Navigation
- Change Log
- Citrix Virtual Apps and Desktops (CVAD) Versions
- CVAD Upgrade Overview
- Upgrade Citrix Virtual Apps and Desktops (CVAD)
- Citrix Licensing Server
- Delivery Controllers
- App Layering (Unidesk)
- Workspace Environment Management (WEM)
- Session Recording
- Citrix Provisioning
- Virtual Delivery Agents (VDA)
- StoreFront
- Workspace app for HTML5
- Director
- Citrix Group Policy Management Plug-in
- Profile Management Group Policy Templates
- Workspace app Group Policy Templates
- Workspace app
- Skype for Business HDX Real Time Optimization Pack
- Federated Authentication Service (FAS)
- Customer Experience Improvement Program (CEIP)
- Citrix ADC (aka NetScaler) Firmware
Change Log
- 2024 June 4 – updated article for Citrix Virtual Apps and Desktops (CVAD) 2203 LTSR CU5
- 2024 April 20 – updated article for Citrix Virtual Apps and Desktops (CVAD) 2402 LTSR
- 2024 April 24 – updated article for Workspace app 2403 (Current Release)
- 2023 Sept 11 – updated article for Citrix Virtual Apps and Desktops (CVAD) 1912 LTSR CU8
- 2022 Sep 11 – Delivery Controllers – added alternate method of upgrading the operating system
- 2022 July 9 – updated entire article for XenApp/XenDesktop 7.15.9000
Citrix Virtual Apps and Desktops (CVAD) Versions
Version Numbering
Citrix Virtual Apps and Desktops (CVAD) is the new name for XenApp and XenDesktop.
The most recent version of Citrix Virtual Apps and Desktops (CVAD) 7 is 2402 LTSR. The version number is based on YYMM (Year Month) format. References to 7.x versions in this article include the YYMM versions.
XenApp and XenDesktop 7.x versions range from 7.0 through 7.18. 7.18 is the last version of XenApp and XenDesktop. Citrix Virtual Apps and Desktops (CVAD) 2402, 2203, and 1912 are newer than XenApp and XenDesktop 7.18.
Release Notifications
Follow my Twitter or EUC Weekly Digests for new release notifications.
Sometimes release notifications are posted to Citrix Blogs, but this is not comprehensive.
Watch Citrix Discussions and Citrix Support Knowledgebase to learn about known issues that are fixed in a later release.
Release Classifications – LTSR, CR
Image from Citrix Blog Post What’s New in XenApp, XenDesktop and XenServer November 2017.
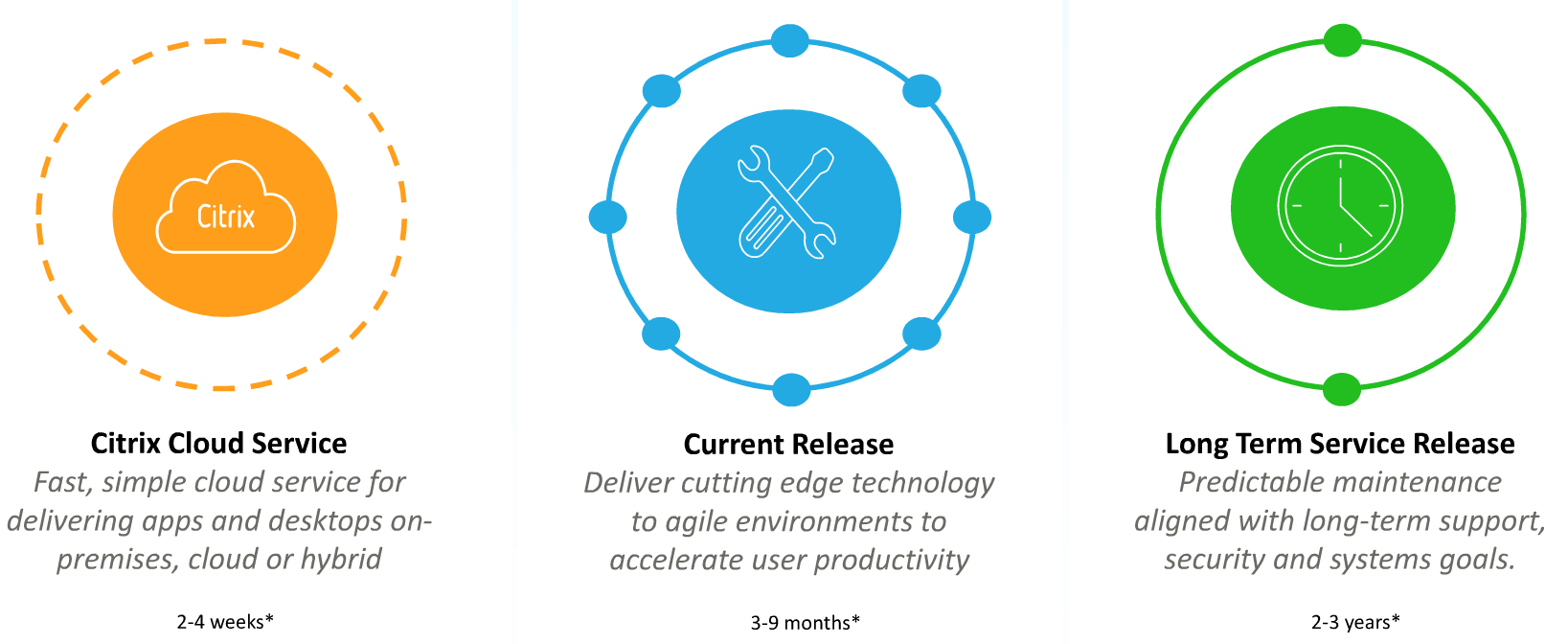
There are three classifications for on-premises releases:
- LTSR (Long Term Service Release) – these releases get 5 years of mainstream support from the release date, plus up to 5 more years of paid extended support
- CR (Current Release) – 6 months support from the release date. Updated quarterly.
- LTSR Compatible Components – non-LTSR components running in a LTSR implementation. This classification provides exceptions to the requirement that all components must be LTSR versions.
Citrix Virtual Apps and Desktops (CVAD) is a bundle of components. Long Term Support requires the components to be specific versions. Any deviation from the required versions results in loss of Long Term Support, and instead is classified and supported as a Current Release. Use Citrix LTSR Assistant tool to confirm LTSR compliance.
LTSR Programs
There are three different LTSR programs:
- Citrix Virtual Apps and Desktops (CVAD) LTSR – includes Delivery Controllers, VDAs, StoreFront, Citrix Provisioning, Session Recording, and Profile Management.
- More info at FAQ: Virtual Apps and Desktops and Citrix Hypervisor Long Term Service Release (LTSR)
- There is no LTSR version of Citrix Workspace Environment Management (WEM) so you should always deploy the latest version of WEM.
- Citrix Hypervisor LTSR
- Workspace app LTSR
LTSR Licensing requirement
LTSR requires you to be on Customer Success Services Select, formerly known as Software Maintenance.
LTSR vs CR
Support Duration
LTSR is supported for 5 years from the LTSR release date, plus 5 more years of optional, paid extended support.
- LTSR Cumulative Updates (similar to service packs) are released periodically. Cumulative Updates for LTSR are installed exactly like upgrading to a newer Current Release, except you don’t get any new features.
- Cumulative Updates are released only for LTSR versions. To patch a Current Release, upgrade to the newest Current Release.
- Be prepared to install these LTSR Cumulative Updates every 6 months. Workspace app LTSR (or Receiver LTSR) too.
Current Releases are end-of-maintenance after 6 months, and end-of-life after 18 months.
- Be prepared to upgrade to a newer Current Release every 6 months. Workspace app too.
See Lifecycle Milestones for Citrix Virtual Apps & Citrix Virtual Apps and Desktops for an explanation of support durations for each release classification.
In either case, you are expected to perform some sort of upgrade or update approximately twice per year.
Release Frequency
New LTSR versions of CVAD are released every 18-24 months.
There are three supported LTSR releases of Citrix Virtual Apps and Desktops: LTSR 2402, LTSR 2203, and LTSR 1912.
- 2402 is the first build of LTSR 2402.
- 2203 Cumulative Update 4 (CU5) is the latest updated build of LTSR 2203.
- 1912 Cumulative Update 8 (CU8) is the latest updated build of LTSR 1912.
LTSR 7.15 is no longer supported by Citrix.
Cumulative Updates (CU) for LTSR are released every few months. Don’t forget to install these patches. I’ve seen CUs fix LTSR issues.
- Cumulative Updates do not include new features.
- Citrix has not yet released any Cumulative Updates for LTSR 2402.
- Citrix has released three Cumulative Updates for LTSR 2203, bumping up the version to 2203.3000.
- Citrix has released eight Cumulative Updates for LTSR 1912, bumping up the version to 1912.8000.
- Citrix will continue to release Cumulative Updates for all currently supported LTSR versions.
You can upgrade directly to the latest Cumulative Update. It is not necessary to upgrade to the base version before upgrading to the latest Cumulative Update.
New Current Release versions are released every quarter. Sometimes longer for Workspace app.
Some Citrix Virtual Apps and Desktops (CVAD) components are released on a separate schedule from the main LTSR or Current Release releases:
- App Layering
- Workspace Environment Management
Citrix Provisioning version numbers don’t line up with Citrix Virtual Apps and Desktops (CVAD) LTSR Cumulative Update version numbers:
- Citrix Virtual Apps and Desktops (CVAD) 2402 LTSR comes with Citrix Provisioning 2402
- Citrix Virtual Apps and Desktops (CVAD) 2203 LTSR CU5 comes with Citrix Provisioning 2203 CU4
- Citrix Virtual Apps and Desktops (CVAD) 1912 LTSR CU8 comes with Provisioning Services 1912 CU7
Current Release cons
New Current Releases add new features, and new bugs.
No hotfixes will be released for Current Releases. To get hotfixes, upgrade to the newest Current Release.
LTSR cons
Features not in LTSR – Some features are not included in the LTSR program. In other words, these features don’t get 5 years of support, and might not even be included in the LTSR installer.
- Personal vDisk and AppDisks – these are replaced by User Personalization Layers.
- Framehawk
Features in Current Release but not LTSR:
- Upcoming CVAD Current Release Version 2405 will have new features that are not in 2402 LTSR. Will you upgrade to CVAD 2405, which puts you on the Current Release upgrade train? Or will you wait until the next LTSR, probably released sometime in 2026?
- Another option is to remain on 2402 LTSR (with latest cumulative update) until you see a Current Release with new features that are desirable enough to upgrade to. You can then upgrade directly from 2402 LTSR to the latest Current Release (e.g., 2502). There’s no need to upgrade to intermediary versions.
Don’t mix Current Release and LTSR components – As soon as you upgrade one LTSR component to Current Release, upgrade all other LTSR components to Current Release and keep them updated with new Current Releases every 6 months.
- When the next LTSR is released, you can stop upgrading (except for Cumulative Updates).
- Or deploy Current Release in a separate environment.
- Use Citrix LTSR Assistant tool to confirm LTSR compliance.
- Some app vendors require you to remain on LTSR.
LTSR “compatible” components require frequent upgrades – Some components, like App Layering, are LTSR “compatible”, meaning there’s no LTSR version, but it’s OK to use them in an LTSR environment. Since they’re Current Release and not LTSR, you’re expected to update the Current Release components to the latest release every 6 months.
- There’s no LTSR version of Citrix Licensing. Instead, always upgrade Citrix Licensing to the latest Current Release version.
- There’s no LTSR version of App Layering. Instead, always upgrade App Layering to the latest Current Release version.
- There’s no LTSR version of Citrix Workspace Environment Management. Instead, always upgrade Citrix Workspace Environment Management (WEM) to the latest Current Release version.
Windows 11 is supported in CVAD 2109 and newer. Windows 11 is not supported in CVAD 1912 LTSR.
Windows 7 and Windows Server 2008 R2 support: 7.16 VDA and newer, including 1912 LTSR VDA, are not supported on Windows 7 or Windows Server 2008 R2. For these operating system versions, install 7.15 LTSR VDA. The 7.15 LTSR VDA can register with newer Delivery Controllers. However, the 7.15 LTSR VDAs cannot take advantage of the newer features in the newer releases.
Citrix Virtual Apps and Desktops (CVAD) Supported versions
The most recent release of Citrix Virtual Apps and Desktops (CVAD) is version 2402.
There are three supported LTSR versions of Citrix Virtual Apps and Desktops (CVAD): LTSR 2402, LTSR 2203, and LTSR 1912.
- No Cumulative Updates have yet been released for LTSR 2402.
- Cumulative Update 5 has been released for LTSR 2203, resulting in version number 2203.5000.
- Cumulative Update 8 has been released for LTSR 1912, resulting in version number 1912.8000.
You can directly install the latest Cumulative Update of any LTSR version. It is not necessary to install the base version of the LTSR version before you upgrade to the latest Cumulative Update.
Examples of non-supported versions:
- Citrix Virtual Apps and Desktops (CVAD) 1909 is not LTSR, and is more than six months past release date, so Citrix will not provide any code fixes. Once 18 months have elapsed, Citrix will not support it at all.
Workspace app Supported Versions
Starting in August 2018, Receiver have been renamed to Workspace app. Also, versioning has changed from 4.x to a YYMM (year month) format.
The most recent Current Release of Workspace app is version Workspace app 2403.
The latest LTSR version of Workspace app is version 2402 LTSR.
- Browser Content Redirection does not work in LTSR Workspace app because Embedded browser is removed due to infrequent updates of LTSR versus frequent updates of the embedded browser.
Citrix Virtual Apps and Desktops (CVAD) Component Version Dependencies
Citrix Virtual Apps and Desktops (CVAD) is a collection of installable components:
- Citrix Licensing Server
- Delivery Controller
- Citrix Studio
- Virtual Delivery Agent
- Director
- StoreFront
- Federated Authentication Service
- App Layering
- Citrix Provisioning
- Citrix Group Policy Management Plug-in
- Profile Management
- Workspace Environment Management
- Session Recording
- Workspace app for Windows, Linux, Mac, iOS, and Android
- Workspace app for HTML5
- Skype for Business HDX RealTime Optimization Pack
- Citrix ADC (aka NetScaler) Load Balancing
- Citrix Gateway
Component behaviors:
- Each component can be installed separately.
- Some components can be combined onto the same machine.
- Some components are completely standalone with no dependency on other components.
- Some components communicate with other components, and thus are dependent on those other components.
The fewest components that make up a Citrix Virtual Apps and Desktops (CVAD) site/farm are License Server + Delivery Controller + Studio + VDA + SQL Databases.
- A farm/site is a collection of Delivery Controllers that share the same SQL databases.
- The official term is Citrix Virtual Apps and Desktops (CVAD) Site. However, since the word “site” has multiple meanings, this article instead refers to a Citrix Virtual Apps and Desktops (CVAD) Site as a Farm, which is the same terminology used in XenApp 6.5 and older.
Some of the components can be used with multiple sites/farms.
- Citrix Licensing Server can be used by multiple sites/farms.
- StoreFront can pull icons from multiple sites/farms, including XenApp 6.5. This enables multi-farm capabilities for the following components that are dependent on StoreFront:
- Federated Authentication Service can be used by multiple StoreFront servers.
- Workspace app for Windows, Linux, Mac, iOS, and Android can connect to multiple StoreFront stores, which can be on different StoreFront servers.
- Each StoreFront server has its own Workspace app for HTML5
- Citrix Gateway connects to one StoreFront server
- Citrix Studio can connect to multiple sites/farms.
- Virtual Delivery Agent can register with only one site/farm at a time, but the farm registration can be easily changed by modifying the ListOfDDCs registry key.
- Director can display monitoring data from multiple sites/farms.
- App Layering has no relationship to Citrix Virtual Apps and Desktops (CVAD) sites/farms, and thus can be used with any number of them.
- Citrix Provisioning has no relationship to Citrix Virtual Apps and Desktops (CVAD) sites/farms, and thus can be used with any number of them.
- Citrix Group Policy Management Plug-in can be used to create Citrix Policies that can apply to multiple sites/farms.
- Profile Management has no relationship to Citrix Virtual Apps and Desktops (CVAD) sites/farms, and thus can be used with any number of them. The profiles are usually tied to a VDA operating system version.
- Workspace Environment Management has no relationship to Citrix Virtual Apps and Desktops (CVAD) sites/farms, and thus can be used with any number of them.
- Session Recording has no relationship to Citrix Virtual Apps and Desktops (CVAD) sites/farms, and thus can be used with any number of them.
- Skype for Business HDX RealTime Optimization Pack has no relationship to Citrix Virtual Apps and Desktops (CVAD) sites/farms, and thus can be used with any number of them. This component only cares about the RealTime Connector that is installed on the VDA.
The Citrix components that don’t have any relationship to Citrix Virtual Apps and Desktops (CVAD) sites/farms can be used with XenApp 6.5 too.
Some components communicate with other components, and thus are dependent on the versions of those other components.
- Citrix Licensing Server should always be the newest version. Citrix Virtual Apps and Desktops (CVAD) Components will verify the Licensing Server version.
- StoreFront can usually work with any Delivery Controller version, including XenApp 6.5.
- Citrix Studio should be the same version as the Delivery Controllers it is managing.
- Virtual Delivery Agents can be any version, including older or newer than the Delivery Controllers.
- Director uses the Citrix Monitoring Service that is installed on the Delivery Controllers.
- New Director features don’t work unless Delivery Controllers, and sometimes VDAs are upgraded. See Director Feature compatibility matrix for details.
- Workspace Environment Management (WEM) – newer WEM can configure newer Profile Management features. Otherwise, WEM is independent from Citrix Virtual Apps and Desktops (CVAD).
- Workspace app – Many newer Citrix Virtual Apps and Desktops (CVAD) features require a specific version of Workspace app.
- The newest Workspace app along with the newest VDA supports the latest Teams optimization (offload) features. LTSR versions of these components might not support the latest Teams optimization features.
- If you are deploying Current Releases, then deploy the newest Current Release Workspace app.
- If you are deploying LTSR, then deploy the latest LTSR Workspace app or LTSR Receiver.
- If you need Browser Content Redirection, then deploy the latest Current Release Workspace app since LTSR Workspace app does not support Browser Content Redirection.
- Citrix Gateway – Some Newer Citrix features require newer Citrix ADC firmware. For example:
- EDT (Enlightened Data Transport) / Adaptive Transport
- Gateway Configuration export/import with StoreFront
- Citrix ADC builds have bug fixes that affect the Citrix Virtual Apps and Desktops (CVAD) experience.
Upgrade Overview
Components
Citrix Virtual Apps and Desktops (CVAD) is composed of multiple Components, each of which is upgraded separately.
- Citrix Licensing Server
- Delivery Controllers
- App Layering (Unidesk)
- Workspace Environment Management (WEM)
- Session Recording
- Citrix Provisioning
- Virtual Delivery Agents (VDA)
- StoreFront
- Workspace app for HTML5
- Director
- Citrix Group Policy Management Plug-in
- Citrix Profile Management Group Policy Templates
- Workspace app Group Policy Templates
- Workspace app
- Skype for Business HDX Real Time Optimization Pack
- Federated Authentication Service (FAS)
- Citrix ADC (aka NetScaler) Firmware
Newer versions of Citrix components enable Customer Experience Improvement Program (CEIP) automatically. If you wish to disable CEIP, see https://www.carlstalhood.com/delivery-controller-cr-and-licensing/#ceip.
Component Upgrade Process
In-place upgrades – CVAD components can be upgraded in-place. No need to rebuild like you did in XenApp 6.5 and older.
- For LTSR releases, you can upgrade directly to the latest Cumulative Update. It is not necessary to install the base LTSR version first.
- For Current Releases, you can upgrade directly to the latest Current Release.
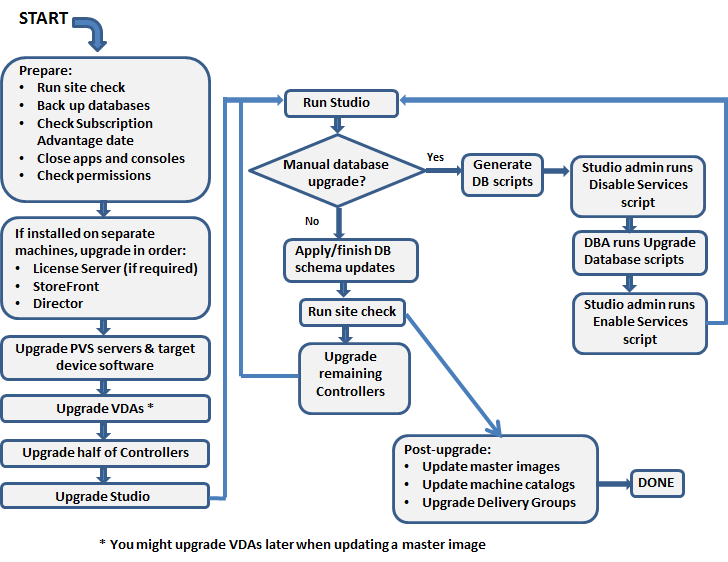
Here’s the general, in-place upgrade process for each component. Detailed instructions for each component are detailed later.
- In-place upgrade one (or half) of the component’s servers.
- Upgrade the component’s database. Requires temporary sysadmin permission on SQL Server. Not all components have databases.
- In-place upgrade the remaining component’s servers.
- In-place upgrade the agents.
- Rebuilding of master images might be preferred, assuming you have time to automate it.
Mix and match VDA/Controller versions – You can upgrade VDAs without upgrading Delivery Controllers. Or vice versa.
- Newer VDA features sometimes require Citrix Policy to enable or configure. The newest Citrix Policy settings are included in Delivery Controller / Citrix Studio upgrades. Or, if you haven’t upgraded your Delivery Controllers yet, you can simply upgrade the Citrix Group Policy Management component.
VDA Operating System version Upgrade – Considerations when upgrading the VDA operating system version:
- Operating System Version – VDA 7.16 and newer no longer support Windows Server 2008 R2, Windows 7, or Windows 8/8.1. If you need these older operating system versions, then install VDA 7.15 instead. VDA 7.15 can register with 1912 Delivery Controllers.
- Windows 11 – VDA 1912 LTSR does not support Windows 11, but CVAD 2109 and newer do support Windows 11
- App compatibility – Verify app compatibility with the new OS version. For compatibility with a Server OS version, check compatibility with the equivalent Desktop OS version.
- Windows Server 2012 R2 = 64-bit Windows 8.1
- Windows Server 2016 = 64-bit Windows 10 1607
- Windows Server 2019 = 64-bit Windows 10 1809
- Windows Server 2022 = 64-bit Windows 10 21H2
- Start Menu in published desktop – If you publish desktops, is the Windows 2012 R2 Start Menu acceptable to the users? Windows 2012 R2 Start Menu is the same as Windows 8.1 Start Menu.
- Windows Server 2016 Start Menu is the same as Windows 10 1607 Start Menu.
- Windows Server 2019 Start Menu is the same as Windows 10 1809 Start Menu.
- Windows Server 2022 Start Menu is the same as Windows 10 21H2 Start Menu.
- GPO settings– Newer OSs have newer Microsoft GPO settings.
- Copy the newer Microsoft ADMX templates to PolicyDefinitions (Sysvol or C:\Windows)
- Configure the newer GPO settings.
- Profile version – Newer OS means newer profile version. Older profile versions do not work on newer operating system versions. For example, you can’t use Windows 7 profiles on Windows 10. This means that an OS upgrade results in new profiles for every user.
- Write a script to copy profile settings from the old profiles to the new profiles.
- Remote Desktop Services (RDS) Licensing – if you are building RDSH (Server OS) VDAs, then every user that connects must have an RDS License for the RDSH operating system version. If RDSH is Windows 2016, then every user needs a Windows 2016 RDS License. Windows 2008 R2 RDS Licenses won’t work.
- RDS Licensing Server – RDS Licensing Server is a built-in Windows Server Role. It must be installed on servers with the same or newer operating system version than the RDSH VDAs.
- Windows 10 versions and Windows 11 versions – See CTX224843Windows 10 & 11 Compatibility with Citrix Virtual Desktops.
- Upgrade Windows 10 or Windows 11 version – If you in-place upgrade Windows 10 or Windows 11, first remove the VDA software, upgrade Windows, and then reinstall VDA.
- App Layering – Due to dependencies between App Layers and OS Layer, you might have to in-place upgrade your OS Layer.
- Citrix Virtual Apps and Desktops (CVAD)Component Agents – ensure the Citrix component agents (WEM Agent, Profile Management, Session Recording Agent, App Layering Tools, etc.) are supported on the new OS version.
Considerations for upgrading the operating system version on component servers:
- Do not in-place upgrade the operating system version. Instead, build new VMs, and join them to the existing infrastructure.
- New OS version requires newer component versions. The required component version might be newer than what you’re currently running.
- When adding a server to the existing component farm/site, the new server must be running the same component version as the existing servers. That means you might have to in-place upgrade your existing component servers before you can add new component servers running a newer operating system version.
- For example:
- Existing Delivery Controllers are version 1912 on Windows Server 2019.
- You desire to migrate to new Windows Server 2022 Delivery Controllers.
- Only Delivery Controller 2203 and newer can be installed on Windows 2022. But you can’t add Delivery Controller 2203 to a Delivery Controller 1912 farm/site.
- Upgrade the existing Delivery Controllers to 2203 or newer first.
- Then you can add the new Windows Server 2022 Delivery Controllers VMs to the existing farm/site.
Here are general instructions to upgrade component server OS version. Detailed instructions for each component are detailed later.
- In-place upgrade the existing component servers to a version that supports the new OS. Check the System Requirements documentation for each component to verify OS version compatibility.
- Build new machine(s) with desired OS version.
- On the new machines, install the same component version as the existing component servers.
- The new machines must be the same component version as the existing machines. You can’t add machines with newer component versions.
- Add the new component servers to the existing farm/site/server group.
- Migrate load balancer, VDAs, Targets, etc. from old to new. See below for detailed instructions for each component.
- Decommission old servers.
Upgrade Guidelines
Test farms – Test Citrix infrastructure upgrades in separate test environments (separate test farms):
- Due to forwards and backwards compatibility, VDA upgrades can usually be tested in production.
- Everything else requires global server-side upgrades first, so you can’t test them in production.
- Upgrade procedures for High Availability components (e.g., multiple Delivery Controllers) are different than upgrade procedures for singe, standalone components. The Test environment should look like production, which means HA too.
- The separate Test environments should include multi-datacenter capabilities (StoreFront icon aggregation, GSLB, etc.) so those multi-datacenter features can be tested.
Known upgrade issues – Read Citrix Discussions, or ask your Citrix Support TRM, for known upgrade issues. Don’t upgrade production immediately after a new version is released.
- Read the release notes, especially the known issues.
Smart Check the environment before upgrading. It’s free. Access it at https://smart.cloud.com.
Backup/snapshot – Backup databases, snapshot machines, etc. before starting the in-place upgrade.
- Have a rollback plan, including the databases.
Citrix Licensing Server – Always upgrade the Citrix Licensing Server before upgrading anything else.
- Check Subscription Advantage (SA) date on the installed licenses. Some components require SA expiration date to be later than the component’s release date.
In-place upgrade preparation:
- Make sure other admins are logged off before starting the upgrades.
- Close all consoles and PowerShell.
- Snapshot the machines.
Upgrade Citrix Virtual Apps and Desktops (CVAD)
All CVAD components can be upgraded in-place.
- For the list of versions that you can upgrade directly from, see Citrix Docs. Also see the Citrix Upgrade Guide.
- Current Release upgrades are cumulative. You can skip intermediary versions.
- LTSR Cumulative Updates are also cumulative, hence the name.
- LTSR Cumulative Updates are installed using the same process as Current Release upgrades. The only difference is that you don’t get new features with LTSR updates.
Some components (Delivery Controllers, Citrix Provisioning, Session Recording, WEM, etc.) require the person doing the upgrade to have temporary sysadmin permissions on the SQL server so the database can be upgraded.
Upgrade order – For the most part, upgrade order doesn’t matter. That’s because there are few dependencies between each component, as detailed earlier.
- Before upgrading anything else, upgrade the Citrix Licensing Server.
- Install updated license files with non-expired Subscription Advantage dates.
- VDAs and Delivery Controllers can be different versions.
- VDAs can be upgraded before Controllers, or vice/versa.
- If Zones, upgrade all Delivery Controllers in all zones at the same time.
- For Director, upgrading Director won’t do you much good if the Controllers aren’t upgraded, since Director uses the Monitoring service that’s installed on the Controllers.
- For Citrix Provisioning, the Citrix Provisioning servers must be upgraded before you upgrade the Target Device Software.
- For Session Recording, the Session Recording server(s) must be upgraded before you upgrade the Session Recording agent.
- For WEM, the WEM server(s) must be upgraded before you upgrade the WEM agent.
If you upgrade to a version that has CEIP functionality, decide if you want to disable CEIP, or leave it enabled.
After upgrading, configure new functionality.
Additional general upgrade guidance can be found at Upgrade a deployment at Citrix Docs.
Citrix Licensing Server
It’s a simple in-place upgrade.
- After upgrading, download the latest license files from http://mycitrix.com, and install the license files on the license server. Make sure the Subscription Advantage date hasn’t expired.
To upgrade the Licensing Server Operating System version:
- Build a new VM with desired OS version.
- Install the latest Current Release License Server.
- At http://mycitrix.com, reallocate licenses to the new case-sensitive hostname, and install the license file on the new Licensing Server.
- In Citrix Studio, go to Configuration > Licensing, and change the License Server to the new Licensing Server.
Delivery Controllers
Both of the following types of upgrades/updates use the same upgrade process:
- Install latest LTSR Cumulative Update
- Upgrade to latest Current Release
To in-place upgrade Delivery Controller version:
- Upgrade the Citrix Licensing Server if you haven’t already. Install current licenses if you haven’t already. Make sure CSS date is not expired.
- Ask a DBA for temporary sysadmin permission to the SQL server.
- Prepare: logoff other admins, close consoles.
- If upgrading from 7.15 to 2203 or newer, then 7.15 must be Cumulative Update 5 or newer.
- In-place upgrade one (or half) of the Delivery Controllers. Upgrade to one of the following:
- Launch Citrix Studio or Site Manager. Upgrade the database when prompted.
- In-place upgrade the remaining Delivery Controllers.
- Temporary SQL sysadmin permissions can now be removed.
- For Citrix Studio that’s installed on administrator machines other than Delivery Controllers, in-place upgrade Citrix Studio by running AutoSelect.exe from the Current Release or LTSR CVAD ISO.
To upgrade the operating system version of the Delivery Controllers:
- In-place upgrade the existing Delivery Controllers to a version that supports the new operating system version.
- For Windows Server 2016, upgrade Delivery Controller to version 7.15 or newer.
- For Windows Server 2019, upgrade Delivery Controller to version 1912 or newer
- For Windows Server 2022, upgrade Delivery Controller to version 2203 or newer.
- CVAD 1912 does not support Windows Server 2022.
- CVAD 2203 does not support Windows Server 2012 R2. If upgrading from Windows 2012 R2 to Windows 2022, then upgrade to CVAD 1912 first, replace the OS to Windows 2019, upgrade to CVAD 2203, and then replace the OS to Windows 2022.
- Build one or more new virtual machines with the new operating system version.
- Install Delivery Controller software with the same version as the other Delivery Controllers.
- If vSphere, import the vCenter cert into Trusted Root or Trusted People.
- Run Citrix Studio and join the new machines to the existing farm/site.
- Reconfigure VDAs to point to the new Delivery Controllers. Edit the ListOfDDCs registry key.
- Reconfigure Director server > IIS Admin > Default Web Site > Director > Application Settings > Service.AutoDiscoveryAddresses to point to the new Delivery Controllers.
- Reconfigure StoreFront console > MyStore > Manage Delivery Controllers to point to the new Delivery Controllers.
- Secure Ticket Authorities:
- Add the new Delivery Controllers to firewall rules between Citrix ADC SNIP and STAs.
- In Citrix Gateway > Edit Virtual Server > scroll down to the Published Applications section > click the line to edit the Secure Ticket Authorities. Add the new Delivery Controllers as Secure Ticket Authorities. Don’t remove the old ones yet.
- In StoreFront Console, go to Manage Citrix Gateways > edit each Gateway > on the Secure Ticket Authority page, add the new Delivery Controllers as Secure Ticket Authorities, and remove the old ones.
- In Citrix Gateway > Edit Virtual Server > scroll down to the Published Applications section > click the line to edit the Secure Ticket Authorities. Remove the older Controllers as Secure Ticket Authorities.
- In Citrix Studio, at Configuration > Controllers, remove the old Delivery Controllers.
- Note: if this doesn’t work, then you might have to manually evict the old Delivery Controllers from the SQL database.
- Decommission the old Delivery Controllers.
An alternate method of upgrading the operating system on the Delivery Controllers while preserving the machine’s identity:
- The new server will have the same Citrix version as already installed. You might have to in-place upgrade Citrix to get to a version that supports the new operating system version. CVAD 1912 can run on Windows Server 2019, but it cannot run on Windows Server 2022. CVAD 2203 supports Windows Server 2022, but it does not support Windows Server 2012 R2. If upgrading from Windows 2012 R2 to Windows 2022, then upgrade to CVAD 1912 first, replace the OS to Windows 2019, upgrade to CVAD 2203, and then replace the OS to Windows 2022.
- Export any certificates that you want to keep and put them on a different machine.
- Record the IP Address and hostname of the machine you want to replace.
- Record the database connection strings. PowerShell Get-BrokerDBConnection shows the main database connection. Get the Logging and Monitoring database names from Citrix Studio > Configuration.
- Shut down a Delivery Controller and never power it on again. Don’t remove this machine from the domain to avoid accidentally deleting the Active Directory computer object.
- Build a new machine with an operating system version supported by the Citrix version running on the other Delivery Controllers. Give it the same name and IP address. Join it to the domain using the existing Active Directory computer object.
- Install the same version of Delivery Controller as was running previously. Don’t run Citrix Studio.
- If vSphere, import the vCenter cert into Trusted Root or Trusted People.
- Use the PowerShell commands at https://www.carlstalhood.com/delivery-controller-cr-and-licensing/#changedbstrings to connect the new machine to the SQL database.
- Run Citrix Studio. It might ask you to upgrade the database but it’s merely finishing the database connection and not actually upgrading anything.
App Layering
To in-place upgrade Citrix App Layering:
- In-place upgrade the ELM appliance.
- From 4.2 and newer, newer versions should be downloaded automatically. Just click the link to start the upgrade.
- From 4.1 and older, download the upgrade package and upload it to the ELM.
- Upgrade the App Layering Citrix Provisioning Agent by uninstalling the Citrix Provisioning Agent and re-installing it.
- Create a new OS Layer version and install the latest OS Machine Tools.
- When the images are published, the drivers will be updated automatically by the ELM.
Workspace Environment Management (WEM)
There is no LTSR version of Citrix Workspace Environment Management (WEM) so you should always deploy the latest version of WEM.
To in-place upgrade Citrix Workspace Environment Management (WEM):
- In-place upgrade the Citrix Licensing Server if you haven’t already.
- Ensure the installed licenses have a non-expired Subscription Advantage date.
- Ask a DBA for temporary sysadmin permission to the SQL server.
- In-place upgrade the first WEM Server. Consider removing it from load balancing before performing the upgrade.
- Use the Database Maintenance tool to upgrade the WEM database.
- Run the WEM Broker Configuration Tool on the upgraded Broker to point to the upgraded database.
- In-place upgrade the remaining WEM Servers. Consider removing them from load balancing before performing the upgrade.
- Temporary sysadmin permissions can now be removed.
- In-place upgrade the WEM Console on all non-server machines where it is installed.
- In-place upgrade the WEM Agents.
- If you are upgrading from WEM 4.2 and older, in the WEM Console, add the WEM Agents (computer accounts) to Configuration Sets instead of the old WEM Sites.
To upgrade the operating system version of the Workspace Environment Management servers, it’s easier if you have a custom DNS name, or load balanced DNS name for WEM, instead of using a server name:
- In-place upgrade the existing WEM servers to a version that supports the OS you intend for the new WEM servers.
- Build new WEM servers with the same WEM version as the existing WEM servers.
- Configure the new WEM servers to point to the same database as the old WEM servers.
- Cutover options:
- If you have a load balanced DNS name for WEM, reconfigure the load balancer to point to the new WEM servers.
- If you have a custom DNS name for WEM, change it to resolve to the new WEM server’s IP address.
- If you were previously using the actual server name, then you can either change the WEM Agent group policy to point to the new WEM server name, or delete the old WEM server and rename the new WEM server, or delete the old WEM server and reconfigure the old DNS name as a custom DNS name for the new WEM server.
- Decommission the old WEM servers.
Session Recording
To in-place upgrade Session Recording:
- In-place upgrade the Citrix Licensing Server if you haven’t already.
- Ensure the installed licenses have a non-expired Subscription Advantage/CSS date.
- Ask a DBA for temporary sysadmin permission to the SQL server.
- In-place upgrade the first Session Recording server to one of the following.
- Session Recording is on the main Citrix Virtual Apps and Desktops (CVAD) ISO.
- Session Recording LTSR 2402
- Session Recording LTSR 2203 CU5
- Session Recording LTSR 1912 CU8
- The upgrade of the first Session Recording server should automatically upgrade the database.
- In-place upgrade the remaining Session Recording Servers. Consider removing them from load balancing before performing the upgrade.
- Temporary sysadmin permissions can now be removed.
- In-place upgrade the Session Recording Agents.
- In-place upgrade the Session Recording Player on all machines where it is installed.
To upgrade the operating system version of the Session Recording servers, it’s easier if you have a custom DNS name or load balanced DNS name for Session Recording, instead of using a server name:
- In-place upgrade the existing Session Recording servers to a version that supports the OS you intend for the new Session Recording servers.
- Build new Session Recording servers with the same Session Recording version as the existing Session Recording servers.
- Configure the new Session Recording servers to point to the same database as the old Session Recording servers.
- Configure the new Session Recording servers to store recordings on the same UNC path as the old Session Recording servers.
- The certificate on the Session Recording servers or load balancer must match the DNS name used by the Session Recording Agents and Player.
- Cutover:
- If you have a load balanced DNS name for Session Recording, reconfigure the load balancer to point to the new Session Recording servers.
- If you have a custom DNS name for Session Recording, change it to resolve to the new Session Recording server’s IP address.
- If you were previously using the actual server name, then you can either: change the Session Recording Agents and Players to point to the new Session Recording server name, or delete the old Session Recording server and rename the new Session Recording server, or delete the old Session Recording server and reconfigure the old DNS name as a custom DNS name for the new Session Recording server.
- If the Session Recording DNS name changed, reconfigure Director to point to the new Session Recording DNS name.
- Decommission the old Session Recording servers.
Citrix Provisioning
Citrix Provisioning servers must be upgraded before you can upgrade Target Devices.
To in-place upgrade Citrix Provisioning servers:
- Make sure Citrix Provisioning High Availability (HA) is working for target devices. If HA is functional, in-place upgrade can be done during the day.
- In the Citrix Provisioning console, you should see an even distribution of Target Devices across all Citrix Provisioning servers.
- Check the WriteCache folders on Citrix Provisioning servers to make sure they’re empty. If any Target Device is caching on Server, then those Target Devices will not failover to another Citrix Provisioning server.
- Get temporary sysadmin permissions to the SQL Server that hosts the Citrix Provisioning database.
- Get the one of the following installation media:
- On the first Citrix Provisioning Server:
- In-place upgrade Citrix Provisioning Console by running the LTSR 2402, LTSR 2203 CU4, or LTSR 1912 CU8, Citrix Provisioning Console installer.
- Re-register the Citrix.PVS.snapin.dll snap-in:
"C:\Windows\Microsoft.NET\Framework64\v4.0.30319\InstallUtil.exe" "c:\program files\citrix\provisioning services console\Citrix.PVS.snapin.dll"
- In-place upgrade Citrix Provisioning Server by running the LTSR 2402, LTSR 2203 CU4, or LTSR 1912 CU8 Citrix Provisioning Server installer
- Run the Citrix Provisioning Configuration Wizard. The farm should already be configured, so just click Next a few times and let it upgrade the database and restart the services.
- In-place upgrade the PVS Console and PVS Server software on the remaining Citrix Provisioning Servers. After installation, run the Citrix Provisioning Configuration Wizard, and click Next until the end.
- Temporary SQL sysadmin permissions can now be removed.
- Target Device Software can now be upgraded.
There are several methods of upgrading the Citrix Provisioning Target Device Software that’s inside a vDisk:
- In-place upgrade the Target Device Software while doing your normal vDisk update process.
- Completely rebuild the vDisk. An automated build process like MDT is recommended.
- Or you can reverse image. To upgrade VMware Tools (or any software that modifies the NIC), you must reverse image.
To in-place upgrade Target Device software:
- Create a new vDisk Maintenance version or put the vDisk in Private Image mode. Then boot an Updater Target Device. This is the normal process for updating a vDisk.
- Run the LTSR 2402, LTSR 2203 CU4, or LTSR 1912 CU8 Target Device software installer to upgrade the software. The Target Device software must be the same version or older than the Citrix Provisioning Servers.
- Shut down the Updater. Promote the Maintenance version to Production or change the vDisk to Standard Image mode. This is the normal process for updating a vDisk.
Reverse image methods:
- Boot from VHD – Build a VM. Copy Citrix Provisioning vDisk VHD/VHDX to VM. Boot from VHD/VHDX.
- Hyper-V can boot from a VHD directly. Copy Citrix Provisioning vDisk VHD/VHDX to Hyper-V host. Create a VM that boots from VHD/VHDX.
- Citrix Image Portability Service can convert PVS VHD to VMware .vmdk.
- Once VHD/VHDX is updated, copy the VHD/VHDX back to Citrix Provisioning, import to a Citrix Provisioning Store, which creates a new vDisk, and assign the new vDisk to target devices. Takes effect at next Target Device reboot.
If using Citrix Provisioning Accelerator, keep XenServer patched.
To upgrade the operating system version of the Citrix Provisioning Servers:
- In-place upgrade the existing Citrix Provisioning Servers to a version that supports the new operating system version.
- Build one or more new virtual machines with the new operating system version.
- Install Citrix Provisioning Server software with the same version as the other Citrix Provisioning Servers.
- Run Citrix Provisioning Configuration Wizard and join the new machines to the existing Citrix Provisioning farm and Citrix Provisioning database.
- Copy the vDisk files from an existing Citrix Provisioning Server to the new Citrix Provisioning Servers. Check Replication Status of each vDisk.
- Install the App Layering Citrix Provisioning Agent.
- In Citrix Provisioning Console, reconfigure Bootstrap to point to the new Citrix Provisioning Servers. Go to Sites > MySite > Servers > right-click each server and click Configure Bootstrap.
- Reconfigure DHCP Options or BDM to point to the new Citrix Provisioning Servers. Do one or more of the following:
- Reconfigure TFTP load balancing to point to the new Citrix Provisioning Servers.
- Change DHCP Scope Options 66/67 to the new Citrix Provisioning Servers.
- Create a new Boot ISO with the new Citrix Provisioning Servers.
- Use the Citrix Provisioning Console to update the BDM Partition on each Target Device.
- Start the PXE Service on the new Citrix Provisioning Servers and stop the PXE Service on the old Citrix Provisioning Servers.
- Reboot some Target Devices to make sure they work.
- In Citrix Provisioning Console, delete the old Citrix Provisioning Servers.
- Decommission the old Citrix Provisioning Servers.
Virtual Delivery Agents (VDA)
To in-place upgrade the Virtual Delivery Agent software:
- In-place upgrade the VDA software to one of the following versions:
- Upgrade the Workspace Environment Management Agent that’s installed on the VDA machines.
- Upgrade the Session Recording Agent that’s installed on the VDA machines.
- Upgrade the Citrix Files software that’s installed on the VDA machines.
- Citrix Files is the new name for ShareFile Drive Mapper. Citrix Files is built into VDA 1903 and newer.
- Upgrade the Connection Quality Indicator software that’s installed on the VDA machines.
- Upgrade the Chrome Receiver File Access software that’s installed on the VDA machines.
- Upgrade the Citrix Provisioning Target Device software that’s installed on the VDA machines.
Instead of in-place upgrading the VDAs, you can also rebuild them with the new software versions. If rebuilding, use an automated method, like MDT.
To upgrade the operating system version of the Virtual Delivery Agents, it’s recommended to rebuild the VDA. But keep in mind the following:
- Windows 11 is not supported by VDA 1912 LTSR, but Windows 11 is supported with VDA 2109 and newer.
- Windows 10 version upgrades should be a rebuild, not an in-place upgrade.
- If you in-place upgrade, uninstall VDA software, upgrade Windows, then reinstall VDA software.
- Citrix App Layering might require in-place upgrade of Windows 10 due to other layers being linked to the OS Layer.
- Newer VDA operating system versions use newer profile versions, which means older profiles will not work.
- Newer RDSH operating system versions require newer RDS Licensing Servers and newer RDS Licenses.
- GPO settings– Newer OSs have newer Microsoft GPO settings.
- Copy the newer Microsoft ADMX templates to PolicyDefinitions (Sysvol or C:\Windows)
- Configure the newer GPO settings.
StoreFront
StoreFront is the most problematic component to upgrade so be prepared to roll back.
- Newer versions of StoreFront installer are adding pre-upgrade checks to prevent known upgrade issues.
Citrix does not support mixing StoreFront versions within a single Server Group, and they instead prefer that you do this: (source = Upgrade StoreFront at Citrix Docs)
- It’s critical that you snapshot the StoreFront machines before beginning the upgrade since there is no rollback from a failed upgrade.
- Remove a StoreFront sever from the Server Group and load balancing.
- Prep: close consoles, close PowerShell, logoff other admins, etc.
- Upgrade the removed server by installing one of the following:
- StoreFront LTSR 2402.
- StoreFront LTSR 2203 CU5.
- StoreFront LTSR 1912 CU8.
- If upgrade fails, review the install logs to determine the cause. Once the cause is determined, revert the VM to prior snapshot, and try the upgrade again.
- Upgrade the HTML5 Workspace app installed on StoreFront. The instructions for all StoreFront versions are the same.
- Swap out the upgraded server on the load balancer so all traffic goes to the new server.
- Uninstall/reinstall StoreFront on the remaining StoreFront servers and join the first server that was already upgraded.
To upgrade the operating system version of the StoreFront Servers:
- Build one or more new virtual machines with the new operating system version.
- Install StoreFront software. Configuration export/import requires the new servers to run the same version of StoreFront as the old servers. After the config is imported, you can in-place upgrade the new StoreFront servers.
- Do one of the following:
- Export the StoreFront configuration from the old servers and import to the new servers.
- Manually configure the new StoreFront Server Group to match the old StoreFront Server Group. This configuration includes: Base URL, entries under Manage Delivery Controllers (case sensitive), SRID (c:\inetpub\wwwroot\Citrix\Roaming\web.config), export/import subscriptions, Beacons, Gateways, Icon Aggregation, etc. Keeping the new configuration identical to old allows Workspace app to failover without any reconfiguration.
- (unsupported): join the new machines to the existing Server Group. This causes configuration and subscriptions to replicate to the new server. Citrix does not support mixing operating system versions in the same StoreFront server group.
- Copy customizations (e.g., default.ica) from old StoreFront to new StoreFront.
- Upgrade the HTML5 Workspace app installed on StoreFront. The instructions for all StoreFront versions are the same.
- Test the new StoreFront by modifying HOSTS file on test workstations. Make sure existing Workspace app can connect to the new StoreFront.
- On cutover night, reconfigure the load balancer to point to the new StoreFront servers instead of the old StoreFront servers.
- Decommission the old StoreFront servers.
Workspace app for HTML5
Workspace app for HTML5 is usually released on a different schedule than StoreFront and is upgraded out-of-band.
- There is no LTSR version of Workspace app for HTML5 so you should upgrade to the latest Workspace app for HTML5, especially for the newer features (e.g. multi-monitor, USB redirection).
To in-place upgrade Workspace app for HTML5:
- Upgrade the HTML5 Workspace app installed on StoreFront. The instructions for all StoreFront versions are the same.
- Upgrade the Chrome File Access software that’s installed on the VDA machines.
Director
To in-place upgrade the Director servers:
- Ensure the Delivery Controllers are already upgraded. There’s no point in upgrading Director if Delivery Controllers aren’t upgraded.
- In-place upgrade to one of the following versions:
- Upgrading Director overrides modifications to LogOn.aspx (e.g., default domain name), so you’ll have to reapply them.
- Repeat for the remaining Director servers.
- Upgrade the StoreFront Probes.
To upgrade the operating system version of the Director servers, it’s easier if you have a custom DNS name or load balanced DNS name for Director instead of using a server name:
- Make sure Delivery Controllers are running a version that supports the OS you intend for Director.
- Build new Director servers with the same version or newer than the Delivery Controllers.
- Configure the new Director servers to point to the same Delivery Controllers as the old Director servers.
- Copy the Director data files from the old Director servers to the new Director servers. Or point the new Director servers to the existing UNC path.
- Cutover:
- If you have a load balanced DNS name for Director, reconfigure the load balancer to point to the new Director servers.
- If you have a custom DNS name for Director, change it to resolve to the new Director server’s IP address.
- If you were previously using the actual server name, then you can either inform users of the new Director server name, or delete the old Director server and rename the new Director server, or delete the old Director server and reconfigure the old DNS name as a custom DNS name for the new Director server.
- Also reconfigure the StoreFront probes to point to the new Director name.
- Decommission the old Director servers.
Citrix Group Policy Management Plug-in
On any machine that has Group Policy Management installed, in-place upgrade the Citrix Group Policy Management Plug-in by running the installer from the Citrix Virtual Apps and Desktops (CVAD) LTSR 2402, CVAD LTSR 2203 CU5, or CVAD LTSR 1912 CU8. Or download it from the DaaS download page.
Profile Management Group Policy Templates
Profile Management service is included with Virtual Delivery Agent. Upgrading the VDA also upgrades Profile Management.
New templates don’t break existing functionality – Upgrading the Profile Management group policy templates (.admx files) will not affect existing functionality. The templates do nothing more than expose new settings that can be configured.
To in-place upgrade the Profile Management Group Policy Templates:
- Copy the newer Profile Management Group Policy Templates to the PolicyDefinitions folder: either Sysvol, or C:\Windows on every group policy editing machine.
- Look for older versions of the templates and delete them. Older template files have the version number in their name (e.g., ctxprofile7.19.0.admx).
- Edit the VDA GPOs that have Profile Management settings configured. Review the new settings, and configure them, if desired. Review the Profile Management release notes for the list of new features.
Workspace app Group Policy Templates
New templates don’t break existing functionality – Upgrading the Workspace app group policy templates (.admx files) will not affect existing functionality. The newer templates do nothing more than expose new settings that can be configured.
To in-place upgrade the Workspace app Group Policy Templates:
- Copy the newer Workspace app Group Policy Templates to the PolicyDefinitions folder: either Sysvol, or C:\Windows\PolicyDefinitions on every group policy editing machine. Overwrite existing template files.
- LTSR Workspace app and Current Release Workspace app have different versions of the group policy template files.
- Current Release Workspace app template files include all of the LTSR Workspace app settings, plus new settings that don’t apply to LTSR Workspace app.
- If you are deploying a newer Current Release Workspace app version, edit the GPOs that have Workspace app settings configured, review the new settings, and configure them, if desired. Review the Workspace app release notes for the list of new features.
Workspace app
To in-place upgrade Workspace app:
- Microsoft Configuration Manager – Use Microsoft Configuration Manager or similar to push one of the following versions:
- StoreFront delivery of Workspace app – If Workspace app is offered directly from StoreFront servers, copy the newer Current Release Workspace app to StoreFront 3.12+.
- StoreFront, by default, does not offer Workspace app upgrades to users but it can be enabled. If Workspace app upgrades are not offered, then Workspace app is provided by StoreFront only if there’s no Workspace app installed on the client device.
- In StoreFront 3.5 and newer, enable Upgrade plug-in at logon at the same place you upload the Workspace app files.
- For StoreFront 3.0 and older, edit C:\inetpub\wwwroot\Citrix\StoreWeb\web.config and set upgradeAtLogin to true.
- StoreFront, by default, does not offer Workspace app upgrades to users but it can be enabled. If Workspace app upgrades are not offered, then Workspace app is provided by StoreFront only if there’s no Workspace app installed on the client device.
- Auto-update – In Workspace app, if Auto-Update is enabled, then users with permissions will receive an update notification. Users can then manually initiate the Workspace app upgrade.
- You can configure group policy or an install switch to only update to LTSR versions of Workspace app.
- Manual update – Inform remote users to upgrade their Workspace app by downloading the Current Release version from http://workspace.app.
- If Workspace app was initially installed as an administrator, then only an administrator can upgrade it.
- If Workspace app was initially installed without administrator permissions, then each non-admin user on the same machine has a different Workspace app installation, and each user has to upgrade it separately.
Skype for Business HDX RealTime Optimization Pack
The Skype for Business HDX RealTime Optimization Pack is usually released separately from the main Citrix Virtual Apps and Desktops (CVAD) releases.
To in-place upgrade HDX RealTime Optimization Pack:
- On the VDAs, install the HDX RealTime Connector.
- 2.9 is the last version of Skype for Business HDX RealTime Optimization Pack.
- On each Workspace app machine, install the HDX RealTime Media Engine normally.
Federated Authentication Service (FAS)
To in-place upgrade the Federated Authentication Service (FAS) servers:
- On the existing FAS servers, run AutoSelect.exe from the Citrix Virtual Apps and Desktops (CVAD) 2402 LTSR ISO, the LTSR 2203 CU5 ISO, or the LTSR 1912 CU8 ISO, and click the button to install Federated Authentication Service. It’s a simple Next, Next, Next process.
- Newer versions of FAS might have newer group policy templates. If so, copy them to Sysvol, or C:\Windows\PolicyDefinitions on all group policy editing machines.
To upgrade the operating system version of the FAS servers:
- Build one or more new FAS servers.
- Request a Registration Authority certificate for each of the FAS servers.
- Change the group policy object for FAS to point to the new FAS servers. Run gpupdate on StoreFront and VDAs.
- Decommission the old FAS servers.
Customer Experience Improvement Program (CEIP)
Newer versions of Citrix Virtual Apps and Desktops (CVAD) components automatically enable Customer Experience Improvement Program (CEIP). To disable, see the following:
- Citrix Virtual Apps and Desktops (CVAD) CEIP
- Citrix License Server CEIP
- Virtual Delivery Agent CEIP
- Profile Management CEIP
- StoreFront CEIP
- Citrix Provisioning CEIP
- Workspace app CEIP
- Workspace app for HTML5 CEIP
- Session Recording CEIP
- Citrix ADC / NetScaler CEIP
Citrix ADC Firmware
Test appliances – Ideally, Citrix ADC firmware upgrades should be tested on separate test appliances. VIPs on the test appliances should then be tested.
Downtime if no High Availability – If you only have a single Citrix ADC appliance, then upgrading the firmware will cause downtime while the appliance is rebooting.
GSLB and mixed versions – If GSLB Metric Exchange Protocol (MEP) is enabled, then the Citrix ADC appliances on both sides of the MEP connection can run different versions of firmware.
To in-place upgrade Citrix ADC Firmware:
- Save the config. Then download a copy of the ns.conf file, or perform a backup of the appliance and download the backup file.
- On the secondary appliance, install the newer firmware.
- To test the new firmware, perform an HA failover.
- Configuration changes made on the primary appliance will not be synchronized to the secondary appliance until the firmware on the secondary appliance is upgraded.
- You can failover HA again to revert to the older firmware.
- To downgrade, on the appliance you’ve already upgraded, you can perform the firmware upgrade process again, but this time upload the older firmware.
- On the primary appliance, install the newer firmware. A HA failover occurs automatically.
Hey Carl,
I am planning on doing an inplace upgrade from 1912 LTSR CU8 to 2402 LTSR CU3.
I have 2 Controllers. They are all in ones (controllers, director, storefront) Licensing is on just one. We also use a netscaler for those incoming storefronts.
Is the best idea to force the outage and enter into LHC mod of EACH delivery controller and disable the storefront loadbalancer on the netscaler to the unregistered controller?
Then update controller 2 in all things. Update site, put back online and flip the netscaler loadbalancer to it and test.
Then update controller 1 and put back online as well.
Does that look about right? Do I need to remove the 2nd server from the strorefront server group before I update it? Then join the 1st server to it after its done? Or by doing LHC am I good to leave it in? That was the one of the main things I was not sure on.
Thanks for any insights
Hey Carl, in my organization we currently use Citrix 1912 LTSR CU9 (2 Dcons, 2 Storefront, and 1 FAS with about 40 VDA Servers. We are currently looking to upgrade from 1912 LTSR to 2402 LTSR. I have done numerous CU upgrades but never a major version change. Am I able to in-place upgrade from 1912 to 2402 or is it recommended to build new Infrastructure servers and VDAs from scratch? Also, do I need to contact Citrix about licensing before attempting any major version upgrade? Not sure if I should build separate servers in parallel to our current ones or just try to upgrade current 1912 servers to 2402. Any information would be appreciated, really appreciate your content over the years, it has really saved me!
Yes, you can in-place upgrade from any 7.x version of CVAD. However, if you want to upgrade the OS on the Delivery Controllers, then you might have to do step version upgrades/replacements because different versions support different OS versions.
Always check the CSS date in your installed license files before upgrading. If not current, download newer license files.
Carl, what is the difference between “Required SA Date” & and “Subscription Advantage” date? I checked the CSS On my installed license and they were out of date. I got newer licenses from my Citrix Account and applied them. Now my CSS date shows 2025.0901 but my Citrix Studio still shows “Required SA date: 2024.0419” when I tried to do the upgrade it kept telling me my environment was unsupported and to contact an admin. I had to roll back the upgrade. We have a concurrent model for Citrix Virtual Apps and Desktop Advanced and the Expiration date is permanent. Any thoughts or suggestions would be helpful thank you sir.
“Required SA Date” means that your licenses must have a CSS date that expires on that date or later.
Do you have the exact error message? Is Citrix License Server the latest version? Is SQL version 2019 or later? Is Windows version 2019 or later?
Also, make sure Citrix Studio > Licensing has the correct Product Edition selected.
can we have mixed windows OS for Citrix DDCs? I have a farm where we already have win 2019 OS installed. Need to add additional DCs at another location in different zone where we got 2022 OS configured. so can we add these new DDCs with OS 2022 to existing farm with OS 2019 version. Citrix farm version is LTSR 2402.
For Delivery Controller I’ve not had any problem doing that. However, StoreFront is not supported on mixed operating systems.
Just successfully upgraded from 7.15 LTSR CU6 to 2402 LTSR CU1. Thank you for the excellent documentation
Hello Carl,
We are planning to upgrade from Citrix 1912 LTSR CU2 on Windows 2016 to CVAD 2203 LTSR latest CU with Windows 2019 provisioned as hosted shared desktop.
We are currently using Citrix App Layering to provision apps and desktop to the users.
During the upgrade we would like to change the application and desktop delivery method to PVS rather applayering.
Can you please guide how we can remove applayering and implement PVS during the upgrade process? What will be the order of upgrade?
Thank you.
Are you using MCS now?
Build new PVS Servers.
Use App Layering to deploy an image. Install the PVS Target Device software. Then convert it to a PVS vDisk.
Hi Carl,
Yes we use MCS at the moment. We want to stop using Citrix App Layering going forward. We can build image using MECM and conver it into a vDisk.
Can we build PVS servers with 2203 LTSR version and keep them ready before we start upgrading our 1912 ltsr environment?
Thank you.
There is no connection between CVAD and PVS. You can build them separately.
We are experiencing connection failure on VDA which was upgraded from 2209 to 2402, session launch is not happening. Session gets disconnected once after launching the application. We checked the event log of VDA machine, and no errors were found, only we can see this info ‘The Citrix Desktop Service detected that a user session has ended. Session ” for user ” has ended; reason code ConnectionFailure.’.
It usually means the app doesn’t run or the app launch times out. There’s a default app launch timeout of 60 seconds.
Thanks Carl,
But we already have timeout policy for 120seconds, this happens only in one of the VDA which was upgraded. We don’t see any connection failure on any other VDA’s.
I have the same problem, can’t connect to upgraded VDA, but I can connect successfully to old VDA from the same client workspace,
Have you managed to solve it?
I ran in to a license problem when attempting to upgrade my delivery controllers from 1912 CU8 to 2203 CU4, error states: Your current license configuration does not allow the use of host connection “AWS-EC2-Prod” for hosting VDAs after the upgrade. For more information, see Knowledge Center article https://support.citrix.com/article/CTX270373, but on checking my license is has the SaaS bit included (we have hybrid license as we have a mix of on-prem and AWS servers).
Any suggestions as to why this is happening?
Greetings Carl,
A customer has his CVAD built on top of 6.5 ESXI Hypervisor, they are looking to migrate their CVAD environment to a new hardware that has 7.0.3 ESXI.
Please note the migration will include migration to all dependences such as the domain, SQL servers , network communication rules,etc ..
( Nothing will change in the environment expect the hardware & hypervisor version.)
Is that supported by our CVAD solution? will that affect control plane components such as DDC ?
Citrix has a list of supported hypervisors. Did you check that list?
Hello there,
I am currently in the planning stages of upgrading from 1912LTSR to 2203 CU4 and I think I have most things covered, but I do have a few questions. I need to upgrade the license server, Studio, StoreFront, Director, Controllers, SQL database, Master image, and Update catalogs. We have a mix of 2019 multi-session and single-session Windows 10 machines VDA machines. Should I assume that the VDA agent should be updated on all machines? I know this is true for 2019 VDA machines, but I’m not sure if it applies to the Windows 10 machines that are currently on 1912. Should they be upgraded to 2203 as well?
Also, I would like to know if there are any other files that need to be backed up aside from taking snapshots and backing up the DQL database. For example, on the StoreFront server, are there any files that need to be backed up in case of any issues?
Thank you.
J
Yes, upgrade all VDAs.
Snapshots of StoreFront servers is sufficient for recovering from a failed upgrade.
Thank you Carl
Hello Carl,
relating to above description “StoreFront -> To upgrade the operating system version of the StoreFront Servers: -> 3. Do one of the following -> (unsupported): join…”
in combination with your comment :
“Snapshots of StoreFront servers is sufficient for recovering from a failed upgrade” (April 5, 2024 at 11:36 am)
i want to ask the following to make sure i understood the roll back scenario:
The StoreFront roll back is sufficient because per default StoreFront server use the local ESENT database located in C:\Windows\ServiceProfiles\NetworkService\AppData\Roaming\Citrix\SubscriptionsStore\\, right?
So in case of upgrading the operating system version of the StoreFront servers i could give it a try with the unsupported way by adding for example additional StoreFront server running on Windows OS 2022 into an existing Store that contains StoreFront server running on OS 2019 if all use the same StoreFront software version.
And if anything goes wrong as roll back i would simply shut down the OS 2022 StoreFront servers and restore the OS 2019 StoreFront servers to a state before i added the OS 2022 StoreFront servers, correct?
Thanks in advance and kind regards
Bernd
I usually snapshot the VMs and revert the snapshot if there’s an issue.
Hi Jason, also, you can upgrade all your master images and VDA machines to 2203 LTSR CU4 BEFORE you upgrade all other infrastructure components. Just make sure you have 1912 LTSR snapshot available in case you need to revert back (it’s highly unlikely that you will have to do this, but better safe than sorry – I always keep minimum one good working previous snapshot on our master image). Ideally, you would have a test machine catalog/delivery group and prod machine catalog/delivery group. Push your new 2203 LTSR image to your test environment first, test all apps and functionality, and if all good, push it to prod. This will save you some time when you upgrade all other components to 2203. Stick to Carl’s (this) document as you have everything that you need in it. Good luck!
Hi Carl!
“Don’t mix Current Release and LTSR components” => do you suggest NOT to mix LTSR Delivery Controllers and newer, Current Release VDAs?
Citrix only provides LTSR support if all components are the same LTSR version. Otherwise Citrix Support will ask you to upgrade everything to the latest Current Release.
Hello Carl,
Thank you for your plethora of knowledge and guidence. Based on my previous inquiries we have narrowed down the issue as to why we cannot delete and/or recreate connection strings to a new SQL and based on another users reply here was:
“Important: we logged in to PowerShell with special Citrix service account with which these databases were initially created. We did this from the main delivery controller and ran the following four scripts separately:”
Recreating connection strings, we are unable to use the original account that originally created the DB’s as they were created using a SQL account not a domain service account. Obviously PS does not allow for this. Is there a potential workaround for this issue migrating to a new SQL server and keeping the existing data? This is the roadblock.
Many thanks to all in this community!
Run Set-MonitorDBConnection -DBConnection $null but leave the datastore defined. You can later use Citrix Studio to move the monitoring and logging databases.
I ran in to a license problem when attempting to upgrade my delivery controllers from 1912 CU8 to 2203 CU4, error states: Your current license configuration does not allow the use of host connection “AWS-EC2-Prod” for hosting VDAs after the upgrade. For more information, see Knowledge Center article https://support.citrix.com/article/CTX270373, but on checking my license is has the SaaS bit included (we have hybrid license as we have a mix of on-prem and AWS servers).
Any suggestions as to why this is happening?
Specifically upgrading the DB for 1912 LTSR (upgrading to 2203) in SQL from 2016 to 2019 SQL Server, what is the best practice approach you’d recommend to doing this? Standalone SQL upgrade from 2016 to 2019?
New SQL Server. Then move the database – https://www.carlstalhood.com/delivery-controller-cr-and-licensing/#changedbstrings
2 questions, moving to a new instance of SQL 2016 (from original being 2016) and doing an in place upgrade of the new 2016 to 2019, is this feasible? Is there something from Citrix that states this is a supported path?
Last, the link you pointed me to, does this refer to SQL 2019?
All SQL versions have the same procedure.
I don’t think Citrix cares if you in-place upgrade SQL.
Sorry to ask this but with my previous questions we are running into an issue we cannot seem to bypass.
When trying to create connection strings, getting this in PS…
“Set-LogDBConnection : A database operation failed and could not be recovered : Reason ?”
and
“set-ConfigDBconnection -dbconnection $csSite
set-ConfigDBconnection : There was a problem communicating with the Citrix Delegated Administration Service.
At line:1 char:1
+ set-ConfigDBconnection -dbconnection $csSite
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (:) [Set-ConfigDBConnection], UnauthorizedAccessException
+ FullyQualifiedErrorId : Citrix.XDPowerShell.Status.AuthorizationError,Citrix.Configuration.Sdk.DataStore.Commands.SetConfigDBConnectionCommand”
emphasis on the permission denied. At this juncture we are stuck. Assuming the scripts are correct, we are running the commands individually and getting the same errors. Here is what we are running…
Add-PSSnapin Citrix*
Set-LogSite -State Disabled
Set-LogDBConnection -DataStore Logging -DBConnection $null
Set-MonitorDBConnection -DataStore Monitor -DBConnection $null
Set-MonitorDBConnection -DBConnection $null
Set-AcctDBConnection -DBConnection $null
Set-ProvDBConnection -DBConnection $null
Set-BrokerDBConnection -DBConnection $null
Set-EnvTestDBConnection -DBConnection $null
Set-SfDBConnection -DBConnection $null
Set-HypDBConnection -DBConnection $null
Set-ConfigDBConnection -DBConnection $null -force
Set-LogDBConnection -DBConnection $null -force
Set-AdminDBConnection -DBConnection $null –force
$ServerName = “SERVERNAME\INSTANCE”
$SiteDBName = “CitrixAPSQASite”
$LogDBName = “CitrixAPSQALogging”
$MonitorDBName = “CitrixAPSQAMonitoring”
$csSite = “Server=$ServerName;Initial Catalog=$SiteDBName;Integrated Security=True;MultiSubnetFailover=False”
$csLogging = “Server=$ServerName;Initial Catalog=$LogDBName;Integrated Security=True;MultiSubnetFailover=False”
$csMonitoring = “Server=$ServerName;Initial Catalog=$MonitorDBName;Integrated Security=True;MultiSubnetFailover=False”
echo $csSite
echo $csLogging
echo $csMonitoring
set-ConfigDBconnection -dbconnection $csSite
set-AdminDBconnection -dbconnection $csSite
set-LogDBconnection -dbconnection $csLogging
set-AcctDBconnection -dbconnection $csSite
set-BrokerDBconnection -dbconnection $csSite
set-EnvTestDBconnection -dbconnection $csSite
set-HypDBconnection -dbconnection $csSite
set-MonitorDBconnection -dbconnection $csMonitoring
set-ProvDBconnection -dbconnection $csSite
set-SfDBconnection -dbconnection $csSite
Set-LogDbConnection -DataStore logging -DbConnection $csLogging
Set-MonitorDbConnection -DataStore monitor -DbConnection $csMonitoring
Set-LogSite -State Enabled
Thank you very much Carl!
After all database connections are null, to reconnect to the database, the first command you should run is:
set-AdminDBconnection -dbconnection $csSite
Hello Carl, still running into this issue whereas we are standing up a new 1912 LTSR to a new SQL 2019 from SQL 2016, backup / restore procedure.
Going through connection strings,I am constantly getting errors only related to logging and monitoring. e.g….
PS C:\Windows\system32> Get-MonitorDBConnection -DataStore Monitor
Get-MonitorDBConnection : A database operation failed and could not be recovered : Reason ?
At line:1 char:1
+ Get-MonitorDBConnection -DataStore Monitor
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : InvalidOperation: (:) [Get-MonitorDBConnection], InvalidOperationException
+ FullyQualifiedErrorId : Citrix.XDPowerShell.Status.DatabaseError,Citrix.Monitor.Sdk.DataStore.Commands.GetMonitorDBConnectionCommand
Permissions appear from a working model to the new set up exactly the same. Any insight on this? Unable to null logging datastore and monitoring datastore. Site is good to go.
Thank you very much!
Hello Todd, last year we also upgraded our Citrix SQL servers from 2012r2 to 2019 which was prerequisite to upgrade from 1912 LTSR to 2203 LTSR.
Important: we logged in to PowerShell with special Citrix service account with which these databases were initially created. We did this from the main delivery controller and ran the following four scripts separately:
1) Existing DB Strings (save the output; this will help you prep the next scripts)
2) Test New SQL Servers (use the output from the above step; just change server names to new servers)
3) Nullify Existing Strings (use -Force switch on all lines; I see above that you only used it on the three lines)
4) Set New SQL Strings
You mentioned that permissions are set up the same; that is good, but also double-check database role membership under User Mapping on the account from which you are running the scripts:
Logging DB must have ConfigLoggingSchema_ROLE, db_owner, public role membership checked
Monitoring DB must have MonitoringData_ROLE, db_owner, public checked
Site DB has bunch of roles checked but you said that Site DB was good for you
Hope this helps.
p.s.
Carl gave me some great tips on this and other upgrades. I almost exclusively use his documentation which practically covers everything Citrix related in much greater detail and clarity than Citrix itself…so huge thanks to Carl one more time 🙂
Cheers,
Petar Lopandic
Hi Carl,
Would you please clarify the bit about Software Maintenance requirements for LTSR/CR? You write “LTSR requires you to be on Customer Success Services Select, formerly known as Software Maintenance.” How about CR? According to the lifecycle KB, it’s also required with an asterisk (Customers with legacy Subscription Advantage have access to Current Releases for the duration of their contract, but are encouraged to upgrade to Customer Success Services.)
What if there’s a licence when SA is dropped? Is CR the way to go then?
Thanks!
After upgrading from 2308 to 2311 (Multi Session 2022) My login time has increased by about 10-15 Sec. This is a simple setup for this test using MCS with the same base image just updated to 2308. Thats the only thing that was updated. I am noticing that TSTheme is sitting for maybe 10 of those sec doing nothing in procmon. Looking at the procmon logs it looks like everything it running synchronous compared to the 2308 procmon output although the GPOs are set correctly. Anyone else seeing this?
Working with a client in an app layering environment.
They want to perform an in-place upgrade of the OS and Platform layers that are built on Windows 10 21HR. They are claiming that Citrix support told them this is supported.
We are trying to discourage this approach.
Have you heard of such an approach being successful?
Please share your thoughts.
Hello Carl!
Is it supported to upgrade 1912 LTSR Delivery Controllers to 2308 Current Release?
Or will we run intro problems going from LTSR to Current Release.
Best Regards, TR
Yes. See https://docs.citrix.com/en-us/citrix-virtual-apps-desktops/upgrade-migrate#versions-you-can-upgrade
Perfect. A follow up question, we are running 1912 LTSR CU0 on Delivery Controllers, running on a SQL 2014. If we want to upgrade to 2308 CR, we figured out that we have to run on SQL 2022 or 2019.
Do we migrate the database first then upgrade delivery controller to 2308?
Can we go from 2014 to 2022 straight away or do we have to bounce on a SQL 2019?
Best Regards, TR
I usually move SQL first so that it is supported by the new version.
Hello! Tell me, is it possible to downgrade the Delivery Controller version from 2203 to 1912 LTSR?
I don’t think so. You’d have to restore the database from backup and revert to snapshots.
We are planning to upgrade Citrix DDC from 1912 to 1912CU8.
SF is also 1912. Do you recommend upgrading to CU8 at the same time?
Or would it be okay to just upgrade DDC to CU8?
Citrix Support might ask for everything to be at CU8. But technically you can update them in separate maintenance windows.
It is not a problem even if the DDC and SF versions are different.
Is it recommended to update to the same version?
Yes. Citrix Support wants specific versions – https://docs.citrix.com/en-us/citrix-virtual-apps-desktops/2203-ltsr/whats-new/cumulative-update-3
Additionally, would you recommend upgrading to CU8 rather than CU7 on the current 1912 LTSR version?
Every CU has bug fixes. I have not heard any issues with CU8.
Hi Carl
Thanks for your detail info, after read your blog and Citrix upgrade guide, both mention upgrade half of the components first (Citrix one suggest upgrade half of the controller first), then upgrade the site’s DB, and then upgrade the remaining components. VDA upgrade can be done later gradually because it should be compatible with new version of the controller. Am I correct?
Based on your experience, may I know you will upgrade the DB and all components in one go (say in-place all over one weekend)? Or you will just upgrade half of the components (or just half controllers) and DB first? then allow users to run a period for pilot test, then upgrade the remaining after pilot success?
I always upgrade all Delivery Controllers in the same maintenance window because they all share the same database. As soon as the database is upgraded only the newer Delivery Controllers will work.
VDAs are forwards and backwards compatible with other Delivery Controller versions.
Thanks Carl
Thanks for your advice. So even if my deployment has multiple zone, then we also need to upgrade all components in the same maintenance windows, because they use share the same DB.
Best regards
Yes. This is one of the reasons I try to discourage zones.
Good Morning,
We upgraded our On Site 1912 CU7 site to 2203 CU3 LTSR over the weekend. everything seems to have gone well, the site is up and running.
the issue i found is that one Admin can logon to the DDC and see the site up and running all the configurations. the other Admin can logon and launch the site and it shows the manual upgrade page, this is on the same server(s) same site.
what would be stuck or blocking that admin’s ability to see the upgraded interface?
Try deleting the saved MMC from %appdata%\Microsoft\MMC
I did this and it still show the same madatory upgrade window.
I believe i have done that before and it fixed it, but not this time.
Good afternoon,
We are looking to upgrade from 1912 CU7 to 2203 CU3. Just looking for anyone who has gone from 1912 to 2203 and if you ran into any “gotchas” that might be good to know about? Any features that might be enabled by default in 2203 that weren’t in 1912? Stuff like that. Any help is greatly appreciated. Thanks!
Virtual Channel Allow List.
Thanks! It’s on the list.
Hi Carl,
I tried several times to find this information by myself before asking you because I know you’re a busy man but you certainly have more connections with the right guys at Citrix than I do : I only find PVS 2203 CU2, wheras CVAD is at the 2203 CU3 level, any plan to release anytime soon a CU3 for PVS ?
Kind regards
Yvan
It’s not uncommon for PVS to be late or skipped.
Hey Carl,
We’ve updated our Citrix back-end from 1912LTSR to 2203.3 LTSR.
Everything seems to be working, but we have a strange issue with Citrix Workspace native detection for all our users.
They login to storefront, but the Workspace detection is not working. It keeps hanging on “Just a moment, we’re detecting if Citrix Workspace app is already installed”. Internally it’s OK, but it does not work from outside the network. (we use Citrix ADC).
Kind regards,
Mark
I think NetScaler needs to be able to resolve the DNS name for the Base URL or something like that. You can use Fiddler to see the HTTP requests that Workspace app is making.
Hey Carl,
Thanks for your fast reply. We logged in through Putty on the both NetScalers, and we are able to ping the base url and it gives reply.
Any other suggestions?
Kind regards,
Mark
Extra info:
We see the ADC looping through here:
“SSO ns_sslvpn_process_sso_conn: After Initialization user HIDDENUSERNAME clientip HIDDENIP sso_state-1 sso_auth_type-5 sso_flags-104”
“SSO sso_svr_output_handler : user HIDDENUSERNAME clientip HIDDENIP state-1 response-0 session-id-5053 sso_flags-104 sso_auth_type-5 copied_nsb-0x0”
“SSO sso_svr_output_handler-after : user HIDDENUSERNAME clientip HIDDENIP state-2 response-0 session-id-5053 sso_flags-6 sso_auth_type-5 copied_nsb-0x1572a33c0”
“SSO nssso_res_hdr_handler : user HIDDENUSERNAME clientip HIDDENIP state-2 response-200 session-id-5053 sso_flags-6 sso_auth_type-5 copied_nsb-0x1572a33c0”
“SSO nssso_res_hdr_handler-forward_2_client : user HIDDENUSERNAME clientip HIDDENIP state-2 response-200 session-id-5053 sso_flags-6 sso_auth_type-5 copied_nsb-0x1572a33c0”
Quick question – Upgrading a customer from XenApp 7.15 CU9 to CVAD 2203 CU2. XenApp 7.15 CU9 is using SQL Express 2014 on the Deliver Controller. Will the standard Delivery Controller upgrade option on the CVAD 2203 CU2 software .ISO upgrade SQL Express automatically, or do I need to do that separately? (CVAD 2203 CU2 does NOT support SQL Express 2014).
It needs to be upgraded separately. https://docs.citrix.com/en-us/citrix-virtual-apps-desktops/upgrade-migrate/upgrade.html#replace-sql-server-express-localdb
Thank you good sir! My original plan was to do the SQL upgrade manually since XenApp 7.15 CU9 supports SQL 2019 Express as well as CVAD 2203 CU2. But then I wondered if would be handled automatically. Appreciate the Citrix link.
Regards,
-Pete
Hi Pete,
Just my 2 cents but, depending on the size of your infra, you should consider hosting the CVAD db on a sql cluster (AlwaysOn) instead of sticking this sql role to only one DC.
Good luck with your migration phases !
Kind regards
Yvan
Carl, what if I was running CVAD 1912 LTSR and…
1) wanted to do an in-place upgrade to CVAD 2203 LTSR, should it work?
2) wanted to set up a new 2203 server and “import all settings from the 1912 server”… is that possible???
1 – Yes
2 – Citrix doesn’t have any tool to extract an on-prem config and import it to a different on-prem farm. But you can use PowerShell commands to export configs (e.g., published apps) and import them. You can find some scripts by Google searching for them.
Hey, thanks for the reply, I know you’re very busy!!
Hello Carl, I have a big issue here and need your help. I have a production farm running as I mentioned before. My new farm is all configured, I tried to test my new farm with netscaler and Internally it is going to the new servers but external it is still going to the old URL. I disable the storefront in Netscaler but it is still not gettting the URL from new farm. What do I am missing?
Are you testing from Workspace app? Does it work from a browser?
I am trying it from the browser and I see the address pointed to the old storfront. I did not tried it from workspace app yet.
In Citrix Gateway > Virtual Servers, edit your Virtual Server. Scroll down to Policies and edit the Session Policies. Right-click a Session Policy and click Edit Profile. On the Published Apps tab is the address of your StoreFront server and store.
Thats great, I think that is the problem. Do I have to change the Beacons also because it is giving me 404 error.
Beacons are only for Workspace app. Beacons help Workspace app determine if Workspace is internal or external.
Hi Carl, Is 404 – File or directory not found.
The resource you are looking for might have been removed, had its name changed, or is temporarily unavailable.
Is this from IIS or do I have to change anything in Netscaler? I got this message after I change the session policy entry with the new Store front web address. Thank you
The WI Address should be something like https://storefront.corp.com/Citrix/StoreWeb. Don’t forget the “Web” on the end. See https://www.carlstalhood.com/citrix-gateway-ica-proxy/#sessionprofiles for details.
Hello Carl, I have been having this issue for few weeks, I created a new farm with the same Web URL for citrix, Everything is the same as my existing farm. Got new Store front and controller. I was testing then new farm after hours, change all my settings in Netscaler, change my web address in session profiles, and every policy from old storefront to new one. When I tried with my Web interface from outside, it gives me 404 – directory not found error message. If I change the URL with the old Storefront address it gives me a page. If I turned off the old SF, It says Cannot Complete the request. Am I missing something in IIS, Netscaler of STOREFRONT? Kind of frustrating right now. Please Help!!!
Internal works? Only external through Gateway doesn’t work?
In the Session Profile, did you add “Web” to the end of the StoreFront path?
Internal is working but from outside it is not. I added Web in the end because it is already there with the existing one. My address in Netscaler is https://my.xxx.com/citrix/xxx1web. Is this the right way? thats how it is configured with the existing URL. Thanks
If your URL has an FQDN, is your NetScaler resolving it to the correct IP address?
I am pretty sure it is resolving the address. How I can check the resolving IP Address to make sure that it is correct?
SSH to the NetScaler and ping the FQDN.
Hi Carl, It is not resolving the name with the new SF IP. What should I do?
I would edit the Session Profile and change the FQDN to an IP address. But you should also fix DNS at Traffic Management > DNS > Name Servers.
Great! I changed it but I am getting the 404 director not found error now. Is this something I can check from IIS?
Hi Carl,
Thanks again for all the great content you create.
A question if you don’t mind: I have been looking around, unsuccessfully, for some information around upgrading VDAs in a UPM environment where the profile version number will change causing new profiles to be created. I think i saw something before about a Citrix policy setting to Migrate helping the cause but can’t for the life of me find it. I am looking to see if there is a way to retain the profile when going from say 2012R2 to 2016-2022 server VDAs without having to migrate user data over. I’m thinking you might have a trusty article i could refer to..
Apologies if that’s been asked already.
Alan
See https://docs.citrix.com/en-us/profile-management/current-release/configure/automatic-migration-of-existing-app-profiles.html
Ah super, again thanks.
Al
Hi Carl,
I followed the “Delivery Controllers” section to upgrade the OS from 2012 r2 to 2019 (method 1) and it was spot on! Citrix documentation is generally very high-level and nowhere near yours in terms of quality and in-depth details.
Thank you so much!
Hi, I am not finding a great source of detail info or document on how or what is the best and fastest way to upgrade/migrate from 6.5 to 1912 LTSR? Any guidance? am not a migration expert so any best steps to help me would be awesome.
There is no in-place upgrade from 6.5. Rebuild everything. Build new Delivery Controllers. Build new StoreFront. Build new VDA machines. Publish apps to the same users as 6.5. Instruct users to use StoreFront instead of Web Interface.
Hello Carl,
Happy New Year 2023!!! I am running a 7.15LTSR and would like to upgrade with 2203 CU2. I am creating a new farm with server 2019 for one storefront, one controller and 3 VDA’s. Should I upgrade my existing citrix version with the new one or new farm is the right approach? I need some expert guidance on this from you. Thank you,
Depends on the number of published apps you’d have to publish again.
Getting from 7.15 to 2203 depends on your current OS. If 2012, you upgrade to CVAD 1912 first, then replace the OS with 2019, then upgrade to CVAD 2203, then replace the OS with 2022.
My current citrix is running on 2016 Std servers, my database is running on 2008 SQl and it will be move to 2014 SQL server. I do not have published apps, all we use is Xen Desktop for our users. If I am configuring a new Farm, does it affect on existing one? Can I use the same License while my production is running for my new one?
Building a new farm with a new database does not affect the existing farm. But you’ll have to plan the cutover of StoreFront.
Thank you so much for your expert advice. I will do that. I believe that I have to change names for site in storefront and can’t keep the same. Upgrade is also an option correct? Thank you!
You can in-place upgrade StoreFront if you’re on Windows Server 2016.
Store name can say the same.
Why change the farm name in Manage Delivery Controllers in StoreFront console?
Can you keep the same name as your production farm for your new one?
Yes. The database names must be different if they are the same SQL server, but farm name can be the same.
Hi Carl,
Would it be a plausible option to have controller, PVS and StoreFront on LTSR, but the VDA and PVS-Device on CR
We recently upgraded controller and PVS to v2203 LTSR, but to use v2206 for VDA and PVS_Device.
Thanks
Technically, yes. However, Citrix Support might want everything on the same LTSR version.
Has anyone seen an issue where after upgrading to 2203, PVS can no longer see the Host resources? When I run the Citrix Virtual Desktop Setup Wizard and authenticate, it takes me to the part where you should be selecting the Host resources… expect there’s nothing there. I even noticed that the “Add host” option was removed from the right-click menu.
Hi Carl. I am having trouble finding your section about upgrading the OS on DDCs. Is there a Citrix reference for the procedure to add higher OS machines to the Site and decommission the old ones that I can provide the customer?
I’m not aware of any Citrix instructions. My instructions are at https://www.carlstalhood.com/cvad-upgrades/#deliverycontrollers
I am planning to upgrade ddc.
Does upgrading from ddc 1912 to 1912cu5 disconnect existing azure hosting? There is an issue with connecting to azure hosting on cu5 in a known issue.
All Citrix services are disconnected while the database is upgraded.
I’m not aware of any issues with upgrading Citrix and Azure connections.
Look at the known issues
Attempts to create a hosting connection to Azure in Citrix Studio might fail with an exception.
Here’s how it came out.
In 1912, is there any problem when upgrading cu5 while connected to hosting?
It seems to indicate that only when creating a new connection, not for existing connections. And I don’t think it applies to every attempt to create new connections or else I would hear customers complaining.
I’ve never seen a problem with hosting connections when upgrading.
Thanks for your kind reply.
I think it will help with the upgrade work.
Hi, Hopefully a simple question here, apologies if it has already been asked…. When following the upgrade path from 7.15 to 2203 will there be any downtime or outages for the users? We have multiple Delivery Controllers and VDA’s so can take them offline individually without affecting users, but is there a point when the DC’s have been upgraded but before the database when users would not be able to connect? Presumably whilst the database is actually being upgraded new connections will not be able to be made (I’m assuming any existing connections would be OK)? Thanks.
Correct. When the Delivery Controllers are disconnected from SQL then launches probably won’t be possible. Already logged in won’t be affected.
Thanks Carl, we have done the upgrade now and I can confirm that we didn’t lose any existing user connections to any VDA’s during the whole process. I had to run the SQL upgrade script manually, but it was very quick (less than a minute) and we didn’t get any calls from users so all good!
Hello, I’m a long time follower and first time commenter looking for some advice on how to proceed. I currently have a small Citrix farm that consists of two servers and one Netscaler virtual appliance. Both of the servers are currently running Windows 2012 R2 and I am looking for the best way to replace these with a newer Windows version. What would be the best way to proceed?
Do you want to rebuild everything, including the database? If so, then start from scratch. You can cutover your FQDN to your new StoreFront servers.
Keeping the database takes more effort. The official method is to add more servers and then remove the old ones as I detailed in this guide. Another option is to shut down a server and rebuild it with new OS but same CVAD version and then use PowerShell commands to connect it to SQL. When you remove the old server, do not delete it from AD or else it won’t be able to connect to SQL.
I recommend engaging a consultant to help you.
Can we upgrade from 7.14 to 2203LTSR directly?
It will probably work but not supported – https://docs.citrix.com/en-us/citrix-virtual-apps-desktops/upgrade-migrate.html#versions-you-can-upgrade
I need to upgrade a customers CVAD 7.8 to 7 1912 LTSR CU5. Should I do this directly (Delivery Controllers) or with a step between with 7.15 LTSR?
regards, Stefan
Go directly to 1912. https://docs.citrix.com/en-us/citrix-virtual-apps-desktops/1912-ltsr/upgrade-migrate.html
Hi Carl,
We’ve upgraded the StoreFront Servers from 1912 LTSR CU2 straight to CU5 and followed this step:
– Remove a StoreFront sever from the Server Group and load balancing.
Upgrading is fine but don’t get the option to add it back to the server group post upgrade – would you know the reason for this?
Thanks in advance.
I think they want you to build new StoreFront servers, add them the new Server Group, then swap them out on the load balancer.
I am guessing this is not the right area for my question but I am going to give it a go. We are planning to upgrade from 7.15 CU3 to 1912 Cu5 or which ever is the latest build. Do you see any issues with that? How long does the upgrade of the DB typically take?
Second we want to deploy Citrix on AWS but not using Citrix Cloud service. For all practical purposes it would be similar to on-prem using EC2 instances for the management plane and managing EC2 instances for the workloads. Is this possible, or is it better to have the management plane on-prem with a direct connect to AWS and manage workloads that way… This will be primarily for DR and use when upgrading.
Hola! A new version 2203 has just been released. It’s not clear if it’s CR or LTSR?
It’s currently both, but 2203 will be the LTSR version going forward.
I see High Availability mentioned here. I’ve been searching for a definitive answer on how to set it up and how it works for a while and can’t find anything. We’re setup with 2 DCs and 2 storefront servers, but high availability definitely isn’t working.
What exactly isn’t working? You typically load balance StoreFront. StoreFront points to both Delivery Controllres.
This part of in place upgrades for Delivery Controllers is what I’m referencing, “If High Availability is configured correctly, then Delivery Controllers can be upgraded during the day.” I’ve attempted this before, but brought down citrix completely. What does a typical highly available configuration look like for CVAD? I haven’t been able to find definitive documentation about it anywhere. We have our storefront servers load balanced. We have 2 delivery controllers. Any time I shut down one DC Citrix is inaccessible. I see local host caching and SQL DB high availability, but nothing about how high availability for Storefront and Delivery Controllers should work or be configured.