Navigation
Workspace app is the new name for Receiver. This post applies to all Workspace app versions, including the Current Release version 2409.10 and the LTSR version 2402 CU3.
- Change Log
- Workspace app versions
- Overview
- Uninstall Old Workspace app Clients
- Installation and Configuration
- Workspace app ADMX GPO Template
- Pass-through Authentication
- Automatically add StoreFront Accounts to Workspace app
- Control Shortcut placement on Desktop and Start Menu – and Workspace Control (Session Reconnect)
- Enable Prelaunch
- Control Device Mapping Prompts
- Desktop Lock
- Use Studio to configure Workspace app Accounts in Published Desktop
- Published Desktop – configure Workspace app to place shortcuts
- Script / Automate Workspace app Self-Service
- Microsoft Teams
- Troubleshoot:
💡 = Recently Updated
Change Log
- 2025 Jan 16 – updated article for Workspace app 2409.10
- 2025 April 2 – Versions – updated for Workspace app 2402 LTSR Cumulative Update 3
- GPO Settings – SSO in Win11 24H2 requires Enable MPR notifications for the System; Desktop Viewer Toolbar Options
- Registry Values – Remember USB connections
- 2023 Nov 15 – Global App Configuration Service is now available to all on-premises customers even if no Citrix Cloud entitlement.
- 2023 May 4 – Pass-through Authentication – added GPO setting Enable MPR notifications for the System
- 2023 Mar 22 – updated article for Workspace app 2303; anti-dll injection GPO setting
- 2022 Dec 19 – updated article for Workspace app 2212; app protection GPO setting
- 2022 Nov 4 – Versions – updated for Workspace app 1912 LTSR Cumulative Update 7 Hotfix 2
Workspace app Versions
Citrix Workspace app uses a YYMM (year/month) versioning format, of which version 2409.10 (24.9.10.28) is the newest Current Release. See Citrix Docs for the list of new features, some of which only apply to Citrix Cloud.
Workspace app 2311 and newer have a new installer interface.
Workspace app 2303 and newer automatically install the App protection components with an option to start them after installation. Older Workspace apps have an option to install App protection and if you don’t select this and later want App protection then you must uninstall Workspace app and reinstall it.
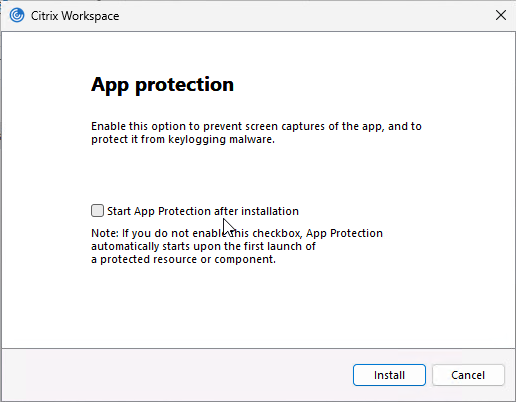
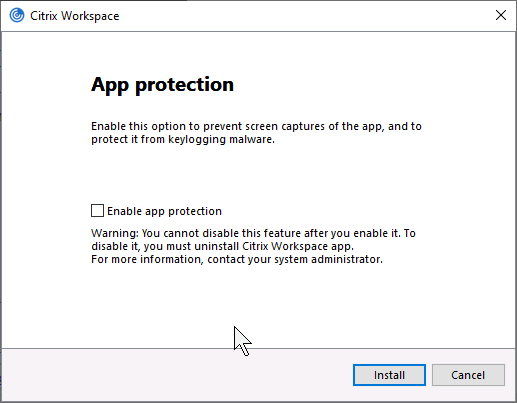
- See App Protection at Citrix Docs to enable App protection for the authentication screen. Workspace app 2305.1 and newer automatically start it for authentication if you have selected the Start App Protection check box during installation.
The newest Current Release version of Workspace app is version 2409.10.
The newest LTSR (Long Term Service Release) version of Workspace app is version 2402 Cumulative Update 3.
Workspace app Modules
The Workspace app installer deploys multiple modules. Here are the important ones:
- ICA Engine (wfica.exe) – process that uses the ICA protocol to connect to published apps and desktops.
- Self-Service (selfservice.exe) – gets icons from StoreFront and displays them in a Window. When an icon is clicked, Self-service passes the ICA file to the ICA Engine to establish a connection.
- Single Sign-on (SSON) for ICA (ssonsvr.exe) – captures user credentials and submits them to VDAs after an ICA connection is established
- Workspace Auto-Update (CitrixReceiverUpdater.exe) – Notifies users of Workspace app updates. The most recent name for this component is Citrix Workspace Update.
Custom ICA files are no longer supported. However, Ryan Butler has created a script that asks StoreFront for an ICA file. Explicit credentials are supported. Find the script at Github.
Workspace app Discovery and Beacon Process
If you are using Workspace app’s built-in user interface (instead of a web browser), then Workspace app first prompts you to perform discovery, which is also called Add Account.
Workspace app will contact the FQDN and request download of the StoreFront Provisioning File.
- If you entered a StoreFront FQDN, then Workspace app will download the Provisioning File directly from the StoreFront server.
- If you entered a Gateway FQDN, then Gateway will first prompt the user to authenticate. After authentication, Gateway will connect to its configured Account Services address, and download the Provisioning File from StoreFront. The Account Services address is configured in the NetScaler Gateway Session Profile on the Published Applications tab.
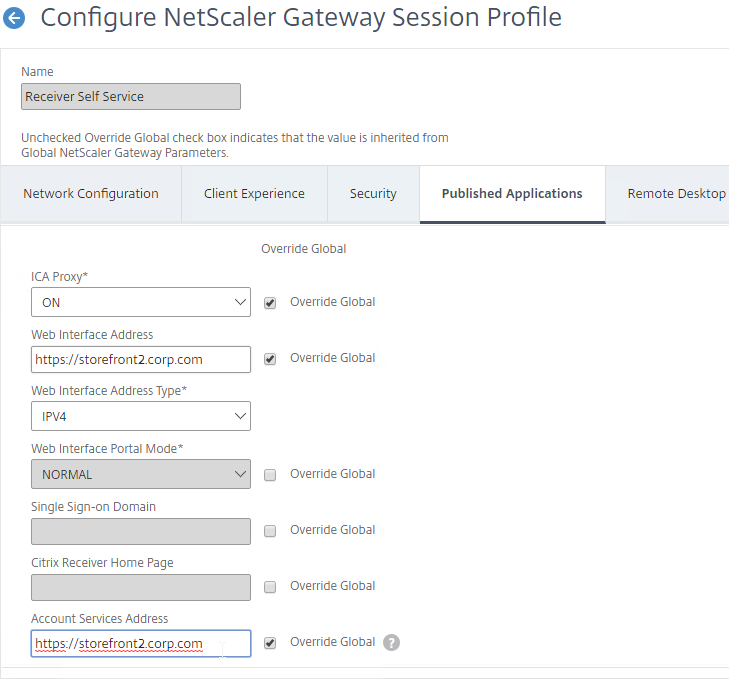
If your StoreFront server is configured with multiple stores, then the user will be prompted to select a store. Unfortunately, there’s no configuration option in NetScaler Gateway to force a particular store.
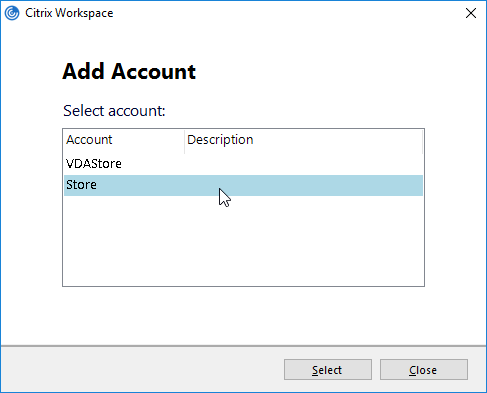
- One workaround is to hide the store that you don’t want visible externally. See How to configure Receiver to a Store that is not advertised for special syntax.
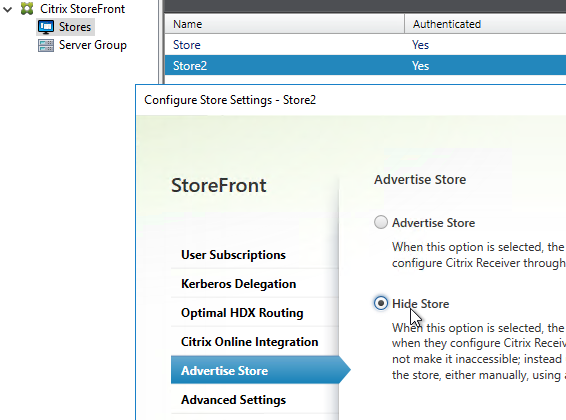
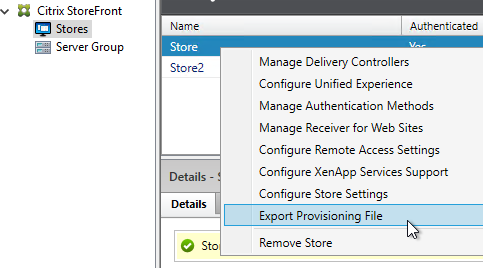
The Provisioning File downloaded from StoreFront is an XML document containing values for several items configured in the StoreFront console. You can export the Provisioning File from the StoreFront console by right-clicking a Store.
The ReceiverConfig.cr Provisioning File looks something like this:
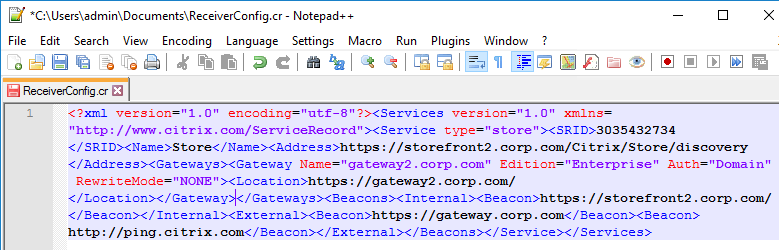
Here are the values in the Provisioning File:
- Address – the Base URL configured in StoreFront Console
- Internal Beacon – as configured in StoreFront Console. This can be the Base URL, or a manually specified URL.
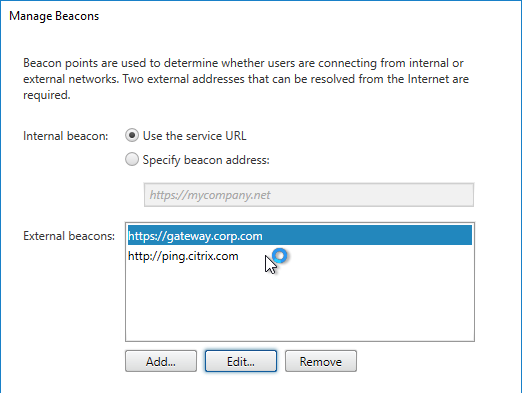
- External Beacons – as configured in StoreFront Console
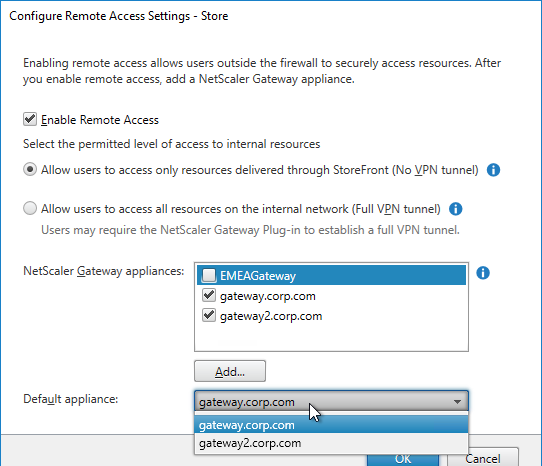
- Gateways – as configured in StoreFront Console. If there are multiple Gateways, when enabling Remote Access on the Store, then only one Gateway is selected as Default
- SRID – Store ID. An important value to consider for multi-datacenter configurations. The SRID is set when the Store is created. It can also be changed by editing C:\inetpub\wwwroot\Citrix\Roaming\web.config.
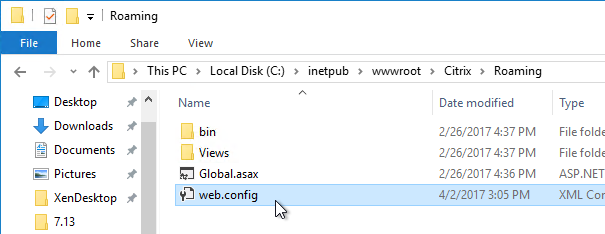
Workspace app reads the Provisioning File, and configures itself by inserting the file’s contents into the user’s registry. The values are located under HKCU\Software\Citrix\Dazzle\Sites and HKCU\Software\Citrix\Receiver\SR. If you performed discovery through NetScaler Gateway, notice that the internal Base URL is added to the user’s registry.
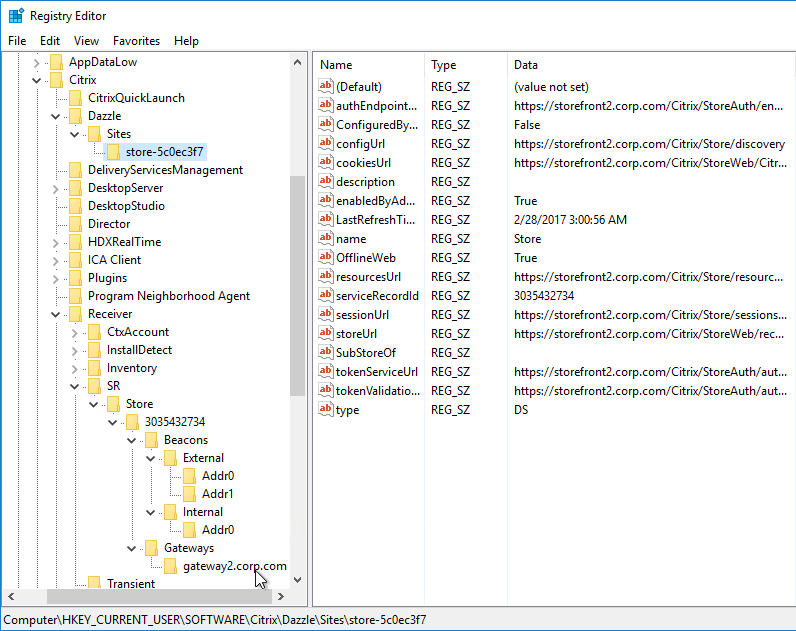
Once Workspace app is configured, it then performs the following steps:
- Attempt to connect to the Internal Beacon.
- If the Internal Beacon is reachable, connect directly to the StoreFront Base URL (Address).
- If the Internal Beacon is not reachable:
- Attempt to connect to the External Beacons. If the External Beacons are not reachable, then stop attempting to connect.
- Connect to the Gateway address configured in the Provisioning File. If there is more than one Gateway, connect to the Gateway that is marked as the Default.
Here are some interesting notes on this connection process:
- The FQDN you entered during Discovery has absolutely nothing to do with how Workspace app connects to StoreFront or Gateway. The actual connection process is controlled by the contents of the Provisioning File, not the Discovery address.
- If the Provisioning File has multiple Gateways defined, Workspace app uses whichever Gateway is marked as Default. Workspace app completely ignores whatever Gateway FQDN you entered during Discovery. To use a non-default Gateway, the user must manually select the other Gateway in Workspace app’s Advanced Preferences.
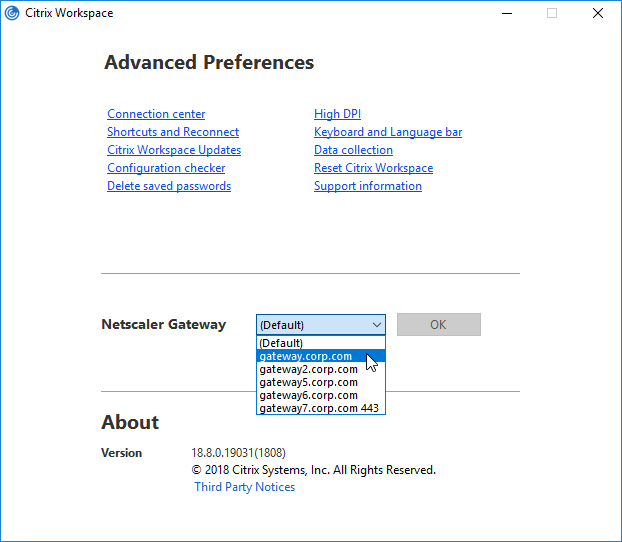
In StoreFront Console, if any configuration changes are performed that affect the Provisioning File, it takes an hour for Workspace apps to reconfigure themselves automatically. Or users can remove Accounts and re-add (or Reset Citrix Workspace) so that the updated Provisioning File is imported.
Here are some additional methods of performing Workspace app Discovery:
- After exporting the Provisioning File from StoreFront Console, distribute it to users, and ask them to double-click it.
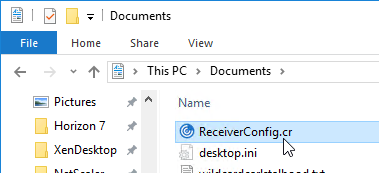
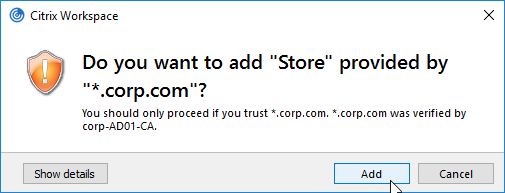
- After logging in to Receiver for Web (StoreFront), at the top right, click the username, and click Activate. This downloads the receiverconfig.cr file, which is identical to the one you can export from StoreFront Console. The user then must run the downloaded file.
Virtual Monitors
In Workspace app 1812 and newer, when connected to a published desktop on a single monitor, you can split the screen into virtual monitors. This feature is intended for large 4K monitors.
- In the desktop toolbar at the top of the screen, click Preferences.
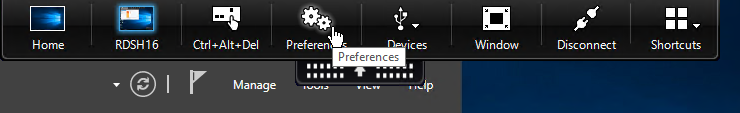
- Switch to the Monitor Layout tab.
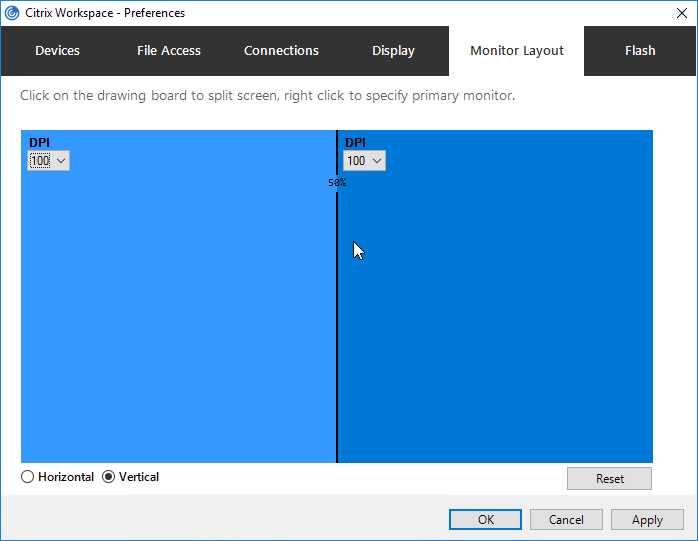
- On the bottom, select Horizontal or Vertical, then click somewhere in the blue box to draw a line. The single monitor will be split along this line. You can set different DPI for each portion of the virtual display.
- Right-clicking one of the split sections changes that section to the primary display.
- Click OK when done.
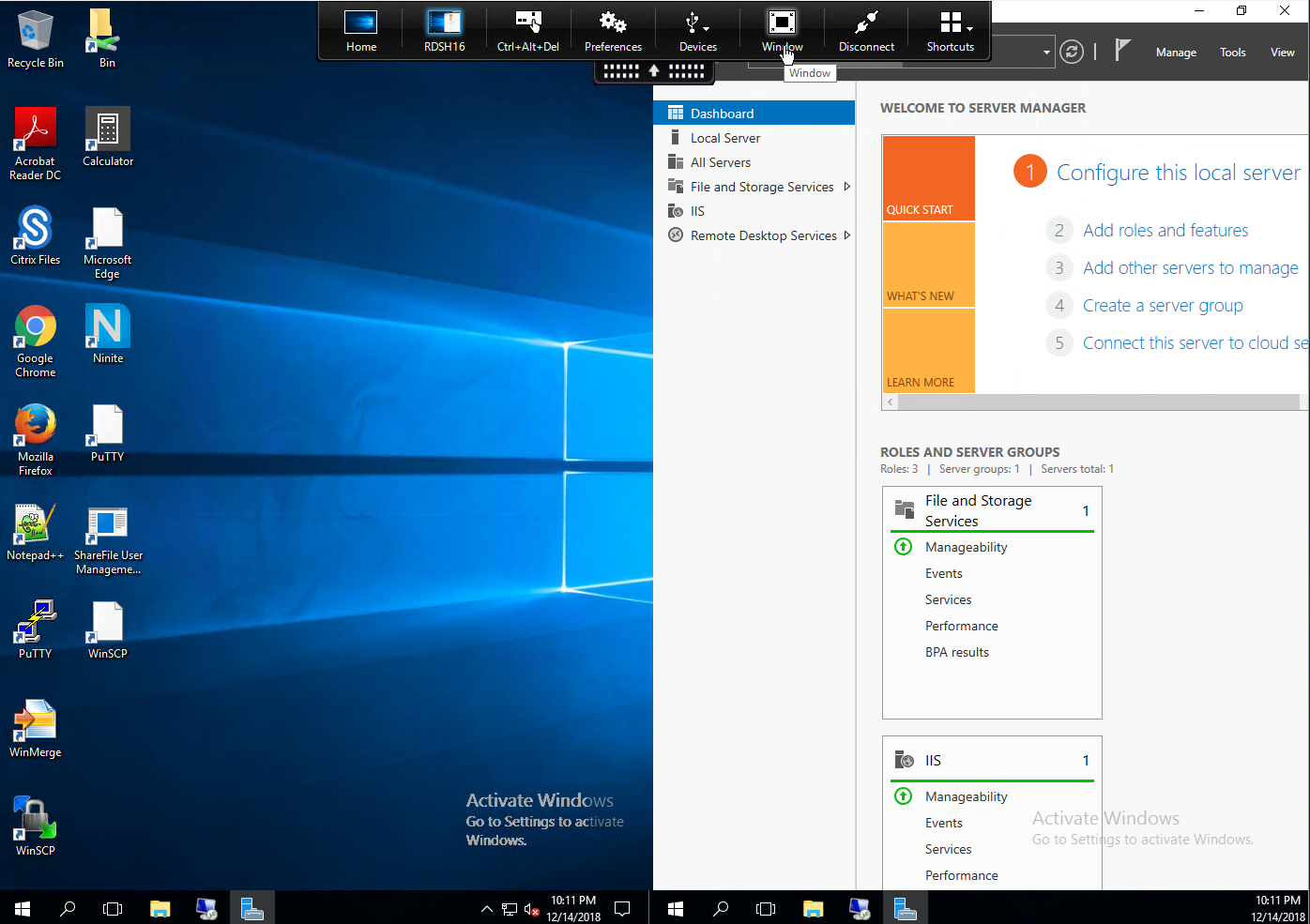
- In the toolbar, click Window to resize it to a window, and then click Full Screen to cause your virtual monitor configuration to take effect.
Uninstall Old Clients
Workspace app installer can do a force uninstall of old clients before installing the new version:
- In Workspace app 2309 and newer, run CitrixWorkspaceApp.exe /CleanInstall /Silent
- In Workspace app 1909 and newer, run CitrixWorkspaceApp.exe /ForceInstall /Silent.
- In Workspace app 1908 and older (including Receiver), run CitrixWorkspaceApp.exe /RCU /Silent or CitrixReceiver.exe /RCU /Silent.
Citrix CTX325140: How to Remove Client Files Remaining on System after Uninstalling Receiver for Windows.
Installation and Configuration
Administrator privileges – Administrator privileges are required to install any missing prerequisites.
Internet required – Recent versions of Workspace app download and install Microsoft Edge WebView2 Runtime, .NET Desktop Runtime 6.0.20, .NET Framework 4.8, and Visual C++. Internet access is required for the Workspace app installer to download these install files. Or there’s an Offline Installer for Workspace app 2309 and newer.
.NET Desktop Runtime 6.0.20 – Workspace app 2309 and newer will install x86 .NET Desktop Runtime 6.0.20 if it’s not already installed.
This section contains a summary of all common command line switches, registry keys, and policy settings for Workspace app.
Links:
- Citrix Blog Post: Optimizing Citrix Receiver for Pre-launch and Single Sign-On
- Citrix CTX202002 How To Deploy Citrix Receiver for Windows Using SCCM 2012 R2
Workspace app 2203 LTSR CU2 and Workspace app 2212 and newer fix security vulnerabilities.
CitrixWorkspaceApp.exe current release version 2409.10 or LTSR version 2402 CU3 can be installed by simply double-clicking it.
- LTSR Workspace app does not support Browser Content Redirection.
- Workspace app 2006 and newer do not support Windows 7.
- Workspace app 2206 and newer enable DPI Matching by default. DPI Matching can be disabled through client-side group policy, or in the Advanced Preferences in Workspace app 2212 and newer. DPI Matching prevents connections to CVAD 7.15. Multi-session VDAs with version 1912, by default, have DPI Matching disabled, but can be enabled in the VDA’s registry. See CTX460068 for details.
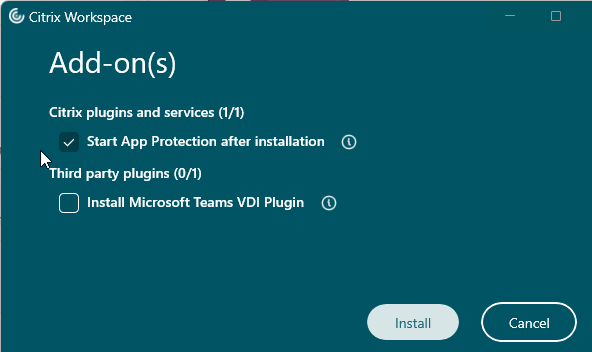
- Workspace app 2311 and newer have a new interface for installation.
- Workspace app 2402 and newer ask if you want to install the Microsoft Teams VDI Plugin or not. This is for Teams 2.1 and newer.
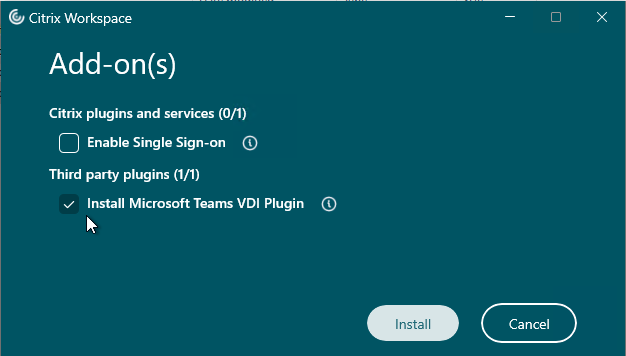
Administrator vs non-administrator
- Non-administrator – If a non-administrator installs Workspace app, then each non-administrator that logs in to the same workstation will have to reinstall Workspace app.
- Non-administrator installations are installed to %USERPROFILE%\AppData\Local\Citrix\ICA Client for each user.
- Administrator – If CitrixWorkspaceApp.exe is installed using an administrator account. then the Workspace app only needs to be installed once.
- Administrator installations are installed to C:\Program Files (x86)\Citrix\ICA Client.
- Administrator installations of Workspace app 1912 and newer can be manually upgraded by non-administrators by clicking Check for Updates. Older versions cannot be upgraded by non-administrators.
- Conflicts – If an administrator install of Workspace app is performed on a machine that has non-administrator installs of Workspace app, then the two installations will conflict. Best option is to uninstall non-admin Workspace app and Receiver before installing admin Workspace app. Otherwise, the user’s profile probably has to be reset before Workspace app is functional again.
- Citrix article CTX249920 Workspace App for Windows – Your apps are not available at this time – Issue when installing Citrix Receiver in not elevated/per-user install mode describes the HKEY_CURRENT_USER registry keys that must be deleted to fix this issue.
- For a script to clean-up the per-user installs, see Mark DePalma at Citrix Receiver Per-User Install Cleanup.
Global App Configuration Service
Global App Configuration Service (GACS) is a Citrix Cloud service that can push configurations to Workspace app clients. This Citrix Cloud service is now available to all on-premises customers even if you don’t own any Citrix Cloud entitlements.
- Login to https://citrix.cloud.com. If you don’t have a Citrix Cloud account, then login using your Citrix.com account credentials and it will create a Citrix Cloud account.
- Use the top left hamburger menu to go to Workspace Configuration.
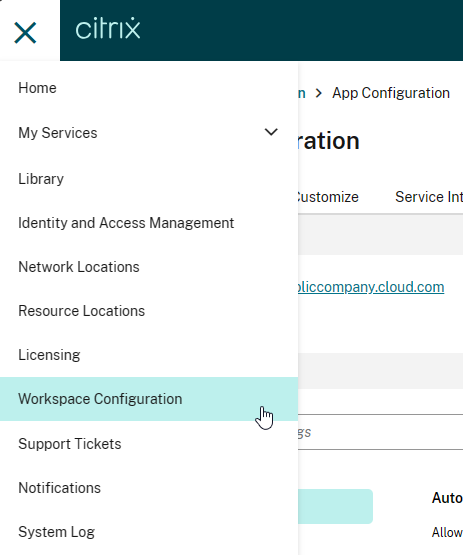
- Switch to the tab named App Configuration.
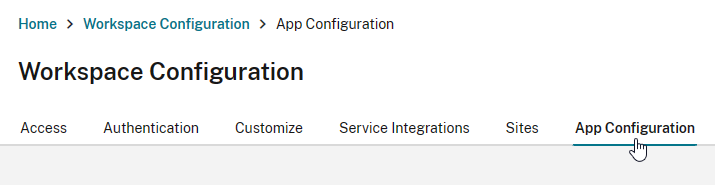
- Click Switch URL.
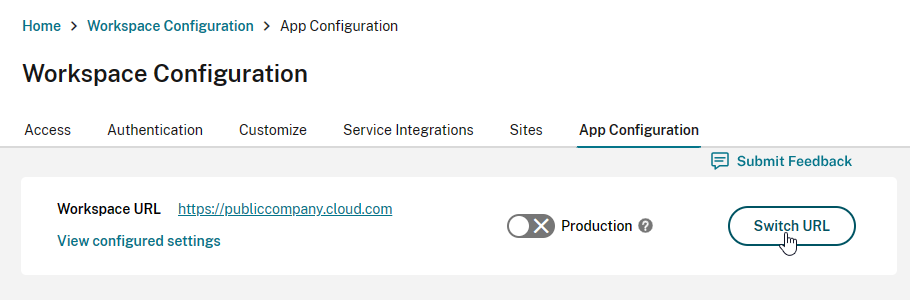
- Near the bottom, click Claim URL.
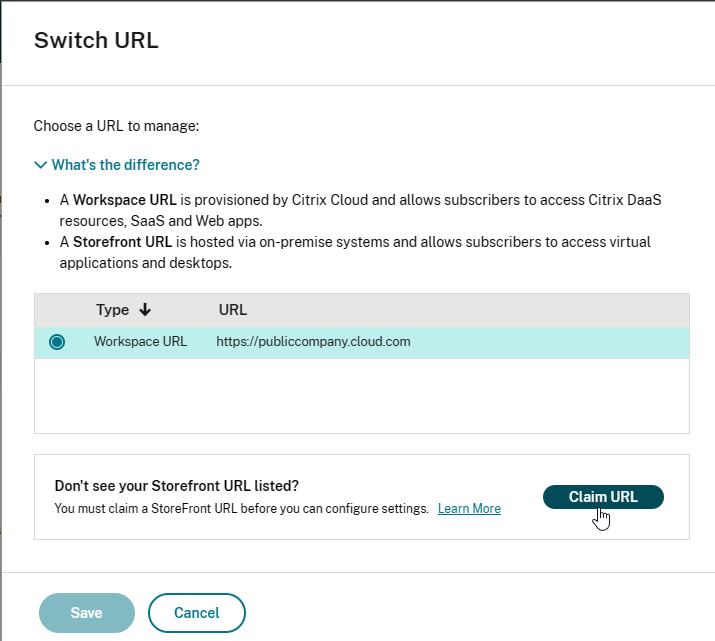
- Click Add URL to add your on-premises StoreFront/Gateway URL. See Citrix Docs for details. GACS uses this URL to determine which Workspace app clients should receive the settings that you configure.
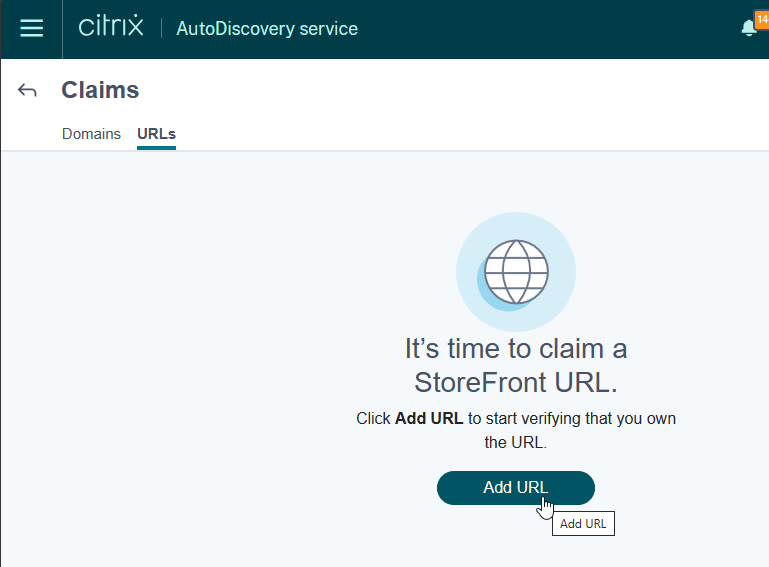
- Back in the App Configuration page, you can now configure Workspace app settings as desired. Workspace apps that have stores under the claimed URL will then receive these settings.
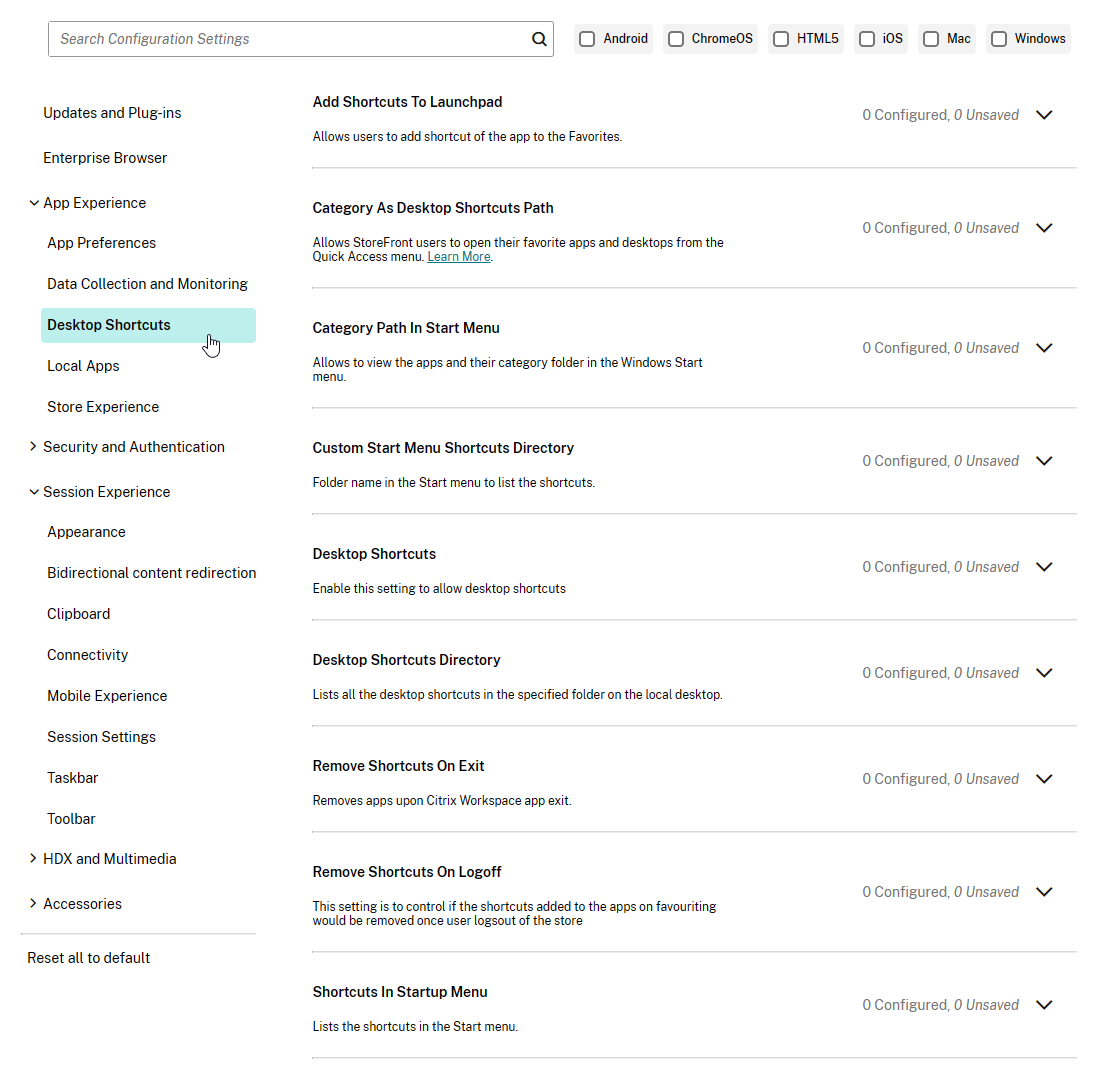
Auto-Update
Workspace app supports auto-update.
Some notes:
- If Workspace app 1912 or newer is installed as administrator, then non-administrators can click Check for Updates to manually update Workspace app. To prevent this, use group policy to disable Citrix Workspace Updates.
- Older versions of Workspace app cannot be upgraded by non-administrators.
- If Workspace app is installed on a VDA, auto-update is automatically disabled. This includes Remote PC.
- Auto-update can be limited to LTSR updates only.
- Auto-update is configurable through several mechanisms: group policy, StoreFront, Workspace app GUI, installer command line. See Configuring Citrix Workspace Updates at Citrix Docs.
- Workspace app 2107 and later let users select an Update channel.
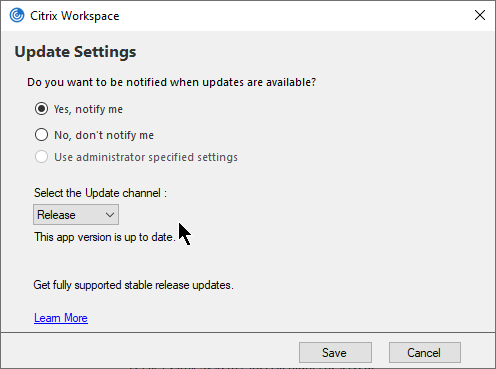
- See George Spiers Citrix Receiver for Windows Auto-Update.
Auto-update is configured using Workspace app group policy under the Citrix Workspace Updates, or Auto-Update node.
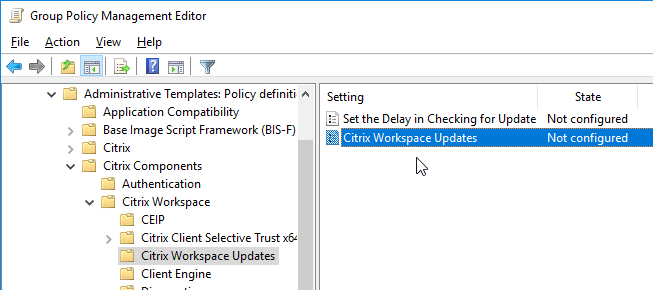
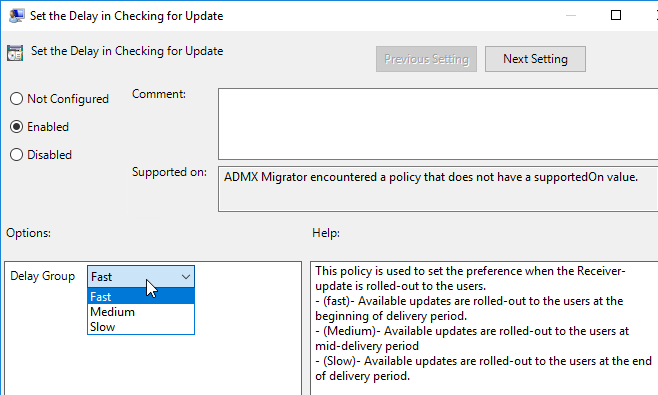
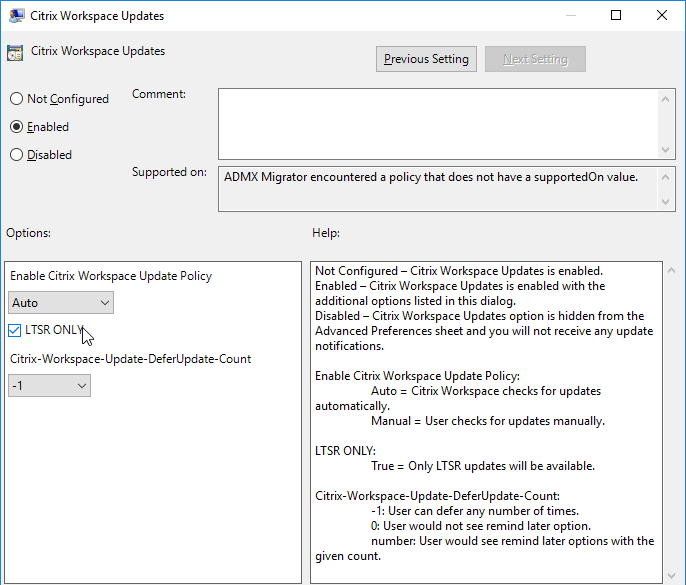
Or use Global App Configuration Service.
Workspace app Splash Screen
Workspace app shows a Splash Screen on first launch with the text “Citrix Workspace app extends the capabilities of Citrix Receiver”.

To prevent this splash screen, set the following registry value: (source = Dennis Span on Twitter)
- Key = HKEY_CURRENT_USER\SOFTWARE\Citrix\Splashscreen
- Value (REG_SZ) = SplashscreenShown = 1
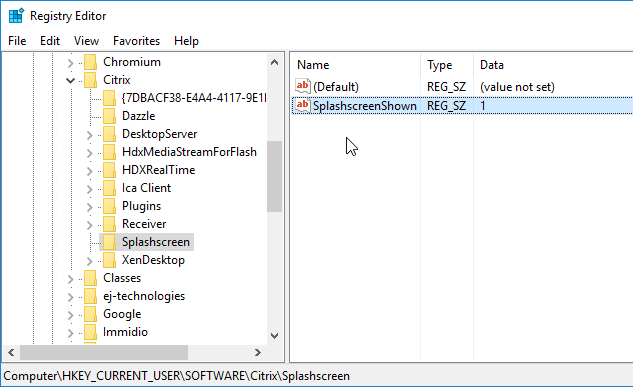
Add Account Wizard
After installation, Workspace app will launch and ask you to add an account. If Workspace app, notice the checkbox Do not show this window automatically at logon.
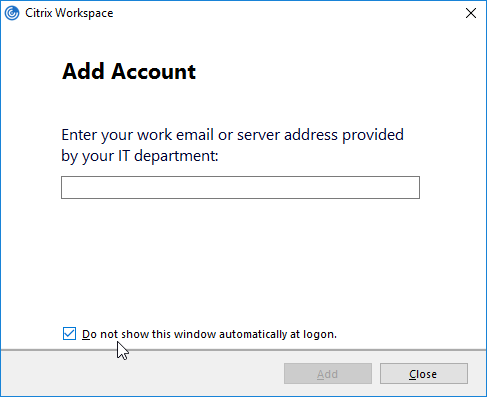
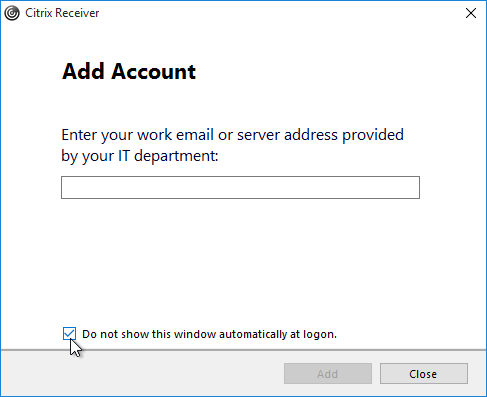
FTU (First Time Use aka Add Account Wizard) will be displayed only if a store is not configured. If a store is already configured via command line, GPO, or Citrix Studio, then FTU screen will not be available after installation. Otherwise, FTU can be suppressed by doing one of the following:
- Rename CitrixWorkspaceApp.exe to CitrixWorkspaceAppWeb.exe.
- Install using a command line switch:
- CitrixWorkspaceApp.exe /ALLOWADDSTORE=N
- Set the registry value: HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Citrix\EnableFTU=dword:00000000 (or EnableX1FTU =dword:0)
- Disable the EnableFTU policy setting in Receiver.admx.
- Change Registry values post installation to suppress the Add Account window. Under HKLM\Software\Wow6432Node\Citrix\Dazzle, set AllowAddStore value to N.
- Set the registry value: HKEY_LOCAL_MACHINE\Software\Citrix\Receiver\NeverShowConfigurationWizard (REG_SZ) = true
- Also see Suppressing Add Account dialog at Citrix Docs.
Discover Hidden Stores
When Workspace app is first launched, it must perform Discovery, which is the process of downloading the .xml provisioning file from StoreFront. Discovery is performed by entering a StoreFront FQDN or Gateway FQDN. To discover a hidden store (a store that’s not advertised), add ?StoreName to the end of the FQDN. CTX214819 How to configure Receiver to a Store that is not advertised.
CitrixWorkspaceApp.exe Command line switches
CTX227370 Citrix Workspace app Commandline Tool contains a GUI tool to build your installer command line.

For unattended installation of Workspace app, see CTA Dennis Span Citrix Workspace App unattended installation with PowerShell or Citrix Receiver unattended installation with PowerShell.
Installer Command Line Switches are detailed at Configure and install Receiver for Windows using command-line parameters at Citrix Docs. Common Command line switches include the following:
- /silent
- /includeSSON – enables pass-through authentication. GPO configuration is also required as detailed below.
CitrixWorkspaceApp.exe /includeSSON
- /ALLOWADDSTORE=A – by default, only SSL (HTTPS) stores are accepted. To allow non-SSL stores:
CitrixWorkspaceApp.exe /ALLOWADDSTORE=A
- /STORE0 – To add a store from the installation command line:
CitrixWorkspaceApp.exe STORE0="AppStore;https://Citrix.corp.com/Citrix/MyStore/discovery;on;App Store"
- Workspace App can discover the Store through NetScaler Gateway.
CitrixWorkspaceApp.exe STORE0="AppStore;https://gateway.corp.com#MyStore;On;App Store"
- Workspace App can discover the Store through NetScaler Gateway.
- /SELFSERVICEMODE=False – disables the Self-Service interface and enables shortcut-only mode:
CitrixWorkspaceApp.exe /SELFSERVICEMODE=False
- /AutoUpdateCheck=auto /AutoUpdateStream=LTSR – enables Citrix Workspace Update notifications and sets it to LTSR Branch only. AutoUpdateCheck can also be set to manual or disabled. AutoUpdateStream can also be set to Current. See Configuring Citrix Workspace Updates at Citrix Docs.
CitrixWorkspaceApp.exe /AutoUpdateCheck=auto /AutoUpdateStream=LTSR
- /ENABLEPRELAUNCH=True – enables prelaunch:
CitrixWorkspaceApp.exe /ENABLEPRELAUNCH=True
- /ALLOW_CLIENTHOSTEDAPPSURL=1 – enables Local App Access:
CitrixWorkspaceApp.exe /ALLOW_CLIENTHOSTEDAPPSURL=1
Registry values
HKLM\Software\Wow6432Node\Citrix\Dazzle on the Workspace app machine. All are of type REG_SZ (string) unless specified. Note: several of these are configurable using the Reciever.admx group policy template.
- SelfServiceMode (REG_SZ) = False – Turns off Workspace app’s Self-Service interface.
- PutShortcutsOnDesktop (REG_SZ) = True – If Self-Service interface is disabled, places all shortcuts on desktop.
- UseDifferentPathsforStartmenuAndDesktop (REG_SZ) = True
- UseCategoryAsStartMenuPath (REG_SZ) = True or False
- UseCategoryAsDesktopPath (REG_SZ) = True or False
- StartMenuDir (REG_SZ) = name of folder on Start Menu where shortcuts are placed.
- DesktopDir (REG_SZ) = name of folder on Desktop where shortcuts are placed
- EnablePreLaunch (REG_SZ) = True – If SSON is enabled then PreLaunch is already enabled by default.
- AllowAddStore (REG_SZ) = A – Only if using http (instead of https) to connect to StoreFront.
- AllowSavePwd (REG_SZ) = A – Only if using http (instead of https) to connect to StoreFront.
- UserDomainName (REG_SZ) = pre-filled domain name
- InitialRefreshMinMs (REG_SZ) = 1 – minimizes the launch delay before contacting store
- InitialRefreshMaxMs (REG_SZ) = 1 – minimizes the launch delay before contacting store
- RefreshMs (REG_SZ) = 3600000 (1 hour) – interval for Receiver icon refreshes. 1 hour is the default value.
- RefreshMs (REG_SZ) = 18000000 – Citrix CTX213755 Citrix Receiver Shows Authentication Window Periodically When Receiver is Not Opened
- MaxSimultaneousFetches (REG_DWORD) = 6 – improves the time of loading icons in Start Menu
- MaxSimultaneousSubscribes (REG_DWORD) = 6 – improves the time of loading icons in Start Menu
- DontWarnOfRemovedResources (REG_SZ) = True – prevents dialog boxes when resources are removed from the server. (or False)
- SilentlyUninstallRemovedResources (REG_SZ) = True – prevents dialog boxes when resources are removed from the server
- PreferTemplateDirectory (REG_SZ) = UNC path or local path containing shortcuts copied by the prefer keyword. Give the shortcuts a short name.
- PnaSSONEnabled (REG_SZ) = True – Enables Single Sign-on for PNAgent (Web Interface).
- WSCReconnectMode (REG_SZ) = 3 (default) – If this Workspace app is running inside a VDA published desktop, set it to 0.
- If you’re having trouble getting sessions to reconnect, see Receiver 4.3 Desktop will not auto-reconnect when logging into a machine at Citrix Discussions
- AlwaysUseStubs (REG_SZ) = True. Workspace app and Receiver 4.3.100 and newer don’t create .exe stubs by default. Set this to create .exe stubs. Also see Citrix CTX211893 Controlling Shortcut behavior in Receiver 4.3.100.
- DontCreateAddRemoveEntry (REG_SZ) = True – don’t create “Delivered by Citrix” entries in Programs and Features
- DesktopNameFormatString = format string for shortcut names – For example “{0}_{1}_{2}_{3}”. See the link for details.
- SelfServiceFlags (REG_DWORD) = 4 – prevents duplicate shortcuts when roaming and Desktop is redirected.
- SelfServiceFlags = 5 to stop external SSON from prompting for authentication
- ReEvaluateNetwork (REG_SZ) = true – for Beacon detection with Single FQDN
To prevent the Win+G popup on Windows 10 machines:
- HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\GameDVR
- AllowGameDVR (REG_DWORD) = 0
To allow adding non-HTTPS stores to Workspace app:
- HKLM\Software\Wow6432Node\Citrix\AuthManager
- ConnectionSecurityMode (REG_SZ) = Any
To increase ICA bandwidth consumption over high latency links, set:
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\ICA Client\Engine\Configuration\Advanced\Modules\TCP/IP
- OutBufCountClient2 = Number of OutBufs (default is 44)
- OutBufCountHost2 = Number of OutBufs (default is 44)
- See CTX125027 How to Optimize HDX Bandwidth Over High Latency Connections for some recommended values (multiples of 44)
To prevent beacon probing from using proxy, set:
- HKEY_LOCAL_MACHINE\Software\WOW6432Node\Citrix\Receiver\inventory
- BeaconProxyEnabled (REG_DWORD) = 0
To enable foreground progress bar, set:
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\ICA Client
- ForegroundProgressBar (REG_DWORD) = 1
For client-to-server file type redirection, set:
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\ICA Client\Engine\Configuration\Advanced\Modules\ClientDrive
- NativeDriveMapping=”TRUE”
To fix USB devices that emulate a keyboard, set:
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\ICA Client\Engine\Lockdown Profiles\All Regions\Lockdown\Virtual Channels\Keyboard
- KeyboardTimer=”10”
To remember manually mapped USB devices when auto-connection is enabled, set: (2409 and newer)
- HKLM\SOFTWARE\Citrix\ICA Client\GenericUSB (same path for 32-bit and 64-bit, create the keys)
- RememberConnections (DWORD) = 0x1
To override the devices that are mapped using optimized channels instead of generic USB, see Citrix CTX123015 How to Configure Automatic Redirection of USB Devices
Group Policy Settings
Copy the Workspace app ADMX template (C:\Program Files (x86)\Citrix\ICA Client\Configuration\receiver.admx) to C:\Windows\PolicyDefinitions (or Sysvol). Also copy receiver.adml to C:\Windows\PolicyDefinitions\en-us (or Sysvol).
Edit a GPO that applies to client machines, go to Computer Configuration | Policies | Administrative Templates | Citrix Components | Citrix Workspace and configure the following:
- To enable pass-through authentication: go to | User Authentication |.
- Local Username and Password – Check the top two boxes.
- Also add the StoreFront FQDN to the Local Intranet zone in Internet Explorer.
- Single Sign-on for NetScaler Gateway (Workspace app 1808 and newer)
- To add a store, go to | StoreFront |
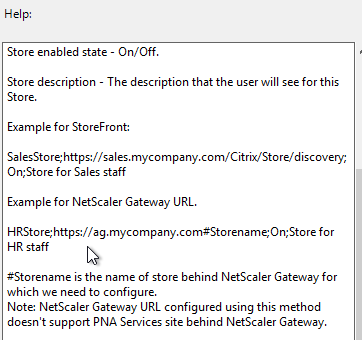
- StoreFront Accounts List – see the help text
- To enable Auto-Update, go to | AutoUpdate | or | Citrix Workspace Updates |. (the node was renamed in 4.11 and Workspace app)
- Enable or Disable AutoUpdate or
- Citrix Workspace Updates
- To modify the desktop viewer toolbar, go to | Client Engine |
- Desktop Viewer Toolbar Options (2409 and newer)
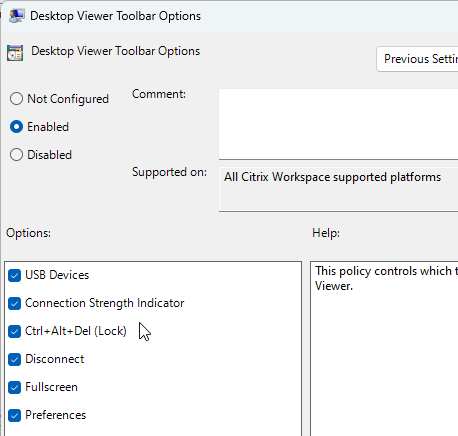
- Desktop Viewer Toolbar Options (2409 and newer)
- To enable Local App Access, go to | User Experience |
- Local App Access Settings
- To prevent the endpoint from sleeping while session is active, go to | User Experience |
- Power Management (2405 and newer)
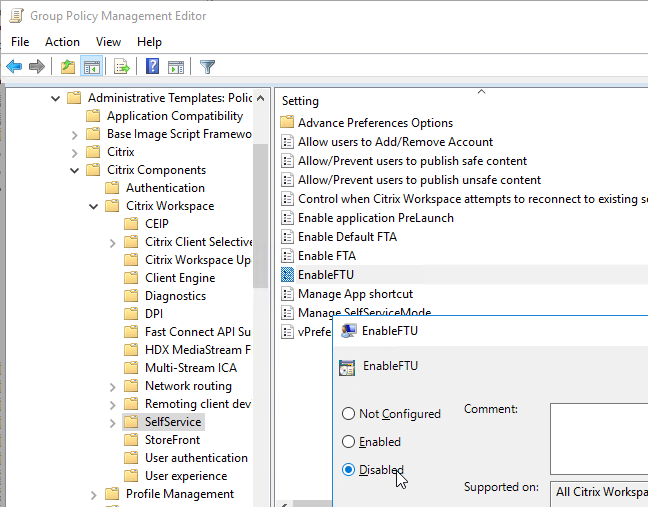
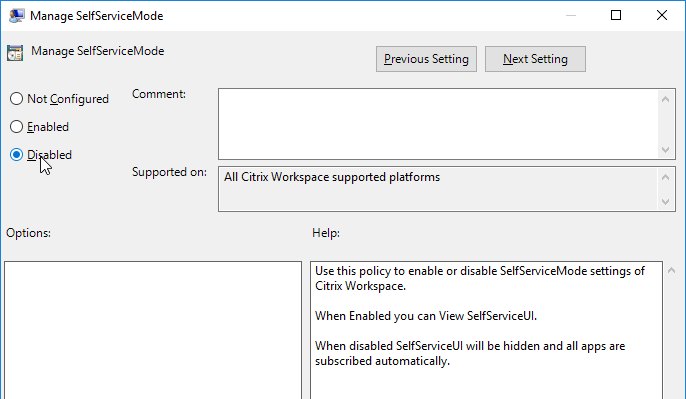
- To configure the Self-Service interface, go to | SelfService |
- Set Manage SelfServiceMode to Disabled to completely disable the Self-Service window. This causes all icons to be placed on the Start Menu.
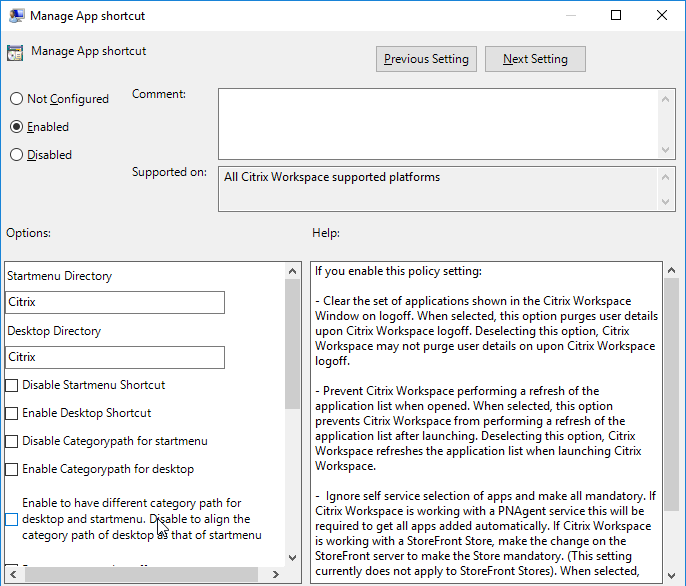
- Enable Manage App Shortcut and configure it as desired.
- To allow the Self-Service window, but prevent it from automatically opening (reside in systray), tick Prevent Citrix Workspace performing a refresh of the application list when opened. Source
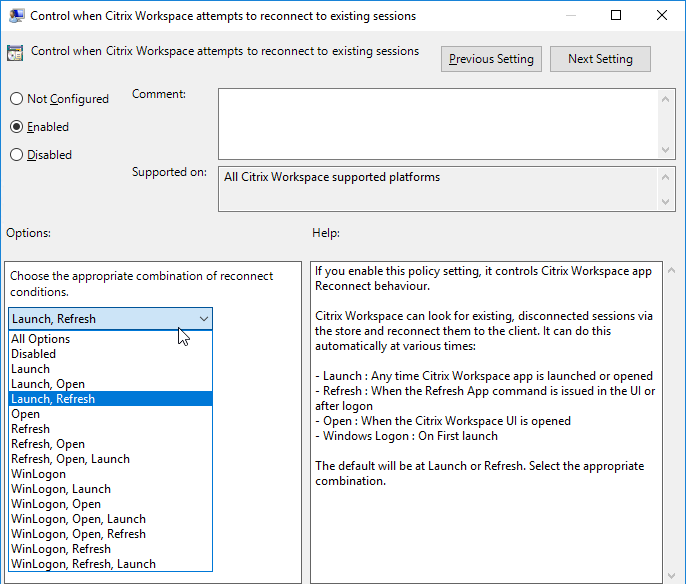
- Enable Control when Workspace attempts to reconnect to existing sessions. If this is a VDA published desktop, set it to Disabled. Otherwise configure it as desired.
- Set Enable FTU to Disabled to prevent the Add Account wizard from displaying.
- Enable Allow/Prevent users to publish unsafe content if publishing content that’s opens a file or file share.
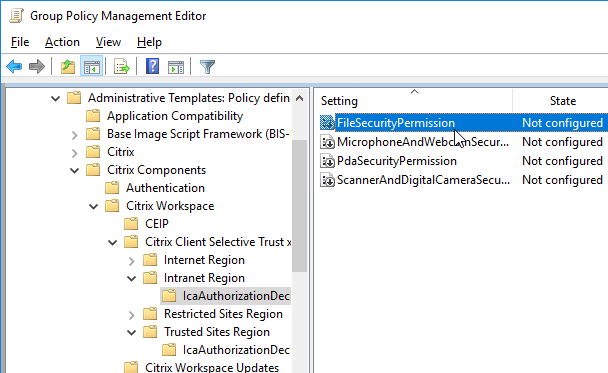
Enable automatic client drive and client microphone mapping:
- In a client-side GPO, add the GPO ADM template from http://support.citrix.com/article/CTX133565.
- Enable the setting Create Client Selective Trust Keys. See Below for details.
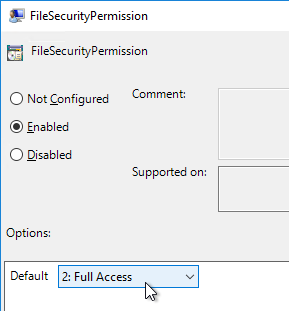
- Configure the FileSecurityPermission setting in one or more of the regions.
- Configure the MicrophoneAndWebcamSecurityPermission setting in one or more of the regions.
Citrix CTX203658 Start Menu Icons Set to Default (Blank Document) After Update to Receiver 4.3.100 – Windows 8 and newer
- Computer Configuration | Policies | Administrative Templates | Windows Components | File Explorer
- Allow the use of remote paths in file shortcut icons = enabled
For Single Sign-on in Windows 11 24H2 and newer, enable the following GPO setting:
- Computer Configuration | Policies | Administrative Templates | Windows Components | Windows Logon Options
- Enable MPR notifications for the System = enabled
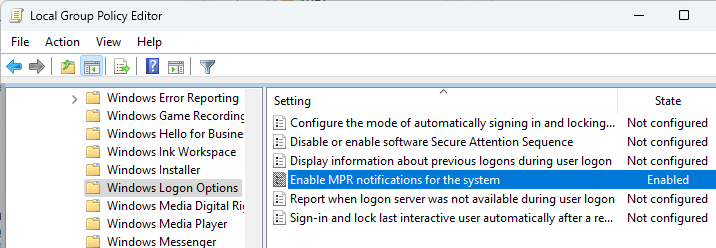
- Enable MPR notifications for the System = enabled
Deploy Workspace app using Active Directory
To deploy Workspace app using Active Directory, configure a GPO with a computer startup script that runs the Workspace app installer executable. Citrix provides sample scripts that can be downloaded from one of the Workspace app download pages (Workspace app current release version 2409.10, or LTSR version 2402 CU3, by expanding Downloads for Admins (Deployment Tools).
Also see CTA Dennis Span Citrix Receiver unattended installation with PowerShell.

Change Workspace App’s Store Configuration, including Reset Citrix Workspace
You can change Workspace app’s configured Store/Account with a couple command lines:
"C:\Program Files (x86)\Citrix\ICA Client\SelfServicePlugin\SelfService.exe" -deleteproviderbyname Corporate "C:\Program Files (x86)\Citrix\ICA Client\SelfServicePlugin\SelfService.exe" -init -createprovider Corporate https://storefront.corp.com/Citrix/Store/discovery
It is sometimes necessary to Reset Citrix Workspace by right-clicking the Workspace app systray icon, clicking Advanced Preferences, and clicking the Reset link. You can do this from the command line by running "C:\Program Files (x86)\Citrix\ICA Client\SelfServicePlugin\CleanUp.exe" -cleanUser -silent. See CTX140149 How to Reset Receiver Using the Command Line.
Workspace app Group Policy ADMX Template
Many of the Workspace app configuration settings must be configured in group policy. These Workspace app settings are only available after installing the GPO templates.
Alternatively, Citrix Cloud customers can use Global App Configuration Service to configure Workspace app. Today it’s a REST API, but Citrix has started adding a GUI at Workspace Configuration > App Configuration.
For GPO configuration:
- From a machine that has Workspace app installed, find the .admx and .adml files in the C:\Program Files (x86)\Citrix\ICA Client\Configuration.
- Copy the CitrixBase.admx and receiver.admx files. Also copy the en-US folder. In Workspace app, the files are still named receiver.admx.
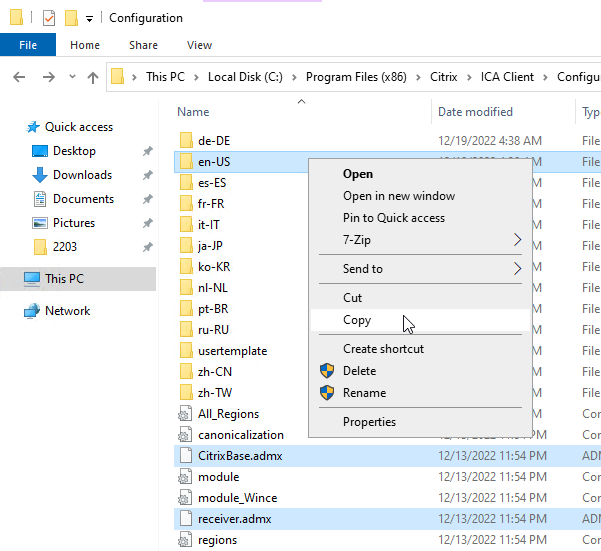
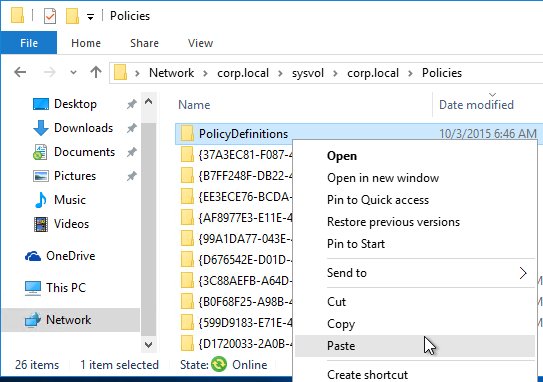
- Go to your domain’s SYSVOL share and in the Policies folder look for a PolicyDefinitions folder. If one exists, paste the .admx file directly into the PolicyDefinitions folder. If this folder doesn’t exist in SYSVOL, instead copy the .admx file to C:\Windows\PolicyDefinitions. Overwrite any existing Receiver ADMX files.
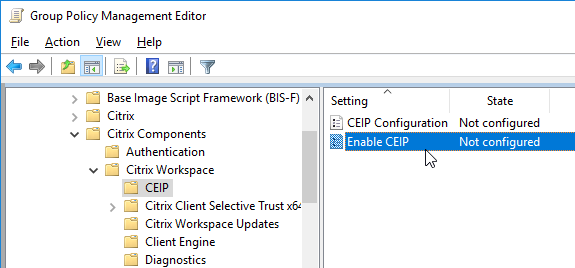
- The GPO settings can then be found at one of the following:
- Computer Configuration > Policies > Administrative Templates > Citrix Components > Citrix Workspace
- Computer Configuration > Policies > Administrative Templates > Citrix Components > Citrix Receiver
- For example, you can disable Customer Experience Improvement Program (CEIP) from here.
- See https://www.carlstalhood.com/delivery-controller-cr-and-licensing/#ceip for additional places where CEIP is enabled.
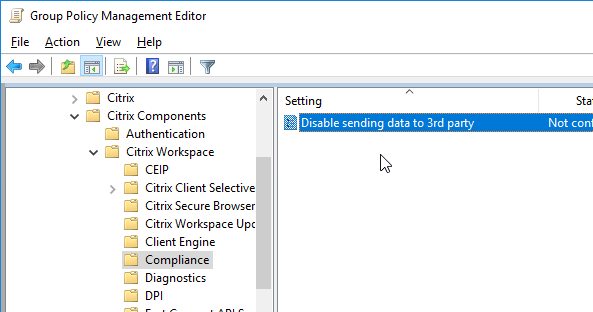
- Workspace app 1905 and newer has a setting to Disable sending data to 3rd party (e.g., Google Analytics).
- Workspace app 1905 and newer let you disable embedded browser caching.
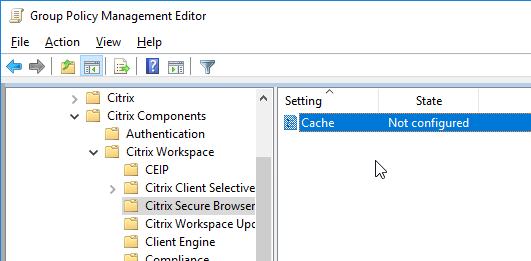
- Workspace app 1905 and newer have NetScaler LAN Proxy under Network routing > Proxy.
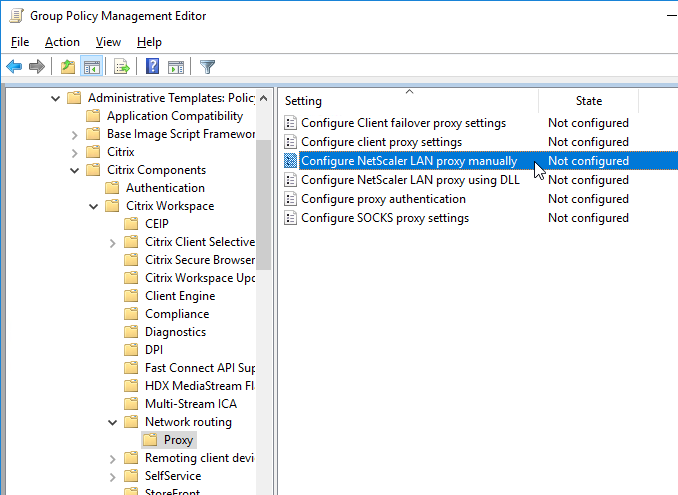
- Workspace app 1808 and newer have User authentication | Single Sign-on for NetScaler Gateway.
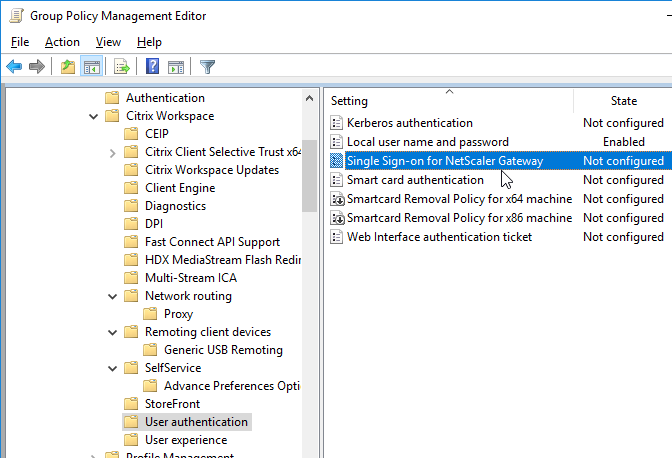
- Citrix Workspace Updates, (aka AutoUpdate) can be configured using group policy. See Configuring Citrix Workspace Updates at Citrix Docs.
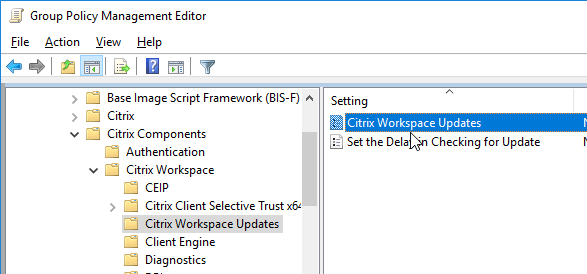
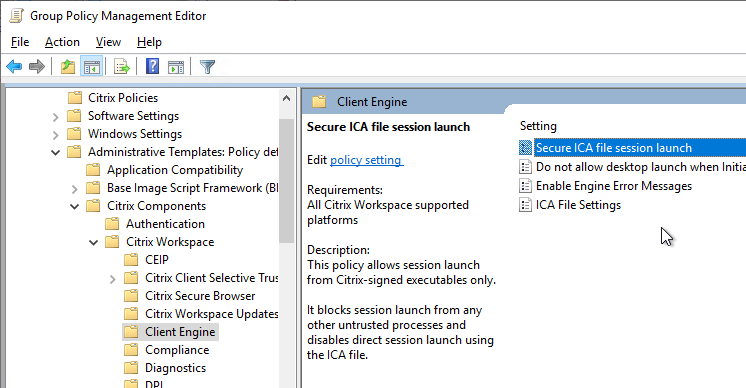
- Workspace app 1912 and newer can be configured to require in-memory ICA files only. The setting called Secure ICA file session launch is under the Client Engine node. See Citrix Docs for details on in-memory ICA files instead of writing ICA files to disk.
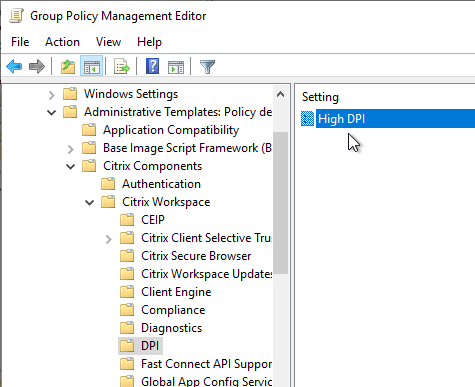
- The DPI node has a setting called High DPI that lets you disable DPI matching, which is enabled by default in Workspace App 2206 and newer.
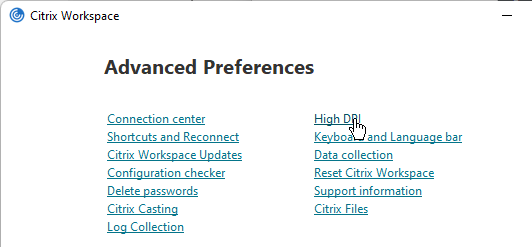
- Workspace app 2210 and newer let you use the GUI to re-enable High DPI.
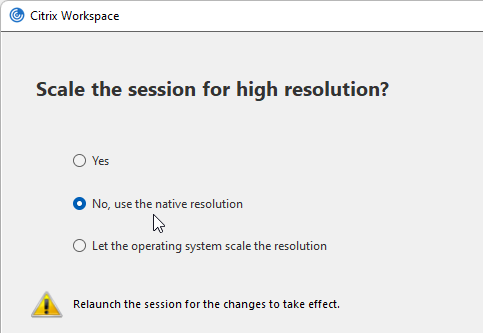
- Native resolution means DPI matching, whereas Yes means force high DPI.
- Workspace app 2210 and newer let you use the GUI to re-enable High DPI.
- Workspace app has settings to hide Advanced Preferences, enable/disable showing the DPI option, and enable/disable H265.
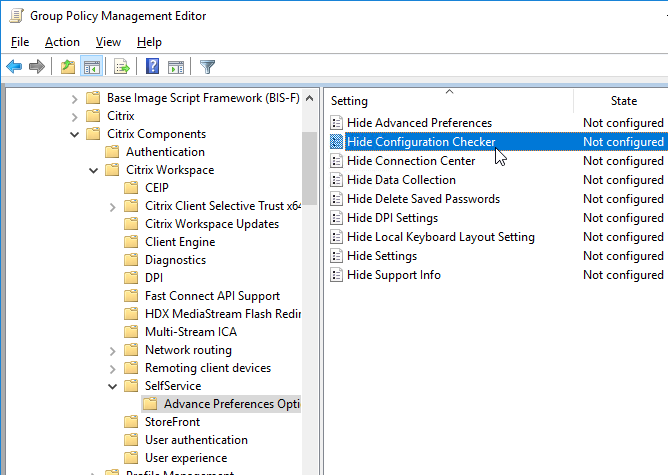
- Workspace app 4.8 and newer have SplitDevices GPO setting under Citrix Workspace | Remoting client devices | Generic USB Remoting. See Configuring composite USB device redirection at Citrix Docs.
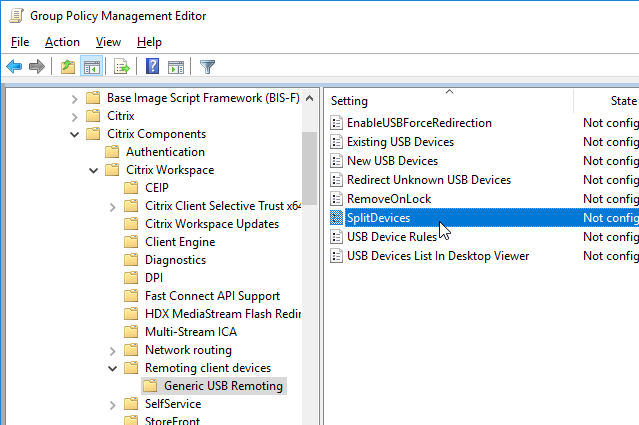
- Workspace app 2212 and newer by default disable App Protection for the authentication screen and icons list. To enable them, configure User authentication | Manage App Protection and SelfService | Manage App Protection.
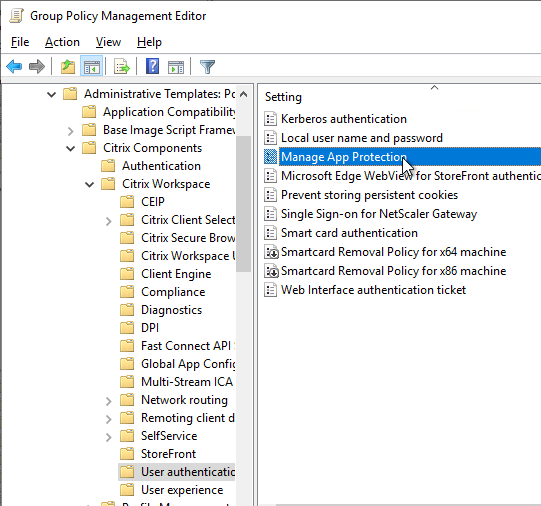
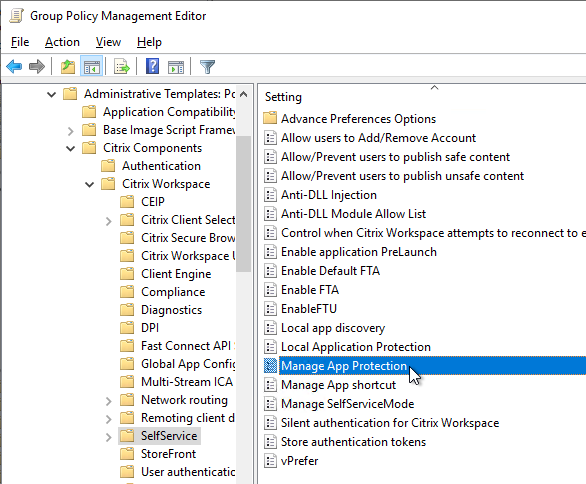
- Workspace app 2303 and newer have Anti-DLL Injection for App Protection. It is disabled by default. Enable it in a GPO at Citrix Components | Citrix Workspace | App Protection | Anti-DLL Injection. See Citrix Docs for details.

Pass-through Authentication
Citrix blog post – A Comprehensive Guide to Enabling Pass-Through Authentication with XenDesktop 7.5
- Run the command
Set-BrokerSite -TrustRequestsSentToTheXmlServicePort $True from a Windows PowerShell command prompt on a Delivery Controller.
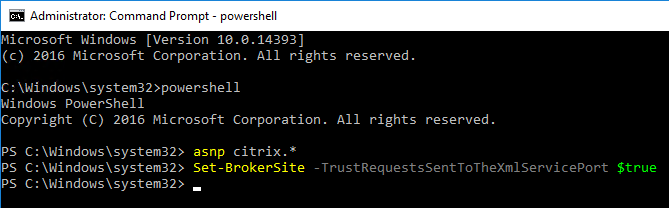
- In XenApp 6.5, this is a Citrix Policy > Computer > Trust XML Requests.
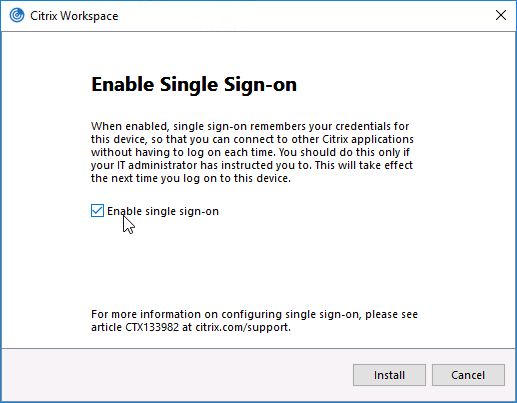
- Login to the PC as an administrator.
- If installing Workspace app, as an administrator, during installation, on the Enable Single Sign-on page, check the box next to Enable Single Sign-on. Then finish the installation.
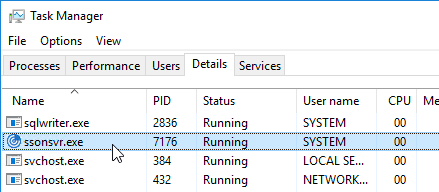
- To verify that SSON is installed, go to C:\Program Files (x86)\Citrix\ICA Client and look for the file ssonsvr.exe.
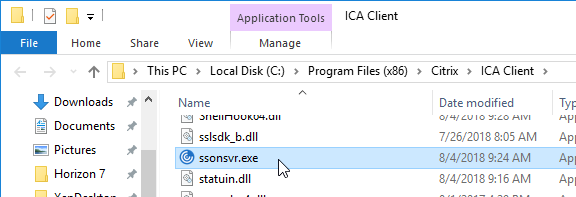
- And if you open regedit and go to HKLM\SYSTEM\CurrentControlSet\Control\NetworkProvider\Order, you should see PnSson in the ProviderOrder.
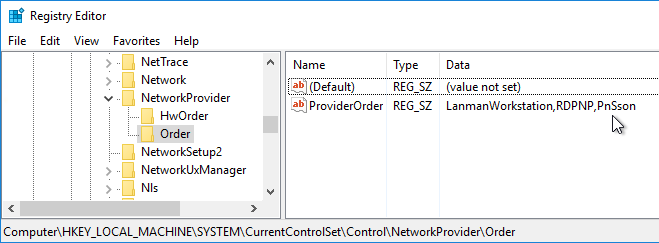
- Install the receiver.admx (and .adml) template into PolicyDefinitions if you haven’t already.
- Edit a GPO that is applied to the client PCs where the Workspace app is installed.
- Go to Computer Configuration > Policies > Administrative Templates > Citrix Components > Citrix Workspace.
- Expand Citrix Workspace and click User authentication.
- On the right, double-click Local user name and password.
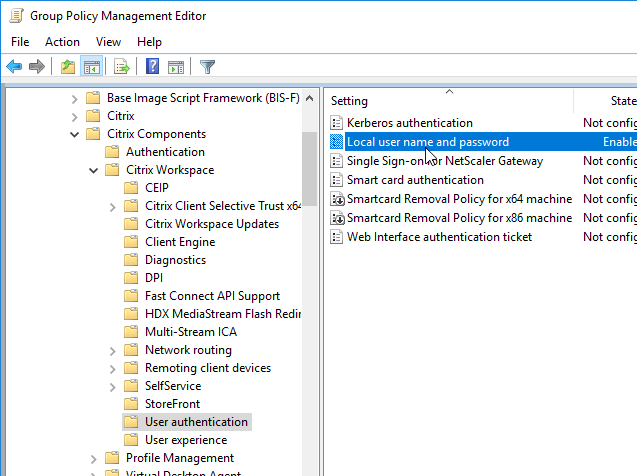
- Select Enabled and then check the box next to Allow pass-through authentication for all ICA connections. Click OK.
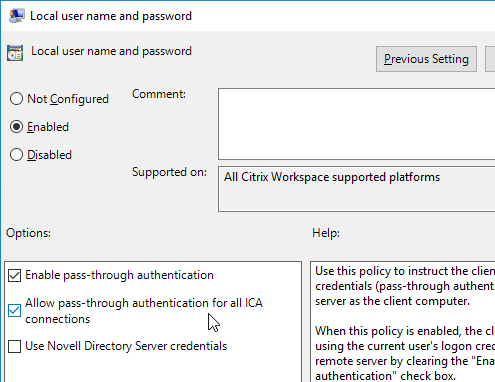
- In Workspace app 1808 and newer, you can enable Single Sign-on for NetScaler Gateway.
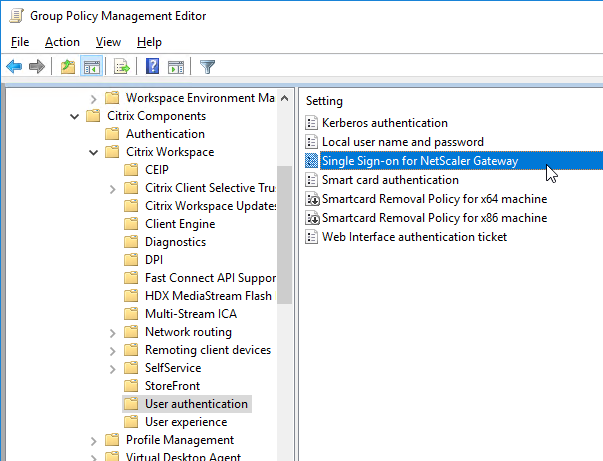
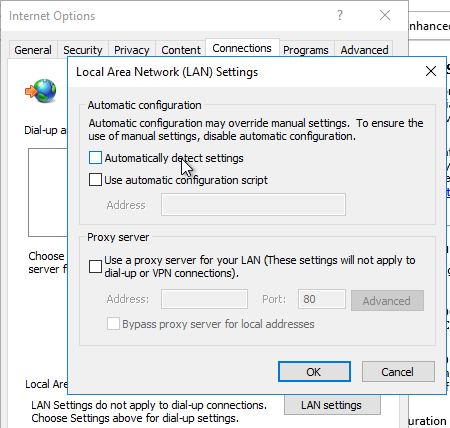
- Ensure that the internal StoreFront FQDN is in the Local Intranet zone in Internet Explorer. You can use a GPO to configure this on the client side.
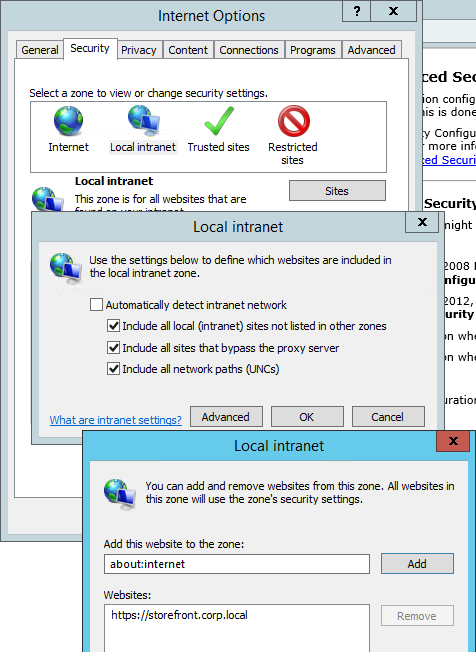
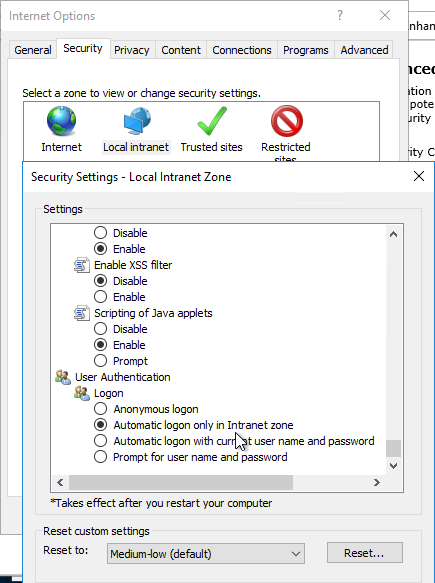
- Local Intranet zone should have Automatic logon only in Intranet zone enabled.
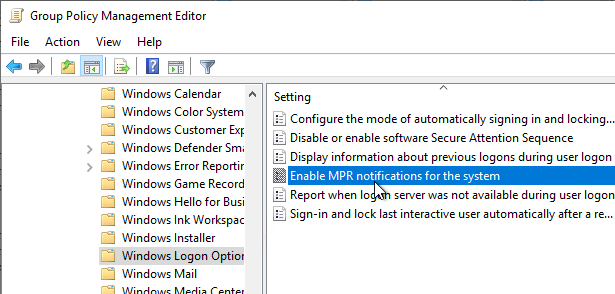
- For Windows 11 24H2 and newer, make sure the GPO setting Enable MPR notifications for the System is enabled at Computer Configuration | Policies | Administrative Templates | Windows Components | Windows Logon Options. Make sure HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\EnableMPRNotifications is set to 1 on the Workspace app machine.
- Logoff Windows and log back on. In Task Manager you should now see ssonsvr.exe. This won’t appear unless you logoff and log back on.
- If Workspace app won’t connect or is slow to enumerate icons, then you might have to disable Automatically detect settings in IE.
- Right-click the Workspace app icon and click Advanced Preferences.
- Click Configuration Checker.
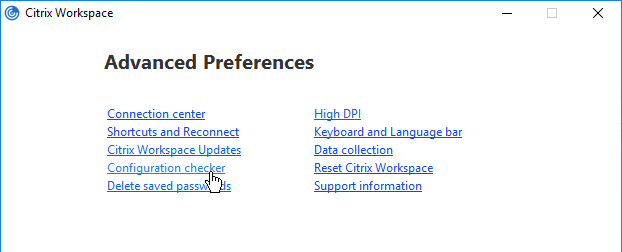
- Check the box next to SSONChecker and click Run.
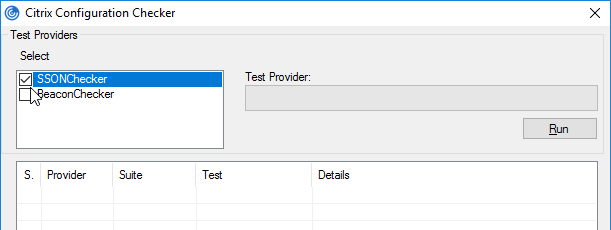
- The lines with red x will indicate the issue and corrective action.
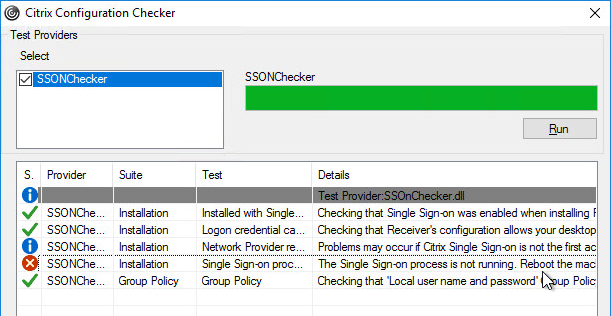
StoreFront Accounts
You can use a client-side GPO to add a store (Account) to Workspace app Self-Service.
- Install the receiver.admx (and .adml) template into PolicyDefinitions if you haven’t already.
- Edit a GPO that applies to endpoint devices that have Citrix Workspace app installed.
- Go to Computer Configuration > Administrative Templates > Policies > Citrix Components > Citrix Workspace > StoreFront.
- On the right, double-click NetScaler Gateway URL/StoreFront Accounts List.
- Select Enabled, and then click Show.
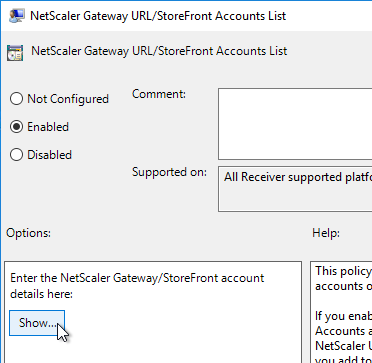
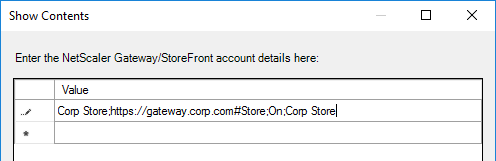
- Enter a store path based on the example shown in the Help box. Workspace app lets you enter a Gateway path. Then click OK.
- Note: Gateway paths work in GPO, but might not work when specified in the CitrixWorkspaceApp.exe installation command line.
Published Shortcuts and Reconnect
Citrix CTX200924 How to Customize App Shortcuts with Receiver for Windows
Workspace app has a user interface for setting Shortcut Paths. Right-click the Workspace app systray icon, click Advanced Preferences, and then click Shortcuts and Reconnect, or Settings Option.
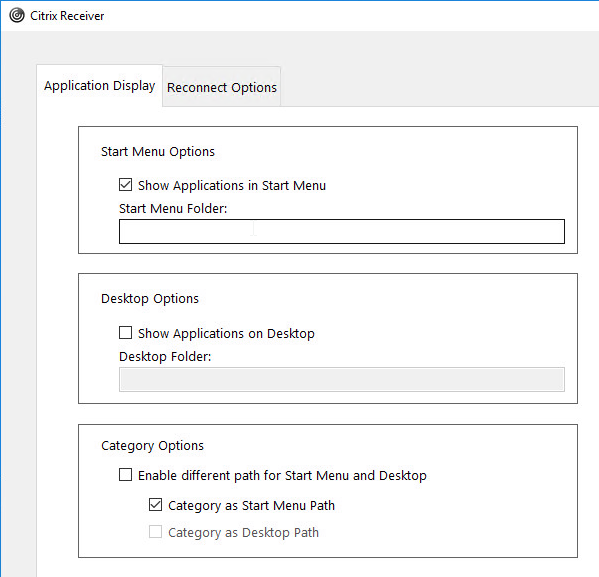
From Citrix Docs Configuring application delivery: There are several methods of controlling how Workspace app displays shortcuts on the Start Menu and Desktop as detailed below:
- Workspace app Registry values
- receiver.admx GPO Template
- From StoreFront in C:\inetpub\wwwroot\Citrix\Roaming\web.config
- Published App Keywords (e.g. prefer).
- Workspace app and Receiver 4.2.100 and newer supports published app Delivery configuration for adding the shortcut to the desktop. This only works if the app is a Favorite, or if Favorites are disabled, or Mandatory Store.
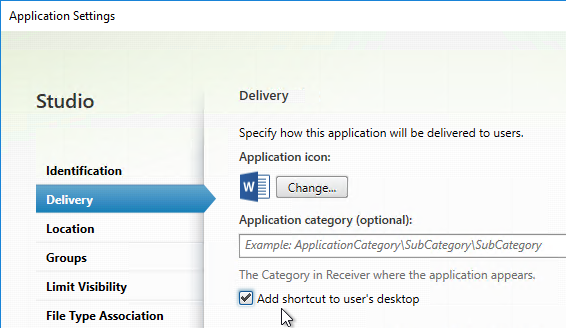
Under HKLM\Software\Wow6432Node\Citrix\Dazzle (or HKCU\Software\Wow6432Node\Citrix\Dazzle) are several registry values related to shortcuts. Some of the settings only apply if SelfServiceMode is set to False. Here are some common options:
- SelfServiceMode – set to False so Receiver disables the Self-Service interface and automatically places all published shortcuts on the Start Menu and/or Desktop. More details in Configuring application delivery at Citrix Docs.
- PutShortcutsOnDesktop – set to True to place every app on the desktop
- DesktopDir – Workspace app places every shortcut on the desktop so it’s probably best to place them in a folder.
- StartMenuDir – If there is potentially a conflict between local apps and remote apps, then you should place the Start Menu shortcuts in a folder.
- PreferTemplateDirectory (with KEYWORDS:prefer=shortcutname) – copies the shortcutname from the template directory to the Start Menu and/or Desktop.
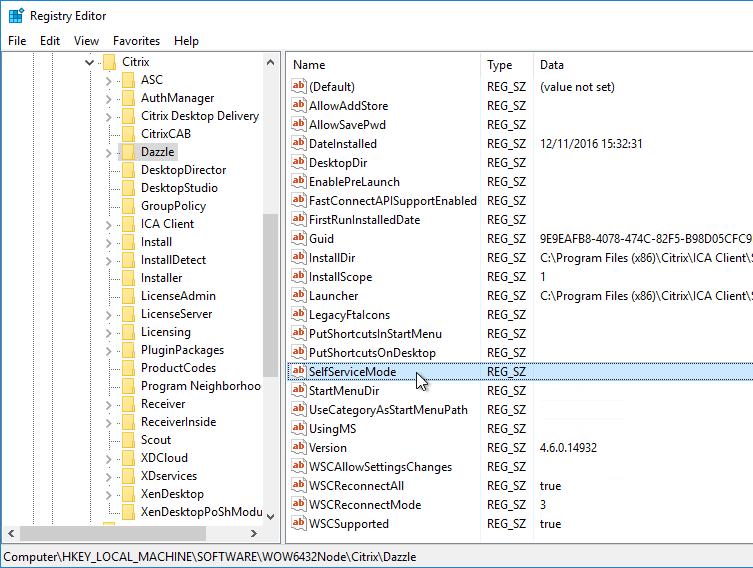
If you import the receiver.admx (and .adml) into the PolicyDefinitions folder, under Computer Configuration > Administrative Templates > Citrix Components > Citrix Workspace (or Receiver) is a node called SelfService.
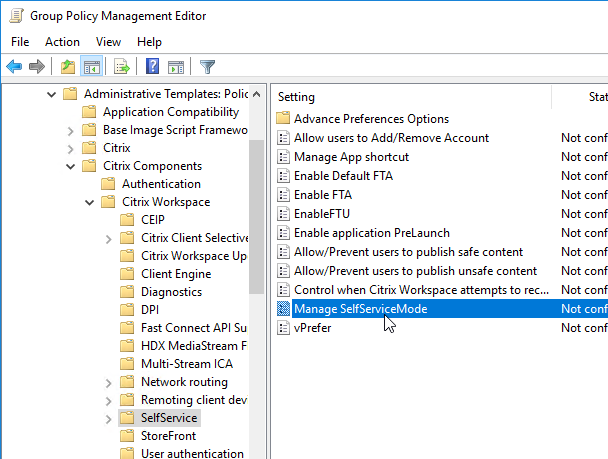
Disable the Manage SelfServiceMode setting to hide the Workspace app Window.
Enable the Manage App shortcut setting to control placement of shortcuts.
Workspace app and Receiver 4.2.100 and newer have the ability to configure (or disable) Workspace Control using group policy. Enable the setting Control when Citrix Workspace attempts to reconnect to existing sessions and configure it as desired.
Prelaunch
Staring with Receiver 4.2, prelaunch is automatically enabled if Workspace app is installed with SSON enabled. Otherwise, set registry values to enable prelaunch. Receiver 4.2.100 prevents the prelaunch icon from appearing on the Start Menu.
- HKLM\Software\[Wow6432Node\]Citrix\Dazzle
- EnablePreLaunch (REG_SZ) = true or false
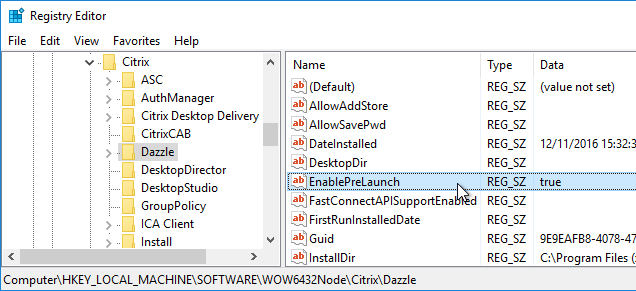
Additional customizations can be configured at:
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\ICA Client\Prelaunch
- Name: State
- REG_SZ: 0 = disable, 1 = just-in-time pre-launch, 2 = scheduled pre-launch
- Name: Schedule
- REG_SZ: HH:MM|M:T:W:TH:F:S:SU where HH and MM are hours and minutes. M:T:W:TH:F:S:SU are the days of the week. For example, to enable scheduled pre-launch on Monday, Wednesday, and Friday at 1:45 p.m., set Schedule as Schedule=13:45|1:0:1:0:1:0:0 . The session actually launches between 1:15 p.m. and 1:45 p.m.
- Name: UserOverride
- REG_SZ: 0 = HKLM overrides HKCU, 1 = HKCU overrides HKLM
Device Access Behavior (Client Selective Trust)
When connecting to a XenApp/XenDesktop session, you might see the following:
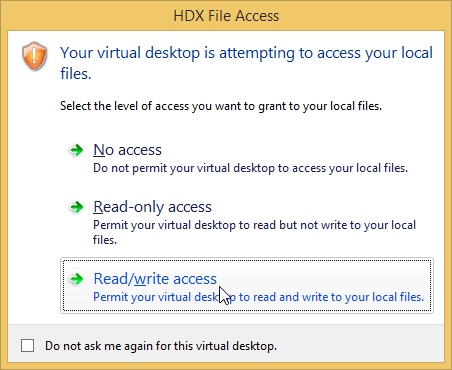
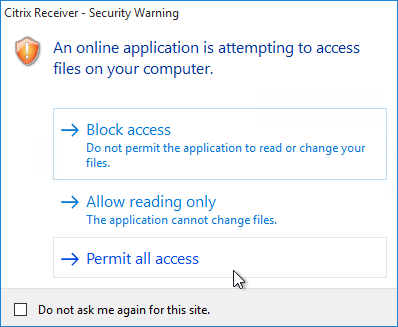
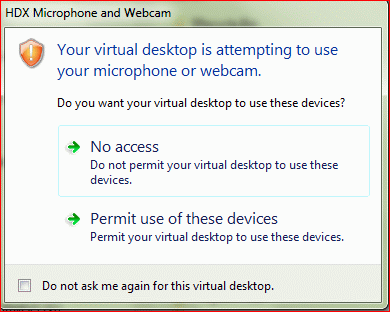
To configure the default behavior, see the Citrix Knowledgebase article How to Configure Default Device Access Behavior of Receiver, XenDesktop and XenApp. Note: there is a bug fixed in Receiver 4.2.100 and newer.
- Download the ADMX file from http://support.citrix.com/article/CTX133565.
- Copy the .admx and .adml files to PolicyDefinitions (Sysvol, or C:\Windows).
- The .adml file goes in the en-US folder.
- Edit a GPO that applies to the endpoint devices that are running Receiver.
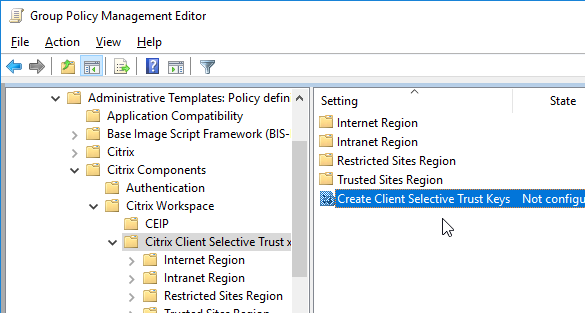
- Go to Computer Configuration | Policies | Administrative Templates | Citrix Components | Citrix Workspace (or Receiver) | Citrix Client Selective Trust (x64).
- Enable the setting Create Client Selective Trust Keys.
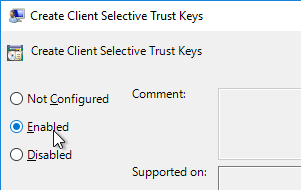
- Then expand the regions, and configure the permission settings as desired.
Desktop Lock
As an alternative to Workspace app Desktop Lock, see Transformer in Citrix Workspace Environment Manager.

External links:
- Dale Scriven YouTube video – Citrix Desktop Lock installation and configuration
- Jarian Gibson and Andrew Morgan – Citrix Receiver Desktop Lock
- An alternative to Desktop Lock – ThinKiosk
Use Studio to configure Workspace app Accounts in Published Desktop
In published desktops, Workspace app can be used for placement of shortcuts on the user’s Start Menu and Desktop. Use group policy to hide the common program groups and then use Workspace app to place published applications back on the Start Menu and Desktop based on user’s group membership and subscription preference.
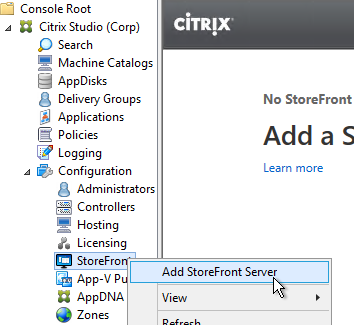
- In Citrix Studio, on the left, expand the Configuration node, right-click StoreFront and click Add StoreFront.
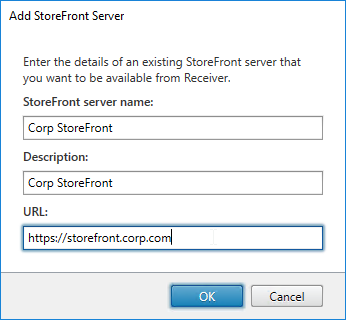
- Enter a descriptive name for the StoreFront server.
- Enter the internal https URL of the load balanced StoreFront servers. Add the path to your store (e.g. /Citrix/Store) and then /discovery on the end of the URL. The full URL would be similar to https://citrix.corp.com/Citrix/Store/discovery. Click OK.
- Edit a Delivery Group that has a published desktop and Citrix Workspace app installed.
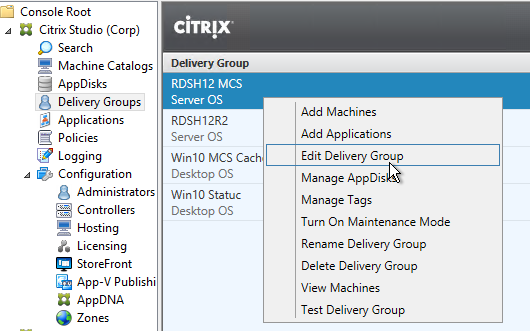
- On the StoreFront page, change the selection to Automatically, using the StoreFront servers selected below, and then check the box next to the StoreFront URL. Click OK. Now when users launch the published desktop, Workspace app will be automatically configured with this URL.
Published Desktop – use Workspace app to control Shortcuts
If you install Workspace app inside a published desktop (Workspace app on a VDA), then Workspace app can get icons from StoreFront and put those icons on the user’s published desktop Start Menu and Desktop. This is an alternative to using a User Experience Management product to control shortcut placement.
Note: Workspace app tends to be slow to create Start Menu shortcuts, so make sure you perform a Proof of Concept to determine how this functionality impacts logon times.
Configuration of Workspace app inside a published desktop is simplified if you have the following minimum versions:
- Workspace app installed inside the VDA
- VDA 7.17 or newer
- StoreFront 3.14 or newer
If you meet these minimum version requirements, then Workspace app installed in the VDA automatically tries to launch published applications on the same local VDA rather than trying to launch them from a different VDA (aka double-hop). This feature is called vPrefer.
- If you don’t meet these minimum version requirements, then you’ll need to use the older Prefer Keyword method of handling Workspace app shortcuts as detailed later.
- For a detailed explanation of vPrefer, see Citrix Blog Post VPrefer: Session Sharing Between a Published Desktop and a Published Application Made Easy
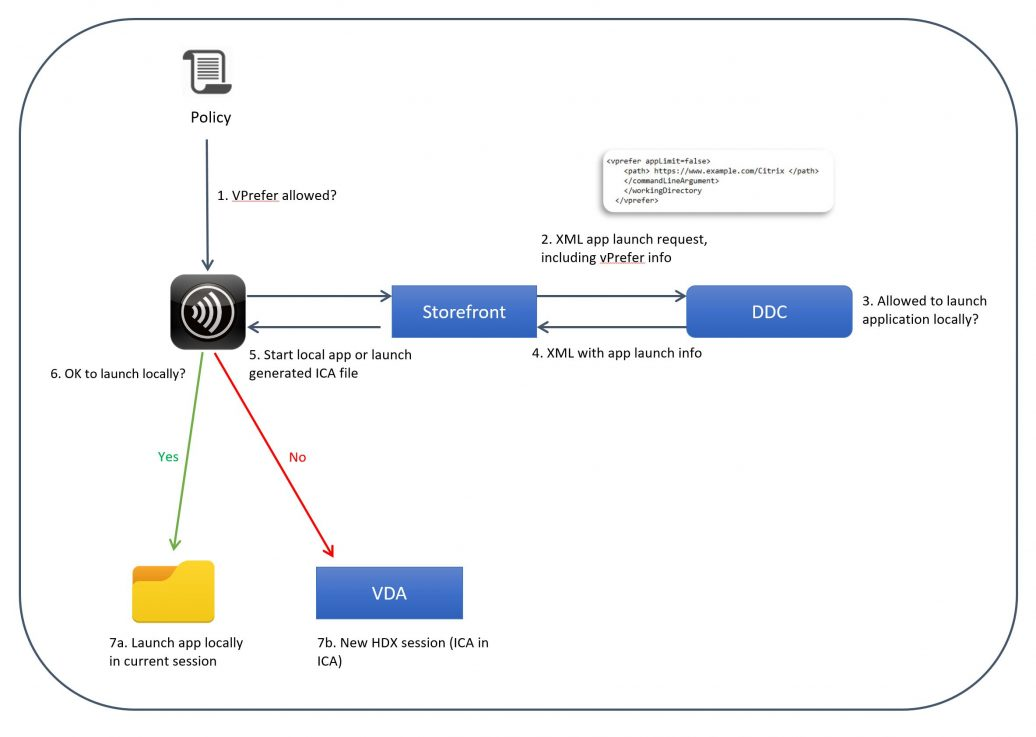
Do the following for all versions of Workspace app, VDA, and StoreFront, whether using the Prefer keyword or not:
- Make sure Workspace app or Receiver version 4.11 or newer is installed on the VDA.
- Install the Workspace app ADMX files if you haven’t already. For vPrefer, make sure they are the ADMX files from Workspace app.
- Enable the Group Policy setting Remove common program groups from Start Menu and apply it to non-administrators.
- This removes all Public (aka All Users) Start Menu shortcuts. Workspace app will re-add the shortcuts based on user group membership.
- On the VDA, configure the following Workspace app Registry keys (or corresponding settings in the receiver.admx GPO template):
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\WSCReconnectMode=”0″ so Workspace app doesn’t try to reconnect to the published desktop you’re already running.
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\SelfServiceMode to False. This turns off the Workspace app Self-Service GUI and acts like all icons are subscribed. Otherwise, only subscribed (favorited) icons would be placed on the Start Menu and Desktop.
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\UseCategoryAsStartMenuPath = True. This creates a Start Menu folder based on the published app’s configured Category.
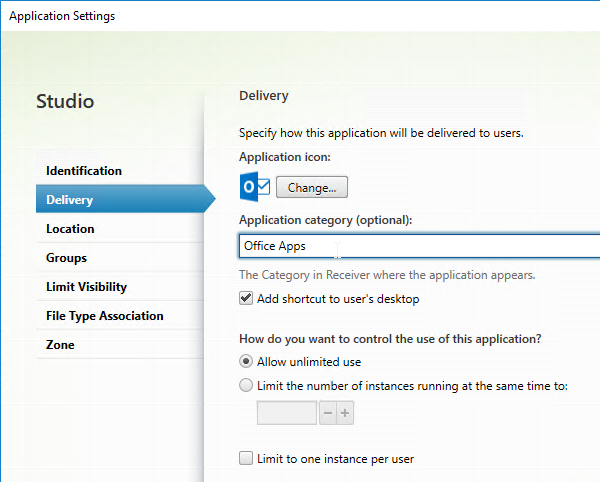
- Configure each desired published app to Add shortcut to user’s desktop.
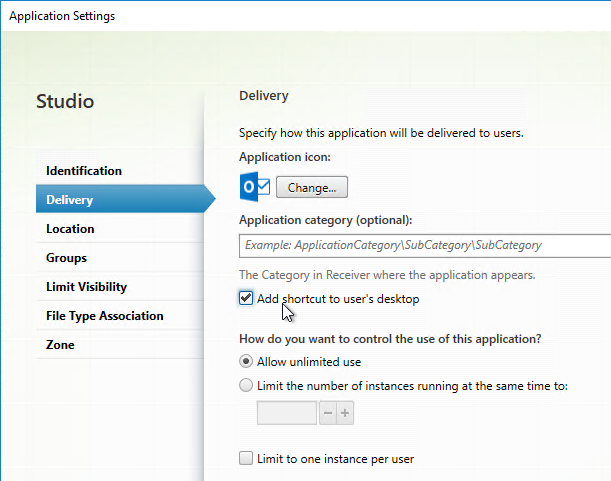
- Or, configure HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\PutShortcutsOnDesktop = True to place all icons on the desktop.
- To control icon placement, configure the following registry values:
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\StartMenuDir to place published applications in a sub-folder. Note: Windows Server 2012 and Windows 10 and newer only supports a single level of Start Menu folders, so setting this effectively turns off published app categories.
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\DesktopDir to place published applications in a sub-folder on the desktop.
- Pass-through authentication:
- In a GPO that applies to the VDA, import the receiver.admx file, and set Local user name and password to Enabled. Check the box next to Allow pass-through authentication for all ICA connections.
- If you’re using Gateway internally, and if Workspace app 1808 or newer, then also enable Single Sign-on for NetScaler Gateway.
- In a user-level GPO that applies to the VDA, add the StoreFront FQDN to the Local Intranet zone. Make sure it is not in the Trusted Sites zone, or enable Automatic logon with current user name and password for the Trusted Sites zone.
- Make sure ssonsvr.exe is running after you login to the VDA. If not, troubleshoot it.
- When configuring Citrix Profile Management, make sure !ctx_startmenu! is not excluded from roaming.
- In Citrix Studio, configure a Delivery Group with delivery type = Desktop and Applications. Assign users to the delivery group, and the individual published applications (if visibility is limited).
- In Citrix Studio, edit each published application, and on the Delivery tab, specify a category. This will become the Start Menu folder name.
- If Workspace app Self Service Mode (GUI) is enabled, in Studio, edit each application, and add KEYWORDS:Auto and/or KEYWORDS:Mandatory to the published application description. This forces the applications to be subscribed/favorited. Only subscribed (or Favorite) apps are displayed in the Start Menu and Desktop. Unless you disable Workspace app’s SelfService interface as described earlier.
- Another option is to go to the StoreFront Console, click Stores on the left, and on the right, click Configure Store Settings, and click Disable User Subscriptions. This causes all apps to appear on the Start Menu and/or Desktop depending on Workspace app configuration.
- Create a group policy that applies to VDAs, and configure the group policy to define the Store URL for Workspace app similar to https://citrix.corp.com/Citrix/Store/discovery. Replace the FQDN with your load balanced StoreFront FQDN. Also replace the path to the store with your store path. Make sure there is /discovery on the end. By default, Workspace app and Receiver only support https.
- Your StoreFront store probably delivers both application and desktop icons. If you want to filter out the desktop icons, then create a new StoreFront store, and configure the Workspace app on the VDA to connect to the new Store.
- In StoreFront Console, click the store for VDAs, and click Configure Store Settings. On the Advanced Settings page, in the Filter resources by type row, choose Citrix.MPS.Desktop.
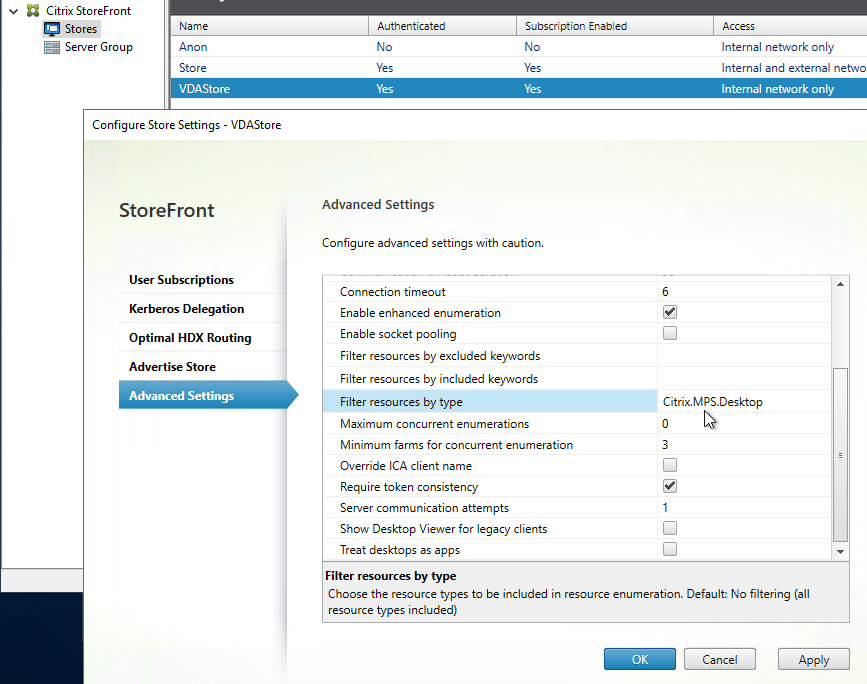
- For vPrefer in Workspace app, VDA 7.17 (or newer), and StoreFront 3.14 (or newer), edit a GPO that applies to the VDAs.
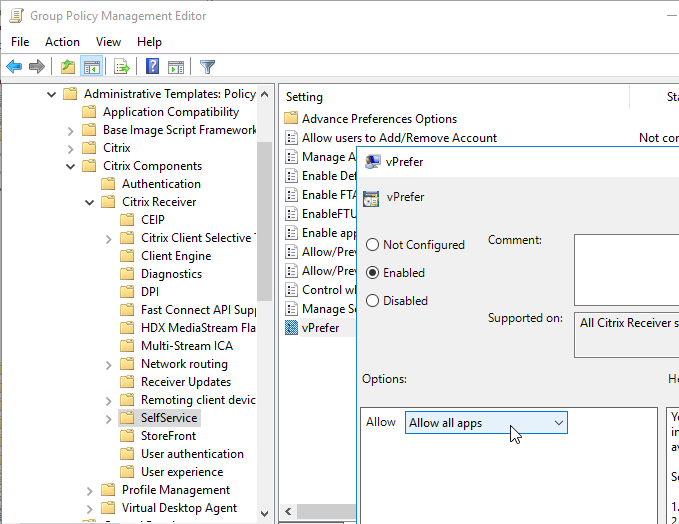
- Go to Computer Configuration | Policies | Administrative Templates | Citrix Components | Citrix Workspace (or Receiver) | SelfService.
- Edit the setting vPrefer. This setting is only in Workspace app ADMX templates from Workspace app.
- Set it to Allow all apps. Source = 7.17 vPrefer – not working with 32Bit Apps at Citrix Discussions.
- On your Delivery Controller, in PowerShell, run set-brokersite -TrustRequestsSentToTheXmlServicePort $true
- This is required for Pass-through Authentication from Workspace app.
- Configure your client devices to connect to the published desktop.
- When users connect to the published desktop, Workspace app will auto-launch and hopefully auto-login.
- If Workspace app Self-Service Mode is disabled, all published applications should automatically appear in the Start Menu and Desktop.
- If Workspace app Self-Service Mode is enabled, then only applications with KEYWORDS:Auto and/or KEYWORDS:Mandatory in the published application description will be displayed. Users can open the systray icon to subscribe to more applications.
- Users can copy icons from the Start Menu to the desktop. Make sure the user Copies the icon and doesn’t Move it.
- Users can then launch applications directly from the Start Menu, from the Desktop, or from the Workspace app (if the Self-Service interface is enabled).
- If Workspace app 4.11 (or newer), VDA 7.17 (or newer), and StoreFront 3.14 (or newer), then vPrefer is enabled by default. When launching an app icon that came from Workspace app, Workspace app checks the local VDA machine to see if the application can be launched on the local VDA instead of by creating a new Citrix double-hop session.
- If the application is installed locally on the VDA then the local application shortcut should launch quickly. If the application is on a different delivery group then a second (double-hop) Citrix HDX/ICA connection will be established.
- If the user deletes Workspace app shortcuts from the Start Menu, you can get them back by going to the systray icon and refreshing the applications. Or sometimes you have to reset Workspace app.
If you are running components older than Receiver 4.11, VDA 7.17, and StoreFront 3.14, then you’ll need to configure the prefer keyword to get Receiver delivered icons to launch on the local VDA instead of in a new double-hop Citrix connection.
- Enable the Group Policy setting Remove common program groups from Start Menu and apply it to non-administrators.
- For applications that are installed on the same VDA that is publishing the desktop, configure Group Policy Preferences to recreate the application shortcuts based on Active Directory group membership. Applications on other delivery groups are handled by Receiver.
- Or use the prefer keyword to copy shortcuts from the PreferTemplateDirectory.
- On the VDA, configure the following Receiver Registry keys (or corresponding settings in the receiver.admx GPO template):
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Dazzle\PreferTemplateDirectory = a UNC path or local path containing shortcuts to be copied by the prefer keyword. This can point to C:\ProgramData\Microsoft\Windows\Start Menu.
- In Citrix Studio, configure a Delivery Group with delivery type = Desktop and Applications. Assign users to the Delivery Group and the applications (if visibility is limited).
- In Studio, edit each application and change KEYWORDS:Prefer to KEYWORDS:prefer. Notice the lower case p. It doesn’t work with uppercase P.
- With the prefer keyword, if you publish an application that is also created using Group Policy Preferences, the Group Policy Preferences icon will take precedence. This is good. Otherwise the Receiver published application icon would result in a new Citrix double-hop session.
- See Ralph Jansen Citrix Receiver 4.1 Prefer keyword examples
- If using the prefer keyword with the PreferTemplateDirectory, enter it as KEYWORDS:prefer=shortcutname where shortcutname is the name of the shortcut that is copied from the Template directory.
- In Studio, edit each application and change KEYWORDS:Prefer to KEYWORDS:prefer. Notice the lower case p. It doesn’t work with uppercase P.
- Configure your client devices to connect to the published desktop.
- When users connect to the published desktop, Group Policy Preferences will create shortcuts to local applications.
- Receiver will auto-launch and hopefully auto-login.
- If Receiver Self-Service Mode is disabled, all published applications should automatically appear in the Start Menu and Desktop.
- If Receiver Self-Service Mode is enabled then only applications with KEYWORDS:Auto and/or KEYWORDS:Mandatory in the published application description will be displayed. Users can open the systray icon to subscribe to more applications.
- For published applications with KEYWORDS:prefer=shortcutname, Receiver should copy icons from the template directory to the Start Menu and/or Desktop. See below for considerations.
- Users can copy icons from the Start Menu to the desktop. Make sure the user Copies the icon and doesn’t Move it.
- Users can then launch applications directly from the Start Menu, from the Desktop, or from the Receiver (if Self-Service interface is enabled).
- If a local shortcut (e.g. Group Policy Preferences shortcut, or copied from template directory) matches a published application with KEYWORDS:prefer then the local shortcut will override the published application icon.
- If the application is installed locally on the VDA then the local application shortcut should launch quickly. If the application is on a different delivery group then a second (double-hop) Citrix HDX/ICA connection will be established.
- If the user deletes Receiver shortcuts from the Start Menu, you can get them back by going to the systray icon and refreshing the applications. Or sometimes you have to reset Receiver.
Notes regarding Prefer Template Directory
- Prefer Template Directory can point to C:\ProgramData\Microsoft\Windows\Start Menu, which is the All Users Start Menu.
- The shortcuts copied from the Prefer Template Directory are renamed to match the published app name.
- For prefer local apps, any command line parameters specified in the published app are ignored. If you need these command line parameters, add them to the shortcut in the Prefer Template Directory.
- If you have multiple published apps pointing to the same prefer local shortcut, then only one copy will be made, and it will have the name of only one of the published apps. To workaround this, in the Prefer Template Directory, create separate shortcuts for each published app, and adjust the published app prefer keyword accordingly.
- Jan Hendrik Meier Automatic Shortcut generation for local installed applications in a Citrix XenDesktop / XenApp 7.x environment has a script that can create shortcuts based on the published apps with prefer keyword. These shortcuts can then be copied to your Prefer Template Directory.
How to Script/Automate Workspace app and Receiver Self-Service
From Citrix Knowledgebase article Driving the Citrix Receiver Self-Service Plug-in Programmatically: by default, Workspace app Self-Service (SSP) activities are driven by user interaction. However, SSP exposes sufficient information for its activities to be scripted.
When SSP builds a shortcut, it builds it to a small stub application in a file %appdata%\Citrix\SelfService\app-name-with-spaces-removed.exe for each resource. These files allow SSP to create a fake ‘install’ record for Add/Remove Software. Running these .exe files causes the application to launch. Note: Workspace app and Receiver 4.3.100 and newer don’t create stubs by default. To enable, set HKLM\Software\Wow6432Node\Citrix\Dazzle\AlwaysUseStubs (REG_SZ) = true.
If you want to drive SSP directly for launch instead of through an .exe stub, look at the keys under HKCU\Software\Microsoft\Windows\CurrentVersion\Uninstall. There will be keys in there named farm-name@@server-farm-name.app-friendly-name. In these keys you’ll find a LaunchString value that shows the relevant parameters. These parameters are user-independent and can therefore be cloned from a reference user to a general case. You can copy and reuse these parameters without interpretation.
Running the command selfservice.exe –init –ipoll –exit starts SSP, performs a refresh (interactive poll) from the current provider, and forces a clean exit.
Additional command line parameters are detailed at Driving the Citrix Receiver Self-Service Plug-in Programmatically.
Citrix Workspace app come with a .dll file that implements the Citrix Common Connection Manager SDK. You can use the CCM SDK to do the following:
- Launch Sessions
- Disconnect Sessions
- Logoff Sessions
- Get Session Information
Citrix was kind enough to develop a PowerShell module that calls functions from the .dll. Get the CCMPowershellModule from Github. The PowerShell module contains functions like the following:
- CCMTerminateApplication
- CCMLaunchApplication
- CCMGetActiveSessionCount
- CCMDisconnectAllSessions
Launcher Scripts
Ryan C Butler Storefront ICA file creator at Github. See Create an ICA File from Storefront using PowerShell or JavaScript for more info.
Stan Czerno – Powershell Script to launch one or more Published Applications from Citrix Storefront 2.x through 3.11: the script launches a browser, connects to StoreFront (or NetScaler Gateway), logs in, and launches an icon. This is a very well-written script that uses a .dll file from Citrix Workspace app to display session information.
Citrix Solutions Lab StoreFront Launcher Script at Github. It attempts to closely resemble what an actual user would do by:
- Opening Internet Explorer.
- Navigating directly to the Receiver for Web site or NetScaler Gateway portal.
- Completing the fields.
- Logging in.
- Clicking on the resource.
- Logging off the StoreFront site.
David Ott StoreFront App/Desktop Launch Testing Script uses Internet Explorer to login to StoreFront and launch a resource. Sends email with the result. Uses wficalib.dll to get session information.
Microsoft Teams
Citrix and Microsoft jointly support the delivery of Microsoft Teams from Citrix Virtual Apps and Desktops using optimization for Microsoft Teams. The Teams optimization components are built into VDA and Workspace app. There is no need to install anything separately. The feature is based on Browser Content Redirection so don’t exclude that feature when installing the VDA.
Microsoft Teams optimization/offloading requires the following:
- Newest version of Microsoft Teams machine-wide installation (ALLUSER=1)
- Newest version of Citrix VDA
- Newest version of Citrix Workspace app.
Feature matrix and version support at Citrix Docs shows the required versions of Teams, Citrix VDA, and Citrix Workspace app for various Teams features.
See Citrix Docs Optimization for Microsoft Teams.
Troubleshooting – Citrix QuickLaunch
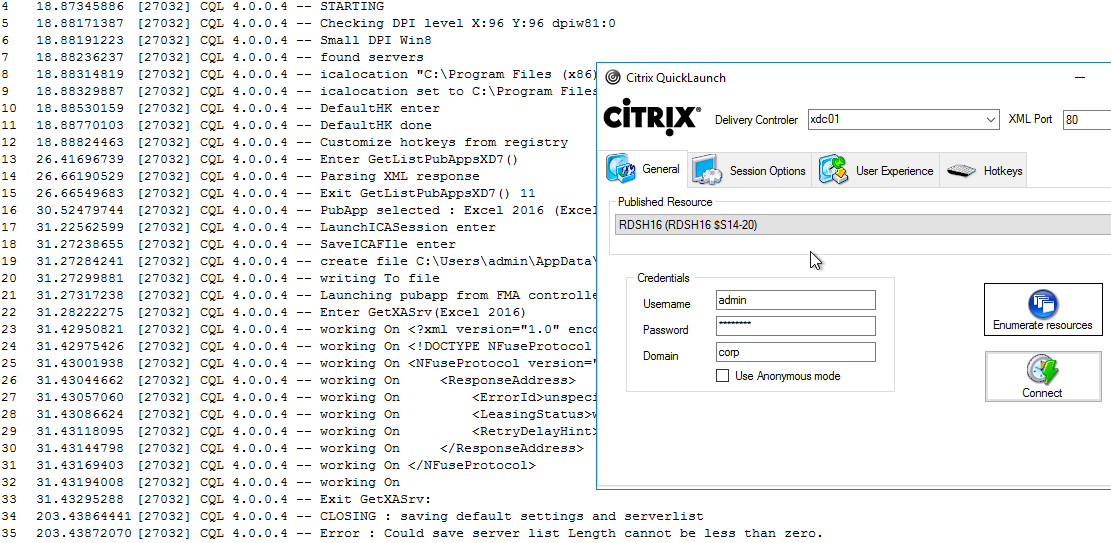
Citrix CTX219718 QuickLaunch Tool (Testing Application and Desktop Launch) lets you launch Citrix sessions directly from a Controller without needing StoreFront.
You enter a Controller address, credentials, and then it shows you the published resources. You can pick a resource, edit properties on the other tabs, and then Connect. This allows you to easily try different connection properties.
If you run into problems launching a session, use Sysinternals DebugView while running CQL in Debug mode (/debug switch).
Troubleshooting – Workspace app Logging
In Workspace app 2309 and newer, if you right-click the Workspace app icon in the system tray, there’s a Troubleshooting menu with a Collect Logs option.
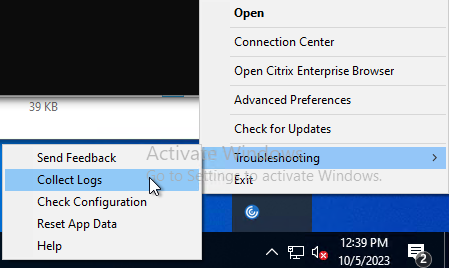
You can also access Log Collection from Advanced Preferences.
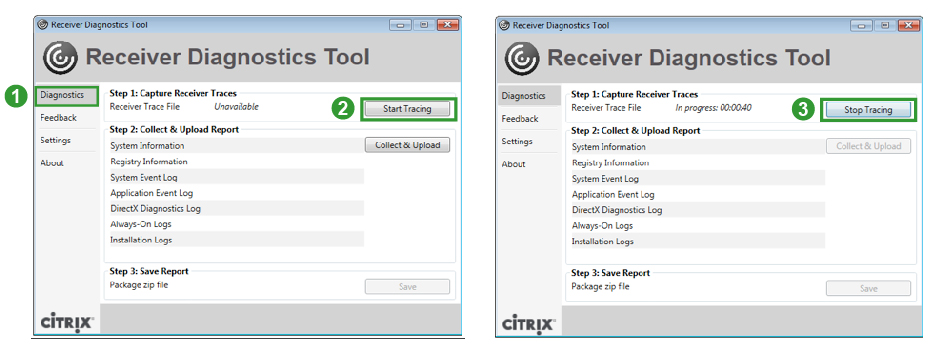
There are a couple methods of logging Workspace app for Windows operations. One method is CTX141751 Citrix Receiver Diagnostics Tool – For Windows, which creates a CDF trace that can be parsed by CDFControl.
Another method is CTX132883 How to Enable Logging on Receiver for Windows Using Registry Entries. The logfiles in %USERPROFILE%\Appdata\Local\Citrix\ are human readable. And CTX206102 Enable SSON Logging Using Registry Key.
Instead of creating the registry keys manually, you can use the following .reg file provided by Wolfgang Thürr:
Windows Registry Editor Version 5.00 ;only for x64 windows os ;import with admin rights ;restart your computer to activate the logging and tracing settings ;create C:\TEMP for the launch ICA log and SSON logn (no environment variables can be used) ;general Workspace app and Receiver logging ;************************ ;logpath: %USERPROFILE%\Appdata\Local\Citrix\Receiver [HKEY_LOCAL_MACHINE\SOFTWARE\ Wow6432Node\Citrix] " ReceiverVerboseTracingEnabled" =dword:00000001 ;Authentication Manager logging ;***************************** * ;logpath: %USERPROFILE%\Appdata\Local\ Citrix\AuthManager [HKEY_LOCAL_MACHINE\SOFTWARE\ Wow6432Node\Citrix\ AuthManager] "LoggingMode"="verbose" "TracingEnabled"="True" "SDKTracingEnabled"="True" ;Self Service logging ;******************** ;logpath: %USERPROFILE%\Appdata\Local\ Citrix\SelfService [HKEY_LOCAL_MACHINE\SOFTWARE\ Wow6432Node\Citrix\Dazzle] "Tracing"="True" "AuxTracing"="True" "DefaultTracingConfiguration"= "global all –detail" ;save launch ICA ;*************** ;logpath: C:\TEMP\ica.log (no environemnt variables allowed) [HKEY_LOCAL_MACHINE\SOFTWARE\ Wow6432Node\Citrix\ICA Client\Engine\Configuration\ Advanced\Modules\Logging] "LogConfigurationAccess"=" true" "LogConnectionAuthorisation"=" true" "LogEvidence"="true" "LogICAFile"="true" "LogFile"="C:\\TEMP\\ica.log" "LogStartup"="true" ;Receiver Always On Tracing ;************************** ;generates ETL Files for analyzing with CDFControl see CTX111961 for details ;can be configured or overruled by GPOs (icaclient.admx) ;path %USERPROFILE%\AppData\Local\ Temp\CTXReceiverLogs [HKEY_LOCAL_MACHINE\SOFTWARE\ Policies\Citrix\ICA Client\AoLog] "EnableTracing"=dword:00000001 ;Single Sign-on Logging ;************************** ;https://support.citrix.com/article/CTX206102 [HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Citrix\Install\SSON] "DebugEnabled"="true" "LogPath"="C:\\Temp"
Troubleshooting – Duplicate Stores
Stores are sometimes duplicated in Workspace app, especially if you are running Workspace app inside a VDA. (h/t Dan High)
StoreFront URLs can be defined in several places:
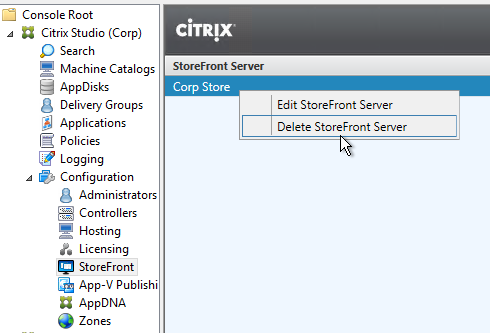
- In Studio, go to Configuration > StoreFront and delete all URLs configured here.
- Look in GPOs for Computer Configuration > Administrative Templates > Policies > Citrix Components > Citrix Workspace > StoreFront > NetScaler Gateway URL/StoreFront Accounts List. Remove any URLs configured here.
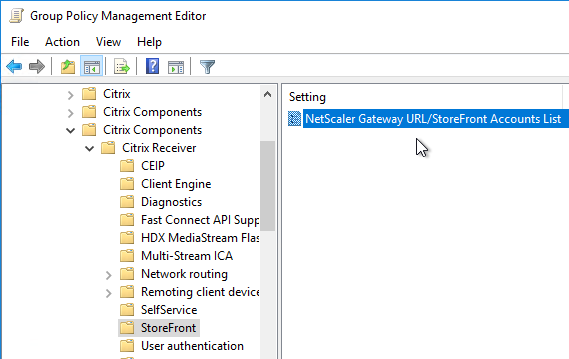
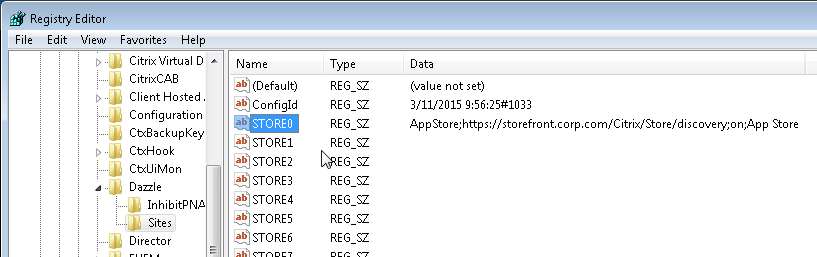
- In the client-side registry, at HKLM\Software\Wow6432Node\Citrix\Dazzle\Sites, you might see store addresses that were specified during a command line installation of Workspace app.
- When Citrix Workspace app switches between StoreFront servers in multiple datacenters, it’s possible for each datacenter to be treated as a separate Workspace app site. This can be prevented by doing the following. From Juan Zevallos at Citrix Discussions:
- Match the Base URL in all datacenters.
- Match the SRID in all datacenters – The SRID can be safely edited in the C:\inetpub\wwwroot\Citrix\Roaming\web.config. Make sure to propagate changes to other servers in the group.
- Match the Delivery Controller names under “Manage Delivery Controllers” – The XML brokers can be different, but the actual name of the Delivery Controller/Farm must be identical.
If you are running Workspace app on a VDA, once you’ve removed the configured URLs shown above, do the following to clean up the VDAs:
- On the VDA, HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Citrix – Delete the number folders representing policy entries.
- On session host VDAs, HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows NT\CurrentVersion\Terminal Server\Install\Software\Citrix – Remove the entries for storefront in the following folders.
- Under \receiver\ctxaccount delete all entries.
- Under \SR\Store delete the entries.
- On the VDA, C:\ProgramData\CitrixCseCache – Delete all files
- On the VDA, C:\ProgramData\Citrix\GroupPolicy – Delete all folders and files.
- Run gpupdate and logoff.
- In the user’s registry, HKEY_CURRENT_USER or the profile registry hive. Possible profile reset.
- Under Software\Citrix\Dazzle\Sites – Delete all entries.
- Under Software\Citrix\Receiver\ctxaccount – delete all entries.
- Under Software\Citrix\SR\Store – delete the entries.
- Verify no cached profile folders for user on server.
Does the Citrix Workspace App (CWA) 2210 have a command line switch to set High DPI Scaling to Yes?
I haven’t found one and it’s not listed at https://developer.cloud.com/citrixworkspace/server-integration/global-app-configuration-service/docs/getting-started
Thanks Carl
I think it is only possible with GPO and Registry.
Hi Carl,
I have a question about pushing modern authentication for Office 2013 in Citrix
What would be the way to create and tweak the following registries through GPO
“Windows Registry Editor Version 5.00
[HKEY_CURRENT_USER\Software\Microsoft\Exchange]
“AlwaysUseMSOAuthForAutoDiscover”=dword:00000001
[HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Common]
[HKEY_CURRENT_USER\Software\Microsoft\Office\15.0\Common\Identity]
“EnableADAL”=dword:00000001
“Version”=dword:00000001
”
thank you
The easy way is Group Policy. Edit one that applies to users. Expand User Configuration, expand Preferences, find Registry, and create registry values.
Hi Carl, regarding WSA, it seems that once a user has signed into the app, their login is cached.
Even after a restart, the user just launches WSA without having to sign in again. Had a quick look at Group Policy but nothing obvious.
Hi Carl – Love your website! I have an issue with cookies on the local web browsers (Chrome and Edge as far as I know) where the published apps in Storefront do not launch. It looks like the launch is trying to occur, but it just stops. When we clear the cookie cache from the web browser, it defaults to detecting the Workspace client and then we hit already installed and it downloads the .ica file and we can launch it. My question is: Is this something we can create some type of policy for clearing the cookie cache upon login? It would definitely save us some heartache. Thanks.
You could tell users to use Private/Incognito window.
Disable HTML5 Workspace App, or force it to be used.
Security/Privacy teams decided that usage of plug-ins must be configured client-side, not server-side.
That’s what I thought. I was hoping to avoid the user in this, but thank you so much for your insight. I appreciate it.
We are having the same issue, I think a browser update with Edge and Chrome broke the Workspace detection.
Does anyone notice that in the devices tab of the 2207 Linux Workspace App, devices always show as Generic?
Hello Carl, I have some questions about HTML5 implementations:
1. Can I see local (and network drives) in an HTML5 session? Meaning is this supported?
2. If yes can you point me to guidance on how this is done. For context I have a SF server and I am forcing HTML5, no other policies in place. I see old documents referencing 6.5 , but they translate well to 7.x.
3. I am also looking for updated information on disabling the desktop viewer in HTML5. I have unchecked in SF console and set ConnectionBar= 0 / Off / False in web.config as well as setting it in the default ICA file . All to no avail.
Running 2203 VDA on Win2k19 and AVD , Citrix Cloud.
There is a File Transfer feature – https://docs.citrix.com/en-us/citrix-workspace-app-for-html5/configure.html#file-transfer
Toolbar – https://docs.citrix.com/en-us/citrix-workspace-app-for-html5/configure.html#toolbar
To reset Citrix Workspace App do I have to use
“C:\Program Files (x86)\Citrix\ICA Client\SelfServicePlugin\CleanUp.exe” /silent -cleanUser
like mentioned in
https://support.citrix.com/article/CTX140149/how-to-reset-receiver-using-the-command-line
or
https://docs.citrix.com/en-us/citrix-workspace-app-for-windows/install.html
or like used earlier (and mentioned in your documentation
“C:\Program Files (x86)\Citrix\ICA Client\SelfServicePlugin\CleanUp.exe” -cleanUser -silent
So how do i have to use the silent parameter?
Use whichever method works.
Hello carl, Given command is perfectly working fine with user login on one machine but how do we push this command remotely on multiple computers. Can we add FORCE /ALL USERS or something. Need help.
In a group policy, add the command as a login script.
Neither method works. I still get a Citrix StoreFront window that pops up after running this command. We don’t want our users seeing these. I’ve tested these command on old Receiver client, as well as current Workspace client. They both have the exact same issue. “Silent” isn’t “Silent”.
Hi Carl
We publish google chrome but have seen issues with the window losing focus or minimizing automatically since upgrading to the latest workspace app. Rolling back seems to resolve the issue.
Any suggestions?
This is a bug. Maybe it is fixed with the 2210 version or in the near future
Hello Thorsten. We’re also affected by this bug since 2206 (also tested with 2207, 2209 and 2210). On 2203 LTSR we didn’t see it. Do you have any official information / confirmation / ticket about this issue? I cannot find it in the known issues.
no sorry
Hi Carl,
is there any chance to use full working SSO without a reboot / logout after fresh Installation of the workspace App? Any hacks here by restarting something?
It collects credentials during the Windows logon process.
Does this mean any upgrade of the WS app with SSO also will require at least one reboot? The app is installed with admin rights, and attempted upgrade by non-admin user needs two reboots here.
The ssonsvr.exe process only captures credentials as the user logs in.
When I migrate our WorkspaceApp from v19.12.7000 to 21.12.1 or 22.03 all Published Desktop icons appear on the user’s desktop.
After deinstalling WorkspaceApp and reinstalling the old v19.12.7000 the Published Desktops are gone and only reside in the start menu (as expected).
Citrix OnPrem, some Desktops have TreatAsApps configured.
I found nothing about this “Show Published Desktop icons on desktop” in the documentation and citrix support (India) could not help on this.
All desktops? Or just the ones with TreatAsApp configured?
I wonder if a CDF trace would help. Or maybe a procmon showing you which Dazzle registry key might be causing it.
Hi Carl, yes all desktops are shown on the desktop.
But your hint with Dazzle pushes me in the right direction. We had a policy which set’s PutShortcutsOnDesktop to True.
With WorkspaceApp 19.12 this setting only shows application shortcut on Desktop, but with WorkspaceApp 21.12 ff. this setting pushes all desktop shortcuts to the Desktop.
Hi Carl,
we are getting a very funny problem, we configured a brand new fresh environment on LTSR 2203 and the latest Netscaler 13 24.38 and we can just connect to the vdi normally with the web portal through the netscaler, everything just fine.
But when we try to add the account on the workspace app it does not work and keep giving the message “Unable to add account with the given server URL. Ensure that it is correct or enter your email address.”. It asks for the logon credentials twice and then throw the error.
Do you could suggest some direction on this problem ? Already redone the whole Netscaler cluster again but nothing has changed. The only thing that is not so normal is that the DDCs and Storefronts are in an exclusive network(192.168.250.0/24), but joined to the same domain as the vdi and the dcs are on (192.168.240.0/24).
It’s usually a problem with the Internal Beacon. Make sure the Internal Beacon cannot be resolved on the Internet.
Hi Carl,
thank you for the tip, was a very good one.
We ended up downgrading the Netscaler to 13.1-4.44 and the same env now works properly.
Thanks and Best Regards,
Alex
I having problems with allowing file access, in the Citrix support article it wants you to import registry, in this blog you accomplish it with just the group policy settings, any advice?
Are you referring to CTX133565? If so, at the top of the article is a download for the GPO template.
We are having issues getting VDI to work on iOS (externally through the netscaler). We use Citrix Cloud (not on prem storefront). We are using the latest iOS workspace app – you launch the VDI, sometimes it lets you type in your password within windows10 and sometimes it just crashes immediately upon launching. Have you seen this before?? Citrix is not providing us much assistance and the logs, which I can provide, don’t seem to be the greatest. I am having a hard time believing it could be the netscaler because it does “launch” the VDI, no errors…just crashes.
Are you using Citrix Cloud Gateway?
Is Rendezvous Protocol enabled on the VDAs?
Is EDT enabled on the VDAs?
Are your VDAs 2106 or newer so that MtuDiscovery is enabled by default?
We have installed/upgraded Citrix Workspace App 2202 on our layered image, in the platform layer. After booting up w/ the new image, the server will not “Azure Join”. We’ve tried multiple times all yielding same result. A dsregcmd /status reveals AZUREJOINED: NO
Hello,
I’m having a question regarding the layout of the Workspace App. I have just set up a new store mainly for workspace connectivity. Everything ist working fine but within workspace the layout looks like the store website. Our old existing workspace stores just have the simple white layout with no banners etc. I would rather prefer this old look and feel but I need a hint where to switch the layout.
Any help would be appreciated.
Maybe you’re looking for the classic experience? https://docs.citrix.com/en-us/storefront/3-12/manage-citrix-receiver-for-web-site/unified-receiver-experience.html
After Updating to Workspace 2112.1 on our Thinclients (W10 1809) after starting a desktop session (Server 2016 with 1912.0.0.24265 and Server 2019 with 1912.0.400.4227) a windows logon prompt appears. The SSO seems to work and I can refresh my apps in Wokspace successfully. But the credentials aren’t passed along to the desktop session. In the Eventlog on the server was nothing suspicious. Version 2109.1 worked fine. Any idea?
If you uninstall, reinstall, and check the box for pass-through authentication during reinstall, does it work?
Thanks for your feedback. I uninstalled and reinstalled the workspace app and made sure to check the SSO checkbox. The SSO-Checker looked fine but still the same problem. I just noticed it only happens when I try to start a Desktop-Session. If i start a seamless app from the same terminalserver the logon seems to work without additional prompt.
Hey Tommy,
Are you sure that you enabled the “Allow pass-through authentication for all ICA connections” setting on your client GPO ? I’ve noticed that not having it enabled wasn’t an issue for SSO on a published desktop with previous versions of the workspace app, but it is now.
Hi Tony,
Thanks for your reply. I’ve set the gpo or at least the corresponding registry values on the client.
[HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Policies\Citrix\ICA Client\Engine\Lockdown Profiles\All Regions\Lockdown\Local Credentials]
“LegacyLocalUserNameAndPassword”=”True”
“EnableSSOnThruICAFile”=”True”
Still the same behavior.
I just tried again with Workspace 2202 and latest MS updates installed. Seems to work now. It was probably really a bug.
Hi Carl,
we have an issue launching sso configured citrix application i.e “The resource is unavailable currently “. here is the scenario, we have Citrix SSO configured and placed citrix application shortcuts on desktop. User launches VDI – Citrix Application shortcuts getting created on user desktop. ssonsrv.exe stores user credentials upon logon.
User Disconnects VDI session
Changed network password
Connecting back to same disconnected session with new password
When trying to launch Citrix Appications from desktop, they are getting “the resource is unavailable currently. Try again later error”
SSO checked shows error iAccess Store configuration (enable domain passthrough authentication for the store)
Any errors in StoreFront Server > Event Viewer > Applications and Services > Citrix Delivery Services?
I am having the same issue. “The resource is unavailable currently. Try again later error. Transaction Id:******” No errors are at SF, DC or VDA…Please help any suggestions?
Hi Arun, Did you find a solution to this
Hey Carl! You always seem to have the answer, so hopefully you can provide some insight to my issue. I wasn’t sure which article to post this with, but since the issue seems to be from Workspace I’ll put it here.
Ok, current production – Double hop -> Server 16 VDA Running VDA1912LTSR and Receiver 4.9LTSR (can’t recall which CU offhand) -> hops to our hosted EMR farm.
Sessions start and stop fine, graceful disconnection and session teardown on first hop vda occurs as expected.
Test environment – Double hop -> Server 19 VDA running 2103 and CWA 2105 (though I see 2107 is available now) -> hop to hosted EMR
Sessions start and hop fine. Teardown never happens as the first hop VDA never disconnects the session. Here’s where it gets complicated. Closing processes of the session to find the one hanging it open seems to lead to the culprit being selfservice.exe. Obviously I can’t add selfservice.exe to LogoffCheckSysModules as it’s what I’m expressly calling for the double hop. I have to assume i’m just missing something. The modules I’m including in workspace install are ReceiverInside, ICA_Client, SSON, and SelfService, so I’ve tried to get that pretty barebones as well.
Any thoughts? Thanks so much by the way, for all you do!
You’re running SelfService as a published app?
Does it work with the full CWA install?
What i’m publishing is %ProgramFiles(x86)%\Citrix\ICA Client\SelfServicePlugin\SelfService.exe -qlaunch “”
We do this rather than pointing the external facing storefront directly at the EMR vendor’s brokers. This forces all external traffic to the EMR to hit our servers first before passing on.
When the user hits my vda as hop 1 it passes thru storefront authentication on login and then launches selfservice.exe pointing at the app. Works great with Server16/vda1912/receiver4.9. Technically works great on the test Server19/vda2103/cwa2105, it just won’t mark the session disconnected at session close as it never closes selfservice.exe. That would be… problematic in production as user sessions would be hanging open and never dropping off.
Carl – As an added test I installed receiver 4.9.9 LTSR on hop 1 (still publishing selfservice.exe -qlaunch “appname”). This worked properly end to end, launching and running and also for application close allowing the session to properly show as disconnected and logging it off. Granted, this is what I’m still using in production but at this point I was unsure if it was something Server 2019 was doing or CWA itself. It definitely seems to be something with the selfservice.exe as part of CWA, but for the life of me I can’t figure what.
Hello Carl and folks,
I’m experiencing a problem with users coming into our environment (on-prem 1912) via vpn. There are two VPN solutions we are using as we transition from one to the other Global VPN and Any Connect. Global VPN uses DTLS while anyconnect is TLS. The anyconnect connection works fine however Global allows the users to logon and establish a session (shared server desktop) but as soon as the initial logon completes the connection is disrupted leaving only the session reliability frozen window up.
The Event log on the VDA , shows the error “connection failed on doman “for user” for reason “Deny”.
EventID 1050.
Are you familiar with this issue at all?
IS there some specific DTLS configuration for VDAs I need to implement to support the vpn connection?
I am currently working through this page:
https://docs.citrix.com/en-us/citrix-virtual-apps-desktops/secure/tls.html#tls-settings-on-vdas
To be clear these connections are internal via VPN so my assumption is the break is between VDA and end-point client inside the VPN tunnel, particularly being that the only difference between working and failing scenarios are the VPN clients being used.
Receiver is 21.6.047
Is MtuDiscovery enabled on the VDAs?
Do you have any security device that is trying to decrypt and inspect the network traffic?
Hi
Since upgrading to 2207 we are seeing the published Chrome application loses focus and moves behind the most active local application window.
We use XenApp 7 to publish the app.
Any ideas?
I have 200+ icons in my WorkspaceApp… is there an easy way to remove them all? I’ve tried “remove store, add store” and “remove, reset, add”… no help.
Hi Carl.
Our users are getting this error when they try to launch the Notepad and other published application in the StoreFront on aws cloud for our users accessing the internet using the company proxy servers ( http/https proxy Trend Micro InterScan Web Security Virtual Appliance IWSVA) ).
Such users are able to successfully authenticate and view the published apps but get the following error when the .ica file is executed to launch the app.
“Unable to connect to the server. Contact your system administrator with the following errors. There is no Citrix XenApp server configured on the specified address. (Socket Error 10060 )”
Other user coming directly without the internet proxy in the browser settings are able to launch the app from their browser . .
We are using the Citrix Workspace.app 2106.
Anyone know if there are “optimization” settings to run Citrix Workspace within a Horizon View environment? In our prod environment. We use Horizon View 7.13 VDI. We installed Citrix Workspace so our end users can reach Cerner which uses Citrix XenApp to server apps to our end users. But the end user experience is really laggy.
I think Cerner has a guide.
Do you have GPUs in your virtual desktops?
I will ask our contact at Cerner to see if they can provide that.
No all our hypervisor do not have GPUs so no GPU for our VDI enivornment.
Is there a way to force users to use the full version instead of the light version by config on the client
Are you asking how to disable the HTML5 Client? In StoreFront console, go to Manage Receiver for Web sites. On Client Deployment tab, change the drop-down to Local Clients only.
I do not wish to disable the HTML% client as it will be used by devices not able to run the receiver. I just want to force the ones on managed devices (Windows) to use the Receiver. Some have set to use HTML5 and I thought switching them back to the Receiver by changing that in the local registry or by GPO if possible
Hello Carl,
I’m using the workspace for linux on Ubuntu 20.04 and the last two versions I have a strange behavior, everything is working well but I launch an apps or a desktop from my browser (FX or Chromium) I have 2 windows. The normal one with the app or the desktop and another one (small one) “Citrix Workspace” Connecting to …… . If I try to close the small one that close both windows so i’m deconnected from my app or my desktop.
Any ideas for removing this annoying windows ?
I try 2 browsers, and the lastest workspace 21.4.0.11
Regards,
Hi Carl, you said : In Workspace app 1808 and newer, you can enable Single Sign-on for NetScaler Gateway.
How it works?
We have just to enable this policy and add a store? (A gateway URL with a store)
Yep. Did you try it?
Nop, next Monday.
You said :
Pass-through authentication:
In a GPO that applies to the VDA, import the receiver.admx file, and set Local user name and password to Enabled. Check the box next to Allow pass-through authentication for all ICA connections.
If you’re using Gateway internally, and if Workspace app 1808 or newer, then also enable Single Sign-on for NetScaler Gateway.
So I have to set :
– local user name and password to Enabled
– Allow pass-through authentication….
– enable Single Sign-on for Netscaler Gateway
(Gateway URL in local intranet zone)
And :
-command line on DDC
-activate SSO on store
I have to set this ? (If I use enable Single Sign-on for NetScaler Gateway.)
-command line on DDC
-activate SSO on store
Hello, I tried but I have a prompt for login 🙁
Sso is activated (process SSO is here and ad policy OK)
ADC version 12.1.XXX
When I enter my login and password everything is OK. I can see and launch my apps (store with an URL gateway and #store)
I have to choose ProxyType : none.
Carl, or anybody, is there a way to create a customized .exe of the Workspace App install file? Or a .msi? We have remote clients, not domain joined, not managed (employee home PCs) that want to login to our Citrix environment through the a browser. Normally we tell them to download and install the citrix client (workspace app).
The kicker is we would like to install with the command line option /ALLOW_CLIENTHOSTEDAPPSURL=1 but have no way to do that. (So if they launch youtube or other video heavy sites, they launch on the client PC, not in the VDA.)
A .msi would let you specify that setting. Why doesn’t Citrix realease a .msi? Or a GUI checkbox when running the .exe for that option?
Greetings Carl ! thanks again for your work !!
On Auto-update subject, you wrote “If Workspace app or Receiver is installed on a VDA, auto-update is automatically disabled. This includes Remote PC.” It’s definitive, there is no way to activate it ? I’ve check Citrix Docs — but sometimes there are some wonderful tips here 😉
Regards,
Hi Carl. We’re currently moving from one Citrix platform to another and everything is working perfectly in on the new platform. The only issue I’m struggling with is moving the users over seamlessly. I have configured the new StoreFront site, along with the old site, in a GPO so that is applied to the users computers. Again, this works. However when the users open their Workspace client they are presented with and “All Accounts” view where content is listed from both Storefront sites. Management would like the focus of the view to remain on the old site until we’re ready to start moving users over.
I have tried setting the AllAccount registry value, via GPO, to that of the old site and although the registry value is applied, the view still changes to the “funky” All Accounts view, which looks completely different to what the user are accustomed to seeing.
Are you aware of a method to enforce the Workspace client to display only the old StoreFront content, without the users having to go to Switch Account and selecting it themselves?
Any help would be most welcome.
Thanks.
Hi Carl and all of you too,
i’m trying to troubleshoot a problem when launching a VDI with Workspace App. All platform is based on 1912LTSR with ADC Gateway for accessing it. I think I’ve a problem regarding certificates. There is anyway to trace/log the connection or errors encountered during the connection process with the Workspace App ? i’ve enabled the logs but I’ve not found anything particular. I can login correctly to the Gateway, I reach the storefront and all desktop available are listed. But when I launch one, it fails with “unable to connect to the server. contact your system administrator with the following error: no error text available” Any advice will be very useful. Thanks!
Point your browser to Gateway and login. In the StoreFront page, if you see Detect Receiver, click Already Installed (don’t click the blue button). Try to launch an app. The browser will download the .ica file. Open the .ica file and edit it with Notepad. What do you see for SSLProxyHost? Are you able to connect to it without certificate errors?
We are currently running Receiver 4.9 LTSR CU6 on our clients that was deployed via SCCM and pointed directly to a store URL. We are trying to use MECM to deploy Workspace 1912 LTSR CU2 which needs to point to a new store URL.
Everything works fine except that the icon shortcuts from Receiver are not being removed and are just turning blank. The new icons for Workspace do show up and work but are renamed to add (1) to the end of the name. Running a Reset Workspace from Preferences fixes this issue but we cannot find a way to do this during the upgrade.
Our MECM script does uninstall Receiver and then runs the Receiver Cleanup Utility. That is the only way we have found that removes the current Store URL so we can then use a new Store URL during the install of Workspace.
Any ideas or advice on removing the blank icons left behind from the old Receiver as part of the upgrade process so our users do not see them upon completion?
Thanks!
I was attempting to install 1912 CU2 LTSR on a machine and I am now being prompted with “This version of Citrix Workspace is not the most recent version. Citrix recommends installing the latest version.’ Is there a switch that can be added to bypass this prompt?
Are you installing the CU2 version? https://www.citrix.com/downloads/workspace-app/workspace-app-for-windows-long-term-service-release/workspace-app-for-windows-1912ltsr.html
CitrixWorkspaceApp_1902.exe /silent /AutoUpdateCheck=disabled
Hi Carl, I’m hoping you can help me figure out something that’s going on – I’m installing the Citrix Workspace app on multiple workstations with Windows 10 Enterprise build 1909, so users can access external Citrix environments (we don’t have a Citrix environment of our own), and after a little bit, the SelfService.exe process will pop up a blank window that can only be seen in alt-tab thumbnails. Screenshot: https://i.imgur.com/rjDaWn4.png
Appears to be related to when SelfService.exe runs with the -periodicpoll argument. It’s been happening with Workspace 2006, 2008, and 2012. I saw in the “fixed issues” section of the notes for 2008 that an issue was fixed where SelfService.exe would occasionally display a blank window – not sure if this is related, and even if it is, supposedly it was fixed. I haven’t yet found a combination of installation arguments that will consistently stop this behavior, but sometimes (not all the time) installing with either “ENABLEPRELAUNCH=false” or changing HKLM\SOFTWARE\WOW6432Node\Citrix\ICA Client\Prelaunch > “State” to “0” will prevent the pop-ups.
I’m concerned users will see this and be confused/worried by it since it looks odd. Any ideas for how to combat this would be greatly appreciated.
Thank you very much for all your extremely detailed information and for all your work on this guide, I have relied on it heavily!
Hey all,
I have a question. Currently Stores – Manage Authentication Methods we have Domain Pass-Through enabled and things work fine, people get logged on with domain credentials in Workspace app and are able to start their published applications fine.
Now we have several users, who want to logon to Workspace app, but they are from a different AD domain so Pass-Through cannot be used anymore.
When we disable Domain passthrough in Manage Authentications, every user gets a question to fill out their credentials.
So far so good.
Now back to the beginning, is it possible to enable Domain Pass-through authentication ON THE CLIENT SIDE, so we can let Storefront as it is, without Domain pass-through.
The clients login to XA servers so every day they connect to a different (random) server.
If anybody has any ideas on how to enable this, I would be very gratefull
hi carl
we dont get app protection running over the netscaler gateway. we will use the native receiver, but logon with token will not pass. we need the native receiver when i am right or not? but so than we need a local installed CWA what is going over NS GW. But no clue how to get it running. can you help?
Any advice or references on configuring CWA using Intune ADMX Ingestion? Doing the ADMX ingestion bit is easy, but some of the OMA-URI entries are….. frustrating. Seeing more and more MDM now over GPO.
Hi David,
Are you willing to share your ADMX ingestion details? I made some interesting findings with the ADMX ingestion of the Lenovo “CommercialVantage” ADMX that may potentially help you. Was going to use the CWA ADMX ingestion to potentially confirm. From my side of the fence, I found crucial details in this part of the registry – HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\AdmxDefault. There’s a GUID folder under here, and then essentially the path that worked in the OMA-URI of the Intune policy. When I do one way of ADMX ingestion, I only see two policies in here for CWA.
Happy to correspond on my Email (matthew.gailer@outlook.com) if you like.
Hello
I want to download Citrix WEM but I see an error: “This content is restricted. The content you are trying to access is restricted and requires additional permissions. To access the content, please sign in.”. But I am signed in.
The error screenshot is attached.
What should I do to download it?
Thanks
Are you licensed for CVAD Advanced Edition? https://www.citrix.com/products/citrix-virtual-apps-and-desktops/feature-matrix.html
If so, then you might have to call Citrix Customer Care.
Hi Carl, see my post regarding low video quality in HDX Teams on a Linux client: https://discussions.citrix.com/topic/410297-hdx-teams-performance-estimation-process-in-citrix-workspace-app-for-linux-set-to-very_slow/
Any clue to mitigate this issue?
For Teams optimization with Linux WorkSpaceApp 2006, if you cannot redirect audio and Webcam, you can probably solved your problem if you set thinclient language from local (french on our case) to english.
Hallo, starting with workspace app 19.12 (19.11 works without any issue) we got a slow “nervewreking” Citrix Workspace refresh application Animation -> https://www.youtube.com/watch?v=5s1Xdwu5EQ8
Any Workspace older than 19.12 is working as excpected. Any Workspace 19.12 an later does this.
Any Ideas?
This look like the older PNAgent method of connecting. Are you connecting to StoreFront? If you remove the store and re-add it, does it look more like it does in a web browser?
Hello Carl, I eventually found the “problem”. The selfservice.exe does an “ArrangeOverrides” Command (WPF-Framework). The workspace App Versions 1911 and lower do no animation in this case (the icons appear directly). The workspace App1912+ do a smooth fliy-in and fly-out (2-3 second each icon). So if i do a refresh, all icons fly out and back in. I have an open call at citrix; but I’ struggling to get the wanted logs of everything together; still trying.
The main problem may be, why all published apps disapear and reapear on every refresh. when this happens, selfservice.exe and explorer.exe are generating 50% CPU Usage each?
Hey Carl,
did somethng break on 2006 when using an old farm for Xenapp 6.5 Apps ? Our clients all of a sudden got problems with multimonitor support so that its not scaled right. we didnt change a thing on the xenapps and besides normal windows update nothng changed. its not even showing in the connection center but the app is opening. any ideas whats broken ?
How can Citrix Workspace prevent any subkeys from being created in HKEY_CURRENT_USER \ Software \ Citrix \ HDXRealTime \?
If it creates, then there are problems with the operation of the Webcam in Google Chrome
If your client-machines are domain-joined, then you can use group policy to change permissions on that key.
Yes, in the domain. But tell me how to do this? There is no HKCU in the policies, the settings for setting permissions for HKCU are not. Perhaps there are options for Citrix Workspace, just which one. Or maybe there is a key for HKEY_CURRENT_USER \ Software \ Citrix \ HDXRealTime \ – do not use this branch by the Citrix client. HKCU is current user, for HKLM – easy…
Maybe create a Scheduled Task that runs periodically that deletes that key and recreates it with whatever values you want?
If you want to delete the whole key (and its values), then group policy preferences can do that. Group policy preferences can also delete individual values.
You can delete it, it’s easy. But the policy works out every 15 minutes. When you launch a published application in the terminal, the Workspace client creates this branch in the registry and a Policies section. If after that the user launches the Web camera in Goolge Chrome, then everything is broken. Setting permissions is the most correct decision.
Try to work with the camera in Google Chrome on any public test resource on the Internet. Create a branch HKEY_CURRENT_USER \ Software \ Citrix \ HDXRealTime \. Create any subsection manually and start the camera again. Everything, the camera is broken.
Hello guys, I am facing this same situation, do you have any news about it?
https://support.citrix.com/article/CTX132764 – topic 7.1
Forcing the 854×480 definition worked for me.
Hey Guys,
I have a question. I run XenApp servers with the Workspace app 2006.1 installed with SSON so I can run an application from a win10 with VDA (published installaion).
When I try to run this published application, nothing happens, untill in the system tray I click the Workspace App symbol which only then triggers the SSO process (as it seems). Then I need to refresh applications (within workspace app) and after that I can start the published application.
What is preventing Workspace App the single sign on and get published applications process automatically?
Driving me nuts.
Thanks in Advance
Nobody???
In a login script, you can run SelfService.exe –poll or SelfService.exe –ipoll. https://support.citrix.com/article/CTX200337
Where is the 2006 documentation? All links here and on Citrix only point to 2002. Thanks
Hi! We have a customer having issues with blurry fonts. If the users log off, and reset Workspace client, the fonts looks good. Have tried different versions of the client, and installed the latest 2006 yesterday, but no solution. They are running on 7.15 cu5. They are also using 4K monitors. Yo have any idea how to resolve this? Thanks!
Seems like a DPI issue. Have you reviewed https://support.citrix.com/article/CTX230017?
Thanks! We have tried this out, but may need to do a new test. We have not tried with the latest release of the client. It also looks like this only happen to a few of the users, not everyone.
Hi I hope anyone can help me with my current issue with Citrix workspace 1907. Any application disable/enable changes i make on cloud console is not getting refreshed automatically on citrix workspace installed when i restart the server.
Citrix workspace application refresh doesnt happen automatically when i logon to workspace or simply restart the machine.
this function was working before and it is very hard to identify which policy is conflicting.
Note: We have Netscaler and Storefront on prem
Please help me with a solution. Thanks for the understanding
Workspace app 2002 throwing error while click on VDA desktop “error number 2308:. The citrix workspace received a corrupt ICA file. The key (coding]) has no associated value.”
Tried Citrix receiver cleanup tool, cleared app data, registry Citrix folders , created new windows profile and installed it still no luck.
Any advice?
Even version 19xx workspace app throws the same. But 18xx and receiver works fine.
Impacted version can work in browser HMTL 5 and downloadable ICA file from browser.
Try this – https://support.citrix.com/article/CTX115304
Hi Carl,
I have an issue in my Citrix environment. We have Citrix VDA Terminal session hosts with Win 2012 R2 (VDA 7.6) with 13 session hosts and 120 users logs in everyday. Users facing slowness throughout the Citrix, mouse clicking takes time, app switching takes time (alt tab or mouse click). But it is better in Citrix light version, problem only in full version. CPU & memory utilization is 60%.
Any suggestions from your side.
Is Legacy Graphics Mode enabled?
Newer VDAs have better codecs.
Yes, legacy graphic mode enabled. Anything else we can tune from Citrix end.
Try turning off Legacy Mode. Also, newer VDAs have much better codecs.
Actually, I have enabled the option post checking some articles due to slowness, so the slowness was there before enable and after enabled the legacy mode.
Sure, thanks for the response. I will turn off the legacy mode. I have one more doubt that our session performance is better in HTML5 but not in full ICA version. even some application works fine in HTML5 session and the same getting crashed in full mode ICA session (app launches fine but when click on selected button in the app crashes the app but this works fine in HMTL 5) what could be the cause, what is the difference between HTML5 based session and ICA based full mode session.
Hi Carl. How do we configure file transfer between chrome book using citrix workspace app and a published windows explorer. Is this possible? Any help
On the Workspace app for Chrome download page, under Additional Components is File Access. https://www.citrix.com/downloads/workspace-app/chrome/workspace-app-for-chrome-latest.html
Hey Carl…..I need a little help if possible. My customer is looking to install SSO with the Citrix Workspace App from a GPO. Users do not have any administrative rights. I placed the CitrixWorkSpaceApp.exe on a file share. I modified the Citrix provided startup scripts to create a BAT file and kicked that off in the GPO Startup Script. Commandline options I entered included /includeSSON and /ENABLE_SSON=yes. SSO is not getting installed. Keep in mind when I install the application on a machine logged in as admin, it works. I read where the startup script runs as LocalSystem which has full administrative rights but it doesn’t work in my scenario. I’m wondering if its because I put the application on a share. I also read that if I use a fileshare, the startup script doesn’t run as LocalSystem anymore but runs as ComputerAccount which is a regular user. I added ComputerAccount to local administrators group on system to see if that would work but it doesn’t. If I move the WorkSpaceApp off of a share, will it continue to install with LocalSystem account. And if it does, where would i move it to? A mapped drive that isn’t mapped yet? Is there a share I can put it on so it gets copied to the local system first? Any idea on how I can add SSO to Workspace using a GPO Windows Startup Script? Thanks, Todd.
Hello Carl, after I install Windows 10 Enterprise LTSC with Workspace app, I see only white screen. Meanwhile I have my citrix resource in start menu, have you any idea ? on every PC with other Windows 10 like LTSB version, no problem.
Thank you
Hi, do you found a solution?
Thank you!
I’m having conflicting experience with the installation of Workspace App installed as Admin vs non-admin and the claim that installing as Admin puts the citrix files into C:\Program Files (x86)\Citrix\ICA Client vs in AppData when a user installs.
I checked 3 environments and all have Citrix files in both C:\Program Files (x86)\Citrix\ICA Client. and AppData. AppData is not populated until a user launches a Citrix app.
We’ve been spending time troubleshooting sudden breaking citrix clients that all get the “This version of Citrix Workspace does not support selected encryption. Please contact your administrator.”
The users profile is broken and no RCU or DePalma’s PS script can resolve it. The user profile has to be deleted and recreated to get Citrix to work again. Then in breaks in 4-8 weeks for dozens of users. This sounds like something in our environment that we inherited that is updating a Appdata dll or HKCU reg key and corrupting it.
Is this environment the only one still experiencing the “This version of Citrix Workspace does not support selected encryption. Please contact your administrator.” error?
Thank you!
Hi Chris, did you ever find a resolve for this issue other than making a new user every few weeks ?
no – no resolution – its been going on for 7 months, I found this post 2 months ago. My experience is that once there are many files in the AppData, Citrix will break. Reading this post led me to believe that most of my users attempted Per-user installs and thats why AppData was populated and also why it broke. I’ve since cleaned out some profiles, cleared out Workspace App , then installed at Admin ONLY – it breaks within 2 months anyhow.
It most likely something in our environment, as a small amount of users are getting mic issues and only clearing out the profiles fixes that too – again pointing to my environments….
Method 2 worked for me after clean up tool and going through the reg and deleting all traces of citrix.
Method 1
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Policies\Citrix\ICA Client\Engine\Lockdown Profiles\All Regions\Lockdown\Logon\Local Credentials
LegacyLocalUserNameAndPassword
REG_SZ
True
Method 2
Delete:
C:\Users\%username%\AppData\Local\Microsoft\Windows\UsrClass.dat
You will need to be signed out of the affected account to delete.
I am getting below error form previously deployed shortcut icons. This is started after NetScaler gateway integration. Earlier receiver was pointing directly to storefront servers. If we reset the receiver everything will work fine, but we don’t have any option reset 5000 users receiver. Can someone please provide a solution?
Could not Start App
There was a problem contacting “PNAgent”
We are getting this error as well. So far the only thing that fixes it is to delete the user’s Windows profile, which is a drag. I would love to know if anyone has figured out a solution to this that isn’t so disruptive to the end user. We are having to delete user profiles at lease three times a week and some users have had this recur up to 5 times so far. We’ve only been using Citrix for about a year. We are using Citrix Workspace 1912 LTSR. We’ve tried uninstalling and reinstalling Citrix using the cleanup tool even though it is my understanding that it is no longer necessary with the Workspace app. We have seen this on Windows 10 Enterprise workstations from 1803 through 20H2. I’ve tried the solutions in https://support.citrix.com/article/CTX133536 but none work.
Confirm that C:\Program Files\Citrix\HDX\bin\;C:\Program Files (x86)\Citrix\HDX\bin is in your path