Navigation
- Change Log
- Script to Extract Configuration
- Configure NetScaler from PowerShell
- Nitro REST API Documentation
💡 = Recently Updated
Changelog
- 2019 Mar 11 – Script to Extract Configuration – rewrote the section in instructional format
- 2018 Dec 2 – Configuration Extractor – added a nFactor visualizer
- 2018 Nov 17 – Configuration Extractor – Out-GridView (GUI) for vServer selection
- 2018 Sep 19 – Configuration Extractor – several fixes
- 2018 July 4 – Configuration Extractor
- Added “*” to select all vServers
- Updated for 12.1 (SSL Log Profile, IP Set, Analytics Profile)
- Extract local LB VIPs from Session Action URLs (e.g. StoreFront URL to local LB VIP)
- Extract DNS vServers from “set vpn parameter” and Session Actions
- 2018 Jan 4 – Configuration Extractor, Sirius’ Mark Scott added code to browse to open and save files. Added kcdaccounts to extraction.
- 2018 Jan 3 – new Powershell-based NetScaler Configuration Extractor script
NetScaler ADC Configuration Extractor
NetScaler ADC Configuration Extractor extracts every NetScaler ADC CLI command needed to rebuild one or more Virtual Servers. Here’s how to use the script:
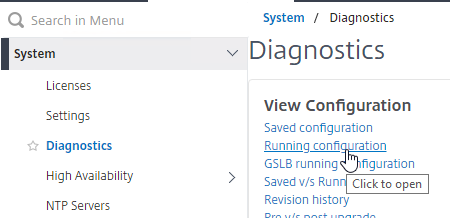
- The extraction script loads a NetScaler ADC Configuration file and parses it. To get a NetScaler ADC Configuration file:
- On your NetScaler ADC, go to System > Diagnostics > Running Configuration and then click the link on bottom to save text to a file.
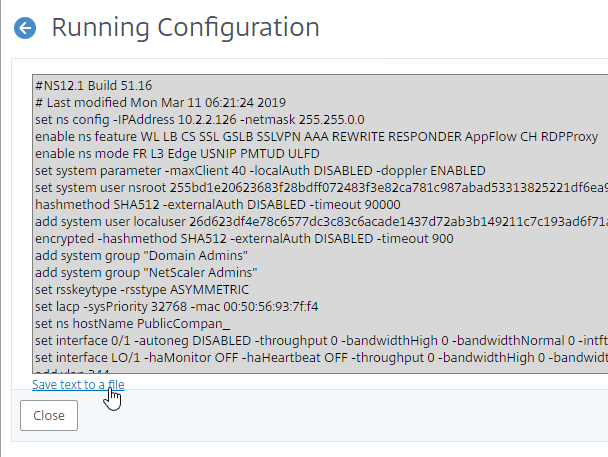
- On your NetScaler ADC, go to System > Diagnostics > Running Configuration and then click the link on bottom to save text to a file.
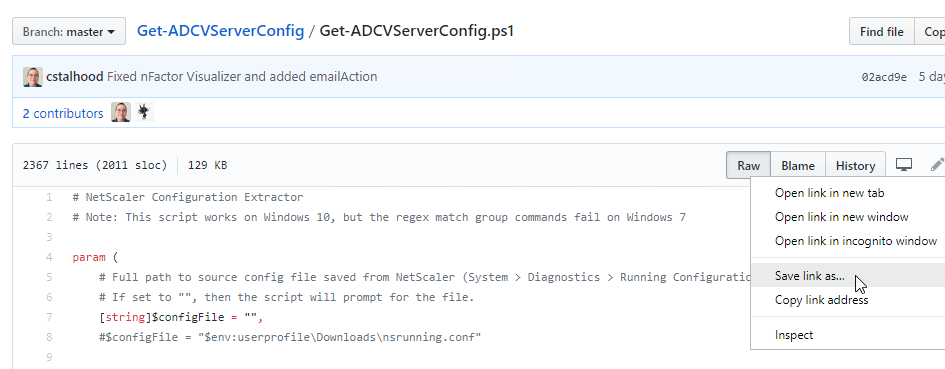
- To download the extraction script, point your browser to https://github.com/cstalhood/Get-ADCVServerConfig/blob/master/Get-ADCVServerConfig.ps1, right-click the Raw button, and Save link as.
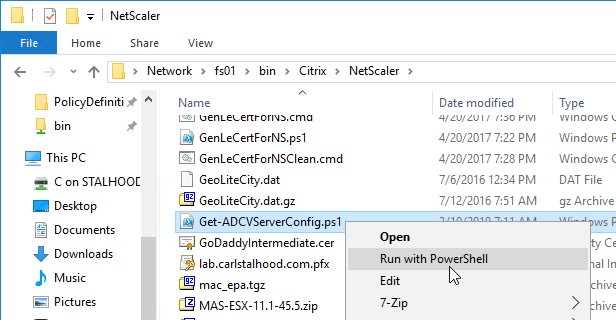
- Run the extraction script in PowerShell. One option is to right-click the script file and click Run with PowerShell. (note: the script doesn’t seem to work on Windows 7)
- Browse for the Running Configuration file that you saved from an appliance.
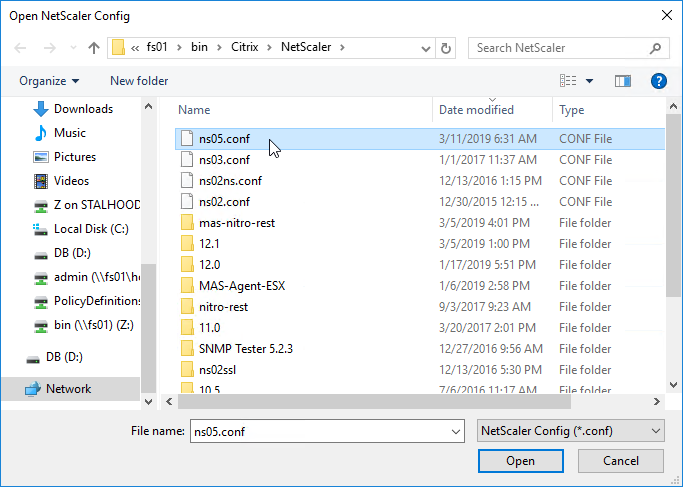
- The script will prompt you to select one or more Virtual Servers.
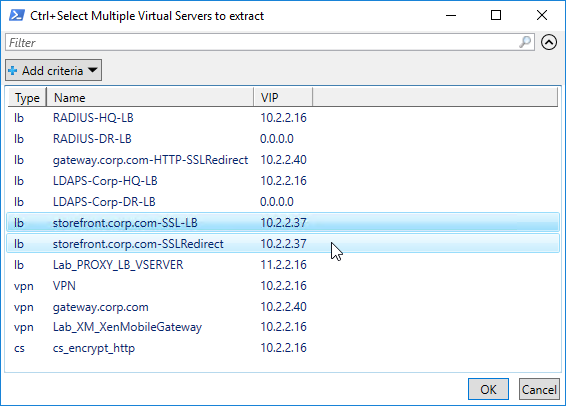
- The script then enumerates all objects linked to the chosen Virtual Servers (e.g. Responder Policies) and provides their configuration too.
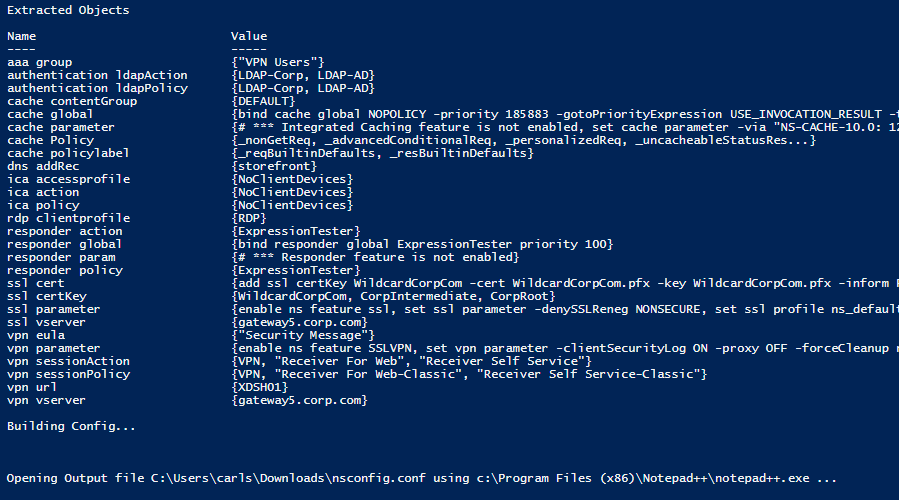
- The script also outputs global settings that might affect the operation of the chosen Virtual Servers.
- The CLI output is listed in proper order. For example, create monitors before binding them to Service Groups.
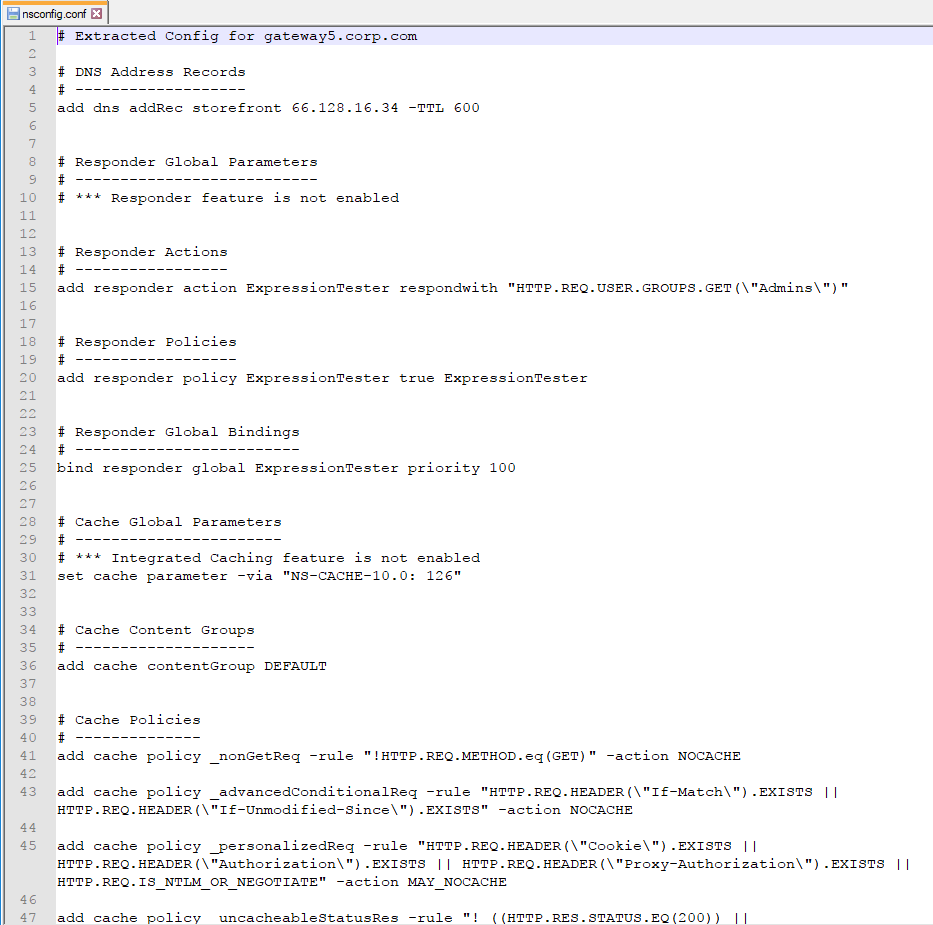
- If the config includes an “authentication vserver”, then a nFactor Visualizer will be shown.
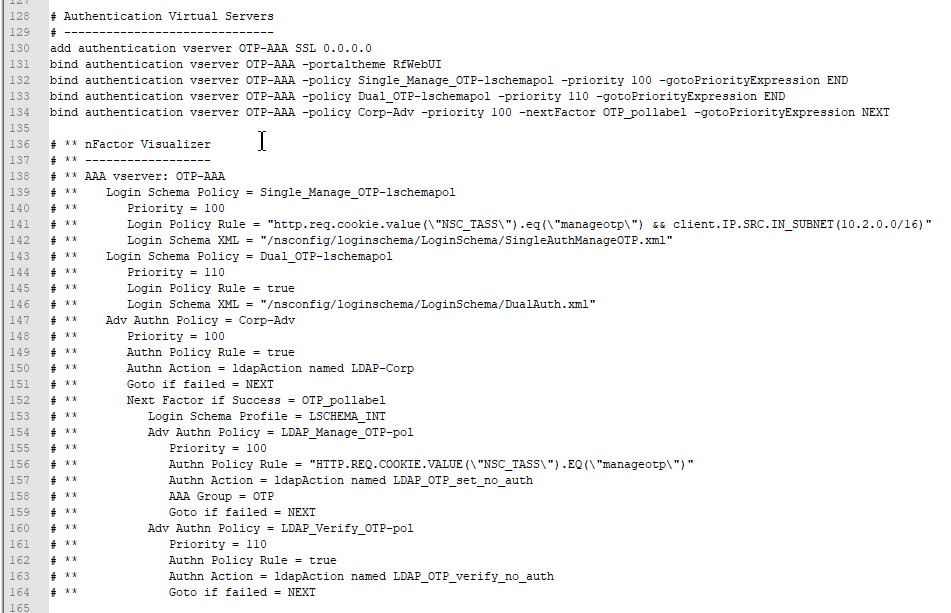
- The extracted Virtual Server CLI configuration can be used for documentation
- Or you can apply the outputted configuration to a different NetScaler ADC appliance:
- To import this output to a different NetScaler ADC, first change the IP addresses of the outputted Virtual Servers so there won’t be any IP Conflict after you import.
- SSH (Putty) to the other NetScaler ADC.
- Then simply copy the outputted lines and paste them into the SSH prompt.
- Alternatively, for longer output file, you can upload the output file to the other NetScaler ADC (e.g. upload to /tmp directory), and then run batch -fileName on the new NetScaler ADC while specifying the uploaded filename (e.g. /tmp/nsconfig.conf).
- Note: the batch command requires that the input file name be in lower case only and without any spaces in the file name.
I originally attempted a dynamic extraction using complicated regular expressions, but there wasn’t enough control over the extraction and output process. The new PowerShell script explicitly enumerates specific objects, thus providing complete control over the output. For example, before binding a cipher group to a Virtual Server, the current ciphers must first be removed.
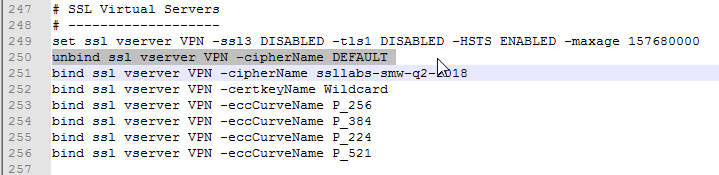
The script uses several techniques to avoid false positive matches, primarily substring matches.
Let me know what bugs you encounter.
Configure NetScaler ADC from PowerShell
You can use any scripting language that supports REST calls. This section is based on PowerShell 3 and its Invoke-RestMethod cmdlet.
Brandon Olin published a PowerShell module for NetScaler at Github. 💡
CTP Esther Barthel maintains a PowerShell module for NetScaler at https://github.com/cognitionIT/PS-NITRO. See Citrix Synergy TV – SYN325 – Automating NetScaler: talking NITRO with PowerShell for an overview.
The below NetScalerPowerShell.zip contains PowerShell functions that use REST calls to configure a NetScaler appliance. It only takes a few seconds to wipe a NetScaler and configure it with almost everything detailed on this site. A glaring omission is file operations including licenses, certificate files, and customized monitor scripts and the PowerShell script assumes these files are already present on the appliance.
[sdm_download id=”1909″ fancy=”0″]
Most of the functions should work on 10.5 and 11.0 with a few obvious exceptions like RDP Proxy. Here are some other differences between 10.5 and 11.0:
- PUT operations in NetScaler 11 do not need an entity name in the URL; however 10.5 does require entity names in every PUT URL.
- https URL for REST calls works without issue in NetScaler 11, but NetScaler 10.5 had inconsistent errors. http works without issue in NetScaler 10.5.
Nitro REST API Documentation
NetScaler Nitro REST API documentation can be found on any NetScaler by clicking the Downloads tab. The documentation is updated whenever you upgrade your firmware.
Look for the Nitro API Documentation.
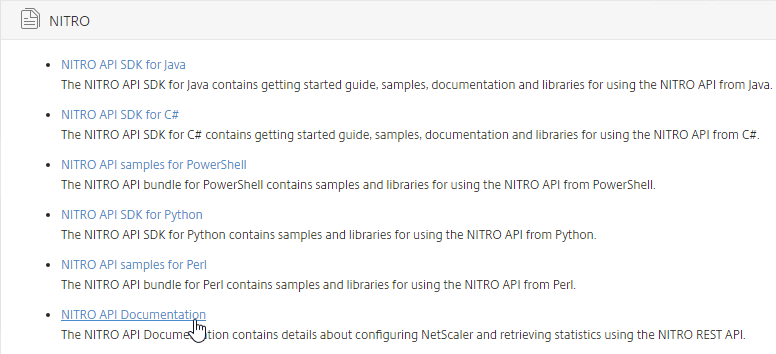
Extract the files, and then launch index.html.
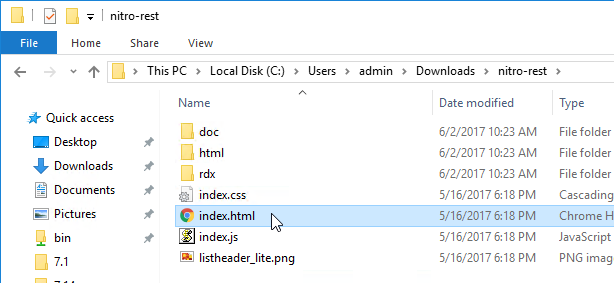
Start by reading the Getting Started Guide, and then expand the Configuration node to see detailed documentation for every REST call.
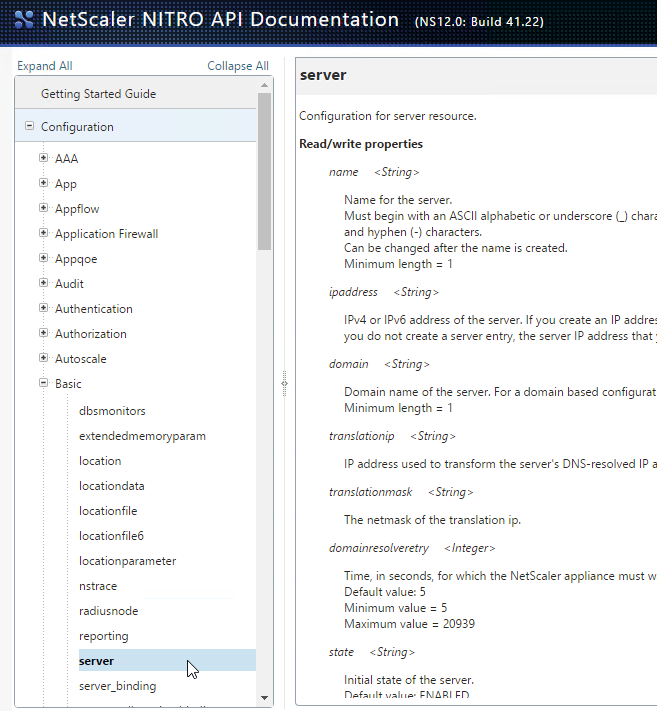
The Nitro API is also documented at REST Web Services at Citrix Docs.
Hi Carl
Great script, just wanted to know why the SNMP Users/Groups/View is not extracted from saved config and put into the new config. Did I miss something? Not sure what else is missing from original config file and not pulled into new config files.
Thank you
Carl
Thank you for all your contribution to the community.
I have a situation where a company is using two different domains, domain one is configured in Active Directory: Example company.local and an email domain called company.com. Up to now they have been using samaccountname to logon via the Netscaler. Company now wants to logon using samaccountname, UPN with @company.local and via email UPN with @company.com. Configuring the NetsScaler for use with samaccountname and company.local UPN is easy as I can query the LDAP server. Do you know how to configure the NetScaler to allow the users to logon via the email UPN @company.com? How is this achieved since the email domain @company.com does not have Active Directory?
Appreciate your help with this. Citrix support says this is not possible.
Regards
JB
Active Directory accounts don’t have @company.com as UPN? If they do, then configure the LDAP Policy/Server Logon Attribute as userPrincipaName instead of samAccountName.
Used this script multiple times and it’s ace! Thanks Carl.
Carl,
I’m having trouble getting my scripts to work against a 13.1 ADC using the NetScaler powershell module. Works fine against a 13.0 instance. I narrowed it down to new-NSLBServiceGroup that fails with an errocode 278. My ciphers and protocols are good as I can create servers/VIPs with the respective functions.
Example Command –
New-NSLBServiceGroup -name test -servicetype http -healthmonitor yes -state enabled
I tried against two different 13.1 ADCs and got the same results. 13.0 and prior works all day long. Any ideas? Kinda pulling my hair out at this point.
Are you getting the error about “sc”? sc is SureConnect, which was removed from 13.1. You can use Github Issues to ask the author to remove it. Or fork the repo and remove it yourself. https://github.com/devblackops/NetScaler/issues
You hit the nail on the head. Thanks!
Invoke-RestMethod : { “errorcode”: 278, “message”: “Invalid argument [sc]”, “severity”: “ERROR” }
Great script Carl!
Thank you.
Carl,
I work for an organization that requires the settings to be listed for DR purposes. I have used the Netscaler_Script_v2_6.ps1 script and it did exactly what I was wanting, but when I run it against a Citrix ADC VPX I get errors about “WARNING: No columns specified and therefore, specified headers will be ignored.”
I have looked through your other scripts, but do not see anything about exporting or capable of doing anything like the original script. Am I not finding a switch on something?
I appreciate all that you do for the community.
Keith L. Jones
Can you be more specific about which script? I’m only maintaining the ones at https://github.com/cstalhood
Does anyone have a NETSCALER 14,000 boot disk and data disk?
I am Looking for a script – I think it will have to be a POWERSHELL script that uses WINSCP.exe or WINSCP.com to log into all my VPX instances and download the ns.conf for backup purposes. Has anyone worked on something like this? Please help and share!
Citrix ADM does that automatically for any NetScaler it manages.
How? I want to save the configuration to a storage device where does the ADM do that. Independent of any other operation?
ADM downloads it to ADM’s drives or database. There’s an option in ADM to perform an external transfer using SCP, SFTP, etc.
I can not find this under configuration jobs . Can you guide me further?
Search for “backup settings” at https://www.carlstalhood.com/citrix-application-delivery-management-adm-13-1/
thank you – but These are ADM backups, not ADC backups.
I have written a CMD based .bat script which calls winSCP.com and passes another script that iterates through all my VPX instances and backs up all ns.conf using the hostname.conf or IP.conf to my local machine. Don’t have admin access so could not use powershell and 3rd party tools. I consider this a win. Thanks for your assistance.
ADM takes backups of every ADC it is monitoring.
You are right I found it on the ADM but my script is a lot more efficient and puts the backups exactly where I want them faster. Thank you again for your support
I just got a NS 14000 on eBay. Does anyone know that format that the DATA disk should be in? or have a copy of the data disk image they can share?
Hi,
If I want to take backup few of Netscaler from ADM then i we can do it, Suppose 100 VPX is config on ADM out which i want to take only backup of 40 then how i can do it
Two different ADM appliances? I think backup settings are global.
Hi Carl,
Thanks again for all the writeups… I am slowly working myself up (or maybe even sideways) the ADC ladder 🙂
Whilst I am familiar with setting up SSH key access to ADC’s from a Linux system and running bash commands to poll/pull data, I cannot seem to find anything online that gives me info on running NITRO scripts using SSH key as I do not want to list passwords on automated scripts.
Any suggestions or leads to use SSH key on NITRO scripts would be gratefully received.
Thanks in advance,
Newbie.
Nitro is a REST API that is HTTP-based (no SSH).
PowerShell has a method of asking a user for a password and securely saving it in a file for later retrieval. I suspect Linux can do the same.
For production scripts, you should have an orchestrator tool that can capture credentials and pass them to your script as variables.
Carl the script is really awesome. Thank you. Has anyone come up with a way to automate collecting screenshots of a CSVS, cert used, the CS-POL and CS-ACT, the LBVS, SRVG and Members?
Basically, where I work they want screen shots and not the actual CLI config.
I can use SNIPPING tool and cut and paste each screen into a WORD template, but this is time consuming.
I also used MS STEP RECORDER but this records all the clicks as steps and you spend a lot of time deleting all this extra garbage.
Carl, as always great article. I am working on a very large configuration file and need to remove a lot of vservers. So I ran your powershell script with that configuration and it took almost 30 minutes to load it to where I could select the vservers. I have a file that has all the names of the vservers I need the full configurations for. Can your script pull from that file and then output the configuration file for those vservers as if I selected them individually? Thanks in advance.
I recently modified the script to speed up that process. When did you last download the script?
Otherwise, I think you can specify the $vserver argument when running the script.
I downloaded it yesterday. The slowness I am sure was the size of the file (config file is over 14 MB). I will look into the $vserver argument. Thanks again.
If anyone else is getting 404’d when trying to hit the downloads section on their appliance, you can grab the tgz directly from /var/netscaler/nitro/ using WinSCP
On a newly deployed ADC I am getting a 404 when trying to download nitro-rest.tgz, is it stored somewhere in particular on the appliance?
Hey Carl,
I am looking to pull a list of ALL Vservers, associated IPs and Ciphers they are using, is there any commands or script to get these info in tabular form. Output will be something like below:
———————————–
vserver | IP | Cipher
————————————
The easy way is to parse the ns.conf file. Look for “bind ssl vserver” to see the cipher binding commands. For customer ciphers, you’d also need “add ssl cipher” to see the actual cipher suites.
Something similar can be done using Nitro. sslvserver_sslciphersuite_binding https://developer-docs.citrix.com/projects/citrix-adc-nitro-api-reference/en/latest/configuration/ssl/sslvserver_sslciphersuite_binding/
Thank you very much, much appreciated Carl!
Hello Carl,
How to monitor cpu utilisation, vip,services and threshold throughout bandwidth in netscaler vpx adc.
SNMP. Citrix ADM automatically polls for these SNMP counters. https://www.carlstalhood.com/citrix-application-delivery-management-adm-13/
Thanks Carl. I’m currently using Citrix netscaler vpx 12.1adc. Does Citrix ADM is free? Or should I buy a new license.
Can’t I configure email alerts directly on netscaler vpx?
Yes, ADM is essentially free.
Thanks a lot. Can you please tell me or share me the procedure of installing and login to the adm?
See https://www.carlstalhood.com/citrix-application-delivery-management-adm-13/
Carl, I see you all over on the Citrix boards too. You seem to be the Netscaler/ADC genius! Here’s a stumper for you… I figured if anyone knew, it would be you.
How do you get the monitor status/feedback for a service via Nitro? Have you figured out how? If I go to the cli and do something like show service SERVICENAME | grep “Last response:” it spits back the pertinent info, like “Last response: Failure – HTTP response code 503 received”. This is such valuable info that seems only available in the GUI and the CLI.
$100 Amazon gift card for you if you tell me where it is in Nitro. Not kidding!
Cheers,
Chuck
GET http://myadc/nitro/v1/config/service_lbmonitor_binding/servicename has a lastresponse property. https://developer-docs.citrix.com/projects/citrix-adc-nitro-api-reference/en/latest/configuration/basic/service_lbmonitor_binding/
Incredible! I’ve looked for 2 days and you knew exactly where it was. You have my email, reply with yours and I’ll send the gift card. Worth every penny!
Hi Carl, It is really good to see your script which could help extract specific configuration. However, when I run script on powershell, it doesn’t show any output on Notepad++. It just get closed on its own. May you please help me?
I fixed that issue. My requirement basically is to import config in excel or .csv format. Is it possible by any chance?
Those are not formats that NetScaler ADC can use. There are output functions that can be modified to your desired format. Can you provide more info on what you’re trying to accomplish? If you’re just looking for a list of VIPs and Servers, you can easily write a for loop that finds a vServer, checks its bindings, and then gets the IP addresses from the bindings. Nitro API can also output the list of service bindings.
Hi Carl,
I recently upgraded my Netscaler firmware version to 12.1.56.22 and after few days HA Sync stopped on secondary device. Unable to connect on SSH port and also unable to run trace on run cli from diagnostic options of GUI.
Can you please suggest if this is a known issue with this firmware version. And how I can fix it.
I launch the script on a ‘ns.conf’ files with Windows 10 and an ADC 13 running config, I select my virtual server, the script end well but nothing happen after 🙁
The ns.conf remain the same, it should edit the files right ? Nothing else is created in the directory. Have you got an idea ?
Regards.
I am looking for scripts which can configure basic SSL based Storefront, Director, WEM loadbalanced VIPs and bind Gateway on the latest NSVPX-ESX-13.0-47.24_nc_64. I have a lab environment and would really like to automate the basic Gateway configurations – but I am not a scripter. I tried to get my head around this NITRO stuff/Powershell – i find it very hard to grasp it.
Searched and even tested Esther Barthel’s https://github.com/cognitionIT/PS-NITRO scripts but they seem to have errors. Somethings work and something error out.
Please help me out 🙂
-Manoj
Here’s one – https://github.com/slauger/netscaler_docs
What language are you using? PowerShell sometimes has difficulty with untrusted certificates on the NSIP.
My method is to see what others are doing and then write my own scripts.
Use this to get past untrusted certs in PowerShell or buy a public cert.
add-type @”
using System.Net;
using System.Security.Cryptography.X509Certificates;
public class TrustAllCertsPolicy : ICertificatePolicy {
public bool CheckValidationResult(
ServicePoint srvPoint, X509Certificate certificate,
WebRequest request, int certificateProblem) {
return true;
}
}
“@
[System.Net.ServicePointManager]::CertificatePolicy = New-Object TrustAllCertsPolicy
posted some updates to https://github.com/closedstack/PS-NITRO and requested Esther / CognitionIT to merge it to master. Among other things.. to collect statistics for VServers, Determine if a node is primary, and a coule of scripts to collect inventory and dump them into CSVs
Hi Carl
we have some method to create a task scheldule in Netscaler to disable and enable some members group from one service group via scripting.
Greatings
NetScaler has a BSD shell with cron. Or you can use a scheduler on any remote machine and have it run scripts that do Nitro API to the NetScaler.
Thank Carl with cron work perfect!!!!
Hi Carl. Any idea if NITRO can be used to send arbitrary shell commands to the NetScaler? I’m using Ether Barthel’s PS module and the built-in cmdlets work great, but I don’t see any way to send, e.g. “shell; df -h /var” and get that back.
I don’t think so. But GET http:///nitro/v1/stat/ns should give you some disk stats.
Thanks, Carl. While disk stats will prove helpful, unfortunately, for my particular requirement I was forced to go a different route. Since I needed to run the following command “find /var/ns_system_backup/ -maxdepth 1 -name backup* -mtime +14 -exec rm -rf {} \;”, I wrote a PowerShell script that calls “plink.exe” from the Putty distribution, and runs it against the list of NetScalers. Thanks for the help!
HI could you please tell me in details. I also want to run the sae command “find /var/ns_system_backup/” but from my ansible playbook. And I could not find any module to let me run shell commands on netscaler from ansible.
How about an aritcle on Ansible?
Fantastic Carl. The power shell script saved me four hours and a couple of hundred greps.
Nice. I wish Citrix would add similar functionality to their products.
Hi Carl,
This is really cool stuff.
I was trying to get ssl certificates with bindings plus I want to add one more column there for Certificate expiration dates.
Any suggestion on this.
Thank you for a great article
Carl- I am looking to pull a list of ALL SSL Certificates installed on the Netscaler and each resource – each SSL cert is bound to.
I have inherited an SSL MESS and the GUI is too slow and painful to go through the 400 + certs.
I was hoping a PS script would work but I do not know how to start this.
Thanks
Leo
One method is to grep the running configuration for “ssl certKey”. That should give you the add and bind commands.
“show ssl certKey” shows all certificates.
“show ssl certKey MyCertKeyName” shows where it is bound.
Also, http:///nitro/v1/config/sslcertkey_binding?bulkbindings=yes gives you a JSON of all bindings.
When I did the JSON – I received this:
{“errorcode”:-1,”message”:”Invalid query parameters”,”severity”:”ERROR”}
What build of NetScaler? Download the Nitro documentation from your Downloads page and check the syntax.
I had to add ?bulkbindings=yes to get it to work.
11.0.70.12
Hello Leo,
you can try my python script getcertbind.py
https://github.com/pehruby/nsbcfg
Petr
I got something for people in Leo’s situation. There is Powershell Nitro Library from Citrix I have added some scripts in my branch to collect inventory on VServers and associated certs (might get merged into the original repo maintained by CognitionIT as well) https://github.com/closedstack/PS-NITRO
I have a python script to allow parsing certs over the network which can be very handy since it allows getting expiration dates for certs bound to servers and/OR VIPs https://relevantsecurity.wordpress.com/2018/12/29/parsing-certificates-on-sites-using-python/
Hey Carl,
For the headers in my version of powershell, it threw an error (the content-type=application/vnd/etc)
The fix was to use the -content-type [String] flag rather than the dictionary object to specify the content-type header. Hope this helps anyone else running into the error I was facing yesterday.
For reference, the error was “The ‘content-Type’ header must be modified using the appropriate property or method.
-Trey
Unfortunately, I haven’t updated that script in a while. You’ll find Esther Barthel’s much more current scripts at https://github.com/cognitionIT/PS-NITRO