Navigation
Workspace app is the new name for Receiver. This post applies to all Workspace app versions, including the Current Release version 2409.10 and the LTSR version 2402 CU3.
- Change Log
- Workspace app versions
- Overview
- Uninstall Old Workspace app Clients
- Installation and Configuration
- Workspace app ADMX GPO Template
- Pass-through Authentication
- Automatically add StoreFront Accounts to Workspace app
- Control Shortcut placement on Desktop and Start Menu – and Workspace Control (Session Reconnect)
- Enable Prelaunch
- Control Device Mapping Prompts
- Desktop Lock
- Use Studio to configure Workspace app Accounts in Published Desktop
- Published Desktop – configure Workspace app to place shortcuts
- Script / Automate Workspace app Self-Service
- Microsoft Teams
- Troubleshoot:
💡 = Recently Updated
Change Log
- 2025 Jan 16 – updated article for Workspace app 2409.10
- 2025 April 2 – Versions – updated for Workspace app 2402 LTSR Cumulative Update 3
- GPO Settings – SSO in Win11 24H2 requires Enable MPR notifications for the System; Desktop Viewer Toolbar Options
- Registry Values – Remember USB connections
- 2023 Nov 15 – Global App Configuration Service is now available to all on-premises customers even if no Citrix Cloud entitlement.
- 2023 May 4 – Pass-through Authentication – added GPO setting Enable MPR notifications for the System
- 2023 Mar 22 – updated article for Workspace app 2303; anti-dll injection GPO setting
- 2022 Dec 19 – updated article for Workspace app 2212; app protection GPO setting
- 2022 Nov 4 – Versions – updated for Workspace app 1912 LTSR Cumulative Update 7 Hotfix 2
Workspace app Versions
Citrix Workspace app uses a YYMM (year/month) versioning format, of which version 2409.10 (24.9.10.28) is the newest Current Release. See Citrix Docs for the list of new features, some of which only apply to Citrix Cloud.
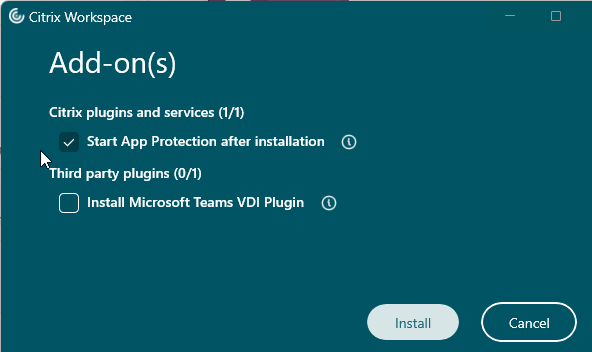
Workspace app 2311 and newer have a new installer interface.
Workspace app 2303 and newer automatically install the App protection components with an option to start them after installation. Older Workspace apps have an option to install App protection and if you don’t select this and later want App protection then you must uninstall Workspace app and reinstall it.
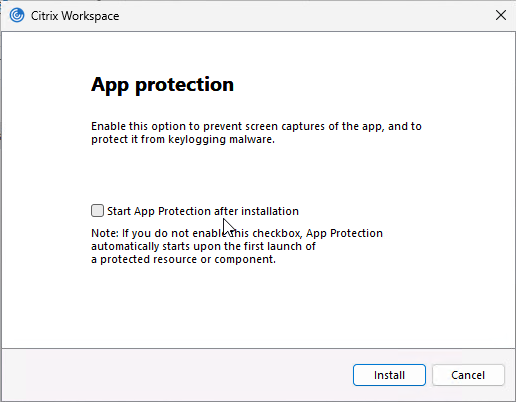
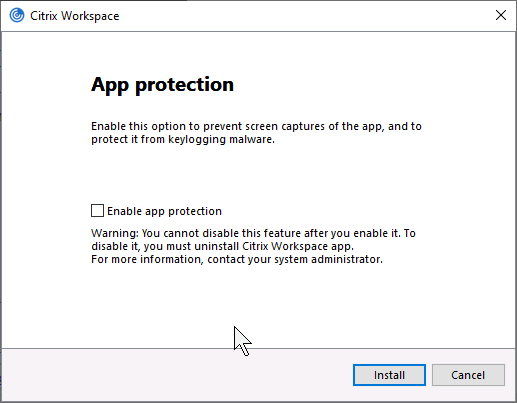
- See App Protection at Citrix Docs to enable App protection for the authentication screen. Workspace app 2305.1 and newer automatically start it for authentication if you have selected the Start App Protection check box during installation.
The newest Current Release version of Workspace app is version 2409.10.
The newest LTSR (Long Term Service Release) version of Workspace app is version 2402 Cumulative Update 3.
Workspace app Modules
The Workspace app installer deploys multiple modules. Here are the important ones:
- ICA Engine (wfica.exe) – process that uses the ICA protocol to connect to published apps and desktops.
- Self-Service (selfservice.exe) – gets icons from StoreFront and displays them in a Window. When an icon is clicked, Self-service passes the ICA file to the ICA Engine to establish a connection.
- Single Sign-on (SSON) for ICA (ssonsvr.exe) – captures user credentials and submits them to VDAs after an ICA connection is established
- Workspace Auto-Update (CitrixReceiverUpdater.exe) – Notifies users of Workspace app updates. The most recent name for this component is Citrix Workspace Update.
Custom ICA files are no longer supported. However, Ryan Butler has created a script that asks StoreFront for an ICA file. Explicit credentials are supported. Find the script at Github.
Workspace app Discovery and Beacon Process
If you are using Workspace app’s built-in user interface (instead of a web browser), then Workspace app first prompts you to perform discovery, which is also called Add Account.
Workspace app will contact the FQDN and request download of the StoreFront Provisioning File.
- If you entered a StoreFront FQDN, then Workspace app will download the Provisioning File directly from the StoreFront server.
- If you entered a Gateway FQDN, then Gateway will first prompt the user to authenticate. After authentication, Gateway will connect to its configured Account Services address, and download the Provisioning File from StoreFront. The Account Services address is configured in the NetScaler Gateway Session Profile on the Published Applications tab.
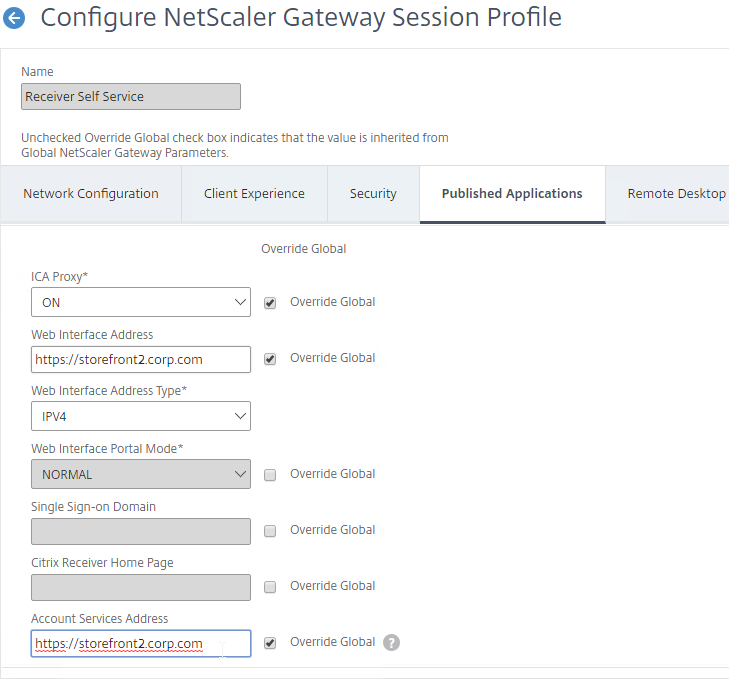
If your StoreFront server is configured with multiple stores, then the user will be prompted to select a store. Unfortunately, there’s no configuration option in NetScaler Gateway to force a particular store.
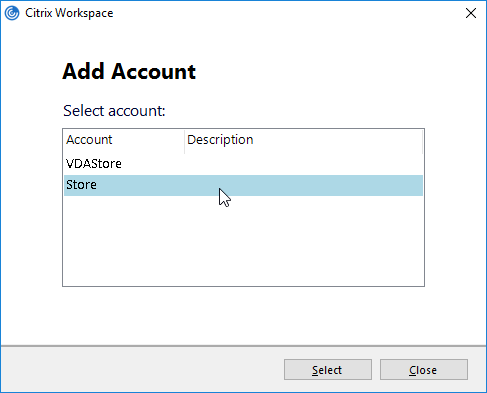
- One workaround is to hide the store that you don’t want visible externally. See How to configure Receiver to a Store that is not advertised for special syntax.
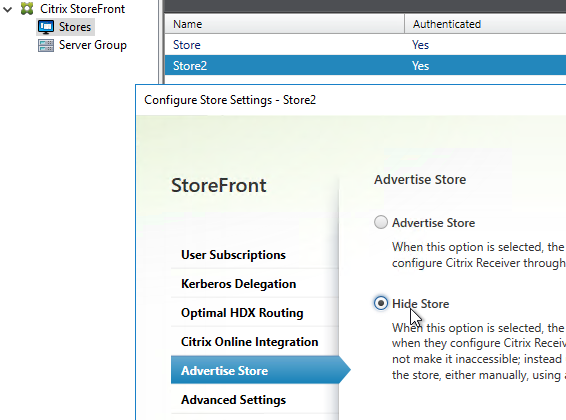
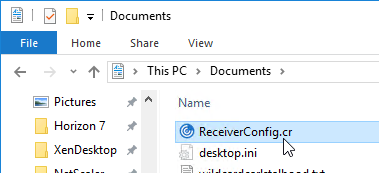
The Provisioning File downloaded from StoreFront is an XML document containing values for several items configured in the StoreFront console. You can export the Provisioning File from the StoreFront console by right-clicking a Store.
The ReceiverConfig.cr Provisioning File looks something like this:
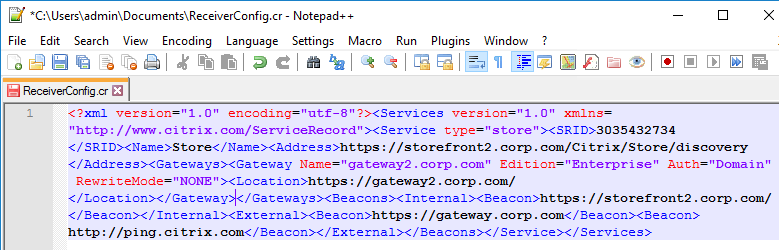
Here are the values in the Provisioning File:
- Address – the Base URL configured in StoreFront Console
- Internal Beacon – as configured in StoreFront Console. This can be the Base URL, or a manually specified URL.
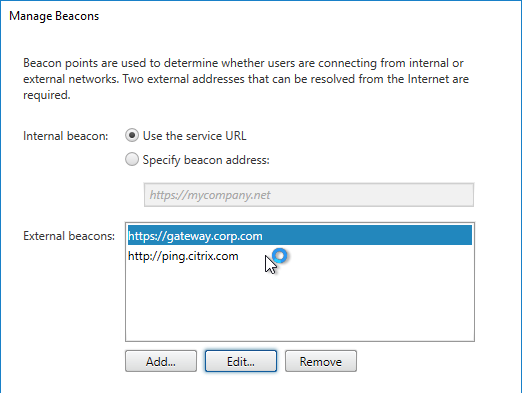
- External Beacons – as configured in StoreFront Console
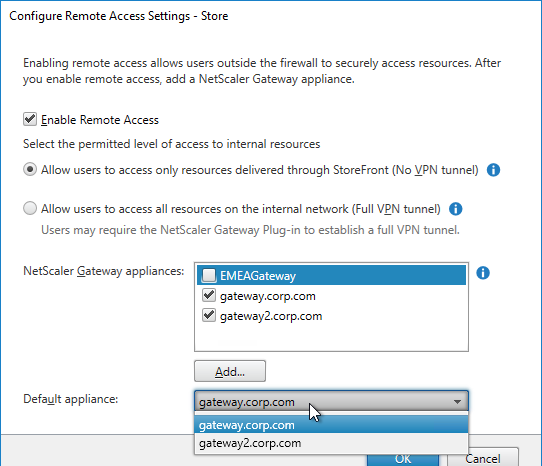
- Gateways – as configured in StoreFront Console. If there are multiple Gateways, when enabling Remote Access on the Store, then only one Gateway is selected as Default
- SRID – Store ID. An important value to consider for multi-datacenter configurations. The SRID is set when the Store is created. It can also be changed by editing C:\inetpub\wwwroot\Citrix\Roaming\web.config.
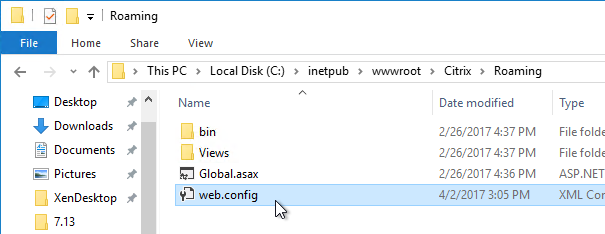
Workspace app reads the Provisioning File, and configures itself by inserting the file’s contents into the user’s registry. The values are located under HKCU\Software\Citrix\Dazzle\Sites and HKCU\Software\Citrix\Receiver\SR. If you performed discovery through NetScaler Gateway, notice that the internal Base URL is added to the user’s registry.
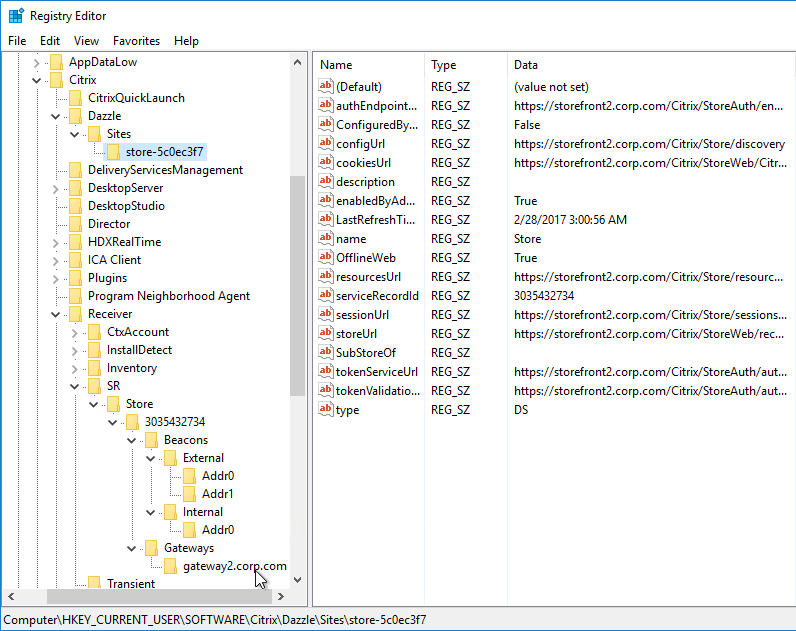
Once Workspace app is configured, it then performs the following steps:
- Attempt to connect to the Internal Beacon.
- If the Internal Beacon is reachable, connect directly to the StoreFront Base URL (Address).
- If the Internal Beacon is not reachable:
- Attempt to connect to the External Beacons. If the External Beacons are not reachable, then stop attempting to connect.
- Connect to the Gateway address configured in the Provisioning File. If there is more than one Gateway, connect to the Gateway that is marked as the Default.
Here are some interesting notes on this connection process:
- The FQDN you entered during Discovery has absolutely nothing to do with how Workspace app connects to StoreFront or Gateway. The actual connection process is controlled by the contents of the Provisioning File, not the Discovery address.
- If the Provisioning File has multiple Gateways defined, Workspace app uses whichever Gateway is marked as Default. Workspace app completely ignores whatever Gateway FQDN you entered during Discovery. To use a non-default Gateway, the user must manually select the other Gateway in Workspace app’s Advanced Preferences.
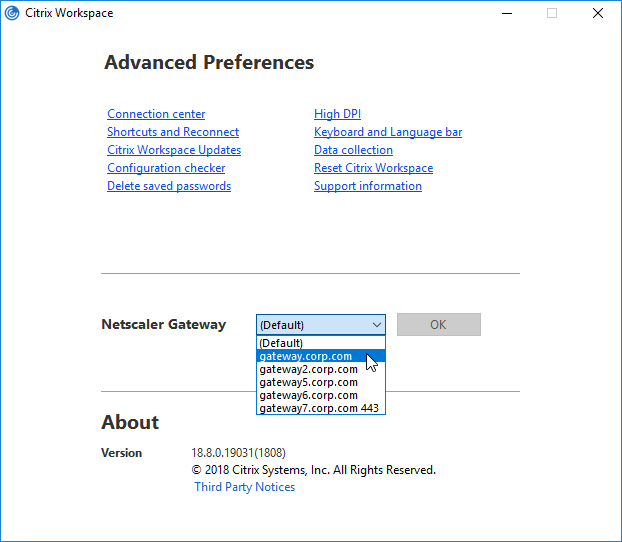
In StoreFront Console, if any configuration changes are performed that affect the Provisioning File, it takes an hour for Workspace apps to reconfigure themselves automatically. Or users can remove Accounts and re-add (or Reset Citrix Workspace) so that the updated Provisioning File is imported.
Here are some additional methods of performing Workspace app Discovery:
- After exporting the Provisioning File from StoreFront Console, distribute it to users, and ask them to double-click it.
- After logging in to Receiver for Web (StoreFront), at the top right, click the username, and click Activate. This downloads the receiverconfig.cr file, which is identical to the one you can export from StoreFront Console. The user then must run the downloaded file.
Virtual Monitors
In Workspace app 1812 and newer, when connected to a published desktop on a single monitor, you can split the screen into virtual monitors. This feature is intended for large 4K monitors.
- In the desktop toolbar at the top of the screen, click Preferences.
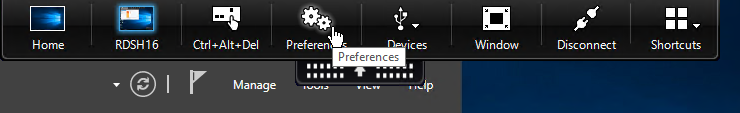
- Switch to the Monitor Layout tab.
- On the bottom, select Horizontal or Vertical, then click somewhere in the blue box to draw a line. The single monitor will be split along this line. You can set different DPI for each portion of the virtual display.
- Right-clicking one of the split sections changes that section to the primary display.
- Click OK when done.
- In the toolbar, click Window to resize it to a window, and then click Full Screen to cause your virtual monitor configuration to take effect.
Uninstall Old Clients
Workspace app installer can do a force uninstall of old clients before installing the new version:
- In Workspace app 2309 and newer, run CitrixWorkspaceApp.exe /CleanInstall /Silent
- In Workspace app 1909 and newer, run CitrixWorkspaceApp.exe /ForceInstall /Silent.
- In Workspace app 1908 and older (including Receiver), run CitrixWorkspaceApp.exe /RCU /Silent or CitrixReceiver.exe /RCU /Silent.
Citrix CTX325140: How to Remove Client Files Remaining on System after Uninstalling Receiver for Windows.
Installation and Configuration
Administrator privileges – Administrator privileges are required to install any missing prerequisites.
Internet required – Recent versions of Workspace app download and install Microsoft Edge WebView2 Runtime, .NET Desktop Runtime 6.0.20, .NET Framework 4.8, and Visual C++. Internet access is required for the Workspace app installer to download these install files. Or there’s an Offline Installer for Workspace app 2309 and newer.
.NET Desktop Runtime 6.0.20 – Workspace app 2309 and newer will install x86 .NET Desktop Runtime 6.0.20 if it’s not already installed.
This section contains a summary of all common command line switches, registry keys, and policy settings for Workspace app.
Links:
- Citrix Blog Post: Optimizing Citrix Receiver for Pre-launch and Single Sign-On
- Citrix CTX202002 How To Deploy Citrix Receiver for Windows Using SCCM 2012 R2
Workspace app 2203 LTSR CU2 and Workspace app 2212 and newer fix security vulnerabilities.
CitrixWorkspaceApp.exe current release version 2409.10 or LTSR version 2402 CU3 can be installed by simply double-clicking it.
- LTSR Workspace app does not support Browser Content Redirection.
- Workspace app 2006 and newer do not support Windows 7.
- Workspace app 2206 and newer enable DPI Matching by default. DPI Matching can be disabled through client-side group policy, or in the Advanced Preferences in Workspace app 2212 and newer. DPI Matching prevents connections to CVAD 7.15. Multi-session VDAs with version 1912, by default, have DPI Matching disabled, but can be enabled in the VDA’s registry. See CTX460068 for details.
- Workspace app 2311 and newer have a new interface for installation.
- Workspace app 2402 and newer ask if you want to install the Microsoft Teams VDI Plugin or not. This is for Teams 2.1 and newer.
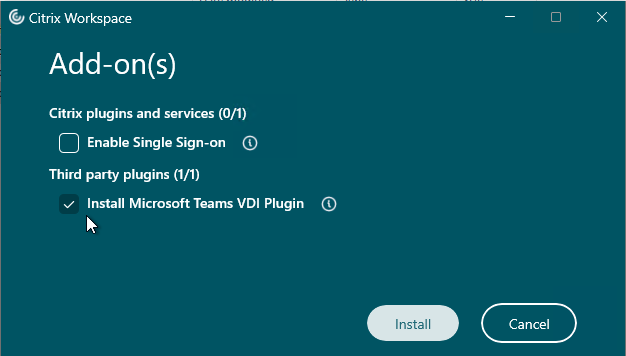
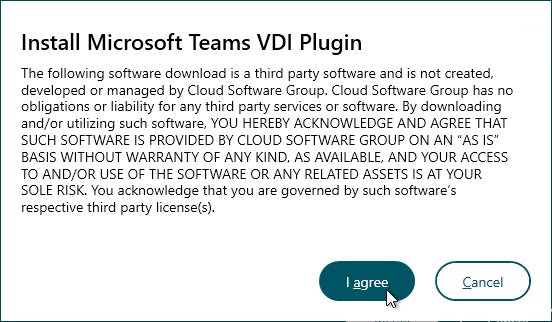
Administrator vs non-administrator
- Non-administrator – If a non-administrator installs Workspace app, then each non-administrator that logs in to the same workstation will have to reinstall Workspace app.
- Non-administrator installations are installed to %USERPROFILE%\AppData\Local\Citrix\ICA Client for each user.
- Administrator – If CitrixWorkspaceApp.exe is installed using an administrator account. then the Workspace app only needs to be installed once.
- Administrator installations are installed to C:\Program Files (x86)\Citrix\ICA Client.
- Administrator installations of Workspace app 1912 and newer can be manually upgraded by non-administrators by clicking Check for Updates. Older versions cannot be upgraded by non-administrators.
- Conflicts – If an administrator install of Workspace app is performed on a machine that has non-administrator installs of Workspace app, then the two installations will conflict. Best option is to uninstall non-admin Workspace app and Receiver before installing admin Workspace app. Otherwise, the user’s profile probably has to be reset before Workspace app is functional again.
- Citrix article CTX249920 Workspace App for Windows – Your apps are not available at this time – Issue when installing Citrix Receiver in not elevated/per-user install mode describes the HKEY_CURRENT_USER registry keys that must be deleted to fix this issue.
- For a script to clean-up the per-user installs, see Mark DePalma at Citrix Receiver Per-User Install Cleanup.
Global App Configuration Service
Global App Configuration Service (GACS) is a Citrix Cloud service that can push configurations to Workspace app clients. This Citrix Cloud service is now available to all on-premises customers even if you don’t own any Citrix Cloud entitlements.
- Login to https://citrix.cloud.com. If you don’t have a Citrix Cloud account, then login using your Citrix.com account credentials and it will create a Citrix Cloud account.
- Use the top left hamburger menu to go to Workspace Configuration.
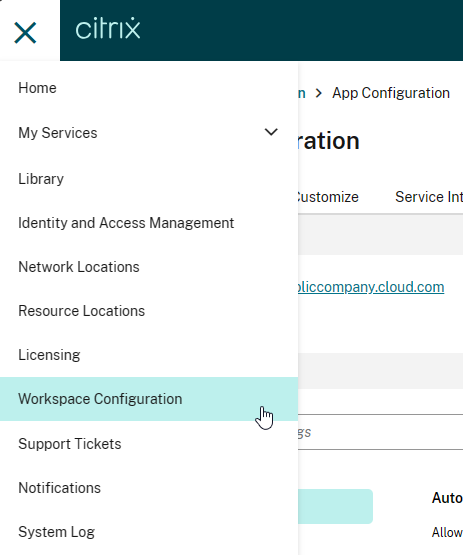
- Switch to the tab named App Configuration.
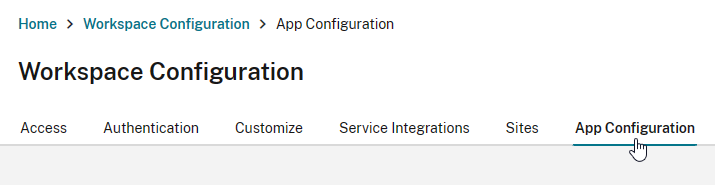
- Click Switch URL.
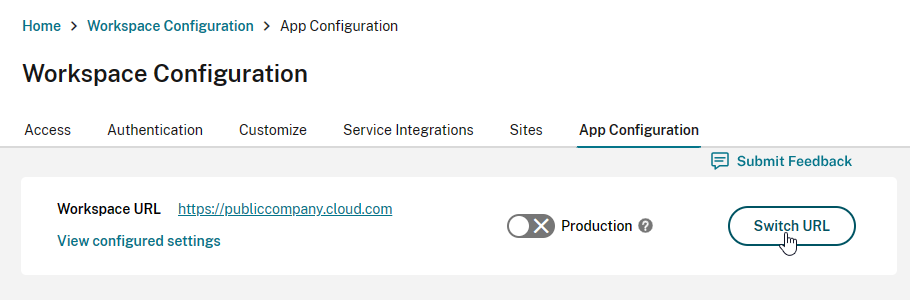
- Near the bottom, click Claim URL.
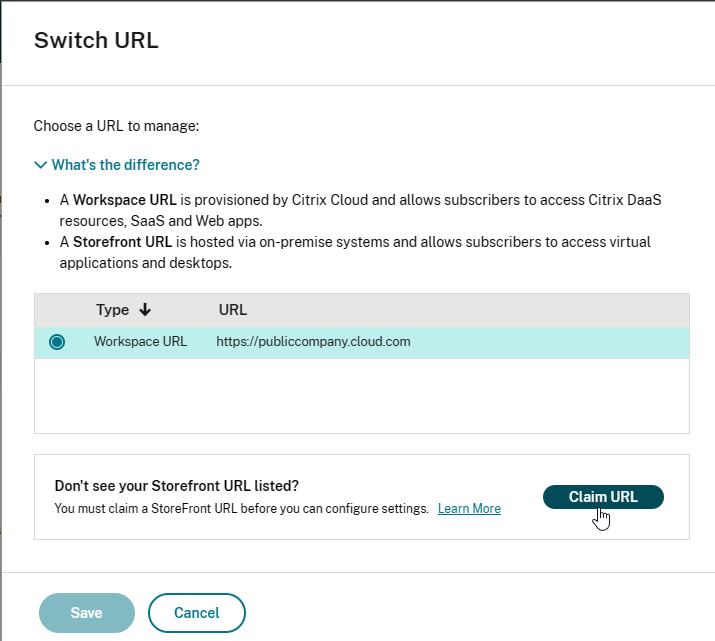
- Click Add URL to add your on-premises StoreFront/Gateway URL. See Citrix Docs for details. GACS uses this URL to determine which Workspace app clients should receive the settings that you configure.
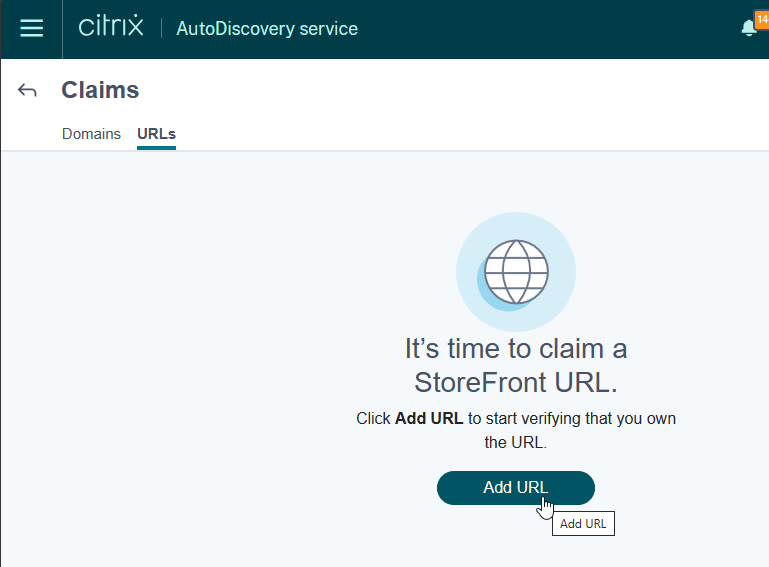
- Back in the App Configuration page, you can now configure Workspace app settings as desired. Workspace apps that have stores under the claimed URL will then receive these settings.
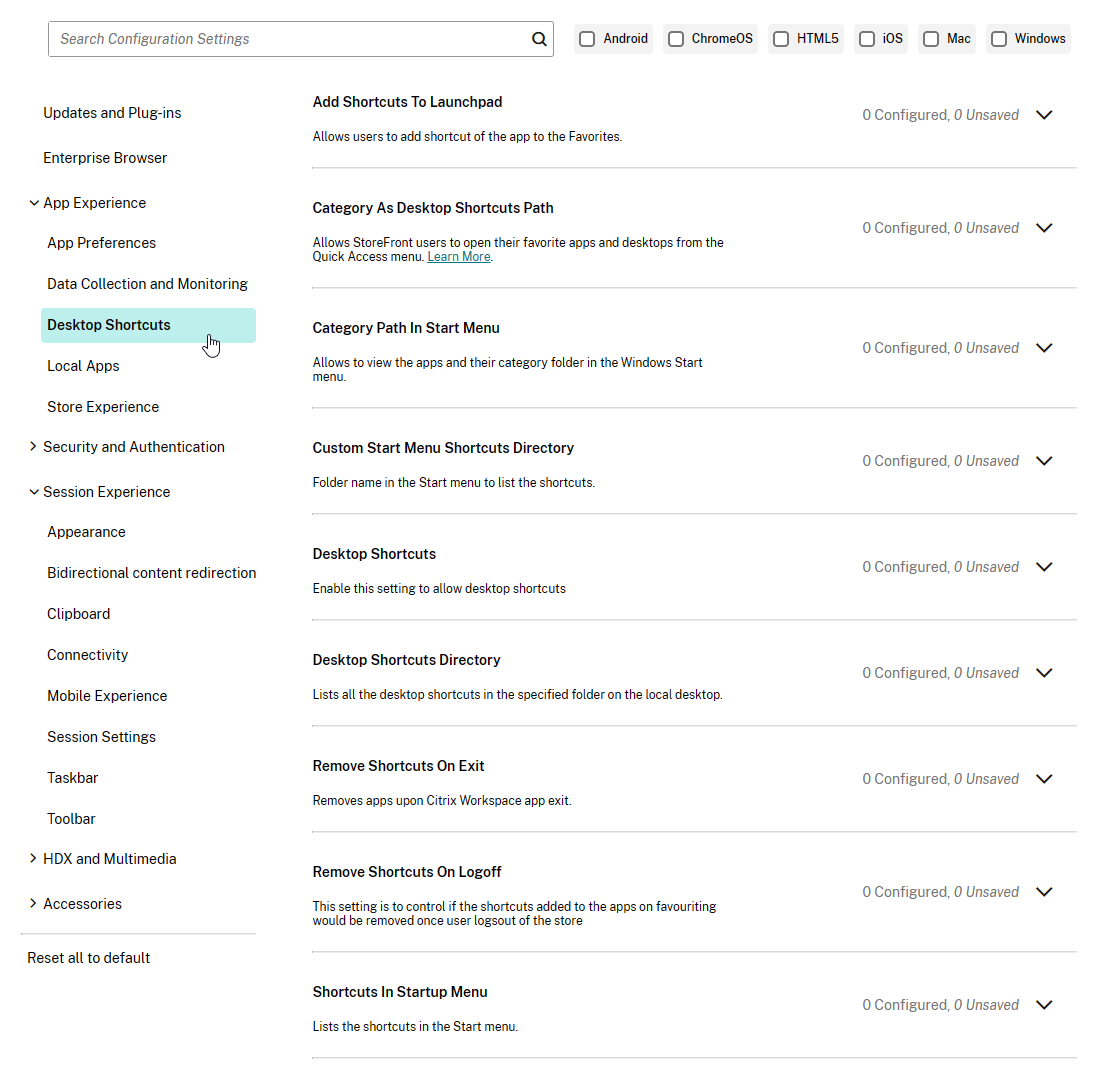
Auto-Update
Workspace app supports auto-update.
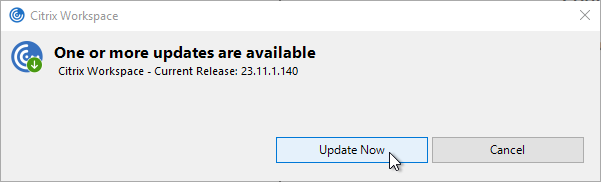
Some notes:
- If Workspace app 1912 or newer is installed as administrator, then non-administrators can click Check for Updates to manually update Workspace app. To prevent this, use group policy to disable Citrix Workspace Updates.
- Older versions of Workspace app cannot be upgraded by non-administrators.
- If Workspace app is installed on a VDA, auto-update is automatically disabled. This includes Remote PC.
- Auto-update can be limited to LTSR updates only.
- Auto-update is configurable through several mechanisms: group policy, StoreFront, Workspace app GUI, installer command line. See Configuring Citrix Workspace Updates at Citrix Docs.
- Workspace app 2107 and later let users select an Update channel.
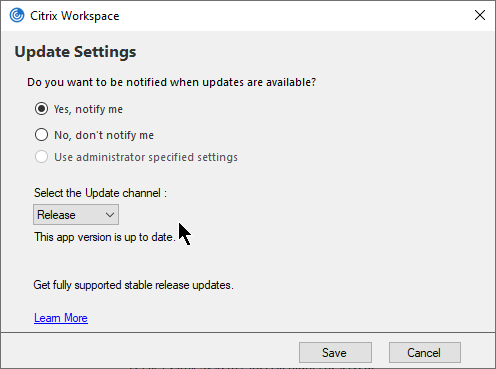
- See George Spiers Citrix Receiver for Windows Auto-Update.
Auto-update is configured using Workspace app group policy under the Citrix Workspace Updates, or Auto-Update node.
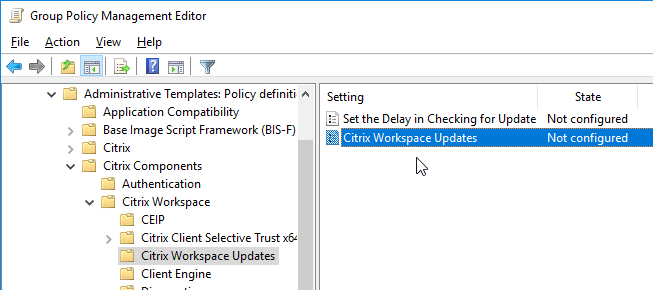
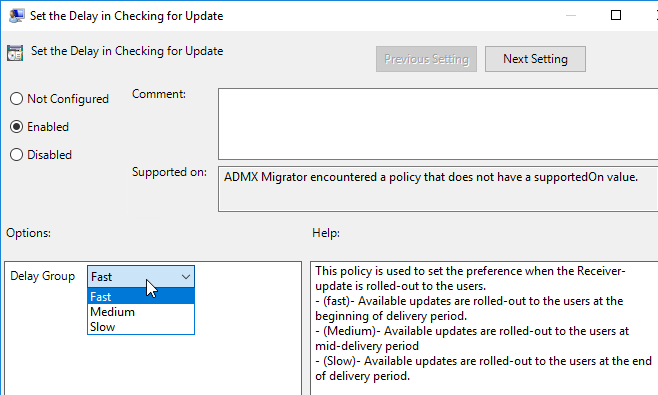
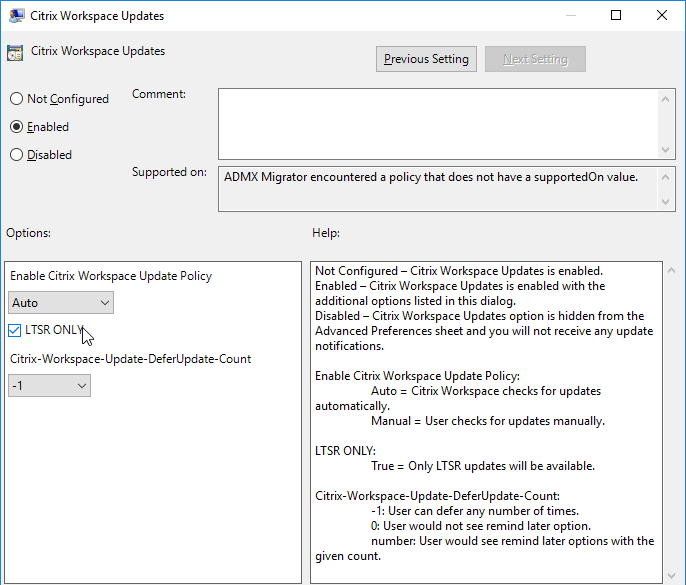
Or use Global App Configuration Service.
Workspace app Splash Screen
Workspace app shows a Splash Screen on first launch with the text “Citrix Workspace app extends the capabilities of Citrix Receiver”.

To prevent this splash screen, set the following registry value: (source = Dennis Span on Twitter)
- Key = HKEY_CURRENT_USER\SOFTWARE\Citrix\Splashscreen
- Value (REG_SZ) = SplashscreenShown = 1
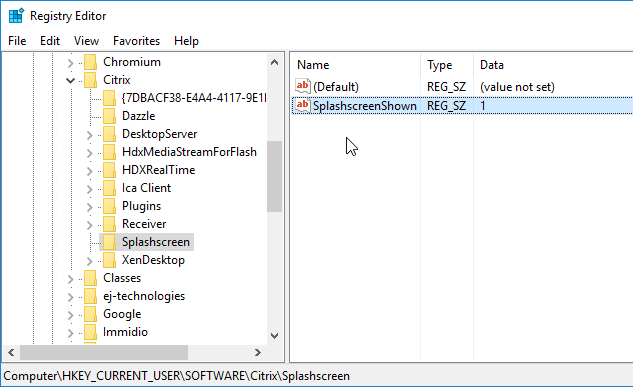
Add Account Wizard
After installation, Workspace app will launch and ask you to add an account. If Workspace app, notice the checkbox Do not show this window automatically at logon.
FTU (First Time Use aka Add Account Wizard) will be displayed only if a store is not configured. If a store is already configured via command line, GPO, or Citrix Studio, then FTU screen will not be available after installation. Otherwise, FTU can be suppressed by doing one of the following:
- Rename CitrixWorkspaceApp.exe to CitrixWorkspaceAppWeb.exe.
- Install using a command line switch:
- CitrixWorkspaceApp.exe /ALLOWADDSTORE=N
- Set the registry value: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Citrix\EnableFTU=dword:00000000 (or EnableX1FTU =dword:0)
- Disable the EnableFTU policy setting in Receiver.admx.
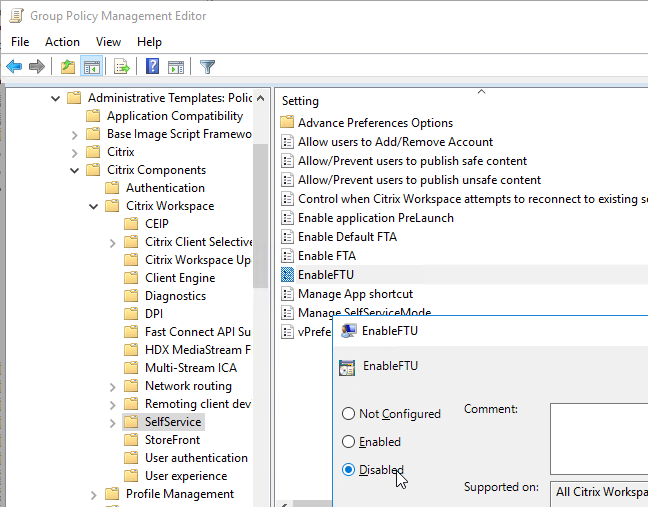
- Change Registry values post installation to suppress the Add Account window. Under HKLM\Software\Wow6432Node\Citrix\Dazzle, set AllowAddStore value to N.
- Set the registry value: HKEY_LOCAL_MACHINE\Software\Citrix\Receiver\NeverShowConfigurationWizard (REG_SZ) = true
- Also see Suppressing Add Account dialog at Citrix Docs.
Discover Hidden Stores
When Workspace app is first launched, it must perform Discovery, which is the process of downloading the .xml provisioning file from StoreFront. Discovery is performed by entering a StoreFront FQDN or Gateway FQDN. To discover a hidden store (a store that’s not advertised), add ?StoreName to the end of the FQDN. CTX214819 How to configure Receiver to a Store that is not advertised.
CitrixWorkspaceApp.exe Command line switches
CTX227370 Citrix Workspace app Commandline Tool contains a GUI tool to build your installer command line.

For unattended installation of Workspace app, see CTA Dennis Span Citrix Workspace App unattended installation with PowerShell or Citrix Receiver unattended installation with PowerShell.
Installer Command Line Switches are detailed at Configure and install Receiver for Windows using command-line parameters at Citrix Docs. Common Command line switches include the following:
- /silent
- /includeSSON – enables pass-through authentication. GPO configuration is also required as detailed below.
CitrixWorkspaceApp.exe /includeSSON
- /ALLOWADDSTORE=A – by default, only SSL (HTTPS) stores are accepted. To allow non-SSL stores:
CitrixWorkspaceApp.exe /ALLOWADDSTORE=A
- /STORE0 – To add a store from the installation command line:
CitrixWorkspaceApp.exe STORE0="AppStore;https://Citrix.corp.com/Citrix/MyStore/discovery;on;App Store"
- Workspace App can discover the Store through NetScaler Gateway.
CitrixWorkspaceApp.exe STORE0="AppStore;https://gateway.corp.com#MyStore;On;App Store"
- Workspace App can discover the Store through NetScaler Gateway.
- /SELFSERVICEMODE=False – disables the Self-Service interface and enables shortcut-only mode:
CitrixWorkspaceApp.exe /SELFSERVICEMODE=False
- /AutoUpdateCheck=auto /AutoUpdateStream=LTSR – enables Citrix Workspace Update notifications and sets it to LTSR Branch only. AutoUpdateCheck can also be set to manual or disabled. AutoUpdateStream can also be set to Current. See Configuring Citrix Workspace Updates at Citrix Docs.
CitrixWorkspaceApp.exe /AutoUpdateCheck=auto /AutoUpdateStream=LTSR
- /ENABLEPRELAUNCH=True – enables prelaunch:
CitrixWorkspaceApp.exe /ENABLEPRELAUNCH=True
- /ALLOW_CLIENTHOSTEDAPPSURL=1 – enables Local App Access:
CitrixWorkspaceApp.exe /ALLOW_CLIENTHOSTEDAPPSURL=1
Registry values
HKLM\Software\Wow6432Node\Citrix\Dazzle on the Workspace app machine. All are of type REG_SZ (string) unless specified. Note: several of these are configurable using the Reciever.admx group policy template.
- SelfServiceMode (REG_SZ) = False – Turns off Workspace app’s Self-Service interface.
- PutShortcutsOnDesktop (REG_SZ) = True – If Self-Service interface is disabled, places all shortcuts on desktop.
- UseDifferentPathsforStartmenuAndDesktop (REG_SZ) = True
- UseCategoryAsStartMenuPath (REG_SZ) = True or False
- UseCategoryAsDesktopPath (REG_SZ) = True or False
- StartMenuDir (REG_SZ) = name of folder on Start Menu where shortcuts are placed.
- DesktopDir (REG_SZ) = name of folder on Desktop where shortcuts are placed
- EnablePreLaunch (REG_SZ) = True – If SSON is enabled then PreLaunch is already enabled by default.
- AllowAddStore (REG_SZ) = A – Only if using http (instead of https) to connect to StoreFront.
- AllowSavePwd (REG_SZ) = A – Only if using http (instead of https) to connect to StoreFront.
- UserDomainName (REG_SZ) = pre-filled domain name
- InitialRefreshMinMs (REG_SZ) = 1 – minimizes the launch delay before contacting store
- InitialRefreshMaxMs (REG_SZ) = 1 – minimizes the launch delay before contacting store
- RefreshMs (REG_SZ) = 3600000 (1 hour) – interval for Receiver icon refreshes. 1 hour is the default value.
- RefreshMs (REG_SZ) = 18000000 – Citrix CTX213755 Citrix Receiver Shows Authentication Window Periodically When Receiver is Not Opened
- MaxSimultaneousFetches (REG_DWORD) = 6 – improves the time of loading icons in Start Menu
- MaxSimultaneousSubscribes (REG_DWORD) = 6 – improves the time of loading icons in Start Menu
- DontWarnOfRemovedResources (REG_SZ) = True – prevents dialog boxes when resources are removed from the server. (or False)
- SilentlyUninstallRemovedResources (REG_SZ) = True – prevents dialog boxes when resources are removed from the server
- PreferTemplateDirectory (REG_SZ) = UNC path or local path containing shortcuts copied by the prefer keyword. Give the shortcuts a short name.
- PnaSSONEnabled (REG_SZ) = True – Enables Single Sign-on for PNAgent (Web Interface).
- WSCReconnectMode (REG_SZ) = 3 (default) – If this Workspace app is running inside a VDA published desktop, set it to 0.
- If you’re having trouble getting sessions to reconnect, see Receiver 4.3 Desktop will not auto-reconnect when logging into a machine at Citrix Discussions
- AlwaysUseStubs (REG_SZ) = True. Workspace app and Receiver 4.3.100 and newer don’t create .exe stubs by default. Set this to create .exe stubs. Also see Citrix CTX211893 Controlling Shortcut behavior in Receiver 4.3.100.
- DontCreateAddRemoveEntry (REG_SZ) = True – don’t create “Delivered by Citrix” entries in Programs and Features
- DesktopNameFormatString = format string for shortcut names – For example “{0}_{1}_{2}_{3}”. See the link for details.
- SelfServiceFlags (REG_DWORD) = 4 – prevents duplicate shortcuts when roaming and Desktop is redirected.
- SelfServiceFlags = 5 to stop external SSON from prompting for authentication
- ReEvaluateNetwork (REG_SZ) = true – for Beacon detection with Single FQDN
To prevent the Win+G popup on Windows 10 machines:
- HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\GameDVR
- AllowGameDVR (REG_DWORD) = 0
To allow adding non-HTTPS stores to Workspace app:
- HKLM\Software\Wow6432Node\Citrix\AuthManager
- ConnectionSecurityMode (REG_SZ) = Any
To increase ICA bandwidth consumption over high latency links, set:
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\ICA Client\Engine\Configuration\Advanced\Modules\TCP/IP
- OutBufCountClient2 = Number of OutBufs (default is 44)
- OutBufCountHost2 = Number of OutBufs (default is 44)
- See CTX125027 How to Optimize HDX Bandwidth Over High Latency Connections for some recommended values (multiples of 44)
To prevent beacon probing from using proxy, set:
- HKEY_LOCAL_MACHINE\Software\WOW6432Node\Citrix\Receiver\inventory
- BeaconProxyEnabled (REG_DWORD) = 0
To enable foreground progress bar, set:
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\ICA Client
- ForegroundProgressBar (REG_DWORD) = 1
For client-to-server file type redirection, set:
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\ICA Client\Engine\Configuration\Advanced\Modules\ClientDrive
- NativeDriveMapping=”TRUE”
To fix USB devices that emulate a keyboard, set:
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\ICA Client\Engine\Lockdown Profiles\All Regions\Lockdown\Virtual Channels\Keyboard
- KeyboardTimer=”10”
To remember manually mapped USB devices when auto-connection is enabled, set: (2409 and newer)
- HKLM\SOFTWARE\Citrix\ICA Client\GenericUSB (same path for 32-bit and 64-bit, create the keys)
- RememberConnections (DWORD) = 0x1
To override the devices that are mapped using optimized channels instead of generic USB, see Citrix CTX123015 How to Configure Automatic Redirection of USB Devices
Group Policy Settings
Copy the Workspace app ADMX template (C:\Program Files (x86)\Citrix\ICA Client\Configuration\receiver.admx) to C:\Windows\PolicyDefinitions (or Sysvol). Also copy receiver.adml to C:\Windows\PolicyDefinitions\en-us (or Sysvol).
Edit a GPO that applies to client machines, go to Computer Configuration | Policies | Administrative Templates | Citrix Components | Citrix Workspace and configure the following:
- To enable pass-through authentication: go to | User Authentication |.
- Local Username and Password – Check the top two boxes.
- Also add the StoreFront FQDN to the Local Intranet zone in Internet Explorer.
- Single Sign-on for NetScaler Gateway (Workspace app 1808 and newer)
- To add a store, go to | StoreFront |
- StoreFront Accounts List – see the help text
- To enable Auto-Update, go to | AutoUpdate | or | Citrix Workspace Updates |. (the node was renamed in 4.11 and Workspace app)
- Enable or Disable AutoUpdate or
- Citrix Workspace Updates
- To modify the desktop viewer toolbar, go to | Client Engine |
- Desktop Viewer Toolbar Options (2409 and newer)
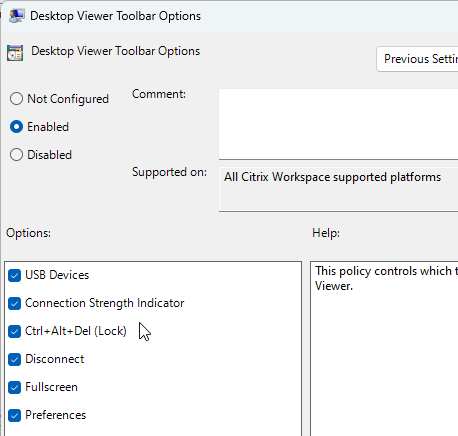
- Desktop Viewer Toolbar Options (2409 and newer)
- To enable Local App Access, go to | User Experience |
- Local App Access Settings
- To prevent the endpoint from sleeping while session is active, go to | User Experience |
- Power Management (2405 and newer)
- To configure the Self-Service interface, go to | SelfService |
- Set Manage SelfServiceMode to Disabled to completely disable the Self-Service window. This causes all icons to be placed on the Start Menu.
- Enable Manage App Shortcut and configure it as desired.
- To allow the Self-Service window, but prevent it from automatically opening (reside in systray), tick Prevent Citrix Workspace performing a refresh of the application list when opened. Source
- Enable Control when Workspace attempts to reconnect to existing sessions. If this is a VDA published desktop, set it to Disabled. Otherwise configure it as desired.
- Set Enable FTU to Disabled to prevent the Add Account wizard from displaying.
- Enable Allow/Prevent users to publish unsafe content if publishing content that’s opens a file or file share.
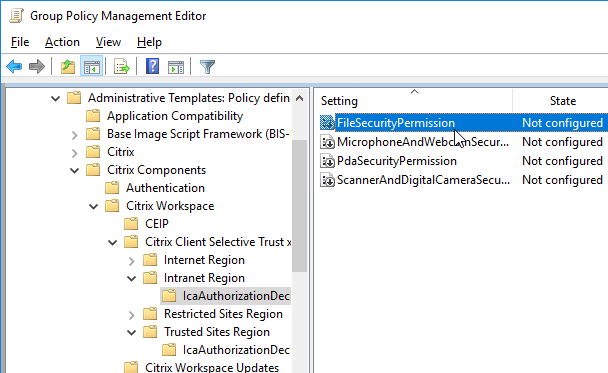
Enable automatic client drive and client microphone mapping:
- In a client-side GPO, add the GPO ADM template from http://support.citrix.com/article/CTX133565.
- Enable the setting Create Client Selective Trust Keys. See Below for details.
- Configure the FileSecurityPermission setting in one or more of the regions.
- Configure the MicrophoneAndWebcamSecurityPermission setting in one or more of the regions.
Citrix CTX203658 Start Menu Icons Set to Default (Blank Document) After Update to Receiver 4.3.100 – Windows 8 and newer
- Computer Configuration | Policies | Administrative Templates | Windows Components | File Explorer
- Allow the use of remote paths in file shortcut icons = enabled
For Single Sign-on in Windows 11 24H2 and newer, enable the following GPO setting:
- Computer Configuration | Policies | Administrative Templates | Windows Components | Windows Logon Options
- Enable MPR notifications for the System = enabled
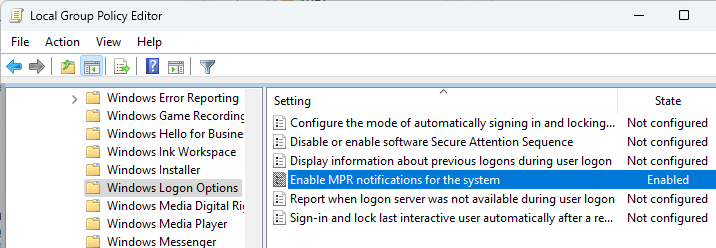
- Enable MPR notifications for the System = enabled
Deploy Workspace app using Active Directory
To deploy Workspace app using Active Directory, configure a GPO with a computer startup script that runs the Workspace app installer executable. Citrix provides sample scripts that can be downloaded from one of the Workspace app download pages (Workspace app current release version 2409.10, or LTSR version 2402 CU3, by expanding Downloads for Admins (Deployment Tools).
Also see CTA Dennis Span Citrix Receiver unattended installation with PowerShell.

Change Workspace App’s Store Configuration, including Reset Citrix Workspace
You can change Workspace app’s configured Store/Account with a couple command lines:
"C:\Program Files (x86)\Citrix\ICA Client\SelfServicePlugin\SelfService.exe" -deleteproviderbyname Corporate "C:\Program Files (x86)\Citrix\ICA Client\SelfServicePlugin\SelfService.exe" -init -createprovider Corporate https://storefront.corp.com/Citrix/Store/discovery
It is sometimes necessary to Reset Citrix Workspace by right-clicking the Workspace app systray icon, clicking Advanced Preferences, and clicking the Reset link. You can do this from the command line by running "C:\Program Files (x86)\Citrix\ICA Client\SelfServicePlugin\CleanUp.exe" -cleanUser -silent. See CTX140149 How to Reset Receiver Using the Command Line.
Workspace app Group Policy ADMX Template
Many of the Workspace app configuration settings must be configured in group policy. These Workspace app settings are only available after installing the GPO templates.
Alternatively, Citrix Cloud customers can use Global App Configuration Service to configure Workspace app. Today it’s a REST API, but Citrix has started adding a GUI at Workspace Configuration > App Configuration.
For GPO configuration:
- From a machine that has Workspace app installed, find the .admx and .adml files in the C:\Program Files (x86)\Citrix\ICA Client\Configuration.
- Copy the CitrixBase.admx and receiver.admx files. Also copy the en-US folder. In Workspace app, the files are still named receiver.admx.
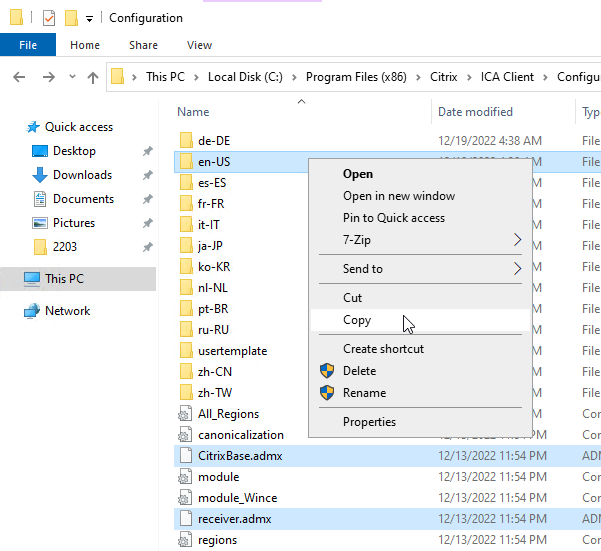
- Go to your domain’s SYSVOL share and in the Policies folder look for a PolicyDefinitions folder. If one exists, paste the .admx file directly into the PolicyDefinitions folder. If this folder doesn’t exist in SYSVOL, instead copy the .admx file to C:\Windows\PolicyDefinitions. Overwrite any existing Receiver ADMX files.
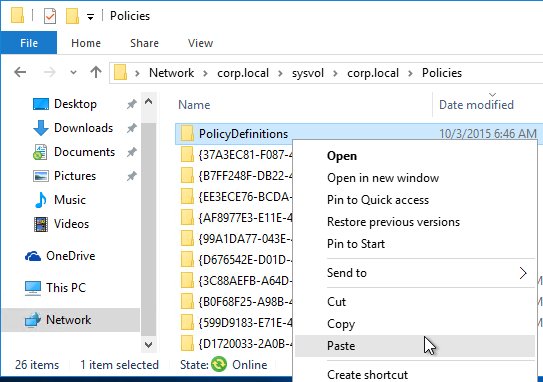
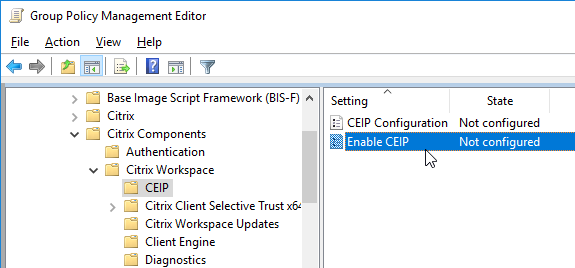
- The GPO settings can then be found at one of the following:
- Computer Configuration > Policies > Administrative Templates > Citrix Components > Citrix Workspace
- Computer Configuration > Policies > Administrative Templates > Citrix Components > Citrix Receiver
- For example, you can disable Customer Experience Improvement Program (CEIP) from here.
- See https://www.carlstalhood.com/delivery-controller-cr-and-licensing/#ceip for additional places where CEIP is enabled.
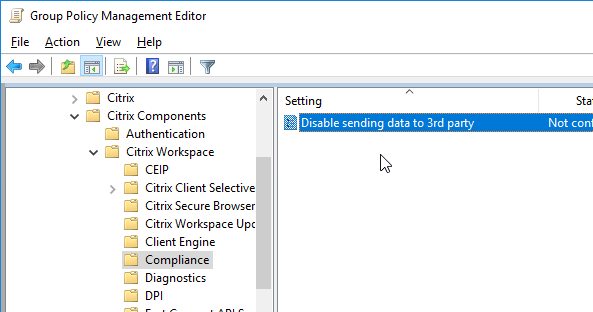
- Workspace app 1905 and newer has a setting to Disable sending data to 3rd party (e.g., Google Analytics).
- Workspace app 1905 and newer let you disable embedded browser caching.
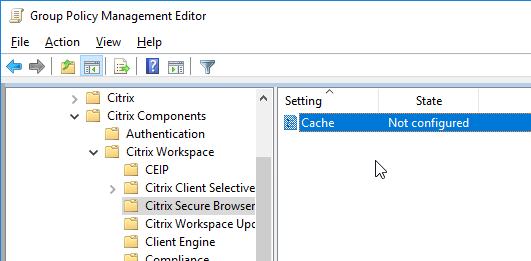
- Workspace app 1905 and newer have NetScaler LAN Proxy under Network routing > Proxy.
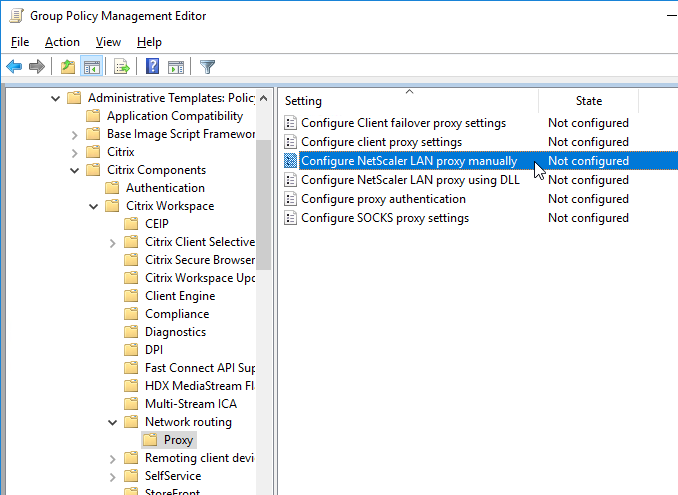
- Workspace app 1808 and newer have User authentication | Single Sign-on for NetScaler Gateway.
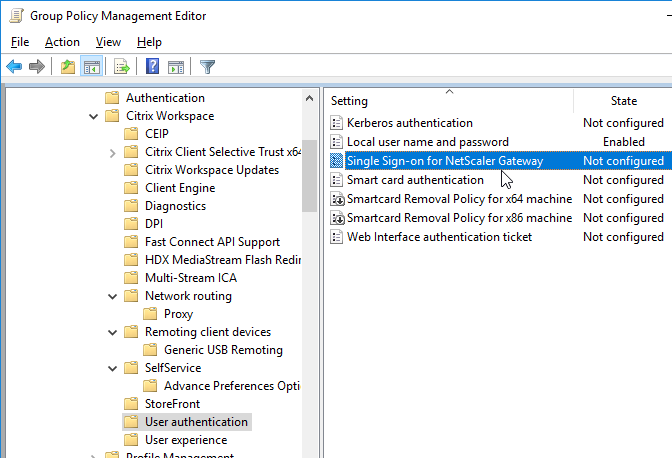
- Citrix Workspace Updates, (aka AutoUpdate) can be configured using group policy. See Configuring Citrix Workspace Updates at Citrix Docs.
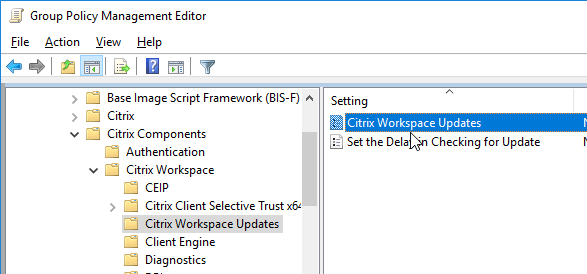
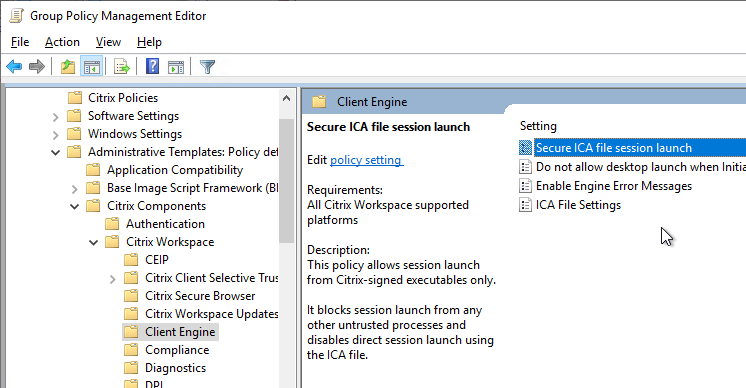
- Workspace app 1912 and newer can be configured to require in-memory ICA files only. The setting called Secure ICA file session launch is under the Client Engine node. See Citrix Docs for details on in-memory ICA files instead of writing ICA files to disk.
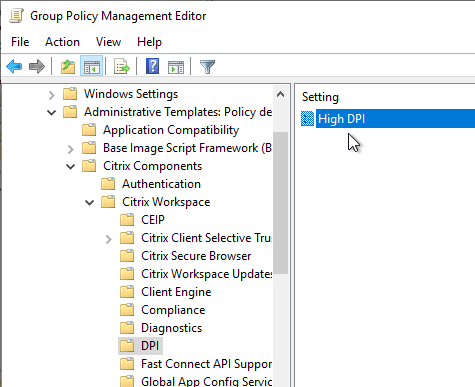
- The DPI node has a setting called High DPI that lets you disable DPI matching, which is enabled by default in Workspace App 2206 and newer.
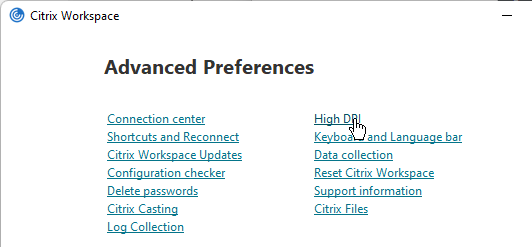
- Workspace app 2210 and newer let you use the GUI to re-enable High DPI.
- Native resolution means DPI matching, whereas Yes means force high DPI.
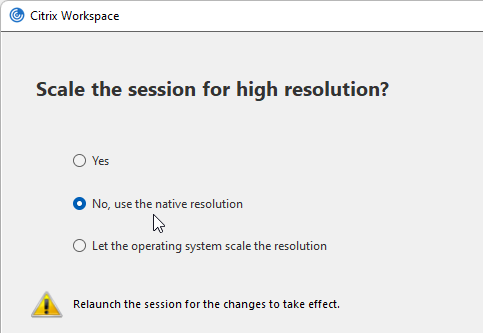
- Workspace app 2210 and newer let you use the GUI to re-enable High DPI.
- Workspace app has settings to hide Advanced Preferences, enable/disable showing the DPI option, and enable/disable H265.
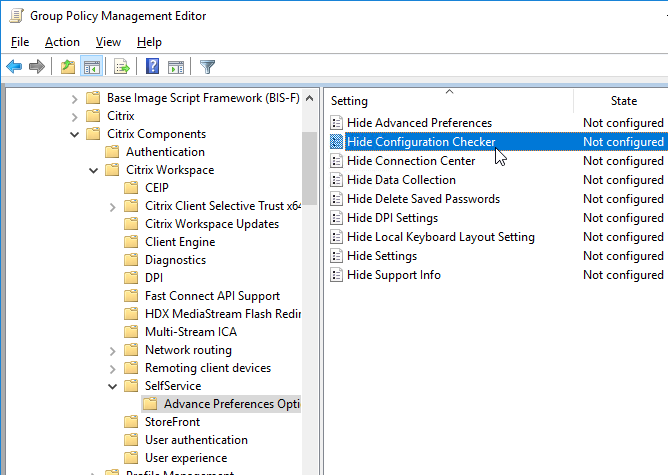
- Workspace app 4.8 and newer have SplitDevices GPO setting under Citrix Workspace | Remoting client devices | Generic USB Remoting. See Configuring composite USB device redirection at Citrix Docs.
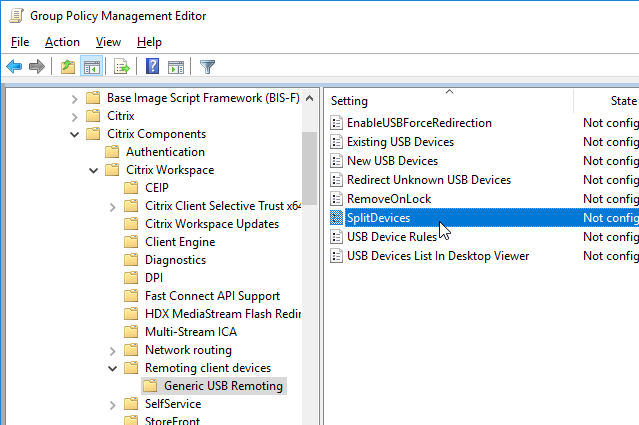
- Workspace app 2212 and newer by default disable App Protection for the authentication screen and icons list. To enable them, configure User authentication | Manage App Protection and SelfService | Manage App Protection.
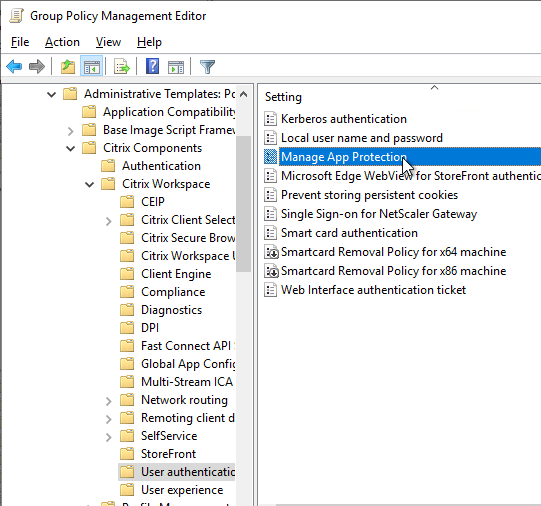
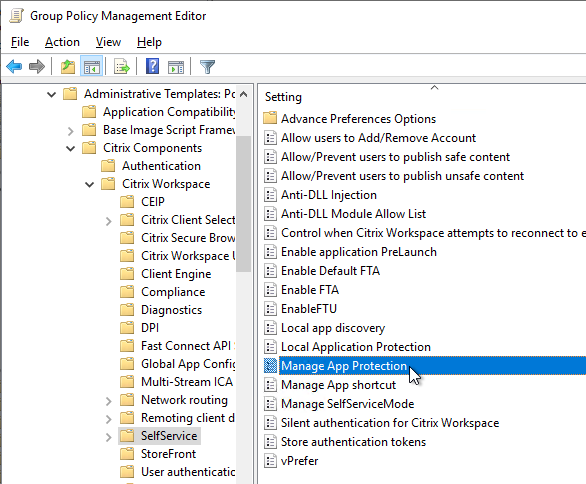
- Workspace app 2303 and newer have Anti-DLL Injection for App Protection. It is disabled by default. Enable it in a GPO at Citrix Components | Citrix Workspace | App Protection | Anti-DLL Injection. See Citrix Docs for details.

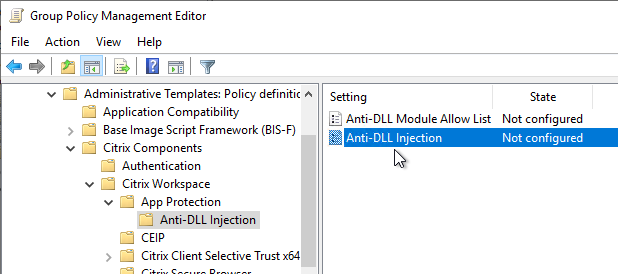
Pass-through Authentication
Citrix blog post – A Comprehensive Guide to Enabling Pass-Through Authentication with XenDesktop 7.5
- Run the command
Set-BrokerSite -TrustRequestsSentToTheXmlServicePort $True from a Windows PowerShell command prompt on a Delivery Controller.
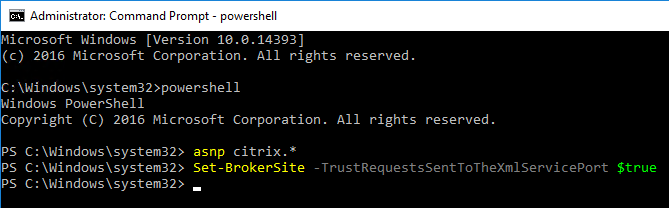
- In XenApp 6.5, this is a Citrix Policy > Computer > Trust XML Requests.
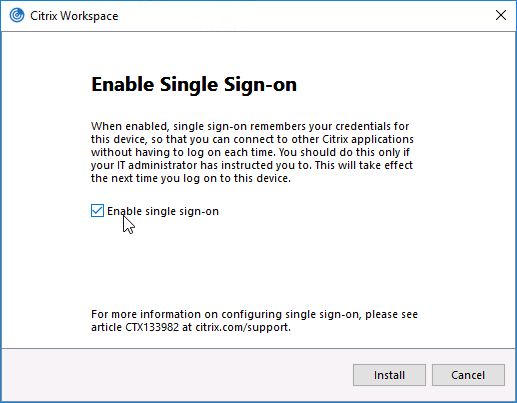
- Login to the PC as an administrator.
- If installing Workspace app, as an administrator, during installation, on the Enable Single Sign-on page, check the box next to Enable Single Sign-on. Then finish the installation.
- To verify that SSON is installed, go to C:\Program Files (x86)\Citrix\ICA Client and look for the file ssonsvr.exe.
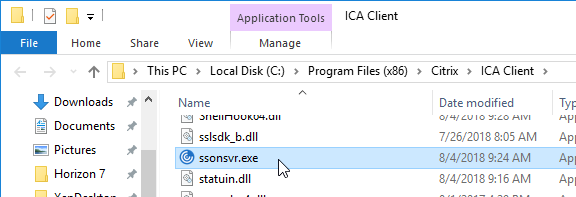
- And if you open regedit and go to HKLM\SYSTEM\CurrentControlSet\Control\NetworkProvider\Order, you should see PnSson in the ProviderOrder.
- Install the receiver.admx (and .adml) template into PolicyDefinitions if you haven’t already.
- Edit a GPO that is applied to the client PCs where the Workspace app is installed.
- Go to Computer Configuration > Policies > Administrative Templates > Citrix Components > Citrix Workspace.
- Expand Citrix Workspace and click User authentication.
- On the right, double-click Local user name and password.
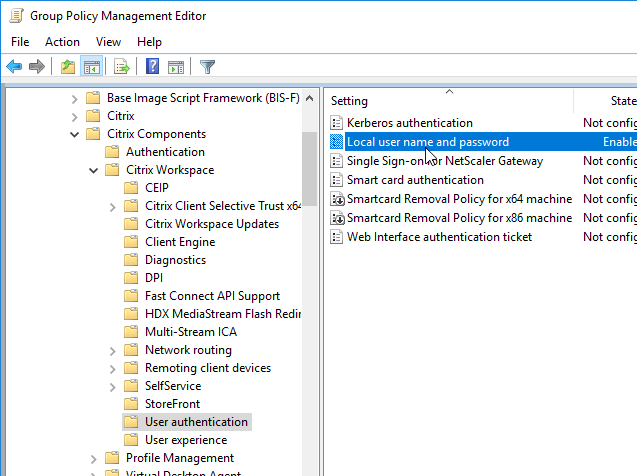
- Select Enabled and then check the box next to Allow pass-through authentication for all ICA connections. Click OK.
- In Workspace app 1808 and newer, you can enable Single Sign-on for NetScaler Gateway.
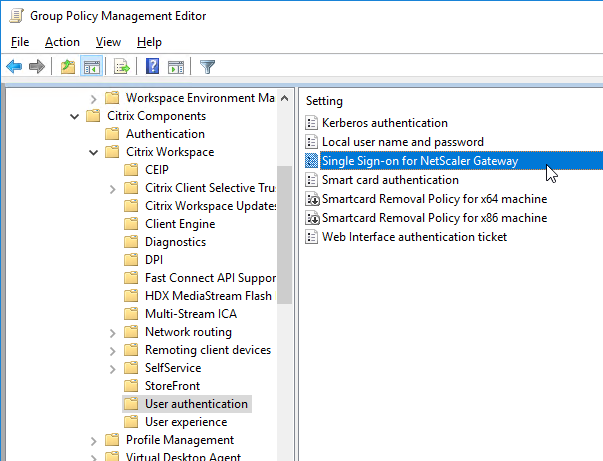
- Ensure that the internal StoreFront FQDN is in the Local Intranet zone in Internet Explorer. You can use a GPO to configure this on the client side.
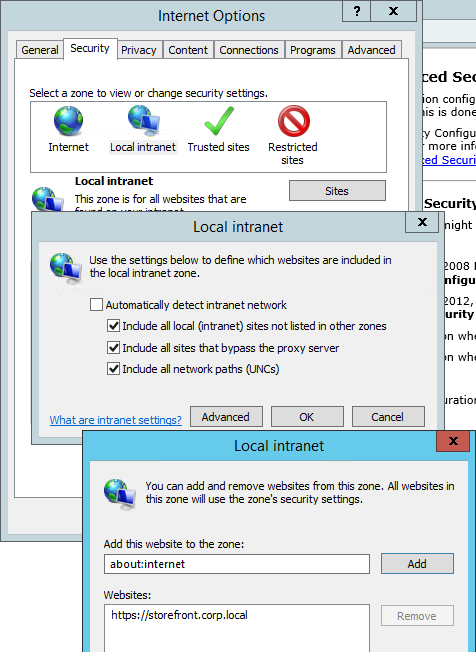
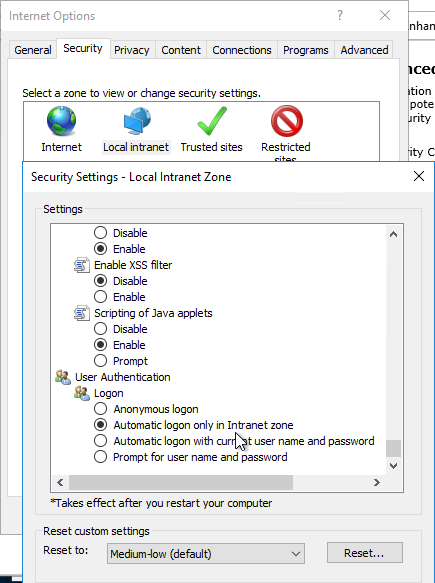
- Local Intranet zone should have Automatic logon only in Intranet zone enabled.
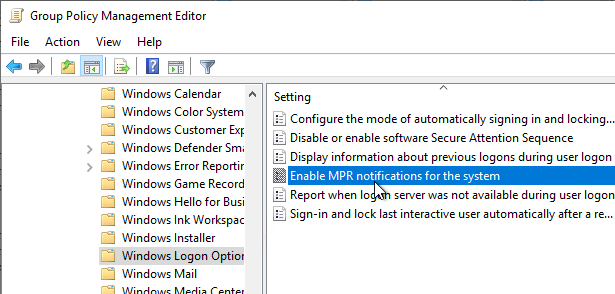
- For Windows 11 24H2 and newer, make sure the GPO setting Enable MPR notifications for the System is enabled at Computer Configuration | Policies | Administrative Templates | Windows Components | Windows Logon Options. Make sure HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\EnableMPRNotifications is set to 1 on the Workspace app machine.
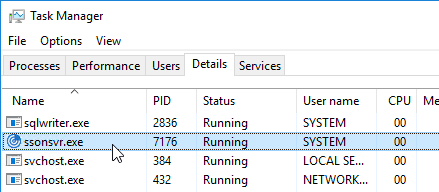
- Logoff Windows and log back on. In Task Manager you should now see ssonsvr.exe. This won’t appear unless you logoff and log back on.
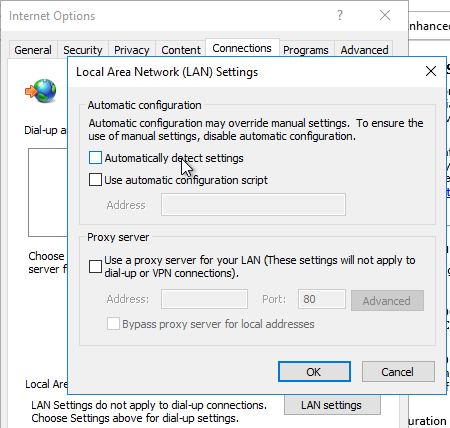
- If Workspace app won’t connect or is slow to enumerate icons, then you might have to disable Automatically detect settings in IE.
- Right-click the Workspace app icon and click Advanced Preferences.
- Click Configuration Checker.
- Check the box next to SSONChecker and click Run.
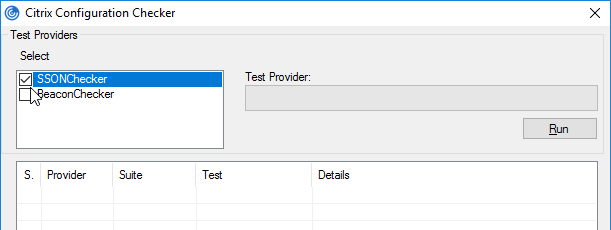
- The lines with red x will indicate the issue and corrective action.
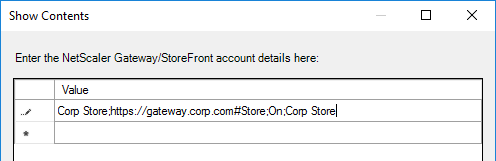
StoreFront Accounts
You can use a client-side GPO to add a store (Account) to Workspace app Self-Service.
- Install the receiver.admx (and .adml) template into PolicyDefinitions if you haven’t already.
- Edit a GPO that applies to endpoint devices that have Citrix Workspace app installed.
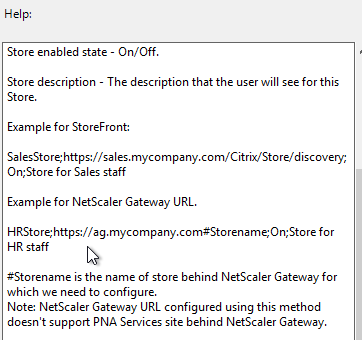
- Go to Computer Configuration > Administrative Templates > Policies > Citrix Components > Citrix Workspace > StoreFront.
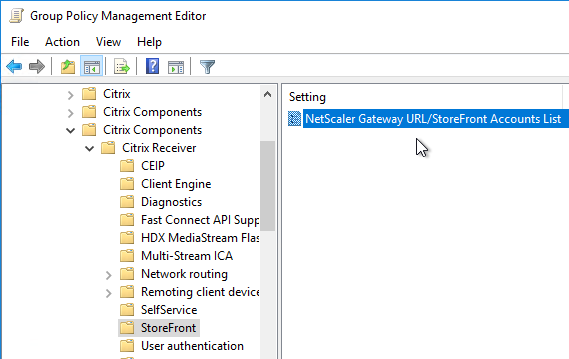
- On the right, double-click NetScaler Gateway URL/StoreFront Accounts List.
- Select Enabled, and then click Show.
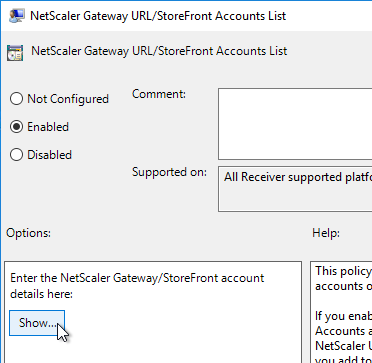
- Enter a store path based on the example shown in the Help box. Workspace app lets you enter a Gateway path. Then click OK.
- Note: Gateway paths work in GPO, but might not work when specified in the CitrixWorkspaceApp.exe installation command line.
Published Shortcuts and Reconnect
Citrix CTX200924 How to Customize App Shortcuts with Receiver for Windows
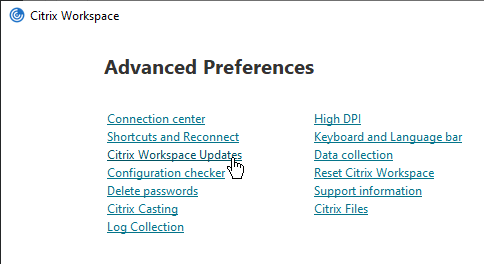
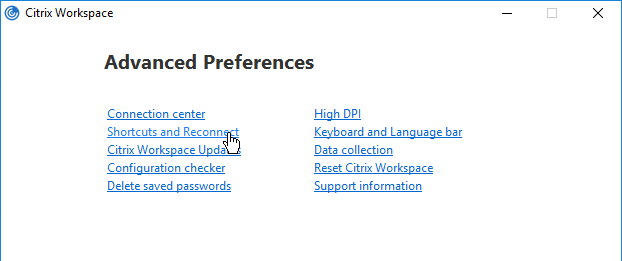
Workspace app has a user interface for setting Shortcut Paths. Right-click the Workspace app systray icon, click Advanced Preferences, and then click Shortcuts and Reconnect, or Settings Option.
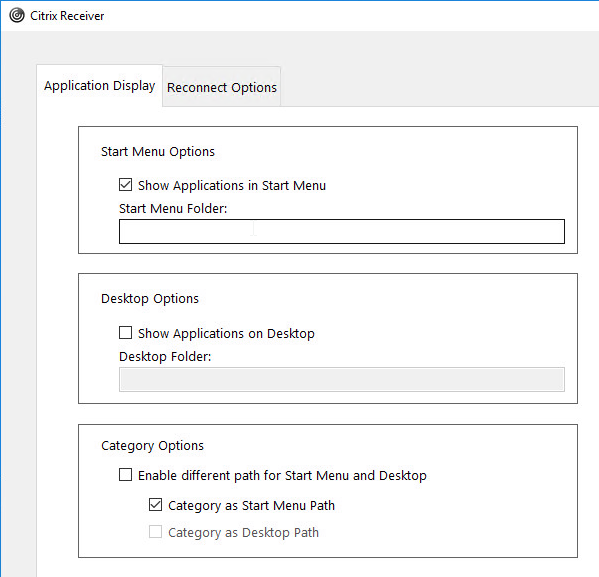
From Citrix Docs Configuring application delivery: There are several methods of controlling how Workspace app displays shortcuts on the Start Menu and Desktop as detailed below:
- Workspace app Registry values
- receiver.admx GPO Template
- From StoreFront in C:\inetpub\wwwroot\Citrix\Roaming\web.config
- Published App Keywords (e.g. prefer).
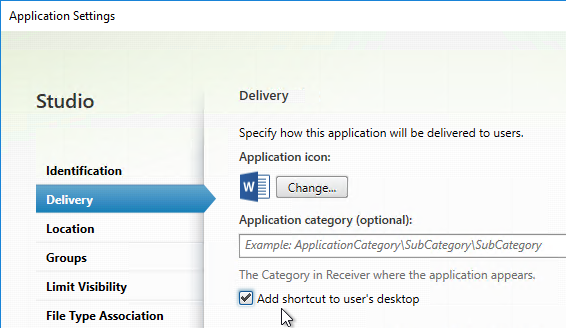
- Workspace app and Receiver 4.2.100 and newer supports published app Delivery configuration for adding the shortcut to the desktop. This only works if the app is a Favorite, or if Favorites are disabled, or Mandatory Store.
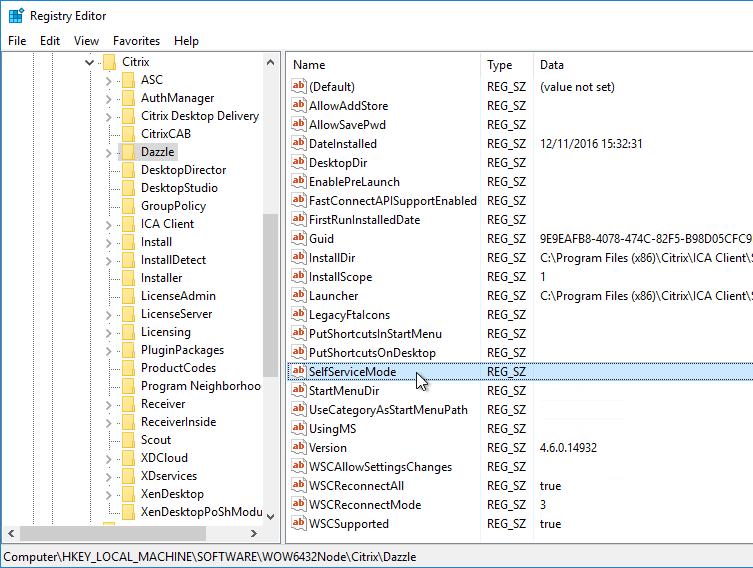
Under HKLM\Software\Wow6432Node\Citrix\Dazzle (or HKCU\Software\Wow6432Node\Citrix\Dazzle) are several registry values related to shortcuts. Some of the settings only apply if SelfServiceMode is set to False. Here are some common options:
- SelfServiceMode – set to False so Receiver disables the Self-Service interface and automatically places all published shortcuts on the Start Menu and/or Desktop. More details in Configuring application delivery at Citrix Docs.
- PutShortcutsOnDesktop – set to True to place every app on the desktop
- DesktopDir – Workspace app places every shortcut on the desktop so it’s probably best to place them in a folder.
- StartMenuDir – If there is potentially a conflict between local apps and remote apps, then you should place the Start Menu shortcuts in a folder.
- PreferTemplateDirectory (with KEYWORDS:prefer=shortcutname) – copies the shortcutname from the template directory to the Start Menu and/or Desktop.
If you import the receiver.admx (and .adml) into the PolicyDefinitions folder, under Computer Configuration > Administrative Templates > Citrix Components > Citrix Workspace (or Receiver) is a node called SelfService.
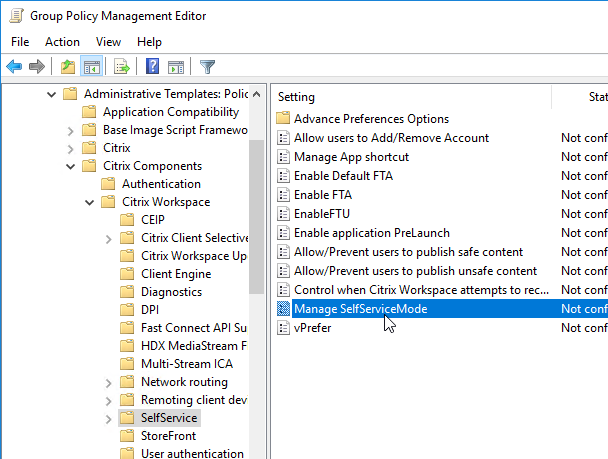
Disable the Manage SelfServiceMode setting to hide the Workspace app Window.
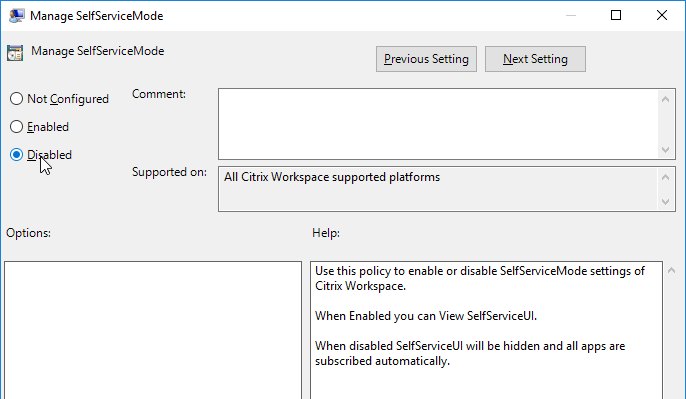
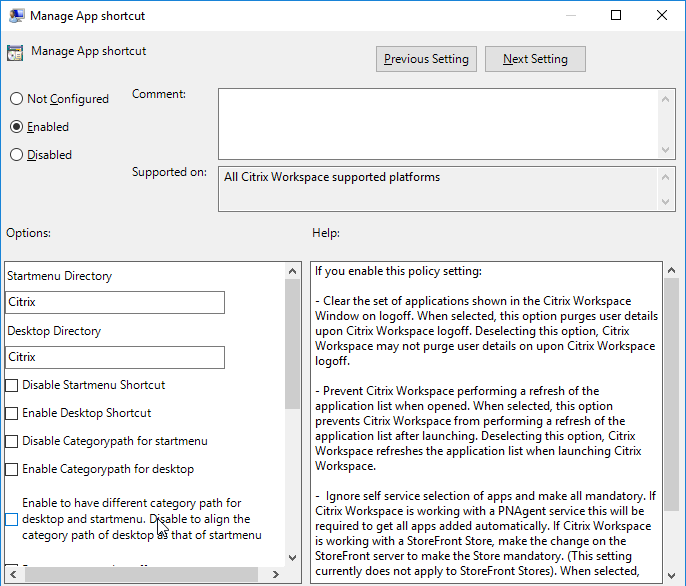
Enable the Manage App shortcut setting to control placement of shortcuts.
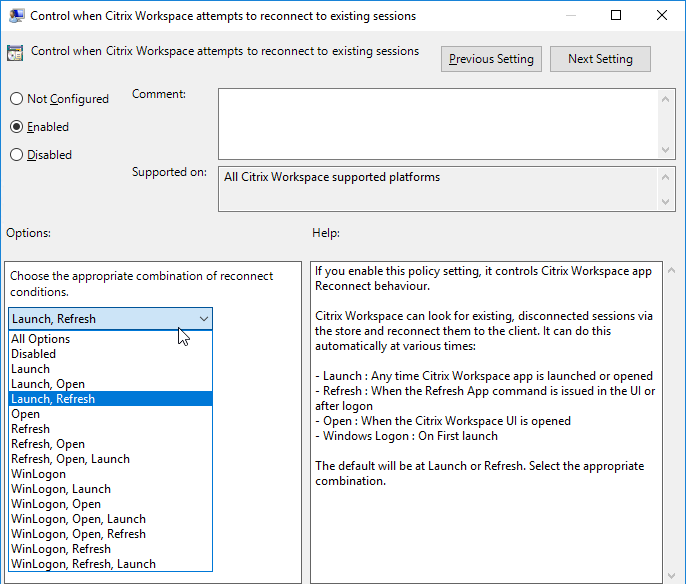
Workspace app and Receiver 4.2.100 and newer have the ability to configure (or disable) Workspace Control using group policy. Enable the setting Control when Citrix Workspace attempts to reconnect to existing sessions and configure it as desired.
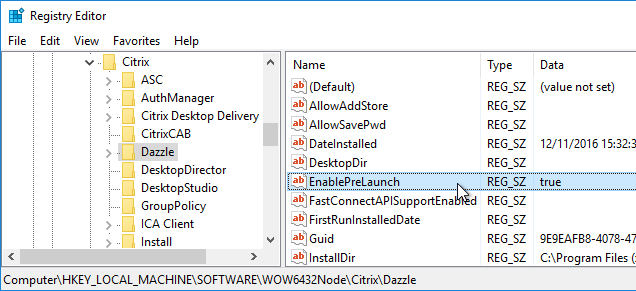
Prelaunch
Staring with Receiver 4.2, prelaunch is automatically enabled if Workspace app is installed with SSON enabled. Otherwise, set registry values to enable prelaunch. Receiver 4.2.100 prevents the prelaunch icon from appearing on the Start Menu.
- HKLM\Software\[Wow6432Node\]Citrix\Dazzle
- EnablePreLaunch (REG_SZ) = true or false
Additional customizations can be configured at:
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\ICA Client\Prelaunch
- Name: State
- REG_SZ: 0 = disable, 1 = just-in-time pre-launch, 2 = scheduled pre-launch
- Name: Schedule
- REG_SZ: HH:MM|M:T:W:TH:F:S:SU where HH and MM are hours and minutes. M:T:W:TH:F:S:SU are the days of the week. For example, to enable scheduled pre-launch on Monday, Wednesday, and Friday at 1:45 p.m., set Schedule as Schedule=13:45|1:0:1:0:1:0:0 . The session actually launches between 1:15 p.m. and 1:45 p.m.
- Name: UserOverride
- REG_SZ: 0 = HKLM overrides HKCU, 1 = HKCU overrides HKLM
Device Access Behavior (Client Selective Trust)
When connecting to a XenApp/XenDesktop session, you might see the following:
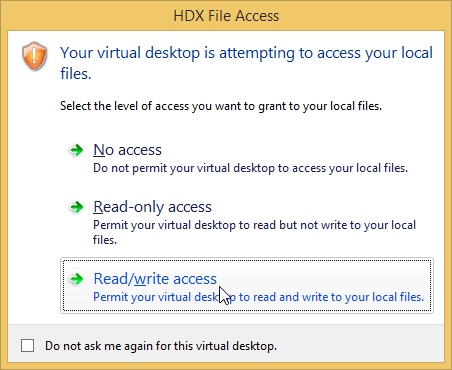
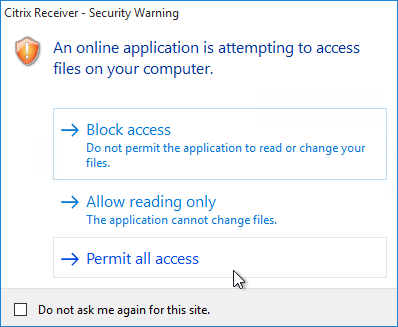
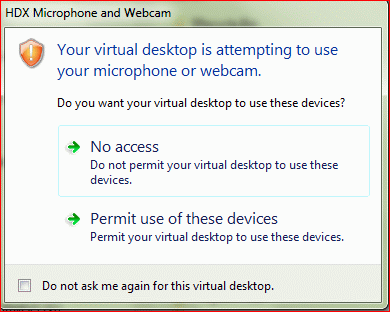
To configure the default behavior, see the Citrix Knowledgebase article How to Configure Default Device Access Behavior of Receiver, XenDesktop and XenApp. Note: there is a bug fixed in Receiver 4.2.100 and newer.
- Download the ADMX file from http://support.citrix.com/article/CTX133565.
- Copy the .admx and .adml files to PolicyDefinitions (Sysvol, or C:\Windows).
- The .adml file goes in the en-US folder.
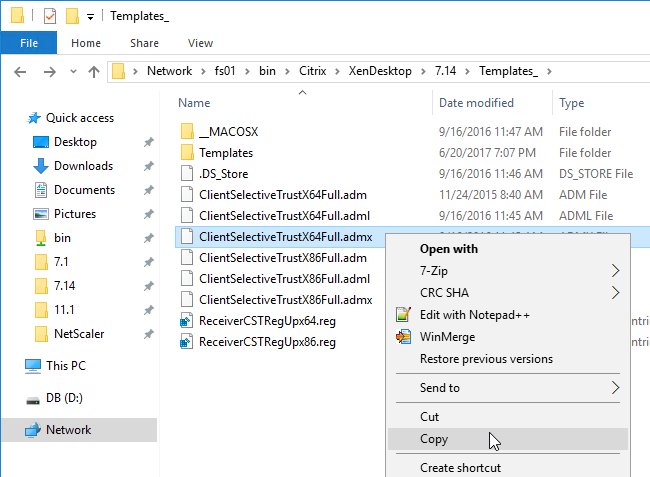
- Edit a GPO that applies to the endpoint devices that are running Receiver.
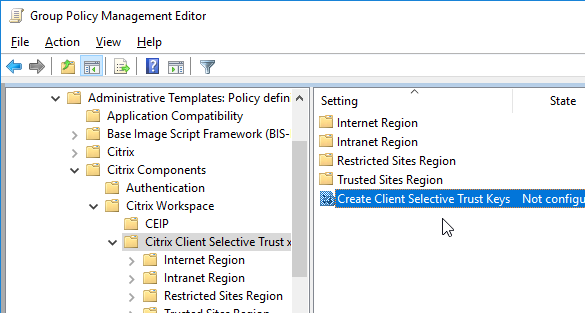
- Go to Computer Configuration | Policies | Administrative Templates | Citrix Components | Citrix Workspace (or Receiver) | Citrix Client Selective Trust (x64).
- Enable the setting Create Client Selective Trust Keys.
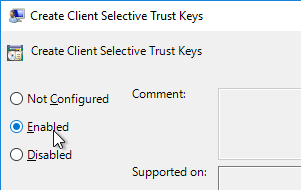
- Then expand the regions, and configure the permission settings as desired.
Desktop Lock
As an alternative to Workspace app Desktop Lock, see Transformer in Citrix Workspace Environment Manager.

External links:
- Dale Scriven YouTube video – Citrix Desktop Lock installation and configuration
- Jarian Gibson and Andrew Morgan – Citrix Receiver Desktop Lock
- An alternative to Desktop Lock – ThinKiosk
Use Studio to configure Workspace app Accounts in Published Desktop
In published desktops, Workspace app can be used for placement of shortcuts on the user’s Start Menu and Desktop. Use group policy to hide the common program groups and then use Workspace app to place published applications back on the Start Menu and Desktop based on user’s group membership and subscription preference.
- In Citrix Studio, on the left, expand the Configuration node, right-click StoreFront and click Add StoreFront.
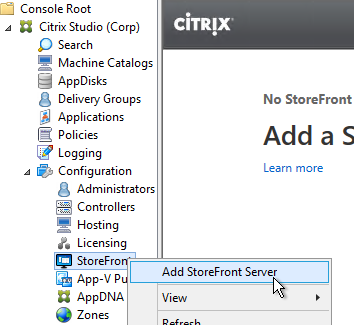
- Enter a descriptive name for the StoreFront server.
- Enter the internal https URL of the load balanced StoreFront servers. Add the path to your store (e.g. /Citrix/Store) and then /discovery on the end of the URL. The full URL would be similar to https://citrix.corp.com/Citrix/Store/discovery. Click OK.
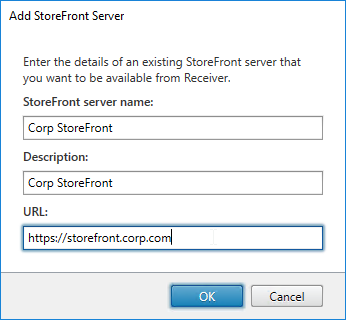
- Edit a Delivery Group that has a published desktop and Citrix Workspace app installed.
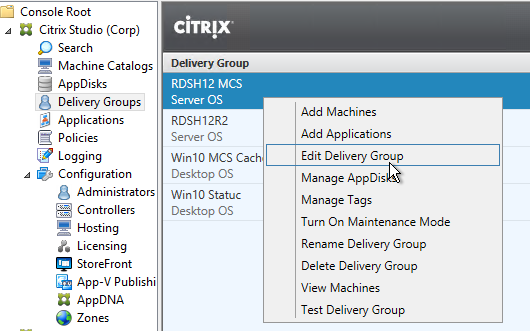
- On the StoreFront page, change the selection to Automatically, using the StoreFront servers selected below, and then check the box next to the StoreFront URL. Click OK. Now when users launch the published desktop, Workspace app will be automatically configured with this URL.
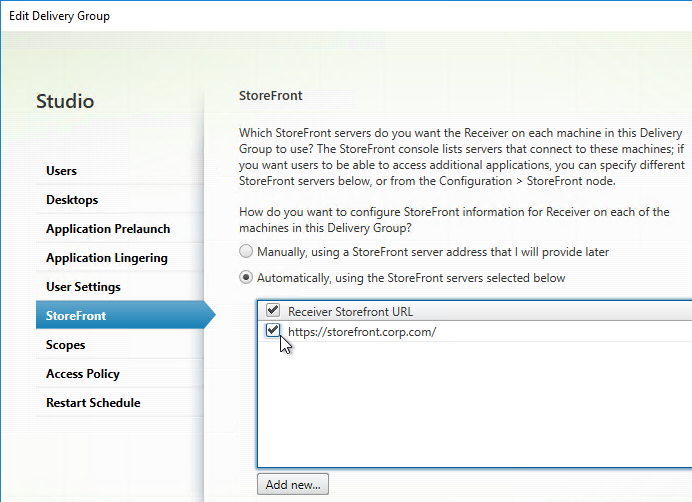
Published Desktop – use Workspace app to control Shortcuts
If you install Workspace app inside a published desktop (Workspace app on a VDA), then Workspace app can get icons from StoreFront and put those icons on the user’s published desktop Start Menu and Desktop. This is an alternative to using a User Experience Management product to control shortcut placement.
Note: Workspace app tends to be slow to create Start Menu shortcuts, so make sure you perform a Proof of Concept to determine how this functionality impacts logon times.
Configuration of Workspace app inside a published desktop is simplified if you have the following minimum versions:
- Workspace app installed inside the VDA
- VDA 7.17 or newer
- StoreFront 3.14 or newer
If you meet these minimum version requirements, then Workspace app installed in the VDA automatically tries to launch published applications on the same local VDA rather than trying to launch them from a different VDA (aka double-hop). This feature is called vPrefer.
- If you don’t meet these minimum version requirements, then you’ll need to use the older Prefer Keyword method of handling Workspace app shortcuts as detailed later.
- For a detailed explanation of vPrefer, see Citrix Blog Post VPrefer: Session Sharing Between a Published Desktop and a Published Application Made Easy
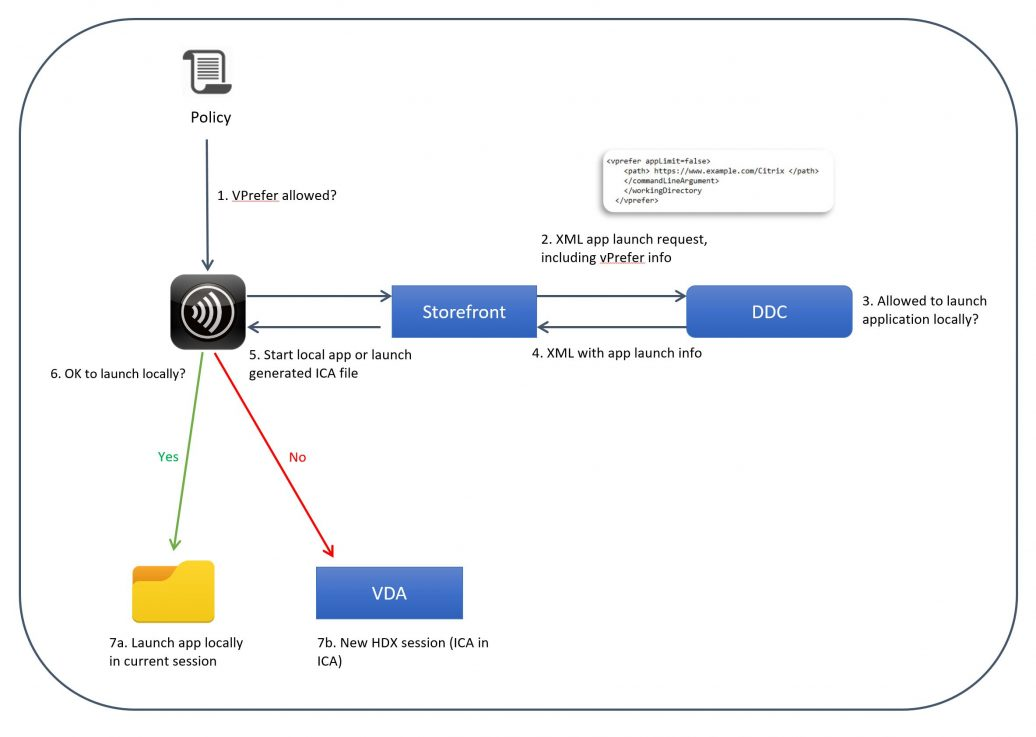
Do the following for all versions of Workspace app, VDA, and StoreFront, whether using the Prefer keyword or not:
- Make sure Workspace app or Receiver version 4.11 or newer is installed on the VDA.
- Install the Workspace app ADMX files if you haven’t already. For vPrefer, make sure they are the ADMX files from Workspace app.
- Enable the Group Policy setting Remove common program groups from Start Menu and apply it to non-administrators.
- This removes all Public (aka All Users) Start Menu shortcuts. Workspace app will re-add the shortcuts based on user group membership.
- On the VDA, configure the following Workspace app Registry keys (or corresponding settings in the receiver.admx GPO template):
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\WSCReconnectMode=”0″ so Workspace app doesn’t try to reconnect to the published desktop you’re already running.
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\SelfServiceMode to False. This turns off the Workspace app Self-Service GUI and acts like all icons are subscribed. Otherwise, only subscribed (favorited) icons would be placed on the Start Menu and Desktop.
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\UseCategoryAsStartMenuPath = True. This creates a Start Menu folder based on the published app’s configured Category.
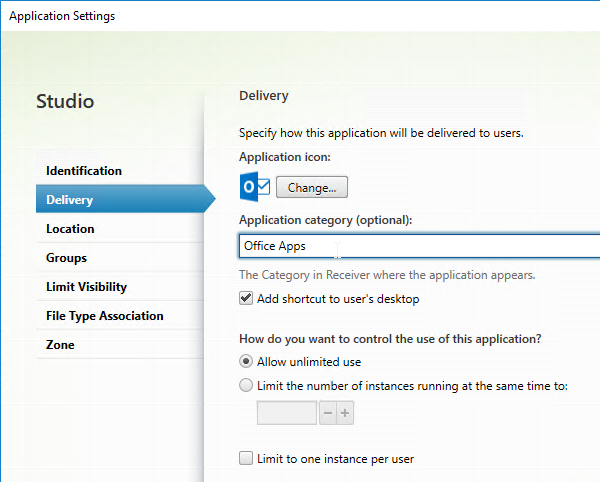
- Configure each desired published app to Add shortcut to user’s desktop.
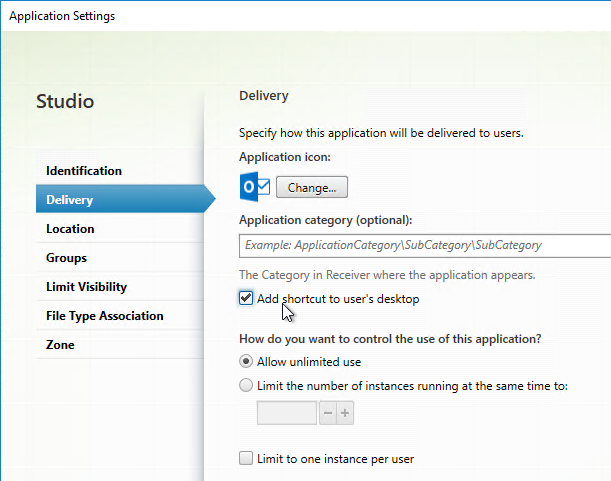
- Or, configure HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\PutShortcutsOnDesktop = True to place all icons on the desktop.
- To control icon placement, configure the following registry values:
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\StartMenuDir to place published applications in a sub-folder. Note: Windows Server 2012 and Windows 10 and newer only supports a single level of Start Menu folders, so setting this effectively turns off published app categories.
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\DesktopDir to place published applications in a sub-folder on the desktop.
- Pass-through authentication:
- In a GPO that applies to the VDA, import the receiver.admx file, and set Local user name and password to Enabled. Check the box next to Allow pass-through authentication for all ICA connections.
- If you’re using Gateway internally, and if Workspace app 1808 or newer, then also enable Single Sign-on for NetScaler Gateway.
- In a user-level GPO that applies to the VDA, add the StoreFront FQDN to the Local Intranet zone. Make sure it is not in the Trusted Sites zone, or enable Automatic logon with current user name and password for the Trusted Sites zone.
- Make sure ssonsvr.exe is running after you login to the VDA. If not, troubleshoot it.
- When configuring Citrix Profile Management, make sure !ctx_startmenu! is not excluded from roaming.
- In Citrix Studio, configure a Delivery Group with delivery type = Desktop and Applications. Assign users to the delivery group, and the individual published applications (if visibility is limited).
- In Citrix Studio, edit each published application, and on the Delivery tab, specify a category. This will become the Start Menu folder name.
- If Workspace app Self Service Mode (GUI) is enabled, in Studio, edit each application, and add KEYWORDS:Auto and/or KEYWORDS:Mandatory to the published application description. This forces the applications to be subscribed/favorited. Only subscribed (or Favorite) apps are displayed in the Start Menu and Desktop. Unless you disable Workspace app’s SelfService interface as described earlier.
- Another option is to go to the StoreFront Console, click Stores on the left, and on the right, click Configure Store Settings, and click Disable User Subscriptions. This causes all apps to appear on the Start Menu and/or Desktop depending on Workspace app configuration.
- Create a group policy that applies to VDAs, and configure the group policy to define the Store URL for Workspace app similar to https://citrix.corp.com/Citrix/Store/discovery. Replace the FQDN with your load balanced StoreFront FQDN. Also replace the path to the store with your store path. Make sure there is /discovery on the end. By default, Workspace app and Receiver only support https.
- Your StoreFront store probably delivers both application and desktop icons. If you want to filter out the desktop icons, then create a new StoreFront store, and configure the Workspace app on the VDA to connect to the new Store.
- In StoreFront Console, click the store for VDAs, and click Configure Store Settings. On the Advanced Settings page, in the Filter resources by type row, choose Citrix.MPS.Desktop.
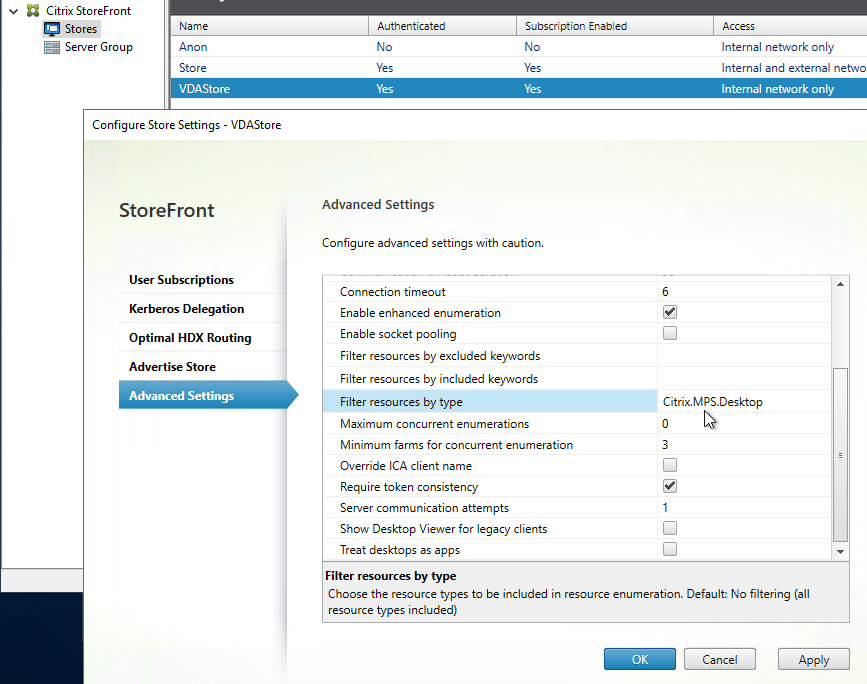
- For vPrefer in Workspace app, VDA 7.17 (or newer), and StoreFront 3.14 (or newer), edit a GPO that applies to the VDAs.
- Go to Computer Configuration | Policies | Administrative Templates | Citrix Components | Citrix Workspace (or Receiver) | SelfService.
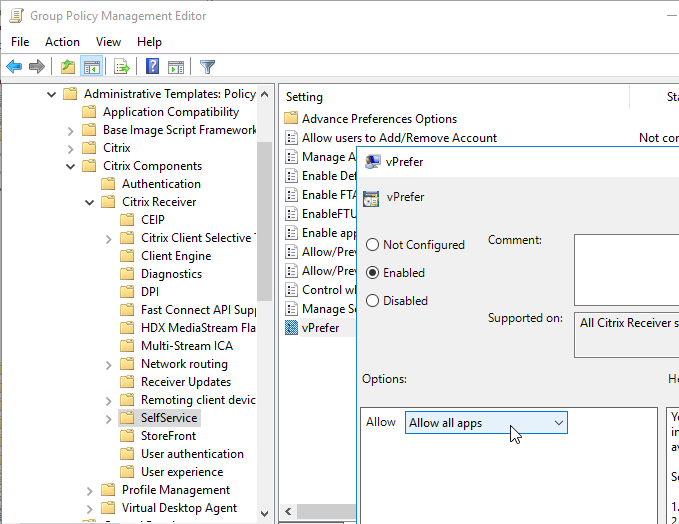
- Edit the setting vPrefer. This setting is only in Workspace app ADMX templates from Workspace app.
- Set it to Allow all apps. Source = 7.17 vPrefer – not working with 32Bit Apps at Citrix Discussions.
- On your Delivery Controller, in PowerShell, run set-brokersite -TrustRequestsSentToTheXmlServicePort $true
- This is required for Pass-through Authentication from Workspace app.
- Configure your client devices to connect to the published desktop.
- When users connect to the published desktop, Workspace app will auto-launch and hopefully auto-login.
- If Workspace app Self-Service Mode is disabled, all published applications should automatically appear in the Start Menu and Desktop.
- If Workspace app Self-Service Mode is enabled, then only applications with KEYWORDS:Auto and/or KEYWORDS:Mandatory in the published application description will be displayed. Users can open the systray icon to subscribe to more applications.
- Users can copy icons from the Start Menu to the desktop. Make sure the user Copies the icon and doesn’t Move it.
- Users can then launch applications directly from the Start Menu, from the Desktop, or from the Workspace app (if the Self-Service interface is enabled).
- If Workspace app 4.11 (or newer), VDA 7.17 (or newer), and StoreFront 3.14 (or newer), then vPrefer is enabled by default. When launching an app icon that came from Workspace app, Workspace app checks the local VDA machine to see if the application can be launched on the local VDA instead of by creating a new Citrix double-hop session.
- If the application is installed locally on the VDA then the local application shortcut should launch quickly. If the application is on a different delivery group then a second (double-hop) Citrix HDX/ICA connection will be established.
- If the user deletes Workspace app shortcuts from the Start Menu, you can get them back by going to the systray icon and refreshing the applications. Or sometimes you have to reset Workspace app.
If you are running components older than Receiver 4.11, VDA 7.17, and StoreFront 3.14, then you’ll need to configure the prefer keyword to get Receiver delivered icons to launch on the local VDA instead of in a new double-hop Citrix connection.
- Enable the Group Policy setting Remove common program groups from Start Menu and apply it to non-administrators.
- For applications that are installed on the same VDA that is publishing the desktop, configure Group Policy Preferences to recreate the application shortcuts based on Active Directory group membership. Applications on other delivery groups are handled by Receiver.
- Or use the prefer keyword to copy shortcuts from the PreferTemplateDirectory.
- On the VDA, configure the following Receiver Registry keys (or corresponding settings in the receiver.admx GPO template):
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\PreferTemplateDirectory = a UNC path or local path containing shortcuts to be copied by the prefer keyword. This can point to C:\ProgramData\Microsoft\Windows\Start Menu.
- In Citrix Studio, configure a Delivery Group with delivery type = Desktop and Applications. Assign users to the Delivery Group and the applications (if visibility is limited).
- In Studio, edit each application and change KEYWORDS:Prefer to KEYWORDS:prefer. Notice the lower case p. It doesn’t work with uppercase P.
- With the prefer keyword, if you publish an application that is also created using Group Policy Preferences, the Group Policy Preferences icon will take precedence. This is good. Otherwise the Receiver published application icon would result in a new Citrix double-hop session.
- See Ralph Jansen Citrix Receiver 4.1 Prefer keyword examples
- If using the prefer keyword with the PreferTemplateDirectory, enter it as KEYWORDS:prefer=shortcutname where shortcutname is the name of the shortcut that is copied from the Template directory.
- In Studio, edit each application and change KEYWORDS:Prefer to KEYWORDS:prefer. Notice the lower case p. It doesn’t work with uppercase P.
- Configure your client devices to connect to the published desktop.
- When users connect to the published desktop, Group Policy Preferences will create shortcuts to local applications.
- Receiver will auto-launch and hopefully auto-login.
- If Receiver Self-Service Mode is disabled, all published applications should automatically appear in the Start Menu and Desktop.
- If Receiver Self-Service Mode is enabled then only applications with KEYWORDS:Auto and/or KEYWORDS:Mandatory in the published application description will be displayed. Users can open the systray icon to subscribe to more applications.
- For published applications with KEYWORDS:prefer=shortcutname, Receiver should copy icons from the template directory to the Start Menu and/or Desktop. See below for considerations.
- Users can copy icons from the Start Menu to the desktop. Make sure the user Copies the icon and doesn’t Move it.
- Users can then launch applications directly from the Start Menu, from the Desktop, or from the Receiver (if Self-Service interface is enabled).
- If a local shortcut (e.g. Group Policy Preferences shortcut, or copied from template directory) matches a published application with KEYWORDS:prefer then the local shortcut will override the published application icon.
- If the application is installed locally on the VDA then the local application shortcut should launch quickly. If the application is on a different delivery group then a second (double-hop) Citrix HDX/ICA connection will be established.
- If the user deletes Receiver shortcuts from the Start Menu, you can get them back by going to the systray icon and refreshing the applications. Or sometimes you have to reset Receiver.
Notes regarding Prefer Template Directory
- Prefer Template Directory can point to C:\ProgramData\Microsoft\Windows\Start Menu, which is the All Users Start Menu.
- The shortcuts copied from the Prefer Template Directory are renamed to match the published app name.
- For prefer local apps, any command line parameters specified in the published app are ignored. If you need these command line parameters, add them to the shortcut in the Prefer Template Directory.
- If you have multiple published apps pointing to the same prefer local shortcut, then only one copy will be made, and it will have the name of only one of the published apps. To workaround this, in the Prefer Template Directory, create separate shortcuts for each published app, and adjust the published app prefer keyword accordingly.
- Jan Hendrik Meier Automatic Shortcut generation for local installed applications in a Citrix XenDesktop / XenApp 7.x environment has a script that can create shortcuts based on the published apps with prefer keyword. These shortcuts can then be copied to your Prefer Template Directory.
How to Script/Automate Workspace app and Receiver Self-Service
From Citrix Knowledgebase article Driving the Citrix Receiver Self-Service Plug-in Programmatically: by default, Workspace app Self-Service (SSP) activities are driven by user interaction. However, SSP exposes sufficient information for its activities to be scripted.
When SSP builds a shortcut, it builds it to a small stub application in a file %appdata%\Citrix\SelfService\app-name-with-spaces-removed.exe for each resource. These files allow SSP to create a fake ‘install’ record for Add/Remove Software. Running these .exe files causes the application to launch. Note: Workspace app and Receiver 4.3.100 and newer don’t create stubs by default. To enable, set HKLM\Software\Wow6432Node\Citrix\Dazzle\AlwaysUseStubs (REG_SZ) = true.
If you want to drive SSP directly for launch instead of through an .exe stub, look at the keys under HKCU\Software\Microsoft\Windows\CurrentVersion\Uninstall. There will be keys in there named farm-name@@server-farm-name.app-friendly-name. In these keys you’ll find a LaunchString value that shows the relevant parameters. These parameters are user-independent and can therefore be cloned from a reference user to a general case. You can copy and reuse these parameters without interpretation.
Running the command selfservice.exe –init –ipoll –exit starts SSP, performs a refresh (interactive poll) from the current provider, and forces a clean exit.
Additional command line parameters are detailed at Driving the Citrix Receiver Self-Service Plug-in Programmatically.
Citrix Workspace app come with a .dll file that implements the Citrix Common Connection Manager SDK. You can use the CCM SDK to do the following:
- Launch Sessions
- Disconnect Sessions
- Logoff Sessions
- Get Session Information
Citrix was kind enough to develop a PowerShell module that calls functions from the .dll. Get the CCMPowershellModule from Github. The PowerShell module contains functions like the following:
- CCMTerminateApplication
- CCMLaunchApplication
- CCMGetActiveSessionCount
- CCMDisconnectAllSessions
Launcher Scripts
Ryan C Butler Storefront ICA file creator at Github. See Create an ICA File from Storefront using PowerShell or JavaScript for more info.
Stan Czerno – Powershell Script to launch one or more Published Applications from Citrix Storefront 2.x through 3.11: the script launches a browser, connects to StoreFront (or NetScaler Gateway), logs in, and launches an icon. This is a very well-written script that uses a .dll file from Citrix Workspace app to display session information.
Citrix Solutions Lab StoreFront Launcher Script at Github. It attempts to closely resemble what an actual user would do by:
- Opening Internet Explorer.
- Navigating directly to the Receiver for Web site or NetScaler Gateway portal.
- Completing the fields.
- Logging in.
- Clicking on the resource.
- Logging off the StoreFront site.
David Ott StoreFront App/Desktop Launch Testing Script uses Internet Explorer to login to StoreFront and launch a resource. Sends email with the result. Uses wficalib.dll to get session information.
Microsoft Teams
Citrix and Microsoft jointly support the delivery of Microsoft Teams from Citrix Virtual Apps and Desktops using optimization for Microsoft Teams. The Teams optimization components are built into VDA and Workspace app. There is no need to install anything separately. The feature is based on Browser Content Redirection so don’t exclude that feature when installing the VDA.
Microsoft Teams optimization/offloading requires the following:
- Newest version of Microsoft Teams machine-wide installation (ALLUSER=1)
- Newest version of Citrix VDA
- Newest version of Citrix Workspace app.
Feature matrix and version support at Citrix Docs shows the required versions of Teams, Citrix VDA, and Citrix Workspace app for various Teams features.
See Citrix Docs Optimization for Microsoft Teams.
Troubleshooting – Citrix QuickLaunch
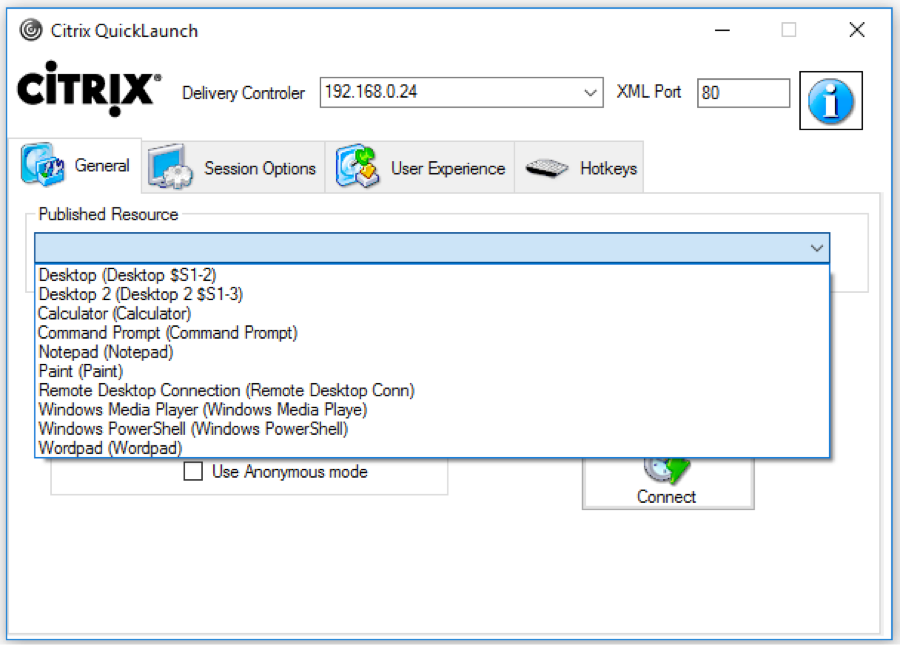
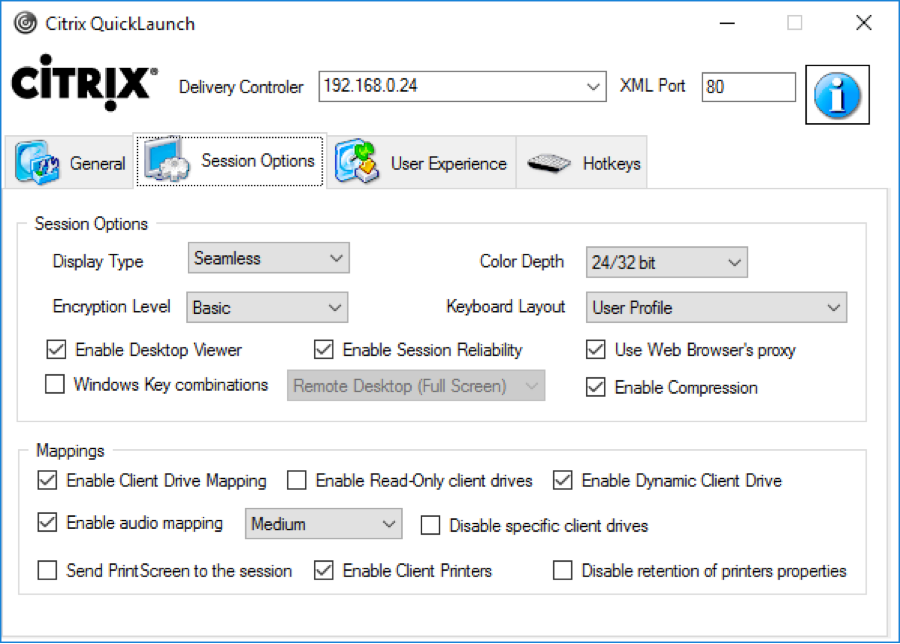
Citrix CTX219718 QuickLaunch Tool (Testing Application and Desktop Launch) lets you launch Citrix sessions directly from a Controller without needing StoreFront.
You enter a Controller address, credentials, and then it shows you the published resources. You can pick a resource, edit properties on the other tabs, and then Connect. This allows you to easily try different connection properties.
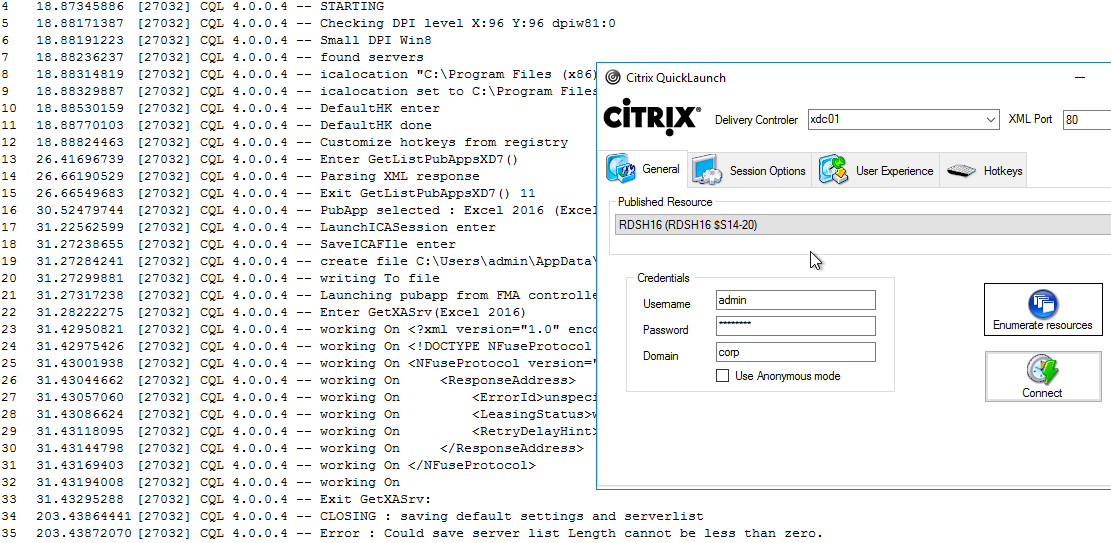
If you run into problems launching a session, use Sysinternals DebugView while running CQL in Debug mode (/debug switch).
Troubleshooting – Workspace app Logging
In Workspace app 2309 and newer, if you right-click the Workspace app icon in the system tray, there’s a Troubleshooting menu with a Collect Logs option.
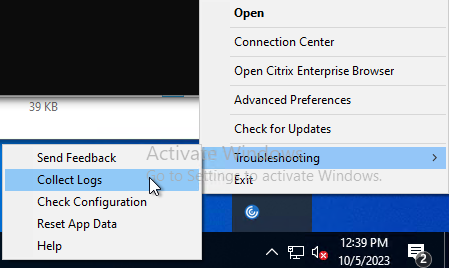
You can also access Log Collection from Advanced Preferences.
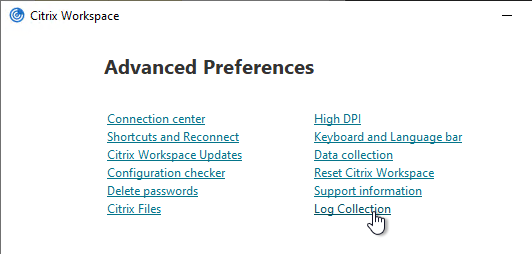
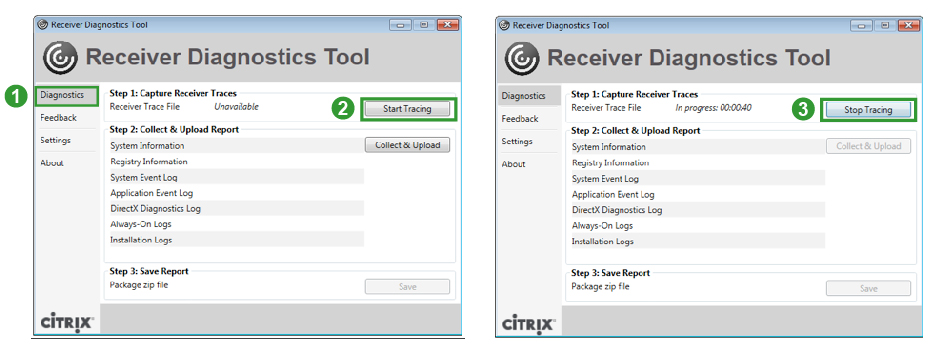
There are a couple methods of logging Workspace app for Windows operations. One method is CTX141751 Citrix Receiver Diagnostics Tool – For Windows, which creates a CDF trace that can be parsed by CDFControl.
Another method is CTX132883 How to Enable Logging on Receiver for Windows Using Registry Entries. The logfiles in %USERPROFILE%\Appdata\Local\Citrix\ are human readable. And CTX206102 Enable SSON Logging Using Registry Key.
Instead of creating the registry keys manually, you can use the following .reg file provided by Wolfgang Thürr:
Windows Registry Editor Version 5.00 ;only for x64 windows os ;import with admin rights ;restart your computer to activate the logging and tracing settings ;create C:\TEMP for the launch ICA log and SSON logn (no environment variables can be used) ;general Workspace app and Receiver logging ;************************ ;logpath: %USERPROFILE%\Appdata\Local\Citrix\Receiver [HKEY_LOCAL_MACHINE\SOFTWARE\ Wow6432Node\Citrix] " ReceiverVerboseTracingEnabled" =dword:00000001 ;Authentication Manager logging ;***************************** * ;logpath: %USERPROFILE%\Appdata\Local\ Citrix\AuthManager [HKEY_LOCAL_MACHINE\SOFTWARE\ Wow6432Node\Citrix\ AuthManager] "LoggingMode"="verbose" "TracingEnabled"="True" "SDKTracingEnabled"="True" ;Self Service logging ;******************** ;logpath: %USERPROFILE%\Appdata\Local\ Citrix\SelfService [HKEY_LOCAL_MACHINE\SOFTWARE\ Wow6432Node\Citrix\Dazzle] "Tracing"="True" "AuxTracing"="True" "DefaultTracingConfiguration"= "global all –detail" ;save launch ICA ;*************** ;logpath: C:\TEMP\ica.log (no environemnt variables allowed) [HKEY_LOCAL_MACHINE\SOFTWARE\ Wow6432Node\Citrix\ICA Client\Engine\Configuration\ Advanced\Modules\Logging] "LogConfigurationAccess"=" true" "LogConnectionAuthorisation"=" true" "LogEvidence"="true" "LogICAFile"="true" "LogFile"="C:\\TEMP\\ica.log" "LogStartup"="true" ;Receiver Always On Tracing ;************************** ;generates ETL Files for analyzing with CDFControl see CTX111961 for details ;can be configured or overruled by GPOs (icaclient.admx) ;path %USERPROFILE%\AppData\Local\ Temp\CTXReceiverLogs [HKEY_LOCAL_MACHINE\SOFTWARE\ Policies\Citrix\ICA Client\AoLog] "EnableTracing"=dword:00000001 ;Single Sign-on Logging ;************************** ;https://support.citrix.com/article/CTX206102 [HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Install\SSON] "DebugEnabled"="true" "LogPath"="C:\\Temp"
Troubleshooting – Duplicate Stores
Stores are sometimes duplicated in Workspace app, especially if you are running Workspace app inside a VDA. (h/t Dan High)
StoreFront URLs can be defined in several places:
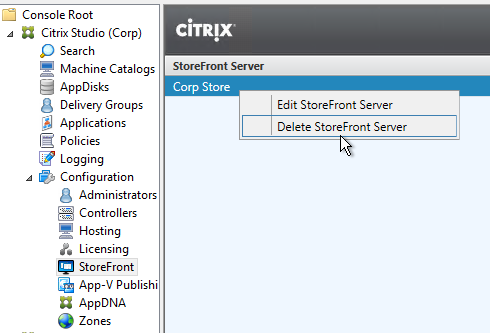
- In Studio, go to Configuration > StoreFront and delete all URLs configured here.
- Look in GPOs for Computer Configuration > Administrative Templates > Policies > Citrix Components > Citrix Workspace > StoreFront > NetScaler Gateway URL/StoreFront Accounts List. Remove any URLs configured here.
- In the client-side registry, at HKLM\Software\Wow6432Node\Citrix\Dazzle\Sites, you might see store addresses that were specified during a command line installation of Workspace app.
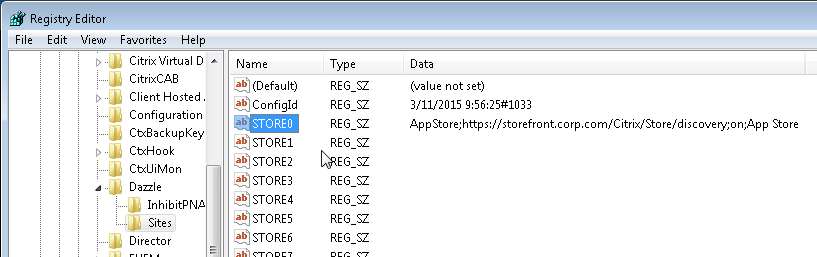
- When Citrix Workspace app switches between StoreFront servers in multiple datacenters, it’s possible for each datacenter to be treated as a separate Workspace app site. This can be prevented by doing the following. From Juan Zevallos at Citrix Discussions:
- Match the Base URL in all datacenters.
- Match the SRID in all datacenters – The SRID can be safely edited in the C:\inetpub\wwwroot\Citrix\Roaming\web.config. Make sure to propagate changes to other servers in the group.
- Match the Delivery Controller names under “Manage Delivery Controllers” – The XML brokers can be different, but the actual name of the Delivery Controller/Farm must be identical.
If you are running Workspace app on a VDA, once you’ve removed the configured URLs shown above, do the following to clean up the VDAs:
- On the VDA, HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Citrix – Delete the number folders representing policy entries.
- On session host VDAs, HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Terminal Server\Install\Software\Citrix – Remove the entries for storefront in the following folders.
- Under \receiver\ctxaccount delete all entries.
- Under \SR\Store delete the entries.
- On the VDA, C:\ProgramData\CitrixCseCache – Delete all files
- On the VDA, C:\ProgramData\Citrix\GroupPolicy – Delete all folders and files.
- Run gpupdate and logoff.
- In the user’s registry, HKEY_CURRENT_USER or the profile registry hive. Possible profile reset.
- Under Software\Citrix\Dazzle\Sites – Delete all entries.
- Under Software\Citrix\Receiver\ctxaccount – delete all entries.
- Under Software\Citrix\SR\Store – delete the entries.
- Verify no cached profile folders for user on server.
Hi there,
Has anyone tried importing ADMX files into Intune and creating a policy that also includes Citrix settings? I can successfully import the ADMX files (Windows and CitrixBase, both “us”) and create a new policy (import Administrative Templates), but when creating a policy, the Citrix settings don’t appear.
Does anyone have a tip or solution? Thanks
You also need to import the reciever.admx files.
It seems the CitrixBase doesn’t contain any settings it needs the other admx files as well.
Hi James,
the receiver.admx cannot imported (Version from 10.1.2025, download from Citrix):
Intune Error: The method or operation is not implemented
i found this with link to Github, but is 3 Years old…think it is old.
https://www.reddit.com/r/Intune/comments/x6bzel/admx_import_failure_citrix_workspace/
than i found a site, the are write vom “combobox” in the admx, but there isn’t.
i think thats is not my/our task to troubleshoot problems from MS or Citrix, or? 😉
another Workaround?
Thanks for help.
Hello Carl
I have install citrix workspace for user under my admin privilege’s id, however when user login and access the VDI/Desktop it is not launching and I can see the background there is workspace install again under their profile and request for reboot. They can access VDI after install completed. Any other way ca we install for all users/any user access.
Hi carl,
I am having an issue accessing apps or VDI desktop via citrix workspac.
I am not able to see anything , however I am able to see if I login via url.
please advice.
Hello,
What is the procedure to start CWA automatically, prompt for user authentication and then citrix VDI should launch automatically once user logged in to Win 11 desktop PC.
Thanks
See https://docs.citrix.com/en-us/citrix-workspace-app-for-windows/workspace-windows-desktop-lock.html
Hi Carl,
Will check and provide the feedback. Thanks
Hi Carl,
we recently upgraded many of our Workspace Installations, all working very well. But two clients can’t connect to the Storefront Server the Users becomming “Unable to connect to the server. Check your network connection and retry.” I’ve already tryed to Reset the Workspace App. Uninstall the Workspace and do an /cleaninstall reinstall. Nothing really helped. I’ve checked the User Registry, and I found something interesting under HKCU\Software\Citrix\Dazzle\Sites\storefront-[id] the REG_SZ serviceRecordID is the Value “dummySRIDhttps://[our right SF URL”. Did you have any hint what I could try to fix this problem.
Thank you very much
Sigi
If you right-click the blue systray icon, expand Troubleshooting, and click Collect Logs, the logs might tell you the issue. However, the logs can be esoteric and you might have to call Citrix Support to interpret them.
Hi,
I am trying to import citrix.admx in intune. i am getting error “Error – Details
The method or operation is not implemented”.”The upload of this ADMX file has failed. To continue, you will need to delete this upload, address the action in the error details and try again”.
I tried multiple citrix.admx which is available in Program Files (x86)\Citrix\ICA Client\Configuration.
Again downloaded https://www.citrix.com/downloads/workspace-app/workspace-app-for-windows-long-term-service-release/workspace-app-for-windows-LTSR-Latest.html.
same error.
Any workaround ?
Thanks
Ram
Hi,
My existing environment years ago preconfigured storefront URL with store name to Citrix Receiver https://LBstorefront.domain.local/Citrix/CitrixStoreWeb.
We deployed Citrix Gateway, new store and deployed GPO to push URL to endpoint Citrix Workspace App with Citrix Gateway FQDN https://cg.domain.local.
However, from the Citrix Workspace App > Account showing https://LBstorefront.domain.local/Citrix/CitrixNewStoreWeb << This is weird as the FQDN not change but the Store name got updated?
Accounts in Workspace App shows the internal name. But if you open Advanced Features in Workspace App you’ll see the Gateway name. See https://www.carlstalhood.com/workspace-app-for-windows/#discovery for more info.
Hi Carl,
Great article first of all. You’ve compiled so much info here which is awesome.
Do you have any experience updating Citrix workspace app to the latest version via Intune? I’ve deployed the client via SOE image when I’ve built laptops across my company, but some laptops are now running older versions due to the refresh cycle. Oldest would be from 2022.
Would I need to push out the latest version of the client with parameters through Intune? And would I need to uninstall the client first before installing the latest? Any help would be appreciated.
Workspace app has an auto-update feature.
If it’s disabled, then you’d need to push out an update. In-place upgrade usually works. Settings previously defined should still be there after upgrade. Use the prior install switches, especially if you’re deploying to new machines.
Hey there,
somehow we have two Terminalserver on which the SelfServicePlugin.exe lies in c:\Program Files (x86)\Citrix\online plugin\ICA Client instead of c:\Program Files (x86)\Citrix\ICA Client. Today we got a user session in which every application had a duplicate. Have of the apps directed to …\online plugin\ica client\selfserviceplugin.exe and the other half to …\ica client\selfserviceplugin.exe. We were never asked to define a path when installing Citrix Workspace. Is there an easy way to fix this?
Uninstall all clients and reinstall. That old path usually occurs when selecting Workspace app during VDA installation.
Client Selective Trust
Stale information about “templates.zip”. The Download is missing on https://support.citrix.com/article/CTX133565
Where do I get the admx templates for 2203 LTSR and newer?
After the Apply the LTSE 2402 I found one problem with .net 6.0, from my poing of view critical.
When .net is updated workspace is closed and reopened and you loose the session, where you are connected.
.net has updates every month.
Do you know how to solve this problem? Citrix has confirmed us that this problem exist.
Hi carl – read your updates around 2403 CR, I’m trying to get this working with sson in our environment but hitting some wierd hurdles. If i enable selfservice then it fails to authenticate properly into CWA, if i disable it then it does seem to authenticate and i get ALL cons into the start menu. Idealy i want this working like old versions whereby CWA works and only favourites are presented in start menu.
To complicate matters we use NetScaler as the access with SAML auth using ADFS, It feels like thats is where this is falling over. Citrix seem to have introduced some new secuirty features in this release and i have seen some posts indicating i’m not the only one in this boat 🙁
Does anyone have any idea on making a powershell script for restarting a citrix session based on an endploint? or a way to display session data in powershell based on an endpoint?
Hi Carl
Great updates to your blog as ever – you completely nailed it as the golden source for Citrix right now.
So, a question -I seem to be having a real issue with 2311.1 workspace with launching VM’s. This is a clean install of 2311.1 not an in place from a previous version.
It’s pretty random, and I see this more often when logging out of workspace and back in as another user, but I will get a permanent spinning wheel. Most of the time a client reset will work, (90%).
I also notice its likely to fail if the favourite icon hasnt turned yellow for a VM – generally if you click refresh here, it will populate. Then the VM launch will work.
Has anyone seen this behaviour?
With v23.11.1.140 (2311.1) of the Citrix Workspace App for Windows, I have several clients now having the ICA file download instead of the published desktop auto-loading as expected. I have confirmed that each of them has the Citrix Web extension installed. This seems to be happening with both Chrome and Edge…
Hi Carl, As usual a great article – very helpful 🙂
I’m doing some testin in prep for rolling out the latest CR version of the Workspace App.
There are a couple of things i want to remove from the system tray icon/right click menu for our users.
I found that the setting ‘Enable Citrix Enterprise Browser Shortcut’ = disabled will also remove the right click option from system tray icon, not just the start menu 🙂 so thats all good…
But I now need to find a way to hide the ‘Send Feedback’ option from our users. Been hunting around to trying to find a setting for this or any info online but I am coming up blank 🙁
Any idea how we can hide this?
thanks
An old error is back with the workspace app 2309/2311/2311.1.
Client to Server FTA is broken if the path contains a special Character (german umlaut).
The LTSR Version works as usual.
I tried to open a ticket, but the first answers are sensless.
Can anyone (from germany) confirm this or has a solution?
Regards Holger
Hey Holger,
same issue here. Can confirm that Workspace crashes when a shortcut containing a Umlaut in the name (Like in “Verknüpfung”) is present in the local folder. The issue was first observed in our environment after upgrading to VDA 2311.
Can confirm that Workspace 2311, 2311.1 and 2309 show this behavior. Did not test an older build though.
Kindest regards,
Laurenz
Thanks for posting this!
I ran into a similar issue with 2311. Citrix sessions would crash when accessing local paths that contained shortcuts with special characters (umlaut/nordic) in the shortcut names.
Seems to be fixed in 2402 (LTSR).
Has 2311 been withdrawn as it does not seem available to download?
We have multiple users who are getting an error failed to start when trying to start their virtual desktop. Was going to remove this and re-install but not available to download from anywhere.
CTX587626 seems to suggest there is an issue with it.
Hi Carl,
since installing CWA LTSR 2203 CU5, when the (some) user unlock (screen lock) the local device it“ s not possible to use the keyboard inner the published XenApp Desktop. The only workaround, disconnect and reconnect the published Desktop do solve this. With CWA LTSR 2203 CU4 all works fine. Case by CITRIX is open but the didn“`t find anything.
Any ideas ?
Best regards
C-M
Hi carl,
We have setup as per below versions, End users are accessing apps& desktop over workspace app(2309.1) externally (MFA enabled with Radius) . users are not able to sign in back in workspace app if they are sign out. they can login only after reset/re-add the account in workspace app again.
what was the cause of this issue.? Citrix team is working with this issue one week no fix yet.
VDA version: 1912 CU5
OS on the VDA: Windows 2019 and Windows 2012 R2
Storefront version: 1912 CU5
No of storefronts: 2
OS on the storefront: Windows server 2019
Hypervisor: vmware
Provisioning method: PVS and manual
Workspace app version: 2309, 1912 CU5, 2203 LTSR
This is through NetScaler Gateway? Check your beacons in your StoreFront Console. Make sure the Internal Beacon is not reachable from the Internet.
Does anyone know how to uninstall? We had version 22.x deployed as a part of MDT imaging. Using 23.9 FULLOFFLINEINSTALLER causes immediate failure. running/cleaninstall or /forceinstall fails with 1612.
I’ve been trying all week to figure out how to manually remove Citrix and get it installed properly. I’m quite frustrated. Sorry about that.
I just cannot figure out how to clean the install. /uninstall runs with no error yet there are tons of Citrix remnants all over the place. REgistry. C:\program files(x86)\Citrix. C:\user\username\appdata\local\temp and more.
The log file shows it failing in general on XENAPP WEB PLUGIN with error 1612. I’ve been up and down the Citrix KB and on GOogle, spiceworks you name it. I’m ready to jump off a tall building.
Help!
I am in a similar situation, sort of.
There is a windows 10 pro endpoint that will run WSA 2307 successfully but fails when upgrading to 2309.1
If you uninstall 2307 and then install 2309.1 (all versions to include the offline installer one, it will still fail and I have an open ticket with Citrix requesting the manual steps to remove all traces of Citrix.
The logs indicate the same error as yours. XENAPP WEB PLUGIN with error 1612.
Hi Chris:
Thanks for the commend. LMK if you hear from Citrix how to resolve or if you figure it out.
I’ve gone through using all I know how to clean it up manually and I’m striking out. I don’t want to throw in the towel and just re-image the machine. I’d like to figure this out.
Hi Chris Yue,
I’m not saying this is a solution, but I just installed 23.3.0.55 without any issues. I just decided to try an earlier 23.xx version.
Makes me wonder if there’s something quite problematic specifically with 23.9.
Again, if you hear from Citrix for resolving the issue with 23.9, I’d love to hear what worked.
Hi Robert,
Just got a remote session with Citrix Support.
In the end, we installed 2311 (preview) and the in-place upgrade worked!
This version will be GA in a few weeks so worth a try.
https://www.citrix.com/downloads/workspace-app/betas-and-tech-previews/workspace-app-tp-for-windows.html
Friend, I cannot thank you enough for this.
I’ve been pulling my hair out. I’ve literally spent the whole week trying to find some solution for my organization.
I’m downloading the full offline installer as we speak. Will give it a try shortly.
THANK YOU!!!
Happy Holidays!
Hi All,
There is a new launch experience introduced in CWA 2309.
https://docs.citrix.com/en-us/citrix-workspace-app-for-windows/improved-virtual-apps-and-desktops-launch-experience
Does anyone know how to disable it (maybe a registry key)? I found the notifications very disturbing.
Hi Carl/everyone,
Thanks for your article.
After Citrix Workspace App has been installed I would like to update the app via command line.
The option with using CitrixReceiverUpdater.exe and parameters does not work.
I have tried with via Citrix docu CitrixReceiverUpdater.exe /AutoUpdateCheck=auto /AutoUpdateStream=Current /DeferUpdateCount=-1 /AURolloutPriority=fast – but no luck.
Are these parameters still up-to-date?
I’m glad to see that Citrix is continuing to update their Workspace app. This app is essential for users who need to access their files from multiple devices.
I have a question about how applications are view with the web interface. I would like to have the application for each site I own group in a folder which the user than needs to click in to view those applications. For instance, AZ Virtual apps would be the folder, once the folder is open than the application icon would appear.
If you edit a published app, on the Delivery tab, there’s a field called Category.
Thanks that help but is there a way to force users to only see the categories?
When there are multiple accounts configured in Citrix Workspace App, how can I remove one of the accounts. In older versions of receivers/workspace app you could delete an account via the gui. Can’t find that in 2305.1.
Open Workspace app. Click the gear icon on the top right and then click Accounts. If you used GPO to push accounts to Workspace app then you can’t remove them using the GUI. You can right-click the Workspace app icon, click Advanced and then click Reset Workspace.
Carl,
I have a large environment and with multiple sites that the users manually entered the accounts / sites into the Workspace app. Now that we are getting close to retiring the old sites and only the new one will remain, is there a way to automate the removal of the old sites without user intervention leaving just the new production site in place?
On Windows, you can use GPO to push store configuration and then configure a logon script Reset Receiver. https://support.citrix.com/article/CTX140149/how-to-reset-receiver-using-the-command-line
Another option is to hack the HKCU registry for each user by deleting keys under HKCU\Software\Citrix\Dazzle and HKCU\Software\Citrix\Receiver. CWA would need to be closed and reopened.
Hello Carl,
Recently I met an issue with my keyboard synchronization with Citrix.
The issue description is:
The [Alt Gr] key does not work when I connect to my workstations from home, via Citrix bridge + RDP.
At the office, when I connect directly with RDP (single jump, no Citrix bridge), the [Alt Gr] keystroke is sent “as is” to my workstation, and there is no issue.
However, when I work from home (double jump, Citrix bridge + RDP), the [Alt Gr] keystroke is incorrectly translated into [Alt] + [Ctrl]. That prevents me from typing curly braces and square brackets.
Thank you.
Hi Carl
Migrating from Receiver 4.12 to WorkSpace (tested with 1912 and 2303), launching an old PS4.0 app from an ICA file, get stucked in the logon Window
With Receiver, it use the user and pass from the ICA file, but with WorkSpace stops at the logon window
Anything I can configure to allow WorkSpace to use teh user and pass from the ICA file?
Thanks in advance
Thank you, carlstalhood, for your incredibly detailed blog on resetting Citrix Workspace. Your step-by-step instructions were clear, concise, and easy to follow. Your attention to detail and thorough explanations made the process smooth and hassle-free. I greatly appreciate the time and effort you put into creating such a comprehensive guide. Your blog has been an invaluable resource for troubleshooting and resolving Citrix Workspace issues. Keep up the excellent work, and thank you for sharing your expertise with the community!
Dear Carl
Did you noticed problems with gateway selecting in the Workspace App for MAC?
We have 2 Gateways which can be selected in the Workspace App.
One is for 2FA authentication and one for “normal” Authentication. Both are listet and can be selected.
If we change the Gateway which is initially selected to the second one, we are able to change the Gateway and it switches to the selected and even the Gateway URL change. But when we want to save this change (click OK) the change will never be affected. We have thoose on all MacOS Devices. In earlier Versions (Workspace App 2012) it worked, but since the Problem from the 23 march we can’t connect with earlier Versions.
https://support.citrix.com/article/CTX491310/workspace-app-for-mac-known-issue-march-23rd-2023
We now have a workaround where we import a modified provisioning File which have both Gateways configured to use the 2FA gateway.
When connecting through NetScaler Gateway we are getting authentication prompt twice with Citrix Workspace noting that we have checked the box on the storefront related to Pass through Citrix Gateway, we have 1 VPX server with one Citrix Gateway that point to our StoreFront server (worth mention here that we have only one store deployed)so through web browsers the users are authenticated one time when they only reach the gateway but when we use Citrix workspace and put the Citrix gateway link inside it we are prompt for a user name and password two times the first time for the gateway and the second time when it reaches the store front server
Appreciate if any one can help with this.
Are you testing from the internal network? If so, then I’m guessing the StoreFront Internal Beacon is reachable, which is causing the second logon.
Yes, ideally thats the idea, we want to access store using Gateway URL only but from internal network only. we have restricted Access from public network.
We want to use ADC EPA protection hence gateway is introduced in-between.
we have created DNS entry using gateway VIP only.
let me know what needs to be done to resolve this issue.
If I put Dummy URL for Internal Beacon will it work?, any impact which may occur post that may be in future. just wanted to be cautious before making any changes
Yes, configure a fake Internal Beacon to force Workspace app to use Gateway even when internal.
Thanks for your help, it is working as expected.
I recently downloaded Citrix Workspace 2303.
I am not able to run receiverconfig.cr, I downloaded it from my workspace web.
May I know what specific application should I use to “open with” the receiverconfig.cr.
Please provide the path and application name to be used.
Thanks.
Try “C:\Program Files (x86)\Citrix\ICA Client\Receiver\SRProxy.exe” “%1”
Hi Carl/everyone,
I began pushing out Workspace 2203 CU3 and all of my users are reporting that they are receiving the Citrix Receiver – Security Warning now even though I followed the steps in this article and have a gpo pushed to prevent that pop up. Any ideas?
Hi
we have a request from our security team requesting, if the downloaded .ICA file can be copied/exported to a different machine within the 100 seconds of being downloaded ( 100 seconds is the TTL for STA) and launch resources?. I am aware of the new feature to download the ica file into memory rather than disk but does anyone know if the above is possible?
Try it. 🙂
It has a one-time use ticket.
Hi Carl, is it posible to block on the Netscaler the users with an old (not actual) version of Citrix Workspace App? Could one use a session policy for this purpose?
thank you very much in advance
I don’t think so. But you can create a login script on the VDA that reads the client version from the VDA’s registry and handle it appropriately.
The following PS-Command should return the client version:
Get-ChildItem -Path HKLM:\SOFTWARE\Citrix\Ica\Session\ | Get-ChildItem | WHERE Property -Contains Username | Get-ItemProperty | WHERE Username -eq $env:USERNAME | SELECT ClientVersion
Hey Tommy, thanks a lot.
Great, thank you for the prompt reply!
Hi Carl,
Do you know where to find out CVAD 2203 requires minimal Citrix Workspace version? THank you.
I think all currently supported versions of Workspace app are valid, but only the newest versions support the newest features. Some info at https://docs.citrix.com/en-us/citrix-workspace-app/citrix-workspace-app-feature-matrix.html
Hi Carl.
Citrix Workspace App for Windows shows add account page as a blank page. This is happening after authentication at Client level. Tested with CWA 2109.1 and 2212. Laptop has Microsoft Edge Browser 109.0.1518.78 and Microsoft Edge Webview2 Runtime 109.0.1518.78.
Any solution available ? apart from moving back to 2108 & below versions.
Thank you for all your great work.
Hey guys,
i have citirix workspace installed on all laptops within our environment for uses to be able to access applications.
Recently, i noticed some users have blank icons when launching citrix workspace.
Any reason as to why this could be happening?
Thanks
Hi Carl,
I’ve installed Workspace client on my VDAs because some of my users use a Saas application. But all sessions open the Workspace and Webview2 process too.
Is it possible to disable lauching Workspace client on user session startup ?
Download http://live.sysinternals.com/autoruns.exe and run it. Then search for Citrix.
Thanks Carl.
This allowed me to understand the mechanics during the logon.
Workspace app installer check Microsoft Edge WebView2 Runtime but check only HKLM key! When you install Microsoft Edge WebView2 Runtime as user its not working. Install as system user.
Hi Carl,
thanks for your time.
I am not able to login to ADC (internal VIP) with workspace app if I’m behind proxy.
HTML 5 works as a charm.
Disabling proxy workspace app works as expected.
Did you have any tips?
Is your proxy trying to decrypt the traffic? If so, can you bypass that?
Thanks very good articles:
SSO works perfect.
But after some time “days” the ssonsvr.exe is no longer running.
Not able to “Sign In”.
Have to reboot or Sign in to Windows again to get ssosvr.exe and SSO running.
Citrix Workspace 2209.
Any tips ?