Navigation
This page details creation of session profiles and policies for NetScaler Gateway 11 where ICA Only (formerly known as Basic Mode) is checked.
Partly based on Citrix Knowledgebase Article CTX139963 – How to Configure NetScaler Gateway with StoreFront
Session Profiles/Policies CLI Commands
The CLI commands are shown below:
add vpn sessionAction "Receiver Self-Service" -transparentInterception OFF -defaultAuthorizationAction ALLOW -SSO ON -icaProxy ON -wihome "https://storefront.corp.com" -ntDomain Corp -clientlessVpnMode OFF -storefronturl "https://storefront.corp.com" add vpn sessionAction "Receiver for Web" -transparentInterception OFF -defaultAuthorizationAction ALLOW -SSO ON -icaProxy ON -wihome "https://storefront.corp.com/Citrix/StoreWeb" -ntDomain Corp -clientlessVpnMode OFF add vpn sessionPolicy "Receiver Self-Service" "REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver" "Receiver Self-Service" add vpn sessionPolicy "Receiver for Web" "REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver" "Receiver for Web"
Session Profiles
Or use the GUI to create the policies/profiles:
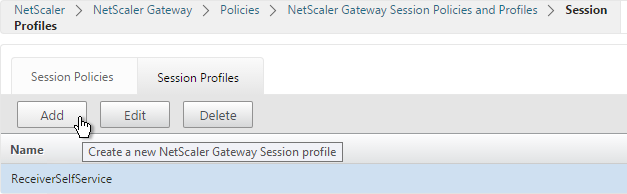
- On the left, expand NetScaler Gateway, expand Policies, and click Session.
- On the right, switch to the Session Profiles tab, and click Add.
- Name the first one ReceiverSelfService or similar. This is for Receiver Self-Service (not in a web browser).
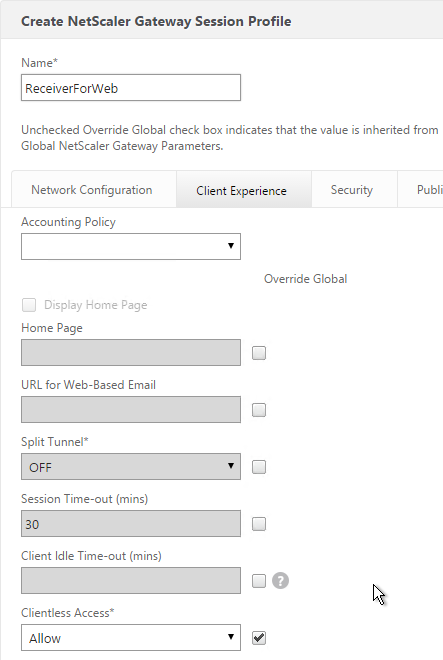
- Switch to the Client Experience tab.
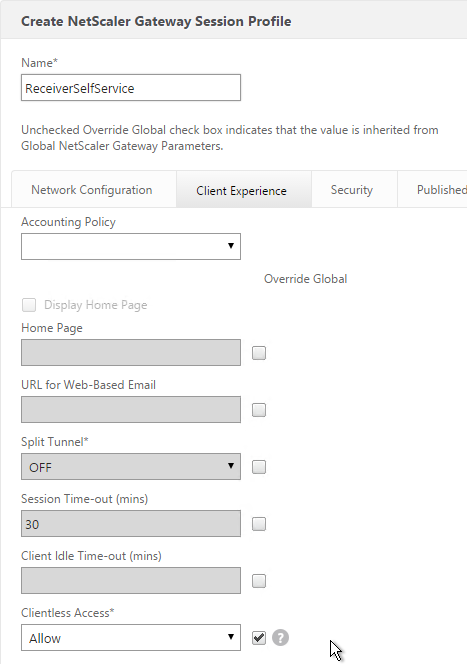
- Check the Override Global box next to Clientless Access and set it to Allow. Scroll down.
- Check the Override Global box next to Plug-in Type and set it to Java.
- Check the Override Global box next to Single Sign-on to Web Applications and enable it. Scroll up.
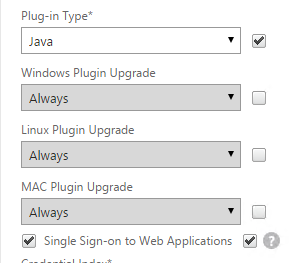
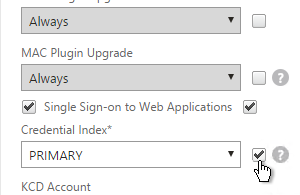
- If you need two-factor authentication, the session policy for Receiver Self-Service needs to be adjusted to indicate which authentication field contains the Active Directory password. On the Client Experience tab is Credential Index. This needs to be changed to SECONDARY. Leave the session policy for Web Browsers set to PRIMARY.
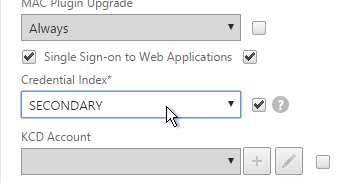
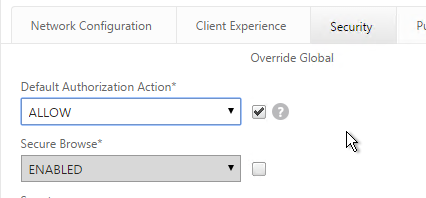
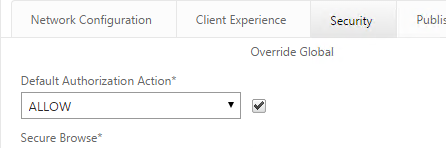
- On the Security tab, check the Override Global box next to Default Authorization Action and set it to Allow.
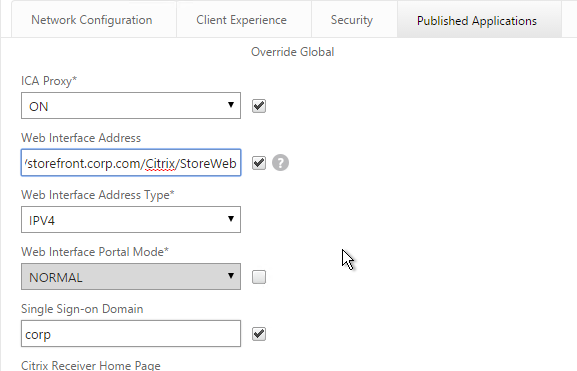
- On the Published Applications tab, check the Override Global box next to ICA Proxy and set it to ON.
- If you only have one domain, then check the Override Global box next to Single Sign-on Domain and enter the name of your Active Directory domain. StoreFront needs to accept this domain name (Configure Trusted Domains).
- If you have multiple domains, then leave Single Sign-on Domain field blank, and ensure the LDAP authentication servers have userPrincipalName in the SSO Name Attribute field.
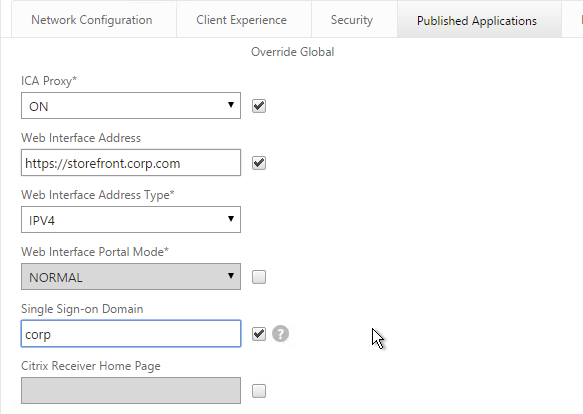
- For Account Services Address, enter the Base URL for StoreFront. NetScaler needs to be able to resolve this DNS name.
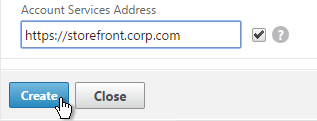
- Highlight the existing session profile and click Add. This copies the settings from the existing profile into the new one.
- Change the name of the second Session Profile to ReceiverForWeb or similar.
- On the Client Experience tab, Clientless Access should be set to Allow. Scroll down.
- Plug-in Type should still be set to Java.
- Single Sign-on to Web Applications should be enabled.

- If you need two-factor authentication, the session policy for Receiver for Web needs Credential Index set to PRIMARY. Only the Receiver Self-Service policy needs SECONDARY as detailed earlier.
- On the Security tab, the Default Authorization Action should still be Allow.
- On the Published Applications tab, for the Web Interface Address field, add the path to your Receiver for Web site (e.g. /Citrix/StoreWeb).
- Account Services Address only applies to Receiver Self-Service so you can leave it or clear it.
- Everything else should be the same. If you only have one domain, then check the Override Global box next to Single Sign-on Domain and enter the NetBIOS name of your Active Directory domain. If you have multiple domains, then leave this field blank and ensure the LDAP authentication servers have userPrincipalName in the SSO Name Attribute field.
- Account Services Address is not needed in this profile but there’s no harm in leaving it.
- Click Create.
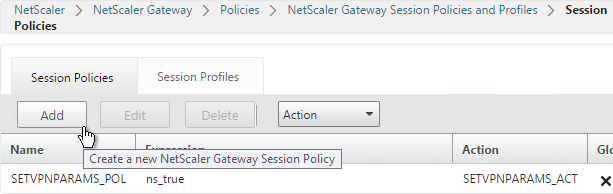
Session Policies
- On the right, switch to the Session Policies tab, and click Add.
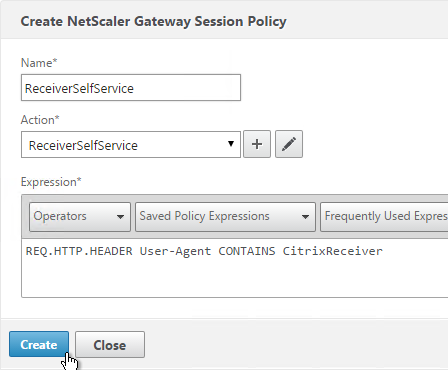
- Name the Policy ReceiverSelfService or similar.
- Change the Request Profile to ReceiverSelfService.
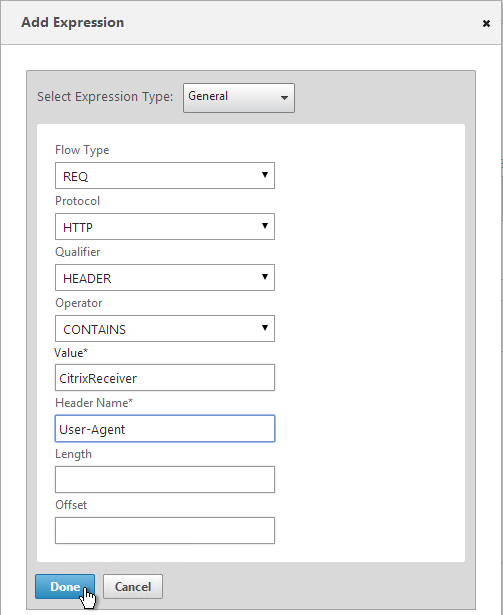
- Either type in or use the Expression Editor link to build the following expression:
REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver
- Then click Create.
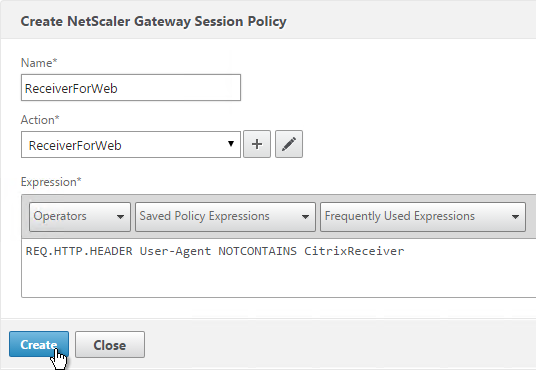
- Add another policy, and name it ReceiverForWeb or similar.
- Change the Action to ReceiverForWeb.
- In the Expression box, either type in the following or use the Expression Editor. It’s the same as the previous expression, except it’s NOTCONTAINS instead of CONTAINS.
REQ.HTTP.HEADER User-Agent NOTCONTAINS CitrixReceiver
- Click Create.
Hi Carl,
Excellent assistance as always. Thank you.
How do you resolve the Receiver error, “The Gateway has Epa Enabled, which is not supported on iOS devices.”
You will need a Gateway vServer that does not have Preauthentication Policy bound. You can instead put EPA expressions in a Session Policy. Or maybe EPA in nFactor, except I’m not sure if nFactor is supported by iOS yet.
Thank you Carl. I have no pre-authentication policies or profiles. Session policy for mobile is configured using REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver. (I also tried what is suggested in this article https://support.citrix.com/article/CTX200748 to no avail.) I don’t know where the epa check is being triggered for the mobile devices.
Hi Mary , Were you able to resolve this issue . I m having the same issue , it works on citrix receiver for iOS devices but does not work for Citrix workspace on iOS devices .
Hi Carl , Seems to work on Citrix Receiver on iOS devices but not on citrix workspace .
Getting the below error “The Gateway has Epa Enabled, which is not supported on iOS devices.”
We have 4 Netscaler 11.0 appliances. We have external customers who lease an application from us. They are currently receiving the Citrix Receiver login prompt about every 30 minutes. I would think that as long as they were active in the session, it would not prompt them? I am guessing the policy is set to 30 minutes but there are a few different places with session timeouts listed and I am not sure which one is causing the prompt. Would appreciate any advice you provide. Thanks.
What is the persistence timeout on your StoreFront load balancer?
Persistence Timeout = 2…whenever I hover over the ? button, it says Default = 2
Does this mean that if they are inactive for 2 minutes, it prompts for creds?
It should be at least as long as the RfWeb timeout.
Hi Carl,
Great article as always, is there any way to apply session policies to devices having a specific certificate..I want to apply session policies only on corporate devices.. is there any way?
Thanks
Vik
Hi Carl,
would that be a sufficient policy priority sequence?
LDAP-Policies
xx.xx.xx.xx_LDAP_pol -> vServer: xxxx-NSG1 Priority 91 Global Priority NA
-> vServer: xxxx-NSG1-internal Priority 92 Global Priority NA
xx.xx.xx.xx_LDAP_pol -> vServer: xxxx-NSG1 Priority 95 Global Priority NA
-> vServer: xxxx-NSG1-internal Priority 96 Global Priority NA
-> GROUP:DL_xxxx_Citrix_Portal_Access_Receiver Priority 85 Global Priority NA
NSG Session Policies
PL_OS_xx.xx.xx.xx -> vServer: xxxx-NSG1 Priority 105 Global Priority NA
-> vServer: xxxx-NSG1-internal Priority 106 Global Priority NA
PL_WB_xx.xx.xx.xx -> vServer: xxxx-NSG1 Priority 101 Global Priority NA
-> vServer: xxxx-NSG1-internal Priority 102 Global Priority NA
-> GROUP:DL_xxxx_Citrix_Portal_Access_WebBrower Priority 81 Global Priority NA
sorry, have to correct:
LDAP-Policies
xx.xx.xx.xx_LDAP_pol -> vServer: xxxx-NSG1 Priority 91 Global Priority NA
-> vServer: xxxx-NSG1-internal Priority 92 Global Priority NA
xx.xx.xx.xx_LDAP_pol -> vServer: xxxx-NSG1 Priority 95 Global Priority NA
-> vServer: xxxx-NSG1-internal Priority 96 Global Priority NA
NSG Session Policies
PL_OS_xx.xx.xx.xx -> vServer: xxxx-NSG1 Priority 105 Global Priority NA
-> vServer: xxxx-NSG1-internal Priority 106 Global Priority NA
-> GROUP:DL_xxxx_Citrix_Portal_Access_Receiver Priority 85 Global Priority NA
PL_WB_xx.xx.xx.xx -> vServer: xxxx-NSG1 Priority 101 Global Priority NA
-> vServer: xxxx-NSG1-internal Priority 102 Global Priority NA
-> GROUP:DL_xxxx_Citrix_Portal_Access_WebBrower Priority 81 Global Priority NA
If multiple Session Policies apply to a user, they are merged, and for conflicts, whichever one has the lowest priority number, will win.
Hi Carl,
currently I have two storefront stores. one for internal an one for external and internal.
But why do I get a choice configuring the receiver of both stores connecting via NSG?
how can I hardcode the store for the receiver policy at all?
thanks
I don’t think that’s possible. This sometimes causes me to build separate StoreFront servers for internal and external.
Why two different stores?
I’ve a customer request (and I’m really interested myself) to configure NSG to publish one store to HTML5 clients and the other to Receiver clients.
I checked a post here:
http://discussions.citrix.com/topic/347876-access-gateway-session-policy-bound-to-ad-group/
but i didn’t manage to work it. Maybe I missed some settings.
I would reply on that post better than here I guess 🙂
You want different session policy based on AD groups. What’s not working? Did you add the case sensitive AD group name as a AAA group? Did you make sure your LDAP Policy is configured for group name extraction? Did you create separate session policies for each AD group and bind them to the AD group with lower priority numbers?
Note: Receiver does not use the store name configured in the session policy, but browsers do use the store name configured in the session policy.
Hi Carl,
I think I need to understand the sequence about the policies that matters during logon and delivering applications.
I’ll do some research and reading before my next reply 🙂
thanks so far
When the user logs in, NetScaler reads the user’s group membership.
NetScaler looks in Gateway > User Administration > AAA Groups for a matching group (case sensitive). If match, it looks for Session Policies bound to the AAA Group. If the policy bind point has a lower priority number than the Session Policies bound to the Gateway vServer (or other AAA Groups), then this Session Policy wins conflicts against other Session Policies.
Hi Carl, is it possible to block clients with specific Citrix receiver version or with version earlier than X (or Citrix IOS/Android Receiver earlier than X).
I think Citrix Receiver version is not present in HTTP Header and there is no way to track it, am I right ot there are other ways to get it? Thank you.
hi carl,
great guides – thanks for putting the time into it.
i am trying to work out why in this post your session policy for receiver for web it doesn’t have the home page set to anything, but in this guide (https://www.carlstalhood.com/storefront-config-for-netscaler-gateway/) you do set it.
I’m sure it is something basic but I can’t figure it out…
cheers
dave
I got that config by looking at the screenshots at http://docs.citrix.com/en-us/storefront/3/advanced-configurations/sf-configure-single-fqdn.html#par_richtext_6. I personally never use that procedure and instead only do the simpler configuration. I’ll leave feedback at that article to see if it’s correct or not. It’s weird that their example is a completely different DNS name than on the Published Apps tab. Thanks for noticing.
Hello Carl, similar question to @Graham.
I’m a bit confused about the recommendation to set “Plugin-in Type: Java” for SelfService Receiver, and “Plugin-in Type: Win/Mac” for the Web Policy.
AFAIK the Web Policy shouldn’t need any setting at all. Only the SelfService Policy would need “Plugin-in Type: Win/Mac”. Is this a mistake on you or my side?
Second, do we need an Plug-in Type definition at all in ICA-Proxy ON mode? Doesn’t that override any Plug-in use at all?
And Third hint from my side: In your step-by-step description you clone the Web-Profile from the SelfService Profile. But compared to the CLI command you don’t clear the “Account Services Address / -storefronturl” which should still be in the clone.
Thanks for all your good work, and I hope I can help you a little bit with the small details!
Marco
Regarding the plugin type, I’m following http://support.citrix.com/article/CTX139963 . This was changed recently. It used to be Java for both but now it’s Windows for Web and Java for Receiver.
The plugin type is used by Receiver Self-Service to contact StoreFront without needing a VPN tunnel. I suspect there’s special code to handle Receiver.
Regarding Account Services Address, it is not used by Browsers, but there’s no harm in leaving it.
Hi Carl,
Thanks for a great series.
Creating a Receiver (not web) policy above, in the GUI you override Plug-in Type to Java. Where does this appear in the command line? Or is it there by default?
Thanks
Graham
It controls the -transparentInterception parameter.
Hi carl,
Don’t you think turning OFF transparentInterceptor is an security risk
I don’t have a good answer. I’m just following Citrix’s guides, which they changed, hopefully for a good reason.
Hi Carl, What if I wanted to set smart card authentication as a primary, but if the user does not have a smart card or smart card reader then fallback to domain authentication? Would this be another session policy?
Why on the ReceiverSelfService command do you have “-wihome “https://storefront.corp.com/Citrix/StoreWeb”” but on the gui build step number 10 you have “Don’t add any path to the end of the URL.” Just trying to make sure which is correct.
That appears to be an error on my part. I fixed the session policy CLI command. Thanks.