.26 and there are still only 5 Netscaler Gateway users allowed. Or do I have to reissue/recreate the license at Citrix.com to activate those additional Netscaler Gateway User licenses?
You can purchase Gateway Universal licenses for around $5 per user. Or you might already own them through XenMobile Enterprise or XenDesktop Platinum. But yes, only NetScaler Standard and higher have built-in licenses.
Dear Carl, thanks always for your helpful articles. We are interested in enabling EPA Scan feature on NetScaler VPX 1000 and have Enterprise Platform license. We have 11.0 version.. Do we need CCU license for EPA or Platform license will give us the ability for enabling EPA Scan ?
Carl… long time fan…. i dont post much but i have been looking around and there little documentation from Citrix that show me how to configure POST-AUTH Session policy. the one you have above is very useful but it uses smart control. im trying to avoid smart access/smart control since i need a callback URL and that posses more complications in the GSLB env i have today. Any suggestions on the POST Auth EPA via Session policy WITH smart access/ smart control ?
Are you asking how to add SmartAccess headers to StoreFront requests without requiring a callback?
nope. i am looking to do Post Auth EPA scans. can that be accomplished with out smart access. i’m looking to scan the BYOD devices for certain security policies, if fails i have a QUarantine group, but it seems even if you are suppose to fail the scans, the current policy just logs you in anyways. how can i implement POST AUTH EPA Without SmartAccess or SmartControl
Preauth scan can prevent login
Postauth is assigned to the Session Policy expression, which means you can have different session policies apply depending on the results of the EPA scan. For example, if EPA scan passes, session policy points you to a portal page. You can have a session policy without a EPA scan expression that takes you to an error page.
Hey Carl! 11.0 53.23 NS here. Smart Control only configured. 6.5 works however 7.x does not. Have you see this? I am just blocking client drives.
Did you enable TrustXML from PowerShell?
Yes.
If you think everything is configured correctly, then you might have to call Citrix Support.
Great article as usual, Carl. One point I had to learn lately “in the field”: in order to use SmartControl (disable ICA functionality by the NetScaler and NOT Citrix policies mapped by SmartAccess), you need to have NetScaler Platinum Edition license. I found it only in the NetScaler feature matrix. Citrix eDocs still is lacking the important part of information …
Regards,
Jochen.
Thanks for this. I just added a note about the Platinum license requirement.
Great article, thank you.
I configured a policy in our environment to not create client printers for remote connections. It works just fine on our internal NetScaler but as soon as I change the filter to the external gateway VIP name, it stops working (allows local printer creation).
The external NetScaler is in our DMZ; does the XML port need to be open from the Gateway VIP to the DDC’s?
Thanks again.
Did you configure all of the SmartAccess prerequisites: Gateway licenses, no ICA Only, Trust XML, callback URL, etc.?
If you add multiple filter types to a policy, I think it is AND, not OR.
I’ve been reading a lot more and I think it is because of our authentication policy. We are using a SAML authentication policy at the Gateway with a redirection URL (secureauth). It’s an older product and doesn’t pass authentication through to StoreFront after the two factor authentication is completed. This means that Passthrough from NetScaler Gateway is turned off on the receiver for web site and it never uses the call back URL. The users are always presented with two authentication prompts; one at the gateway and one at StoreFront.
I don’t think it will work with just a simple XD policy.
I am setting up a NetScaler ICA policy now in QA to test. More
Or you can implement Citrix Federated Authentication Services.
That’s the plan… eventually. Big ship. Small rudder.
Thanks for the replies.
Good morning Carl,
I have a customer who needs to control access to his environment to only his thin client devices (HP with Linux), as he is delivering their desktops via internet access but do not want their users to access it from anywhere else. What are your recommendations in this scenario?
Thank you and your blog is awesome! 🙂
Non-Windows Thin Clients would fail any EPA scan.
You might be able to use User-Agent Header to control access, but be aware that User-Agent is easy to change by the user.
Thank you!
Sorry for my lack of knowledge, but the user-agent header that I know of is “receiver or not receiver”, is there a way to input the type of receiver as in Receiver for linux?
You’ll have to do some network traces or look in web server logs to see what user-agent the machines are using.
Thank you again, will do!
Perfect- Thank you, Carl!
Carl –
My situation: Were using the same URL for internal and external NSGW VIP’s in the environment. We need to implement Smart Access (NS version 11.0 66.11.nc) so that we can limit connectivity to specified domain names.
Question: In Step 9 under “Prerequisites” you state “If you are configuring Single FQDN for internal and external then the Callback FQDN must be different than the Single FQDN.”. Does the different FQDN need to be registered somewhere (DNS), to those NSGW VIP’s? Or can you just make something up and place it in the Netscaler Gateway Config on the Storefront servers?
The callback is from StoreFront to Gateway. You can edit HOSTS file on StoreFront. Make sure the Gateway certificate matches the DNS name.
Thank you, Carl-
So, if our internal and external NSGW URL is “https://LetMeIn.com” (IP: 123.456.789.123) and I wanted to make my call back URL “https://LetMeInCB.com”, I could place a host file entry on my Storefront box that looks like this: https://LetMeInCB.com = 123.456.789.123 ?
Is that what you’re saying on the first portion of your response?
When you say “Gateway Certificate” are you referring to the Wildcard cert on the Netscalers?
To further clarify: The Netscalers are currently working, we just want to add the “Endpoint Analysis” piece to check for Domain.
If your Callback Gateway certificate is a wildcard, then it should match the new FQDN you make up for the callback.
Are you saying I should have 2 certs on the Netscaler or replace the current Wildcard?
Wildcard: https://LetMeIn.com
Callback Gateway Cert: https://LetMeInCB.com
All that matters is that your Callback FQDN resolve to a Gateway VIP and the certificate on that Gateway matches whatever FQDN you’re using.
Hi Carl, we’re currently working on trying to allow local printer pass through for one of my employers subsidiaries. We only want to allow the the client creation of printers if they are connecting from specific public IP’s (work offices). I can see how we could apply the policy based on NetScaler Access Policies, but I am not sure about the NetScaler end of things. Would EPA be the way to accomplish this? I do not have a lot of NetScaler experience, but I am working with our Network engineering team to see if we can pull this off. Thanks in advance, you are the best and have helped me get through a lot of issues in our Citrix 7.6 deployment.
You might be able to create an ICA Policy (Smart Control) on the NetScaler that disables client printing. The Policy expression would be client.IP.SRC.EQ(12.1.1.1).NOT or something like that. Or you can create two policies, one that disables printing and one that leaves it the default. Then bind both policies to the Gateway but in the correct priority order.
Thanks Carl! I am Sorry I am just getting back to you, I was on PTO and it has been a whirlwind!. We are going to give that a shot and see how it goes. Right now we’re just researching to confirm that the client.IP.SRC will return the public IP of the client and not the endpoint IP (local address) of the client. I’m thinking it will work as expected, otherwise this is no different than setting a security policy within Citrix Studio based on IP (which can only check the endpoint IP).
NetScaler sees the outer IP. The local client IP is embedded in ICA and not sure NetScaler can see that like the VDAs can.
That answers that for me! Thank you! I am not sure when we will implement the solution, but I will definitely write back and let you and everyone know how it goes.
Hi Carl,
You mention setting ICA Only to be false, switches the NetScaler to use Universal licenses. Currently, we have an Enterprise license, which has unlimited ICA connections, but only 5 “SSL VPN” licenses, and we’re looking at using SmartAccess. However, if we untick ICA Only, does that mean that we have to upgrade the license to allow for all our users, even if the majority purely use ICA?
Also, thanks for your blog, it’s been a lifesaver many times!
Cheers
Yes, Gateway Universal licenses are required for SmartAccess. If you have XA/XD Platinum then you already have the licenses. You can also buy them “a la carte”.
Hi Carl
Thanks again for the the details.
We have Netscaler 10.5, Standard Platform license and Universal Gateway license. Can we have Smart Access/Control feature there?
Yes, but only up to the number of Universal Gateway licenses.
Hi Carl,
great Article.
We configured SmartAccess with post-authentication EPA through Session Policy. EPA is working, but the correspondingly Citrix Policy is not working. We’re using Netscaler 11 and XenApp 6.5. Any idea why this is not working or where to find helpful log files? Thank you
Syslog should should you the failed scan. On the client side there’s nsepa.txt file in C:\ProgramData.
Hi Carl the scan is not the problem. This is working as expected. Depending on the result of the epa scan, another session policy is applied. And a citrix policy (example: drive mapping not allowed) is linked with the session policy. And this “link” is not working, and so the citrix policy is not applied.
So SmartAccess is not working. This is usually because Callback is not configured in StoreFront, or XML Trust is not enabled in the farm Site Settings. You might have to run CDF Trace on StoreFront and/or the Controller to troubleshoot the issue.
Carl, we use NetScaler 11 to make a endpoint analysis to check if a domain member or not. In our environment, NetScaler deploy in two-arm-mode, so we have two AGVS and AG-Callback VS. when configure by your step, I find that the end device which in our domain cannot get XenDesktop resource. Can you tell me how to cause it. many thanks.
Is the EPA scan failing?
Is it not working for anybody? If so, you might have to a Citrix Partner or Citrix Support to review your configuration.
BTW, we use post-authentication.
Dear Carl, thanks for your help! We have successfully build endpoint analysis environment. When some login to NetScaler Gateway, if Sales’s device is not a domain member, he cannot get his resource. But another question, by customer requirements, when Executive&Administrative login, whatever his device is a domain member or not, he will obtain his VDI resource. As you know, all the Roles are using hosted shared desktop from ONE delivery group, so we cannot use Policy Access in delivery group to classify different roles that who can get resource or cannot get resource by SmartAccess. So, could you please tell me how to achieve our customer’s requirements by NetScaler or other useful ways?
SmartAccess is only configurable at the Delivery Group level. Do you want it for each published desktop?